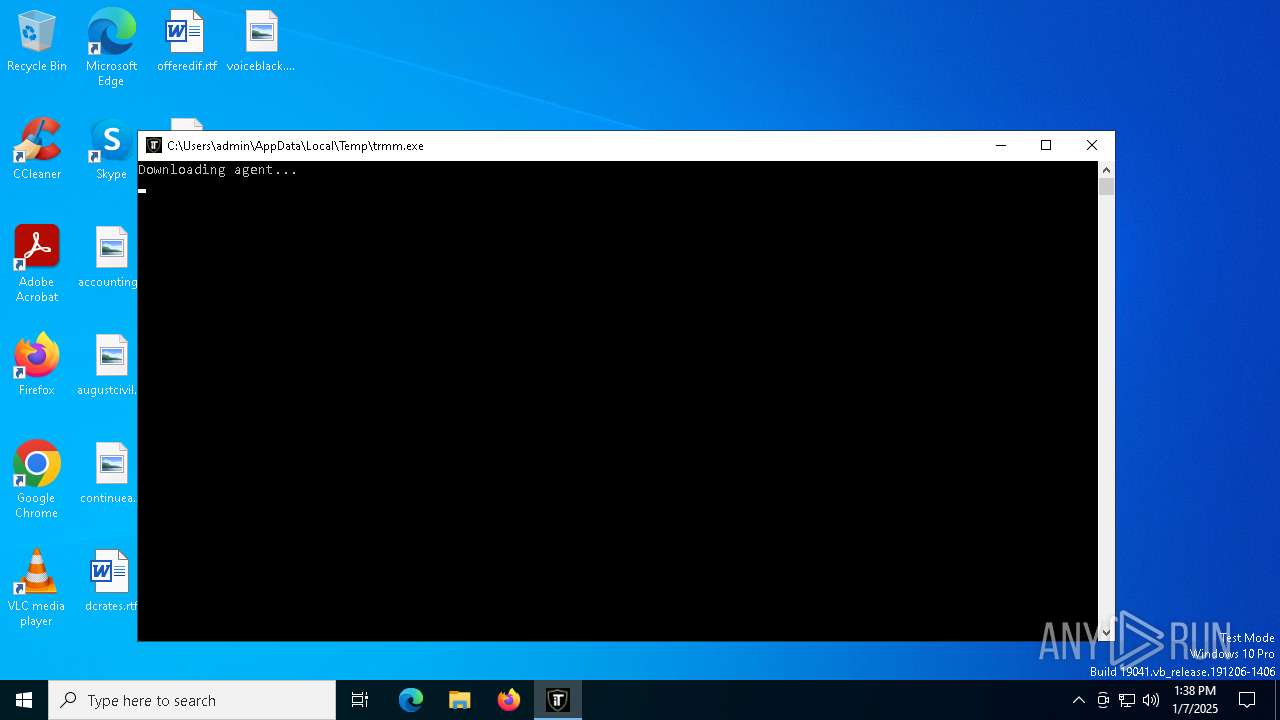
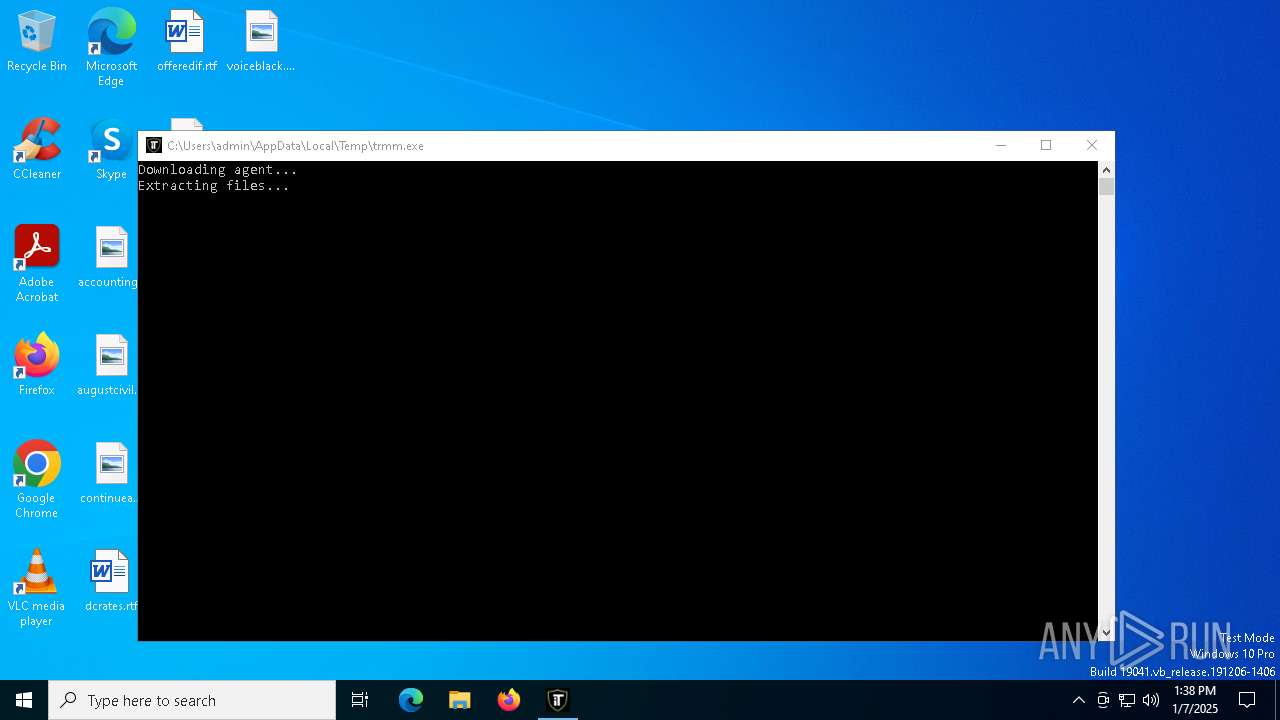
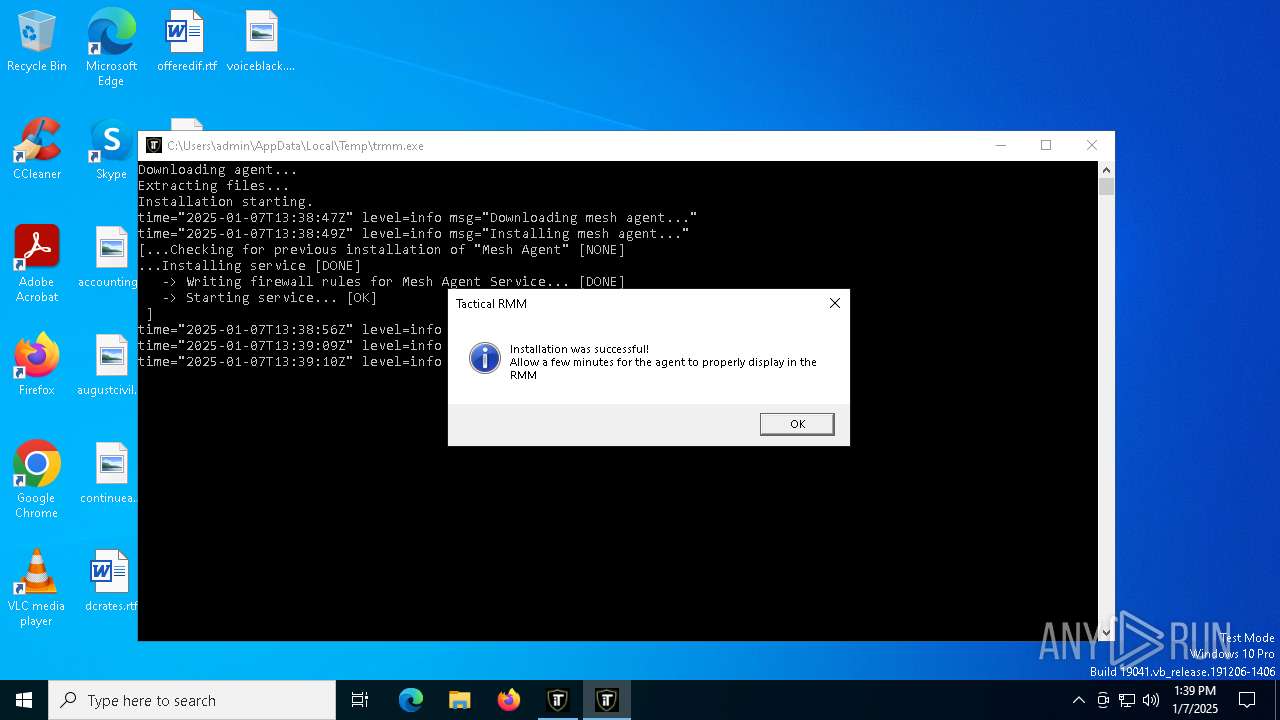
| File name: | trmm.exe |
| Full analysis: | https://app.any.run/tasks/1a3714e1-9fe7-47b1-920d-66f88dd1ddee |
| Verdict: | Malicious activity |
| Analysis date: | January 07, 2025, 13:38:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64 (stripped to external PDB), for MS Windows, 7 sections |
| MD5: | F2EE8BC836244128970BC15750D2CEF2 |
| SHA1: | 743790300F725FACA8AF66BD5E2DC63BE877B940 |
| SHA256: | 227984D93BA945A135C43944D9098737B5B4ACC5E41F2F71D8B63AC3AC0AFAA3 |
| SSDEEP: | 98304:7nz9OgVgXP7aOhce1jIz4ZSCjy1vYQau6q:1 |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 7148)
- net.exe (PID: 7044)
- net.exe (PID: 6280)
- cmd.exe (PID: 6732)
- cmd.exe (PID: 4996)
- net.exe (PID: 6404)
- net.exe (PID: 6908)
- cmd.exe (PID: 6820)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 6964)
SUSPICIOUS
Executable content was dropped or overwritten
- tacticalagent-v2.8.0-windows-amd64.exe (PID: 6692)
- trmm.exe (PID: 6568)
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 6712)
- tacticalrmm.exe (PID: 6776)
- meshagent.exe (PID: 1328)
- tacticalrmm.exe (PID: 6720)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 6732)
- cmd.exe (PID: 4996)
Reads the Windows owner or organization settings
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 6712)
Starts CMD.EXE for commands execution
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 6712)
- MeshAgent.exe (PID: 7148)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4992)
Creates or modifies Windows services
- tacticalrmm.exe (PID: 2996)
Windows service management via SC.EXE
- sc.exe (PID: 5540)
- sc.exe (PID: 4932)
Executes as Windows Service
- MeshAgent.exe (PID: 7148)
- tacticalrmm.exe (PID: 6720)
Uses WMIC.EXE to obtain system information
- MeshAgent.exe (PID: 7148)
Uses WMIC.EXE to obtain operating system information
- MeshAgent.exe (PID: 7148)
Uses WMIC.EXE to obtain computer system information
- MeshAgent.exe (PID: 7148)
Starts POWERSHELL.EXE for commands execution
- MeshAgent.exe (PID: 7148)
The process hides Powershell's copyright startup banner
- MeshAgent.exe (PID: 7148)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6964)
The process bypasses the loading of PowerShell profile settings
- MeshAgent.exe (PID: 7148)
Process drops legitimate windows executable
- tacticalrmm.exe (PID: 6720)
Application launched itself
- tacticalrmm.exe (PID: 6720)
Process drops python dynamic module
- tacticalrmm.exe (PID: 6720)
INFO
Creates files in the program directory
- trmm.exe (PID: 6568)
- meshagent.exe (PID: 1328)
- MeshAgent.exe (PID: 7148)
- tacticalrmm.exe (PID: 6776)
Checks supported languages
- tacticalagent-v2.8.0-windows-amd64.exe (PID: 6692)
- trmm.exe (PID: 6568)
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 6712)
- tacticalrmm.exe (PID: 6776)
- tacticalrmm.exe (PID: 2996)
- meshagent.exe (PID: 1328)
Create files in a temporary directory
- tacticalagent-v2.8.0-windows-amd64.exe (PID: 6692)
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 6712)
Reads the computer name
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 6712)
- tacticalrmm.exe (PID: 2996)
- meshagent.exe (PID: 1328)
The sample compiled with english language support
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 6712)
- tacticalrmm.exe (PID: 6776)
- meshagent.exe (PID: 1328)
- tacticalrmm.exe (PID: 6720)
- trmm.exe (PID: 6568)
Creates a software uninstall entry
- tacticalagent-v2.8.0-windows-amd64.tmp (PID: 6712)
Reads Environment values
- tacticalrmm.exe (PID: 2996)
- tacticalrmm.exe (PID: 6776)
Reads the machine GUID from the registry
- tacticalrmm.exe (PID: 2996)
- tacticalrmm.exe (PID: 6776)
Reads product name
- tacticalrmm.exe (PID: 2996)
- tacticalrmm.exe (PID: 6776)
Application based on Golang
- trmm.exe (PID: 6568)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6932)
The process uses the downloaded file
- powershell.exe (PID: 6964)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6356)
- powershell.exe (PID: 6060)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4872)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 4872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 2520576 |
| InitializedDataSize: | 246784 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x66fe0 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 2.0.4.0 |
| ProductVersionNumber: | 2.0.4.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | AmidaWare LLC |
| FileDescription: | Tactical RMM Installer |
| FileVersion: | v2.0.4.0 |
| InternalName: | rmm.exe |
| LegalCopyright: | Copyright (c) 2022 AmidaWare LLC |
| OriginalFileName: | installer.go |
| ProductName: | Tactical RMM Installer |
| ProductVersion: | v2.0.4.0 |
Total processes
199
Monitored processes
65
Malicious processes
5
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | wmic os get oslanguage /FORMAT:LIST | C:\Windows\System32\wbem\WMIC.exe | — | MeshAgent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | "C:\Program Files\TacticalAgent\meshagent.exe" -fullinstall | C:\Program Files\TacticalAgent\meshagent.exe | tacticalrmm.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: MeshCentral Background Service Agent Exit code: 0 Version: 2022-Dec-2 11:42:16-0800 Modules
| |||||||||||||||
| 1544 | C:\WINDOWS\system32\net1 stop tacticalagent | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1752 | "C:\Program Files\Mesh Agent\MeshAgent.exe" -nodeid | C:\Program Files\Mesh Agent\MeshAgent.exe | — | tacticalrmm.exe | |||||||||||
User: admin Integrity Level: HIGH Description: MeshCentral Background Service Agent Exit code: 0 Version: 2022-Dec-2 11:42:16-0800 Modules
| |||||||||||||||
| 2992 | /c manage-bde -protectors -get C: -Type recoverypassword | C:\Windows\System32\cmd.exe | — | MeshAgent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2996 | tacticalrmm.exe -m installsvc | C:\Program Files\TacticalAgent\tacticalrmm.exe | — | cmd.exe | |||||||||||
User: admin Company: AmidaWare Inc Integrity Level: HIGH Description: Tactical RMM Agent Exit code: 0 Version: v2.8.0.0 Modules
| |||||||||||||||
| 2996 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3280 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3532 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
49 077
Read events
49 010
Write events
61
Delete events
6
Modification events
| (PID) Process: | (6568) trmm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | D1CBCA5DB2D52A7F693B674DE5F05A1D0C957DF0 |
Value: | |||
| (PID) Process: | (6568) trmm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D1CBCA5DB2D52A7F693B674DE5F05A1D0C957DF0 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000FA68BCD9B57FADFDC91D068328CC24C11400000001000000140000003AE10986D4CF19C29676744976DCE035C663639A6200000001000000200000004FF460D54B9C86DABFBCFC5712E0400D2BED3FBC4D4FBDAA86E06ADCD2A9AD7A090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F00000001000000300000000B043572C899DEC43EFD590CFCE610CF443A6315925EBFE589F7506907E44824608489581C7CA0E041458514CF157614030000000100000014000000D1CBCA5DB2D52A7F693B674DE5F05A1D0C957DF019000000010000001000000076935B5C5A037216DAAF8AAC76DF42C153000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C00B00000001000000180000005300650063007400690067006F00200045004300430000001D0000000100000010000000280CF6042C30A2646644BA7286A3AA972000000001000000930200003082028F30820215A00302010202105C8B99C55A94C5D27156DECD8980CC26300A06082A8648CE3D040303308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374204543432043657274696669636174696F6E20417574686F72697479301E170D3130303230313030303030305A170D3338303131383233353935395A308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374204543432043657274696669636174696F6E20417574686F726974793076301006072A8648CE3D020106052B81040022036200041AAC545AA9F96823E77AD5246F53C65AD84BABC6D5B6D1E67371AEDD9CD60C61FDDBA08903B80514EC57CEEE5D3FE221B3CEF7D48A79E0A3837E2D97D061C4F199DC259163AB7F30A3B470E2C7A1339CF3BF2E5C53B15FB37D327F8A34E37979A3423040301D0603551D0E041604143AE10986D4CF19C29676744976DCE035C663639A300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF300A06082A8648CE3D040303036800306502303667A11608DCE49700411D4EBEE16301CF3BAA421164A09D94390211795C7B1DFA64B9EE1642B3BF8AC209C4ECE4B14D023100E92A61478C524A4B4E1870F6D644D66EF583BA6D58BD24D95648EAEFC4A24681886A3A46D1A99B4DC961DAD15D576A18 | |||
| (PID) Process: | (6568) trmm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D1CBCA5DB2D52A7F693B674DE5F05A1D0C957DF0 |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000800100001D0000000100000010000000280CF6042C30A2646644BA7286A3AA970B00000001000000180000005300650063007400690067006F002000450043004300000053000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C019000000010000001000000076935B5C5A037216DAAF8AAC76DF42C1030000000100000014000000D1CBCA5DB2D52A7F693B674DE5F05A1D0C957DF00F00000001000000300000000B043572C899DEC43EFD590CFCE610CF443A6315925EBFE589F7506907E44824608489581C7CA0E041458514CF157614090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703086200000001000000200000004FF460D54B9C86DABFBCFC5712E0400D2BED3FBC4D4FBDAA86E06ADCD2A9AD7A1400000001000000140000003AE10986D4CF19C29676744976DCE035C663639A040000000100000010000000FA68BCD9B57FADFDC91D068328CC24C12000000001000000930200003082028F30820215A00302010202105C8B99C55A94C5D27156DECD8980CC26300A06082A8648CE3D040303308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374204543432043657274696669636174696F6E20417574686F72697479301E170D3130303230313030303030305A170D3338303131383233353935395A308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374204543432043657274696669636174696F6E20417574686F726974793076301006072A8648CE3D020106052B81040022036200041AAC545AA9F96823E77AD5246F53C65AD84BABC6D5B6D1E67371AEDD9CD60C61FDDBA08903B80514EC57CEEE5D3FE221B3CEF7D48A79E0A3837E2D97D061C4F199DC259163AB7F30A3B470E2C7A1339CF3BF2E5C53B15FB37D327F8A34E37979A3423040301D0603551D0E041604143AE10986D4CF19C29676744976DCE035C663639A300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF300A06082A8648CE3D040303036800306502303667A11608DCE49700411D4EBEE16301CF3BAA421164A09D94390211795C7B1DFA64B9EE1642B3BF8AC209C4ECE4B14D023100E92A61478C524A4B4E1870F6D644D66EF583BA6D58BD24D95648EAEFC4A24681886A3A46D1A99B4DC961DAD15D576A18 | |||
| (PID) Process: | (6568) trmm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | D1EB23A46D17D68FD92564C2F1F1601764D8E349 |
Value: | |||
| (PID) Process: | (6568) trmm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D1EB23A46D17D68FD92564C2F1F1601764D8E349 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000497904B0EB8719AC47B0BC11519B74D0140000000100000014000000A0110A233E96F107ECE2AF29EF82A57FD030A4B4620000000100000020000000D7A7A0FB5D7E2731D771E9484EBCDEF71D5F0C3E0A2948782BC83EE0EA699EF4090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F00000001000000140000003E8E6487F8FD27D322A269A71EDAAC5D57811286030000000100000014000000D1EB23A46D17D68FD92564C2F1F1601764D8E3491900000001000000100000002AA1C05E2AE606F198C2C5E937C97AA253000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C00B000000010000001C0000005300650063007400690067006F0020002800410041004100290000001D00000001000000100000002E0D6875874A44C820912E85E964CFDB200000000100000036040000308204323082031AA003020102020101300D06092A864886F70D0101050500307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C18414141204365727469666963617465205365727669636573301E170D3034303130313030303030305A170D3238313233313233353935395A307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C1841414120436572746966696361746520536572766963657330820122300D06092A864886F70D01010105000382010F003082010A0282010100BE409DF46EE1EA76871C4D45448EBE46C883069DC12AFE181F8EE402FAF3AB5D508A16310B9A06D0C57022CD492D5463CCB66E68460B53EACB4C24C0BC724EEAF115AEF4549A120AC37AB23360E2DA8955F32258F3DEDCCFEF8386A28C944F9F68F29890468427C776BFE3CC352C8B5E07646582C048B0A891F9619F762050A891C766B5EB78620356F08A1A13EA31A31EA099FD38F6F62732586F07F56BB8FB142BAFB7AACCD6635F738CDA0599A838A8CB17783651ACE99EF4783A8DCF0FD942E2980CAB2F9F0E01DEEF9F9949F12DDFAC744D1B98B547C5E529D1F99018C7629CBE83C7267B3E8A25C7C0DD9DE6356810209D8FD8DED2C3849C0D5EE82FC90203010001A381C03081BD301D0603551D0E04160414A0110A233E96F107ECE2AF29EF82A57FD030A4B4300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF307B0603551D1F047430723038A036A0348632687474703A2F2F63726C2E636F6D6F646F63612E636F6D2F414141436572746966696361746553657276696365732E63726C3036A034A0328630687474703A2F2F63726C2E636F6D6F646F2E6E65742F414141436572746966696361746553657276696365732E63726C300D06092A864886F70D010105050003820101000856FC02F09BE8FFA4FAD67BC64480CE4FC4C5F60058CCA6B6BC1449680476E8E6EE5DEC020F60D68D50184F264E01E3E6B0A5EEBFBC745441BFFDFC12B8C74F5AF48960057F60B7054AF3F6F1C2BFC4B97486B62D7D6BCCD2F346DD2FC6E06AC3C334032C7D96DD5AC20EA70A99C1058BAB0C2FF35C3ACF6C37550987DE53406C58EFFCB6AB656E04F61BDC3CE05A15C69ED9F15948302165036CECE92173EC9B03A1E037ADA015188FFABA02CEA72CA910132CD4E50826AB229760F8905E74D4A29A53BDF2A968E0A26EC2D76CB1A30F9EBFEB68E756F2AEF2E32B383A0981B56B85D7BE2DED3F1AB7B263E2F5622C82D46A004150F139839F95E93696986E | |||
| (PID) Process: | (6568) trmm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D1EB23A46D17D68FD92564C2F1F1601764D8E349 |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000000800001D00000001000000100000002E0D6875874A44C820912E85E964CFDB0B000000010000001C0000005300650063007400690067006F00200028004100410041002900000053000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C01900000001000000100000002AA1C05E2AE606F198C2C5E937C97AA2030000000100000014000000D1EB23A46D17D68FD92564C2F1F1601764D8E3490F00000001000000140000003E8E6487F8FD27D322A269A71EDAAC5D57811286090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B06010505070308620000000100000020000000D7A7A0FB5D7E2731D771E9484EBCDEF71D5F0C3E0A2948782BC83EE0EA699EF4140000000100000014000000A0110A233E96F107ECE2AF29EF82A57FD030A4B4040000000100000010000000497904B0EB8719AC47B0BC11519B74D0200000000100000036040000308204323082031AA003020102020101300D06092A864886F70D0101050500307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C18414141204365727469666963617465205365727669636573301E170D3034303130313030303030305A170D3238313233313233353935395A307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C1841414120436572746966696361746520536572766963657330820122300D06092A864886F70D01010105000382010F003082010A0282010100BE409DF46EE1EA76871C4D45448EBE46C883069DC12AFE181F8EE402FAF3AB5D508A16310B9A06D0C57022CD492D5463CCB66E68460B53EACB4C24C0BC724EEAF115AEF4549A120AC37AB23360E2DA8955F32258F3DEDCCFEF8386A28C944F9F68F29890468427C776BFE3CC352C8B5E07646582C048B0A891F9619F762050A891C766B5EB78620356F08A1A13EA31A31EA099FD38F6F62732586F07F56BB8FB142BAFB7AACCD6635F738CDA0599A838A8CB17783651ACE99EF4783A8DCF0FD942E2980CAB2F9F0E01DEEF9F9949F12DDFAC744D1B98B547C5E529D1F99018C7629CBE83C7267B3E8A25C7C0DD9DE6356810209D8FD8DED2C3849C0D5EE82FC90203010001A381C03081BD301D0603551D0E04160414A0110A233E96F107ECE2AF29EF82A57FD030A4B4300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF307B0603551D1F047430723038A036A0348632687474703A2F2F63726C2E636F6D6F646F63612E636F6D2F414141436572746966696361746553657276696365732E63726C3036A034A0328630687474703A2F2F63726C2E636F6D6F646F2E6E65742F414141436572746966696361746553657276696365732E63726C300D06092A864886F70D010105050003820101000856FC02F09BE8FFA4FAD67BC64480CE4FC4C5F60058CCA6B6BC1449680476E8E6EE5DEC020F60D68D50184F264E01E3E6B0A5EEBFBC745441BFFDFC12B8C74F5AF48960057F60B7054AF3F6F1C2BFC4B97486B62D7D6BCCD2F346DD2FC6E06AC3C334032C7D96DD5AC20EA70A99C1058BAB0C2FF35C3ACF6C37550987DE53406C58EFFCB6AB656E04F61BDC3CE05A15C69ED9F15948302165036CECE92173EC9B03A1E037ADA015188FFABA02CEA72CA910132CD4E50826AB229760F8905E74D4A29A53BDF2A968E0A26EC2D76CB1A30F9EBFEB68E756F2AEF2E32B383A0981B56B85D7BE2DED3F1AB7B263E2F5622C82D46A004150F139839F95E93696986E | |||
| (PID) Process: | (6712) tacticalagent-v2.8.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.2 | |||
| (PID) Process: | (6712) tacticalagent-v2.8.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\TacticalAgent | |||
| (PID) Process: | (6712) tacticalagent-v2.8.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\TacticalAgent\ | |||
| (PID) Process: | (6712) tacticalagent-v2.8.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: (Default) | |||
Executable files
110
Suspicious files
10
Text files
484
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6568 | trmm.exe | C:\ProgramData\TacticalRMM\tacticalagent-v2.8.0-windows-amd64.exe | executable | |
MD5:ED40540E7432BACAA08A6CD6A9F63004 | SHA256:D6C7BDAB07151678B713A02EFE7AD5281B194B0D5B538061BDAFDF2C4CA1FDAA | |||
| 6712 | tacticalagent-v2.8.0-windows-amd64.tmp | C:\Program Files\TacticalAgent\is-11HJ6.tmp | executable | |
MD5:5E81857286E2795352225BE245FBD62B | SHA256:2624C22DA19E89717DCD522D22B21849A1C3F0EB781333DF85BE5FCD57597278 | |||
| 6712 | tacticalagent-v2.8.0-windows-amd64.tmp | C:\Program Files\TacticalAgent\tacticalrmm.exe | executable | |
MD5:6CFBD2DA5F304A3B8972EAFE6FE4D191 | SHA256:AD29D4E9E01870FFBDB6F2498E6CE36A708E56DB2AD431BA2D80BF5A6CAAC069 | |||
| 6692 | tacticalagent-v2.8.0-windows-amd64.exe | C:\Users\admin\AppData\Local\Temp\is-7M9KA.tmp\tacticalagent-v2.8.0-windows-amd64.tmp | executable | |
MD5:A639312111D278FEE4F70299C134D620 | SHA256:4B0BE5167A31A77E28E3F0A7C83C9D289845075B51E70691236603B1083649DF | |||
| 6712 | tacticalagent-v2.8.0-windows-amd64.tmp | C:\Users\admin\AppData\Local\Temp\is-V0L9B.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6712 | tacticalagent-v2.8.0-windows-amd64.tmp | C:\Program Files\TacticalAgent\unins000.exe | executable | |
MD5:5E81857286E2795352225BE245FBD62B | SHA256:2624C22DA19E89717DCD522D22B21849A1C3F0EB781333DF85BE5FCD57597278 | |||
| 6712 | tacticalagent-v2.8.0-windows-amd64.tmp | C:\Program Files\TacticalAgent\unins000.dat | binary | |
MD5:2EA9959173810F8DF204C3DCA58552A2 | SHA256:6C629FF90E5E893D14A18C2598ED590A96D0ED67A3F601E271165BC507F5ADF6 | |||
| 6712 | tacticalagent-v2.8.0-windows-amd64.tmp | C:\Program Files\TacticalAgent\is-NJFUJ.tmp | executable | |
MD5:6CFBD2DA5F304A3B8972EAFE6FE4D191 | SHA256:AD29D4E9E01870FFBDB6F2498E6CE36A708E56DB2AD431BA2D80BF5A6CAAC069 | |||
| 1328 | meshagent.exe | C:\Program Files\Mesh Agent\MeshAgent.exe | executable | |
MD5:7450D1FC59FF95B1763698ABF88CA6EF | SHA256:F5BDCB4432E1058CF9316F81FC80561C95539D7AB4254C1E46E48B29CB1D33FF | |||
| 7148 | MeshAgent.exe | C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\SystemCertificates\My\Keys\2EE242CBDC658F745B34A27CF5FA9DF167B3B894 | binary | |
MD5:B86A595CBCF58A8B7B5B7D0B84A1C296 | SHA256:C61A99F8D0D2A38C9F14E2A7F4735219C38D8BA8AD7A122FF31E4C496A1275CB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
47
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4244 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7076 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7076 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.21.110.139:443 | — | AKAMAI-AS | DE | unknown |
1176 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6568 | trmm.exe | 140.82.121.4:443 | github.com | GITHUB | US | shared |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6568 | trmm.exe | 185.199.111.133:443 | objects.githubusercontent.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
github.com |
| shared |
go.microsoft.com |
| whitelisted |
objects.githubusercontent.com |
| unknown |
api.rmmlot.ru |
| unknown |