analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
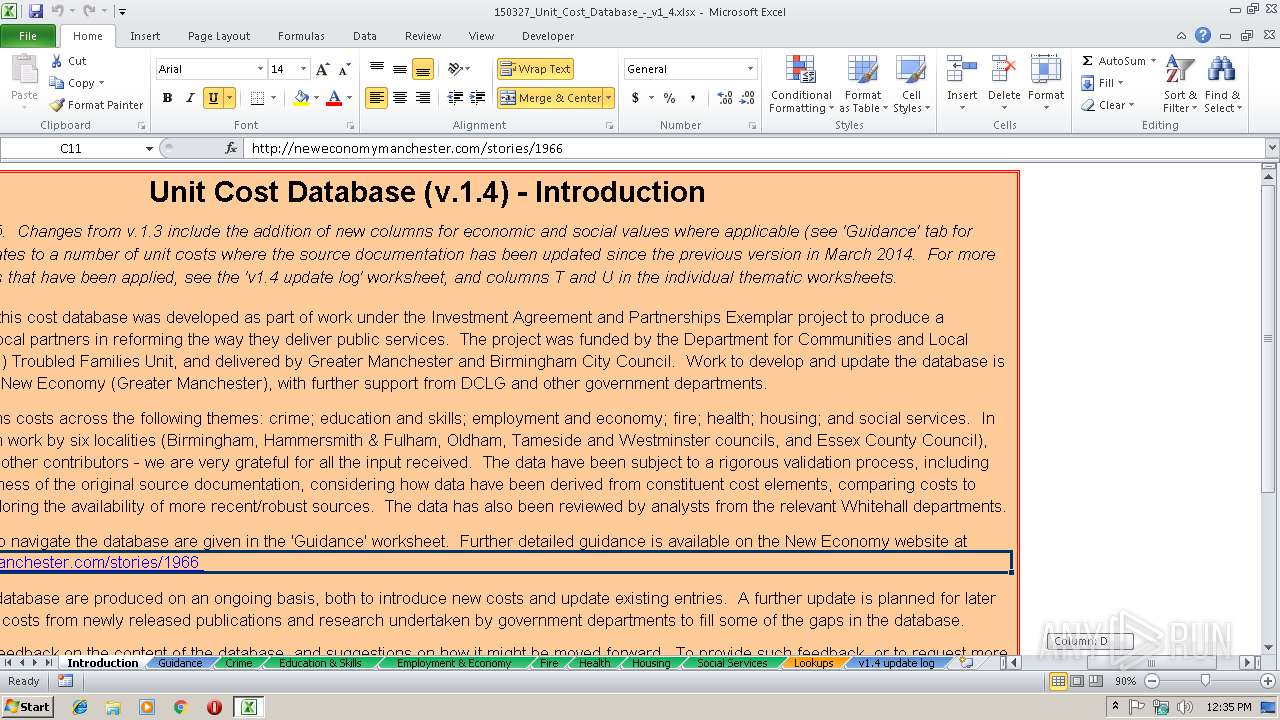
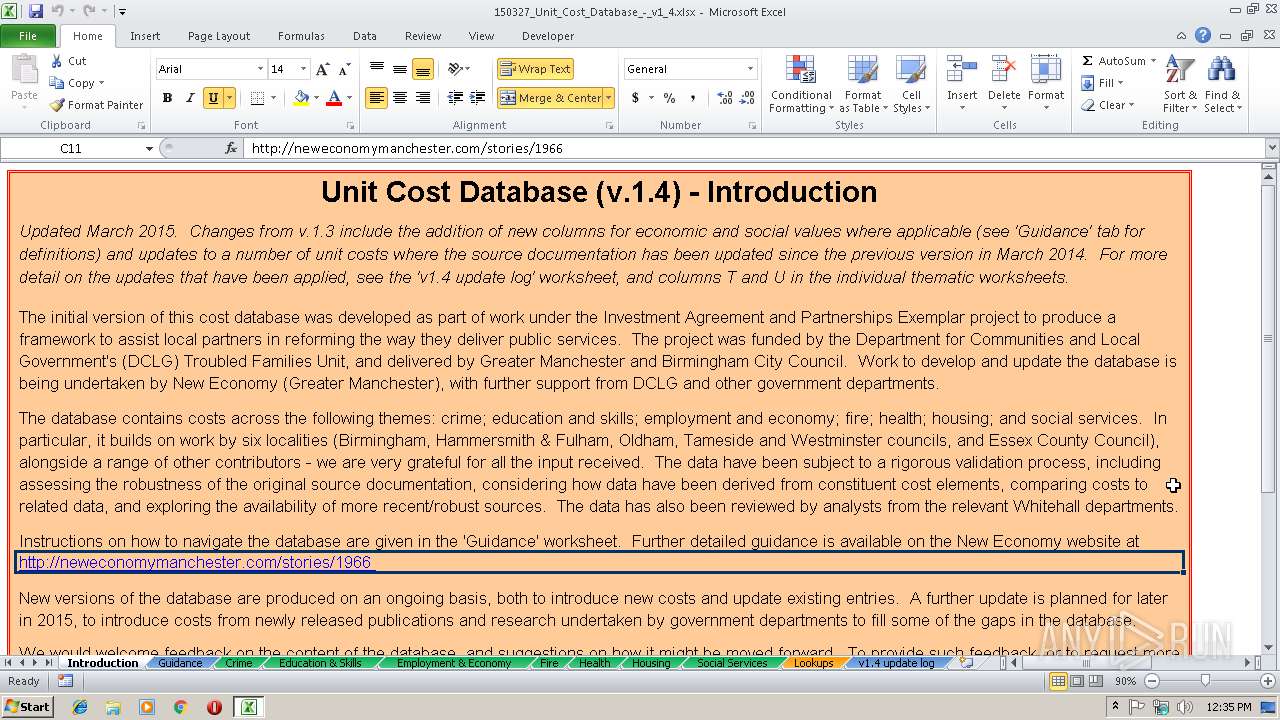
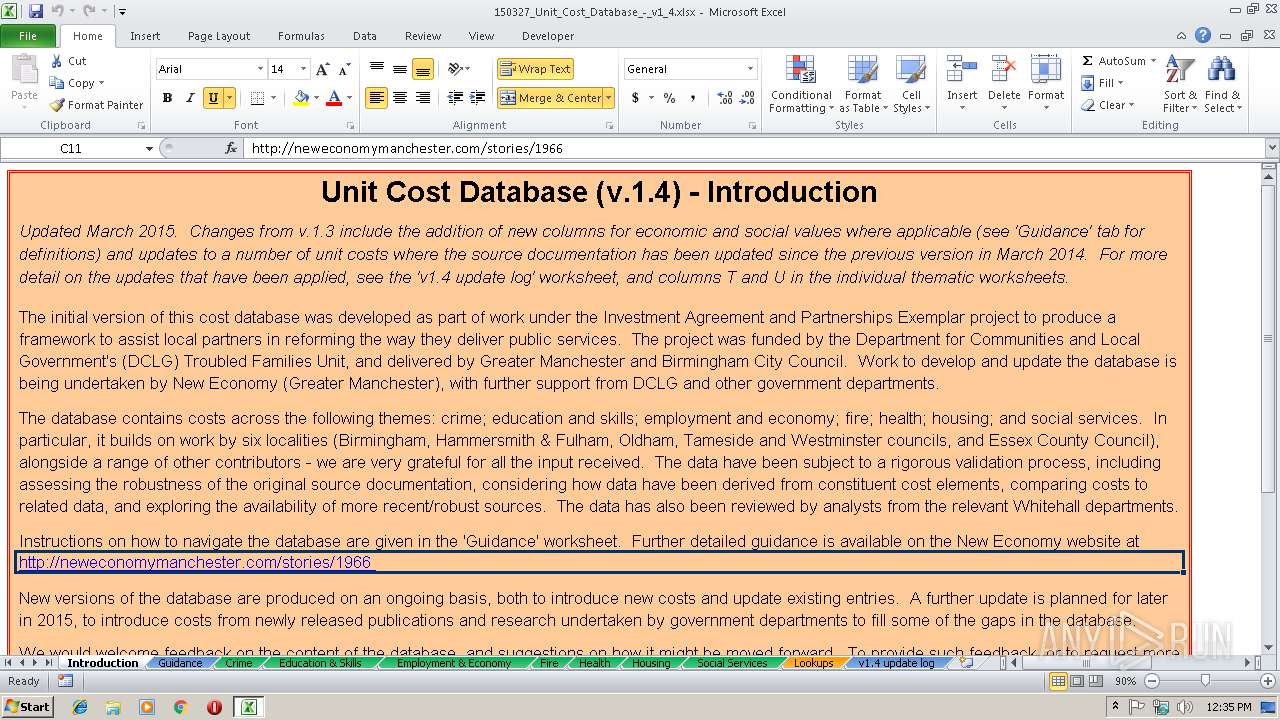
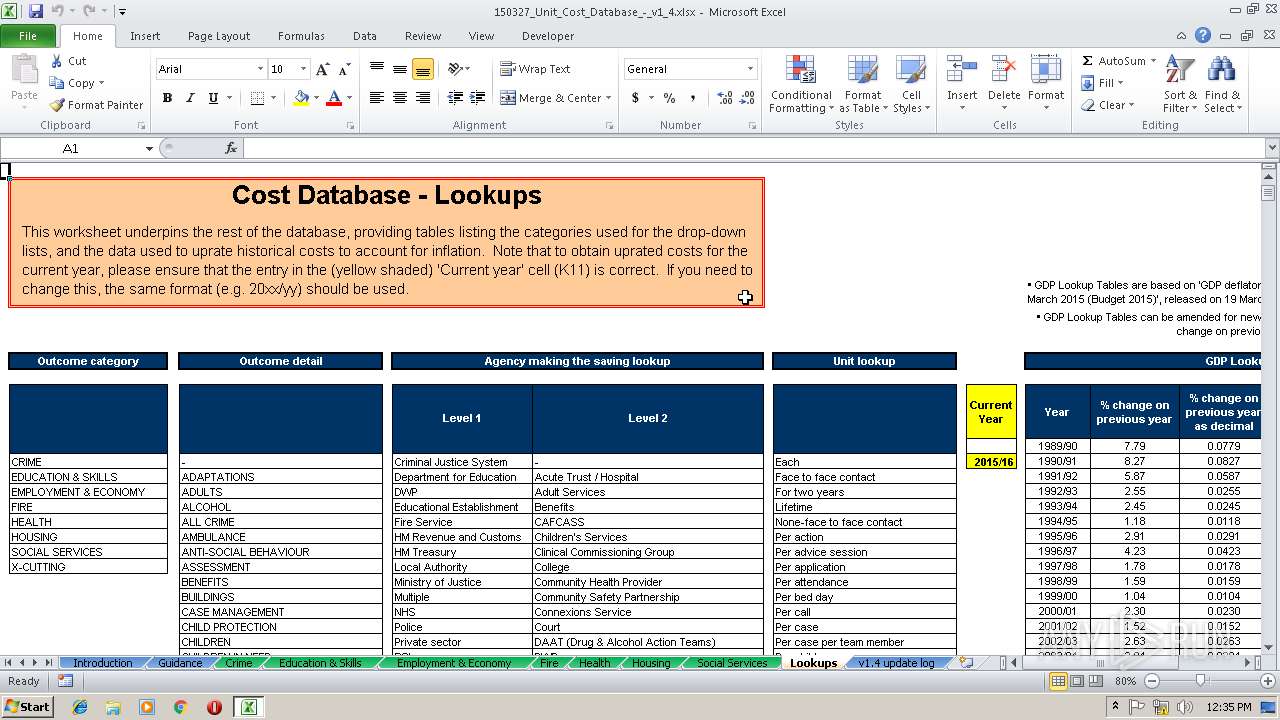
| download: | 150327_Unit_Cost_Database_-_v1_4.xlsx |
| Full analysis: | https://app.any.run/tasks/96cd786b-2a7b-4412-b31d-0294f56f909a |
| Verdict: | Malicious activity |
| Analysis date: | February 11, 2019, 12:34:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | 572D51D98EB29444D444D0B09907EE52 |
| SHA1: | AAF3065F0EA0AC068FDD5437E669977A4E318854 |
| SHA256: | 2246F5935D135A6A1353A81BE57C11B808C052F06F7A182A05C1C6B710460B89 |
| SSDEEP: | 6144:xWcBarCyXOMOx0U/0gsaVu+tivIboSBTcwX3GG8vK21L0jlwVluDxHI7ySy6sv:xWFrCyI/FPtqIBBTcNGAgS+x/ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads internet explorer settings
- EXCEL.EXE (PID: 2988)
Unusual connect from Microsoft Office
- EXCEL.EXE (PID: 2988)
INFO
Creates files in the user directory
- EXCEL.EXE (PID: 2988)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2080)
- iexplore.exe (PID: 3568)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2988)
Changes internet zones settings
- iexplore.exe (PID: 3300)
Reads Internet Cache Settings
- iexplore.exe (PID: 3568)
- iexplore.exe (PID: 3300)
Reads internet explorer settings
- iexplore.exe (PID: 3568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlsx | | | Excel Microsoft Office Open XML Format document (61.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (31.5) |
| .zip | | | ZIP compressed archive (7.2) |
EXIF
XML
| Security0: | Restricted |
|---|---|
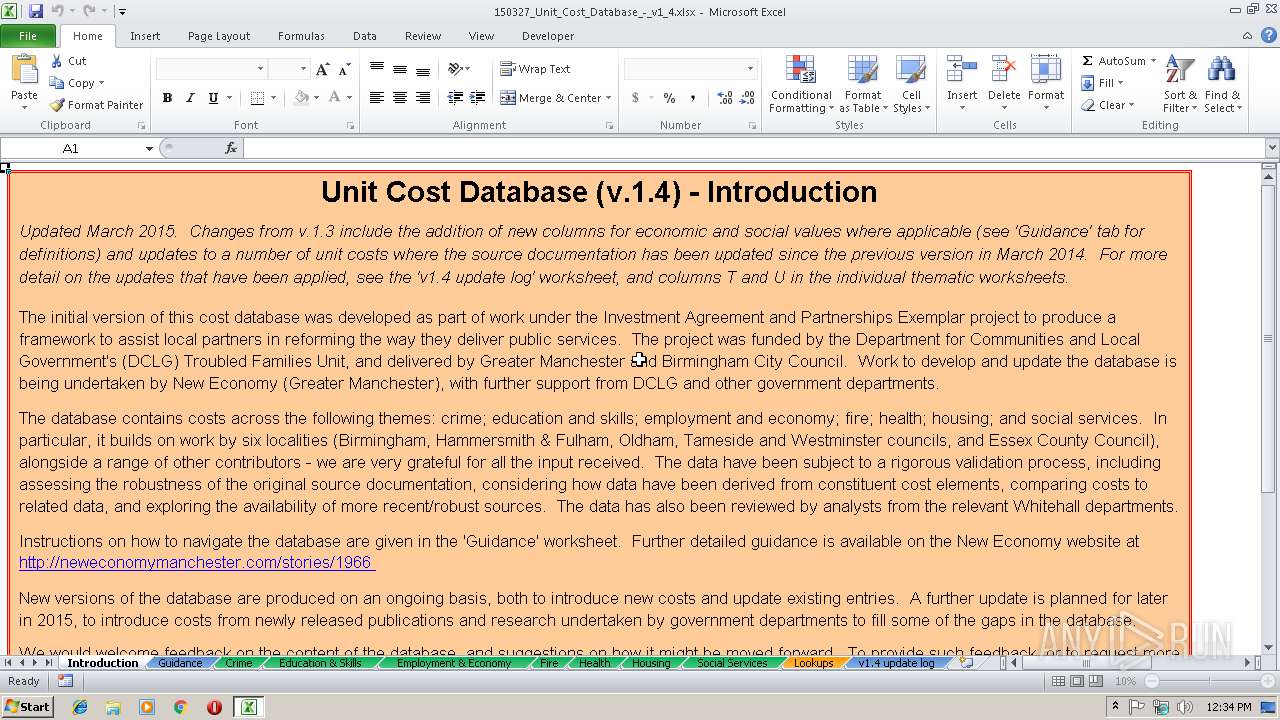
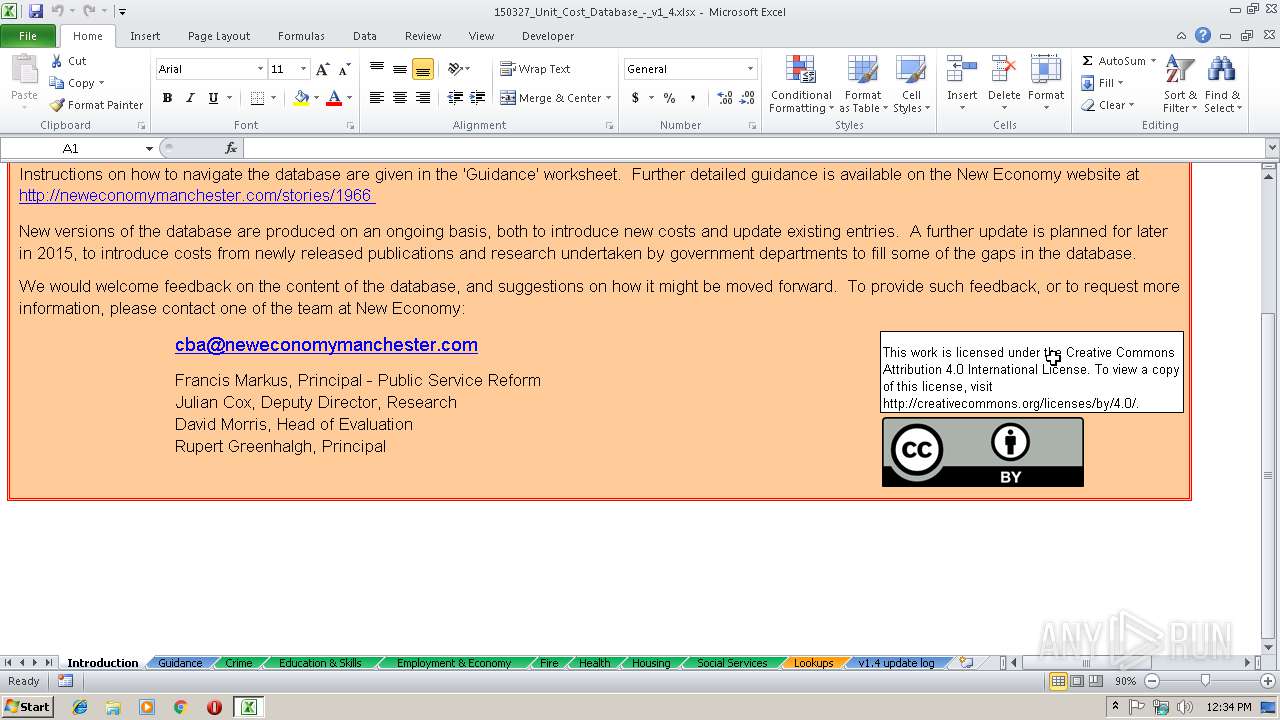
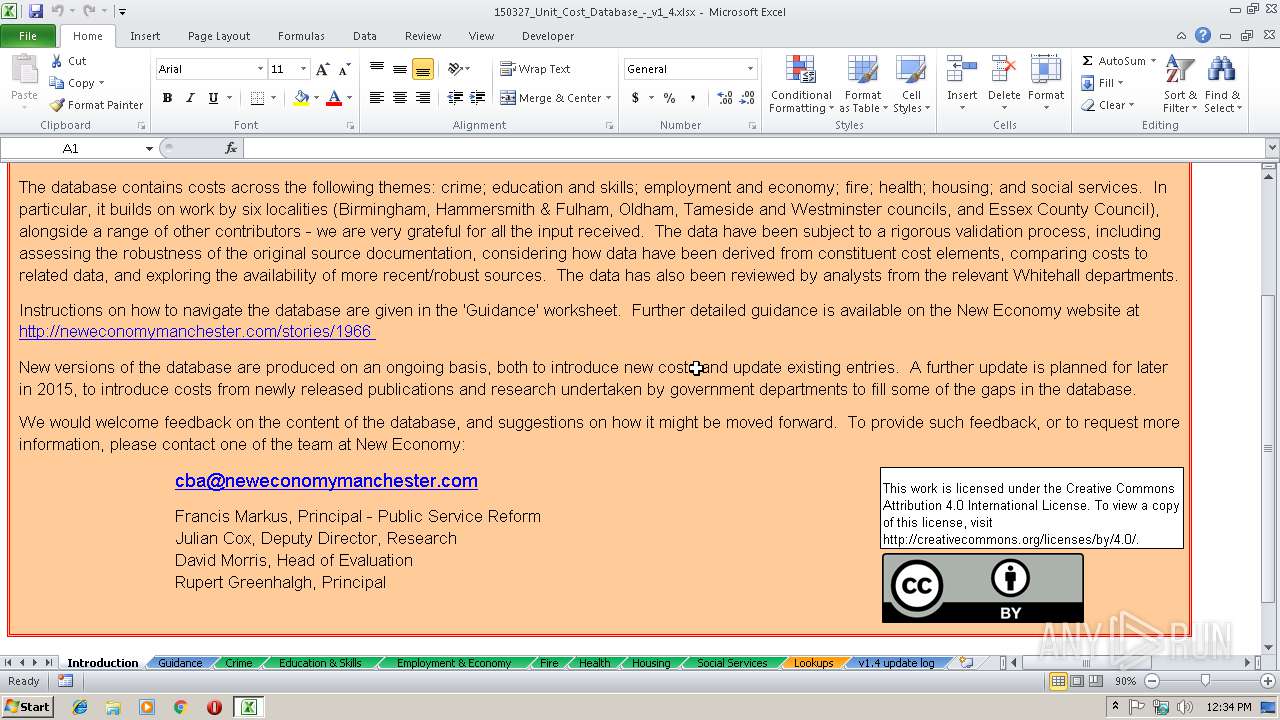
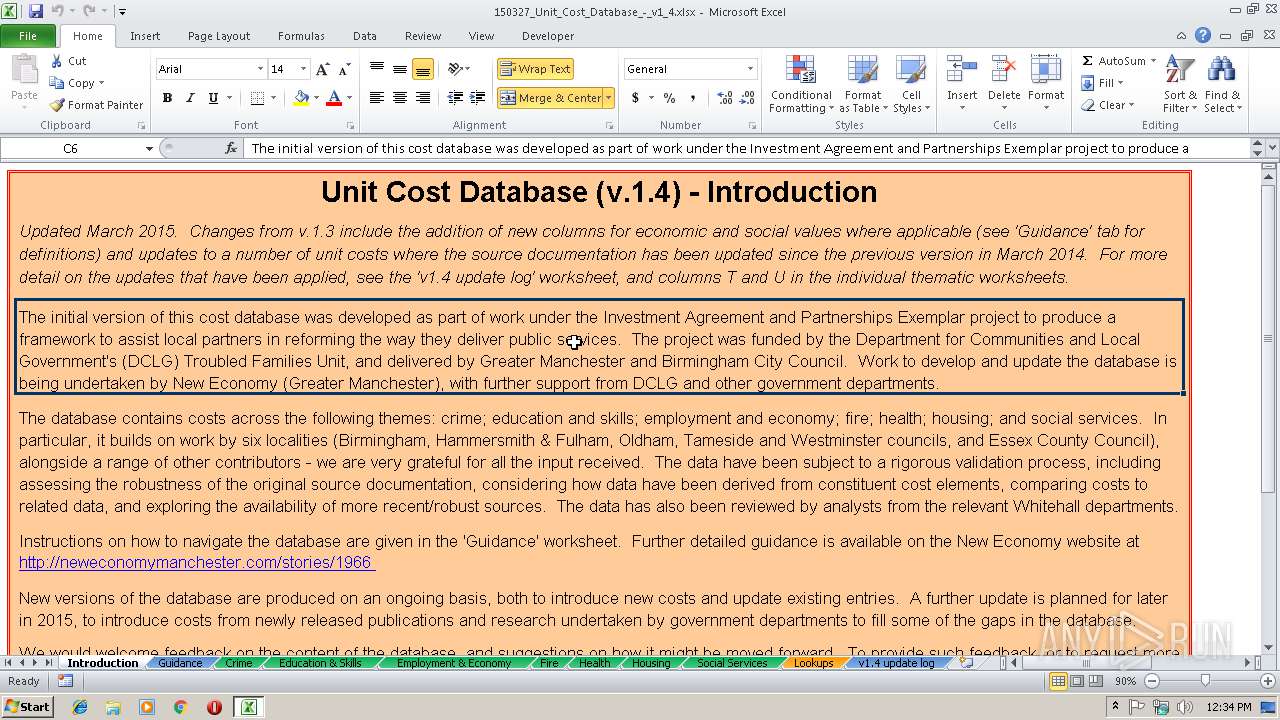
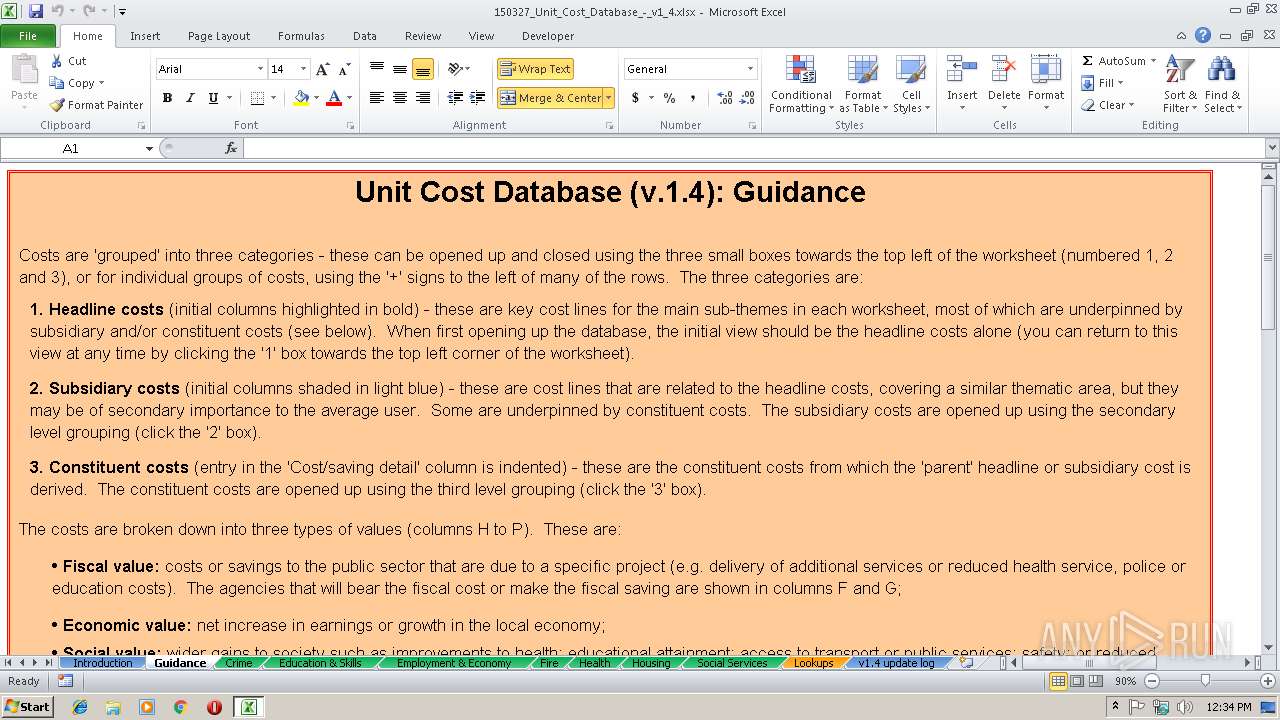
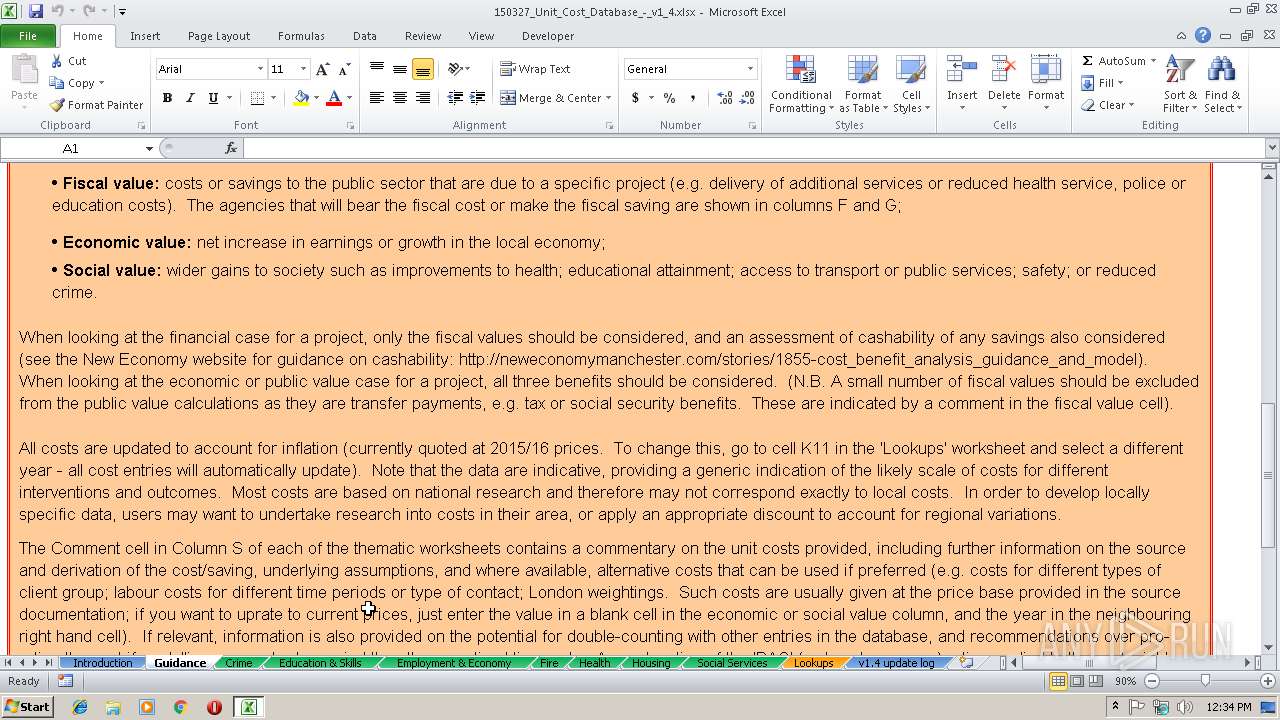
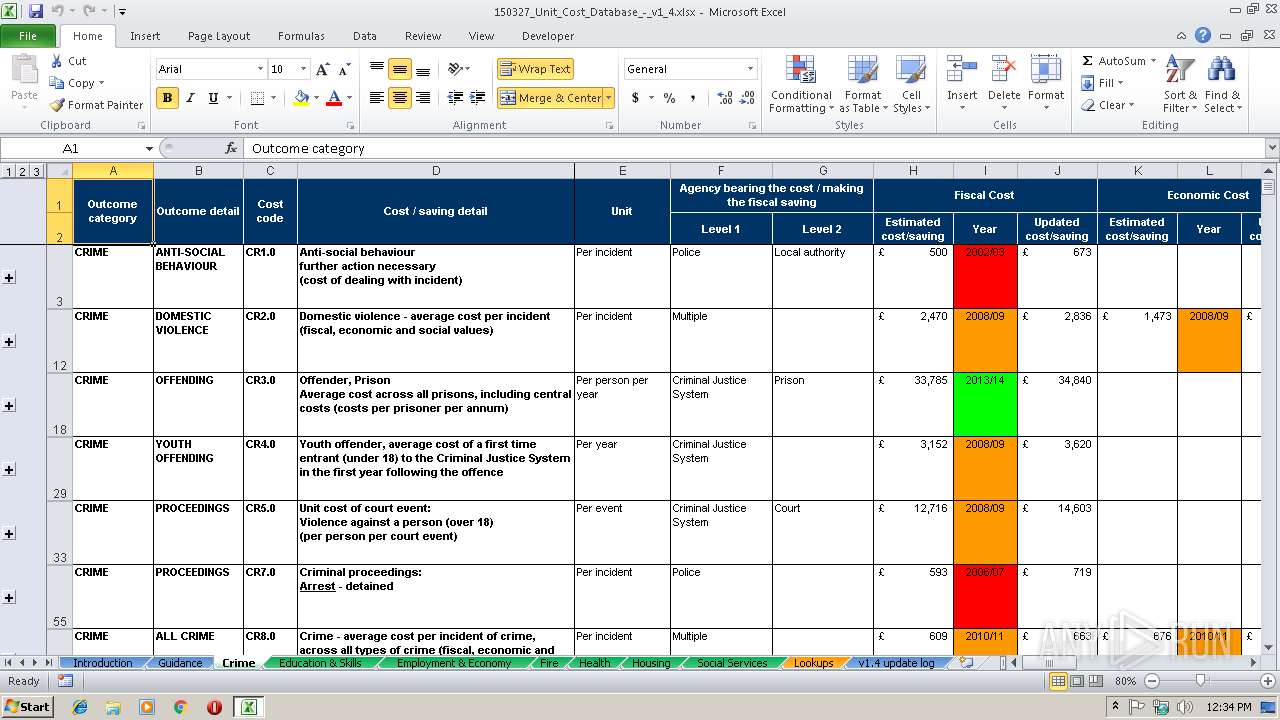
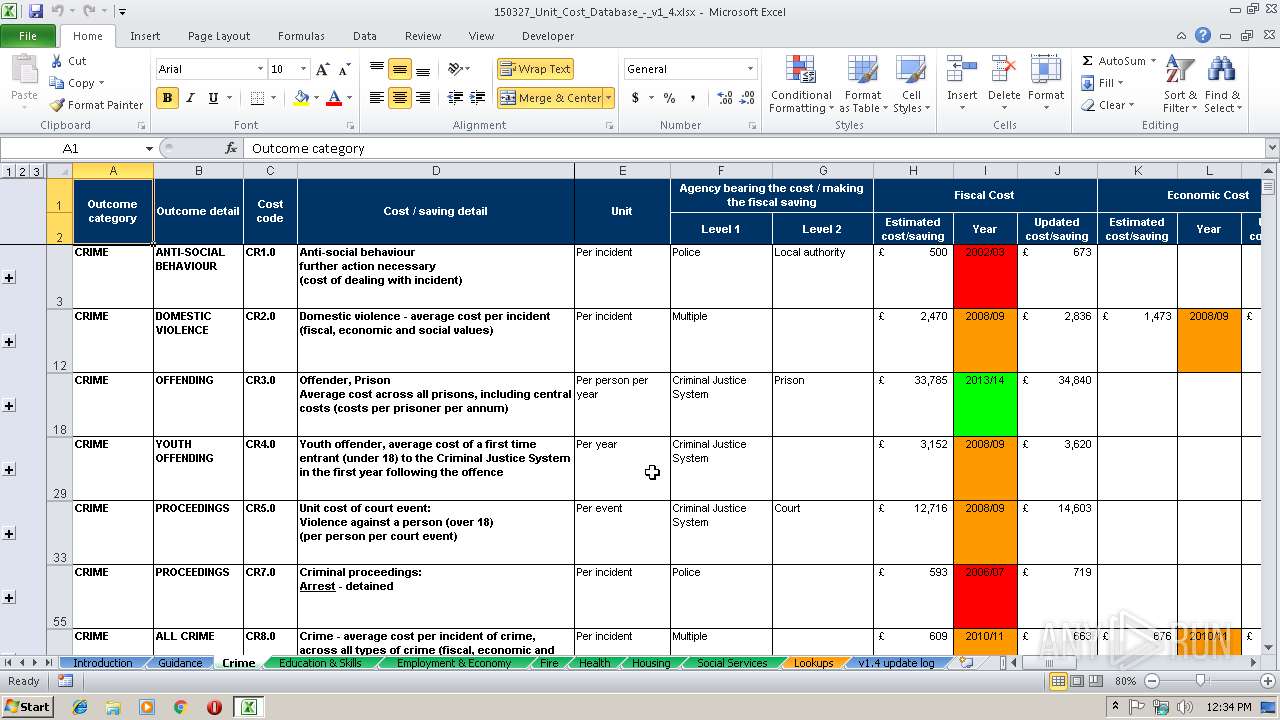
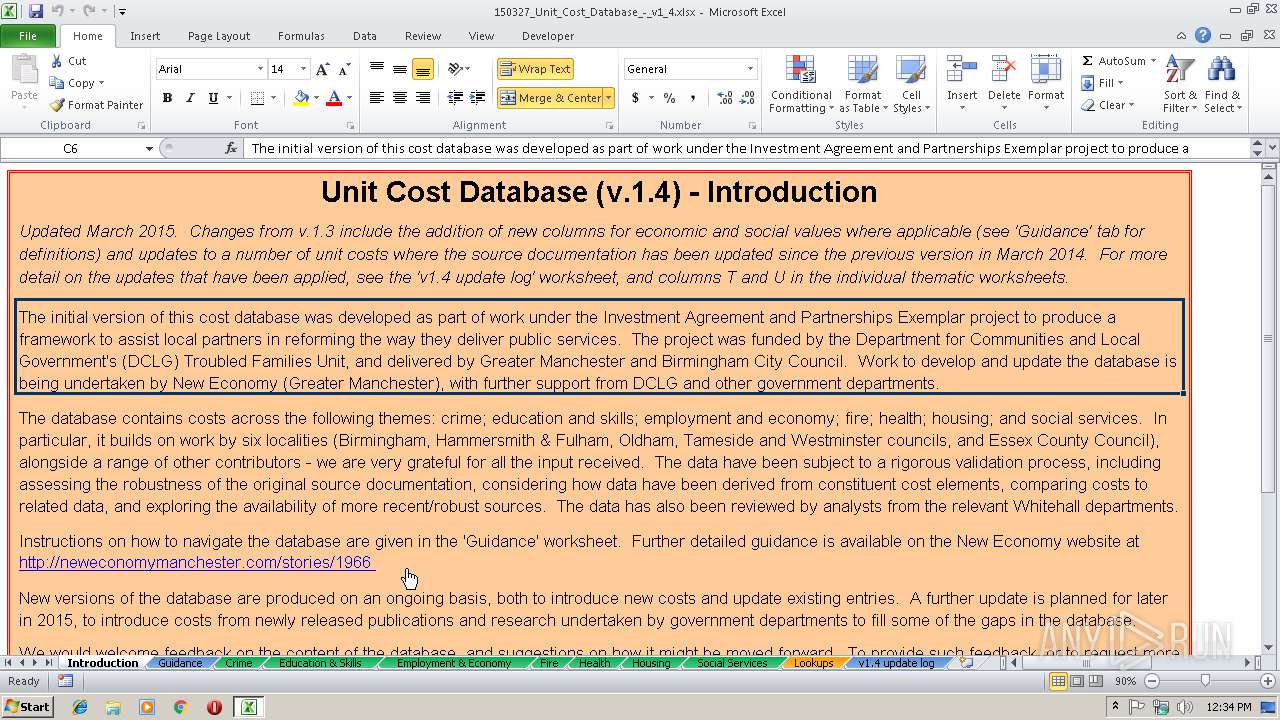
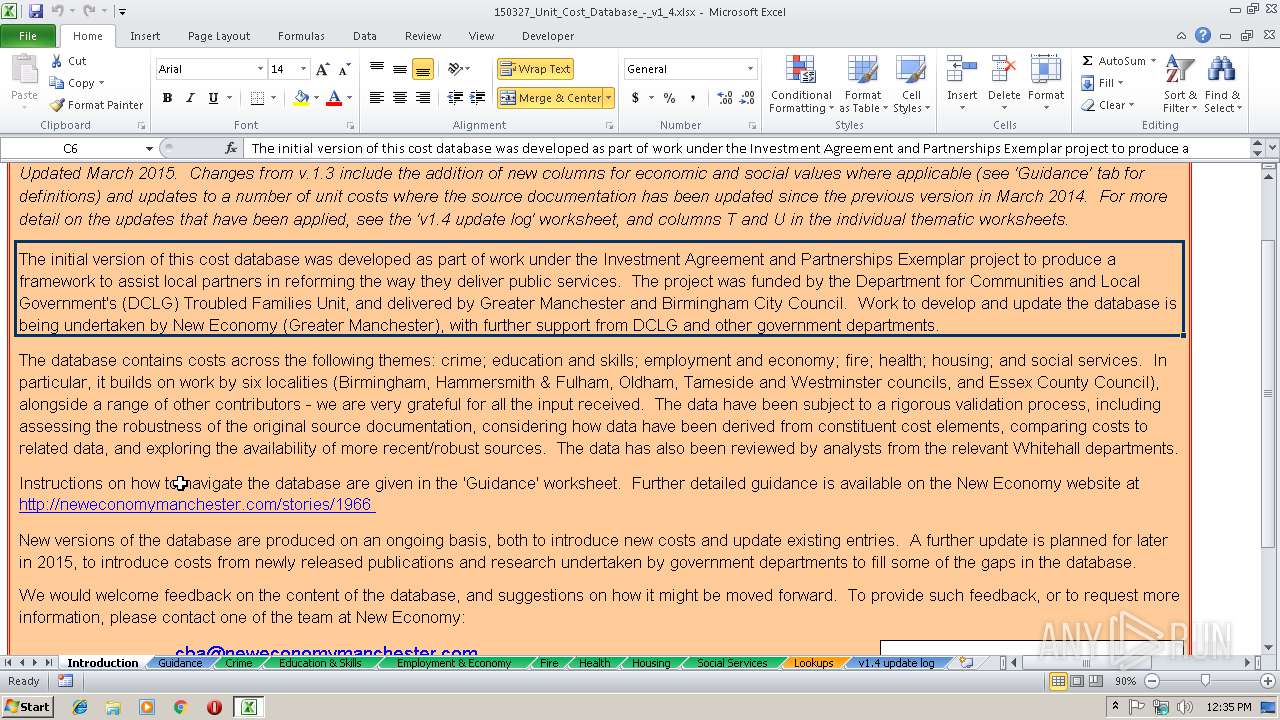
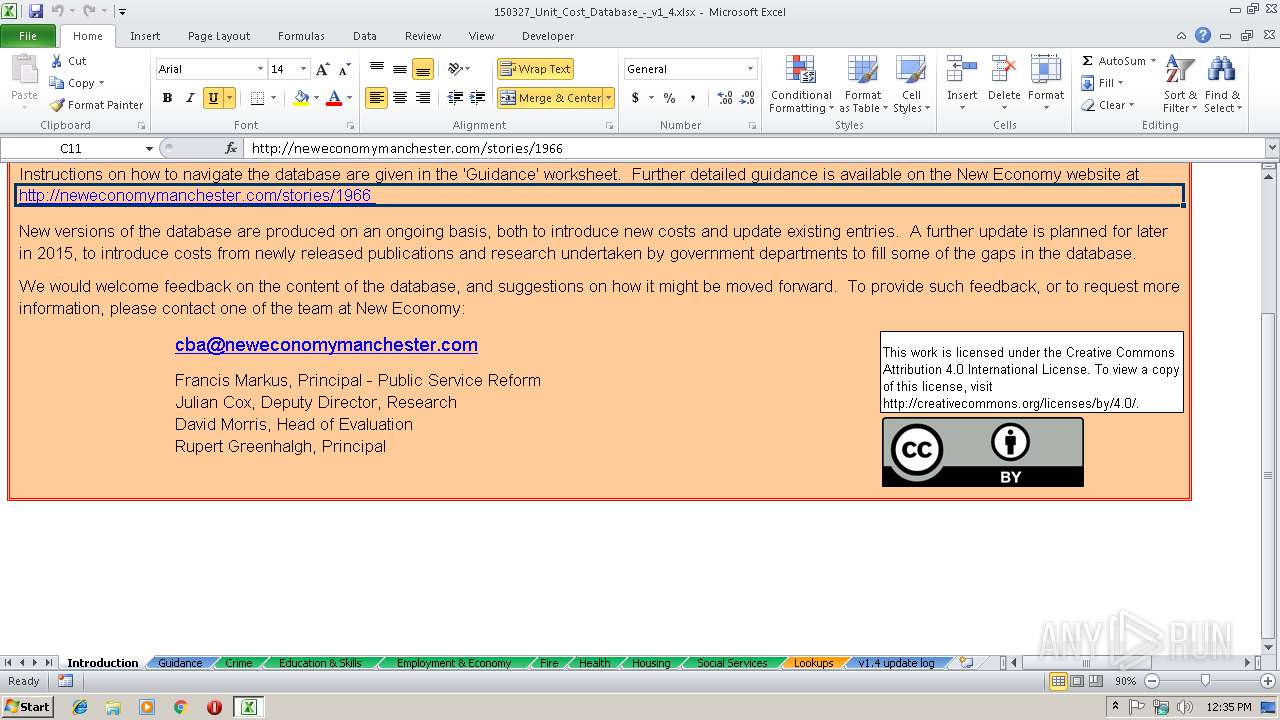
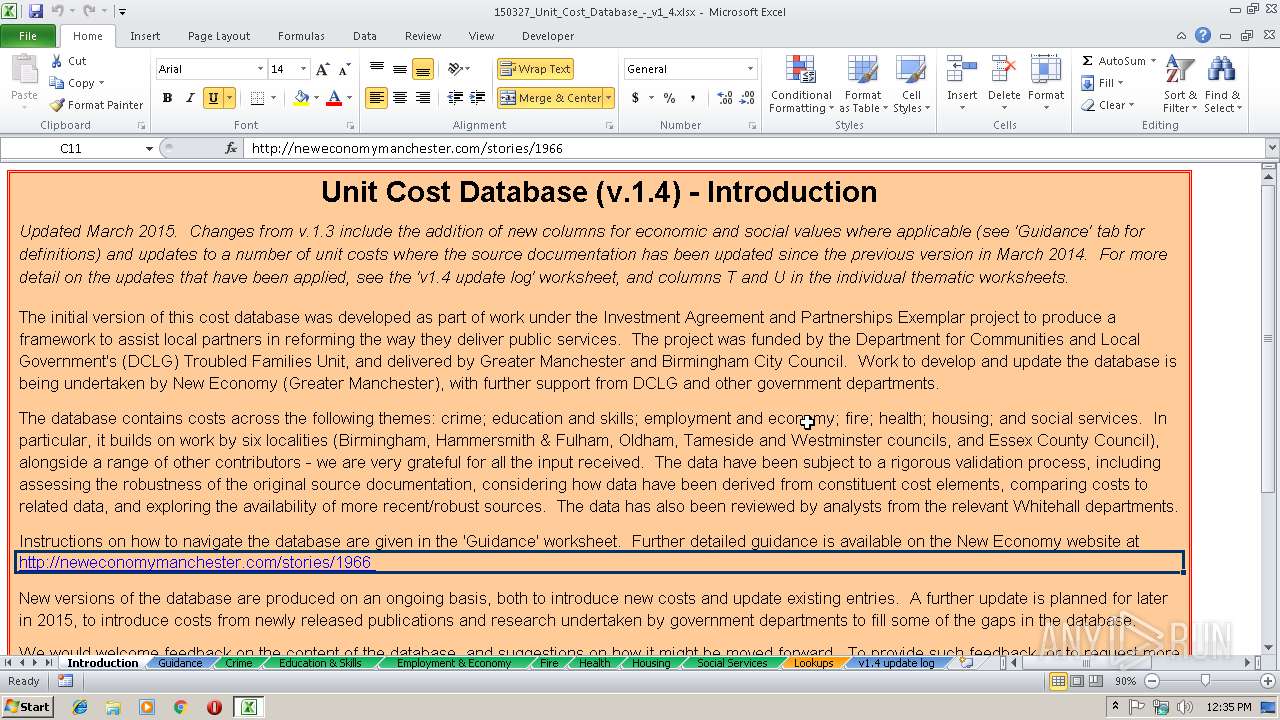
| Description0: | Database of costs across different boroughs involved in Community Budgets |
| DocumentType: | Data Analysis |
| ContentTypeId: | 0x010100C128D4B275C3DD4D83EC82E871B2F6FB |
| Tag_NewReviewCycle: | - |
| AppVersion: | 12 |
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| Company: | TMBC |
| TitlesOfParts: |
|
| HeadingPairs: |
|
| ScaleCrop: | No |
| DocSecurity: | None |
| Application: | Microsoft Excel |
| ContentStatus: | - |
| ContentType: | Document |
| ModifyDate: | 2015:03:27 22:00:22Z |
| CreateDate: | 2011:06:29 07:05:00Z |
| LastPrinted: | 2015:03:27 21:33:05Z |
| LastModifiedBy: | MEGFMA |
| Keywords: | New Economy |
XMP
| Creator: | Francis Markus |
|---|---|
| Title: | Unit cost database |
ZIP
| ZipFileName: | [Content_Types].xml |
|---|---|
| ZipUncompressedSize: | 3569 |
| ZipCompressedSize: | 563 |
| ZipCRC: | 0x2880cf3d |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0006 |
| ZipRequiredVersion: | 20 |
Total processes
35
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2988 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | explorer.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 14.0.6024.1000 | ||||
| 3300 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) | ||||
| 3568 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3300 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) | ||||
| 2080 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe |
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 | ||||
Total events
1 048
Read events
965
Write events
72
Delete events
11
Modification events
| (PID) Process: | (2988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | w<0 |
Value: 773C3000AC0B0000010000000000000000000000 | |||
| (PID) Process: | (2988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: AC0B00008A82242606C2D40100000000 | |||
| (PID) Process: | (2988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | w<0 |
Value: 773C3000AC0B0000010000000000000000000000 | |||
| (PID) Process: | (2988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2988) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\2471E6 |
| Operation: | write | Name: | 2471E6 |
Value: 04000000AC0B00004700000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C003100350030003300320037005F0055006E00690074005F0043006F00730074005F00440061007400610062006100730065005F002D005F00760031005F0034002E0078006C0073007800000000002200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C000100000000000000603A402706C2D401E6712400E671240000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
2
Text files
40
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2988 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR6C57.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2988 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF8B874CB7FC0E01DB.TMP | — | |
MD5:— | SHA256:— | |||
| 3568 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@neweconomymanchester[1].txt | — | |
MD5:— | SHA256:— | |||
| 2988 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\cost-benefit-analysis[1].txt | html | |
MD5:63715D7E397CF597777D08457DA47BAE | SHA256:BA6C014109C1124F8868A81B9BEF6B9AC7FEDD53784676A3E79B012DCD2B6D75 | |||
| 3568 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\cost-benefit-analysis[1].htm | html | |
MD5:63715D7E397CF597777D08457DA47BAE | SHA256:BA6C014109C1124F8868A81B9BEF6B9AC7FEDD53784676A3E79B012DCD2B6D75 | |||
| 3568 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\manchester-buildings[1].jpg | image | |
MD5:5DF57D19D101C6F4F638DBAE4D42567E | SHA256:E2AF91DC4295A19D1DB63F23CADB6DF3F690C2878F5E82C9666D427E271EF72E | |||
| 3568 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\css[1].txt | text | |
MD5:B3ABD2FD73422456C1C8E9324DD87EC0 | SHA256:BF226BAC5EB385704A13135BC2B1DA9B1FC7A9824B9627636EB59736513F4B47 | |||
| 3568 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\new-economy-1.0.0[1].js | text | |
MD5:A61421F2A7FB07ACF38F33A8F72A8C99 | SHA256:770E5F4EE47362D9776A7B404F978E5EA33A383B4D7322EEF01FA501368E636E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
17
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
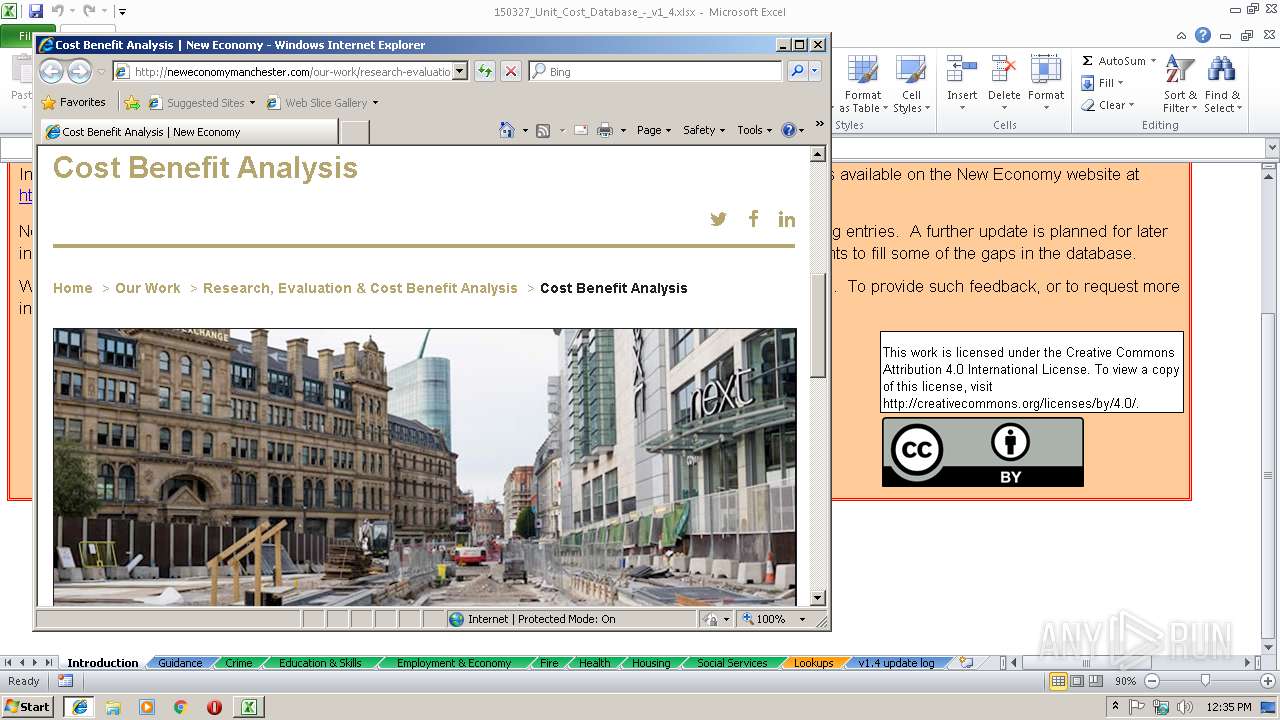
2988 | EXCEL.EXE | GET | 301 | 37.128.190.166:80 | http://neweconomymanchester.com/stories/1966 | GB | — | — | unknown |
2988 | EXCEL.EXE | GET | 200 | 37.128.190.166:80 | http://neweconomymanchester.com/our-work/research-evaluation-cost-benefit-analysis/cost-benefit-analysis | GB | html | 5.51 Kb | unknown |
3568 | iexplore.exe | GET | 200 | 37.128.190.166:80 | http://neweconomymanchester.com/our-work/research-evaluation-cost-benefit-analysis/cost-benefit-analysis | GB | html | 5.51 Kb | unknown |
3568 | iexplore.exe | GET | 200 | 37.128.190.166:80 | http://neweconomymanchester.com/css/style.css | GB | text | 4.53 Kb | unknown |
3568 | iexplore.exe | GET | 200 | 37.128.190.166:80 | http://neweconomymanchester.com/scripts/new-economy-1.0.0.js | GB | text | 721 b | unknown |
3568 | iexplore.exe | GET | 200 | 37.128.190.166:80 | http://neweconomymanchester.com/media/1016/skyline-with-noma.jpg?mode=crop&width=135&height=80&rnd=131322279770000000 | GB | image | 5.64 Kb | unknown |
3568 | iexplore.exe | GET | 200 | 37.128.190.166:80 | http://neweconomymanchester.com/media/1017/event.jpg?mode=crop&width=135&height=80&rnd=131322281100000000 | GB | image | 5.84 Kb | unknown |
3568 | iexplore.exe | GET | 200 | 37.128.190.166:80 | http://neweconomymanchester.com/fonts/font-awesome/css/font-awesome.min.css | GB | text | 6.98 Kb | unknown |
3300 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3568 | iexplore.exe | GET | 200 | 216.58.208.42:80 | http://fonts.googleapis.com/css?family=Open+Sans:400,700,400italic,700italic | US | text | 167 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3300 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3568 | iexplore.exe | 37.128.190.166:80 | neweconomymanchester.com | iomart Cloud Services Limited. | GB | unknown |
2988 | EXCEL.EXE | 37.128.190.166:80 | neweconomymanchester.com | iomart Cloud Services Limited. | GB | unknown |
3568 | iexplore.exe | 216.58.208.35:80 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3568 | iexplore.exe | 216.58.208.42:80 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3568 | iexplore.exe | 23.67.137.77:443 | ws.sharethis.com | Akamai International B.V. | NL | whitelisted |
3568 | iexplore.exe | 172.217.16.142:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
3300 | iexplore.exe | 37.128.190.166:80 | neweconomymanchester.com | iomart Cloud Services Limited. | GB | unknown |
3568 | iexplore.exe | 74.125.133.156:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
3568 | iexplore.exe | 2.16.186.243:443 | c.sharethis.mgr.consensu.org | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
neweconomymanchester.com |
| unknown |
www.bing.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ws.sharethis.com |
| shared |
fonts.gstatic.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
c.sharethis.mgr.consensu.org |
| whitelisted |