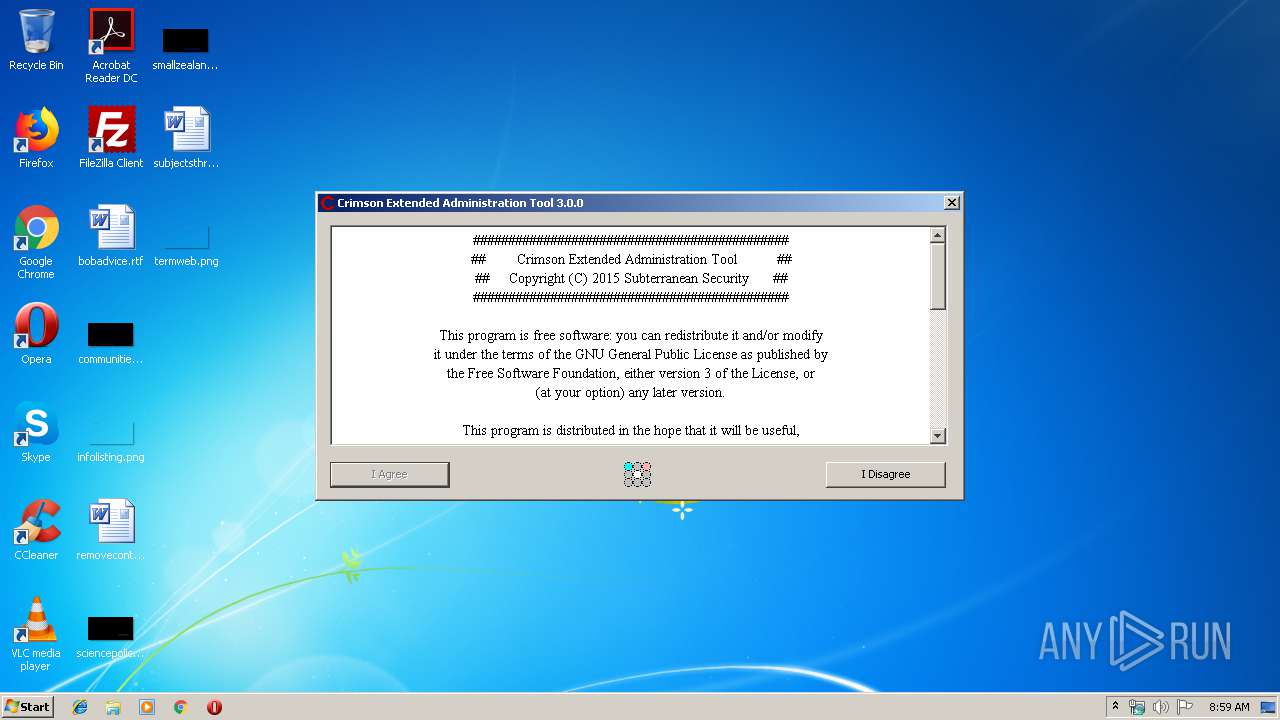
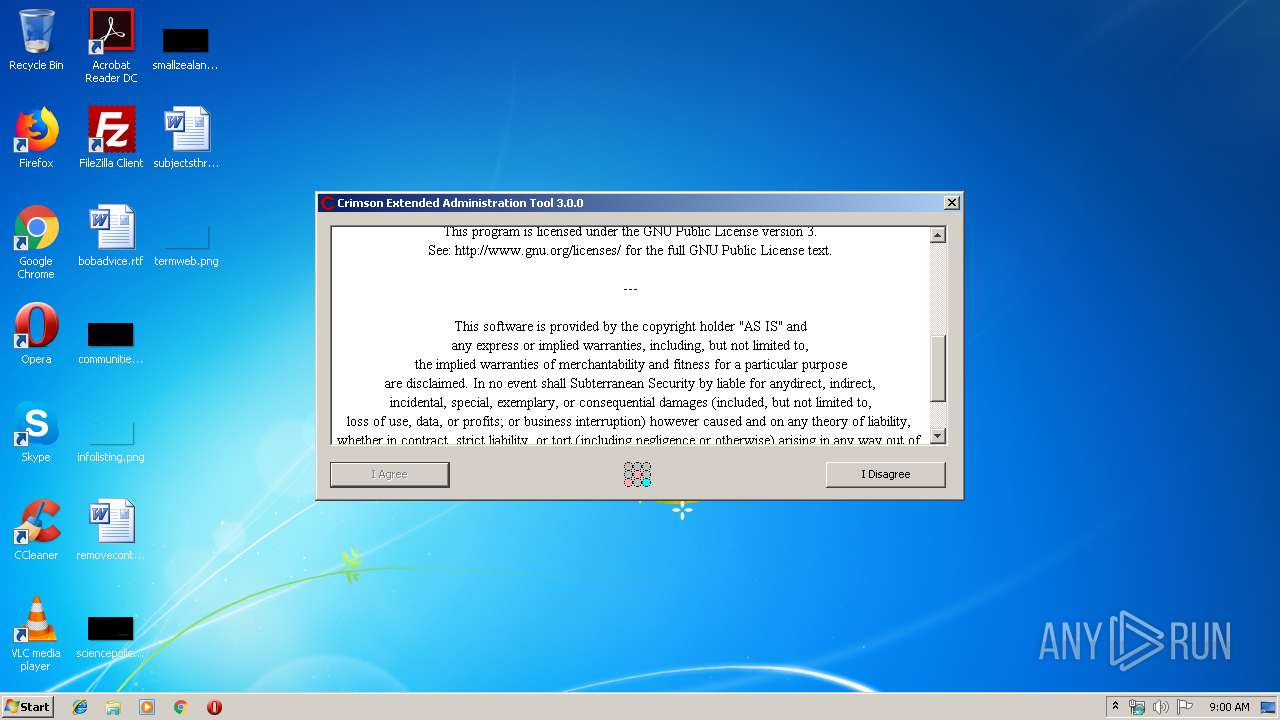
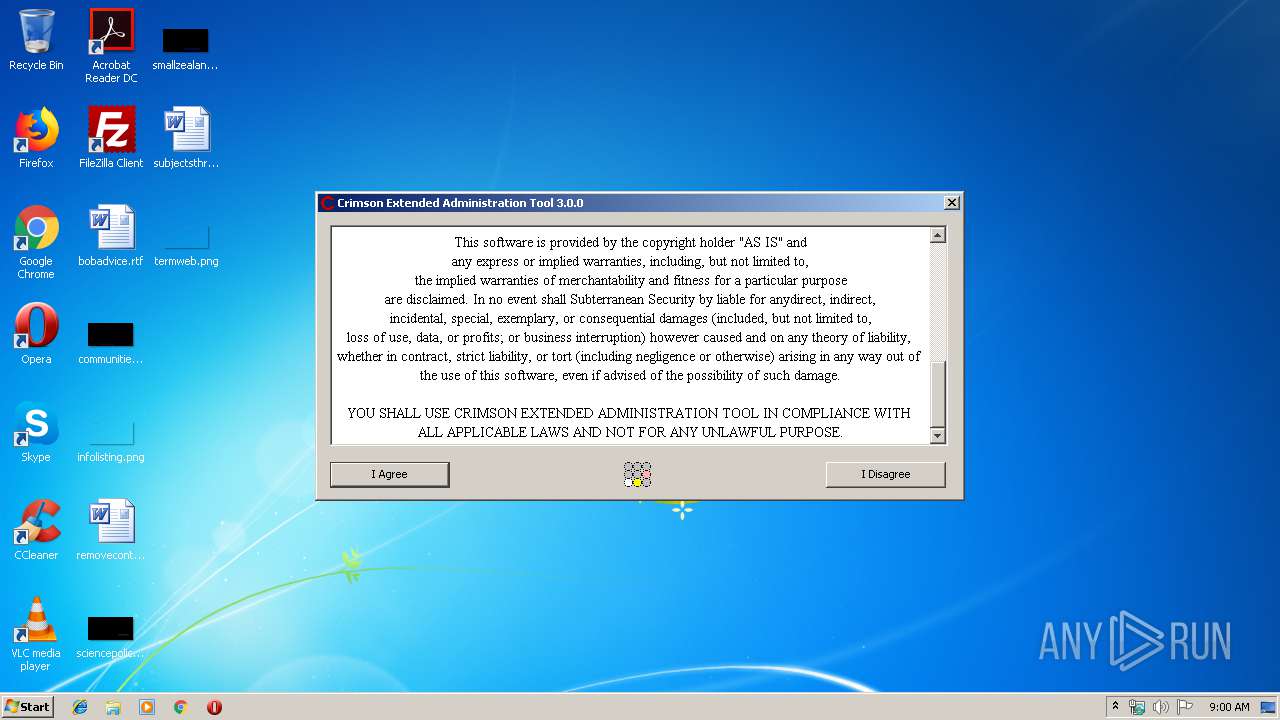
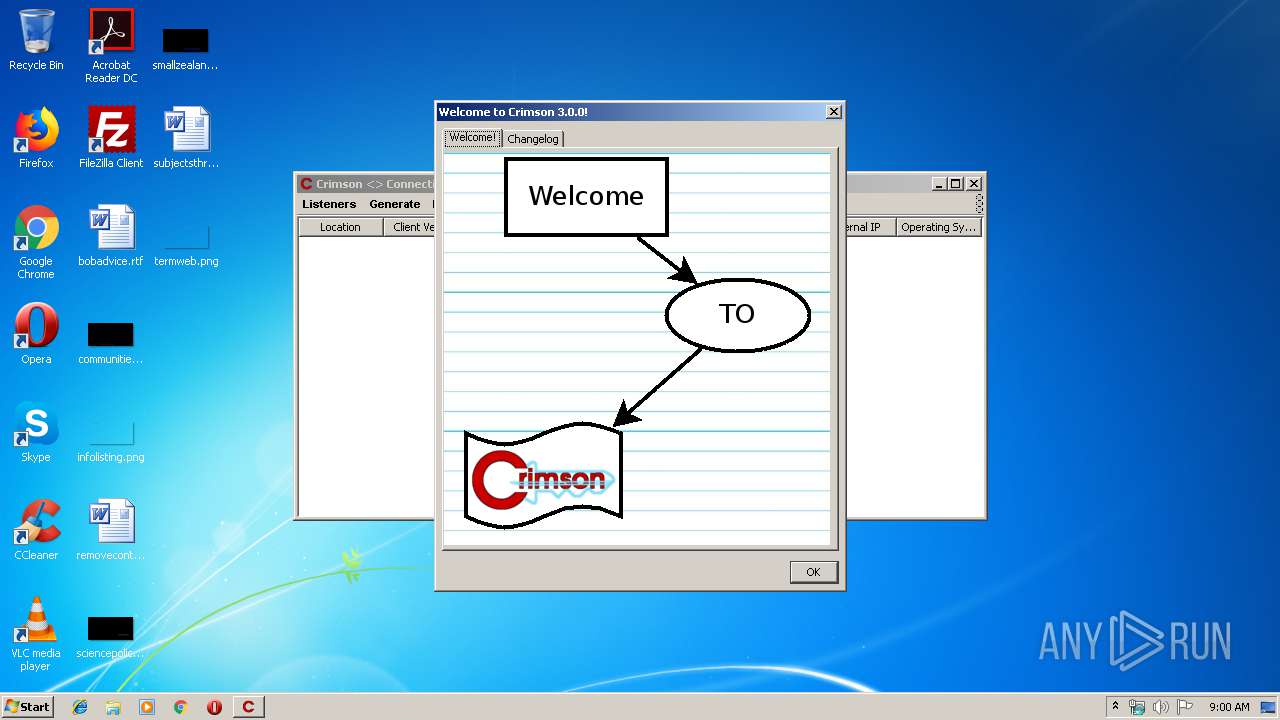
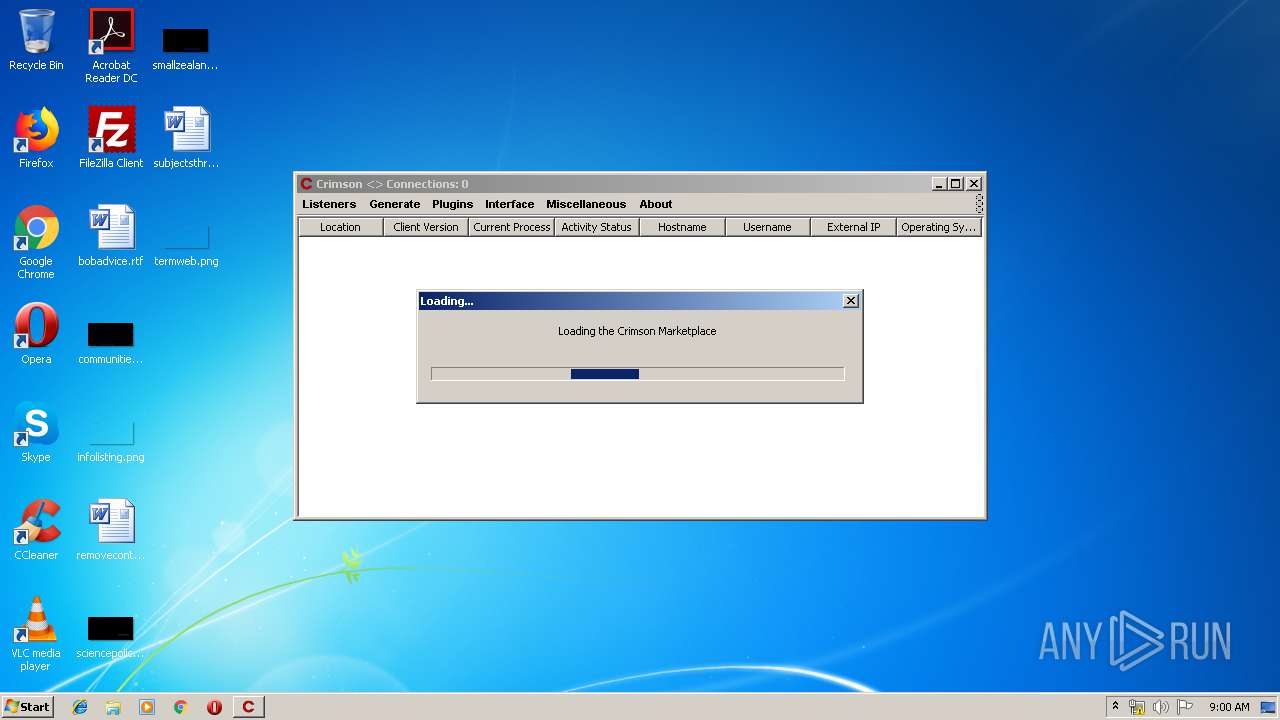
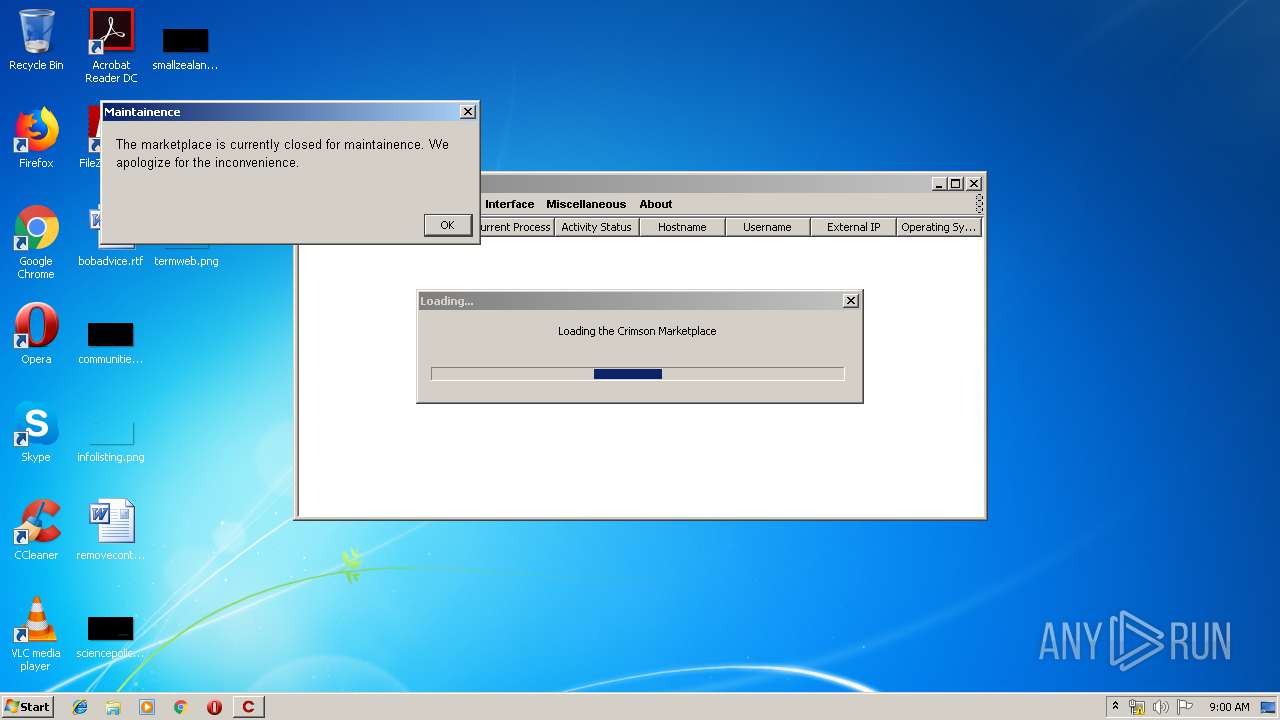
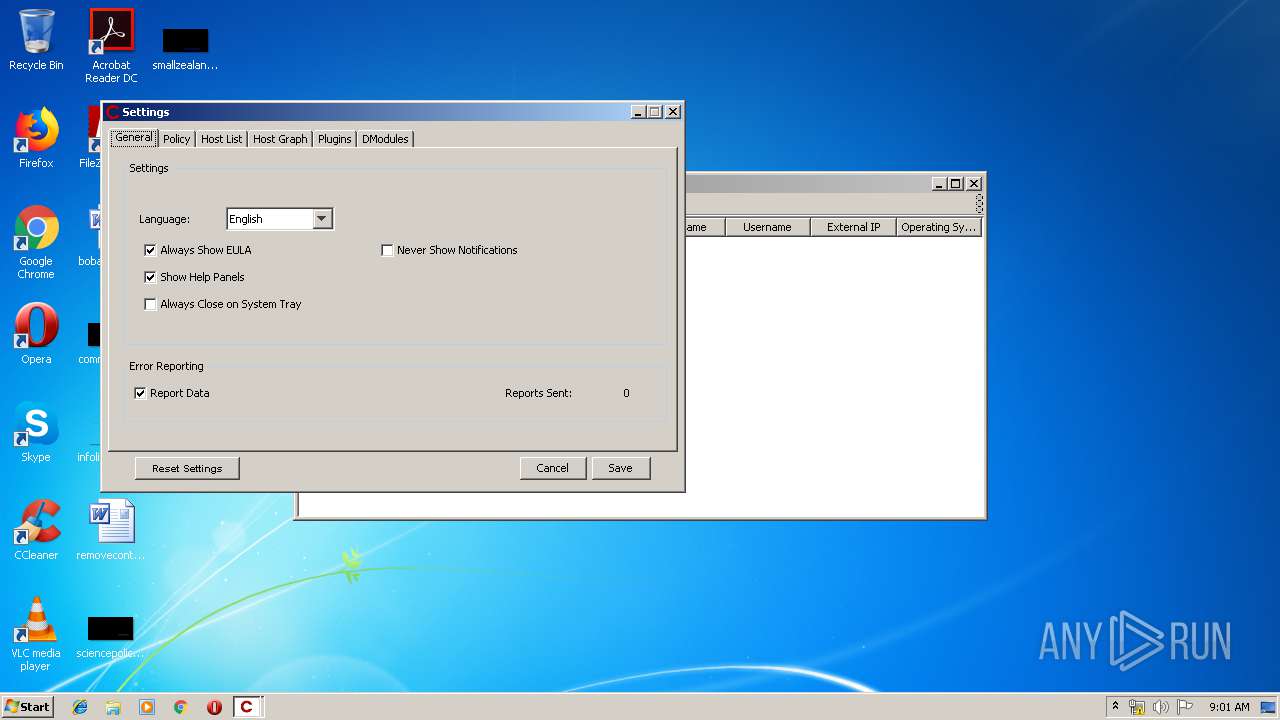
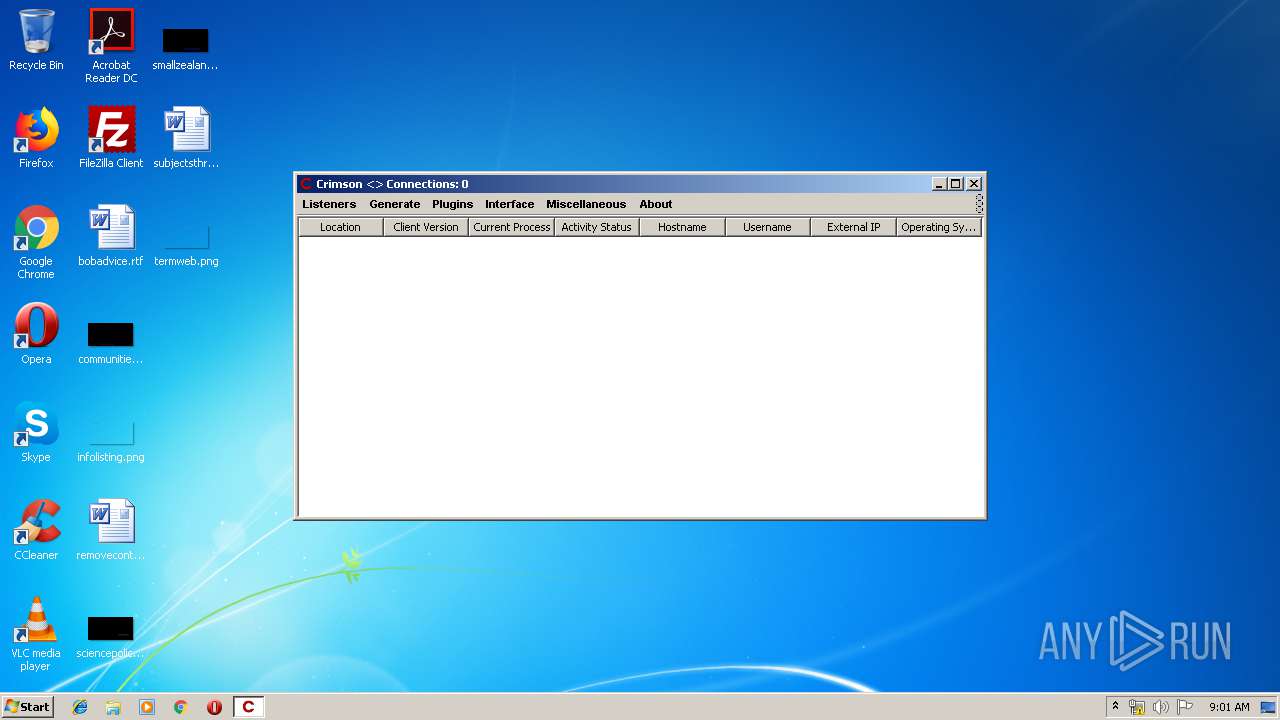
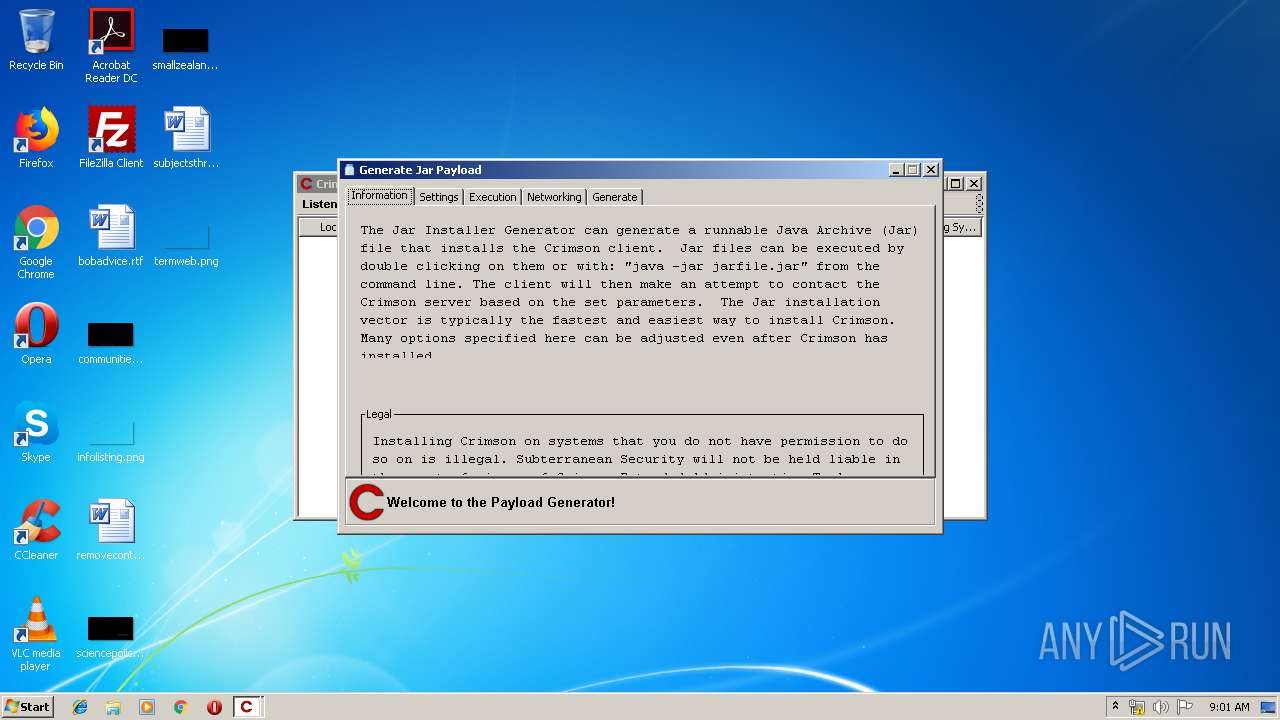
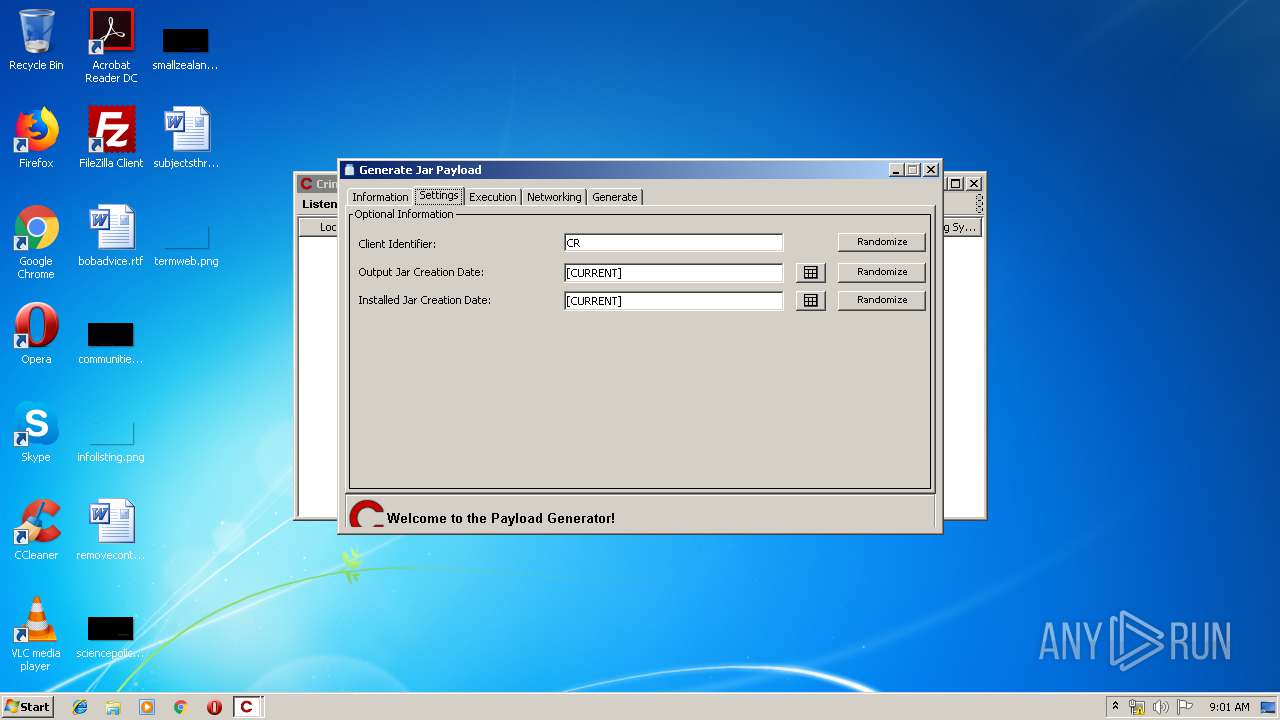
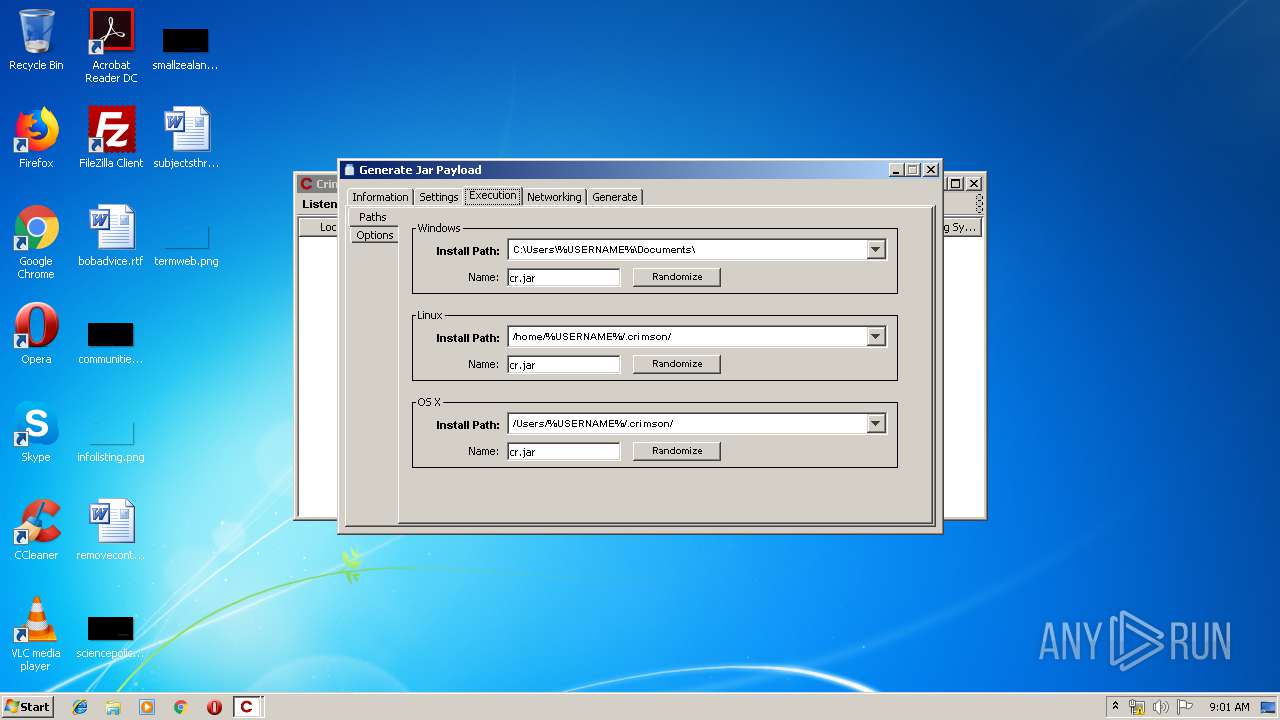
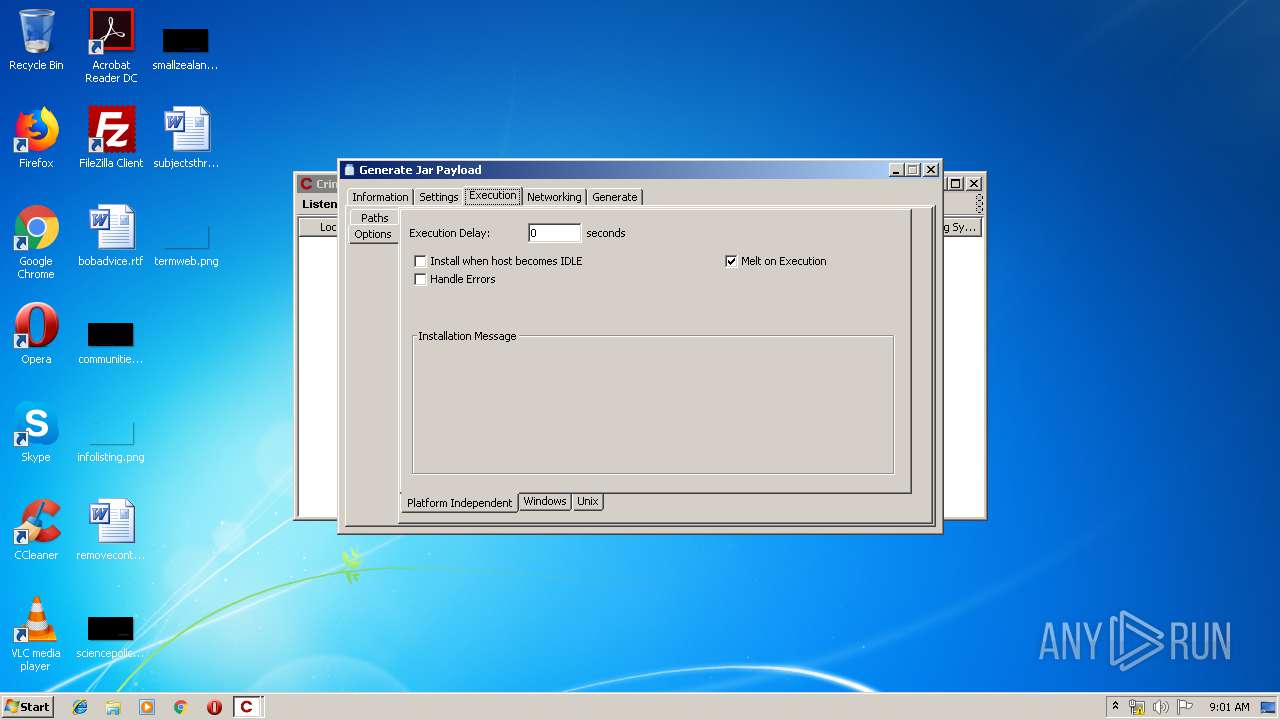
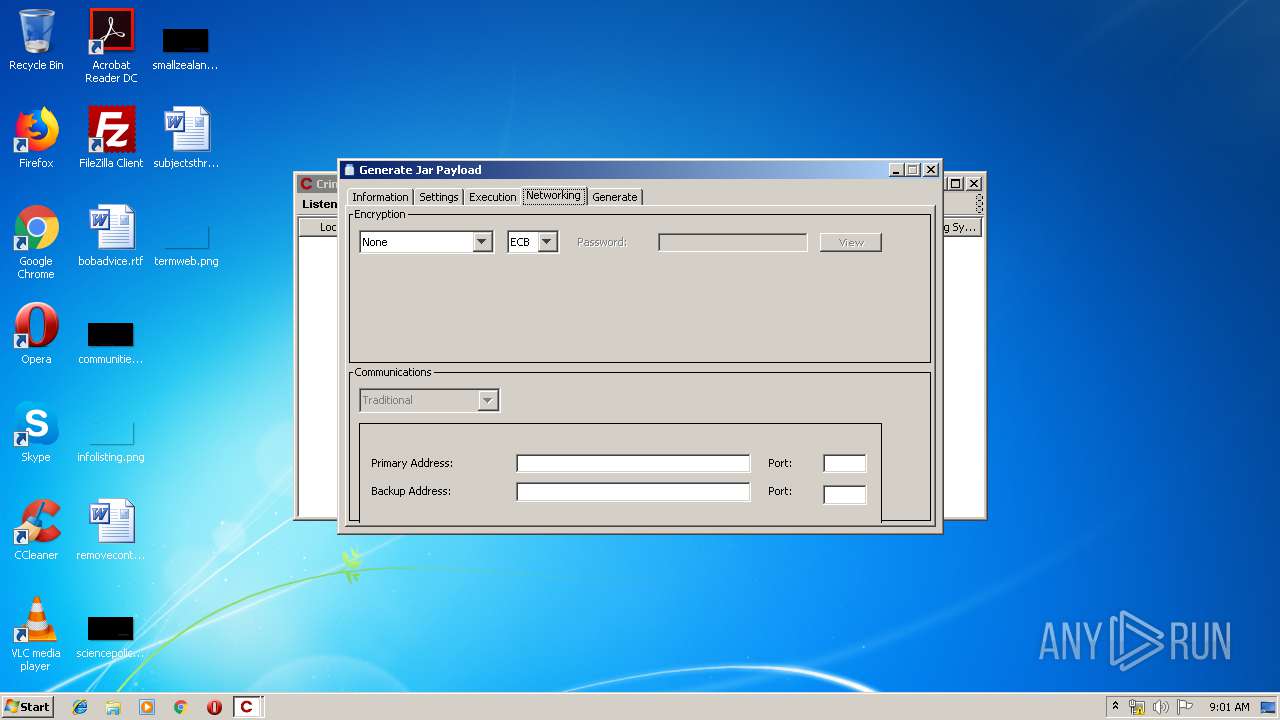
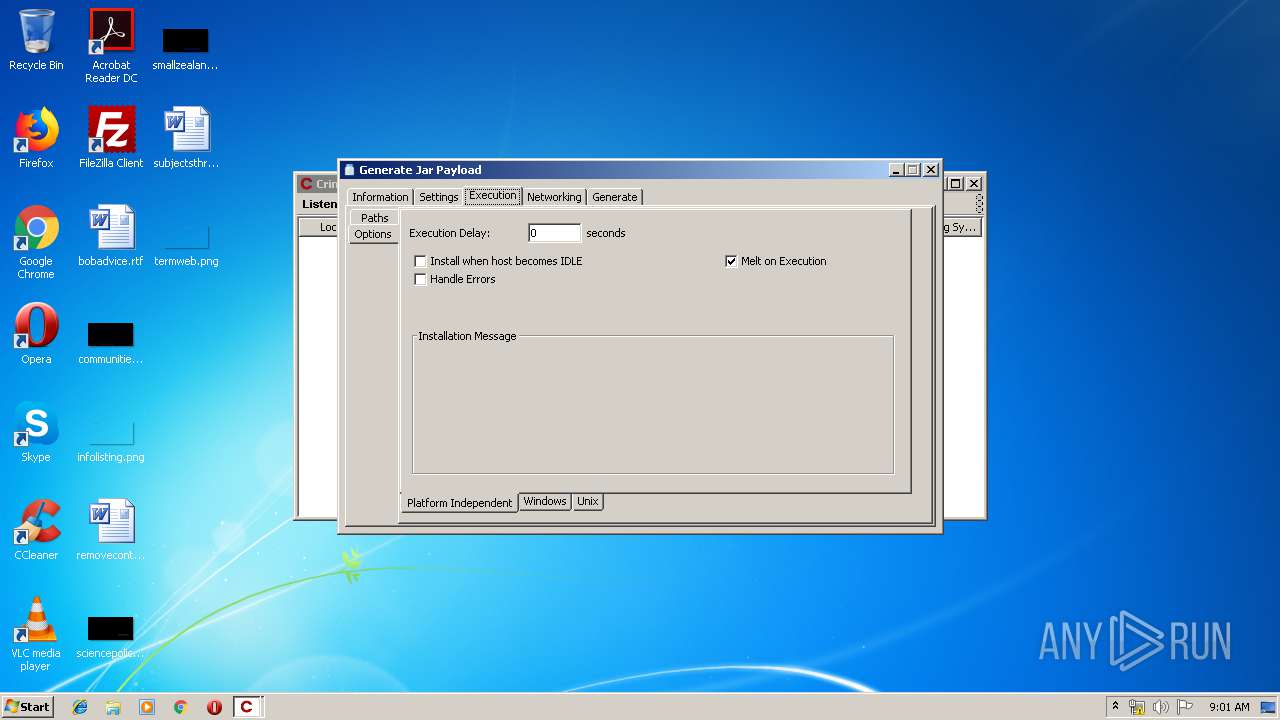
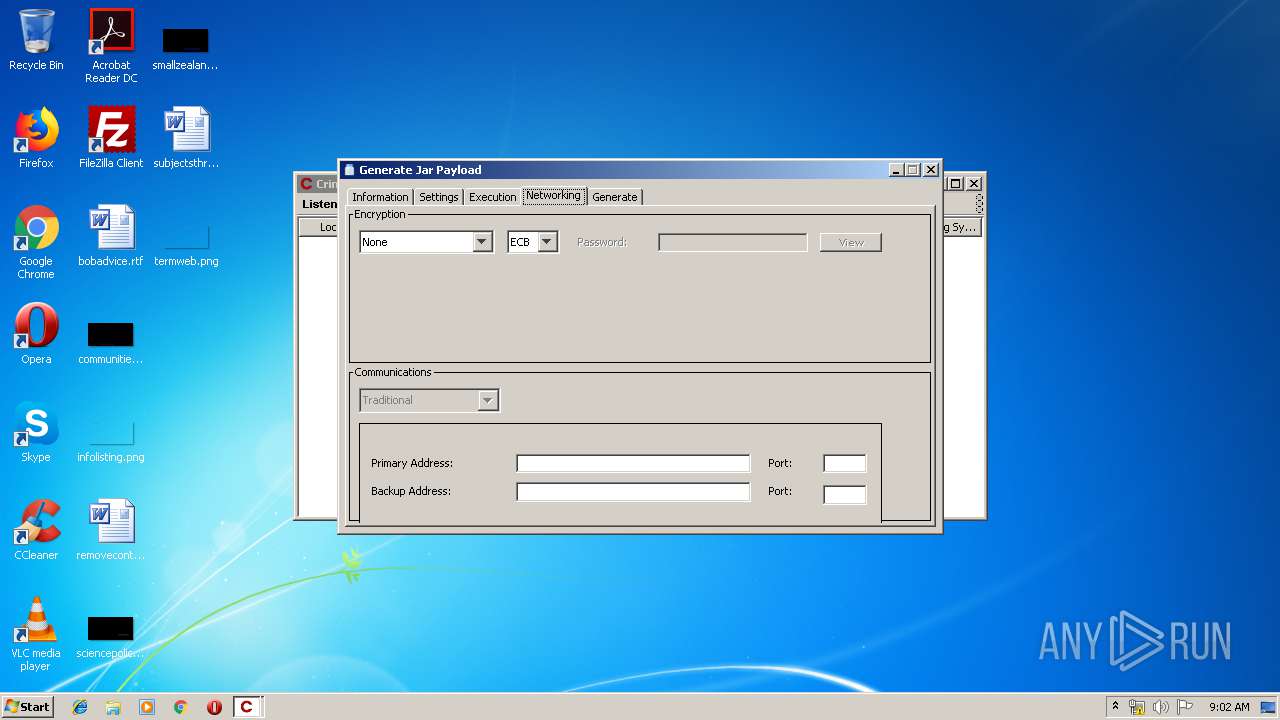
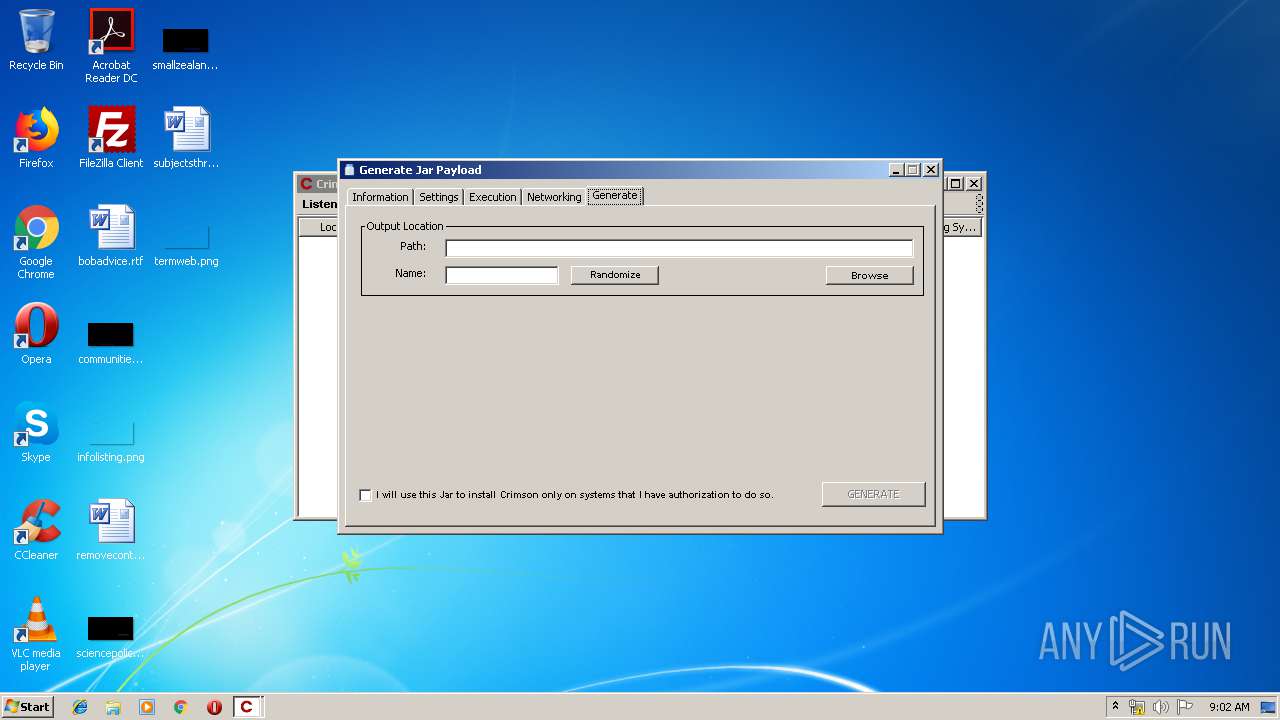
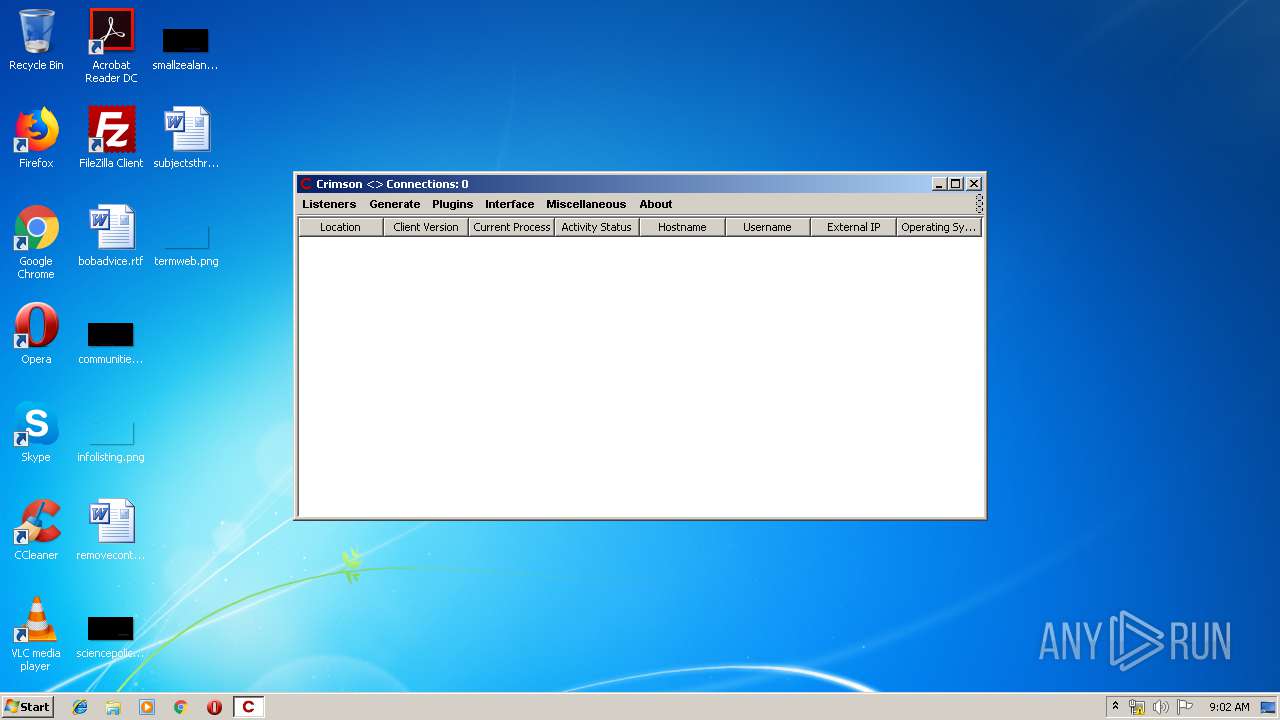
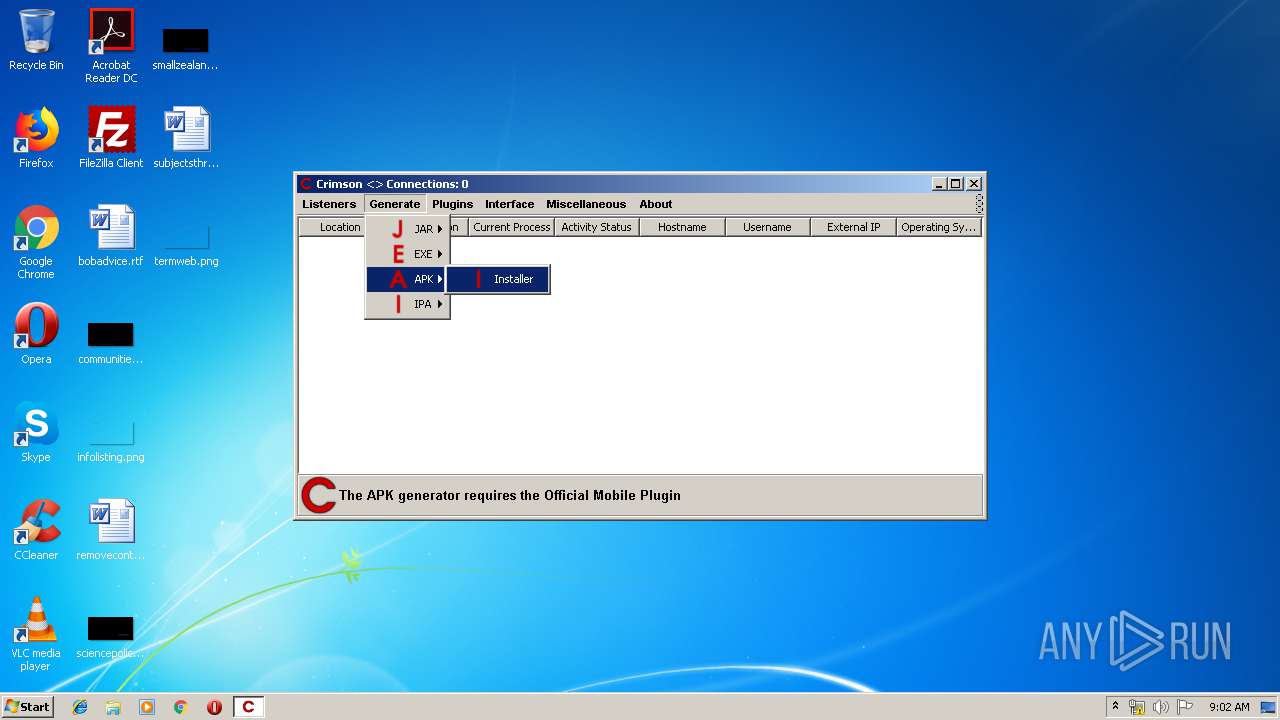
| File name: | Crimson3.0.0.jar |
| Full analysis: | https://app.any.run/tasks/f7235b93-6ac9-411d-bb11-f1c745e091b3 |
| Verdict: | Malicious activity |
| Analysis date: | November 16, 2019, 08:59:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | D568964FAAB371221530E93316092837 |
| SHA1: | 827A0E4BF0009422EB3CE81F23486B36FE69A99D |
| SHA256: | 224D58CD2346D12B1AFC902CC7C8737670C543286573607D83D09075DA195B97 |
| SSDEEP: | 196608:X7gDnEvuhyfMZY7tg7xR7oM3+l+YS35OlLGgkalPZXPufeZu:X7g/hyfMg+7b7oM3wDS35OQ3sPVGfJ |
MALICIOUS
Loads dropped or rewritten executable
- javaw.exe (PID: 788)
SUSPICIOUS
Creates files in the user directory
- javaw.exe (PID: 788)
Executable content was dropped or overwritten
- javaw.exe (PID: 788)
Checks for external IP
- javaw.exe (PID: 788)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2014:12:25 19:21:02 |
| ZipCRC: | 0x2cdc8b21 |
| ZipCompressedSize: | 126 |
| ZipUncompressedSize: | 166 |
| ZipFileName: | META-INF/MANIFEST.MF |
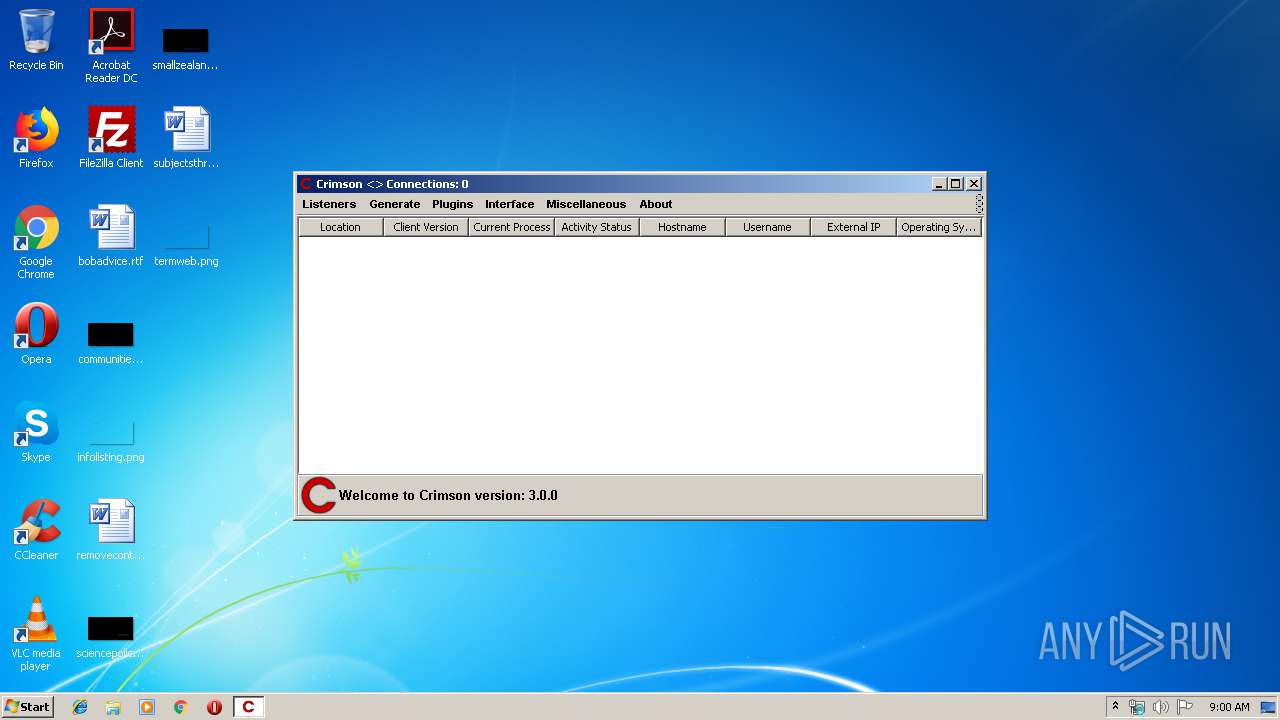
Total processes
34
Monitored processes
1
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 788 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\AppData\Local\Temp\Crimson3.0.0.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
Total events
415
Read events
412
Write events
3
Delete events
0
Modification events
| (PID) Process: | (788) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
| (PID) Process: | (788) javaw.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
1
Suspicious files
0
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 788 | javaw.exe | C:\Users\admin\AppData\Local\Temp\Ssettings.db-journal | — | |
MD5:— | SHA256:— | |||
| 788 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 788 | javaw.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\83aa4cc77f591dfc2374580bbd95f6ba_90059c37-1320-41a4-b58d-2b75a9850d2f | dbf | |
MD5:C8366AE350E7019AEFC9D1E6E6A498C6 | SHA256:11E6ACA8E682C046C83B721EEB5C72C5EF03CB5936C60DF6F4993511DDC61238 | |||
| 788 | javaw.exe | C:\Users\admin\AppData\Local\Temp\sqlite-3.8.7-f77f0e99-c62d-4e02-8f16-b6aef7a0ce52-sqlitejdbc.dll | executable | |
MD5:F017FCD918DCEA77C40E88210565066D | SHA256:2394696215211746215241E1255C0D4A65B462D5C057840DB8F6BC9C339B35BF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
3
DNS requests
3
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
788 | javaw.exe | GET | 200 | 34.196.181.158:80 | http://checkip.amazonaws.com/ | US | text | 16 b | malicious |
788 | javaw.exe | GET | 301 | 104.26.14.73:80 | http://freegeoip.net/xml/185.183.107.236 | US | — | — | malicious |
788 | javaw.exe | GET | 403 | 104.26.14.73:80 | http://freegeoip.net/shutdown | US | text | 1.51 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
788 | javaw.exe | 104.26.14.73:80 | freegeoip.net | Cloudflare Inc | US | shared |
788 | javaw.exe | 34.196.181.158:80 | checkip.amazonaws.com | Amazon.com, Inc. | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
checkip.amazonaws.com |
| malicious |
freegeoip.net |
| malicious |
subterranean-security.pw |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
4 ETPRO signatures available at the full report