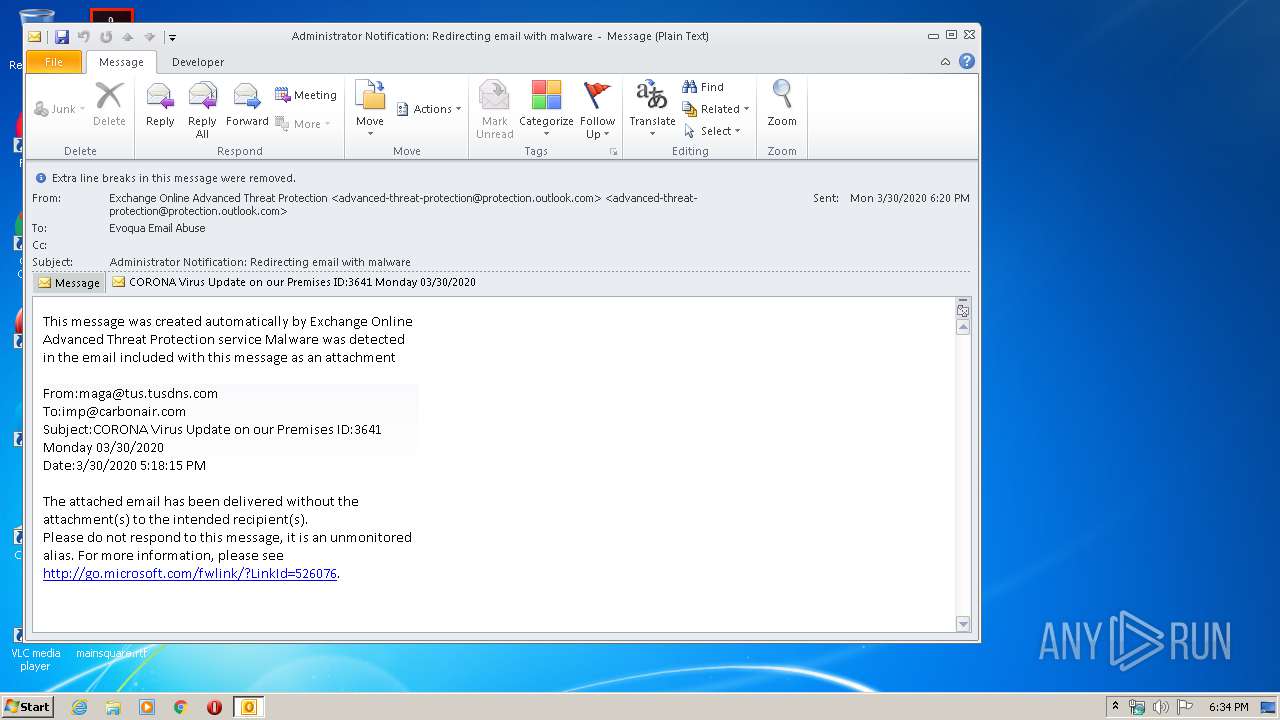
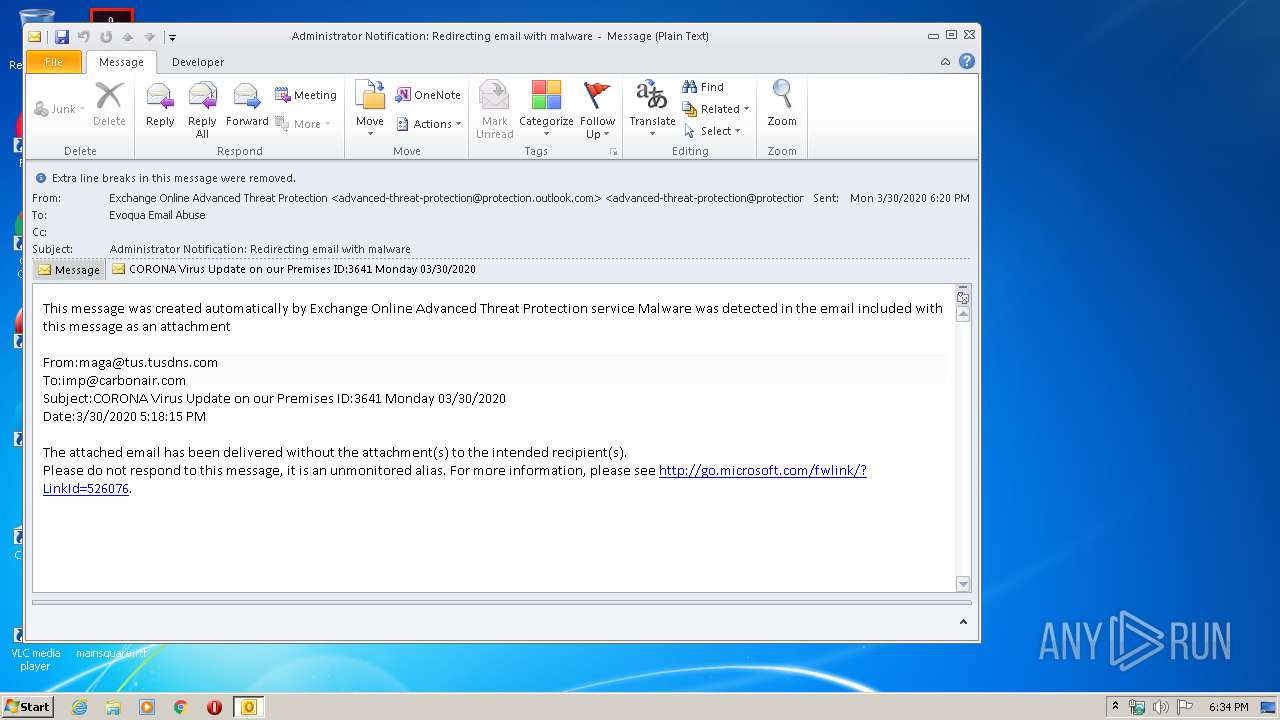
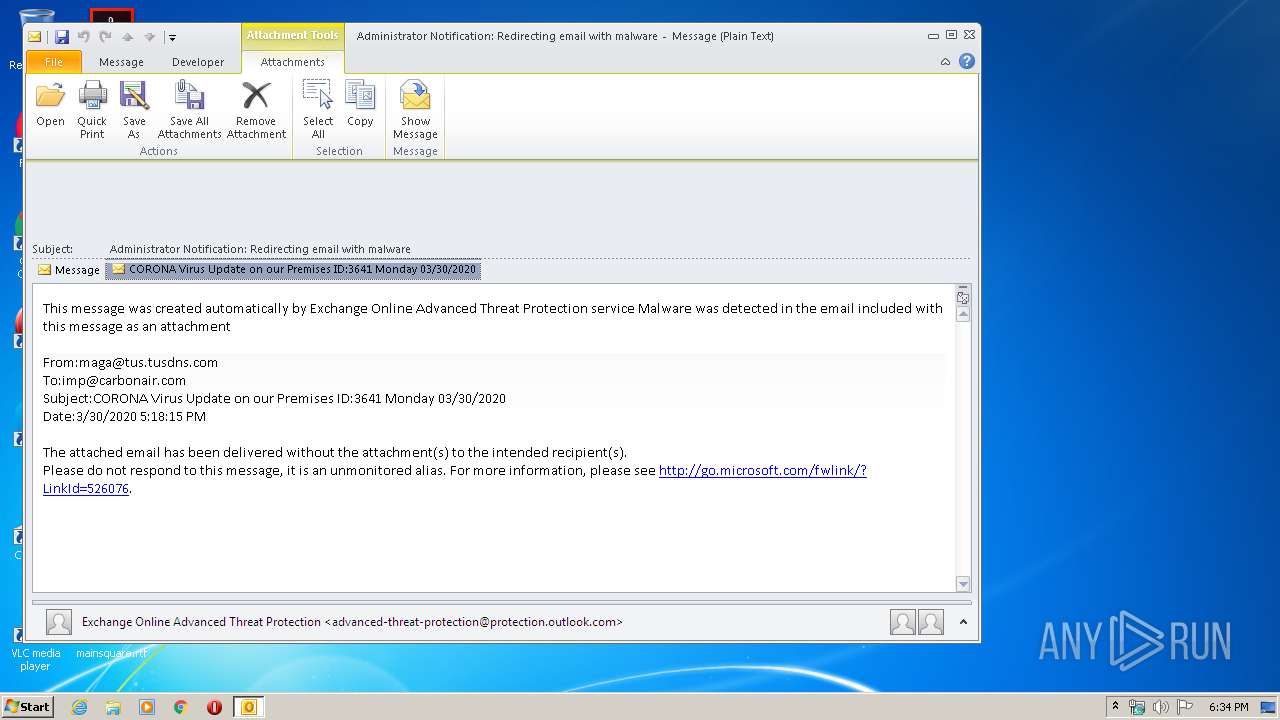
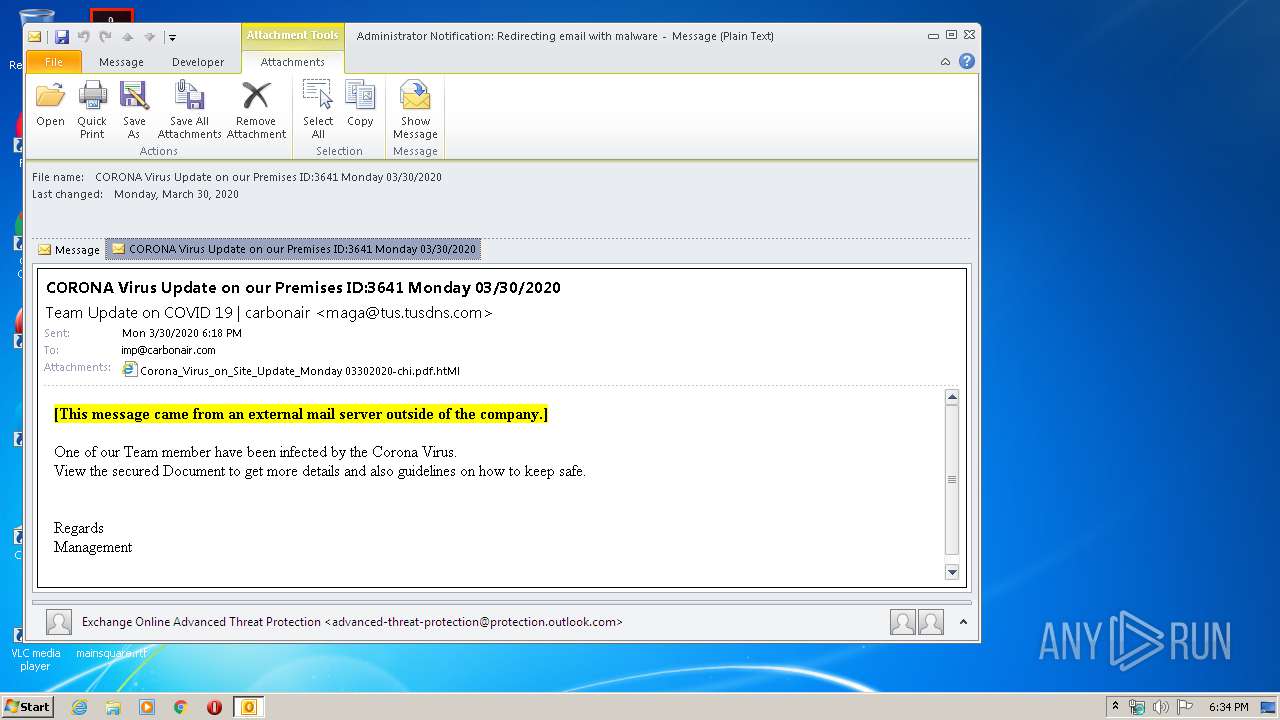
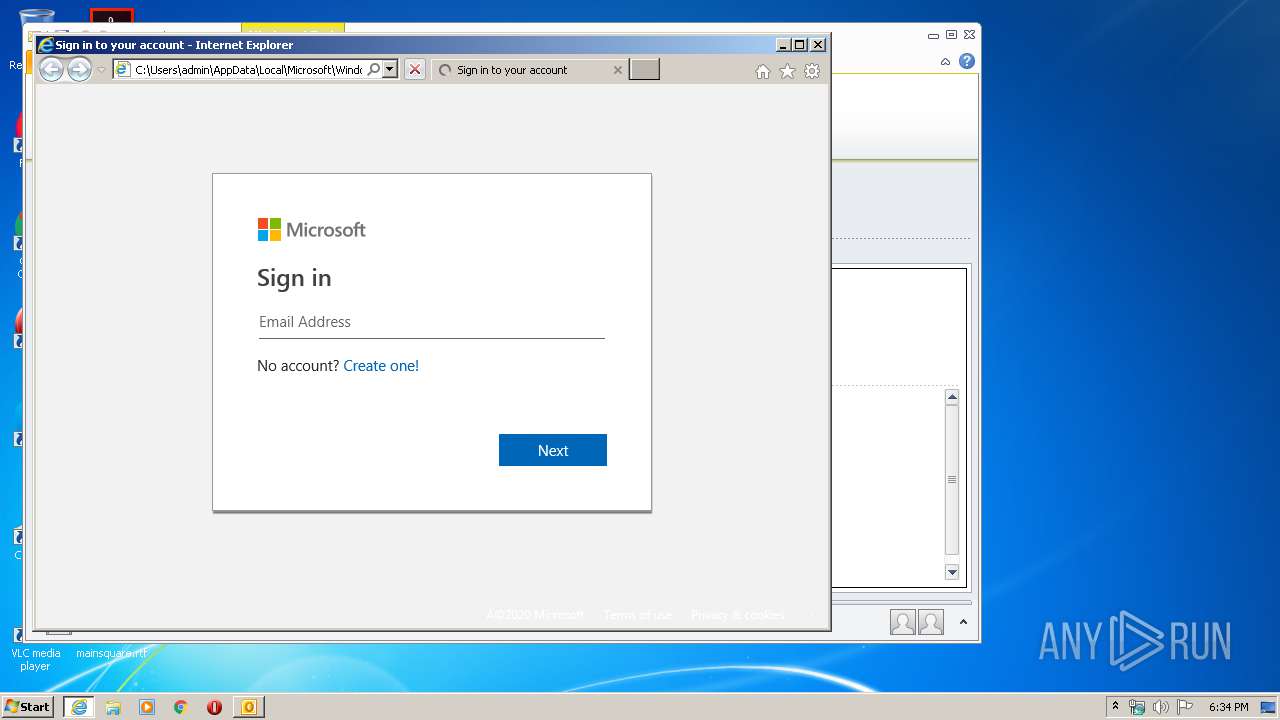
| File name: | Administrator Notification_ Redirecting email with malware.msg |
| Full analysis: | https://app.any.run/tasks/ebddfc36-4fa7-4145-ae91-b3f4b33f37e7 |
| Verdict: | Malicious activity |
| Analysis date: | March 30, 2020, 17:33:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | CAD25D44F7501B46604A9B8ECC5B291E |
| SHA1: | 6211C86CD8F26791C07E325823A8486DEE35BC1D |
| SHA256: | 22951A67B22D8477D3D708CE133E8D84A3D199A2F07A2374F56FAAE09A9506B4 |
| SSDEEP: | 1536:9h/W4WTc/dnKM5VYWWUWsjN9ldnauBlSEFUJueU7kJdoVW6Y7G9fPVoIBIc5J:9hWc/9KMVjJbSVP6Y7GNVoIBIc5J |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2856)
SUSPICIOUS
Starts Internet Explorer
- OUTLOOK.EXE (PID: 2856)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2856)
INFO
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2856)
- iexplore.exe (PID: 2892)
- iexplore.exe (PID: 3244)
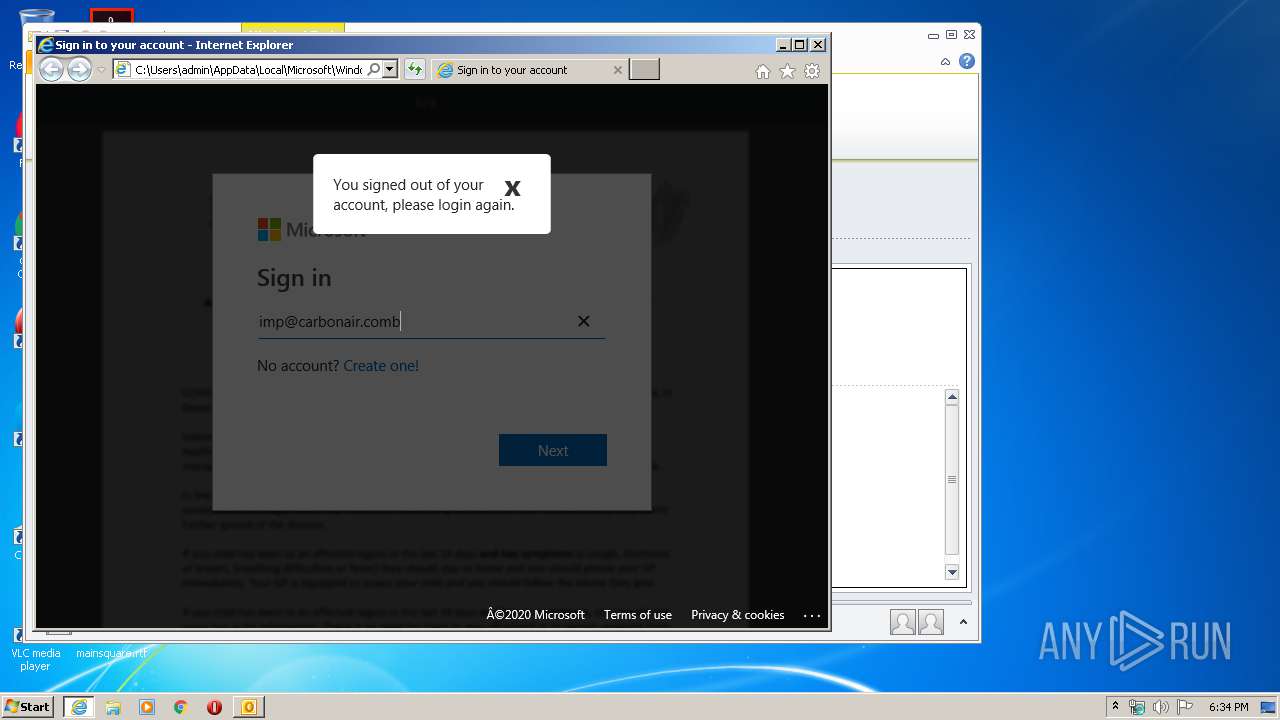
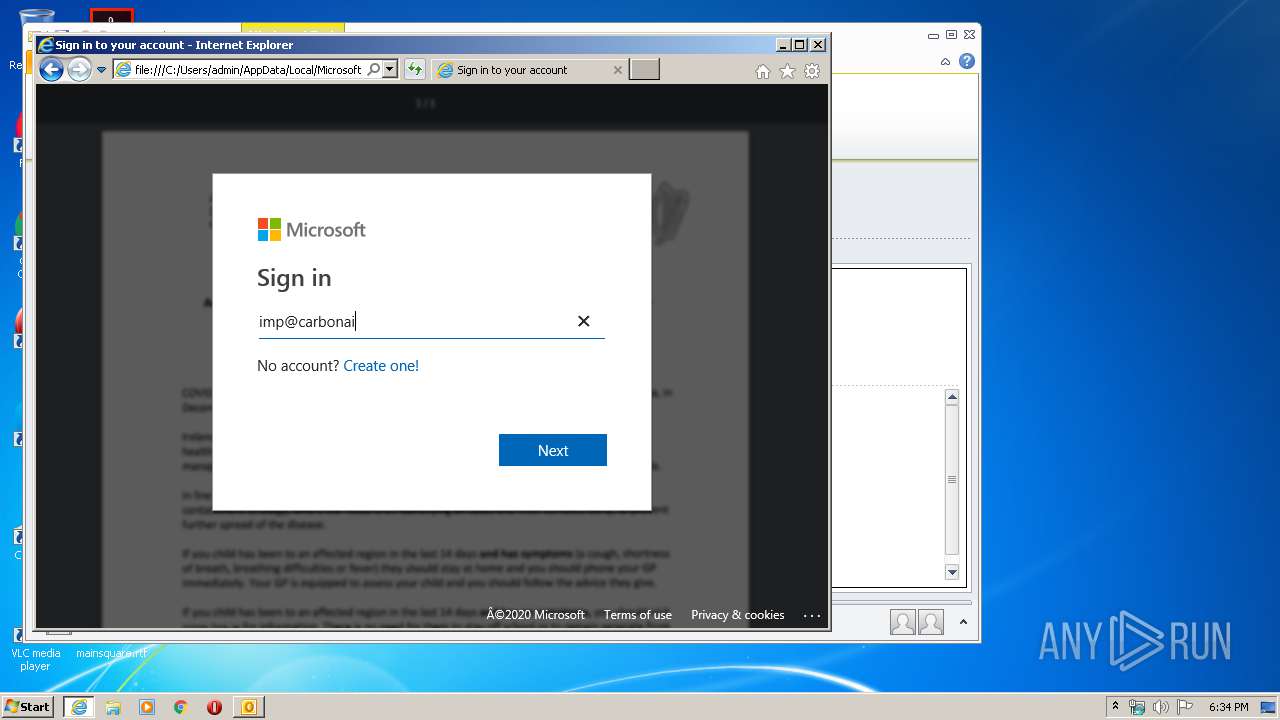
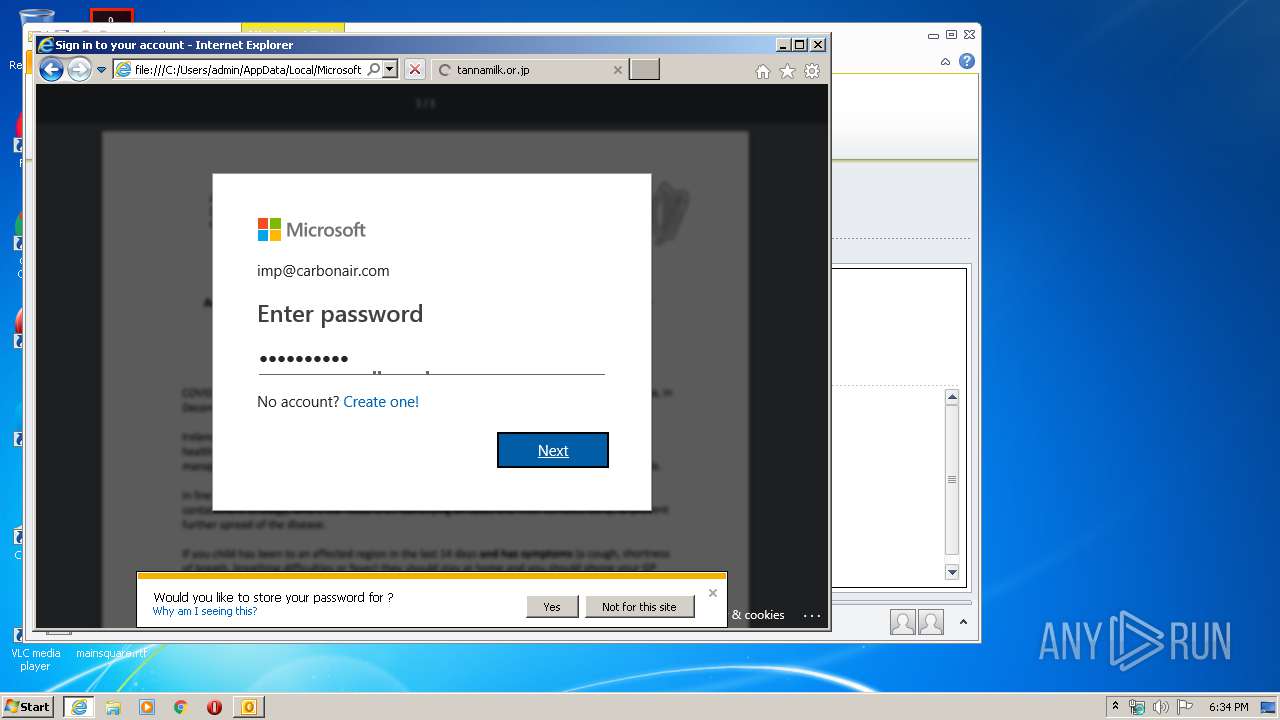
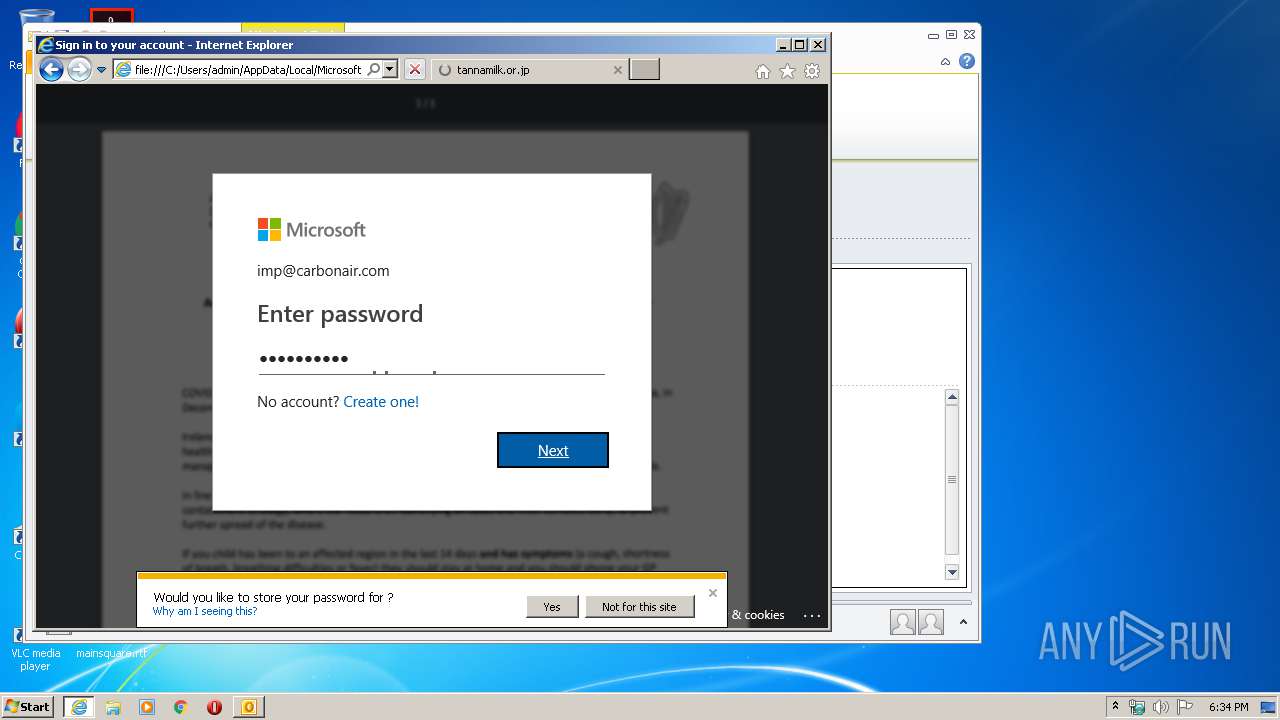
Drops Coronavirus (possible) decoy
- OUTLOOK.EXE (PID: 2856)
Changes internet zones settings
- iexplore.exe (PID: 2892)
Application launched itself
- iexplore.exe (PID: 2892)
Reads internet explorer settings
- iexplore.exe (PID: 3244)
Reads settings of System Certificates
- iexplore.exe (PID: 3244)
- iexplore.exe (PID: 2892)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2856)
Changes settings of System certificates
- iexplore.exe (PID: 2892)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
39
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2856 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Administrator Notification_ Redirecting email with malware.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
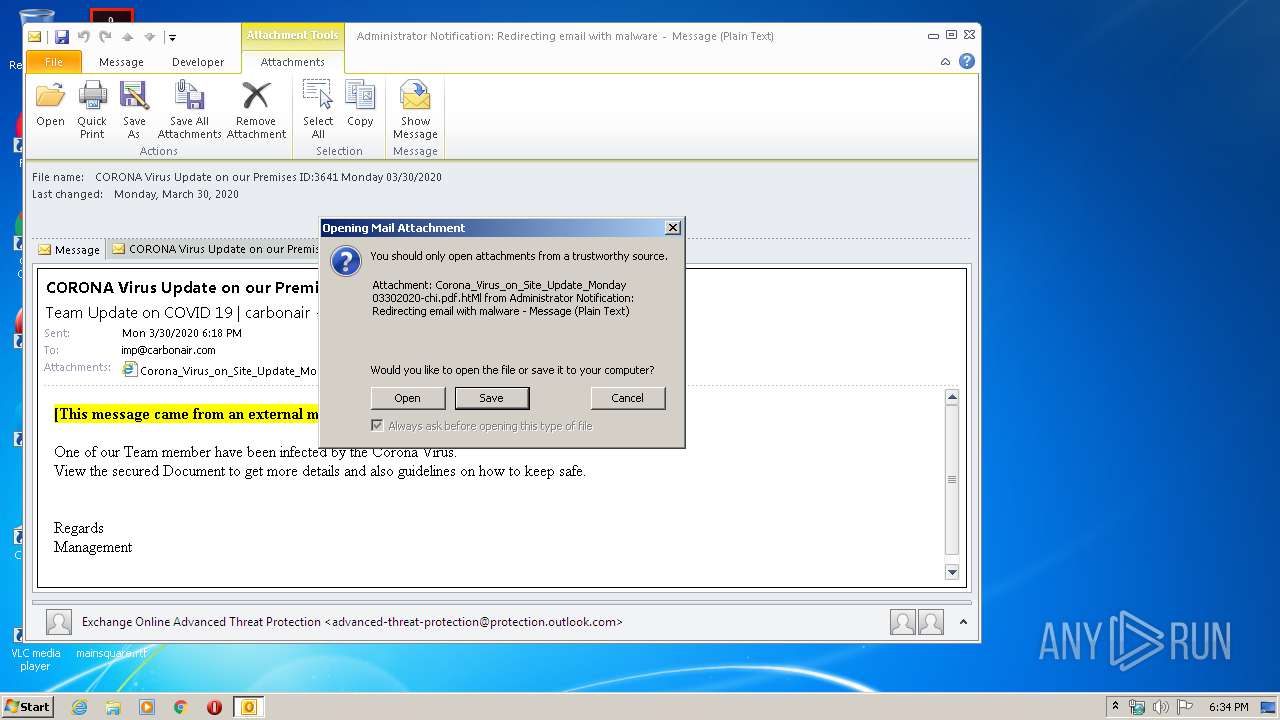
| 2892 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\66SQBMZV\Corona_Virus_on_Site_Update_Monday 03302020-chi pdf.htMl | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3244 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2892 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
5 601
Read events
2 158
Write events
2 481
Delete events
962
Modification events
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2856) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
18
Text files
43
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2856 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR653A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2856 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF444AF8FFFB8E9201.TMP | — | |
MD5:— | SHA256:— | |||
| 2856 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\66SQBMZV\Corona_Virus_on_Site_Update_Monday 03302020-chi pdf (2).htMl\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2856 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2856 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2856 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\66SQBMZV\Corona_Virus_on_Site_Update_Monday 03302020-chi pdf (2).htMl | html | |
MD5:— | SHA256:— | |||
| 2856 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\66SQBMZV\Corona_Virus_on_Site_Update_Monday 03302020-chi pdf.htMl | html | |
MD5:— | SHA256:— | |||
| 2856 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
| 3244 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab97E3.tmp | — | |
MD5:— | SHA256:— | |||
| 3244 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar97E4.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
33
DNS requests
19
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2856 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
2892 | iexplore.exe | GET | 200 | 166.62.13.1:80 | http://ozturkkilcadir.com/favicon.ico | US | — | — | suspicious |
3244 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAtqs7A%2Bsan2xGCSaqjN%2FrM%3D | US | der | 1.47 Kb | whitelisted |
3244 | iexplore.exe | GET | 200 | 95.101.72.151:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
3244 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | US | der | 471 b | whitelisted |
3244 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCECsuburZdTZsFIpu26N8jAc%3D | US | der | 727 b | whitelisted |
3244 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCECsuburZdTZsFIpu26N8jAc%3D | US | der | 727 b | whitelisted |
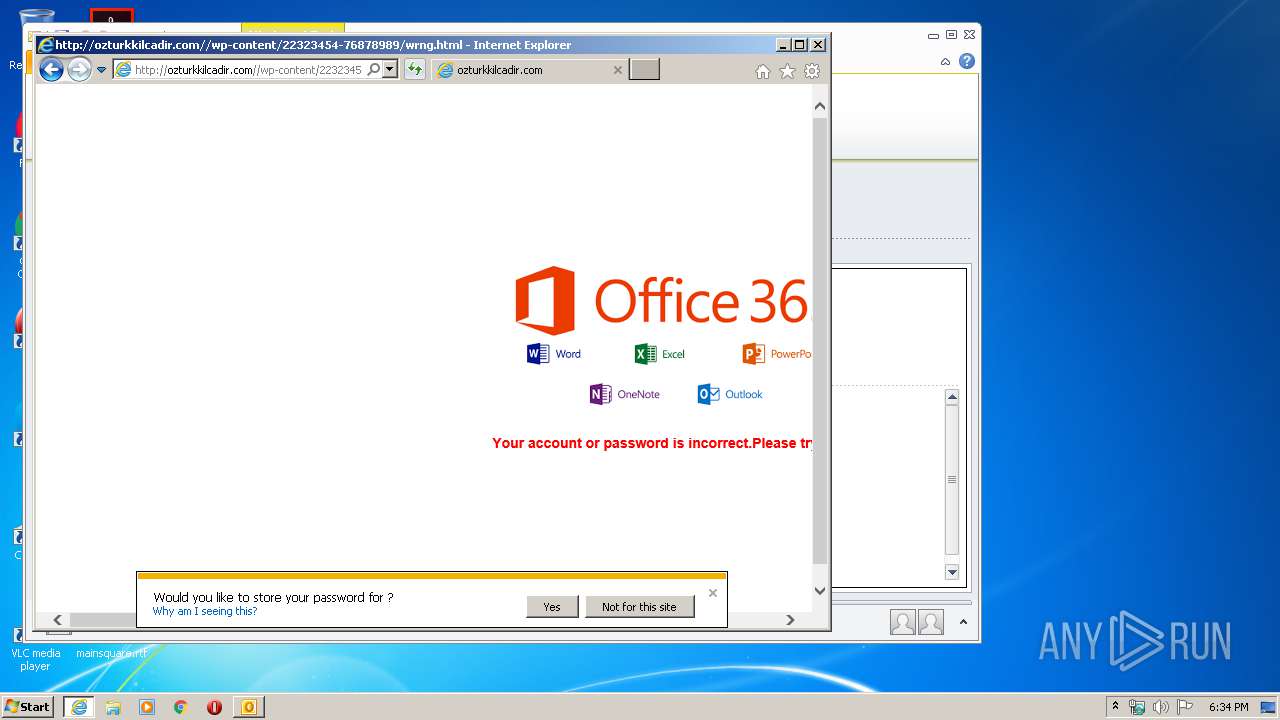
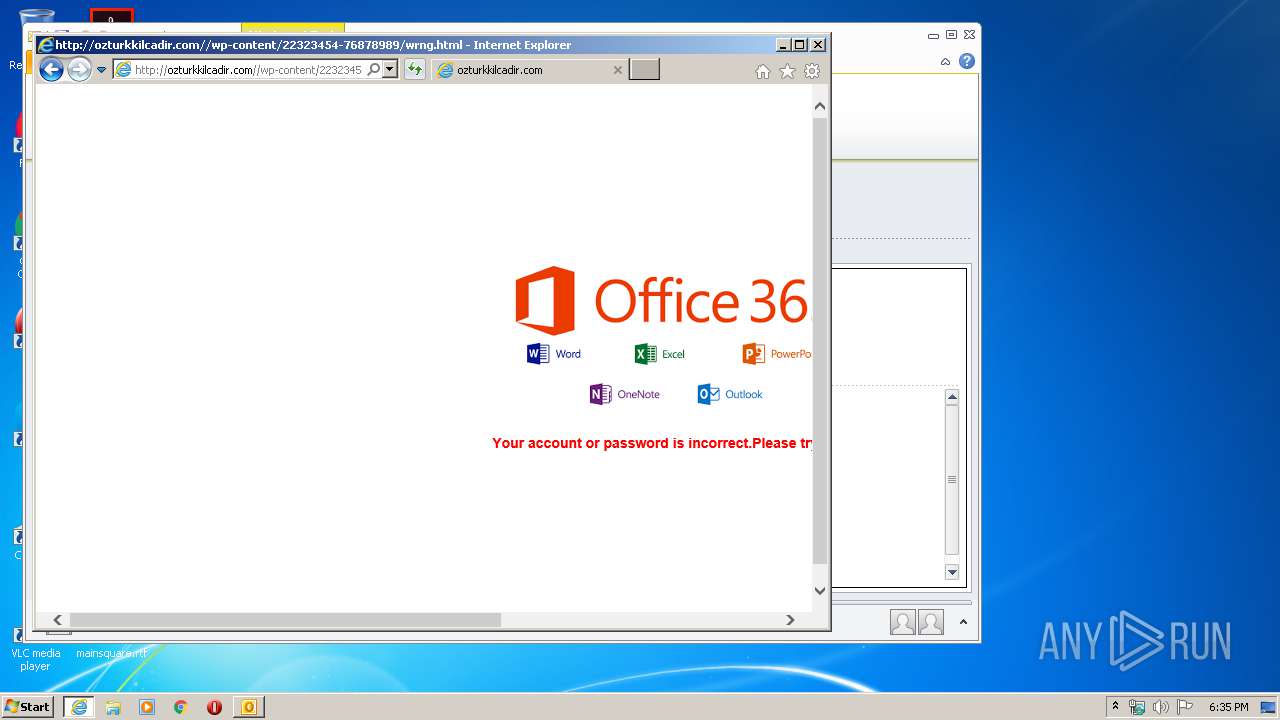
3244 | iexplore.exe | GET | 200 | 166.62.13.1:80 | http://ozturkkilcadir.com//wp-content/22323454-76878989/wrng.html | US | text | 761 b | suspicious |
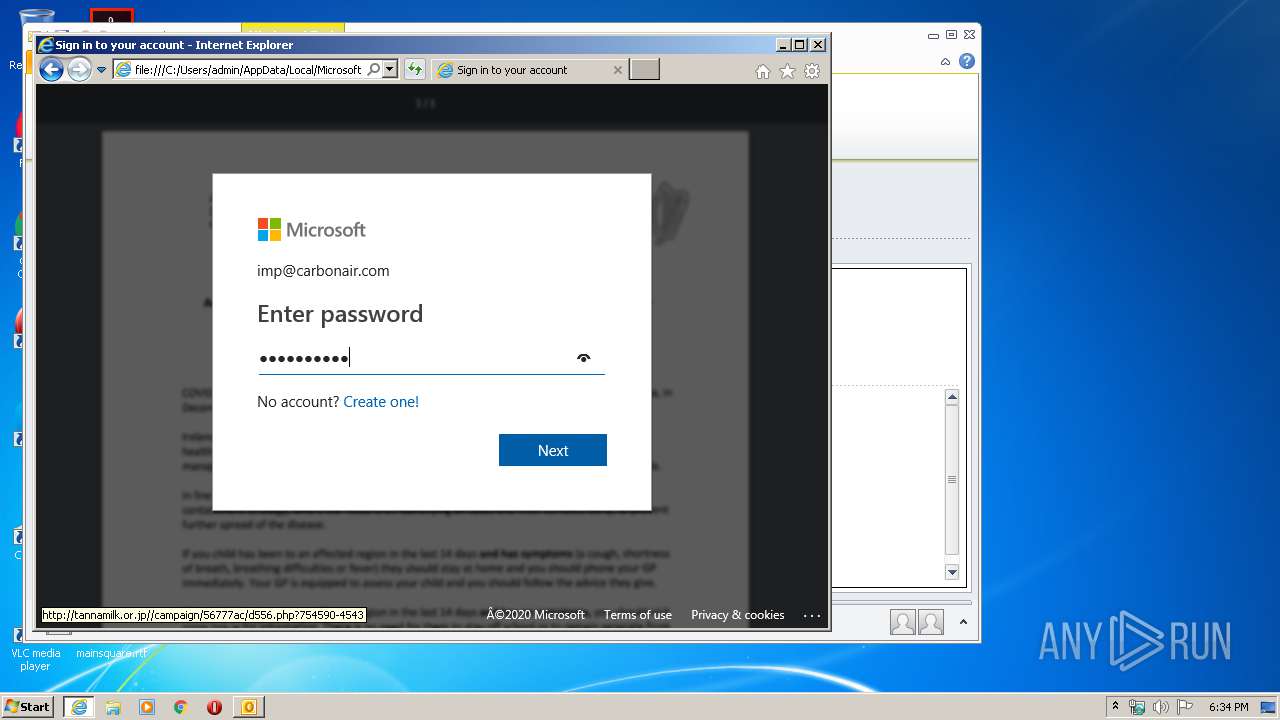
3244 | iexplore.exe | POST | 302 | 211.10.17.60:80 | http://tannamilk.or.jp//campaign/56777ac/d556.php?754590-4543 | JP | — | — | suspicious |
3244 | iexplore.exe | GET | 200 | 172.217.21.227:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDL%2FQslYWVuogIAAAAAXGdc | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3244 | iexplore.exe | 50.87.153.159:80 | ibuykenya.com | Unified Layer | US | suspicious |
2856 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3244 | iexplore.exe | 51.15.21.205:443 | i.postimg.cc | Online S.a.s. | NL | unknown |
3244 | iexplore.exe | 51.15.22.18:443 | i.ibb.co | Online S.a.s. | NL | unknown |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3244 | iexplore.exe | 95.101.72.151:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
2892 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3244 | iexplore.exe | 151.139.128.14:80 | ocsp.usertrust.com | Highwinds Network Group, Inc. | US | suspicious |
3244 | iexplore.exe | 211.10.17.60:80 | tannamilk.or.jp | Yahoo Japan Corporation | JP | suspicious |
3244 | iexplore.exe | 172.217.16.206:443 | encrypted-tbn1.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
ibuykenya.com |
| suspicious |
secure.aadcdn.microsoftonline-p.com |
| whitelisted |
i.postimg.cc |
| whitelisted |
code.jquery.com |
| whitelisted |
i.ibb.co |
| shared |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
3244 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY Http Client Body contains pass= in cleartext |