| File name: | 699.exe |
| Full analysis: | https://app.any.run/tasks/5538eca3-9875-4c00-9f07-542f2180f561 |
| Verdict: | Malicious activity |
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | November 08, 2018, 17:54:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 97A449FED7D800A8A635592605FF8A67 |
| SHA1: | 2F339D8B2EDB7C07126D9A3C37EFFE14966817C5 |
| SHA256: | 233437B647F9482A8A3BA51D0AF69039BB58FB48609704A39DB1F709A0E6ACA6 |
| SSDEEP: | 12288:hEm67VkaivvtYku9hoVw7G/znXoABEg6s0u1Tw:dEivv+bGuuznXONq10 |
MALICIOUS
GandCrab keys found
- 699.exe (PID: 3744)
SUSPICIOUS
No suspicious indicators.INFO
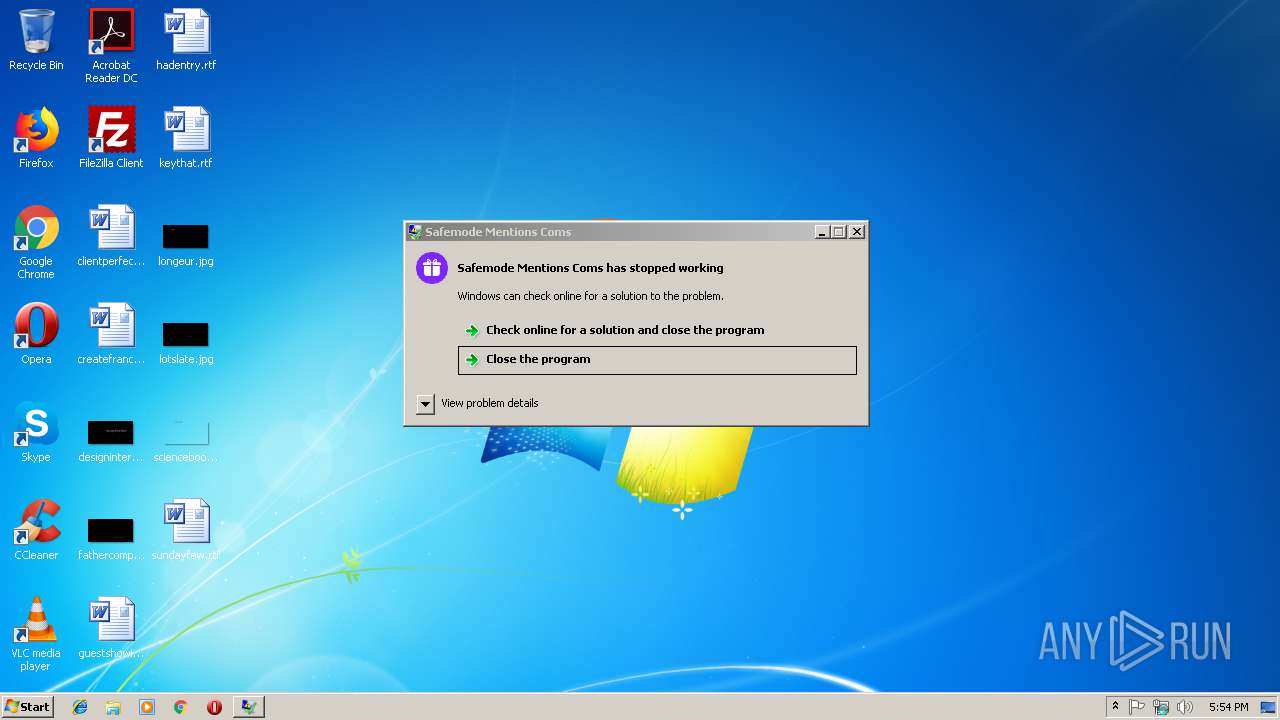
Application was crashed
- 699.exe (PID: 3744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (64.5) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (13.6) |
| .exe | | | Win32 Executable (generic) (9.3) |
| .exe | | | Clipper DOS Executable (4.1) |
| .exe | | | Generic Win/DOS Executable (4.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:11:07 22:01:29+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 98816 |
| InitializedDataSize: | 396288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa4c1 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.3.38.4 |
| ProductVersionNumber: | 5.3.38.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| PrivateBuild: | 5.3.38.4 |
| InternalName: | SelectivelyL2p |
| OriginalFileName: | SelectivelyL2p |
| FileDescription: | Safemode Mentions Coms |
| LegalCopyright: | (c). All rights reserved. HWorks |
| Languages: | English |
| CompanyName: | HWorks |
| ProductName: | SelectivelyL2p |
| LegalTrademarks: | (c). All rights reserved. HWorks |
| Comments: | Safemode Mentions Coms |
| FileVersion: | 5.3.38.4 |
| ProductVersion: | 5.3.38.4 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 07-Nov-2018 21:01:29 |
| Detected languages: |
|
| Debug artifacts: |
|
| PrivateBuild: | 5.3.38.4 |
| InternalName: | SelectivelyL2p |
| OriginalFilename: | SelectivelyL2p |
| FileDescription: | Safemode Mentions Coms |
| LegalCopyright: | (c). All rights reserved. HWorks |
| Languages: | English |
| CompanyName: | HWorks |
| ProductName: | SelectivelyL2p |
| LegalTrademarks: | (c). All rights reserved. HWorks |
| Comments: | Safemode Mentions Coms |
| FileVersion: | 5.3.38.4 |
| ProductVersion: | 5.3.38.4 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 07-Nov-2018 21:01:29 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00017688 | 0x00017800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.78949 |
.gcode | 0x00019000 | 0x000008E0 | 0x00000A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.91875 |
.rdata | 0x0001A000 | 0x000064D8 | 0x00006600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.55978 |
.data | 0x00021000 | 0x00003608 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.55819 |
.gdata | 0x00025000 | 0x000001D2 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.91269 |
.rsrc | 0x00026000 | 0x00058ED0 | 0x00059000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.7248 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.9402 | 634 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 2.86655 | 21640 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 2.25784 | 2664 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 3.40411 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 4.00359 | 2440 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 4.03401 | 1128 | Latin 1 / Western European | English - United States | RT_ICON |
101 | 3.08108 | 90 | Latin 1 / Western European | English - United States | RT_GROUP_ICON |
442 | 7.97101 | 6504 | Latin 1 / Western European | English - United States | RCDATA |
443 | 7.98449 | 235906 | Latin 1 / Western European | English - United States | RCDATA |
444 | 7.98353 | 65040 | Latin 1 / Western European | English - United States | RCDATA |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
KERNEL32.dll |
MSACM32.dll |
NETAPI32.dll |
SHELL32.dll |
SHLWAPI.dll |
Secur32.dll |
Total processes
33
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3744 | "C:\Users\admin\AppData\Local\Temp\699.exe" | C:\Users\admin\AppData\Local\Temp\699.exe | explorer.exe | ||||||||||||
User: admin Company: HWorks Integrity Level: MEDIUM Description: Safemode Mentions Coms Exit code: 3221225477 Version: 5.3.38.4 Modules
| |||||||||||||||
Total events
6
Read events
3
Write events
3
Delete events
0
Modification events
| (PID) Process: | (3744) 699.exe | Key: | HKEY_CURRENT_USER\Software\ex_data\data |
| Operation: | write | Name: | ext |
Value: 2E0074007800760072006D000000 | |||
| (PID) Process: | (3744) 699.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | public |
Value: 0602000000A4000052534131000800000100010015C8529915F177F53B3393FBED448C9798A6546E1AE8A3A3B1E55655AD70292EB64D84189C63D480DD84F80DFD2B60FA03AC1CF01C4B59A636A8CBB32FDDE7906224337F2D1F6D95173173F1C9577C74247E096289EECD27759FADC3940D0506C71F2107CDEC7304314847DBDC7B99C5DB0D89856A68F78A246C97A7B14B2C30CC9EF5038D7CF84589DFEEDDF854B5F0AA67809AE79CBD782440AF992D990EA0F33F6BC543A2C3E136E411942C02C81EC65FAD8CF9F90894743DF13999CDA75FEDA3C726BF6F16A6AC197DA4E68AC2C5CD70AA672E0F63B720870C3A35CD01EFDC088FC44027C74F539E1A0A9ACD1869718D10F6E0B77085D9E4B4182DB8919D | |||
| (PID) Process: | (3744) 699.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | private |
Value: 940400009D733DA06605A351FA888A6190F1B961A0F1ED3C108D5ED564C38F6B8357489DC104F19BF2A60CD474753C8F9C81D2813BDC600EC7B23EB8AA9164C47D7649A7681A644CAC6E6D5ECD3CEB6C383E3E6805A844EA88D06100C1B592ECA82DD45B484FB54B09A287F6A677FF8CE33F494E8981AA6B37B793DFACA4EA5E1FD7F2D54F71E162A37635EE42B3391D491400C88C38553E55C3D6B22A1015E7AE75AB23F2921E0FCF3407DA9ACC41173CCABB6FE186E568CD388D44615625CE648ADF258305534C12ED9C0A43F5E922A18F01AF903D0B87FCA43D4657FA40B2A14310649B46808AB047E70E79C9D5F72B77AA4E68C7EAB1F7467A098C6073E91B9B4874BF1C70262F9A968A08E9708BF764FD24972DF1055D38248757B5A6C6179D09BDE6AF97F2F7DD00B63A358DF71CACA201F62139A70A8533E13E1887EE14ABB46BB6F666B7E2811A7761C0B13F5B8B01CF91E8853CB72333CB6145ED39D5E9418B294BC938655011488A0CE1E2379D5DE0B844706D8CA0FDEC12D3BE958567D44F54A4AA99A9A4D722692EC3B549455F9A5B3920FB72EE87D9DE0587EBA83148AEAB7551C00F228AB73C50F03332E4BA38ADA14D52C5908F69D3F7491D56A59F11C2B7ED66DFDCFDAC9A4E814DBAF53CE62C5AFDB2F2E0C600F6C953B4C5DE2C3C4CD3584BAA824F9305E363A5774E8AA12E516A8CA7D851EB7E0FA7FEED72425E2018CBDAEFB148F713886224D39F6C953AA084CD05249512D45E431F3A5EA2472745AAE17C005E02AC2FEF29769B66C4954A0AEA71D6CB7BC530F10DDCD8E7EDBD99E1D6F7A8E0390778BCDDEBB39E21FFDAD30B1ECE302AF7CD2F67C46A21C015EBE1F95E41D5CE1CD5FB65A758084359D47519DBE67A55BF10B1FB55247B7AC4255BF3AB9CC7368A1D0216C45592DD096F4DE2ED80D4D9041BF2CC04C04D6D23FDAB28B7AEFBE5146DA30ECDE40D310E7E1A6E554BDF8E1879377FCF938AF34B681E53AE08F81D3ACE52CABB164FFF319C629340273197340DBCA5777FF83A25E25BA6CF3241D6475F876840AFD9F6F09DFB972F7C4DFAAB02E646C5EB5C04CDB8391D86BD10D98EE00352D2321BE7861354922FA5BB9DD7296CAF8BDC3D477F1518B6571DF4F280F3E1C7800760219FFF78E97C0CB660379B705E914D1506001340D0831B52FFD4036076D1AAF0A95466E480520B8FC7EA7F8290BF99781FC741D555ABF3CBE58D2F4FC77DC5E5D9EF05EDD623B884C863291633713A08C7EE175D2A2C5E8DEED55CB5138882C2AA3B43346BA7DE4B8812FFA0B4334387AFD694136A1B522336F440D0EAE52923C5E9D3214BBB9D608EDF45689869035923D253080C0AD281121C3BD21B9E71EFD66567CEBD9868C7AD9D726EE17E0A36FB8F2A54B32BA26702BAD54247881F5ABD01007E9560022B7C118ABC05B70DA7585707C342F7922CEB2B60AAD2B78D34C88429073E206E3A0E7BD506E05CDE99C5C366B9BBE0B9B7FF05861E887D176F7F06A73E5781BCA192750FD1442108D8BD09FE9BCC817CAE9850B507C5B1124858F4E54CCB3DA7D7BAB21377018F52E0DFE16012018EBDB52345CA8A5F05C302F42F5D2F58F053D718F3F04600274C6588A94AEFF8DB49C7D993F87347DC03E14699C32C0FC41B58DCBB805E734D9E350C29ACFD0E65DBBF0E8F06AC5188C320877CC95F43B4C4A57553A603D20393798F7E7EBA7139F7E81A521D4741BF1F6D5F68012E8A7A45820C16CE982DDB587803D746355B0103BED5E97E0C2E9FF2D065B8D06FD3D052B85C0D37AD26A362AB4EE0A4FA00071842448B033BB03F7E1777CFF0BC1308AB277AC2F87C57DA512EAA93A58949D3FFE81D168F8D080B9E7D9EA8627B3A78815E84F682E5CBD5EA75E909E8D910CD784C1872BA06E6DADBFAABEF2B71BDC04789A36DC6EA877AB254EFF40E708F32BDB3656E954909D28D5280FBB701BCF6836A60232AD377C8E380538F6E540DD178412CD7F1F539ED70EDD5D97493957435BD4DE174BAB80CAE3B948C7C0F48C596CD4AC11021802138AE83A8EC03EC5EEBDEA52824816A71617533D1A046B7FE963ED955FD43EC92012AC3E97C2651A4079D6B6ADE8496C491301D689DFAD06ADA9744F73CEFD84B3B6C9F5AEEF95B9C038F720B9E9F16F48231FA0283A0220132F80D703A4E3AEE3AD1FD4988562822A09E4667D87C6FDE0B06BA973AD9E24D187AFD3BFB1F943CF174FBF306D6CB368827C308C6466B001C9220661BCE0CE8FAFA3FE17D686EAA185FFA98648FB71884CBDC94D4A05DA47B295F2650D044A379230D84B52ADE4A797A3058E3C2D152AF86218AE75C572490CCF47FF32481EC45F140555F55F47FE9045DBA0C6ECC | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report