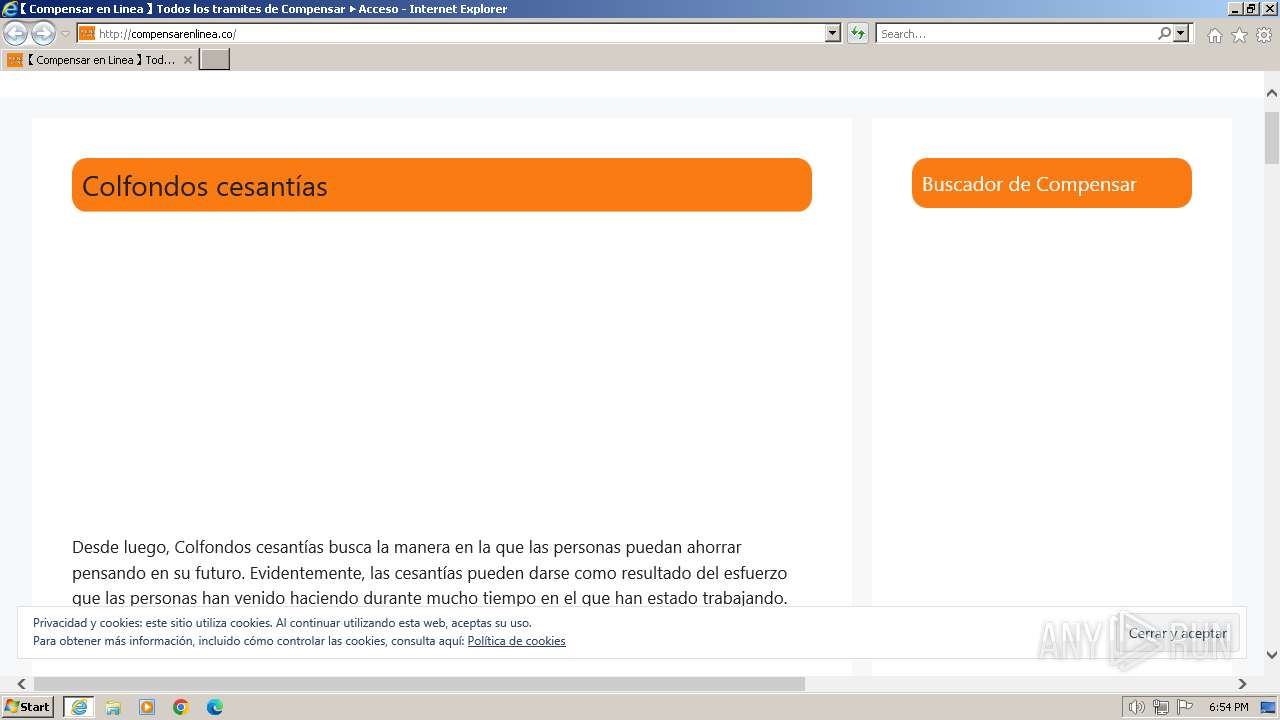
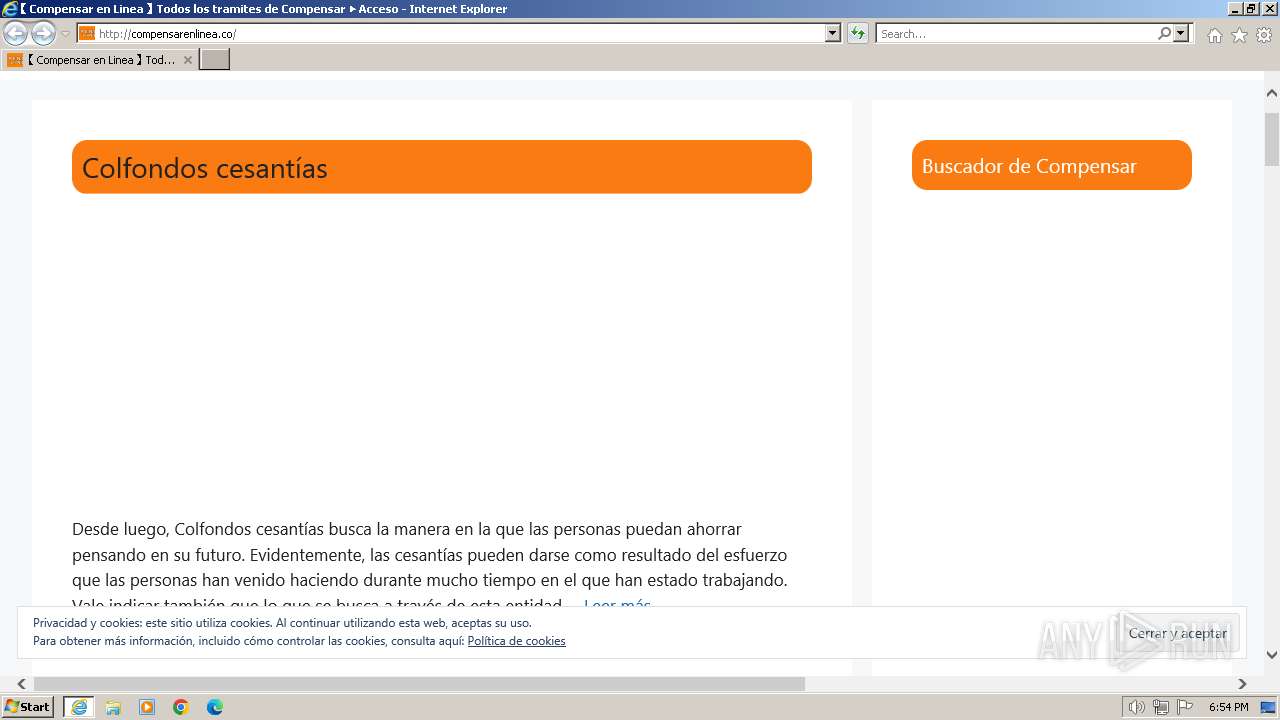
| URL: | compensarenlinea.co |
| Full analysis: | https://app.any.run/tasks/fccc8486-2c7f-4b0f-a6e7-4426543646e6 |
| Verdict: | Malicious activity |
| Analysis date: | January 18, 2024, 18:53:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A1AB8C63612E30642AEEF7CC6C45B6F4 |
| SHA1: | 3286B5D22D301E6104F8679226224110ADACBCD7 |
| SHA256: | 2366973652D59E920B88408FFC3ABD4BC4F9A20F4E7EC1CA22EE209D246F6915 |
| SSDEEP: | 3:OAiEXu8d:vld |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Internet Explorer\iexplore.exe" "compensarenlinea.co" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 324 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:116 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
36 065
Read events
35 972
Write events
89
Delete events
4
Modification events
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
32
Text files
63
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\style.min[1].css | text | |
MD5:CF235B02F713E74768216002C9A55FF6 | SHA256:FAE6C43A92A3CA2F58FBD857E48CE32D4EAD869440FBE3283BD016DA0865639B | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\main.min[1].css | text | |
MD5:B41333DEA9C0BC7B5493ACCF491D3FEF | SHA256:0468AF8D74BA377EEC707308168B6BFCD146FE0A2669A11A9AF0128AD85B3BC2 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\front.min[1].js | text | |
MD5:DB6AFE5FC3125BFBB7631CDC894F95F7 | SHA256:4B179562B883C1257AABBAD3A5641F965DD7331FAA31FE06382A5D8C62D5EE19 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\intersection-observer[1].js | text | |
MD5:ED3B4417DF0895E4CF8465D32B69ADC6 | SHA256:9900B23F9F49AF5F34387EB63A8673A563AB131C1E171CFAF14CF8B67A466B9D | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\screen.min[1].css | text | |
MD5:C36A54231034D43C59838CFFD223AE0E | SHA256:2E36BD3BDBB929F427E79A6C84B7922B4375589386981EBA29EB0CFF57B02B1B | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\mejorcluster[1].css | text | |
MD5:50EBB11CC679869C123DF9A00C1B6D2C | SHA256:D52E3E614CBEA1E87E4D7700CD6F9C78A68940E05E0DC7612636BD8F1DD62ED7 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\menu.min[1].js | text | |
MD5:203BFC7AB2D64673E71C76D7B20AEFEA | SHA256:775A02C37772954D38FE41B802B94A0EE37DCCB98A03827CDEF3EDDD2ABC13D1 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\widget-areas.min[1].css | text | |
MD5:A9C570C8914976CC3BAD2A46A9500376 | SHA256:E6B4122B94B82886E32952C07C78D342647B3A38A2834F4489E0922308A95EAB | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\infinite-scroll.pkgd.min[1].js | text | |
MD5:3245E69CE4F3B5B42B02B9D0EC2C9AB4 | SHA256:2D13EE814DE8E52A14D59B30841E65432E6534DA336D1B11EF76D936A9A7A74E | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\lazy-images[1].js | text | |
MD5:9855FB5D7DEE948D776D7E36EDE8A2C9 | SHA256:C99FFA666406B233D0791D6F9C7B4675C37AE1E537813B213BC3968A95321355 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
52
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
324 | iexplore.exe | GET | 200 | 178.211.133.33:80 | http://compensarenlinea.co/ | unknown | compressed | 71.4 Kb | unknown |
324 | iexplore.exe | GET | 200 | 178.211.133.33:80 | http://compensarenlinea.co/wp-content/plugins/mejorcluster/public/css/mejorcluster.css?ver=1.1.12 | unknown | compressed | 522 b | unknown |
324 | iexplore.exe | GET | 200 | 178.211.133.33:80 | http://compensarenlinea.co/wp-content/plugins/table-of-contents-plus/screen.min.css?ver=2106 | unknown | compressed | 471 b | unknown |
324 | iexplore.exe | GET | 200 | 178.211.133.33:80 | http://compensarenlinea.co/wp-content/themes/generatepress/assets/css/components/widget-areas.min.css?ver=3.2.0 | unknown | compressed | 829 b | unknown |
324 | iexplore.exe | GET | 200 | 178.211.133.33:80 | http://compensarenlinea.co/wp-content/themes/generatepress/assets/css/main.min.css?ver=3.2.0 | unknown | compressed | 5.36 Kb | unknown |
324 | iexplore.exe | GET | 200 | 178.211.133.33:80 | http://compensarenlinea.co/wp-content/plugins/gp-premium/blog/functions/css/style.min.css?ver=2.1.1 | unknown | compressed | 1.24 Kb | unknown |
324 | iexplore.exe | GET | 200 | 178.211.133.33:80 | http://compensarenlinea.co/wp-content/plugins/table-of-contents-plus/front.min.js?ver=2106 | unknown | compressed | 2.40 Kb | unknown |
324 | iexplore.exe | GET | 200 | 178.211.133.33:80 | http://compensarenlinea.co/wp-content/themes/generatepress/assets/js/menu.min.js?ver=3.2.0 | unknown | compressed | 1.85 Kb | unknown |
324 | iexplore.exe | GET | 200 | 178.211.133.33:80 | http://compensarenlinea.co/wp-content/plugins/jetpack/jetpack_vendor/automattic/jetpack-lazy-images/dist/intersection-observer.js?minify=false&ver=83ec8aa758f883d6da14 | unknown | compressed | 3.17 Kb | unknown |
324 | iexplore.exe | GET | 200 | 178.211.133.33:80 | http://compensarenlinea.co/wp-content/plugins/jetpack/jetpack_vendor/automattic/jetpack-lazy-images/dist/lazy-images.js?minify=false&ver=8767d0da914b289bd862 | unknown | compressed | 1.02 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
324 | iexplore.exe | 178.211.133.33:80 | compensarenlinea.co | Raiola Networks S.L. | ES | unknown |
324 | iexplore.exe | 192.0.77.37:443 | c0.wp.com | AUTOMATTIC | US | unknown |
324 | iexplore.exe | 178.211.133.33:443 | compensarenlinea.co | Raiola Networks S.L. | ES | unknown |
324 | iexplore.exe | 192.0.76.3:443 | stats.wp.com | AUTOMATTIC | US | unknown |
324 | iexplore.exe | 87.248.204.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
324 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
324 | iexplore.exe | 23.192.153.142:80 | x1.c.lencr.org | AKAMAI-AS | GB | unknown |
324 | iexplore.exe | 93.184.220.66:80 | platform.twitter.com | EDGECAST | GB | whitelisted |
324 | iexplore.exe | 157.240.251.9:443 | connect.facebook.net | FACEBOOK | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
compensarenlinea.co |
| malicious |
c0.wp.com |
| whitelisted |
stats.wp.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
connect.facebook.net |
| whitelisted |
platform.twitter.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |