| File name: | SirHurt V4.exe |
| Full analysis: | https://app.any.run/tasks/aa29b6c7-2494-4aed-b9c8-a3d59f0d822c |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2024, 19:22:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7C3571A7144EC0C26D3A9D79372FFF35 |
| SHA1: | 3296D8DCE9241321C67A16345C58258D53AA5853 |
| SHA256: | 22E8E3D7E060D661F3D7AA3A8C1161C79AE82DA32CEE3B8C2C9786FB2E850DA1 |
| SSDEEP: | 98304:Wdpgu4ewCl1HujBKUlVqaphqLHbuBYKqR9c4Uhsdlwq/SkNqlaT4n5vwMTe/zFNz:Mj7sWN0dC+soFM+ttGJSB |
MALICIOUS
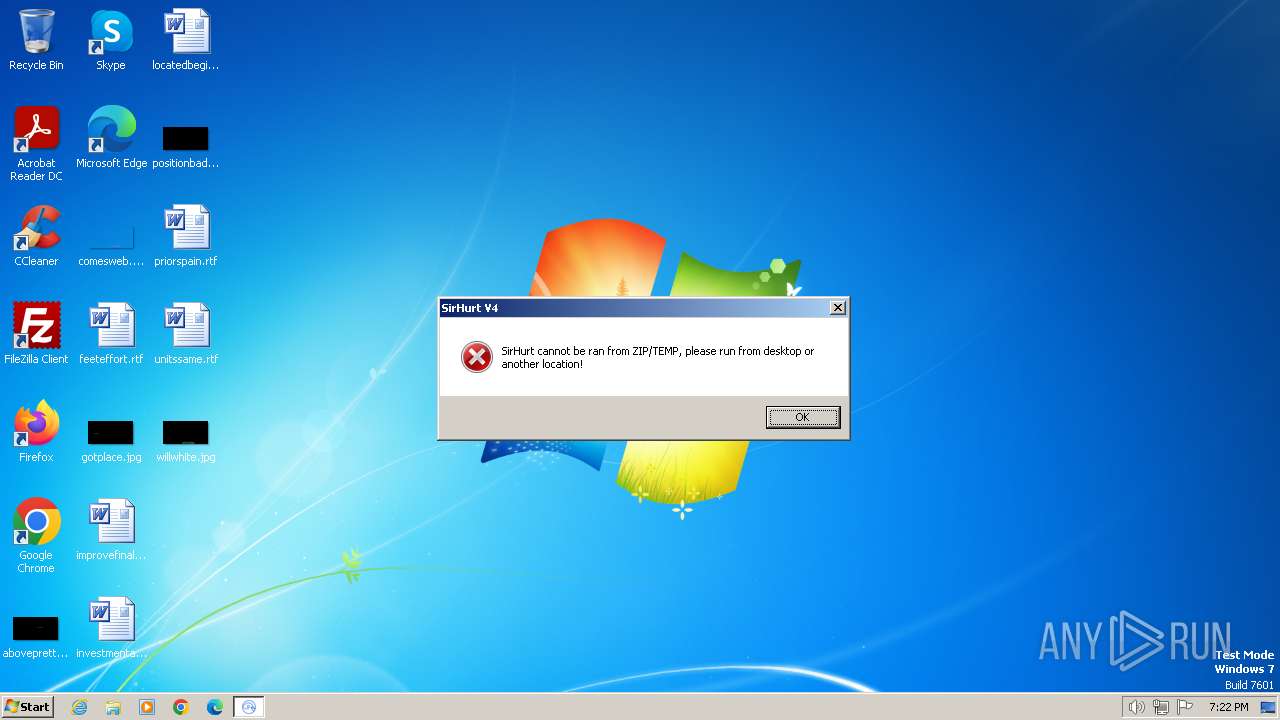
Drops the executable file immediately after the start
- SirHurt V4.exe (PID: 2036)
SUSPICIOUS
Reads the BIOS version
- SirHurt V4.exe (PID: 2036)
INFO
Checks supported languages
- SirHurt V4.exe (PID: 2036)
Reads the computer name
- SirHurt V4.exe (PID: 2036)
Create files in a temporary directory
- SirHurt V4.exe (PID: 2036)
Reads the machine GUID from the registry
- SirHurt V4.exe (PID: 2036)
Creates files or folders in the user directory
- SirHurt V4.exe (PID: 2036)
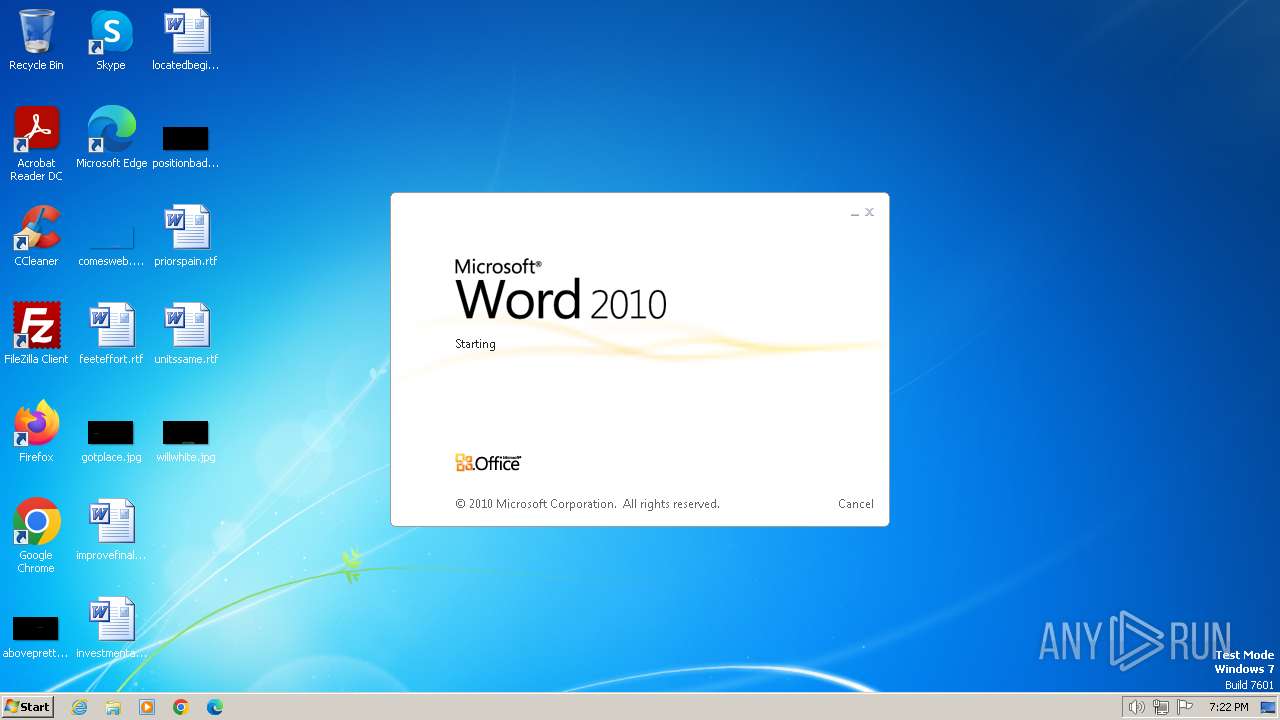
Manual execution by a user
- WINWORD.EXE (PID: 2068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2040:06:15 06:34:53+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 7749120 |
| InitializedDataSize: | 36352 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xcf6058 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Sirhurt V4 |
| FileVersion: | 1.0.0.0 |
| InternalName: | Sirhurt V4.exe |
| LegalCopyright: | Copyright © 2020 |
| LegalTrademarks: | - |
| OriginalFileName: | Sirhurt V4.exe |
| ProductName: | Sirhurt V4 |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
35
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2036 | "C:\Users\admin\AppData\Local\Temp\SirHurt V4.exe" | C:\Users\admin\AppData\Local\Temp\SirHurt V4.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Sirhurt V4 Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2068 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\unitssame.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 689
Read events
2 235
Write events
317
Delete events
137
Modification events
| (PID) Process: | (2068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (2068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
1
Suspicious files
4
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2068 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR292E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2068 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:CB74A710D47AA8124E57BEFB64816944 | SHA256:768644E16A10CD41867500A90587FBAD5B6A2C562A7E7C4B8BABC7C0E499411B | |||
| 2036 | SirHurt V4.exe | C:\Users\admin\AppData\Local\Packages\ROBLOXCORPORATION.ROBLOX_55nm5eh3cm0pr\AC\sirhurt\sirhui\sirhurtw.dat | text | |
MD5:10B03F6B0A4CEA538F518172AA1EC820 | SHA256:1124D012B5A6AC9937960E29B7E7CB984E6758116124F1C6913B6449612E65EB | |||
| 2068 | WINWORD.EXE | C:\Users\admin\Desktop\~$itssame.rtf | binary | |
MD5:3C4EFC550AB3FC9BC89F06E605465D06 | SHA256:6B46EA9CFEC35AE0D688EC4FBE702EDD579A88B43825A5BA4289C997B45FDA3F | |||
| 2068 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\unitssame.rtf.LNK | binary | |
MD5:056ED606E62E913A11AF1E88D406D8E6 | SHA256:54C637BF9F3C4B5C5D3A3FA343B61FCBDB9A89224486CDDB93FCD408EF1F1460 | |||
| 2036 | SirHurt V4.exe | C:\Users\admin\AppData\Local\Temp\bin\DebugData.txt | text | |
MD5:8E66019A88F0A3514018C70CE174466E | SHA256:954305B90583D2D8449F6DD8D7B1357C47CB11DA0FAB37F4BA30AC9F7A48B6CB | |||
| 2068 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:5ADA66AC94DE4E39DB9ACD4CF39E1750 | SHA256:F1C07329133C09BF7C4847FF71ED5A903689F9300896C0CECBFF86878E4F0742 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |