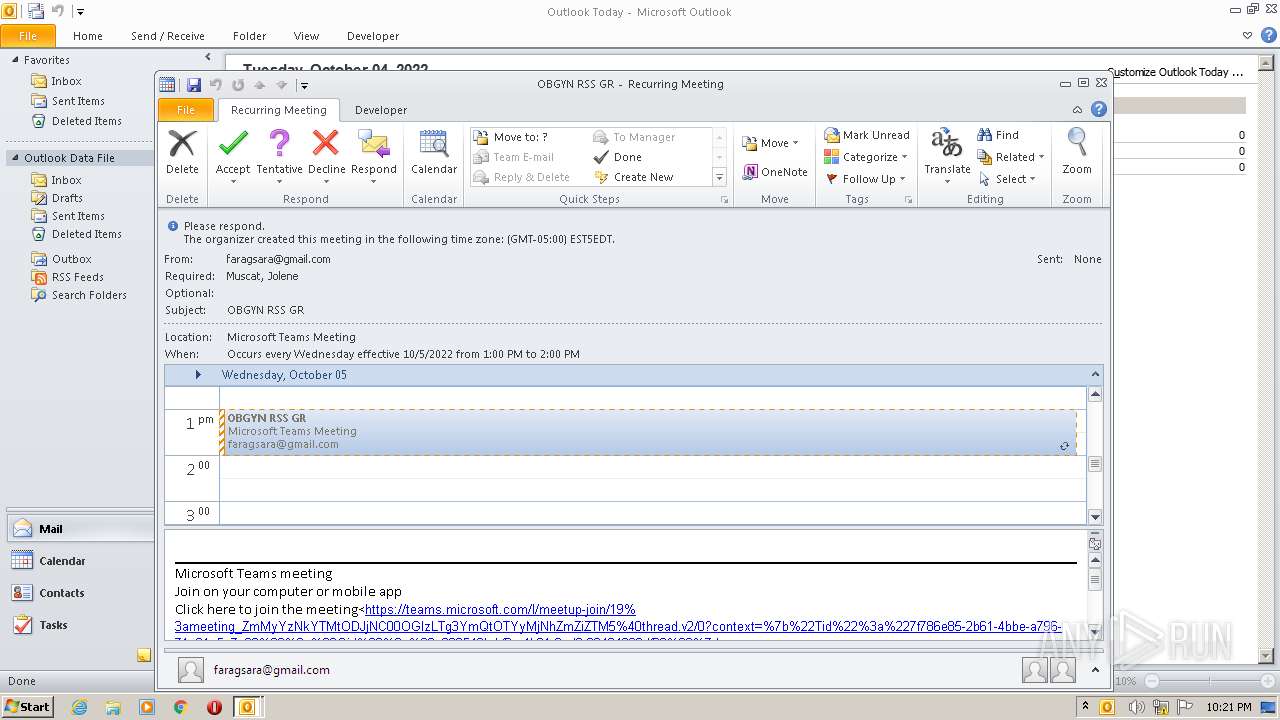
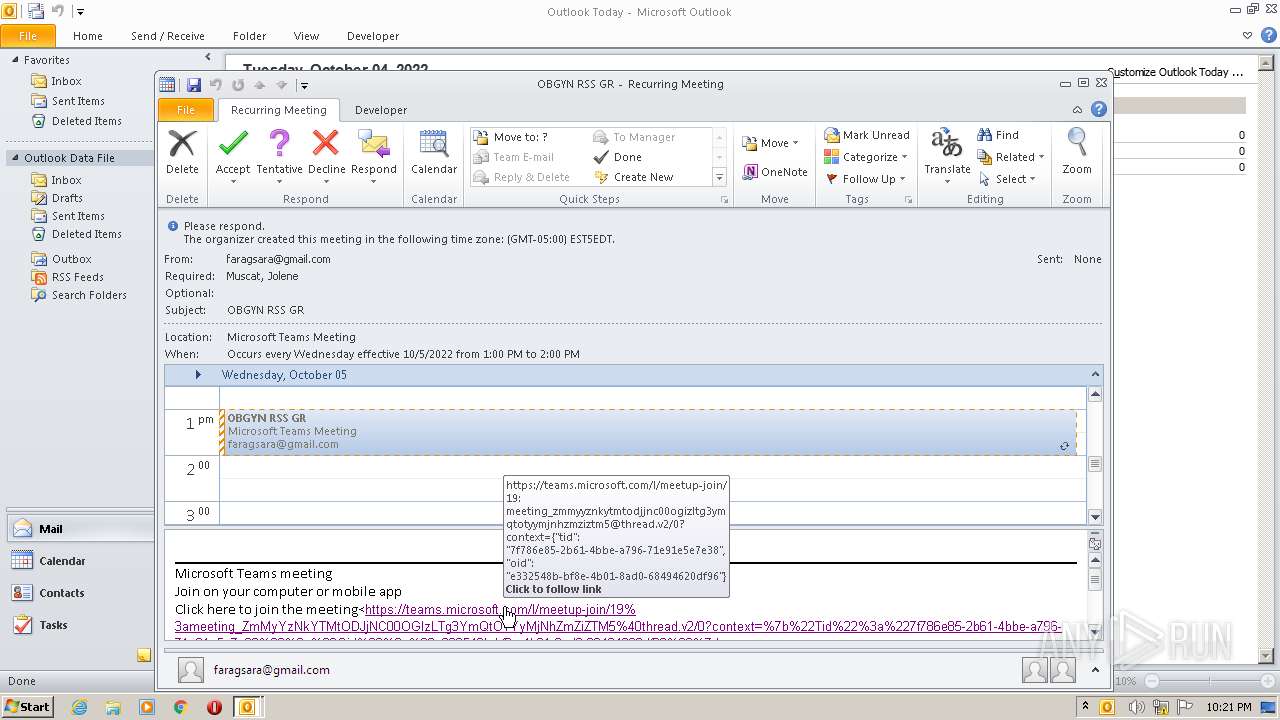
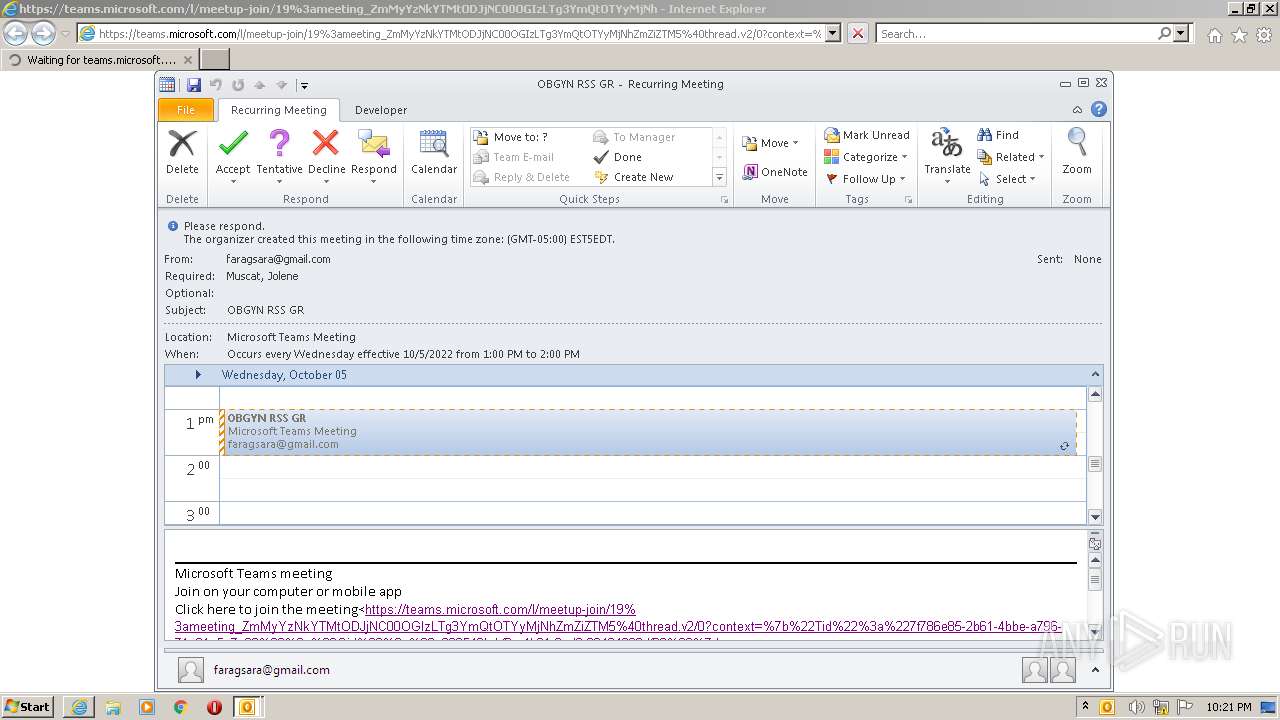
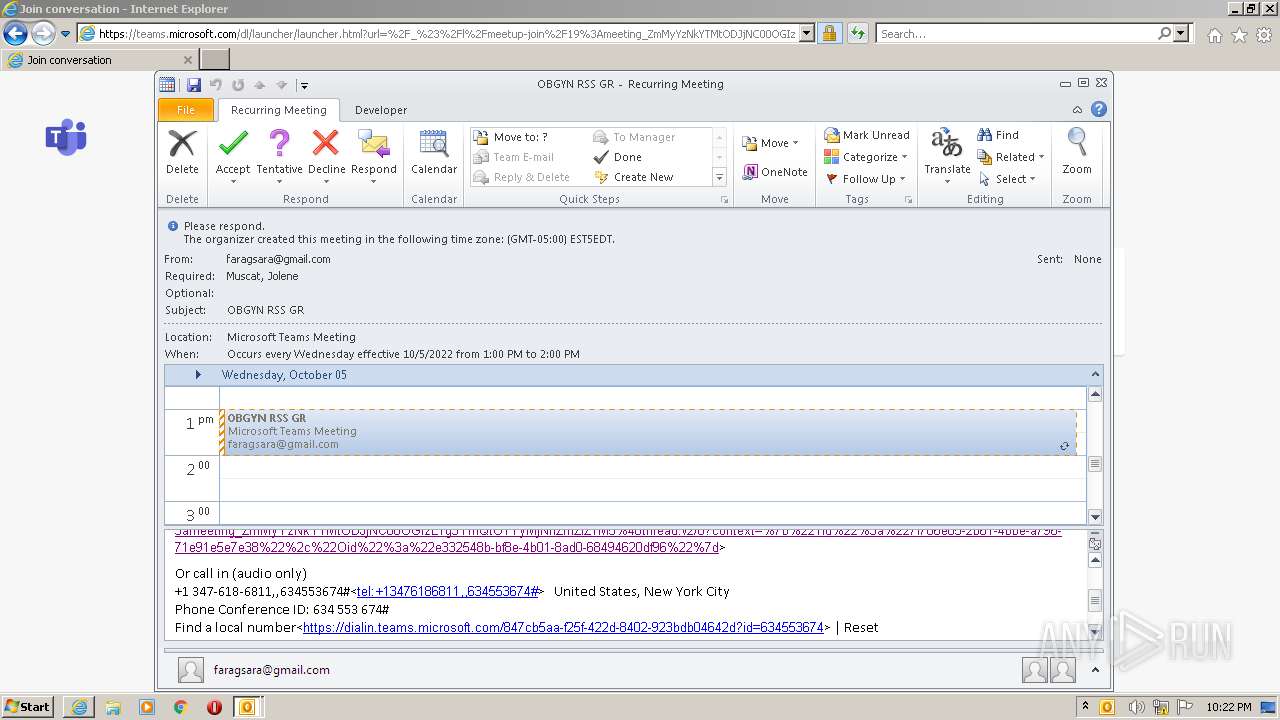
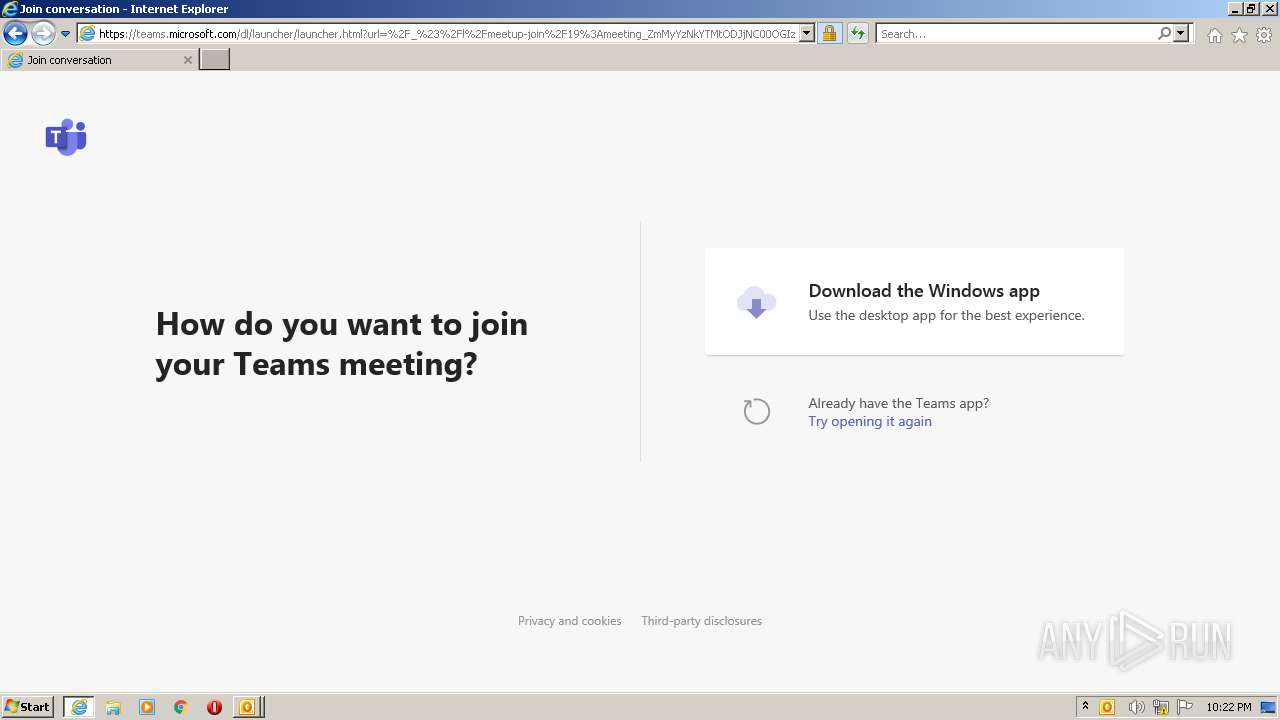
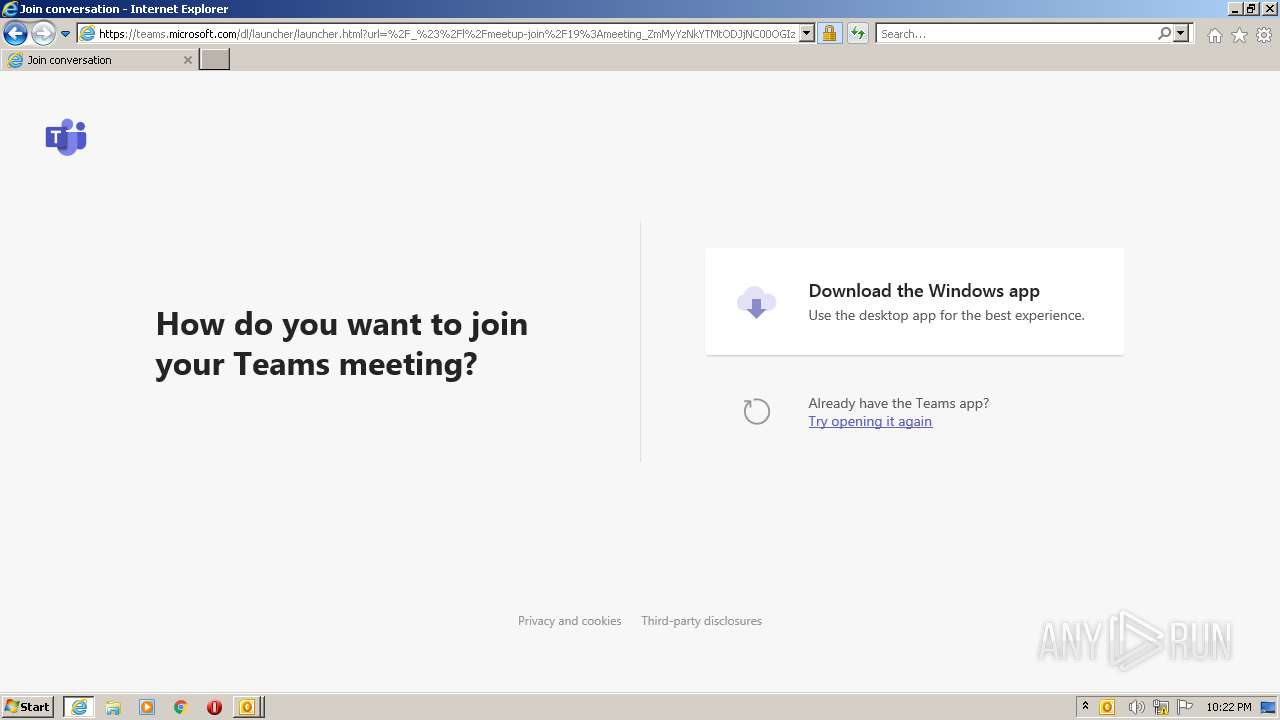
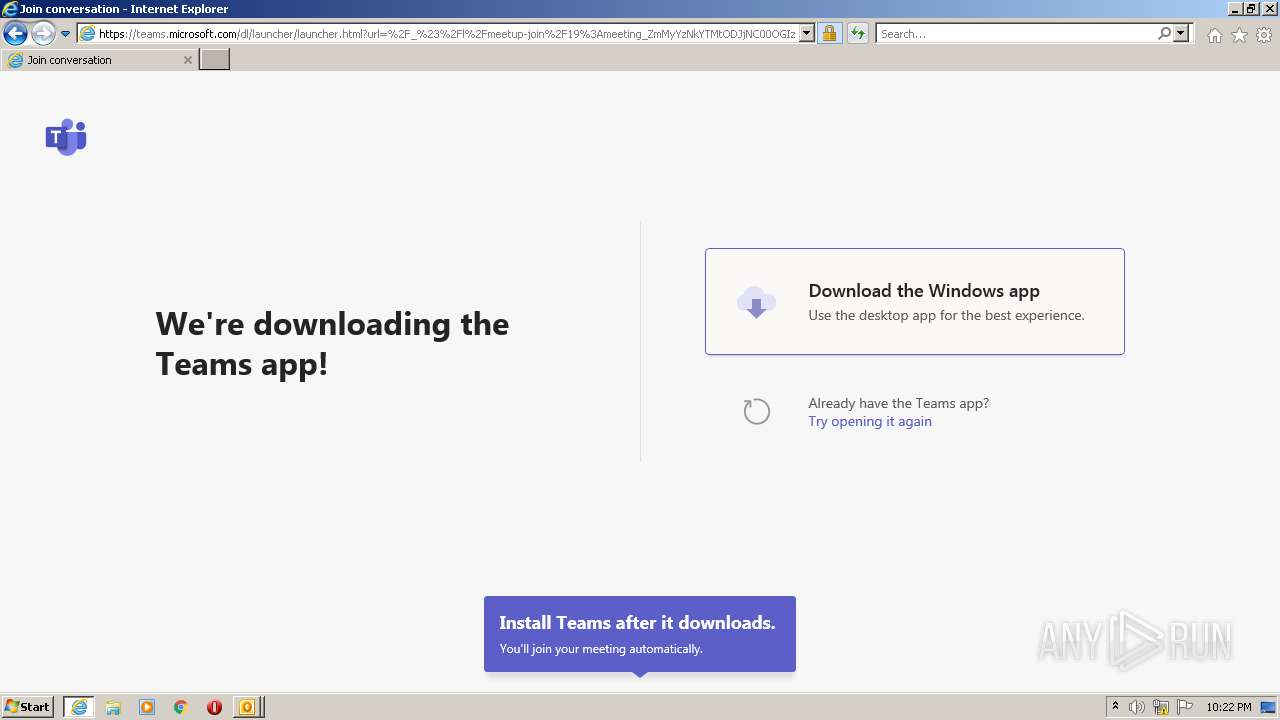
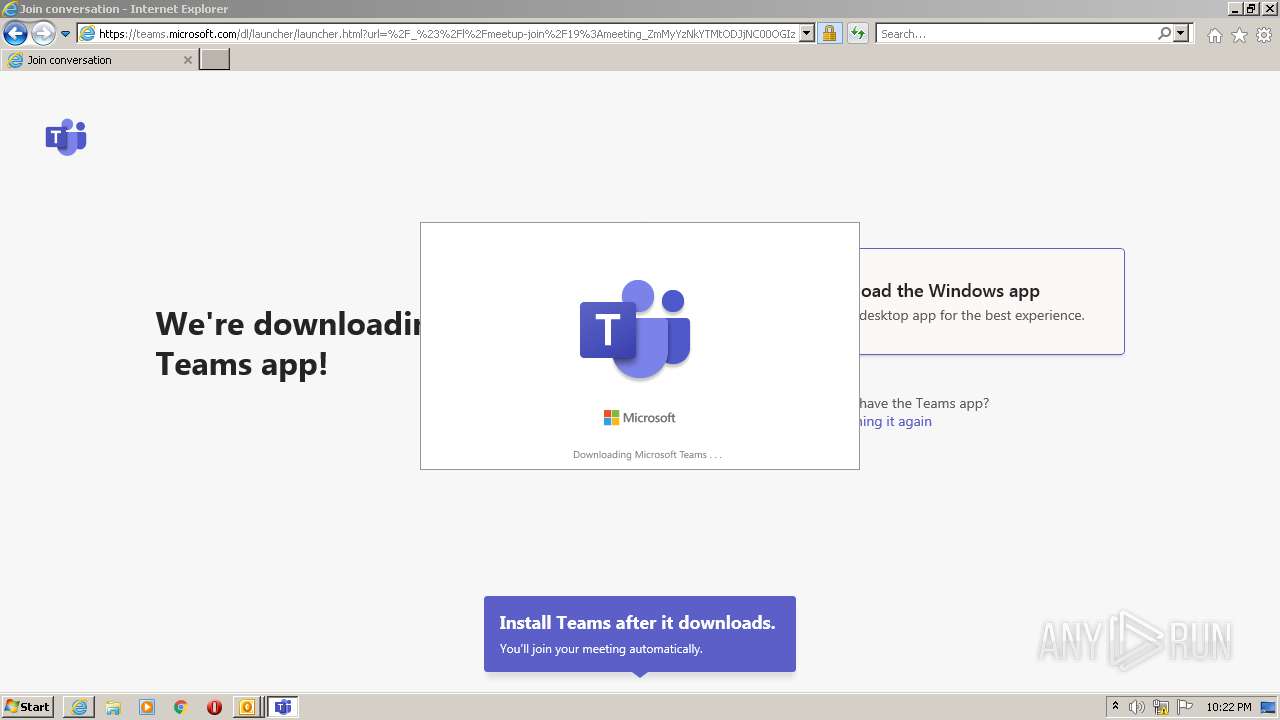
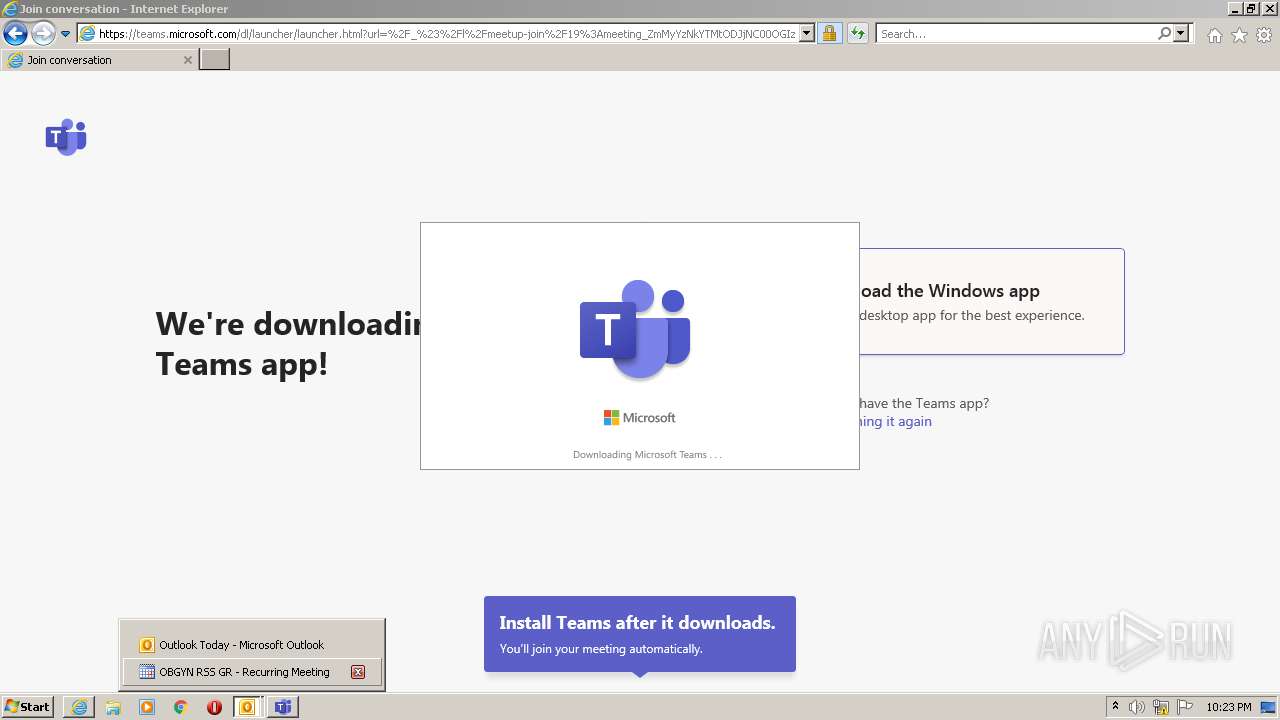
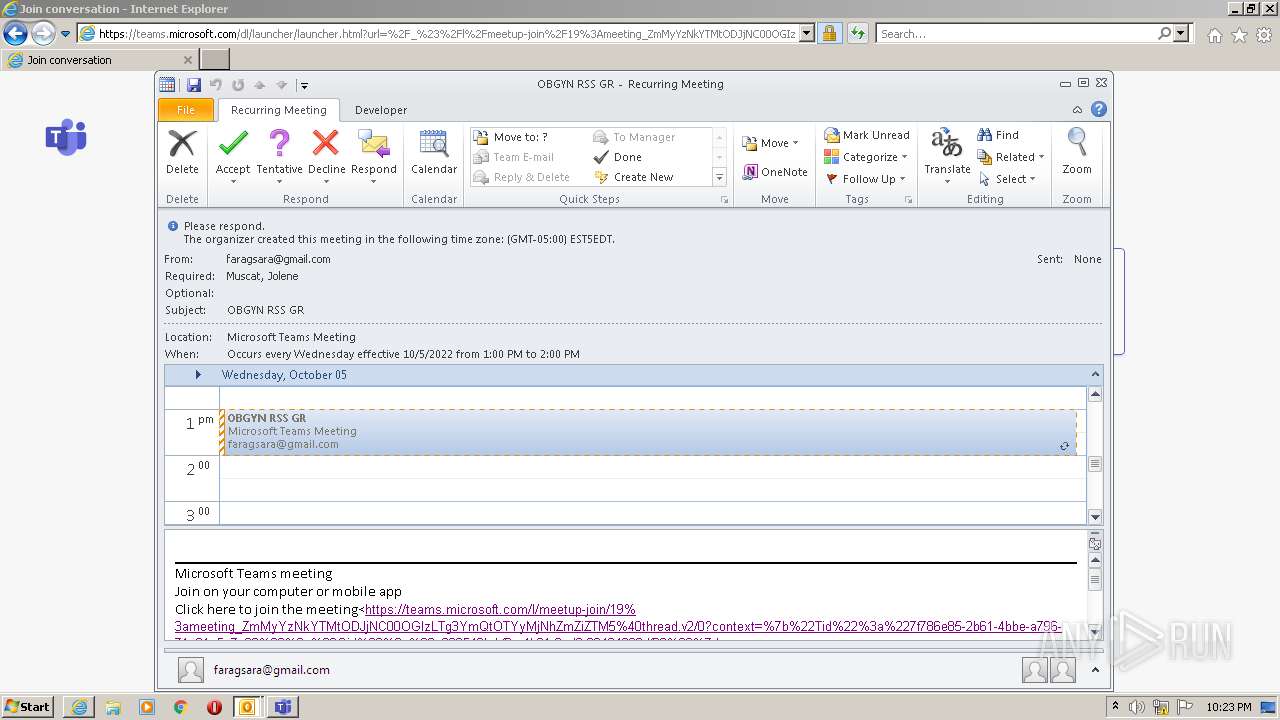
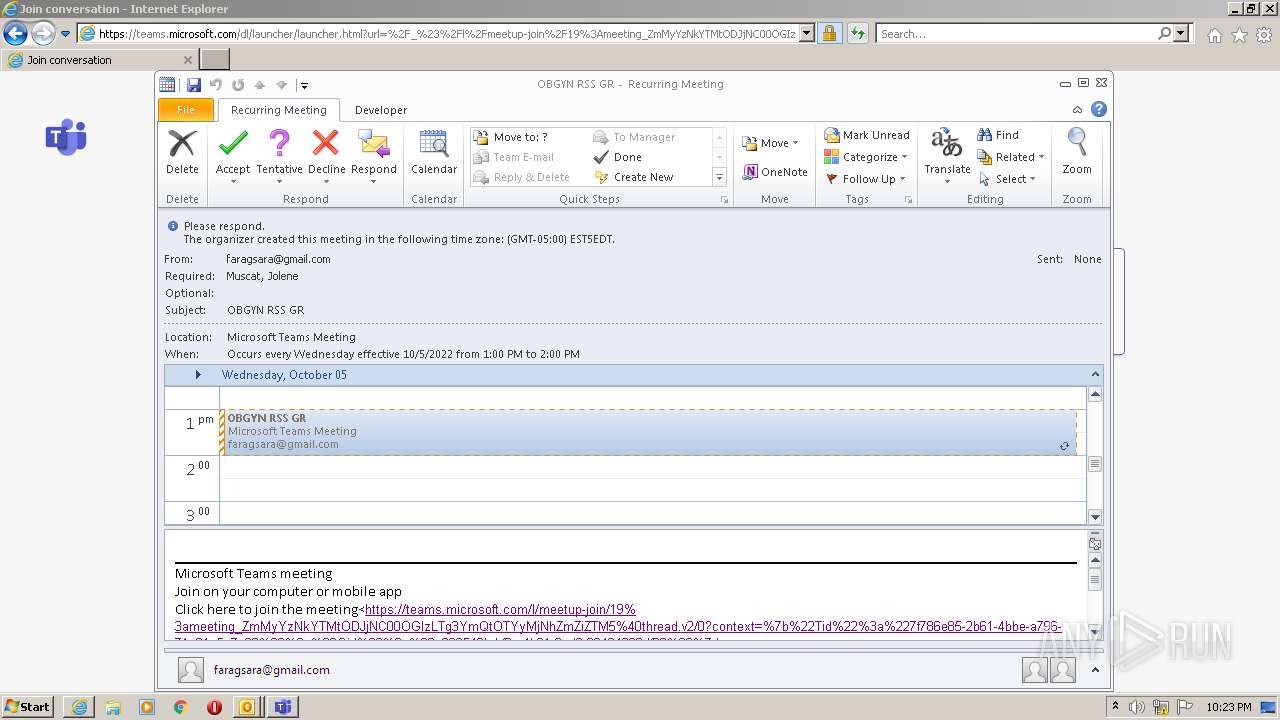
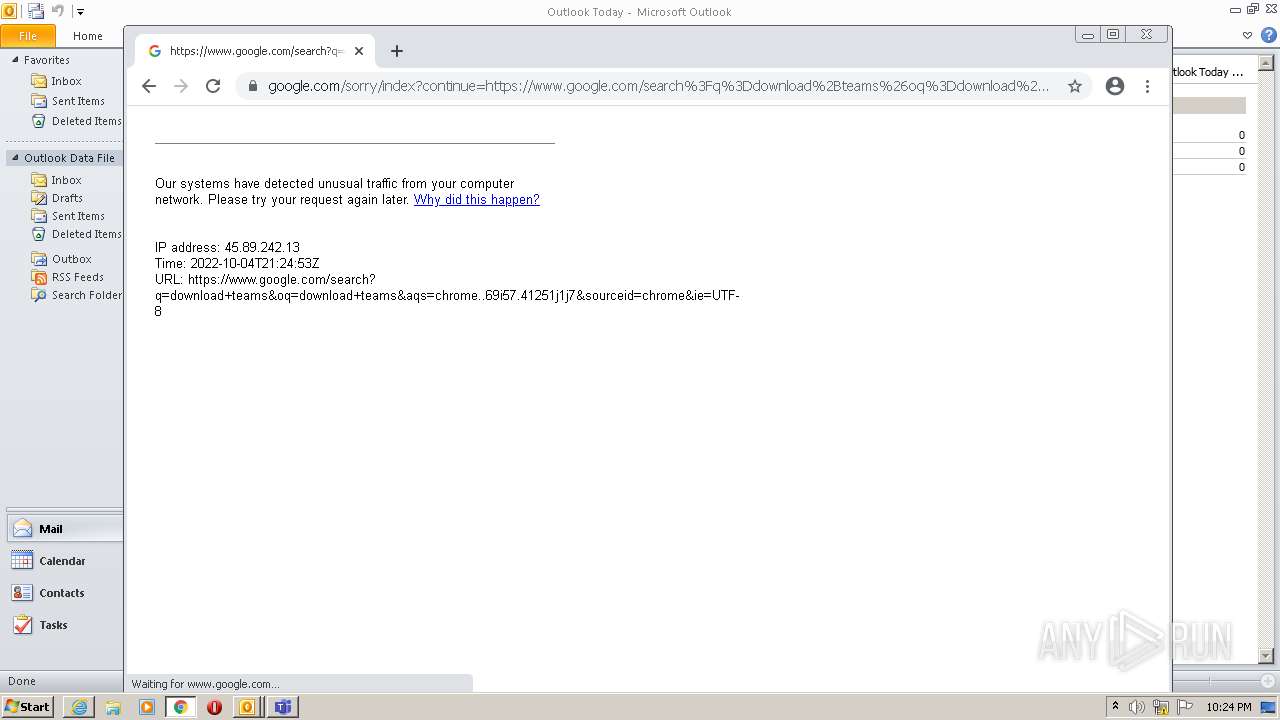
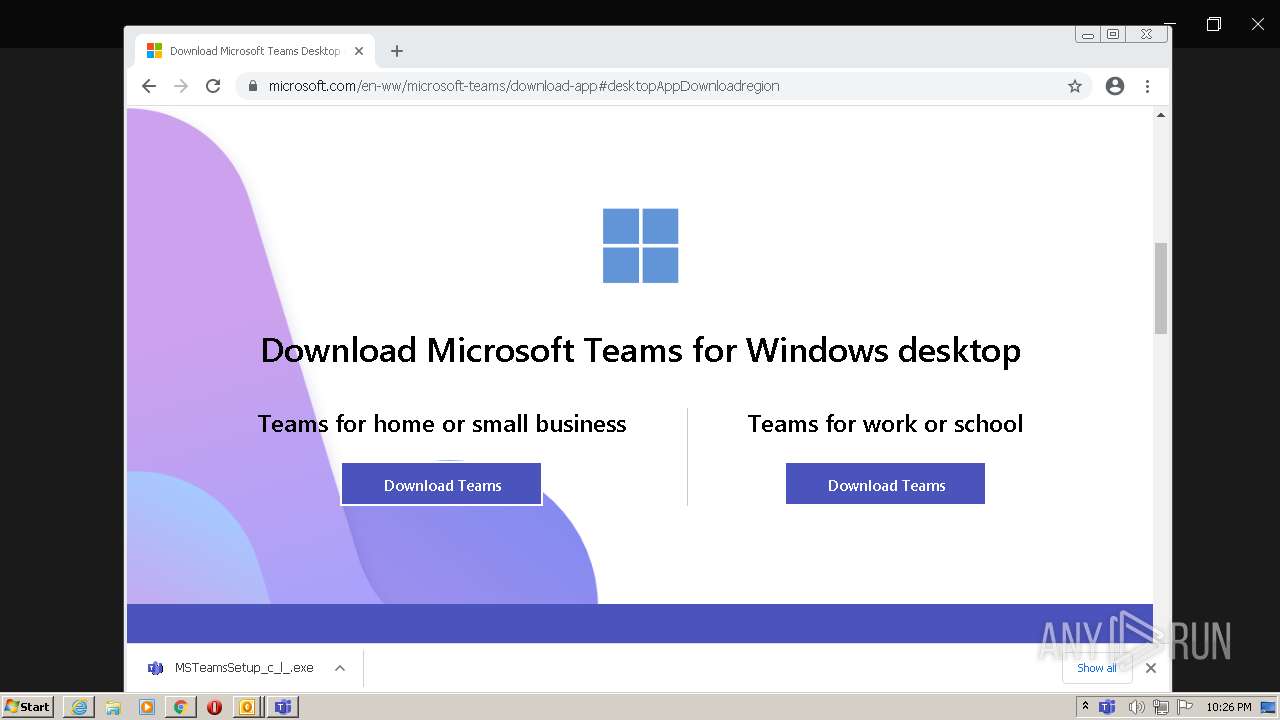
| File name: | invite.ics |
| Full analysis: | https://app.any.run/tasks/f3c18ba0-8f38-4876-a083-b21971ed36fb |
| Verdict: | Malicious activity |
| Analysis date: | October 04, 2022, 21:21:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
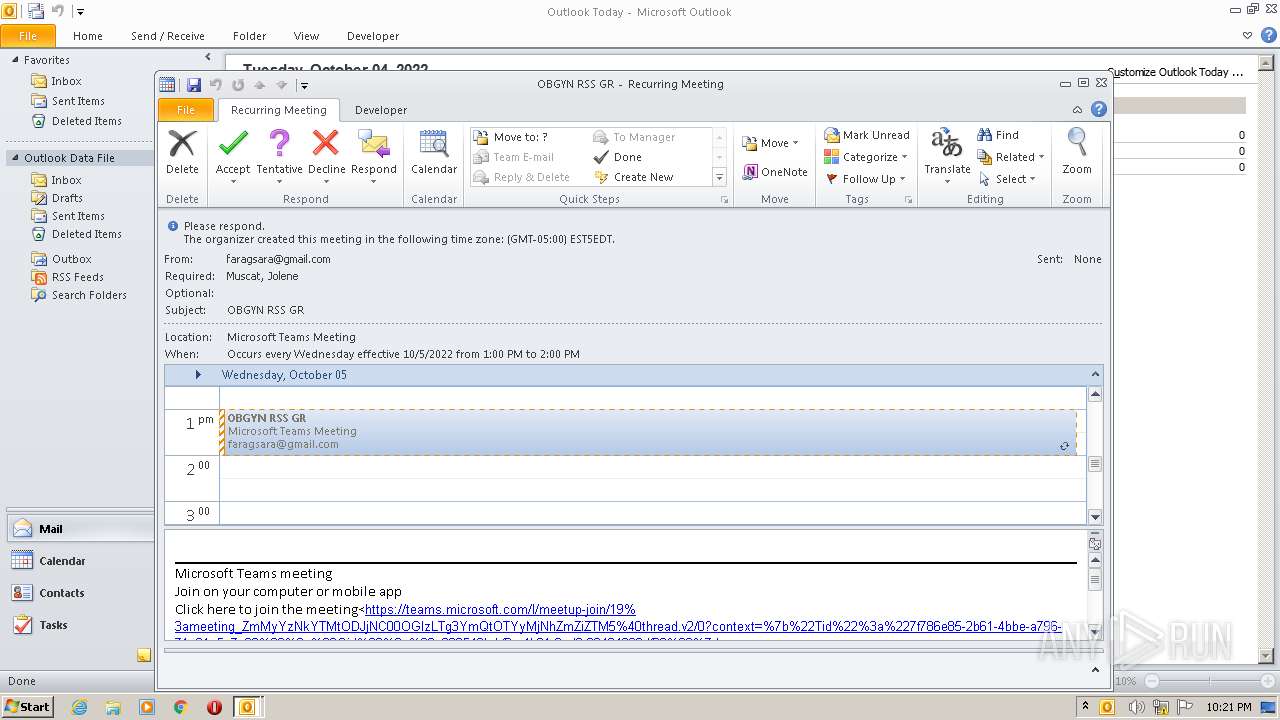
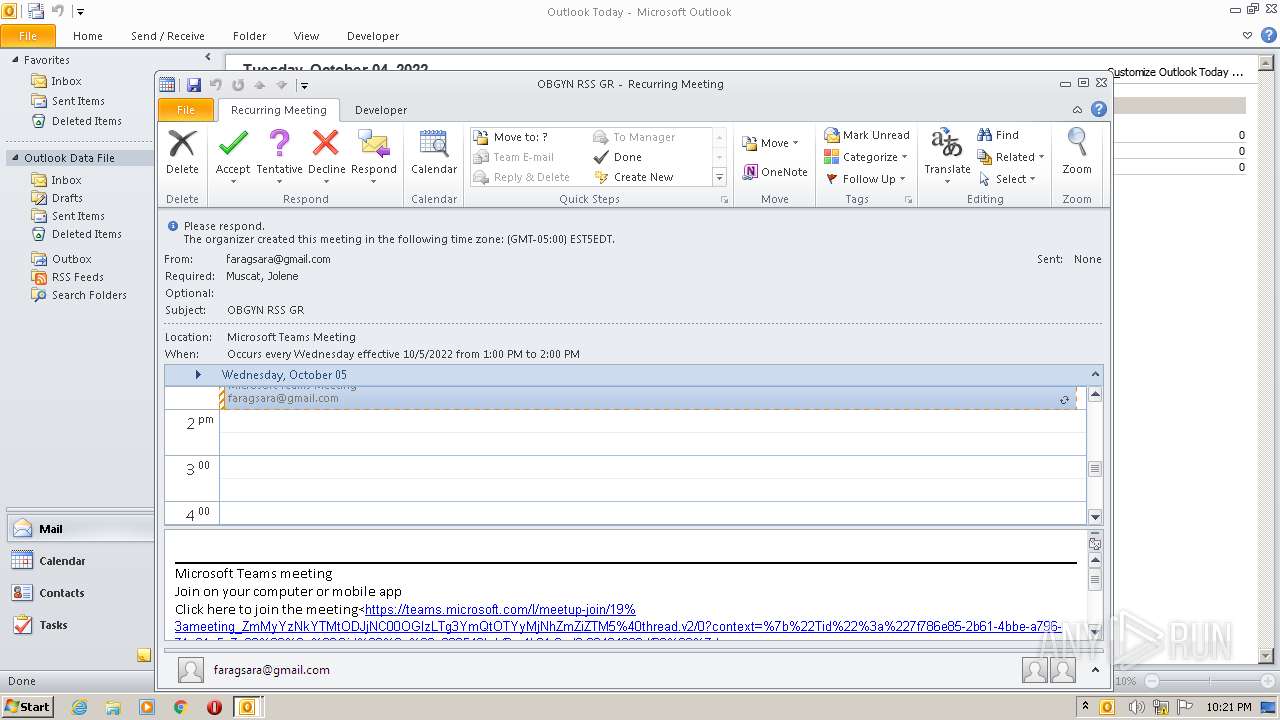
| MIME: | text/calendar |
| File info: | vCalendar calendar file |
| MD5: | 2267A2D81F027CCE26405CE781070D19 |
| SHA1: | 80C2AA727E9C0E878D63510D978EE2E798D49FA3 |
| SHA256: | 22C85532B8798E080534070E8D128BCCAEC45D00E46EAD490FE968811017EA21 |
| SSDEEP: | 48:EgfozMQQX2YPppf0EDXkF1InxwHNR+Iq9p5OUOMycqGJs:EgfoxQtHfxLqwwtR+p9VtqGJs |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 1160)
Drops executable file immediately after starts
- iexplore.exe (PID: 3984)
- iexplore.exe (PID: 944)
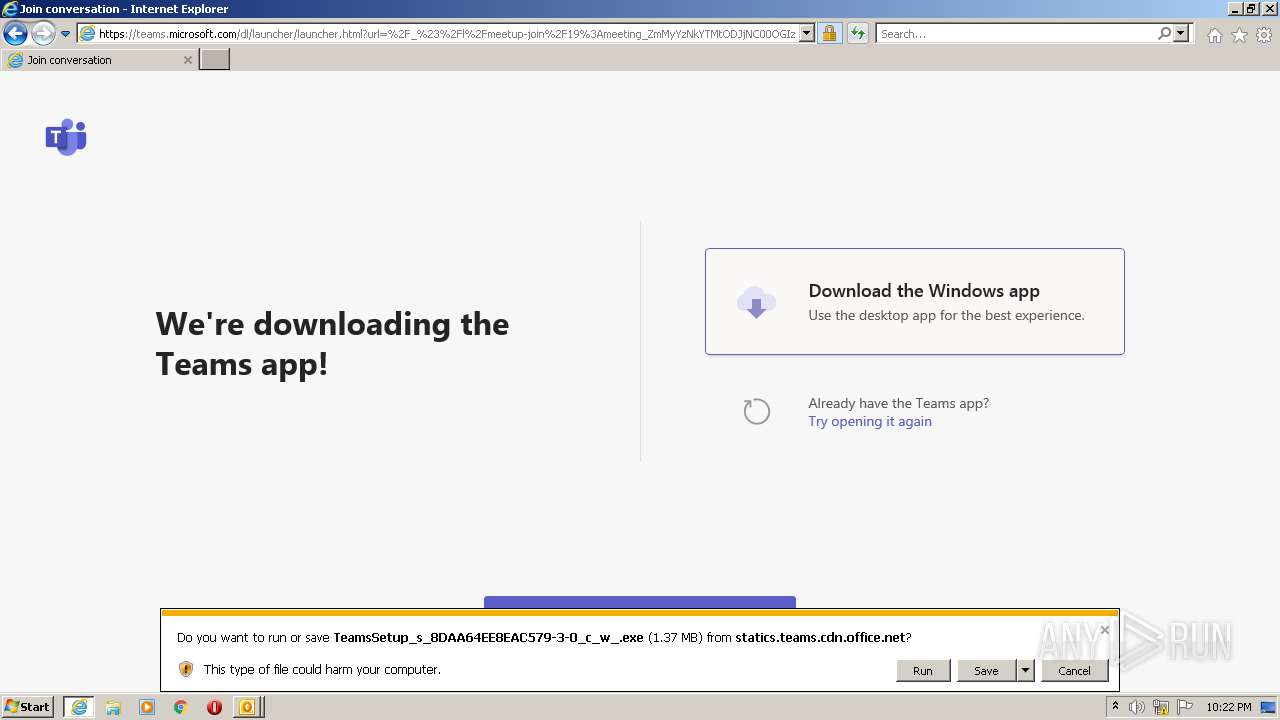
- TeamsSetup_s_8DAA64EE8EAC579-3-0_c_w_.exe (PID: 588)
- Update.exe (PID: 592)
- chrome.exe (PID: 3160)
- chrome.exe (PID: 3764)
Application was dropped or rewritten from another process
- TeamsSetup_s_8DAA64EE8EAC579-3-0_c_w_.exe (PID: 588)
- Update.exe (PID: 592)
- Squirrel.exe (PID: 3760)
- Update.exe (PID: 2096)
Loads dropped or rewritten executable
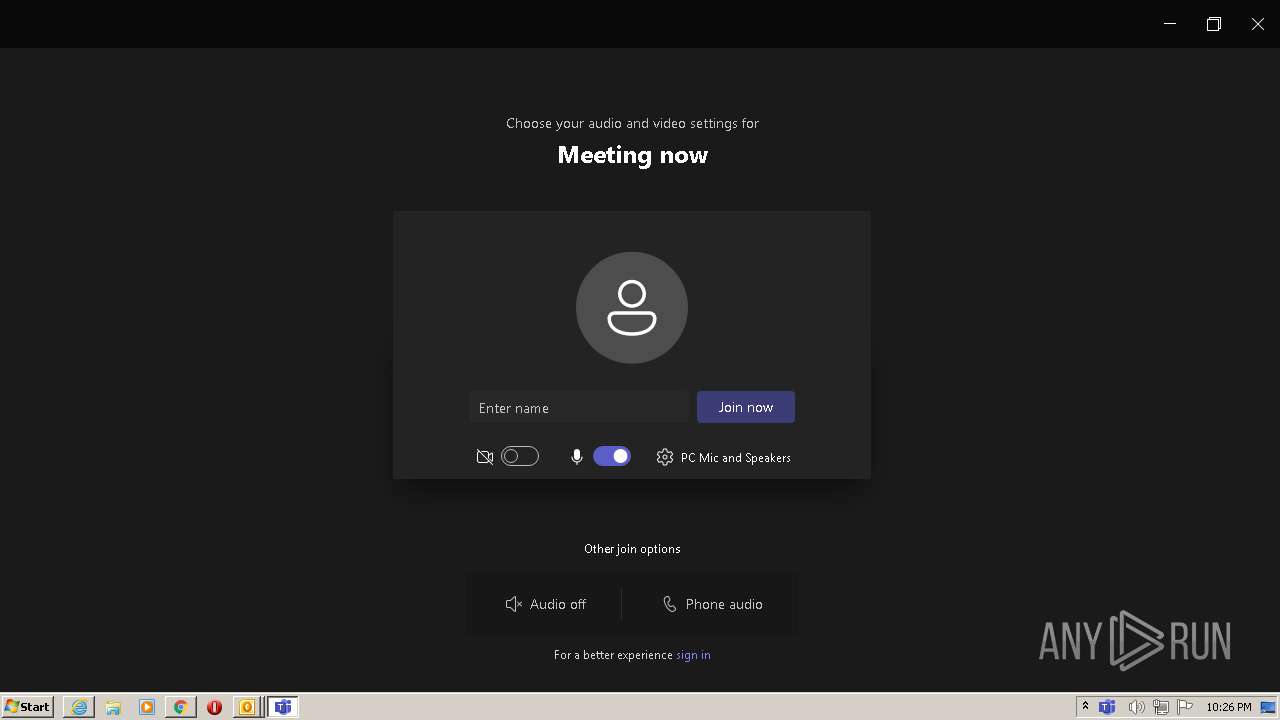
- Teams.exe (PID: 3332)
- Teams.exe (PID: 2568)
- Teams.exe (PID: 1764)
- Teams.exe (PID: 2880)
- Teams.exe (PID: 1340)
- Teams.exe (PID: 2344)
- Teams.exe (PID: 1368)
- Teams.exe (PID: 3036)
- regsvr32.exe (PID: 3816)
- Teams.exe (PID: 628)
- Teams.exe (PID: 664)
- Teams.exe (PID: 2576)
- Teams.exe (PID: 3060)
- Teams.exe (PID: 2628)
Changes the autorun value in the registry
- Teams.exe (PID: 3036)
Registers / Runs the DLL via REGSVR32.EXE
- Update.exe (PID: 592)
SUSPICIOUS
Reads the date of Windows installation
- OUTLOOK.EXE (PID: 1160)
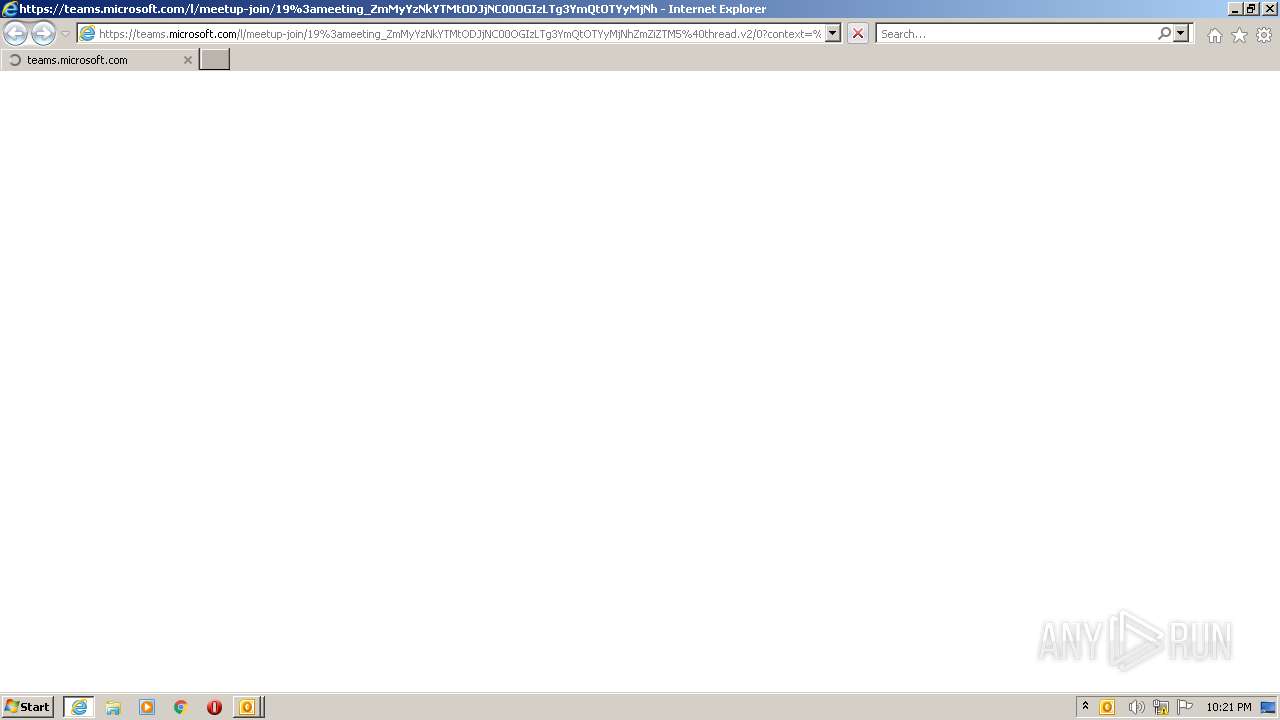
Starts Internet Explorer
- OUTLOOK.EXE (PID: 1160)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 944)
Executable content was dropped or overwritten
- iexplore.exe (PID: 944)
- TeamsSetup_s_8DAA64EE8EAC579-3-0_c_w_.exe (PID: 588)
- iexplore.exe (PID: 3984)
- Update.exe (PID: 592)
- chrome.exe (PID: 3160)
- chrome.exe (PID: 3764)
Drops a file with a compile date too recent
- iexplore.exe (PID: 3984)
- iexplore.exe (PID: 944)
- TeamsSetup_s_8DAA64EE8EAC579-3-0_c_w_.exe (PID: 588)
- Update.exe (PID: 592)
- chrome.exe (PID: 3764)
- chrome.exe (PID: 3160)
Checks supported languages
- Update.exe (PID: 592)
- TeamsSetup_s_8DAA64EE8EAC579-3-0_c_w_.exe (PID: 588)
- Squirrel.exe (PID: 3760)
- Teams.exe (PID: 3332)
- Teams.exe (PID: 2568)
- Teams.exe (PID: 1764)
- Update.exe (PID: 2096)
- Teams.exe (PID: 2880)
- Teams.exe (PID: 3036)
- Teams.exe (PID: 1340)
- Teams.exe (PID: 2344)
- Teams.exe (PID: 3060)
- Teams.exe (PID: 628)
- Teams.exe (PID: 664)
- Teams.exe (PID: 1368)
- Teams.exe (PID: 2576)
- Teams.exe (PID: 2628)
Reads the computer name
- Update.exe (PID: 592)
- Squirrel.exe (PID: 3760)
- Teams.exe (PID: 3332)
- Teams.exe (PID: 1764)
- Teams.exe (PID: 2568)
- Update.exe (PID: 2096)
- Teams.exe (PID: 2880)
- Teams.exe (PID: 3036)
- Teams.exe (PID: 1340)
- Teams.exe (PID: 2344)
- Teams.exe (PID: 628)
- Teams.exe (PID: 664)
- Teams.exe (PID: 2628)
Reads Environment values
- Update.exe (PID: 592)
- Update.exe (PID: 2096)
- Teams.exe (PID: 3036)
- Squirrel.exe (PID: 3760)
Creates files in the user directory
- Update.exe (PID: 592)
- Teams.exe (PID: 3332)
- Update.exe (PID: 2096)
- Teams.exe (PID: 3036)
- Teams.exe (PID: 2344)
- Teams.exe (PID: 2628)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3160)
Reads CPU info
- Teams.exe (PID: 3332)
- Teams.exe (PID: 3036)
Application launched itself
- Teams.exe (PID: 3332)
- Teams.exe (PID: 3036)
Changes default file association
- Teams.exe (PID: 3036)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 3816)
Creates a software uninstall entry
- Update.exe (PID: 592)
INFO
Checks supported languages
- OUTLOOK.EXE (PID: 1160)
- iexplore.exe (PID: 3984)
- iexplore.exe (PID: 944)
- WISPTIS.EXE (PID: 3088)
- chrome.exe (PID: 3160)
- chrome.exe (PID: 3276)
- chrome.exe (PID: 2464)
- chrome.exe (PID: 3764)
- chrome.exe (PID: 1712)
- chrome.exe (PID: 3608)
- chrome.exe (PID: 4008)
- chrome.exe (PID: 732)
- chrome.exe (PID: 2232)
- chrome.exe (PID: 1752)
- chrome.exe (PID: 3180)
- chrome.exe (PID: 2944)
- chrome.exe (PID: 3796)
- chrome.exe (PID: 3832)
- chrome.exe (PID: 1324)
- chrome.exe (PID: 924)
- chrome.exe (PID: 2108)
- chrome.exe (PID: 2332)
- chrome.exe (PID: 3324)
- chrome.exe (PID: 3072)
- chrome.exe (PID: 3748)
- chrome.exe (PID: 2832)
- chrome.exe (PID: 2260)
- chrome.exe (PID: 3132)
- chrome.exe (PID: 3452)
- chrome.exe (PID: 1764)
- chrome.exe (PID: 1596)
- chrome.exe (PID: 4048)
- chrome.exe (PID: 924)
- chrome.exe (PID: 2984)
- chrome.exe (PID: 440)
- chrome.exe (PID: 3668)
- chrome.exe (PID: 3200)
- chrome.exe (PID: 2128)
- chrome.exe (PID: 1360)
- chrome.exe (PID: 3016)
- chrome.exe (PID: 2668)
- chrome.exe (PID: 1564)
- chrome.exe (PID: 2744)
- chrome.exe (PID: 3824)
- chrome.exe (PID: 1144)
- chrome.exe (PID: 4012)
- chrome.exe (PID: 3192)
- chrome.exe (PID: 2260)
- chrome.exe (PID: 3072)
- chrome.exe (PID: 3540)
- chrome.exe (PID: 1004)
- chrome.exe (PID: 3600)
- chrome.exe (PID: 1388)
- chrome.exe (PID: 1408)
- chrome.exe (PID: 2480)
- chrome.exe (PID: 3048)
- chrome.exe (PID: 3320)
- chrome.exe (PID: 2068)
- chrome.exe (PID: 3248)
- chrome.exe (PID: 868)
- chrome.exe (PID: 4008)
- chrome.exe (PID: 752)
- regsvr32.exe (PID: 3816)
- chrome.exe (PID: 2600)
- chrome.exe (PID: 3312)
- chrome.exe (PID: 3732)
- chrome.exe (PID: 904)
- chrome.exe (PID: 2608)
- chrome.exe (PID: 120)
- chrome.exe (PID: 1484)
- chrome.exe (PID: 3744)
- chrome.exe (PID: 572)
- chrome.exe (PID: 3240)
- chrome.exe (PID: 752)
- chrome.exe (PID: 2388)
- chrome.exe (PID: 2136)
- chrome.exe (PID: 2524)
- chrome.exe (PID: 1488)
- explorer.exe (PID: 2832)
Reads Microsoft Outlook installation path
- OUTLOOK.EXE (PID: 1160)
Reads the computer name
- OUTLOOK.EXE (PID: 1160)
- iexplore.exe (PID: 3984)
- iexplore.exe (PID: 944)
- WISPTIS.EXE (PID: 3088)
- chrome.exe (PID: 3160)
- chrome.exe (PID: 2464)
- chrome.exe (PID: 3764)
- chrome.exe (PID: 1752)
- chrome.exe (PID: 924)
- chrome.exe (PID: 3132)
- chrome.exe (PID: 1360)
- chrome.exe (PID: 1564)
- chrome.exe (PID: 2068)
- chrome.exe (PID: 2524)
- explorer.exe (PID: 2832)
- chrome.exe (PID: 752)
Reads internet explorer settings
- OUTLOOK.EXE (PID: 1160)
- iexplore.exe (PID: 944)
Changes internet zones settings
- iexplore.exe (PID: 3984)
Application launched itself
- iexplore.exe (PID: 3984)
- chrome.exe (PID: 3160)
Creates files in the user directory
- OUTLOOK.EXE (PID: 1160)
- iexplore.exe (PID: 944)
- iexplore.exe (PID: 3984)
Reads settings of System Certificates
- iexplore.exe (PID: 3984)
- iexplore.exe (PID: 944)
- Update.exe (PID: 592)
- chrome.exe (PID: 3764)
- Teams.exe (PID: 2344)
- Teams.exe (PID: 2628)
Searches for installed software
- OUTLOOK.EXE (PID: 1160)
Checks Windows Trust Settings
- iexplore.exe (PID: 944)
- iexplore.exe (PID: 3984)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3984)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 1160)
- Update.exe (PID: 592)
- Update.exe (PID: 2096)
- Teams.exe (PID: 3036)
- Squirrel.exe (PID: 3760)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3984)
Changes settings of System certificates
- iexplore.exe (PID: 3984)
Manual execution by user
- chrome.exe (PID: 3160)
- explorer.exe (PID: 2832)
Reads the hosts file
- chrome.exe (PID: 3764)
- chrome.exe (PID: 3160)
- Teams.exe (PID: 2568)
- Teams.exe (PID: 3332)
- Teams.exe (PID: 3036)
- Teams.exe (PID: 2344)
Reads the date of Windows installation
- chrome.exe (PID: 1360)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .ics/vcs | | | iCalendar - vCalendar (100) |
|---|
Total processes
144
Monitored processes
97
Malicious processes
15
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,14678372788603869326,3946627528915566078,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=64 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1888 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1036,14678372788603869326,3946627528915566078,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3648 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 572 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --field-trial-handle=1036,14678372788603869326,3946627528915566078,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=icon_reader --mojo-platform-channel-handle=1832 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 588 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\TeamsSetup_s_8DAA64EE8EAC579-3-0_c_w_.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\TeamsSetup_s_8DAA64EE8EAC579-3-0_c_w_.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Installer for Squirrel-based applications Exit code: 0 Version: 1.4.4.0 Modules
| |||||||||||||||
| 592 | "C:\Users\admin\AppData\Local\SquirrelTemp\Update.exe" --install . --exeName=TeamsSetup_s_8DAA64EE8EAC579-3-0_c_w_.exe --bootstrapperMode | C:\Users\admin\AppData\Local\SquirrelTemp\Update.exe | TeamsSetup_s_8DAA64EE8EAC579-3-0_c_w_.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Teams Exit code: 0 Version: 3.0.4.0 Modules
| |||||||||||||||
| 628 | "C:\Users\admin\AppData\Local\Microsoft\Teams\current\Teams.exe" --type=gpu-process --field-trial-handle=1016,11426921577451894438,18356876829050747916,131072 --enable-features=ContextBridgeMutability,WebComponentsV0Enabled,WinUseBrowserSpellChecker,WinUseHybridSpellChecker --disable-features=CookiesWithoutSameSiteMustBeSecure,SameSiteByDefaultCookies,SpareRendererForSitePerProcess --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=1212 /prefetch:2 | C:\Users\admin\AppData\Local\Microsoft\Teams\current\Teams.exe | — | Teams.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Teams Exit code: 0 Version: 1.5.00.21668 Modules
| |||||||||||||||
| 664 | "C:\Users\admin\AppData\Local\Microsoft\Teams\current\Teams.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --field-trial-handle=1016,11426921577451894438,18356876829050747916,131072 --enable-features=ContextBridgeMutability,WebComponentsV0Enabled,WinUseBrowserSpellChecker,WinUseHybridSpellChecker --disable-features=CookiesWithoutSameSiteMustBeSecure,SameSiteByDefaultCookies,SpareRendererForSitePerProcess --lang=en-US --service-sandbox-type=audio --enable-wer --mojo-platform-channel-handle=1768 /prefetch:8 | C:\Users\admin\AppData\Local\Microsoft\Teams\current\Teams.exe | — | Teams.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Teams Exit code: 0 Version: 1.5.00.21668 Modules
| |||||||||||||||
| 732 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,14678372788603869326,3946627528915566078,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2244 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 752 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,14678372788603869326,3946627528915566078,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=55 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2400 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 752 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --field-trial-handle=1036,14678372788603869326,3946627528915566078,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2008 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
64 214
Read events
62 081
Write events
2 088
Delete events
45
Modification events
| (PID) Process: | (1160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (1160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
351
Suspicious files
448
Text files
411
Unknown types
158
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1160 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR98C6.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1160 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 1160 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1160 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\9SYD2G1TFBD5WEIIH0TI.temp | binary | |
MD5:— | SHA256:— | |||
| 1160 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\Microsoft Outlook.lnk | lnk | |
MD5:— | SHA256:— | |||
| 1160 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DFE7EDE971D29B4B63.TMP | gmc | |
MD5:— | SHA256:— | |||
| 1160 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF3D4723E75DC97A2A.TMP | oft | |
MD5:— | SHA256:— | |||
| 1160 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 1160 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\be71009ff8bb02a2.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 1160 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF00C35B0CE8FFDD8F.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
134
DNS requests
101
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1160 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
880 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | — | — | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 9.69 Kb | whitelisted |
944 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3984 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 9.66 Kb | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 43.4 Kb | whitelisted |
944 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | US | der | 471 b | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 46.0 Kb | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 20.9 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1160 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
944 | iexplore.exe | 52.113.194.132:443 | teams.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | suspicious |
944 | iexplore.exe | 23.216.77.69:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | suspicious |
3984 | iexplore.exe | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3984 | iexplore.exe | 23.216.77.69:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | suspicious |
3984 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
3984 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
944 | iexplore.exe | 20.42.72.131:443 | browser.pipe.aria.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | suspicious |
3984 | iexplore.exe | 20.25.53.147:443 | query.prod.cms.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3984 | iexplore.exe | 204.79.197.203:443 | www.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
teams.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
statics.teams.cdn.office.net |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Update.exe | Update.exe Information: 0 : |
Update.exe | Starting TelemetryManager constructor
|
Update.exe | Update.exe Information: 0 : |
Update.exe | TelemetryManagerImpl creation started
|
Update.exe | Update.exe Information: 0 : |
Update.exe | Performance counters are disabled. Skipping creation of counters category.
|
Update.exe | Update.exe Information: 0 : |
Update.exe | RecordBatcherTask with ID 4 started.
|
Update.exe | Update.exe Information: 0 : |
Update.exe | DataPackageSender with UserAgent name: AST-exe-C#, version: 3.0.4.0, [Ast_Default_Source]
|