| File name: | Drill_2024.doc |
| Full analysis: | https://app.any.run/tasks/2ca08369-557e-492c-866f-6b9b4ff5658e |
| Verdict: | Malicious activity |
| Analysis date: | July 19, 2024, 17:12:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | CDFV2 Microsoft Word |
| MD5: | 1F0B037CFAD1882478C0075F05BA427D |
| SHA1: | 665F48C9413EE76D667453DB39DC5234B0D92037 |
| SHA256: | 226AD9680E604D4D538FB5E48948F2A72084DA86407A93BF7D4F2C9EFBB2742C |
| SSDEEP: | 3072:8cIfOgeP2J+gCHEg6s93vgbhfXk/Exgr7:NgeoCHEgTcvS97 |
MALICIOUS
The DLL Hijacking
- OfficeClickToRun.exe (PID: 3872)
Unusual execution from MS Office
- WINWORD.EXE (PID: 7316)
- WINWORD.EXE (PID: 5112)
Creates a writable file in the system directory
- OfficeClickToRun.exe (PID: 3872)
Scans artifacts that could help determine the target
- OfficeClickToRun.exe (PID: 3872)
SUSPICIOUS
Executes as Windows Service
- OfficeClickToRun.exe (PID: 3872)
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 5112)
- WINWORD.EXE (PID: 7316)
Reads data from a binary Stream object (SCRIPT)
- WINWORD.EXE (PID: 7316)
- WINWORD.EXE (PID: 5112)
Checks Windows Trust Settings
- OfficeClickToRun.exe (PID: 3872)
INFO
Reads the computer name
- OfficeClickToRun.exe (PID: 3872)
Checks supported languages
- OfficeClickToRun.exe (PID: 3872)
Reads Microsoft Office registry keys
- OfficeClickToRun.exe (PID: 3872)
Reads the machine GUID from the registry
- OfficeClickToRun.exe (PID: 3872)
Checks proxy server information
- OfficeClickToRun.exe (PID: 3872)
Process checks computer location settings
- OfficeClickToRun.exe (PID: 3872)
Manual execution by a user
- WINWORD.EXE (PID: 7316)
- WINWORD.EXE (PID: 5112)
Reads Environment values
- OfficeClickToRun.exe (PID: 3872)
Reads CPU info
- OfficeClickToRun.exe (PID: 3872)
Reads the software policy settings
- OfficeClickToRun.exe (PID: 3872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| CompObjUserTypeLen: | 32 |
|---|---|
| CompObjUserType: | Microsoft Word 97-2003 Document |
| Identification: | Word 8.0 |
| LanguageCode: | English (US) |
| DocFlags: | 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| ModifyDate: | 2024:04:01 14:52:37 |
| CodePage: | Unicode (UTF-8) |
| Company: | home |
| Bytes: | 106496 |
| CharCountWithSpaces: | 141 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
| CreateDate: | 2017:04:18 16:00:00Z |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 67 |
| TotalEditTime: | 4.0 days |
| Words: | 21 |
| Characters: | 121 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
154
Monitored processes
13
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
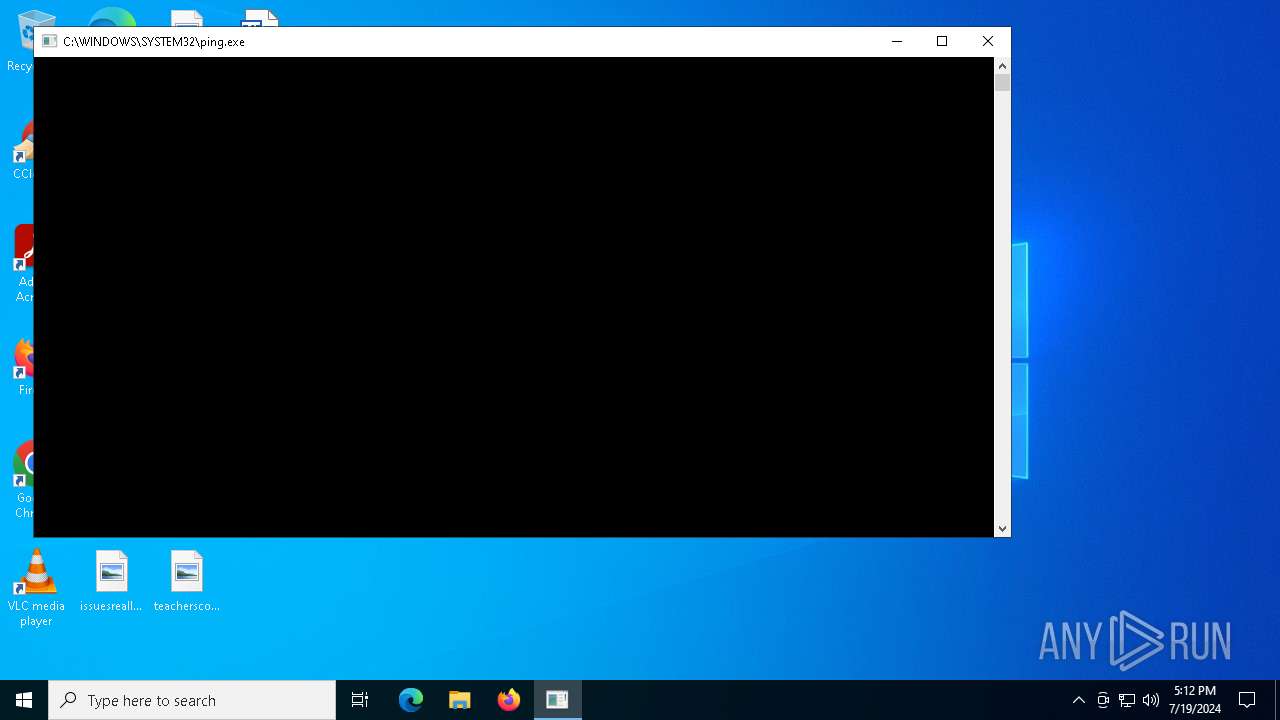
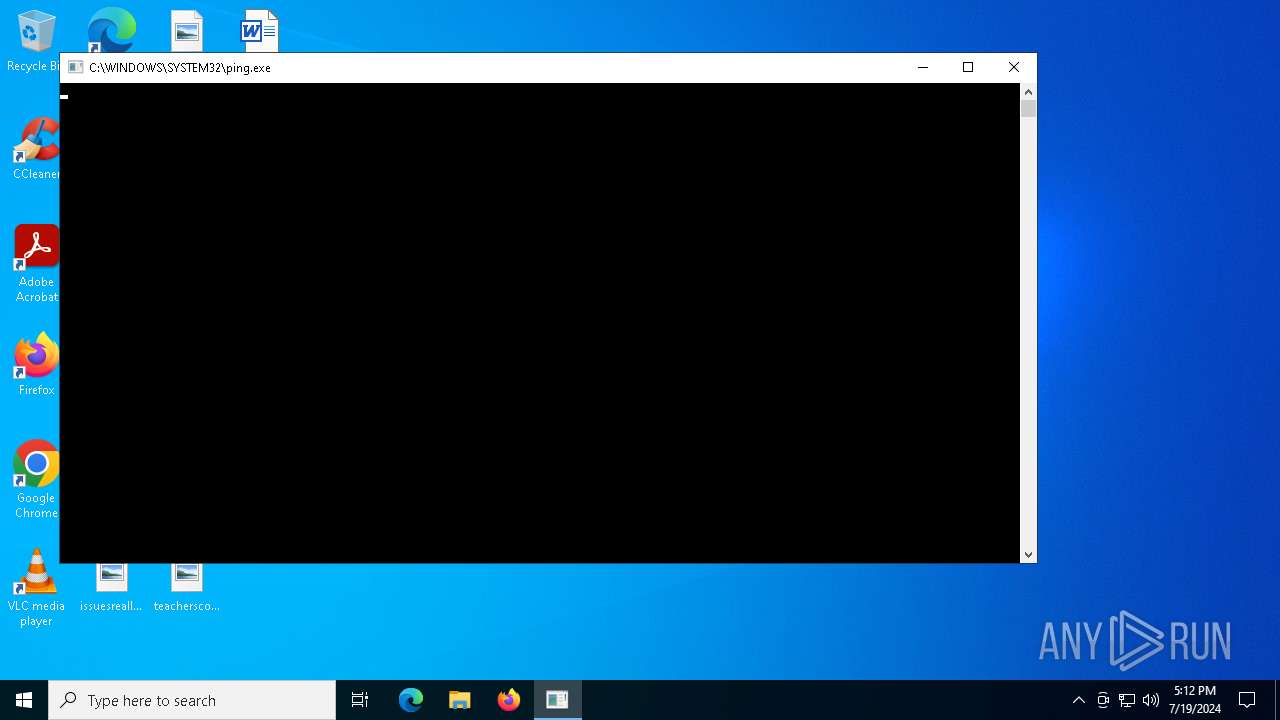
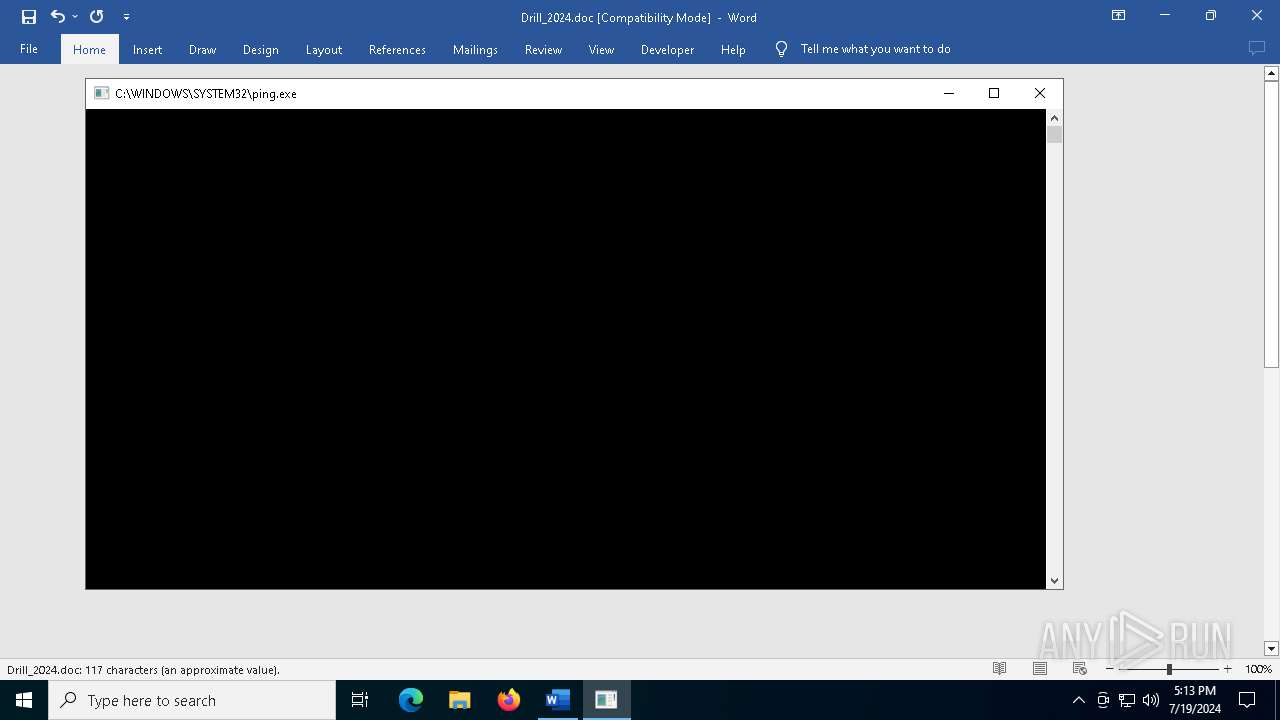
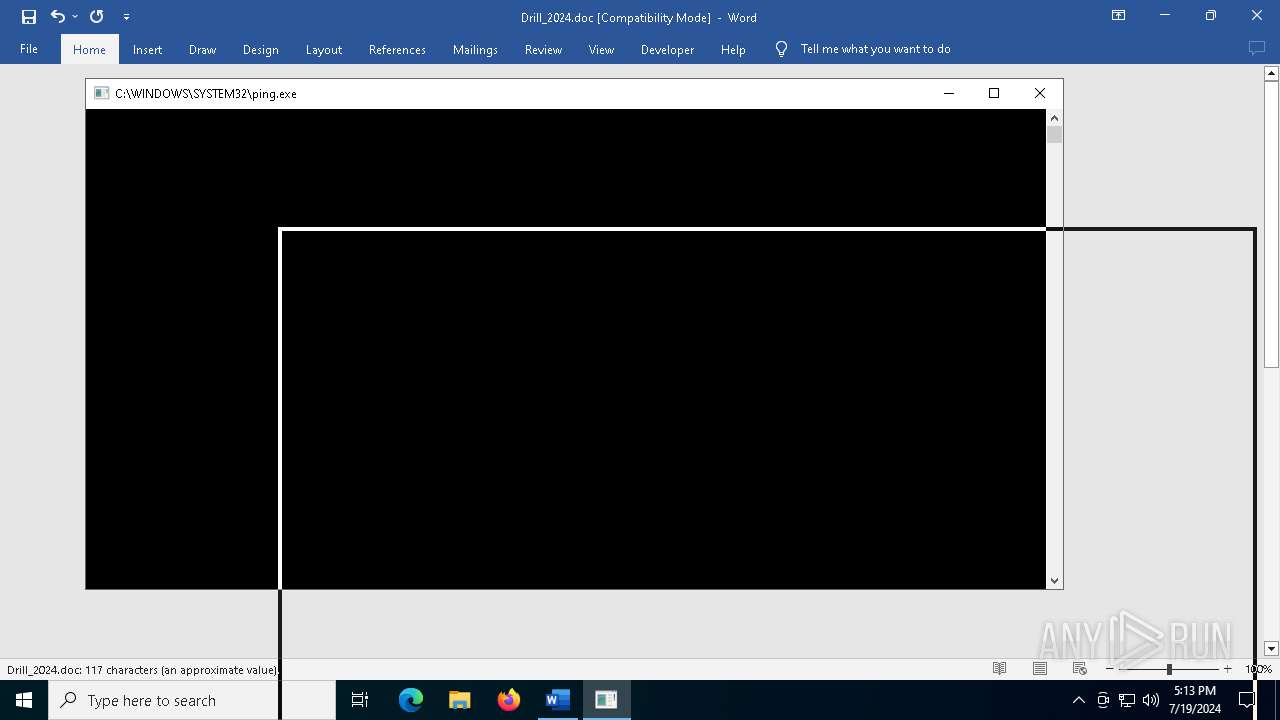
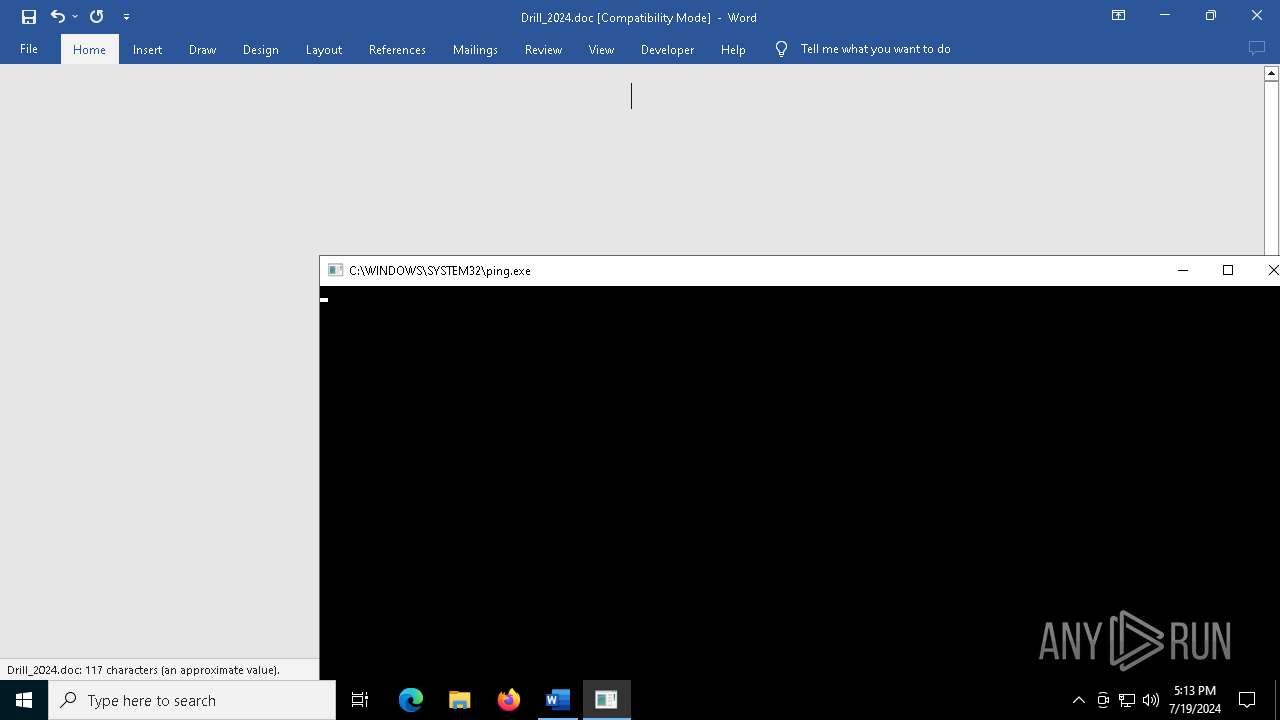
| 2276 | ping -n 1 149.28.22.48 | C:\Windows\System32\PING.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2860 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "DDF2EDC8-E792-4467-8F17-5E8805FCF083" "1CC3C92D-5456-4B85-A9BB-1E5047174832" "5112" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 3872 | "C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeClickToRun.exe" /service | C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeClickToRun.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Office Click-to-Run (SxS) Version: 16.0.16026.20140 Modules
| |||||||||||||||
| 5112 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\Drill_2024.doc" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5716 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PING.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5720 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "908C6737-97F4-4A9A-9561-D3DC8BBC4E87" "E0E60E71-2B43-4625-9F88-27624C9DA6EE" "7316" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 6800 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\Desktop\Drill_2024.doc /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PING.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6968 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6992 | ping -n 1 149.28.22.48 | C:\Windows\System32\PING.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
26 955
Read events
26 181
Write events
727
Delete events
47
Modification events
| (PID) Process: | (3872) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (3872) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 1 | |||
| (PID) Process: | (3872) OfficeClickToRun.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting\RuntimeExceptionHelperModules |
| Operation: | write | Name: | C:\Program Files\Common Files\Microsoft Shared\ClickToRun\c2r64werhandler.dll |
Value: 0 | |||
| (PID) Process: | (3872) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Office\16.0\Common |
| Operation: | write | Name: | SessionId |
Value: 11EE2191D3B2CB4B8D35B2E37235559D | |||
| (PID) Process: | (3872) OfficeClickToRun.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun |
| Operation: | write | Name: | MachineMetadataSentTime |
Value: 13365882767379 | |||
| (PID) Process: | (3872) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3872) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3872) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3872) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (7316) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E01000000000000000500000000000000 | |||
Executable files
1
Suspicious files
46
Text files
9
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6800 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:578BF57BBC5919E5A1401725CB662CAF | SHA256:61AC1D5DDCFF57BF2E76EE6AAD560F256E7134C64BF80EB11A633DDA4C909C1E | |||
| 7316 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:22BB225CA114B763C7BF129706F50F49 | SHA256:BC517C4B438656B547DF4F8078292C353701E209E7E10711D00269A456352159 | |||
| 7316 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:CF00CACB5A8ADE8733F18857556C60D7 | SHA256:FE7360FD811BEC08BB6B83261A905135D280F5F198AA62F825BB1EF9882DE3D3 | |||
| 6800 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Diagnostics\WINWORD\App1721409169445430200_E606C85E-307D-40FA-B80B-11389AB521D9.log | — | |
MD5:— | SHA256:— | |||
| 7316 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | der | |
MD5:620FC0DC450746BABE32BFA9CE1BBD73 | SHA256:BB2C39FA92F6B55791FB33BCC0B1FC1994D9D4184E2A9EB4311950B528A799CA | |||
| 7316 | WINWORD.EXE | C:\Users\admin\Desktop\~$ill_2024.doc | binary | |
MD5:229849B9ED2880644BA2032E91C2E3D9 | SHA256:DEFB0036CA451566EA1BE0BD9041506174AA64370603BEDB321B2B2B0B89EC2A | |||
| 6800 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:02C9DE2C10162A2BC0F666BD2970E40A | SHA256:B5FE885ACC88C0914ABB925178D95AD5CC4D3C782CC54792587D4F7B98FA3F26 | |||
| 7316 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 6800 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\2B786B12-8918-4CDC-A8FD-665A495850FE | xml | |
MD5:53C8F1C9CEC7F76E25C6F6FEE5AE6192 | SHA256:7C8EFE4FE489632648ED4298804FF476F13E5289D0CB7F4C4BB1FD679CDE1E5D | |||
| 7316 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\Drill_2024.doc.LNK | binary | |
MD5:18EFAFFC5FDFE2D58E87E0ADFF351975 | SHA256:52BBB042DF851141311D3C435E3AD66EF6E34A10049FF1CC9BBA793765A187E1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
49
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7316 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5620 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4716 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
— | — | 4.209.32.67:443 | licensing.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2760 | svchost.exe | 40.115.3.253:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2892 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4716 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5620 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
licensing.mp.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |