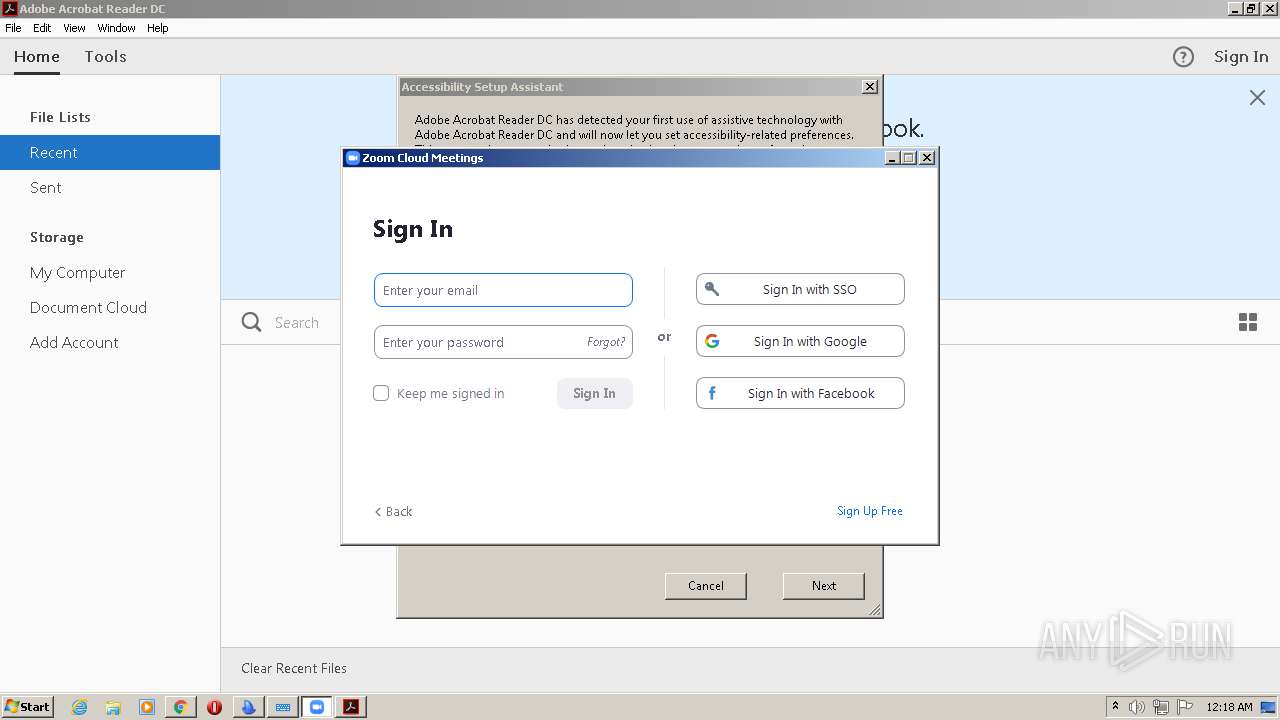
| URL: | https://ninite.com/zoom/ninite.exe |
| Full analysis: | https://app.any.run/tasks/85c8128b-488e-44f9-9086-9aaa8a367c7b |
| Verdict: | Malicious activity |
| Analysis date: | September 21, 2020, 23:14:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 1D53A2144F48485C1AB9F5CDF610E627 |
| SHA1: | 30ED7730291A38092BE00E18A0A9D05F0AB9B490 |
| SHA256: | 223460F428BC9C8EE2BA9F455933CC0116735AE9B1B31773FDEC19A1C383D002 |
| SSDEEP: | 3:N8DAyIuQMLV0dA:2DAyjZLV0dA |
MALICIOUS
Application was dropped or rewritten from another process
- Ninite Zoom Installer.exe (PID: 2900)
- Ninite.exe (PID: 1700)
- Ninite.exe (PID: 2336)
- CptService.exe (PID: 3060)
- ZoomOutlookIMPlugin.exe (PID: 3780)
- CptInstall.exe (PID: 3432)
- Zoom.exe (PID: 2428)
- Zoom.exe (PID: 3324)
Changes settings of System certificates
- Ninite.exe (PID: 2336)
Loads dropped or rewritten executable
- Zoom.exe (PID: 2428)
- regsvr32.exe (PID: 4008)
- ZoomOutlookIMPlugin.exe (PID: 3780)
- Zoom.exe (PID: 3324)
Registers / Runs the DLL via REGSVR32.EXE
- ZoomOutlookIMPlugin.exe (PID: 3780)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 936)
- chrome.exe (PID: 1716)
- Ninite Zoom Installer.exe (PID: 2900)
Reads Internet Cache Settings
- Ninite Zoom Installer.exe (PID: 2900)
- Ninite.exe (PID: 2336)
Application launched itself
- Ninite.exe (PID: 1700)
- Zoom.exe (PID: 2428)
Cleans NTFS data-stream (Zone Identifier)
- Ninite.exe (PID: 2336)
Adds / modifies Windows certificates
- Ninite.exe (PID: 2336)
Starts Microsoft Installer
- Ninite.exe (PID: 2336)
Creates files in the user directory
- MsiExec.exe (PID: 2148)
- ZoomOutlookIMPlugin.exe (PID: 3780)
- Zoom.exe (PID: 2428)
- Zoom.exe (PID: 3324)
Changes IE settings (feature browser emulation)
- MsiExec.exe (PID: 2148)
- AcroRd32.exe (PID: 2084)
Creates files in the program directory
- CptInstall.exe (PID: 3432)
- AdobeARM.exe (PID: 1676)
Changes the autorun value in the registry
- MsiExec.exe (PID: 2148)
Modifies the open verb of a shell class
- MsiExec.exe (PID: 2148)
Searches for installed software
- Ninite.exe (PID: 2336)
Modifies files in Chrome extension folder
- chrome.exe (PID: 936)
Executed as Windows Service
- CptService.exe (PID: 3060)
INFO
Application launched itself
- chrome.exe (PID: 936)
- RdrCEF.exe (PID: 256)
- AcroRd32.exe (PID: 2084)
- iexplore.exe (PID: 2864)
Reads the hosts file
- chrome.exe (PID: 936)
- chrome.exe (PID: 1716)
- RdrCEF.exe (PID: 256)
Reads settings of System Certificates
- chrome.exe (PID: 936)
- chrome.exe (PID: 1716)
- AcroRd32.exe (PID: 2084)
Reads Internet Cache Settings
- chrome.exe (PID: 936)
- AcroRd32.exe (PID: 2084)
- AcroRd32.exe (PID: 3768)
- iexplore.exe (PID: 972)
- iexplore.exe (PID: 2864)
Manual execution by user
- osk.exe (PID: 2508)
- osk.exe (PID: 2424)
- Zoom.exe (PID: 2428)
- osk.exe (PID: 3788)
- osk.exe (PID: 1724)
- AcroRd32.exe (PID: 2084)
- explorer.exe (PID: 972)
- iexplore.exe (PID: 2864)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2148)
Changes internet zones settings
- iexplore.exe (PID: 2864)
Reads internet explorer settings
- iexplore.exe (PID: 972)
Creates files in the program directory
- MsiExec.exe (PID: 2148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
103
Monitored processes
43
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 256 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1064,15907956112672543579,13523605682409828816,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12519076206560706877 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2244 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=464 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 660 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6cbca9d0,0x6cbca9e0,0x6cbca9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "https://ninite.com/zoom/ninite.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 972 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2864 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 972 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1064,15907956112672543579,13523605682409828816,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10998418696620404418 --mojo-platform-channel-handle=2592 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1676 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:15.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.27.2646 Modules
| |||||||||||||||
| 1688 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1064,15907956112672543579,13523605682409828816,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11964877893557809337 --mojo-platform-channel-handle=2040 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
6 180
Read events
3 945
Write events
2 218
Delete events
17
Modification events
| (PID) Process: | (936) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (936) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (936) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (936) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (564) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 936-13245203712370875 |
Value: 259 | |||
| (PID) Process: | (936) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (936) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (936) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (936) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2832-13239195546717773 |
Value: 0 | |||
| (PID) Process: | (936) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
8
Suspicious files
51
Text files
2 842
Unknown types
42
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 936 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\38047619-e86c-4dec-907d-6b138bb2f33f.tmp | — | |
MD5:— | SHA256:— | |||
| 936 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000032.dbtmp | — | |
MD5:— | SHA256:— | |||
| 936 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 936 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 936 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 936 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 936 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\AvailabilityDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 936 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 936 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFed82b.TMP | — | |
MD5:— | SHA256:— | |||
| 936 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RFed6b4.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
46
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2900 | Ninite Zoom Installer.exe | GET | 304 | 67.27.159.126:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | — | — | whitelisted |
2084 | AcroRd32.exe | GET | 304 | 2.16.177.123:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
2084 | AcroRd32.exe | GET | 304 | 2.16.177.123:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
2084 | AcroRd32.exe | GET | 304 | 2.16.177.123:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/279_15_23_20070.zip | unknown | — | — | whitelisted |
2084 | AcroRd32.exe | GET | 304 | 2.16.177.123:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
2900 | Ninite Zoom Installer.exe | GET | 200 | 99.84.158.104:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
2900 | Ninite Zoom Installer.exe | GET | 200 | 99.84.158.217:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
2900 | Ninite Zoom Installer.exe | GET | 200 | 99.84.158.42:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEAifaueiPpzwZvk3zBnQBZQ%3D | US | der | 471 b | whitelisted |
2900 | Ninite Zoom Installer.exe | GET | 200 | 99.84.158.126:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
936 | chrome.exe | GET | 304 | 67.27.159.126:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1716 | chrome.exe | 52.7.124.208:443 | ninite.com | Amazon.com, Inc. | US | unknown |
1716 | chrome.exe | 172.217.21.206:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
1716 | chrome.exe | 172.217.22.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1716 | chrome.exe | 172.217.22.68:443 | www.google.com | Google Inc. | US | whitelisted |
2900 | Ninite Zoom Installer.exe | 99.84.158.104:80 | ocsp.rootg2.amazontrust.com | AT&T Services, Inc. | US | whitelisted |
936 | chrome.exe | 67.27.159.126:80 | www.download.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
2900 | Ninite Zoom Installer.exe | 99.84.158.217:80 | ocsp.rootg2.amazontrust.com | AT&T Services, Inc. | US | whitelisted |
1716 | chrome.exe | 172.217.22.67:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2900 | Ninite Zoom Installer.exe | 107.20.104.77:443 | ninite.com | Amazon.com, Inc. | US | unknown |
2900 | Ninite Zoom Installer.exe | 99.84.158.126:80 | o.ss2.us | AT&T Services, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ninite.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| malicious |
www.download.windowsupdate.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
Threats
Process | Message |
|---|---|
MsiExec.exe | [CZoomProductPathHelper::RecursiveRemoveDirA] Path is: |
MsiExec.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Zoom |
MsiExec.exe | [CZoomProductPathHelper::RecursiveRemoveDirA] Path is: |
MsiExec.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Zoom |
MsiExec.exe | C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Zoom |
MsiExec.exe | C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Zoom |
Zoom.exe | Parse Text. Load file success! String counts:4687.
|
Zoom.exe | Menu Item: ID:10014, Value:P??????
|
Zoom.exe | Menu Item: ID:-1, Value:Sign in
|
Zoom.exe | Menu Item: ID:-1, Value:
|