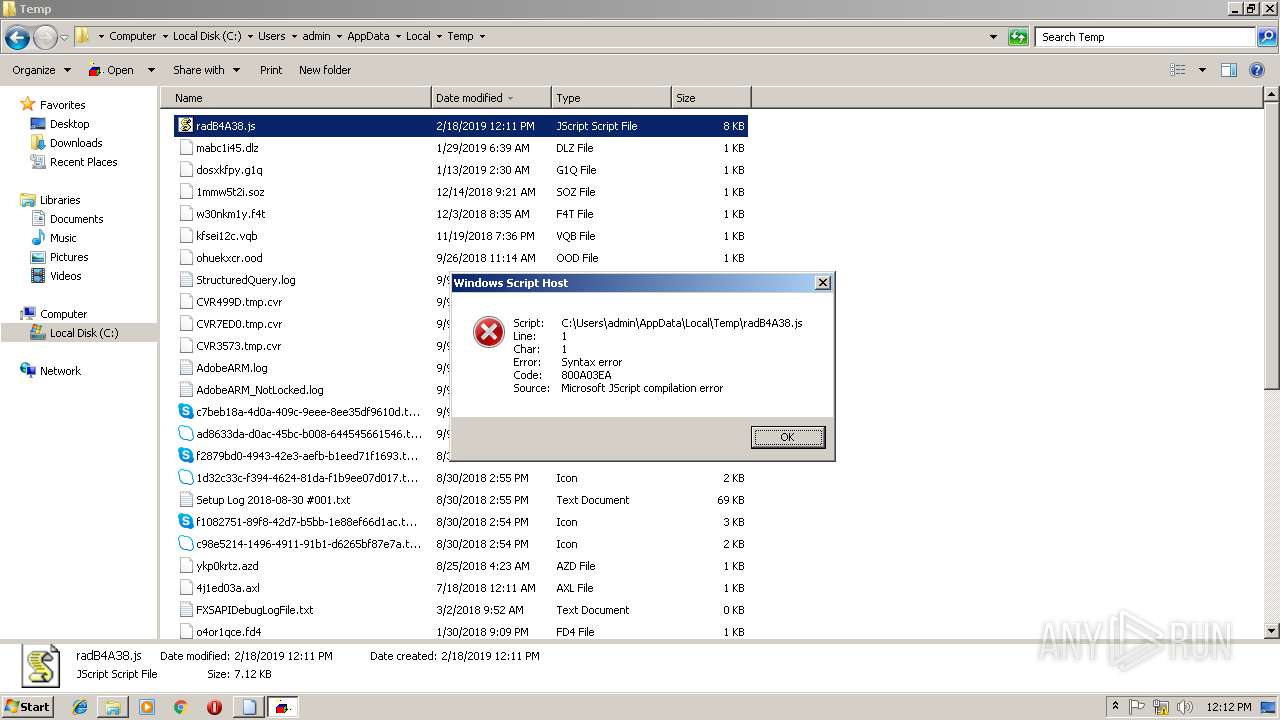
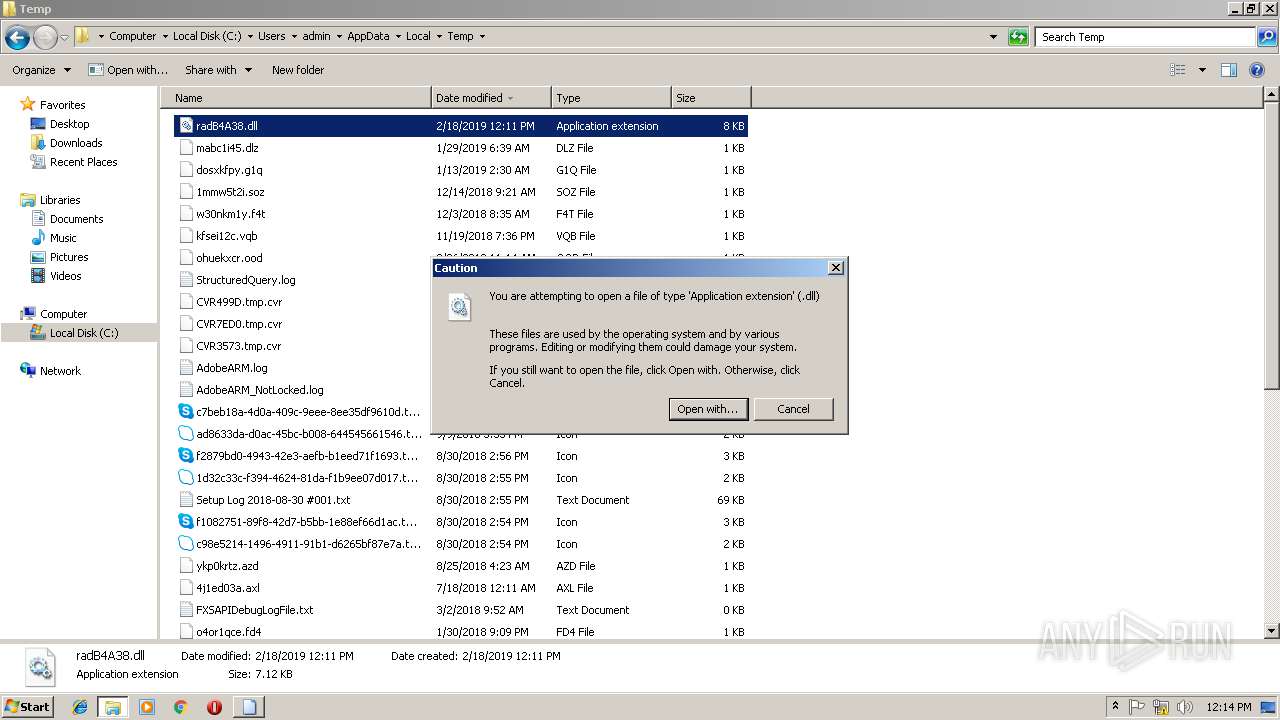
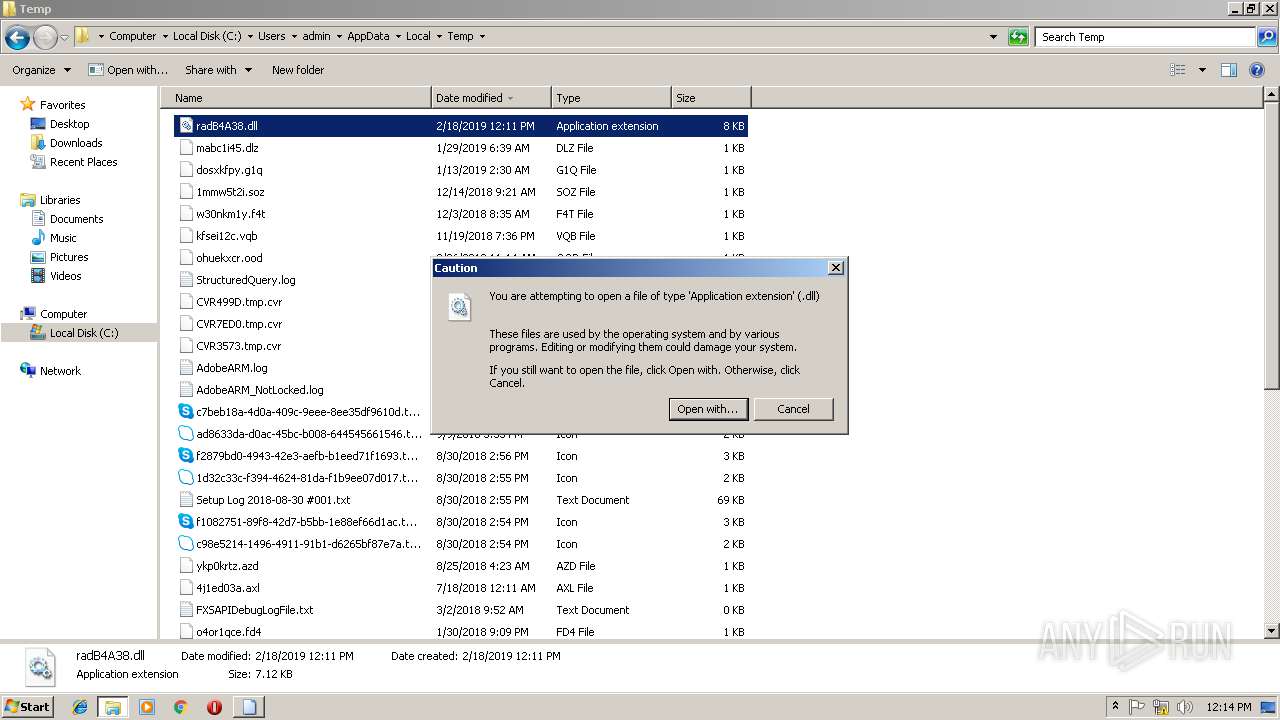
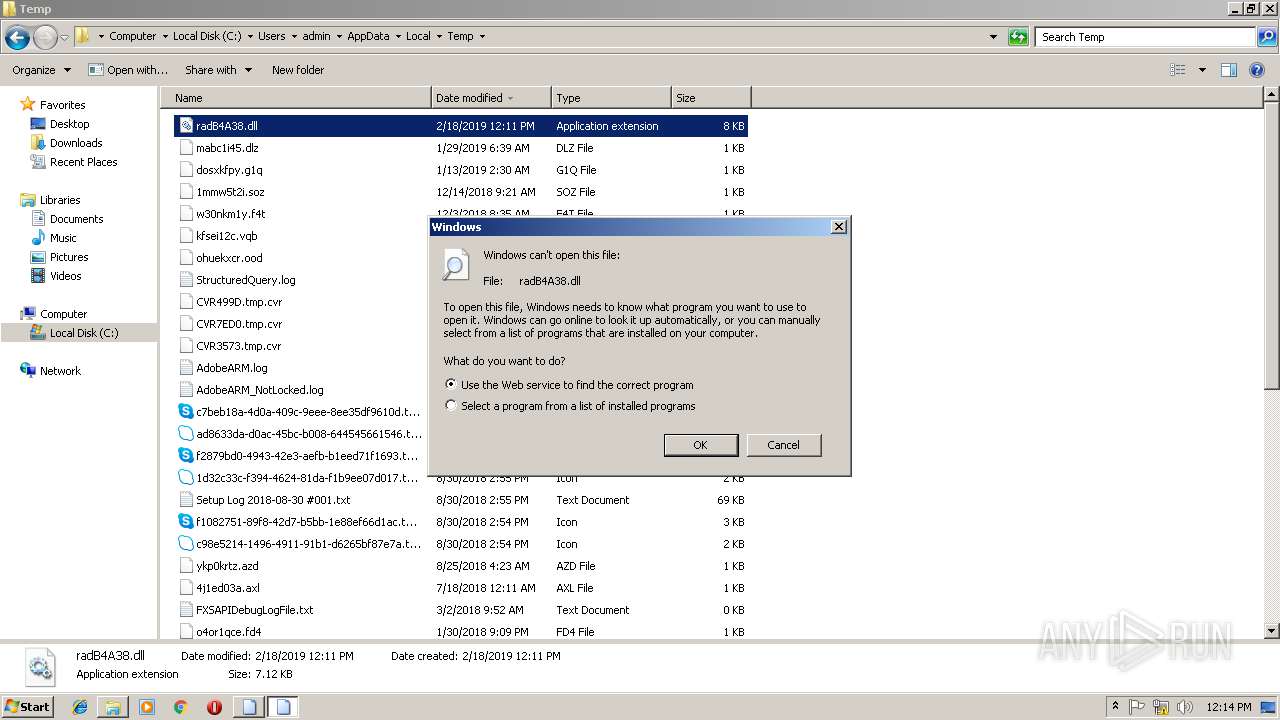
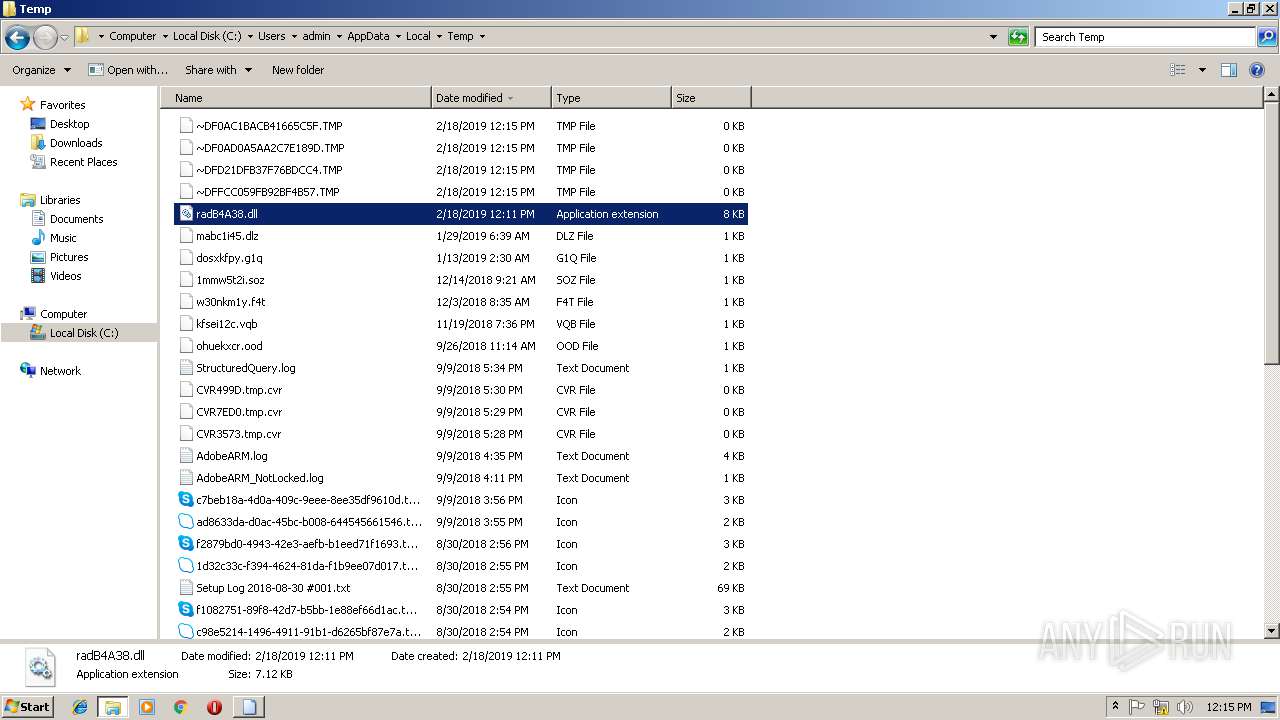
| File name: | «ПАО «НГК «Славнефть» подробности заказа.js |
| Full analysis: | https://app.any.run/tasks/89793716-548a-4af8-a0c4-ab889483eac5 |
| Verdict: | Malicious activity |
| Analysis date: | February 18, 2019, 12:11:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF, LF line terminators |
| MD5: | 1FC1C936DA1B3DFAF031CF634460C0CC |
| SHA1: | 0319C7F581DCD5BF1E48002D183F71BB36A62E1B |
| SHA256: | 22B1EA0639F1AB25E4050363266D219C17AAFBEC8F42F2E0CD119D6322810024 |
| SSDEEP: | 96:tMgFFHTUcsmshD3PUZT1OmTws34cKnEQW5cv3mITZoKLdPN:DPaFUZhOmTwfcK2vGomX |
MALICIOUS
Changes settings of System certificates
- WScript.exe (PID: 2984)
SUSPICIOUS
Adds / modifies Windows certificates
- WScript.exe (PID: 2984)
Starts Internet Explorer
- rundll32.exe (PID: 3440)
Starts CMD.EXE for commands execution
- WScript.exe (PID: 2984)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 3132)
INFO
Changes internet zones settings
- iexplore.exe (PID: 1412)
Application launched itself
- iexplore.exe (PID: 1412)
Reads Internet Cache Settings
- iexplore.exe (PID: 3240)
Reads settings of System Certificates
- iexplore.exe (PID: 1412)
Reads internet explorer settings
- iexplore.exe (PID: 3240)
Changes settings of System certificates
- iexplore.exe (PID: 1412)
Creates files in the user directory
- iexplore.exe (PID: 3240)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
51
Monitored processes
11
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1412 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
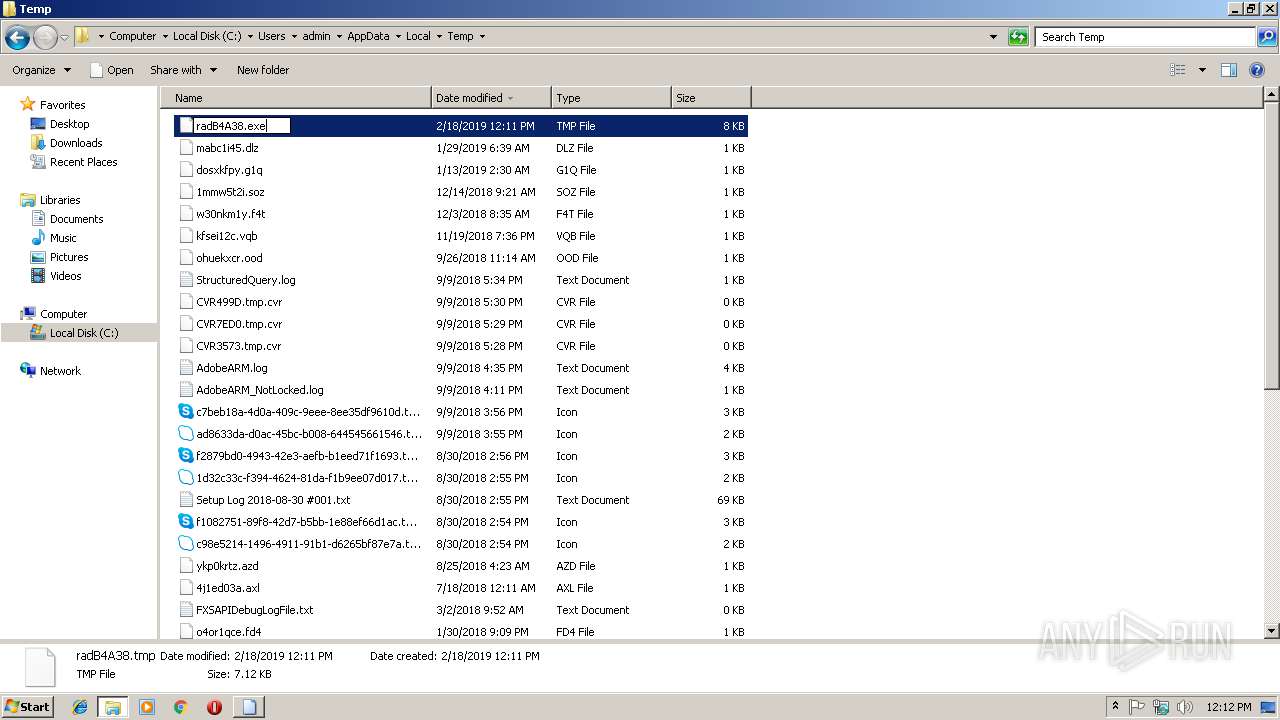
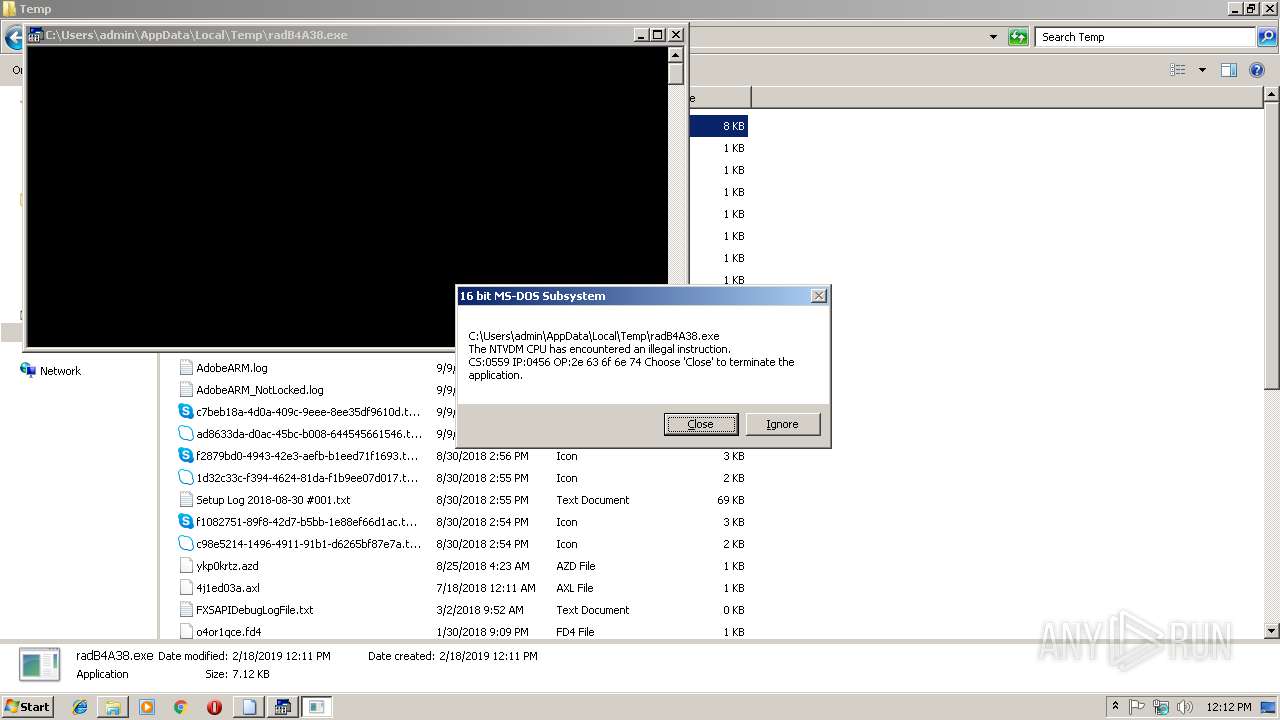
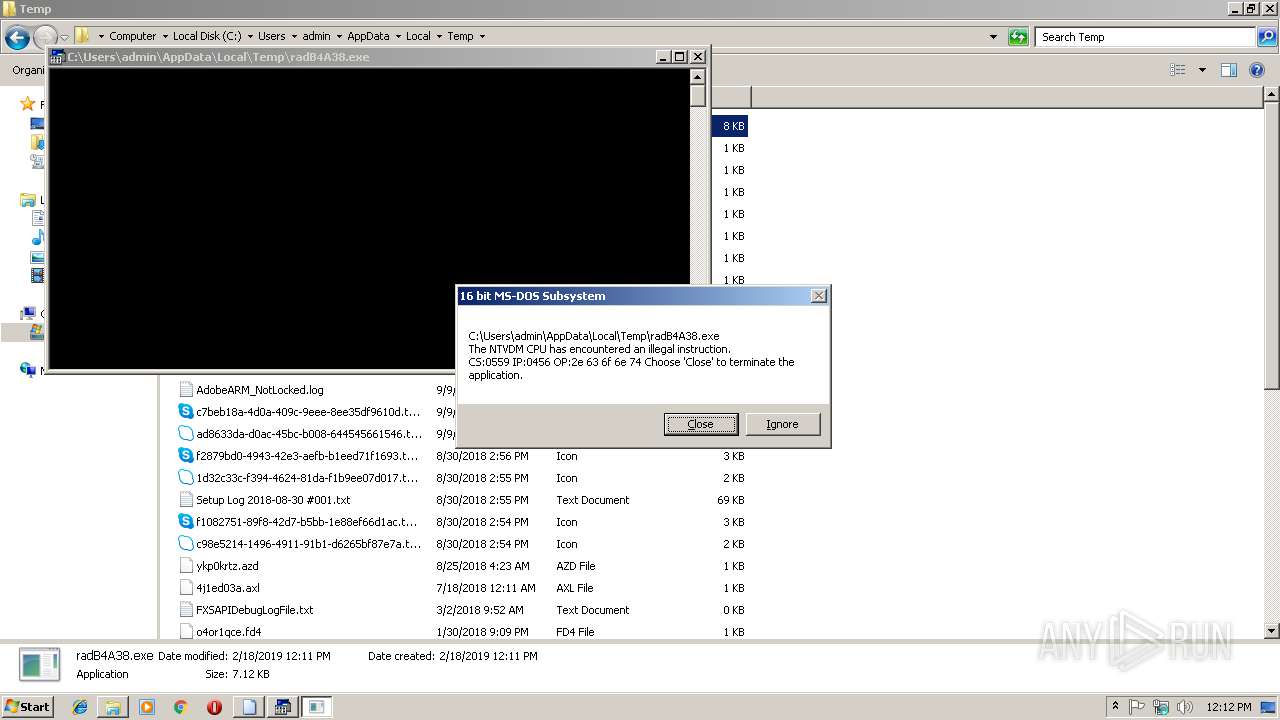
| 2076 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\system32\ntvdm.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 255 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
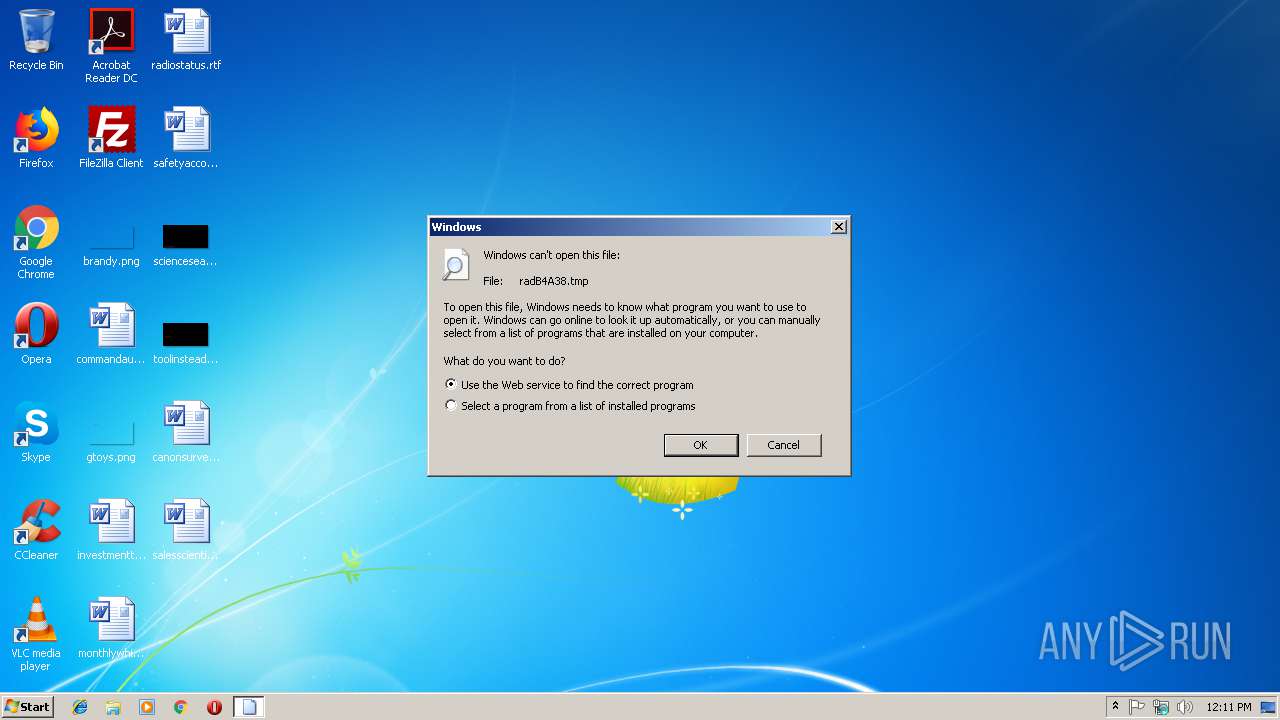
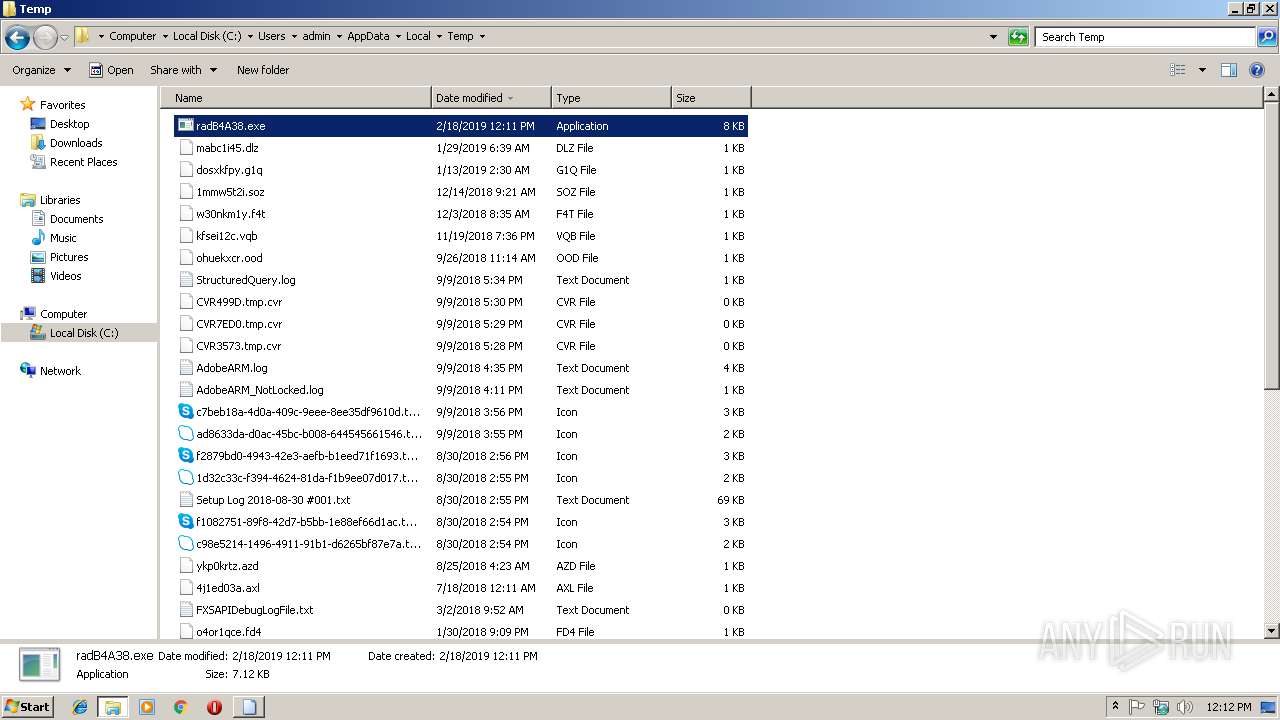
| 2596 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\radB4A38.tmp | C:\Windows\system32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2984 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\«ПАО «НГК «Славнефть» подробности заказа.js" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3132 | "C:\Windows\System32\cmd.exe" /c C:\Users\admin\AppData\Local\Temp\radB4A38.tmp | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3240 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1412 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
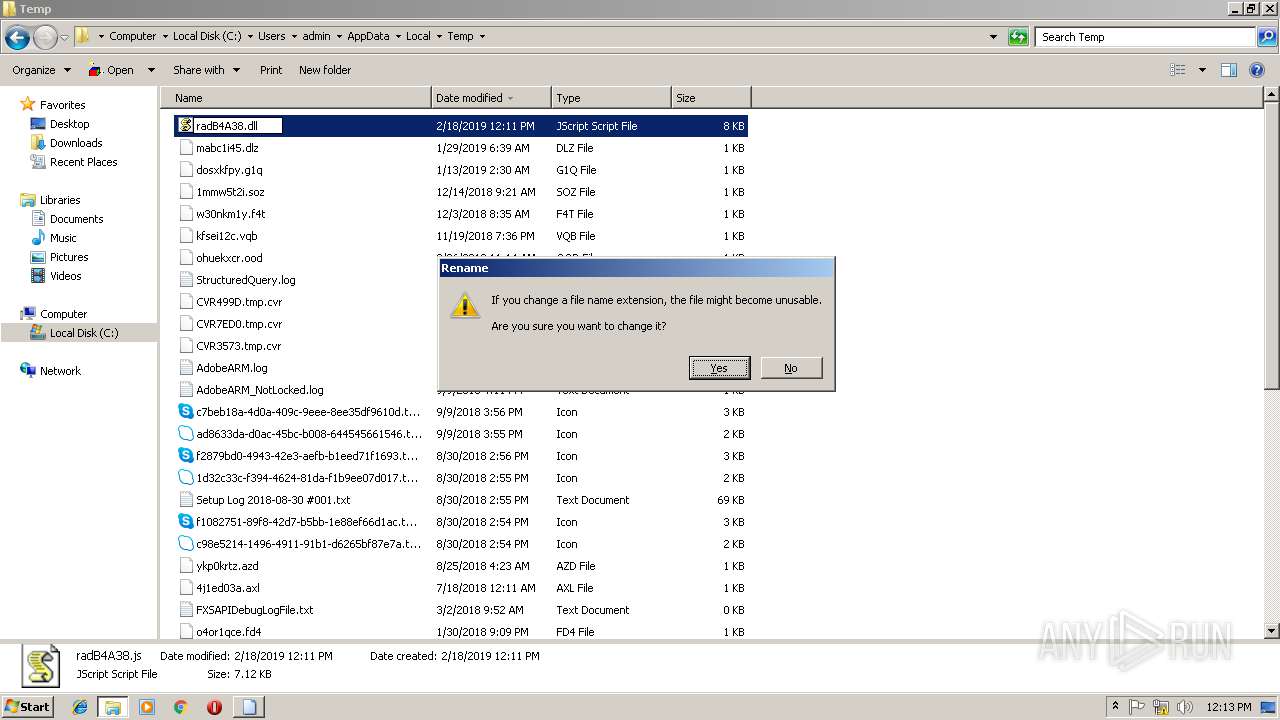
| 3440 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\radB4A38.dll | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3472 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\radB4A38.dll | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3636 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\radB4A38.js" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3736 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 682
Read events
1 581
Write events
95
Delete events
6
Modification events
| (PID) Process: | (2984) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2984) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2984) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2984) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2984) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2984) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2984) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2984) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2984) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2984) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
0
Suspicious files
3
Text files
31
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2076 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs7CC.tmp | — | |
MD5:— | SHA256:— | |||
| 2076 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs7CD.tmp | — | |
MD5:— | SHA256:— | |||
| 3864 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs11CE.tmp | — | |
MD5:— | SHA256:— | |||
| 3864 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs11DF.tmp | — | |
MD5:— | SHA256:— | |||
| 1412 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 1412 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@bing[2].txt | — | |
MD5:— | SHA256:— | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\search[1].txt | — | |
MD5:— | SHA256:— | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@bing[1].txt | text | |
MD5:— | SHA256:— | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\9a358300[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
12
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3240 | iexplore.exe | GET | 301 | 2.16.186.27:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=dll | unknown | — | — | whitelisted |
3240 | iexplore.exe | GET | 302 | 2.19.38.59:80 | http://go.microsoft.com/fwlink/?LinkId=57426&Ext=dll | unknown | — | — | whitelisted |
1412 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2984 | WScript.exe | 66.147.244.243:443 | texassweetiesdogrescue.org | Unified Layer | US | unknown |
1412 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3240 | iexplore.exe | 2.19.38.59:80 | go.microsoft.com | Akamai International B.V. | — | whitelisted |
3240 | iexplore.exe | 2.16.186.27:80 | shell.windows.com | Akamai International B.V. | — | whitelisted |
3240 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
1412 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3240 | iexplore.exe | 65.55.163.78:443 | login.live.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
texassweetiesdogrescue.org |
| unknown |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
shell.windows.com |
| whitelisted |
login.live.com |
| whitelisted |