| File name: | UziClicker.exe |
| Full analysis: | https://app.any.run/tasks/cb46ac8c-b227-4e39-9c37-e72e6febccbc |
| Verdict: | Malicious activity |
| Analysis date: | April 20, 2022, 07:16:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | A30FB211645CF11E0DC5FB9517899701 |
| SHA1: | 76B6DF6E73540ABECCAA31FB1E7FB43DE93349BE |
| SHA256: | 2288449CD65625C4DB6985EC4071D24B174164FED73EF5D16900A4DB6795F03A |
| SSDEEP: | 98304:9Qf3s64R9ybzUcwti78OqJ7TPBF3ZlHHgkWJ0P39qXSaDv0ICf:wzUcwti7TQlF3ZxxWJSUnDvo |
MALICIOUS
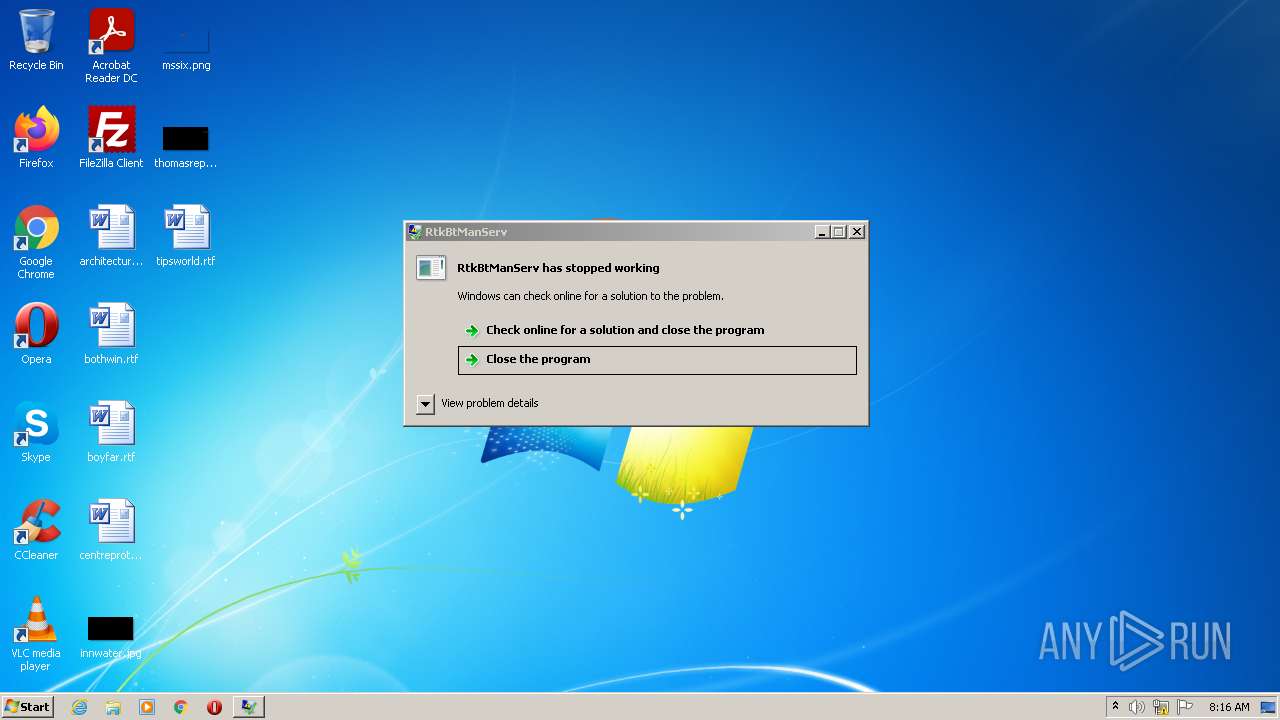
Drops executable file immediately after starts
- RtkBtManServ.exe (PID: 1556)
- UziClicker.exe (PID: 3876)
Writes to a start menu file
- UziClicker.exe (PID: 3876)
Disables Windows Defender
- reg.exe (PID: 1348)
- reg.exe (PID: 3980)
- reg.exe (PID: 3868)
- reg.exe (PID: 2120)
- reg.exe (PID: 4068)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3508)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2100)
- schtasks.exe (PID: 3184)
- schtasks.exe (PID: 3348)
- schtasks.exe (PID: 3452)
- schtasks.exe (PID: 2692)
Creates or modifies windows services
- reg.exe (PID: 2632)
Application was dropped or rewritten from another process
- RtkBtManServ.exe (PID: 1556)
SUSPICIOUS
Checks supported languages
- UziClicker.exe (PID: 3876)
- RtkBtManServ.exe (PID: 1556)
- cmd.exe (PID: 3508)
Executable content was dropped or overwritten
- UziClicker.exe (PID: 3876)
- RtkBtManServ.exe (PID: 1556)
Reads the computer name
- UziClicker.exe (PID: 3876)
- RtkBtManServ.exe (PID: 1556)
Creates files in the user directory
- UziClicker.exe (PID: 3876)
Drops a file with a compile date too recent
- UziClicker.exe (PID: 3876)
- RtkBtManServ.exe (PID: 1556)
Starts CMD.EXE for commands execution
- UziClicker.exe (PID: 3876)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3508)
Creates or modifies windows services
- reg.exe (PID: 1204)
- reg.exe (PID: 2216)
- reg.exe (PID: 4020)
- reg.exe (PID: 1120)
Reads Environment values
- RtkBtManServ.exe (PID: 1556)
Modifies files in Chrome extension folder
- chrome.exe (PID: 1364)
INFO
Checks supported languages
- reg.exe (PID: 3676)
- reg.exe (PID: 568)
- reg.exe (PID: 1348)
- reg.exe (PID: 3980)
- reg.exe (PID: 3868)
- reg.exe (PID: 876)
- reg.exe (PID: 2120)
- reg.exe (PID: 4068)
- reg.exe (PID: 2408)
- reg.exe (PID: 772)
- reg.exe (PID: 3792)
- reg.exe (PID: 2572)
- reg.exe (PID: 3720)
- reg.exe (PID: 2796)
- reg.exe (PID: 2132)
- schtasks.exe (PID: 2100)
- schtasks.exe (PID: 3184)
- schtasks.exe (PID: 3348)
- schtasks.exe (PID: 2692)
- schtasks.exe (PID: 3452)
- reg.exe (PID: 4076)
- reg.exe (PID: 1204)
- reg.exe (PID: 3688)
- reg.exe (PID: 680)
- reg.exe (PID: 3572)
- reg.exe (PID: 3824)
- reg.exe (PID: 1120)
- reg.exe (PID: 2632)
- reg.exe (PID: 2216)
- reg.exe (PID: 4020)
- chrome.exe (PID: 1364)
- chrome.exe (PID: 3844)
- chrome.exe (PID: 2444)
- chrome.exe (PID: 2436)
- chrome.exe (PID: 2628)
- chrome.exe (PID: 1872)
- chrome.exe (PID: 1968)
- chrome.exe (PID: 1008)
- chrome.exe (PID: 988)
- chrome.exe (PID: 2912)
- chrome.exe (PID: 920)
- chrome.exe (PID: 3432)
- chrome.exe (PID: 2780)
- chrome.exe (PID: 3124)
- chrome.exe (PID: 3496)
- chrome.exe (PID: 2012)
- chrome.exe (PID: 3604)
- chrome.exe (PID: 2568)
- chrome.exe (PID: 1836)
Reads the computer name
- schtasks.exe (PID: 2100)
- schtasks.exe (PID: 3184)
- schtasks.exe (PID: 3348)
- schtasks.exe (PID: 2692)
- schtasks.exe (PID: 3452)
- chrome.exe (PID: 1364)
- chrome.exe (PID: 2444)
- chrome.exe (PID: 2628)
- chrome.exe (PID: 988)
- chrome.exe (PID: 2568)
- chrome.exe (PID: 3604)
- chrome.exe (PID: 2436)
Manual execution by user
- chrome.exe (PID: 1364)
Application launched itself
- chrome.exe (PID: 1364)
Reads the hosts file
- chrome.exe (PID: 1364)
- chrome.exe (PID: 2436)
Reads settings of System Certificates
- chrome.exe (PID: 2436)
Reads the date of Windows installation
- chrome.exe (PID: 2568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (34.4) |
|---|---|---|
| .exe | | | InstallShield setup (20.2) |
| .exe | | | Win64 Executable (generic) (12.9) |
| .exe | | | UPX compressed Win32 Executable (12.7) |
| .exe | | | Win32 EXE Yoda's Crypter (12.4) |
EXIF
EXE
| AssemblyVersion: | 1.0.0.0 |
|---|---|
| ProductVersion: | 1.0.0.0 |
| OriginalFileName: | Obfuscated Name.exe |
| LegalCopyright: | |
| InternalName: | Obfuscated Name.exe |
| FileVersion: | 1.0.0.0 |
| FileDescription: | |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.0.0.0 |
| FileVersionNumber: | 1.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x478a7e |
| UninitializedDataSize: | - |
| InitializedDataSize: | 198656 |
| CodeSize: | 4680704 |
| LinkerVersion: | 11 |
| PEType: | PE32 |
| TimeStamp: | 2022:04:20 09:11:58+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 20-Apr-2022 07:11:58 |
| Debug artifacts: |
|
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | Obfuscated Name.exe |
| LegalCopyright: | - |
| OriginalFilename: | Obfuscated Name.exe |
| ProductVersion: | 1.0.0.0 |
| Assembly Version: | 1.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 20-Apr-2022 07:11:58 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00476A84 | 0x00476C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.83014 |
.rsrc | 0x0047A000 | 0x00030430 | 0x00030600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.83249 |
.reloc | 0x004AC000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.0980042 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 4.83306 | 196240 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 2.22322 | 20 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
91
Monitored processes
52
Malicious processes
3
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | reg add "HKLM\Software\Policies\Microsoft\Windows Defender" /v "DisableAntiVirus" /t REG_DWORD /d "1" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 680 | reg delete "HKLM\Software\Microsoft\Windows\CurrentVersion\Run" /v "SecurityHealth" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 772 | reg add "HKLM\Software\Policies\Microsoft\Windows Defender\SpyNet" /v "SubmitSamplesConsent" /t REG_DWORD /d "2" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 876 | reg add "HKLM\Software\Policies\Microsoft\Windows Defender\Real-Time Protection" /v "DisableRealtimeMonitoring" /t REG_DWORD /d "1" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 920 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1036,15765977911028684857,7988574247333143849,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2372 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 988 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1036,15765977911028684857,7988574247333143849,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3196 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,15765977911028684857,7988574247333143849,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3444 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1120 | reg add "HKLM\System\CurrentControlSet\Services\WdFilter" /v "Start" /t REG_DWORD /d "4" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1204 | reg add "HKLM\System\CurrentControlSet\Services\WdBoot" /v "Start" /t REG_DWORD /d "4" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1348 | reg add "HKLM\Software\Policies\Microsoft\Windows Defender" /v "DisableAntiSpyware" /t REG_DWORD /d "1" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
12 834
Read events
12 708
Write events
122
Delete events
4
Modification events
| (PID) Process: | (3876) UziClicker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3876) UziClicker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3876) UziClicker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3876) UziClicker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3676) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Real-time Protection |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3676) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1348) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
| (PID) Process: | (568) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiVirus |
Value: 1 | |||
| (PID) Process: | (3792) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\MpEngine |
| Operation: | write | Name: | MpEnablePus |
Value: 0 | |||
| (PID) Process: | (3980) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection |
| Operation: | write | Name: | DisableBehaviorMonitoring |
Value: 1 | |||
Executable files
8
Suspicious files
135
Text files
100
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3876 | UziClicker.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Microsoft Update Manager4889708.exe | executable | |
MD5:— | SHA256:— | |||
| 1556 | RtkBtManServ.exe | C:\Users\admin\AppData\Local\Temp\xwizard.cfg | text | |
MD5:AE8EED5A6B1470AEC0E7FECE8B0669EF | SHA256:3F6CA2BC068C8436044DAAB867F8FF8F75060048B29882CB2AC9FDEF1800DF9E | |||
| 3876 | UziClicker.exe | C:\Users\admin\AppData\Local\Temp\whysosad | text | |
MD5:FC3C88C2080884D6C995D48E172FBC4F | SHA256:1637CE704A463BD3C91A38AA02D1030107670F91EE3F0DD4FA13D07A77BA2664 | |||
| 1556 | RtkBtManServ.exe | C:\Users\admin\AppData\Local\Temp\costura.discord.net.core.dll.compressed | binary | |
MD5:4104898CA34FEBB688ED63812EFE8CF4 | SHA256:265850B1887F252E04C54F81EF872587B3CFD66B0D708621D2520BC6D4BBDCAC | |||
| 3876 | UziClicker.exe | C:\Users\admin\AppData\Local\Temp\RtkBtManServ.exe | executable | |
MD5:3405F654559010CA2AE38D786389F0F1 | SHA256:BC1364D8E68F515F9F35A6B41C11A649B1F514302EB01812C68C9A95A3198B30 | |||
| 3876 | UziClicker.exe | C:\Users\admin\AppData\Local\Temp\dav.bat | text | |
MD5:FC3C88C2080884D6C995D48E172FBC4F | SHA256:1637CE704A463BD3C91A38AA02D1030107670F91EE3F0DD4FA13D07A77BA2664 | |||
| 1556 | RtkBtManServ.exe | C:\Users\admin\AppData\Local\Temp\bfsvc.exe | executable | |
MD5:899D3ED011EB58459B8A4FC2B81F0924 | SHA256:5E3F311AE67F046B56435067BCDD39FBF836FA0421FBC8C8B0E43E8E47524954 | |||
| 1556 | RtkBtManServ.exe | C:\Users\admin\AppData\Local\Temp\hh.exe | executable | |
MD5:4D4C98ECA32B14AEB074DB34CD0881E4 | SHA256:4182172A01BDFC08C5CF7E8652F7D9D81858345A770E2B6B507840E4C1C7764F | |||
| 3876 | UziClicker.exe | C:\Users\admin\AppData\Local\Temp\config | binary | |
MD5:5CF0B95F68C3304427F858DB1CDDE895 | SHA256:353DE1200B65A2E89E84B32067A908103CCA22AD2E51BA62C171EEF3C25B73AA | |||
| 1556 | RtkBtManServ.exe | C:\Users\admin\AppData\Local\Temp\costura.discord webhook.dll.compressed | binary | |
MD5:F999480EC537EC2126251977CBF8F4E3 | SHA256:84E5C3EAC27895AB23B9F827F9B259F5A1277D4A7F1930D04638FBF47AD4D2CE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
27
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2436 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | crx | 242 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2436 | chrome.exe | 142.250.186.45:443 | accounts.google.com | Google Inc. | US | suspicious |
2436 | chrome.exe | 142.250.185.132:443 | www.google.com | Google Inc. | US | whitelisted |
2436 | chrome.exe | 142.250.185.99:443 | update.googleapis.com | Google Inc. | US | whitelisted |
2436 | chrome.exe | 172.217.18.110:443 | chrome.google.com | Google Inc. | US | whitelisted |
2436 | chrome.exe | 34.104.35.123:80 | edgedl.me.gvt1.com | — | US | whitelisted |
2436 | chrome.exe | 142.250.186.78:443 | consent.google.com | Google Inc. | US | whitelisted |
2436 | chrome.exe | 142.250.186.67:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2436 | chrome.exe | 142.250.185.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2436 | chrome.exe | 172.217.18.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2436 | chrome.exe | 142.250.74.206:443 | play.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.googleusercontent.com |
| whitelisted |
chrome.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
consent.google.com |
| shared |
edgedl.me.gvt1.com |
| whitelisted |