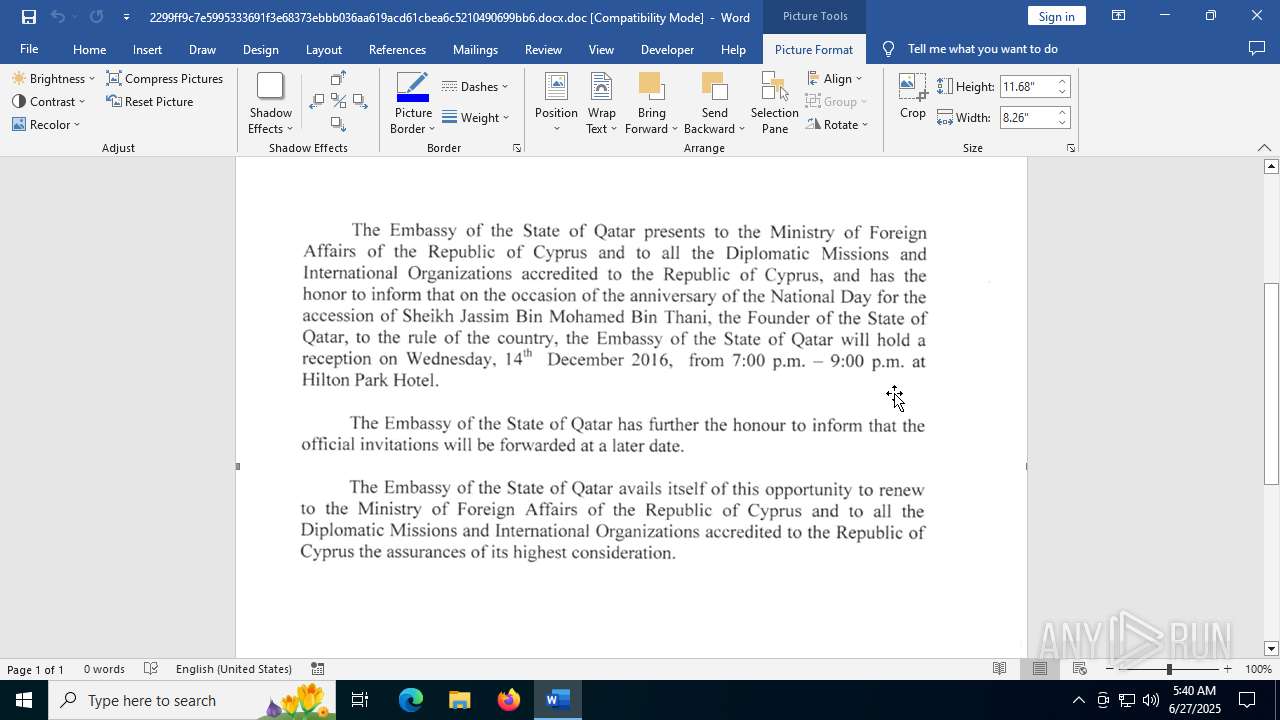
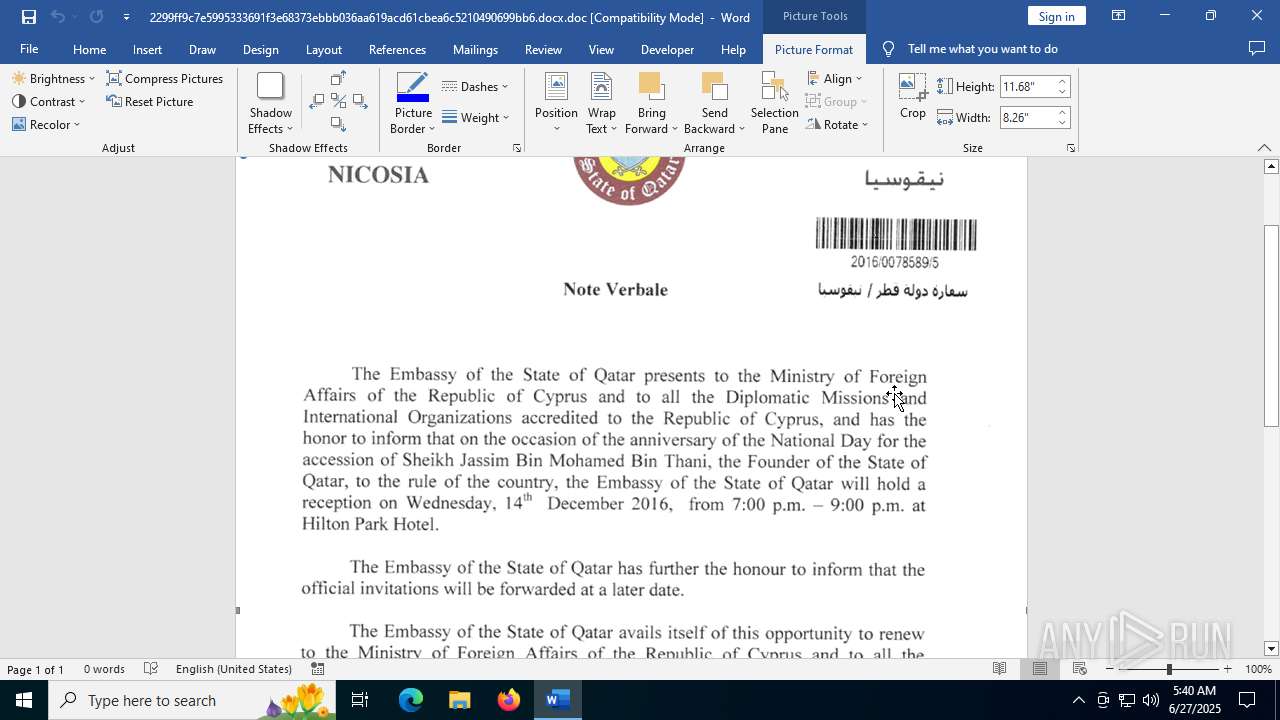
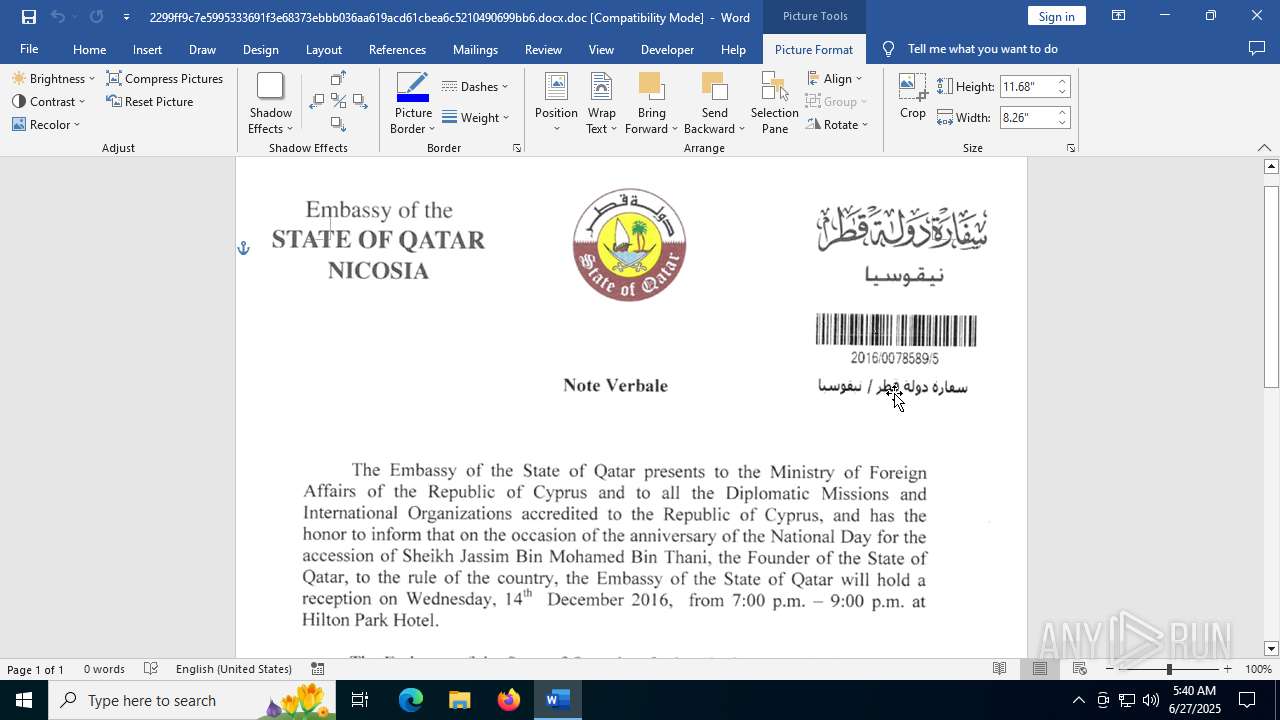
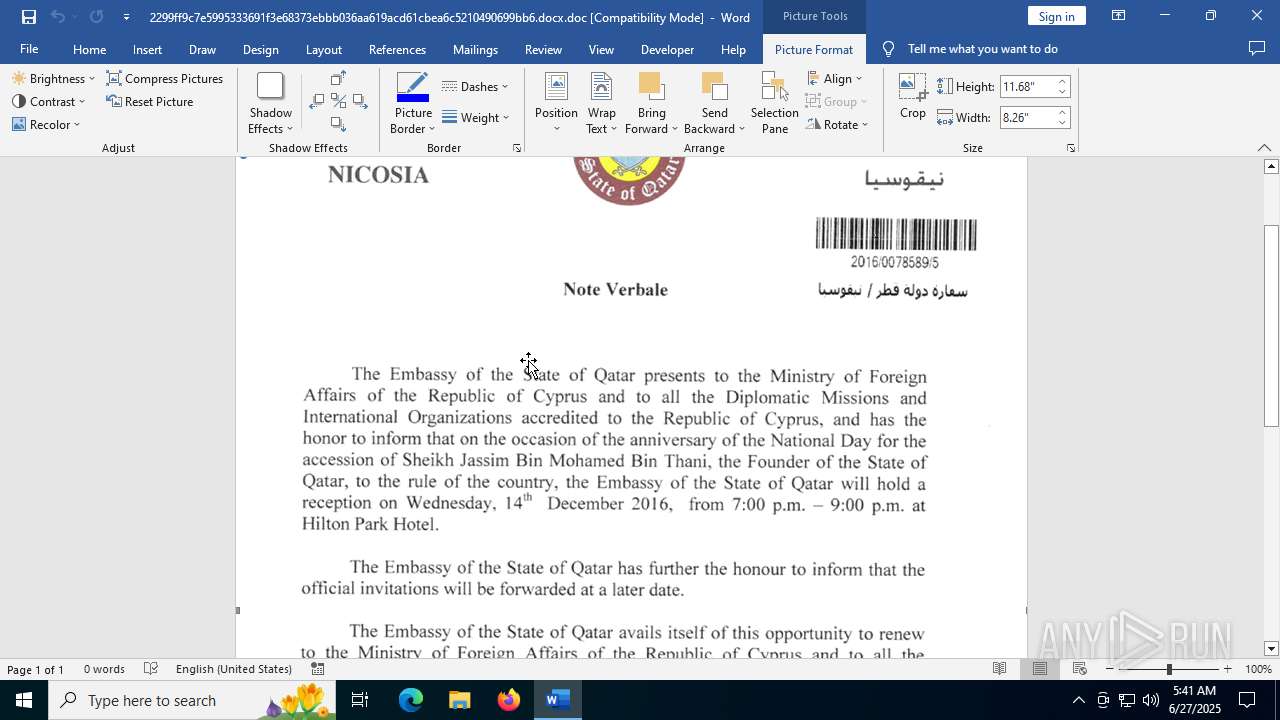
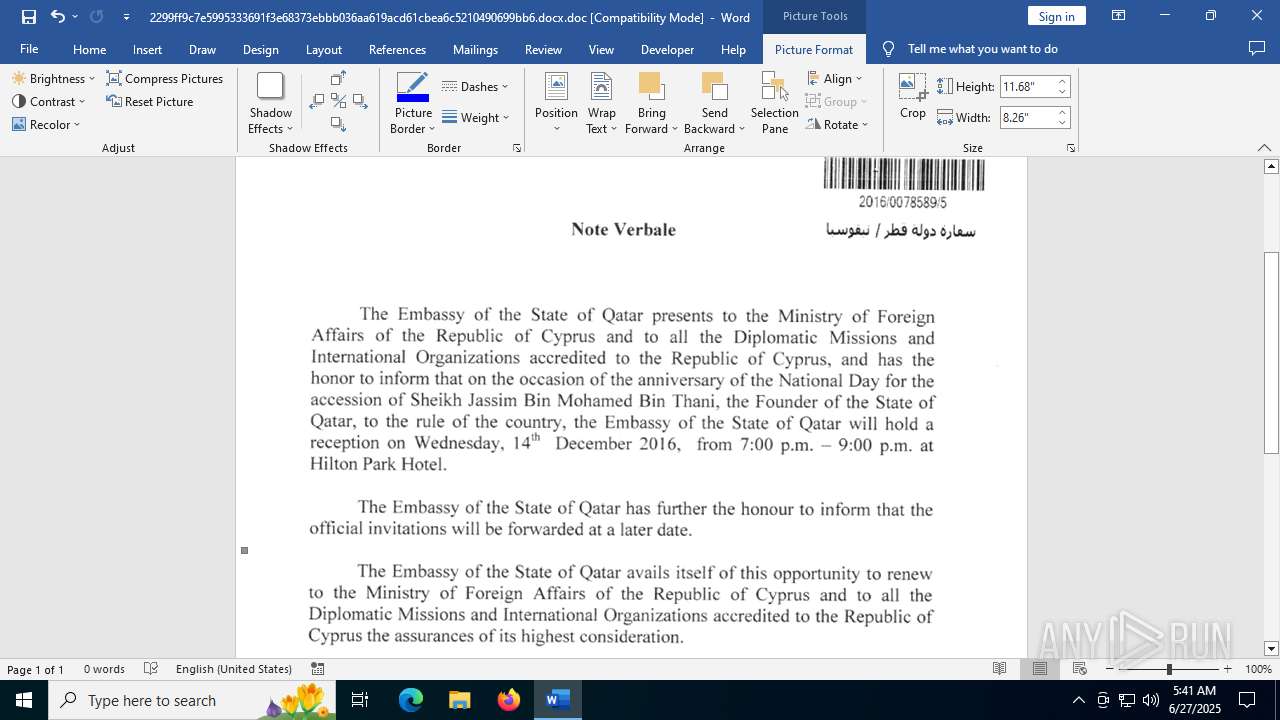
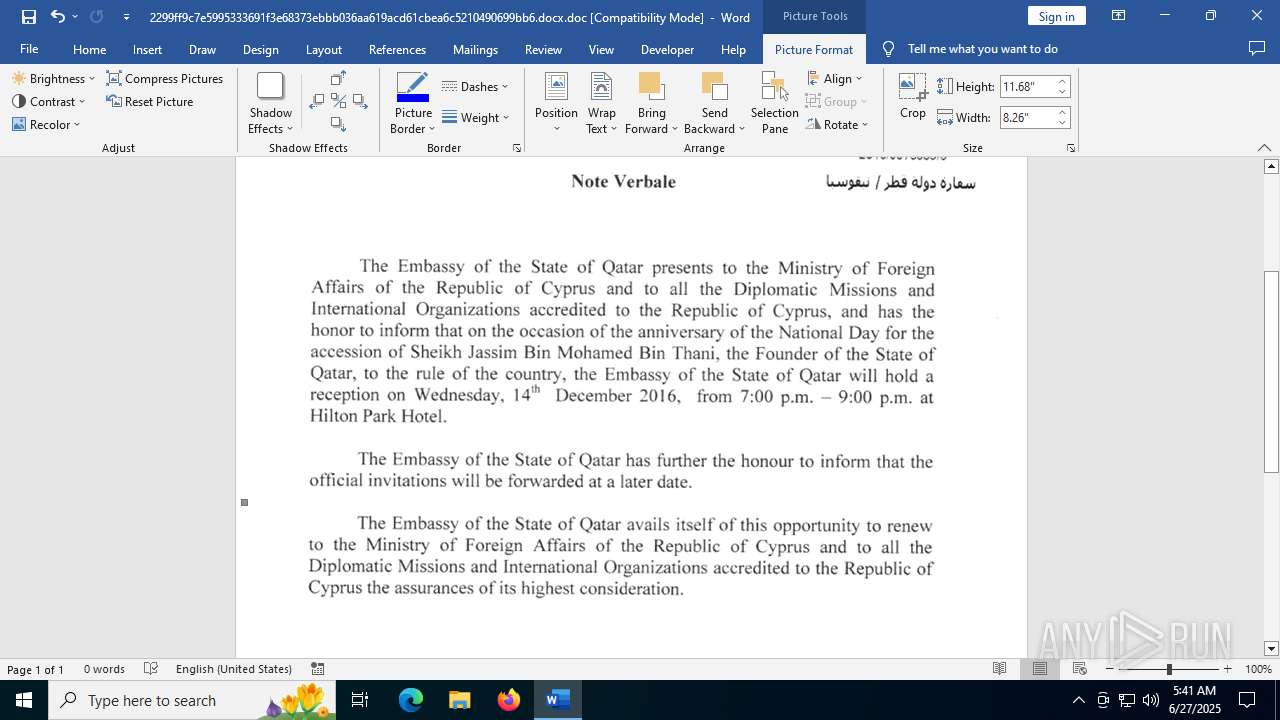
| File name: | 2299ff9c7e5995333691f3e68373ebbb036aa619acd61cbea6c5210490699bb6.docx |
| Full analysis: | https://app.any.run/tasks/2b012dea-d195-4fd4-9e8e-88f8c9517d6c |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2025, 05:40:18 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: user, Template: Normal.dotm, Last Saved By: John, Revision Number: 15, Name of Creating Application: Microsoft Office Word, Total Editing Time: 07:00, Create Time/Date: Wed Nov 16 21:58:00 2016, Last Saved Time/Date: Thu Nov 24 17:42:00 2016, Number of Pages: 1, Number of Words: 0, Number of Characters: 2, Security: 0 |
| MD5: | 6E7991F93C53A58BA63A602B277E07F7 |
| SHA1: | D6E6EAB05AF60A496060D266F144E43F6D5D6EC1 |
| SHA256: | 2299FF9C7E5995333691F3E68373EBBB036AA619ACD61CBEA6C5210490699BB6 |
| SSDEEP: | 6144:xfx4ml75YTwo90TbUYMkHTZjH3E1/x7a7V+TcXl1J85EGGVU:xJ4ml7KD9d1kHVjHYx7ifXl1J8SGG |
MALICIOUS
Unusual execution from MS Office
- WINWORD.EXE (PID: 1044)
Checks whether a specified folder exists (SCRIPT)
- WINWORD.EXE (PID: 1044)
- wscript.exe (PID: 4920)
Copies file to a new location (SCRIPT)
- wscript.exe (PID: 4920)
Deletes a file (SCRIPT)
- WINWORD.EXE (PID: 1044)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- WINWORD.EXE (PID: 1044)
- wscript.exe (PID: 4920)
Accesses command line arguments (SCRIPT)
- wscript.exe (PID: 4920)
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 1044)
Gets name of the script (SCRIPT)
- wscript.exe (PID: 4920)
Accesses current user name via WMI (SCRIPT)
- wscript.exe (PID: 4920)
The process executes JS scripts
- WINWORD.EXE (PID: 1044)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 4920)
INFO
Reads the software policy settings
- slui.exe (PID: 2764)
Checks proxy server information
- slui.exe (PID: 2764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | user |
| Keywords: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | John |
| Software: | Microsoft Office Word |
| CreateDate: | 2016:11:16 21:58:00 |
| ModifyDate: | 2016:11:24 17:42:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| CharCountWithSpaces: | 2 |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 15 |
| TotalEditTime: | 7 minutes |
| Words: | - |
| Characters: | 2 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
144
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1044 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\AppData\Local\Temp\2299ff9c7e5995333691f3e68373ebbb036aa619acd61cbea6c5210490699bb6.docx.doc /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 2764 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4920 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\mailform.js" NPEfpRZ4aqnh1YuGwQd0 | C:\Windows\System32\wscript.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6412 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "191BEB18-7A1C-444E-A8D9-7BCEB4C1576C" "E752AA26-4C1C-4615-A01F-D41B88E60359" "1044" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
15 395
Read events
15 000
Write events
364
Delete events
31
Modification events
| (PID) Process: | (1044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (1044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\1044 |
| Operation: | write | Name: | 0 |
Value: 0B0E1020BAF442A7EB8643A0DD2E2B81FAF5CF230046D384C0D4DFE4F9ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5119408D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (1044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (1044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (1044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (1044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (1044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (1044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (1044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (1044) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
33
Suspicious files
159
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1044 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:4BF08289328750363E73C0BA92BE977E | SHA256:9978C6A1885569AE8532C2B0B7FE78E2652526C5472A96CC153AA618A0189F9E | |||
| 1044 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms~RF17784d.TMP | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 1044 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 4920 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\mailform.js | text | |
MD5:05D07279ED123B3A9170FA2C540D2919 | SHA256:4F8BC0C14DD95AFEB5A14BE0F392A66408D3039518543C3E1E666D973F2BA634 | |||
| 1044 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:DA65996FD8B4E340509D9BA92E7CBDBD | SHA256:95A945824CC0DD8641DC7C1E5EAE388E8BD5677E7E549EB25EDFDCB446297F1E | |||
| 1044 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\AGXBMZTMU9PXCJ3WLMWX.temp | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 1044 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\6FB05137.emf | binary | |
MD5:4288D229BC00B40F92976E3D80FF0048 | SHA256:997D3D5A4FFF0227EB50E06F3A954D949CC649ED86B73031BE4C93D651A3C982 | |||
| 1044 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Word\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAQ.S | binary | |
MD5:F3567D68BEE56E3D602AA0D97B1BE495 | SHA256:FF5AE7F9308F0B4721DA06057A879EC6FC9A16D8FAB293913B61A4BD9854C3B8 | |||
| 1044 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Word\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:F3567D68BEE56E3D602AA0D97B1BE495 | SHA256:FF5AE7F9308F0B4721DA06057A879EC6FC9A16D8FAB293913B61A4BD9854C3B8 | |||
| 1044 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\31D90E8E.emf | binary | |
MD5:4288D229BC00B40F92976E3D80FF0048 | SHA256:997D3D5A4FFF0227EB50E06F3A954D949CC649ED86B73031BE4C93D651A3C982 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
77
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2668 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1044 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
1044 | WINWORD.EXE | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
1044 | WINWORD.EXE | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
1044 | WINWORD.EXE | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1044 | WINWORD.EXE | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
1044 | WINWORD.EXE | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
1044 | WINWORD.EXE | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
892 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1044 | WINWORD.EXE | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1044 | WINWORD.EXE | 23.48.23.18:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
1044 | WINWORD.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1044 | WINWORD.EXE | 52.111.231.13:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
ecs.office.com |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|