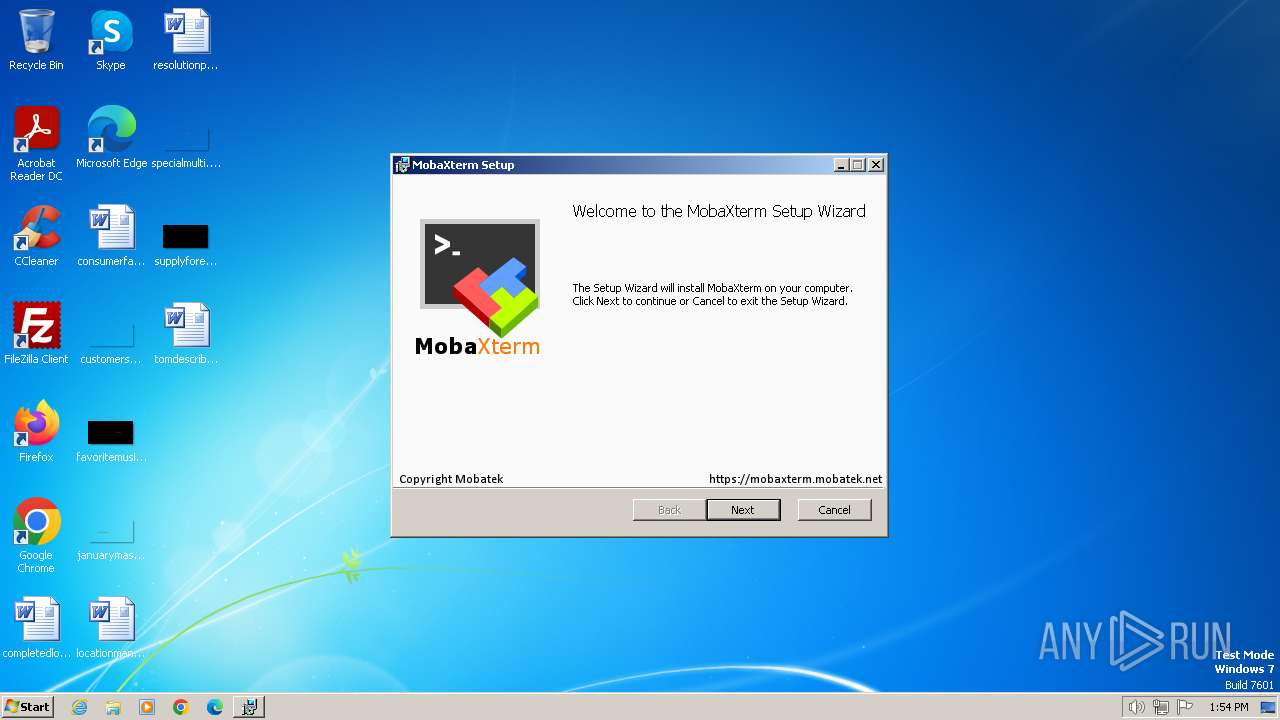
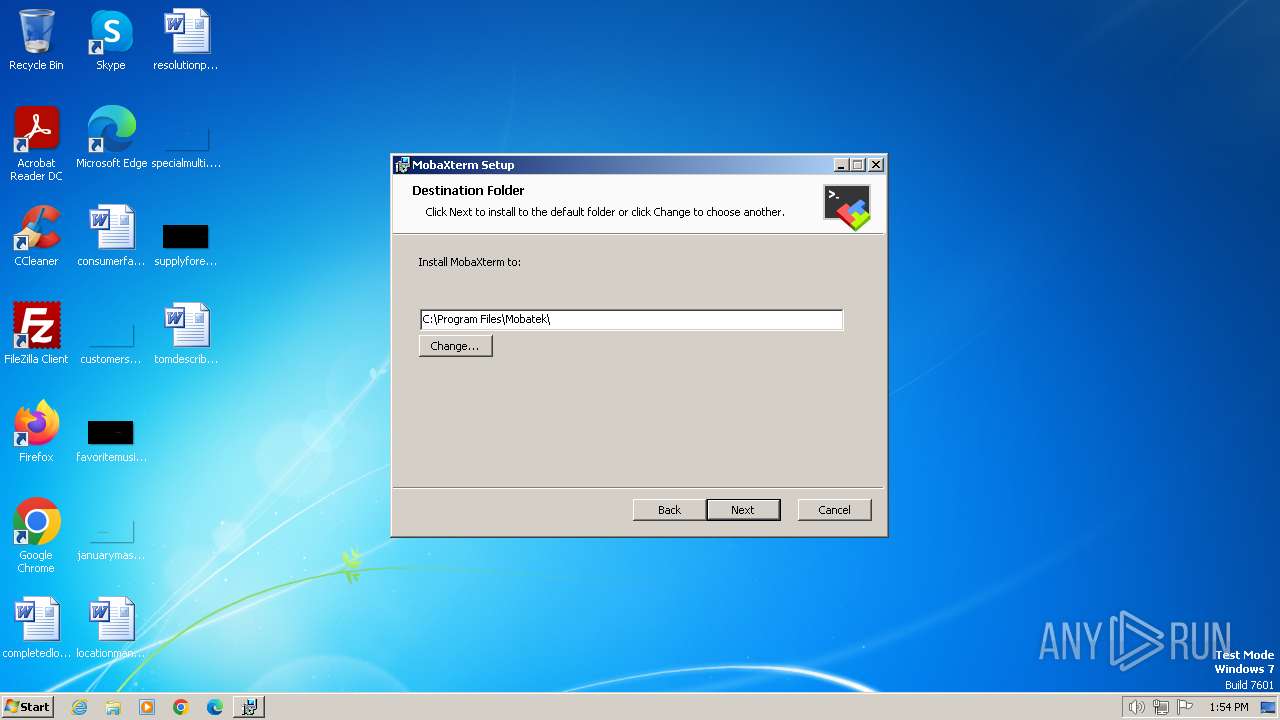
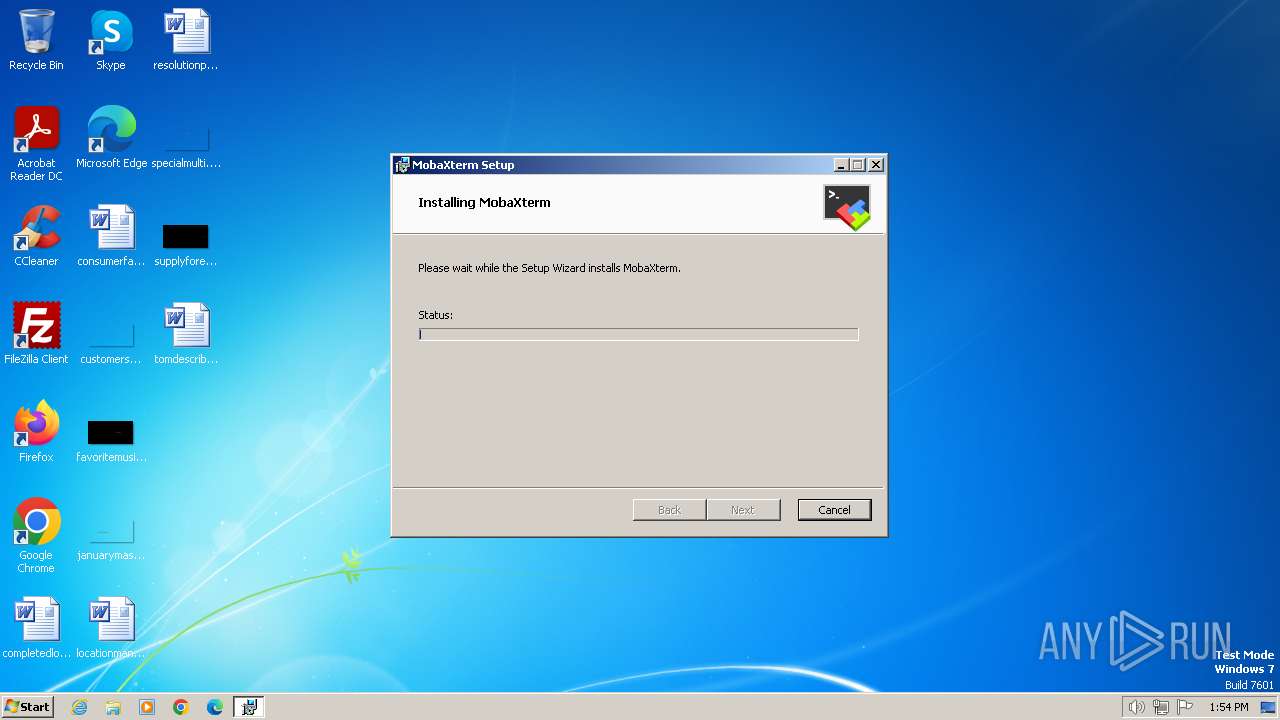
| File name: | MobaXterm_installer_24.0.msi |
| Full analysis: | https://app.any.run/tasks/bc8ea2b6-6215-4062-9441-3774cbfa12b7 |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2024, 12:54:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Title: Installation Database, Subject: MobaXterm, Author: Mobatek, Keywords: Installer, Comments: This installer database contains the logic and data required to install MobaXterm., Template: Intel;1033, Revision Number: {F91FC256-FD29-44CB-908F-87A511F5B6D2}, Create Time/Date: Sun Feb 25 20:10:50 2024, Last Saved Time/Date: Sun Feb 25 20:10:50 2024, Number of Pages: 100, Number of Words: 2, Name of Creating Application: Windows Installer XML (3.0.5419.0), Security: 2 |
| MD5: | 472A864C6648BB01F0CDD44F942E5E62 |
| SHA1: | 47C3B829BF4ADA054EE7C7BCBD101EDD82DE0CE2 |
| SHA256: | 22D4EDC469689EB8712333DC5A578733BD8305E28895A91685208945B81BDA92 |
| SSDEEP: | 98304:ypJbYMgGUzIYXULckiXi0Smt18NsQ8V0gQbaznnRyy3IdoRLwhdnXSKeywDcTjUc:+Ah8O0Iv9czpD8XISjGyLUuR1Fv |
MALICIOUS
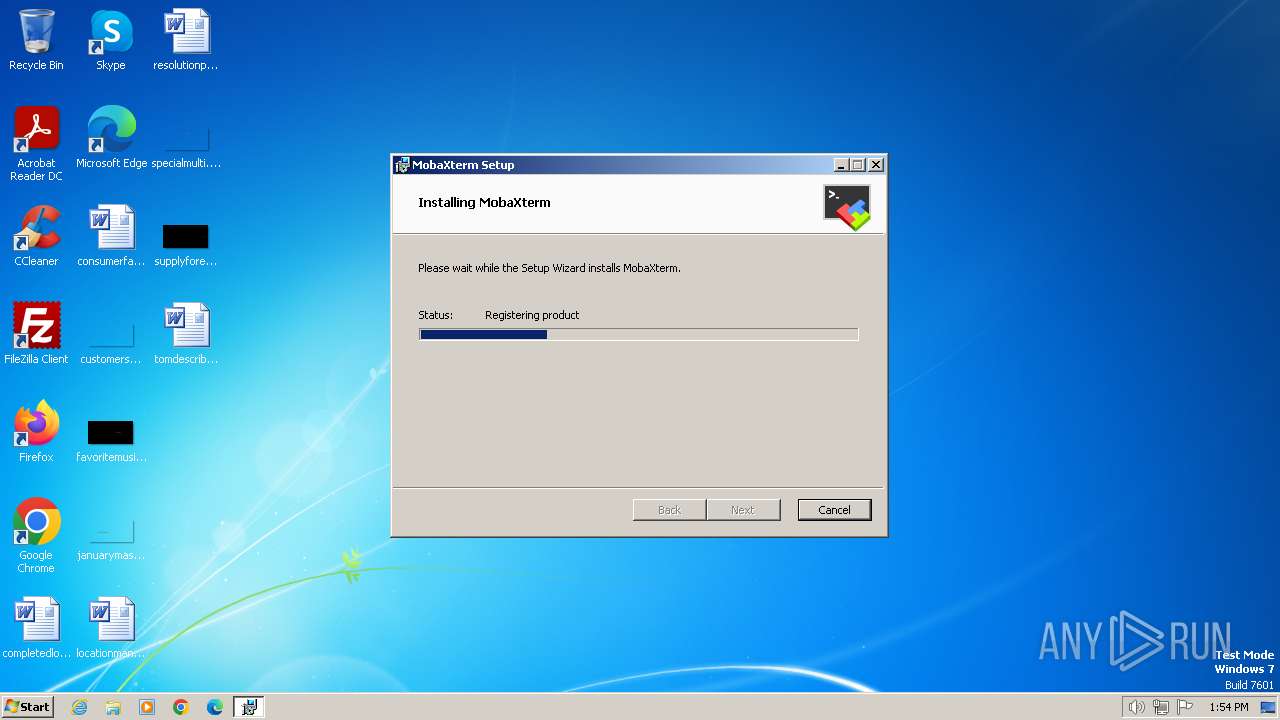
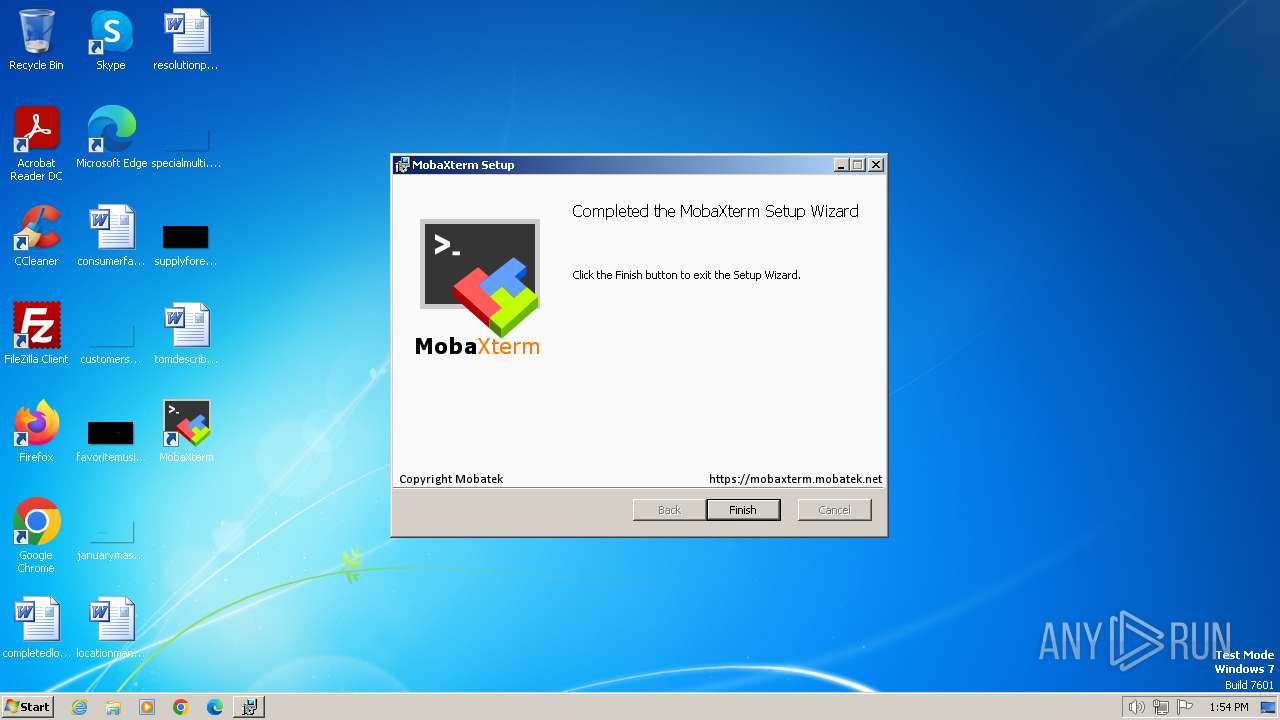
Drops the executable file immediately after the start
- msiexec.exe (PID: 1036)
- MobaXterm.exe (PID: 2932)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 1036)
Executes as Windows Service
- VSSVC.exe (PID: 4080)
Executable content was dropped or overwritten
- MobaXterm.exe (PID: 2932)
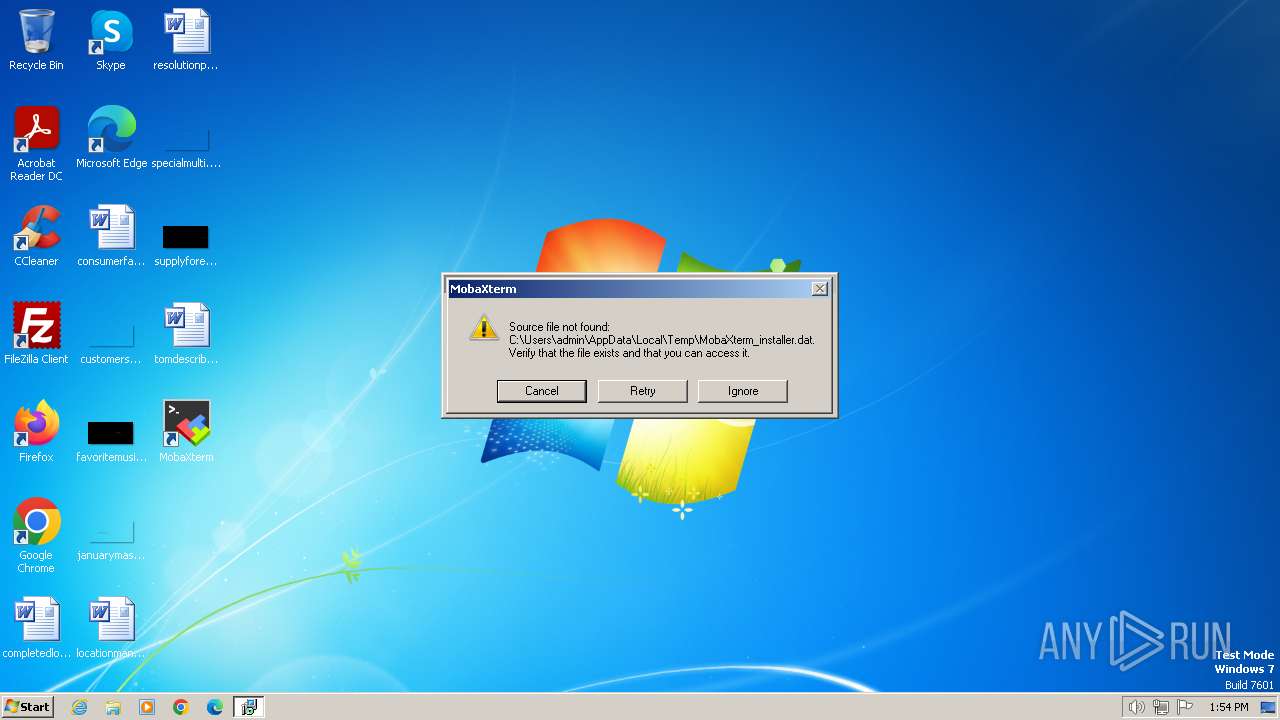
The process creates files with name similar to system file names
- MobaXterm.exe (PID: 2932)
Reads the Internet Settings
- MobaXterm.exe (PID: 2932)
Reads security settings of Internet Explorer
- MobaXterm.exe (PID: 2932)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1036)
Reads the software policy settings
- msiexec.exe (PID: 1036)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1036)
Checks supported languages
- MobaXterm.exe (PID: 2932)
- XWin_MobaX.exe (PID: 3344)
- xkbcomp_w32.exe (PID: 2648)
Reads product name
- MobaXterm.exe (PID: 2932)
Manual execution by a user
- MobaXterm.exe (PID: 2932)
Reads mouse settings
- MobaXterm.exe (PID: 2932)
Reads the computer name
- MobaXterm.exe (PID: 2932)
- XWin_MobaX.exe (PID: 3344)
Reads the machine GUID from the registry
- MobaXterm.exe (PID: 2932)
Create files in a temporary directory
- msiexec.exe (PID: 1036)
Creates files or folders in the user directory
- MobaXterm.exe (PID: 2932)
- XWin_MobaX.exe (PID: 3344)
- xkbcomp_w32.exe (PID: 2648)
Reads Environment values
- MobaXterm.exe (PID: 2932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | MobaXterm |
| Author: | Mobatek |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install MobaXterm. |
| Template: | Intel;1033 |
| RevisionNumber: | {F91FC256-FD29-44CB-908F-87A511F5B6D2} |
| CreateDate: | 2024:02:25 20:10:50 |
| ModifyDate: | 2024:02:25 20:10:50 |
| Pages: | 100 |
| Words: | 2 |
| Software: | Windows Installer XML (3.0.5419.0) |
| Security: | Read-only recommended |
Total processes
50
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1036 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\MobaXterm_installer_24.0.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2648 | "C:\Users\admin\AppData\Roaming\MobaXterm\slash\bin\xkbcomp_w32.exe" -w 1 "-RC:\Users\admin\AppData\Roaming\MobaXterm\slash\usr\share\X11\xkb" -xkm "C:\Users\admin\AppData\Roaming\MobaXterm\slash\var\log\xwin\xkb_a03812" -em1 "The XKEYBOARD keymap compiler (xkbcomp) reports:" -emp "> " -eml "Errors from xkbcomp are not fatal to the X server" "C:\Users\admin\AppData\Roaming\MobaXterm\slash\var\log\xwin\server-0.xkm" | C:\Users\admin\AppData\Roaming\MobaXterm\slash\bin\xkbcomp_w32.exe | — | XWin_MobaX.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2932 | "C:\Program Files\Mobatek\MobaXterm\MobaXterm.exe" | C:\Program Files\Mobatek\MobaXterm\MobaXterm.exe | explorer.exe | ||||||||||||
User: admin Company: Mobatek Integrity Level: MEDIUM Description: MobaXterm Version: 24.0.0.5204 Modules
| |||||||||||||||
| 3344 | "C:\Users\admin\AppData\Roaming\MobaXterm\slash\bin\XWin_MobaX.exe" -silent-dup-error -notrayicon -nolisten inet6 -hostintitle +bs -clipboard -nowgl -multiwindow -noreset :0 | C:\Users\admin\AppData\Roaming\MobaXterm\slash\bin\XWin_MobaX.exe | — | MobaXterm.exe | |||||||||||
User: admin Company: Mobatek Integrity Level: MEDIUM Description: MobaXterm embedded X11 server Version: 21.1.8 Modules
| |||||||||||||||
| 4080 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 037
Read events
7 581
Write events
456
Delete events
0
Modification events
| (PID) Process: | (1036) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4080) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000020FB6A0C348FDA01F00F0000B80C0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4080) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000020FB6A0C348FDA01F00F0000C8060000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4080) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000020FB6A0C348FDA01F00F00001C0C0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4080) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000020FB6A0C348FDA01F00F00000C0B0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4080) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 40000000000000007A5D6D0C348FDA01F00F00000C0B0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4080) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 40000000000000007A5D6D0C348FDA01F00F00001C0C0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4080) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000D4BF6F0C348FDA01F00F0000C8060000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4080) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 40000000000000002E22720C348FDA01F00F0000B80C0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4080) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SwProvider_{b5946137-7b9f-4925-af80-51abd60b20d5} |
| Operation: | write | Name: | PROVIDER_BEGINPREPARE (Enter) |
Value: 40000000000000009E87DC0D348FDA01F00F0000B80C000001040000010000000000000000000000B5C6050DEA27924F97F937C9E0A4F3CA0000000000000000 | |||
Executable files
64
Suspicious files
301
Text files
486
Unknown types
114
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1036 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI323.tmp | executable | |
MD5:— | SHA256:— | |||
| 1036 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI8eee0.LOG | text | |
MD5:— | SHA256:— | |||
| 2932 | MobaXterm.exe | C:\Users\admin\AppData\Roaming\MobaXterm\slash\bin\MobAgent.exe | executable | |
MD5:— | SHA256:— | |||
| 2932 | MobaXterm.exe | C:\Users\admin\AppData\Roaming\MobaXterm\slash\bin\MobaKeyGen.exe | executable | |
MD5:— | SHA256:— | |||
| 2932 | MobaXterm.exe | C:\Users\admin\AppData\Roaming\MobaXterm\slash\bin\MobaRTE.exe | executable | |
MD5:— | SHA256:— | |||
| 2932 | MobaXterm.exe | C:\Users\admin\AppData\Roaming\MobaXterm\slash\bin\MobaSCP.exe | executable | |
MD5:— | SHA256:— | |||
| 2932 | MobaXterm.exe | C:\Users\admin\AppData\Roaming\MobaXterm\slash\bin\MoTTY.exe | executable | |
MD5:— | SHA256:— | |||
| 2932 | MobaXterm.exe | C:\Users\admin\AppData\Roaming\MobaXterm\slash\bin\stgames.exe | executable | |
MD5:— | SHA256:— | |||
| 2932 | MobaXterm.exe | C:\Users\admin\AppData\Roaming\MobaXterm\slash\bin\wsltermd | o | |
MD5:— | SHA256:— | |||
| 2932 | MobaXterm.exe | C:\Users\admin\AppData\Roaming\MobaXterm\slash\bin\_TCPCapture.sh | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |