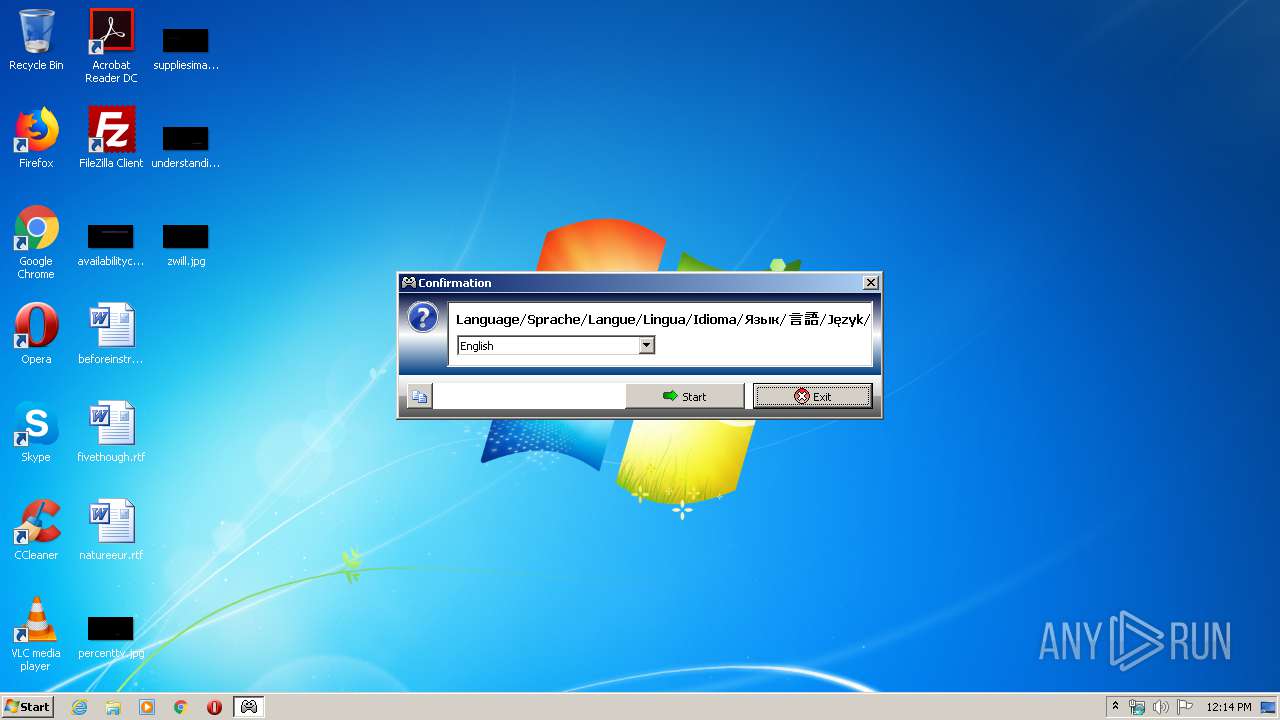
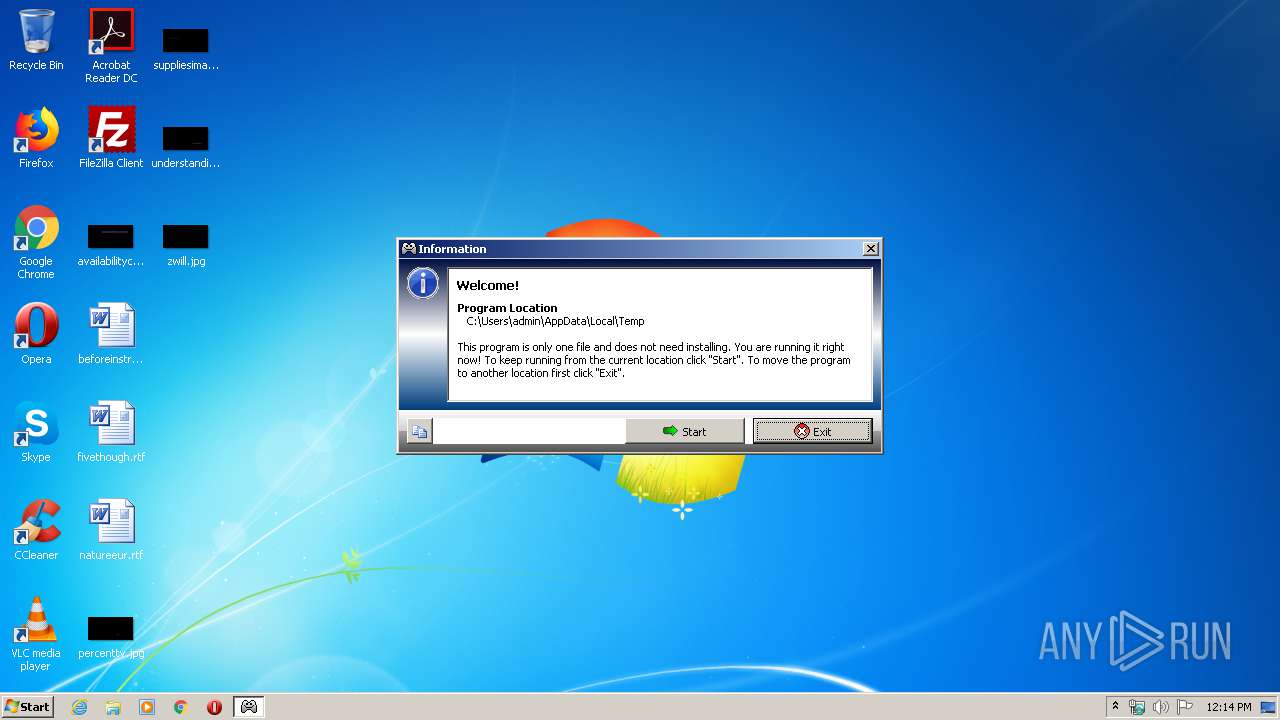
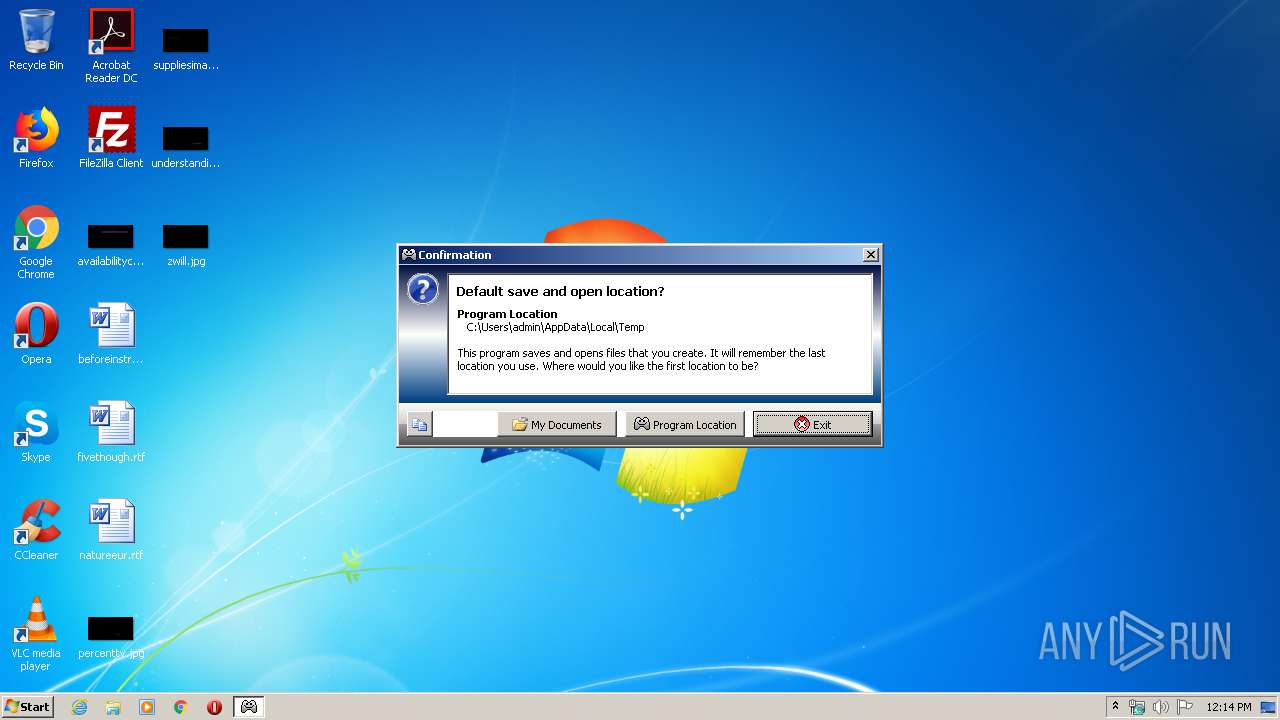
| File name: | Xpadder.exe |
| Full analysis: | https://app.any.run/tasks/f2cbfcb8-8b47-4d42-a59a-559bb8e22997 |
| Verdict: | No threats detected |
| Analysis date: | April 13, 2020, 11:14:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 3A7EF90BEE313058317938103B615138 |
| SHA1: | 60CBA3E7792D6E31AD4FA71182F14CD457DAB384 |
| SHA256: | 226696979497CF86A6917C014D03F4668E0E748D563EDC800D40F0588843634E |
| SSDEEP: | 24576:qqZf8bFzRhCvsr/h1F9rQIjg/q6pCt8lvJ8:cIqzg/I2C |
MALICIOUS
No malicious indicators.SUSPICIOUS
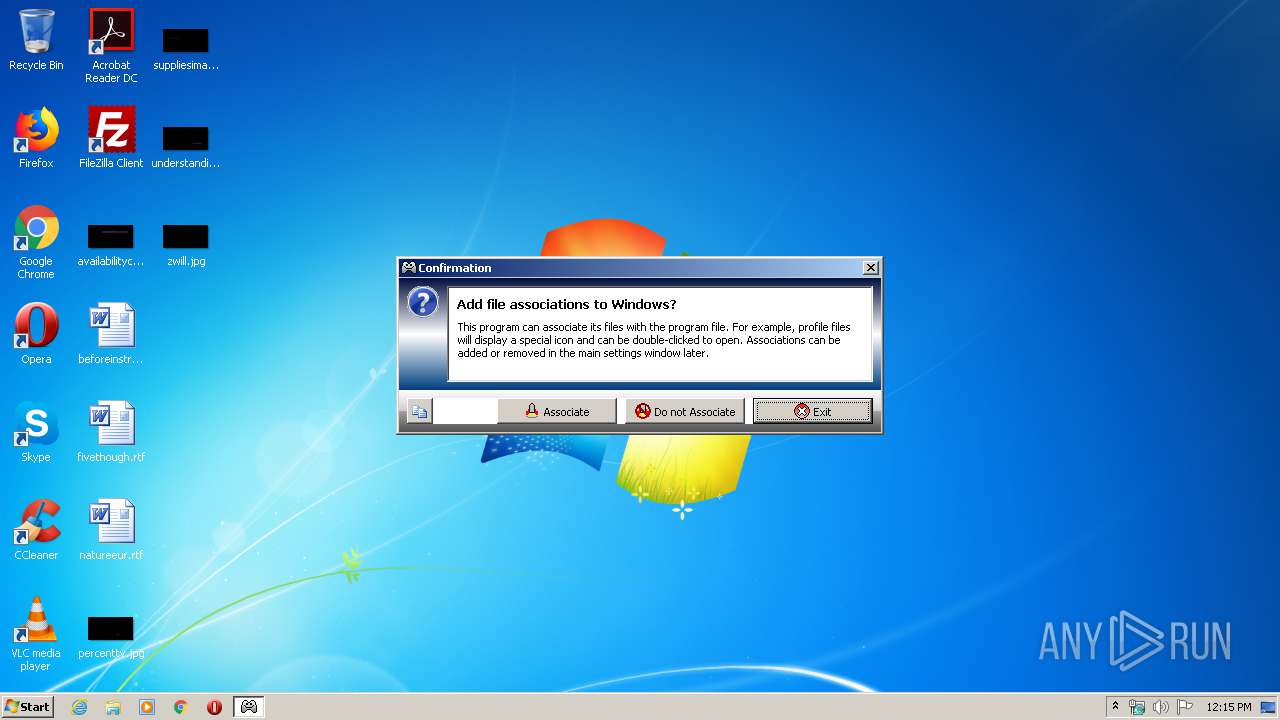
Modifies the open verb of a shell class
- Xpadder.exe (PID: 3836)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (31.9) |
|---|---|---|
| .scr | | | Windows screen saver (29.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (14.8) |
| .exe | | | Win32 Executable (generic) (10.1) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:01:01 14:38:49+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 1045504 |
| InitializedDataSize: | 132096 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x100868 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 01-Jan-2015 13:38:49 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 01-Jan-2015 13:38:49 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000FE8A8 | 0x000FEA00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.60714 |
.itext | 0x00100000 | 0x000008F4 | 0x00000A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.7146 |
.data | 0x00101000 | 0x0000DF30 | 0x0000E000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.58695 |
.bss | 0x0010F000 | 0x0002CB70 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x0013C000 | 0x000033F6 | 0x00003400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.23926 |
.tls | 0x00140000 | 0x0000003C | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x00141000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.170146 |
.rsrc | 0x00142000 | 0x0000EE00 | 0x0000EE00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.42954 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.21471 | 807 | UNKNOWN | English - United Kingdom | RT_MANIFEST |
2 | 2.0815 | 20 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
3 | 2.43138 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 2.56318 | 308 | UNKNOWN | English - United States | RT_CURSOR |
5 | 2.6949 | 308 | UNKNOWN | English - United States | RT_CURSOR |
6 | 2.62527 | 308 | UNKNOWN | English - United States | RT_CURSOR |
7 | 2.91604 | 308 | UNKNOWN | English - United States | RT_CURSOR |
4081 | 2.69141 | 176 | UNKNOWN | UNKNOWN | RT_STRING |
4082 | 3.32854 | 900 | UNKNOWN | UNKNOWN | RT_STRING |
4083 | 3.52913 | 172 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
Psapi.dll |
advapi32.dll |
comctl32.dll |
comdlg32.dll |
gdi32.dll |
kernel32.dll |
msimg32.dll |
ole32.dll |
oleaut32.dll |
psapi.dll |
Total processes
34
Monitored processes
1
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3836 | "C:\Users\admin\AppData\Local\Temp\Xpadder.exe" | C:\Users\admin\AppData\Local\Temp\Xpadder.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
19
Read events
5
Write events
14
Delete events
0
Modification events
| (PID) Process: | (3836) Xpadder.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\DirectInput\XPADDER.EXE54A54DE90011FC00 |
| Operation: | write | Name: | Name |
Value: XPADDER.EXE | |||
| (PID) Process: | (3836) Xpadder.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\DirectInput\XPADDER.EXE54A54DE90011FC00 |
| Operation: | write | Name: | UsesMapper |
Value: 00000000 | |||
| (PID) Process: | (3836) Xpadder.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: XPADDER.EXE | |||
| (PID) Process: | (3836) Xpadder.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Id |
Value: XPADDER.EXE54A54DE90011FC00 | |||
| (PID) Process: | (3836) Xpadder.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Version |
Value: 00080000 | |||
| (PID) Process: | (3836) Xpadder.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | MostRecentStart |
Value: D0C9B7B38411D601 | |||
| (PID) Process: | (3836) Xpadder.exe | Key: | HKEY_CLASSES_ROOT\.xpadderprofile |
| Operation: | write | Name: | |
Value: Xpadder.Profile | |||
| (PID) Process: | (3836) Xpadder.exe | Key: | HKEY_CLASSES_ROOT\Xpadder.Profile |
| Operation: | write | Name: | |
Value: Xpadder Profile | |||
| (PID) Process: | (3836) Xpadder.exe | Key: | HKEY_CLASSES_ROOT\Xpadder.Profile\shell\open\command |
| Operation: | write | Name: | |
Value: "C:\Users\admin\AppData\Local\Temp\Xpadder.exe" "%1" | |||
| (PID) Process: | (3836) Xpadder.exe | Key: | HKEY_CLASSES_ROOT\Xpadder.Profile\DefaultIcon |
| Operation: | write | Name: | |
Value: C:\Users\admin\AppData\Local\Temp\Xpadder.exe,2 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report