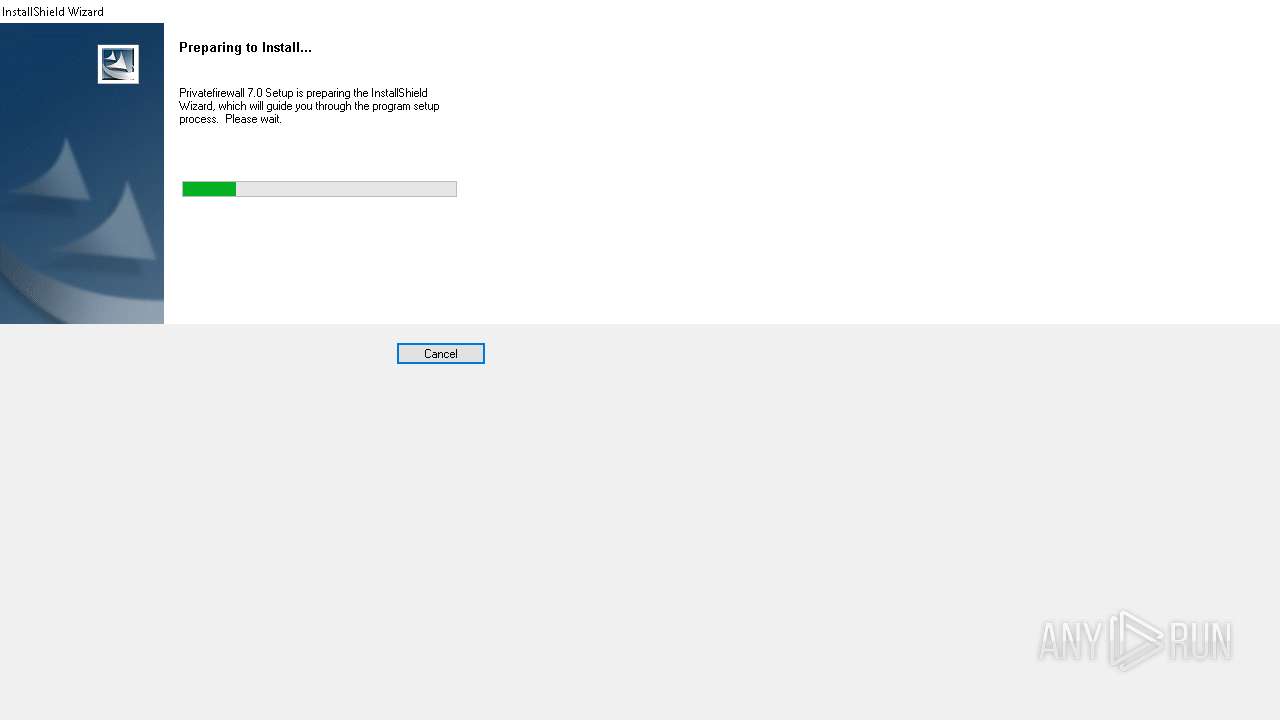
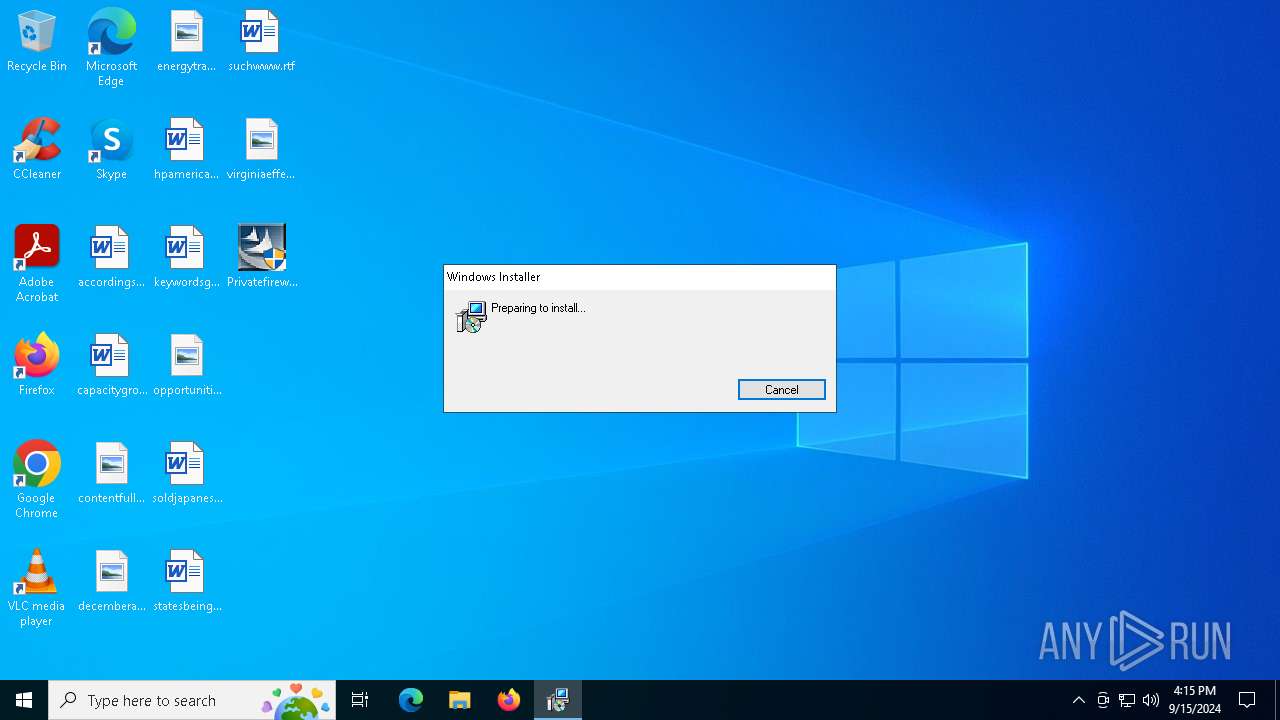
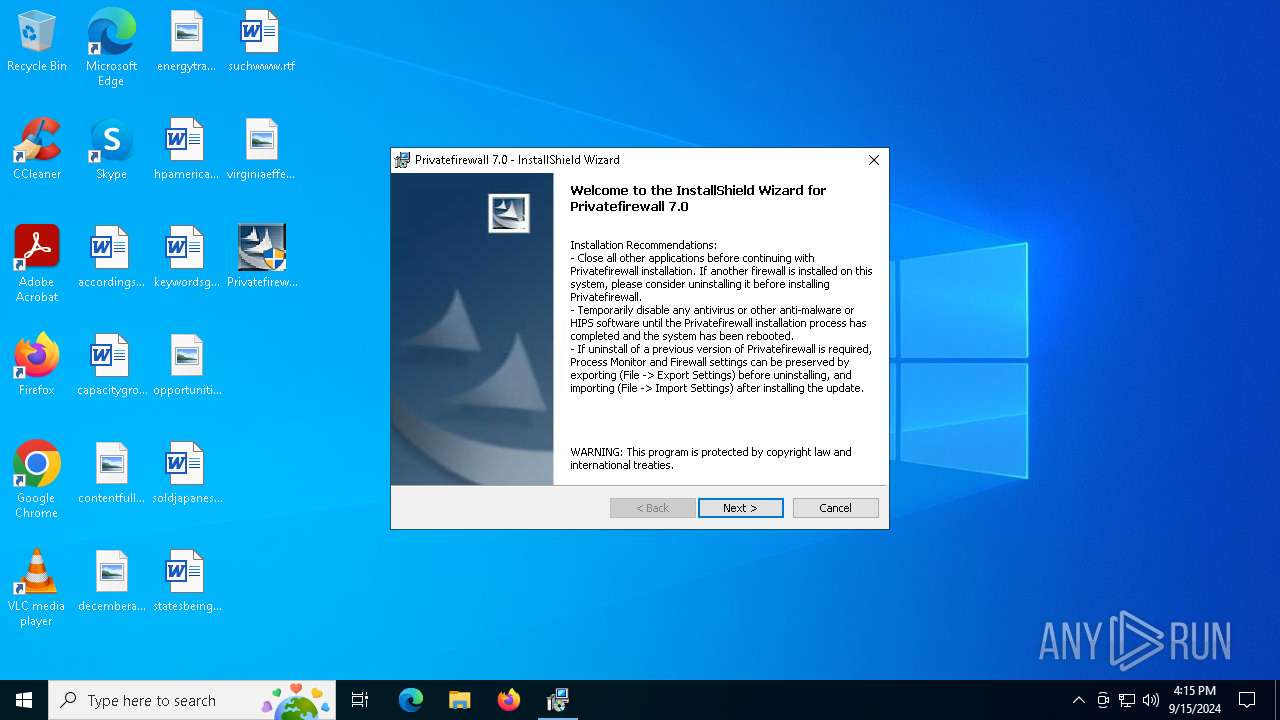
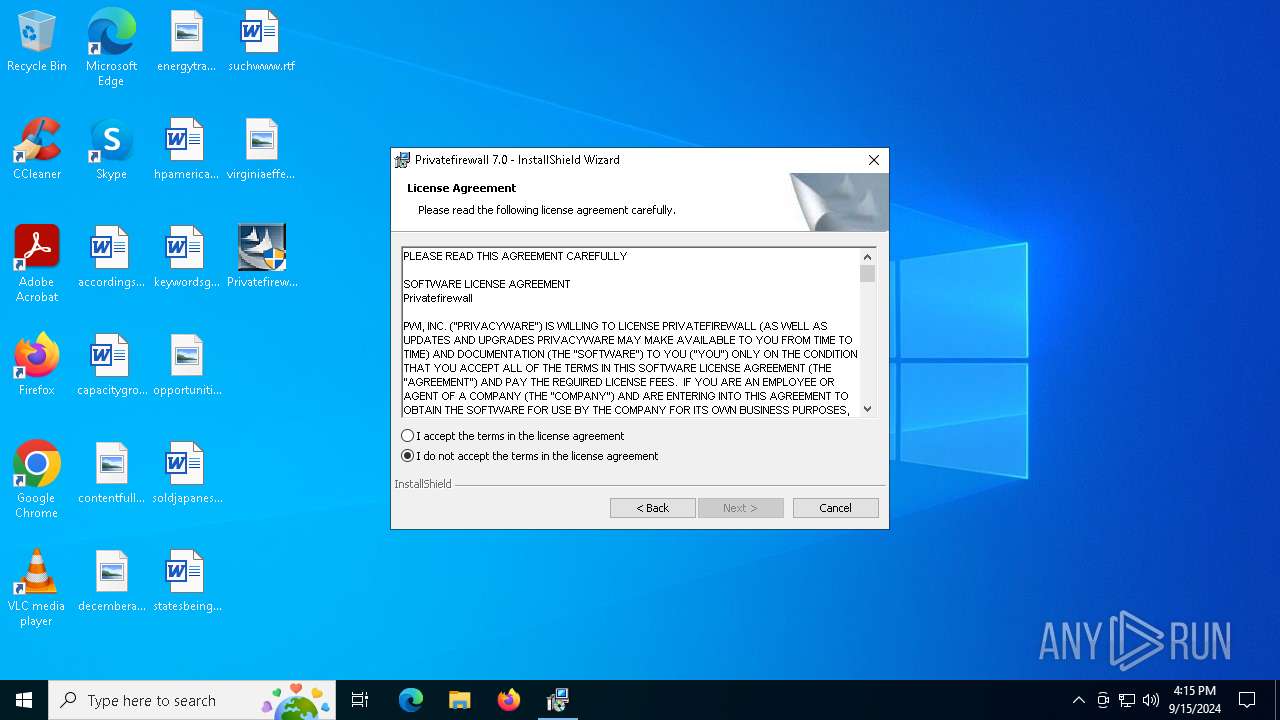
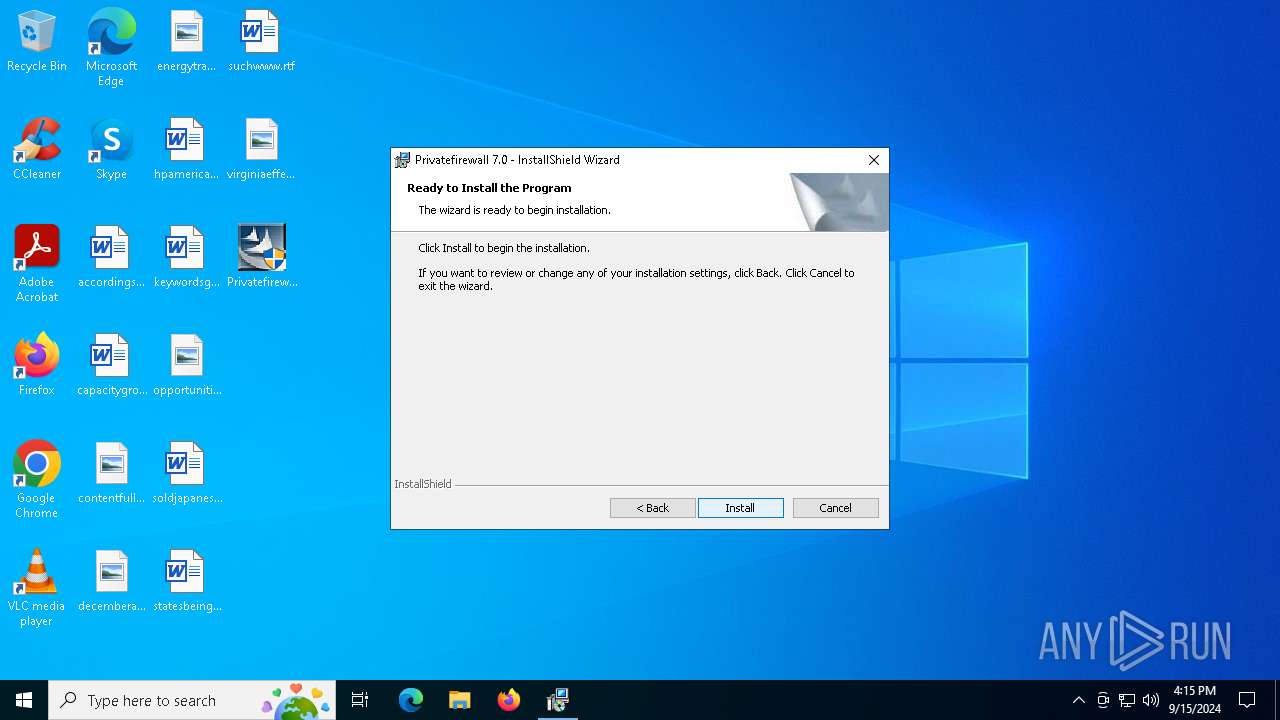
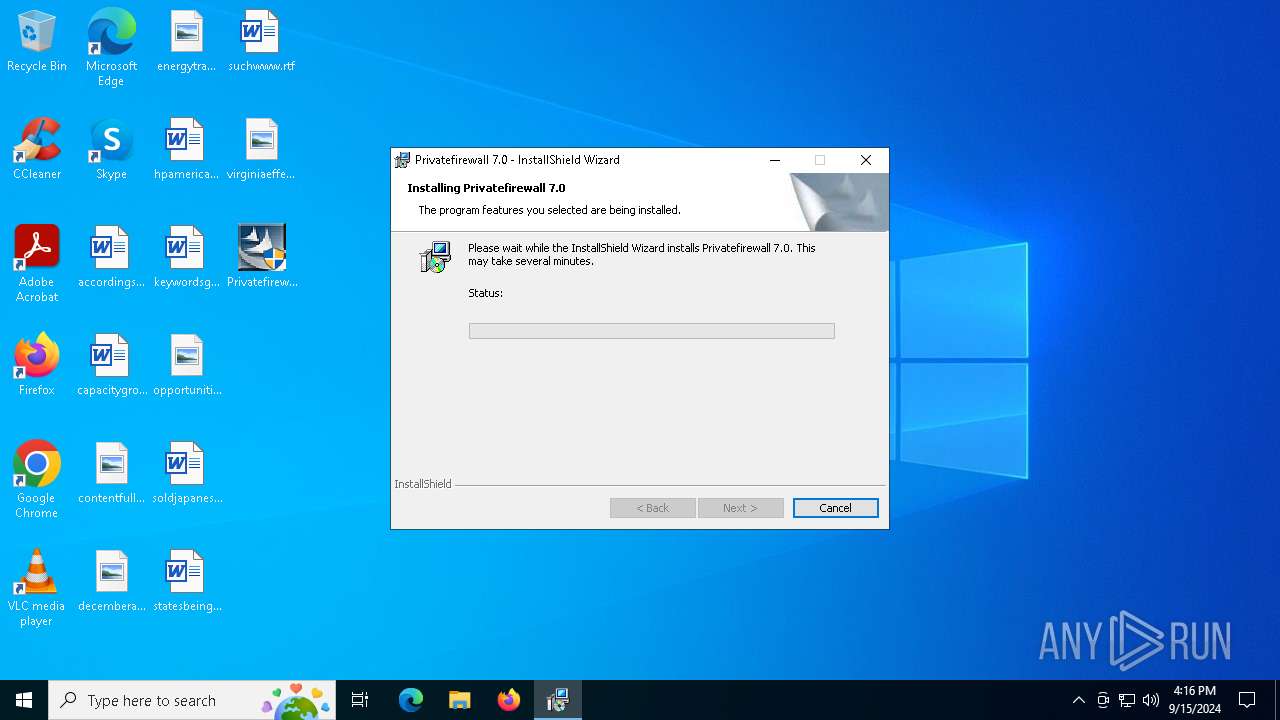
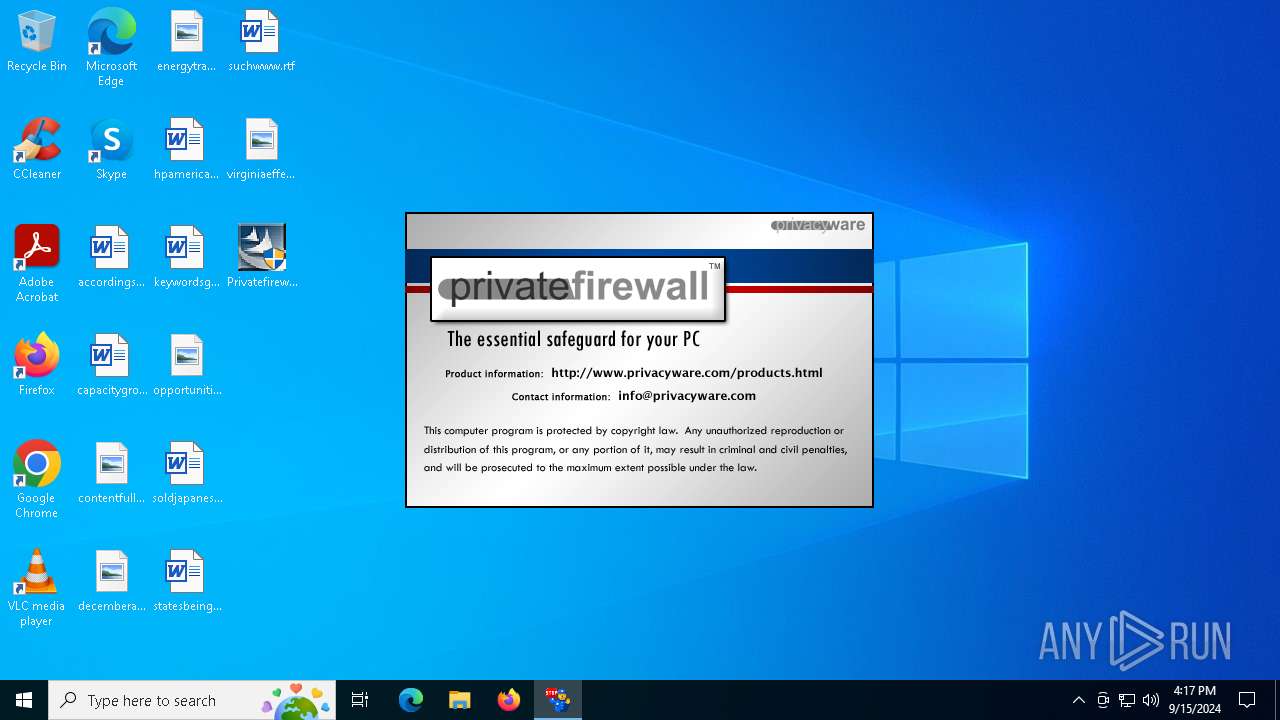
| File name: | Privatefirewall.7.0.30.3.exe |
| Full analysis: | https://app.any.run/tasks/2d432ed1-7e3e-45dc-b334-f8de892e7839 |
| Verdict: | Malicious activity |
| Analysis date: | September 15, 2024, 16:15:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1134918C235BEFFA66FA20C737AD539D |
| SHA1: | F7ADDF66A7271BDF3C9F098743C97042FBDC611A |
| SHA256: | 22F3CA36EB80670C5EEDFD8FFB72422A576E4F473E1FF92ABD28F754F11DF184 |
| SSDEEP: | 98304:Q2kwkZJ1QsX4nif4usQiTotCrN4mY5J9/A3s2h/Xgvp1arXljZxtmm7KBu6VTdI1:ML1sdL |
MALICIOUS
Changes the autorun value in the registry
- msiexec.exe (PID: 6840)
- msiexec.exe (PID: 2208)
SUSPICIOUS
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6840)
Executes as Windows Service
- VSSVC.exe (PID: 6164)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 6840)
- pwipf6.exe (PID: 5548)
- drvinst.exe (PID: 5516)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 2208)
Executable content was dropped or overwritten
- pwipf6.exe (PID: 5548)
- drvinst.exe (PID: 5516)
Creates files in the driver directory
- drvinst.exe (PID: 5516)
- pwipf6.exe (PID: 5548)
Checks Windows Trust Settings
- drvinst.exe (PID: 5516)
- pwipf6.exe (PID: 5548)
- PFGUI.exe (PID: 5960)
Reads security settings of Internet Explorer
- pwipf6.exe (PID: 5548)
- PFGUI.exe (PID: 5960)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 3404)
The process checks if it is being run in the virtual environment
- PFGUI.exe (PID: 5960)
Reads Microsoft Outlook installation path
- PFGUI.exe (PID: 5960)
Reads Internet Explorer settings
- PFGUI.exe (PID: 5960)
INFO
Checks supported languages
- msiexec.exe (PID: 6840)
- Privatefirewall.7.0.30.3.exe (PID: 4128)
- msiexec.exe (PID: 6284)
- msiexec.exe (PID: 2208)
- msiexec.exe (PID: 6012)
- pwipf6.exe (PID: 5548)
- drvinst.exe (PID: 5516)
- PLUGScheduler.exe (PID: 3404)
- PFGUI.exe (PID: 5960)
Create files in a temporary directory
- Privatefirewall.7.0.30.3.exe (PID: 4128)
- pwipf6.exe (PID: 5548)
- PFGUI.exe (PID: 5960)
Reads the computer name
- Privatefirewall.7.0.30.3.exe (PID: 4128)
- msiexec.exe (PID: 6840)
- msiexec.exe (PID: 6284)
- msiexec.exe (PID: 2208)
- msiexec.exe (PID: 6012)
- pwipf6.exe (PID: 5548)
- drvinst.exe (PID: 5516)
- PLUGScheduler.exe (PID: 3404)
- PFGUI.exe (PID: 5960)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5184)
- msiexec.exe (PID: 6840)
Creates a software uninstall entry
- msiexec.exe (PID: 6840)
Reads the machine GUID from the registry
- drvinst.exe (PID: 5516)
- pwipf6.exe (PID: 5548)
- PFGUI.exe (PID: 5960)
Reads the software policy settings
- pwipf6.exe (PID: 5548)
- drvinst.exe (PID: 5516)
- PFGUI.exe (PID: 5960)
Creates or modifies Windows services
- msiexec.exe (PID: 2208)
Manual execution by a user
- PFGUI.exe (PID: 5960)
Creates files in the program directory
- PLUGScheduler.exe (PID: 3404)
- PFGUI.exe (PID: 5960)
The process uses the downloaded file
- PFGUI.exe (PID: 5960)
Checks proxy server information
- PFGUI.exe (PID: 5960)
Disables trace logs
- PFGUI.exe (PID: 5960)
Creates files or folders in the user directory
- PFGUI.exe (PID: 5960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2003:09:03 09:09:31+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 139264 |
| InitializedDataSize: | 106496 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x194ec |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9.0.333.0 |
| ProductVersionNumber: | 9.0.0.0 |
| FileFlagsMask: | 0x0002 |
| FileFlags: | Pre-release |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | |
| CompanyName: | PWI, Inc. |
| FileDescription: | Setup Launcher |
| FileVersion: | 7.0.30.3 |
| InternalName: | setup.exe |
| OriginalFileName: | setup.exe |
| LegalCopyright: | Copyright (C) 2003 InstallShield Software Corp. |
| ProductName: | Privatefirewall 7.0 |
| ProductVersion: | 7.0.30.3 |
Total processes
260
Monitored processes
14
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1288 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2208 | C:\Windows\syswow64\MsiExec.exe -Embedding 473CBCC8A9A60E886828BF3CAABE9AD3 | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3404 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
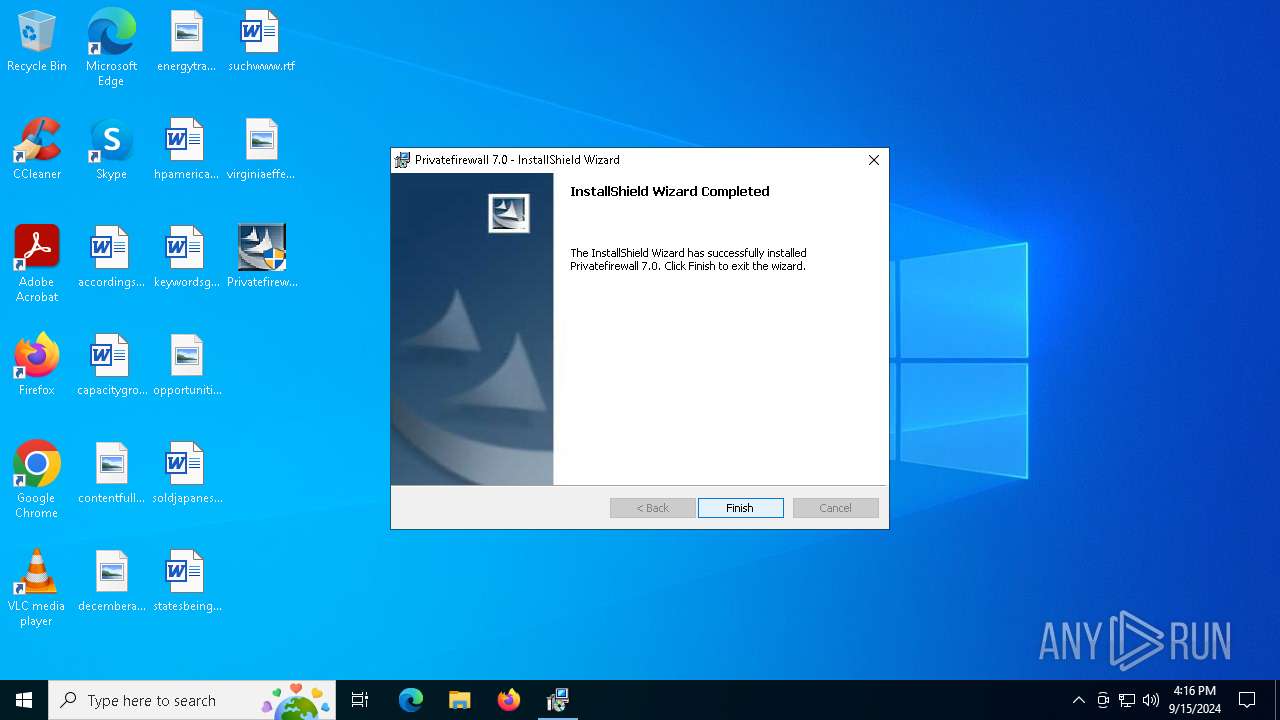
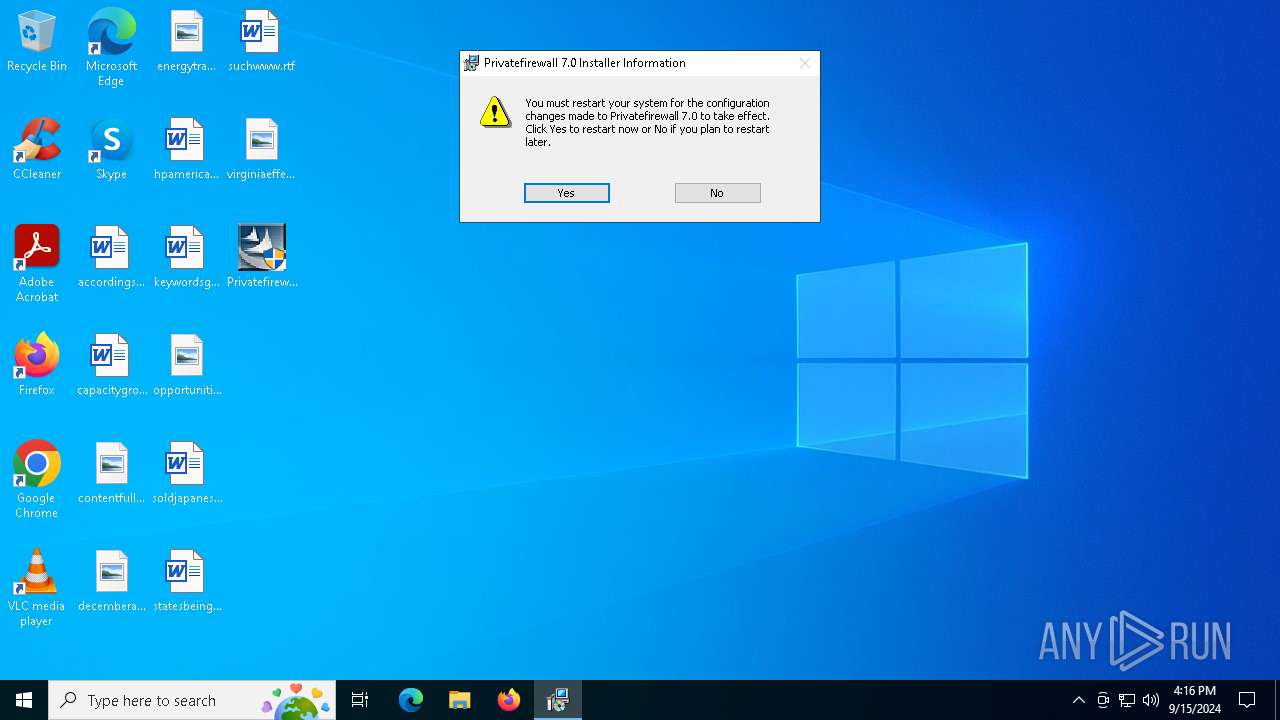
| 4128 | "C:\Users\admin\Desktop\Privatefirewall.7.0.30.3.exe" | C:\Users\admin\Desktop\Privatefirewall.7.0.30.3.exe | explorer.exe | ||||||||||||
User: admin Company: PWI, Inc. Integrity Level: HIGH Description: Setup Launcher Exit code: 1073807364 Version: 7.0.30.3 Modules
| |||||||||||||||
| 5044 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5184 | MSIEXEC.EXE /i "C:\Users\admin\AppData\Local\Temp\_isB4F1\Privatefirewall 7.0.msi" SETUPEXEDIR="C:\Users\admin\Desktop" | C:\Windows\SysWOW64\msiexec.exe | Privatefirewall.7.0.30.3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 1641 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5388 | "C:\Users\admin\Desktop\Privatefirewall.7.0.30.3.exe" | C:\Users\admin\Desktop\Privatefirewall.7.0.30.3.exe | — | explorer.exe | |||||||||||
User: admin Company: PWI, Inc. Integrity Level: MEDIUM Description: Setup Launcher Exit code: 3221226540 Version: 7.0.30.3 Modules
| |||||||||||||||
| 5516 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{f4a8f811-0a94-7b42-be8a-eb42704a9a22}\pwipf6.inf" "9" "4775f5ff3" "00000000000001E0" "WinSta0\Default" "00000000000001D0" "208" "C:\ProgramData\Privacyware\Privatefirewall" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5548 | pwipf6.exe /i | C:\ProgramData\Privacyware\Privatefirewall\pwipf6.exe | msiexec.exe | ||||||||||||
User: admin Company: Privacyware/PWI, Inc. Integrity Level: HIGH Description: PrivateFirewall Filter Install Application Exit code: 0 Version: 7, 0, 28, 1 Modules
| |||||||||||||||
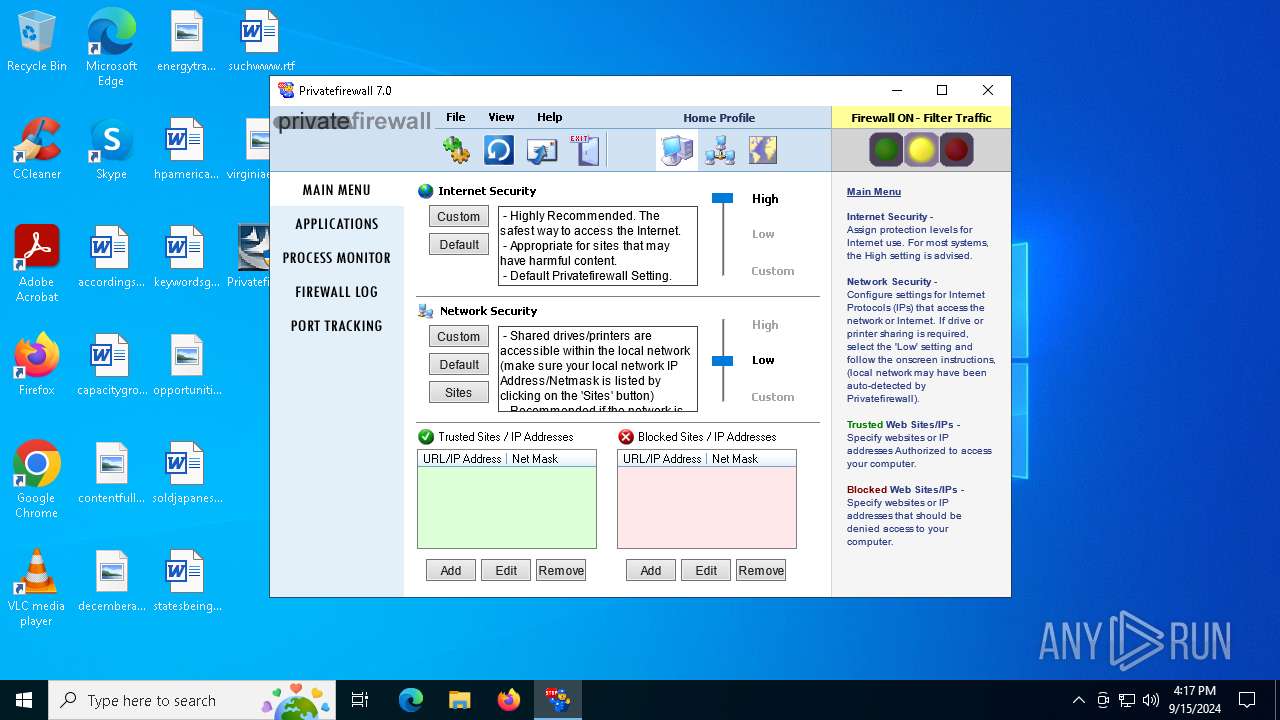
| 5960 | "C:\Program Files (x86)\Privacyware\Privatefirewall 7.0\PFGUI.exe" | C:\Program Files (x86)\Privacyware\Privatefirewall 7.0\PFGUI.exe | runonce.exe | ||||||||||||
User: admin Company: Privacyware/PWI, Inc. Integrity Level: MEDIUM Description: Privatefirewall 7.0 Application Version: 7, 0, 30, 3 Modules
| |||||||||||||||
Total events
16 781
Read events
15 286
Write events
1 194
Delete events
301
Modification events
| (PID) Process: | (5184) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (5184) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (5184) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (5184) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (6840) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000A4CCD68E8A07DB01B81A0000A01A0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6840) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000A4CCD68E8A07DB01B81A0000A01A0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6840) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000C414238F8A07DB01B81A0000A01A0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6840) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000007879258F8A07DB01B81A0000A01A0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6840) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000009CE1278F8A07DB01B81A0000A01A0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6840) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000DA442A8F8A07DB01B81A0000A01A0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
24
Suspicious files
73
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6840 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4128 | Privatefirewall.7.0.30.3.exe | C:\Users\admin\AppData\Local\Temp\~B4E1.tmp | binary | |
MD5:C7F549BE3E0FB519A95ECDF226A36742 | SHA256:9FB8EE7253D11F25B9082E6CC3C47CA450EAC873215DFBB5052728AB747E7D91 | |||
| 4128 | Privatefirewall.7.0.30.3.exe | C:\Users\admin\AppData\Local\Temp\_isB4F1\Privatefirewall 7.0.msi | binary | |
MD5:B1D86FD5F0CA7E95F7763DB1039ACA49 | SHA256:79752B8F52ABF0B39D7DA65F410E7E7DC9CB010739561D0171AE40BB955E0B8E | |||
| 5184 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSICA6C.tmp | executable | |
MD5:7F3DE8FD5015194169072A9D39F3E1AF | SHA256:A96F9EF51F87EB6786AC6857A61A35C43B0B8E9DF5A349DEEF23B20A8934CAE2 | |||
| 6840 | msiexec.exe | C:\Windows\Installer\MSI5BDF.tmp | executable | |
MD5:7F3DE8FD5015194169072A9D39F3E1AF | SHA256:A96F9EF51F87EB6786AC6857A61A35C43B0B8E9DF5A349DEEF23B20A8934CAE2 | |||
| 6840 | msiexec.exe | C:\Windows\Installer\MSI5E42.tmp | executable | |
MD5:EC6178B0AAAE2DC27560070C1E68F6CD | SHA256:7B5B3DFCD05F9DFA34B6E5915ABC079D88111BEB282D67BF8B13FE345F8FA4CD | |||
| 6840 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{ce65508a-61ab-4d98-840c-d49f62585c70}_OnDiskSnapshotProp | binary | |
MD5:8448C08D97E41F137A436AE57C76E554 | SHA256:9E18F2AC5E94F07FBFA790C56135A4D3A6DAF4052C573AC2E23C14E0FFB42359 | |||
| 6840 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:8448C08D97E41F137A436AE57C76E554 | SHA256:9E18F2AC5E94F07FBFA790C56135A4D3A6DAF4052C573AC2E23C14E0FFB42359 | |||
| 2208 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~5E50.tmp | text | |
MD5:F146293A9DAE1B9A662FACF0A9CBB101 | SHA256:0D12F8E9555A6584529E8CE3DC9C8B26F56AC27604012EF4C03ECF94BC7019C2 | |||
| 6840 | msiexec.exe | C:\Windows\Installer\MSI5EA1.tmp | executable | |
MD5:7F3DE8FD5015194169072A9D39F3E1AF | SHA256:A96F9EF51F87EB6786AC6857A61A35C43B0B8E9DF5A349DEEF23B20A8934CAE2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
33
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
608 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5960 | PFGUI.exe | GET | 301 | 104.21.62.77:80 | http://www.privacyware.com/software/privatefirewall.xml | unknown | — | — | unknown |
— | — | GET | 200 | 92.123.104.41:443 | https://www.bing.com/fd/ls/l?IG=16800713CD244755B15D5E88DF9D3BC0&Type=Event.ClientInst&DATA=[{%22T%22:%22CI.ClientInst%22,%22FID%22:%22CI%22,%22Name%22:%22max%20errors%20reached%22}] | unknown | — | — | unknown |
— | — | GET | 404 | 92.123.104.18:443 | https://r.bing.com/rb/4N/jnc,nj/Btu7tBP0vQIHDIMxag4vCxAtQuY.js?bu=FrYs9ir8AYcriyuNK48rtCu9LIMs_BGfLKUswSz8AfwBpSjmK_oR8RH6K-sr&or=w | unknown | — | — | unknown |
— | — | GET | 200 | 92.123.104.32:443 | https://r.bing.com/rb/6j/ortl,cc,nc/QNBBNqWD9F_Blep-UqQSqnMp-FI.css?bu=AboK&or=w | unknown | — | — | unknown |
2040 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 404 | 172.67.221.205:443 | https://www.privacyware.com/software/privatefirewall.xml | unknown | html | 177 b | unknown |
— | — | GET | 200 | 92.123.104.21:443 | https://r.bing.com/rp/-UAIppANYxiGpRWJy2NDph4qOEw.gz.js | unknown | text | 20.3 Kb | unknown |
— | — | POST | 204 | 92.123.104.35:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
608 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2040 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
608 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2040 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
608 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
r.bing.com |
| whitelisted |
www.privacyware.com |
| unknown |
www.bing.com |
| whitelisted |