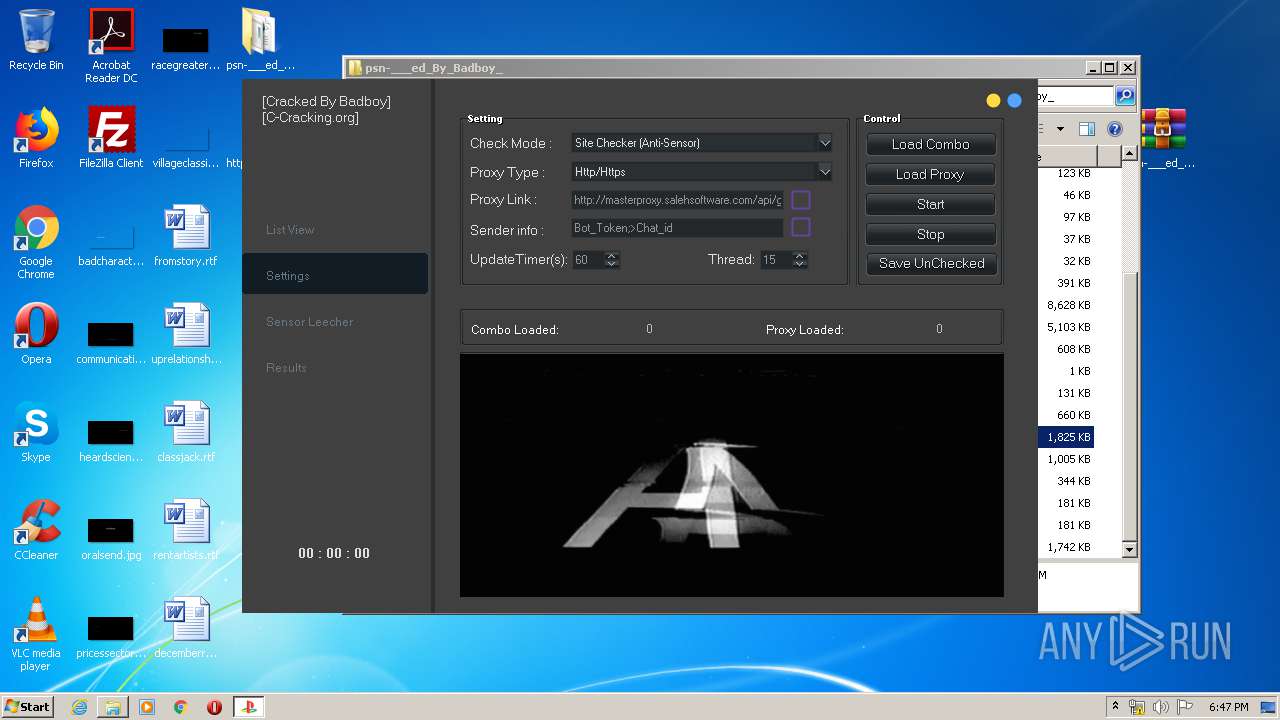
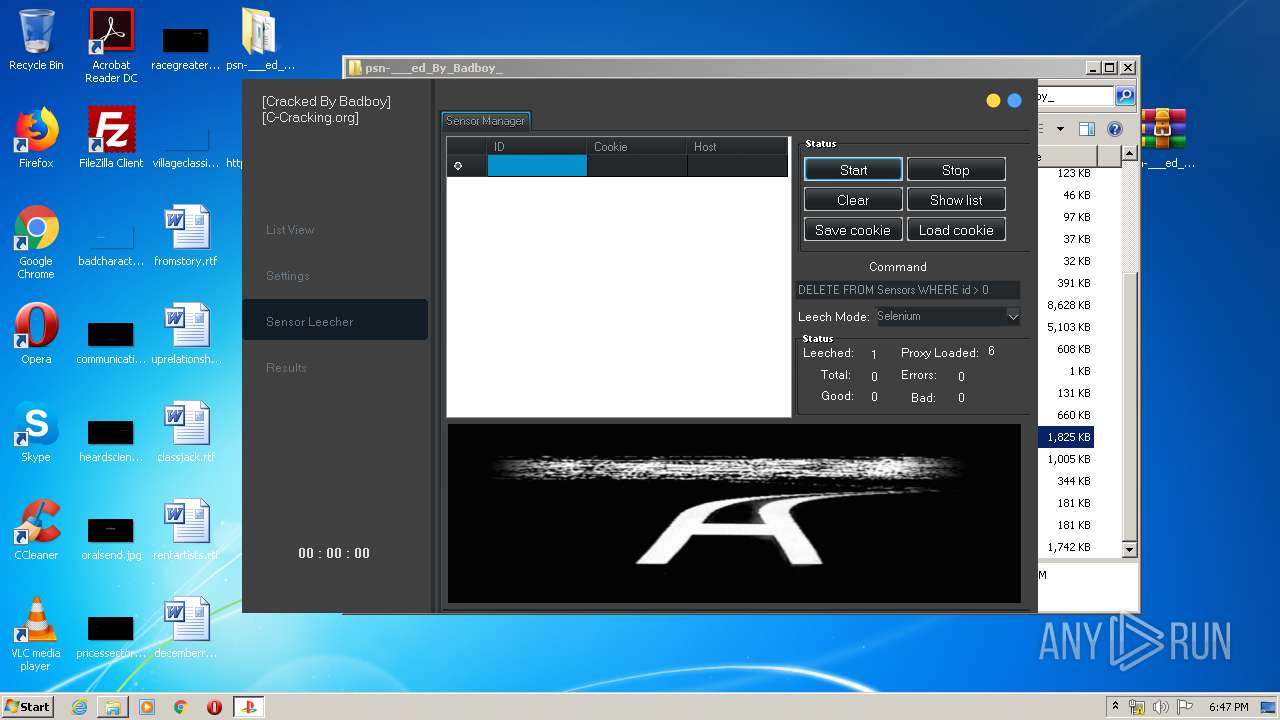
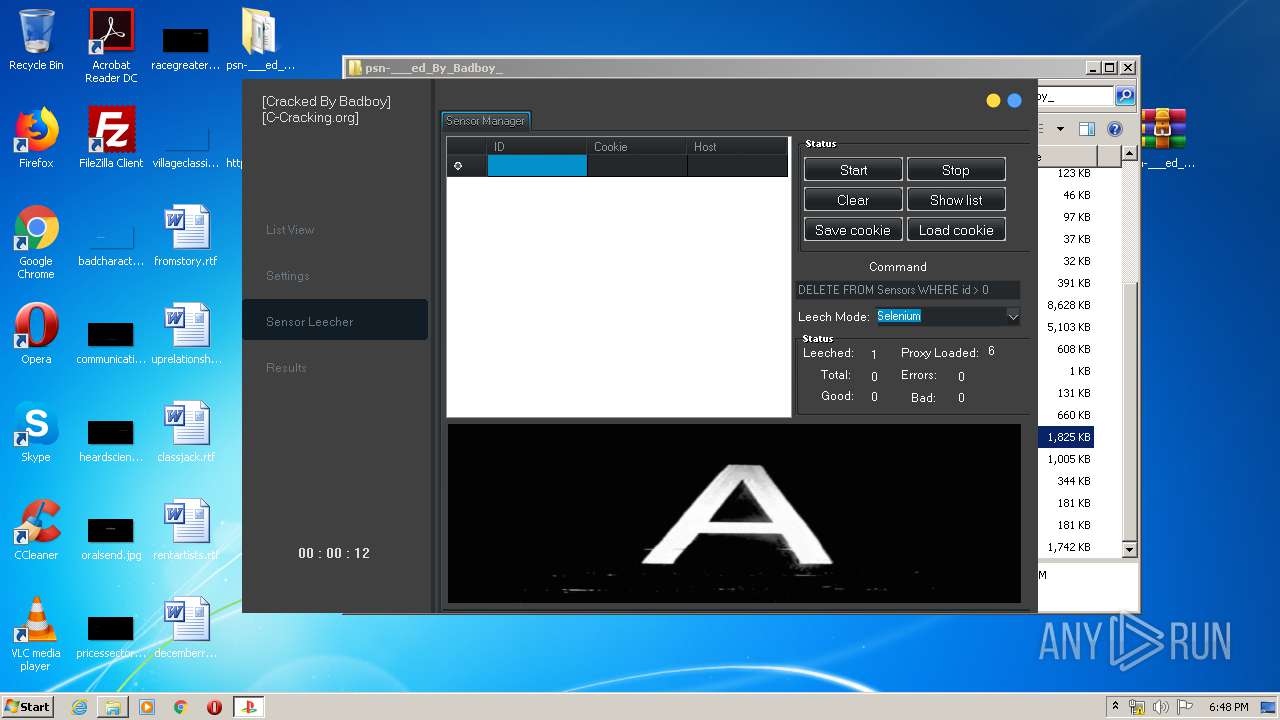
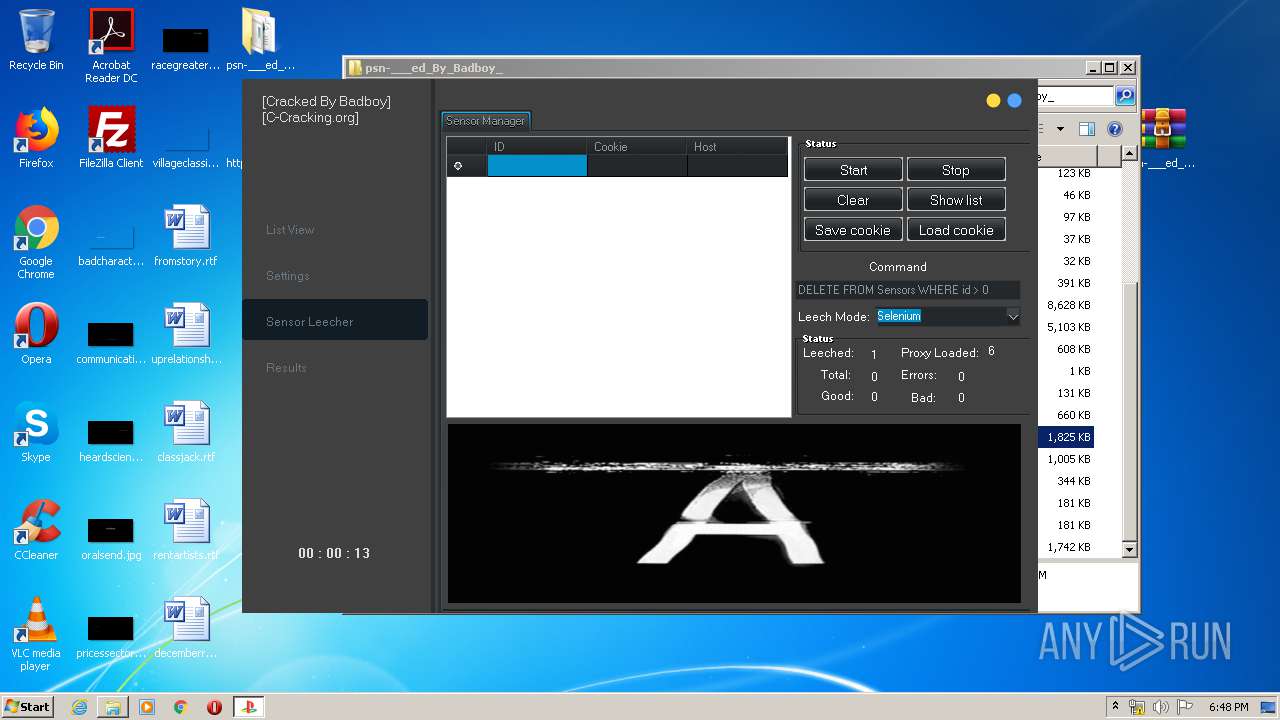
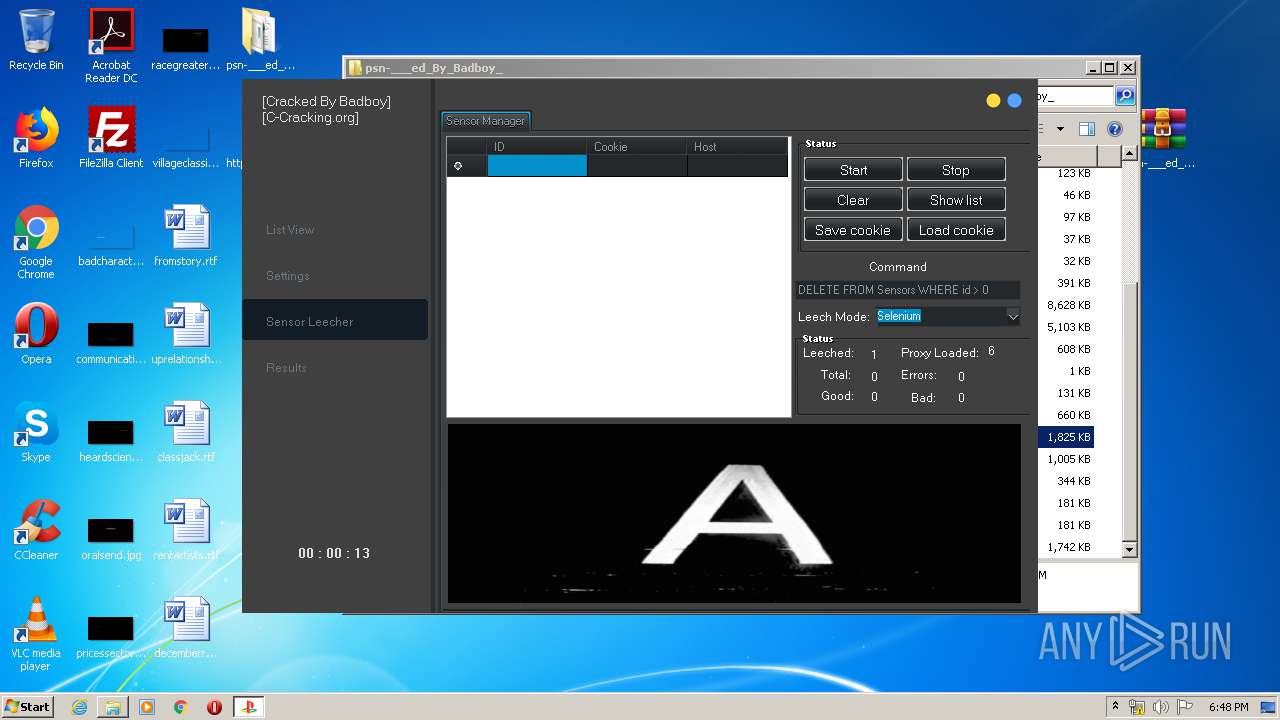
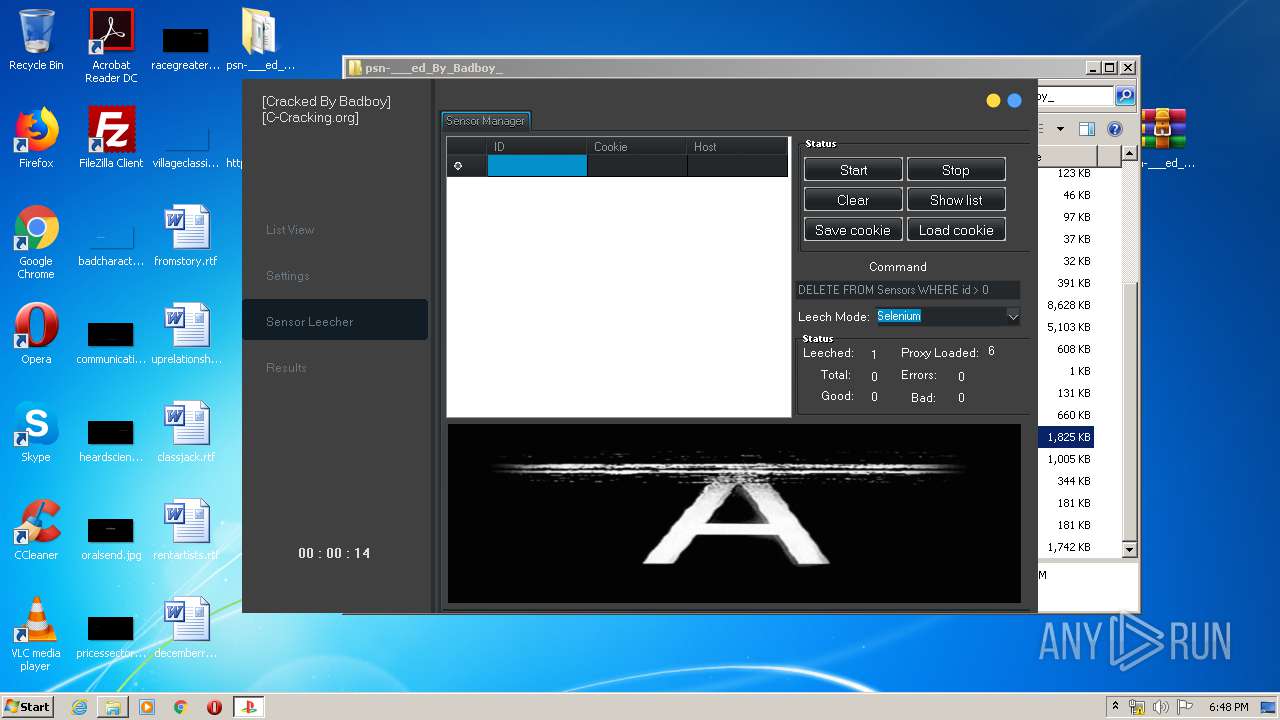
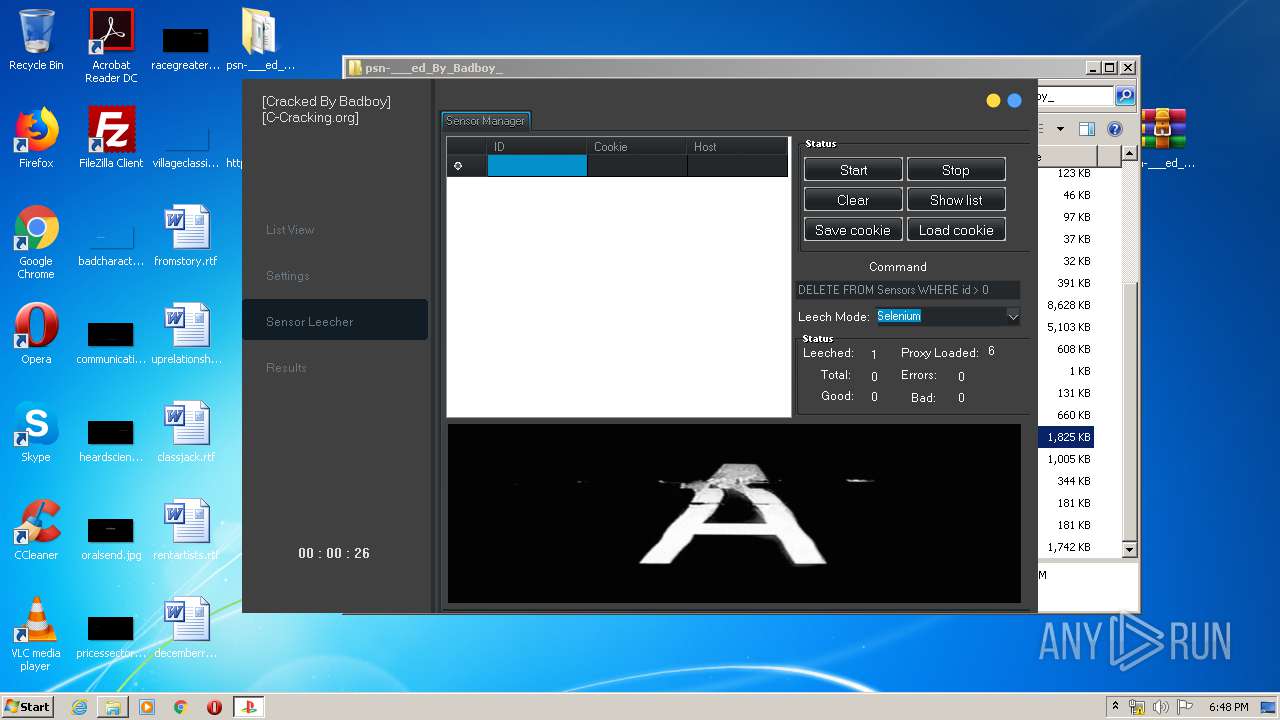
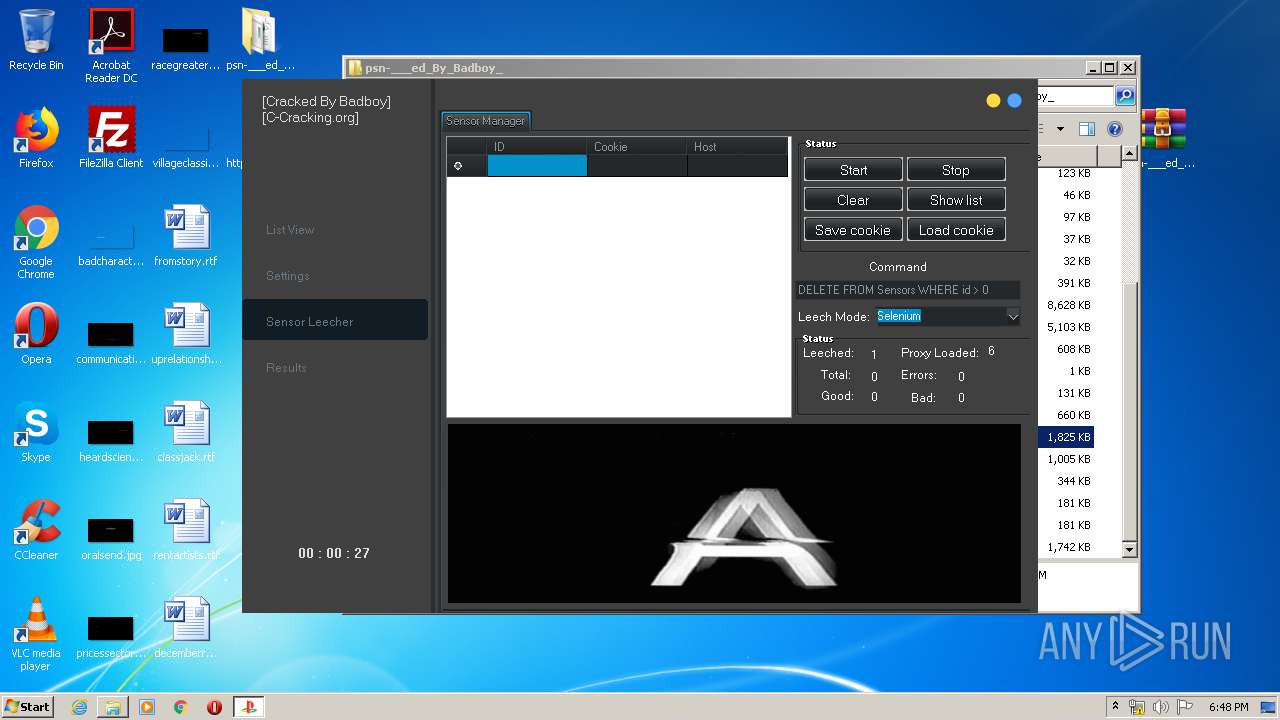
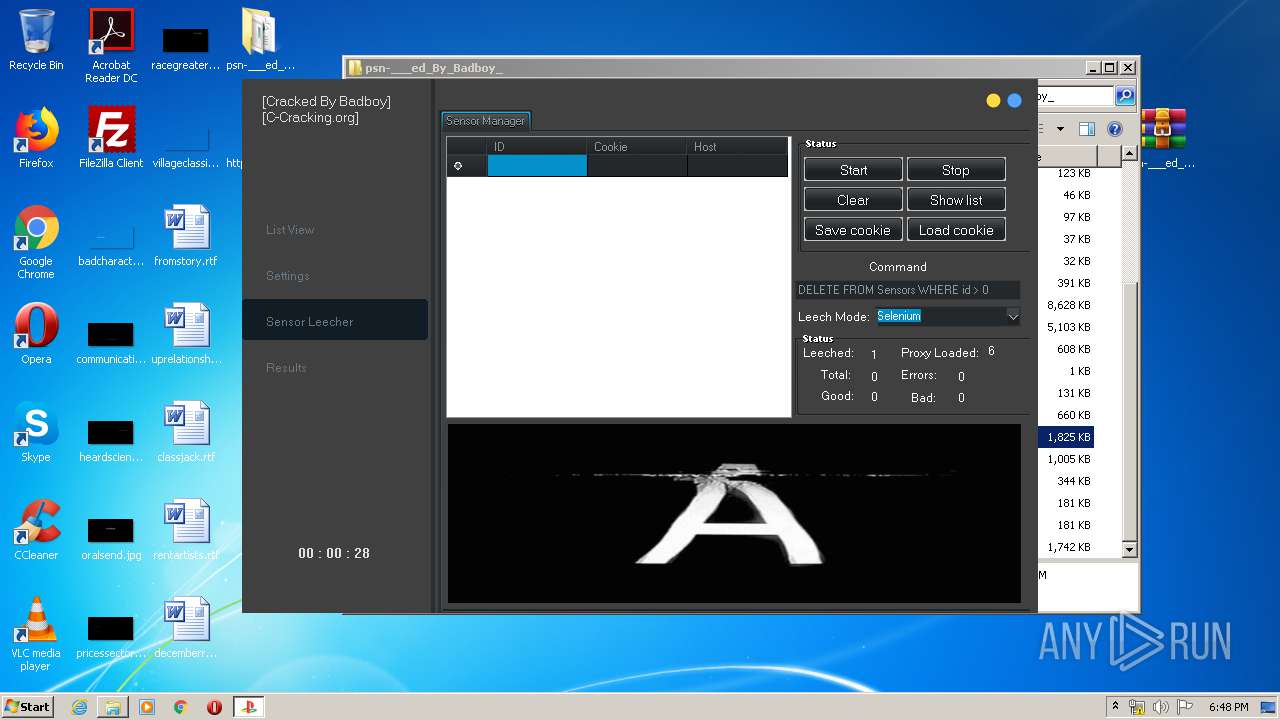
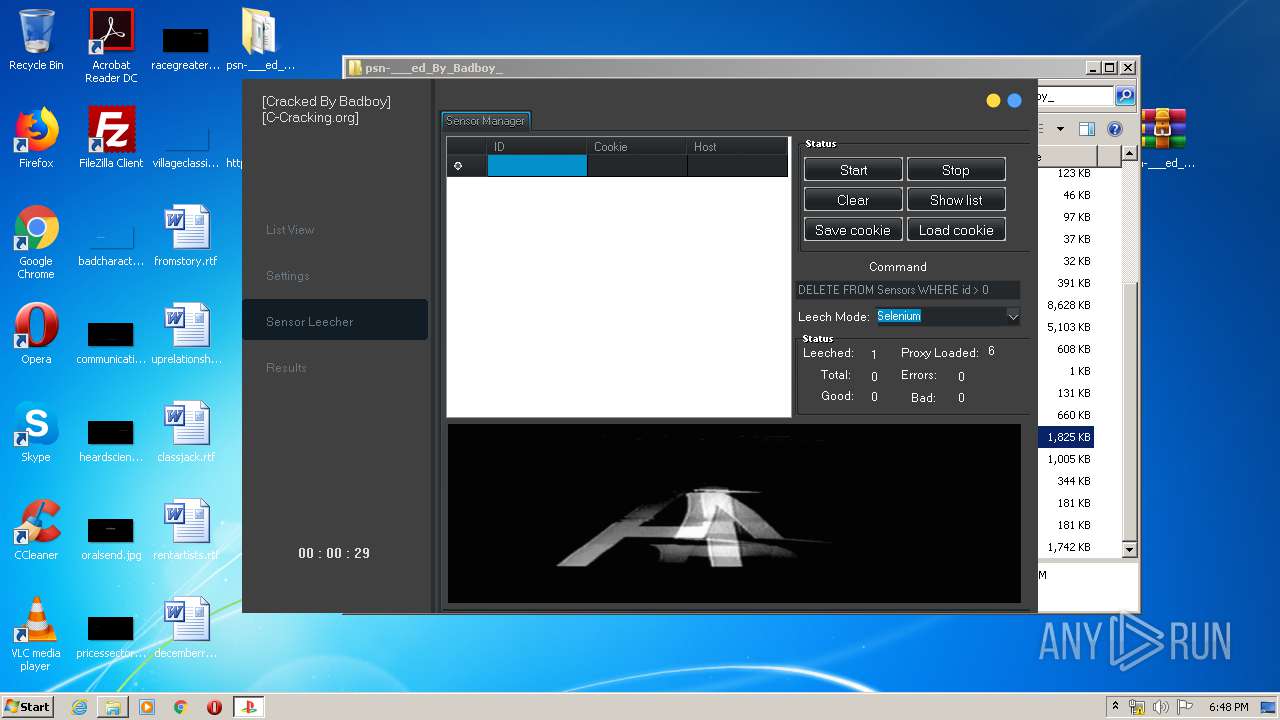
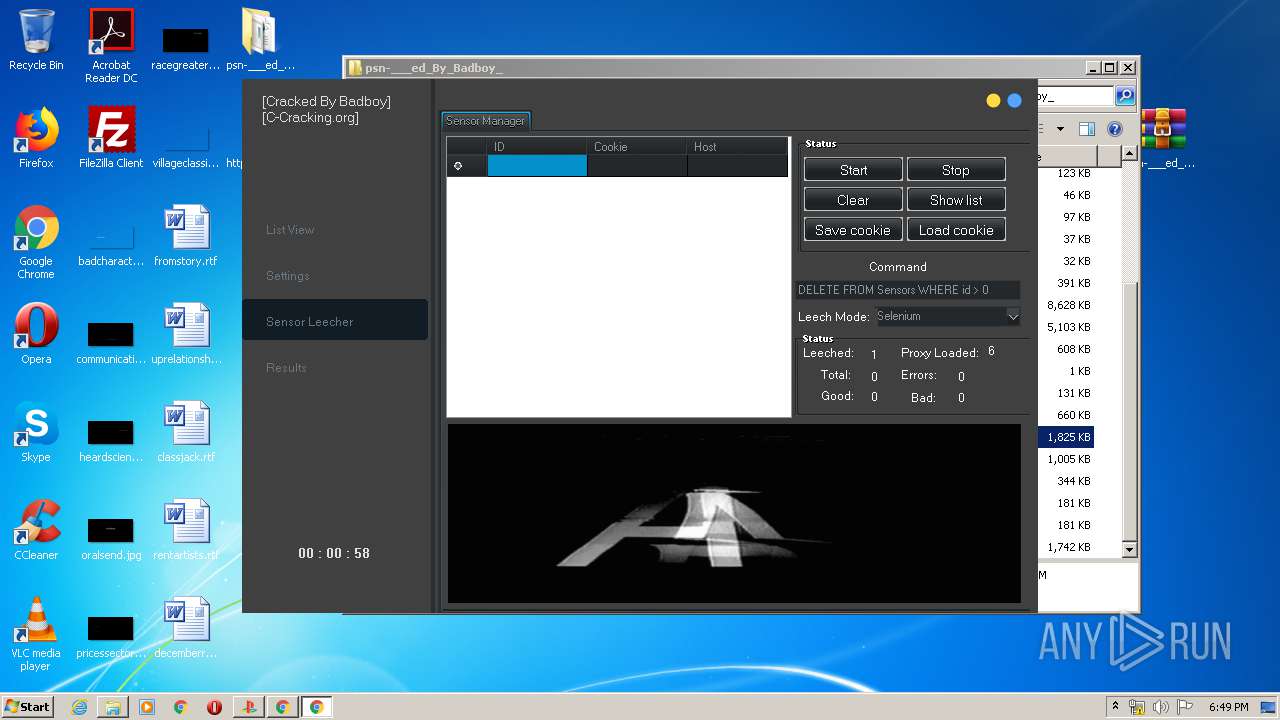
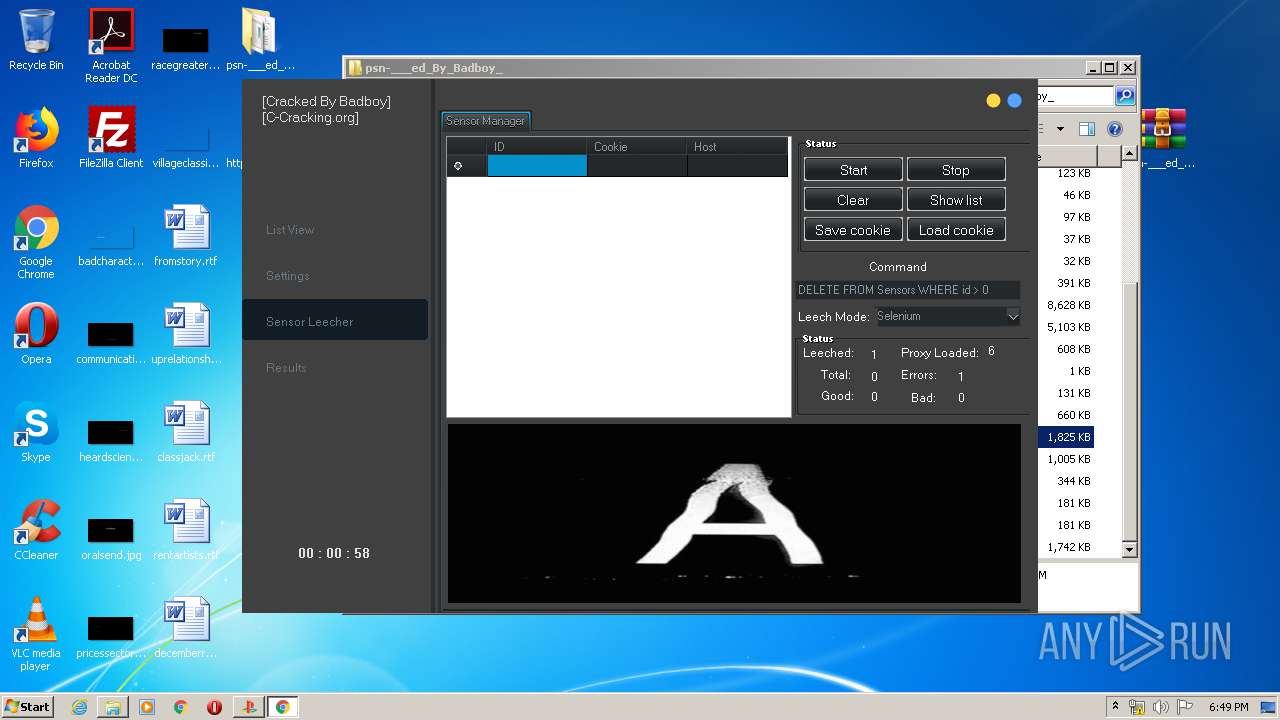
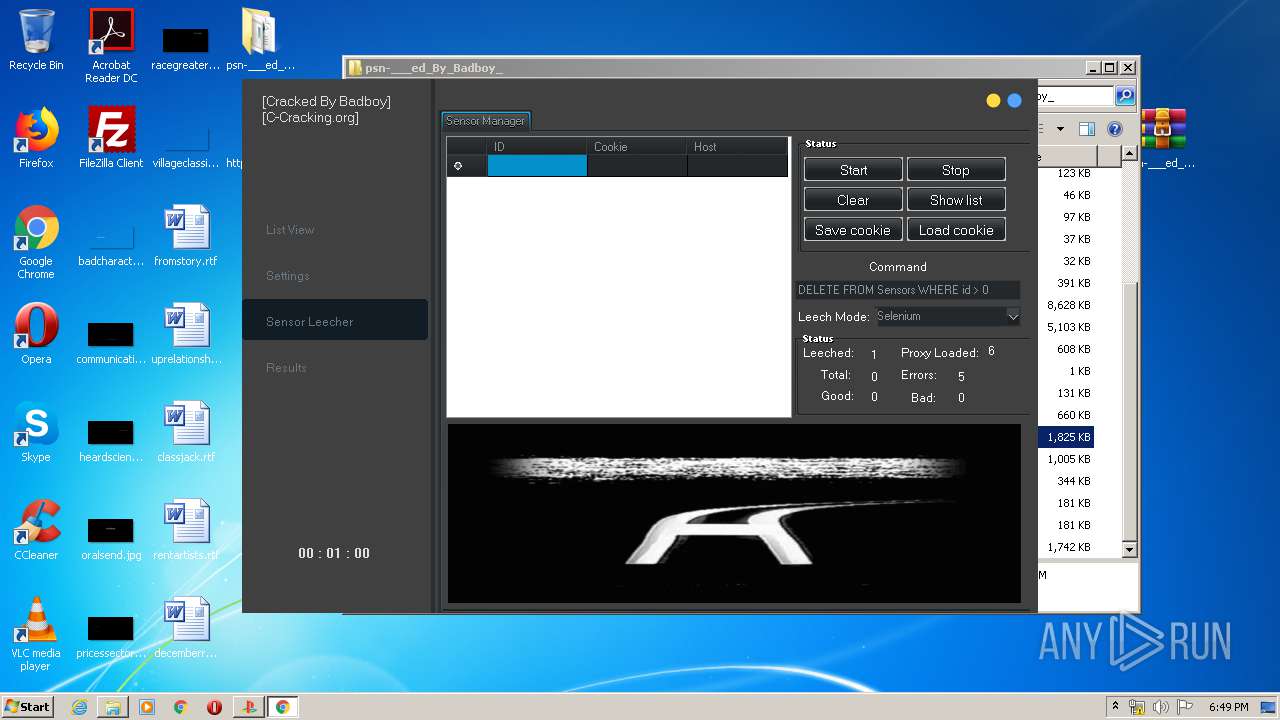
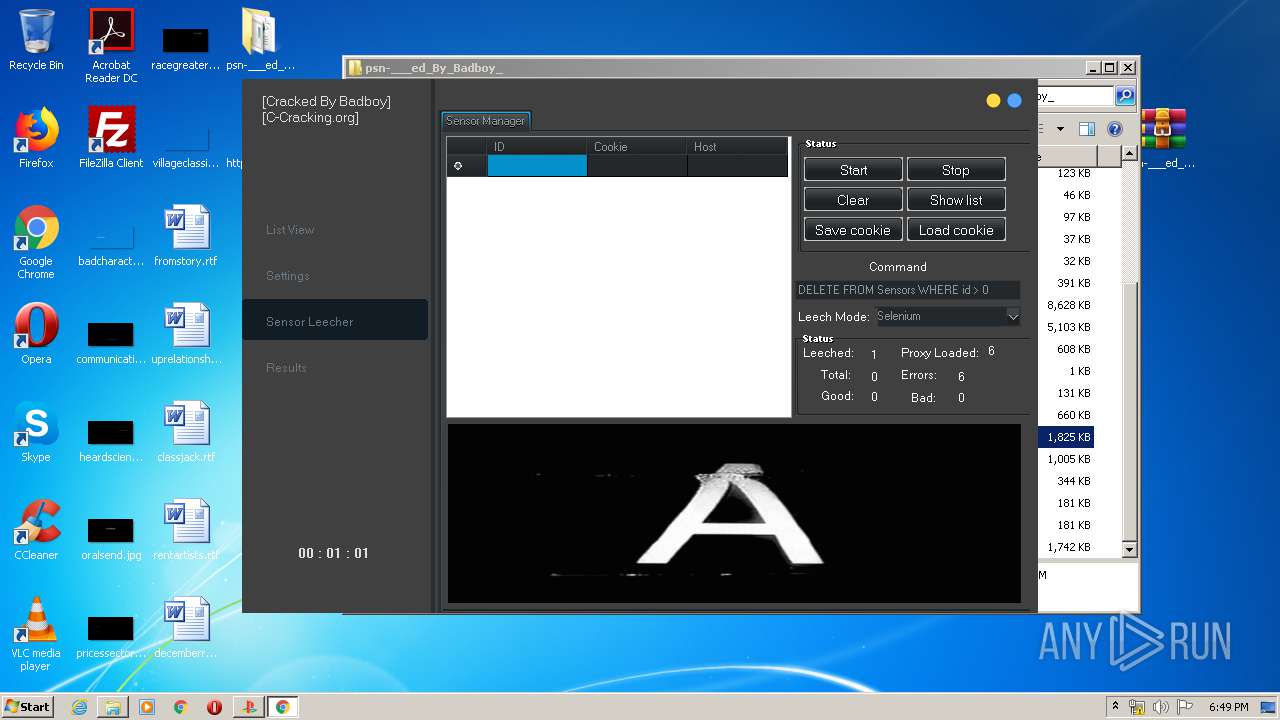
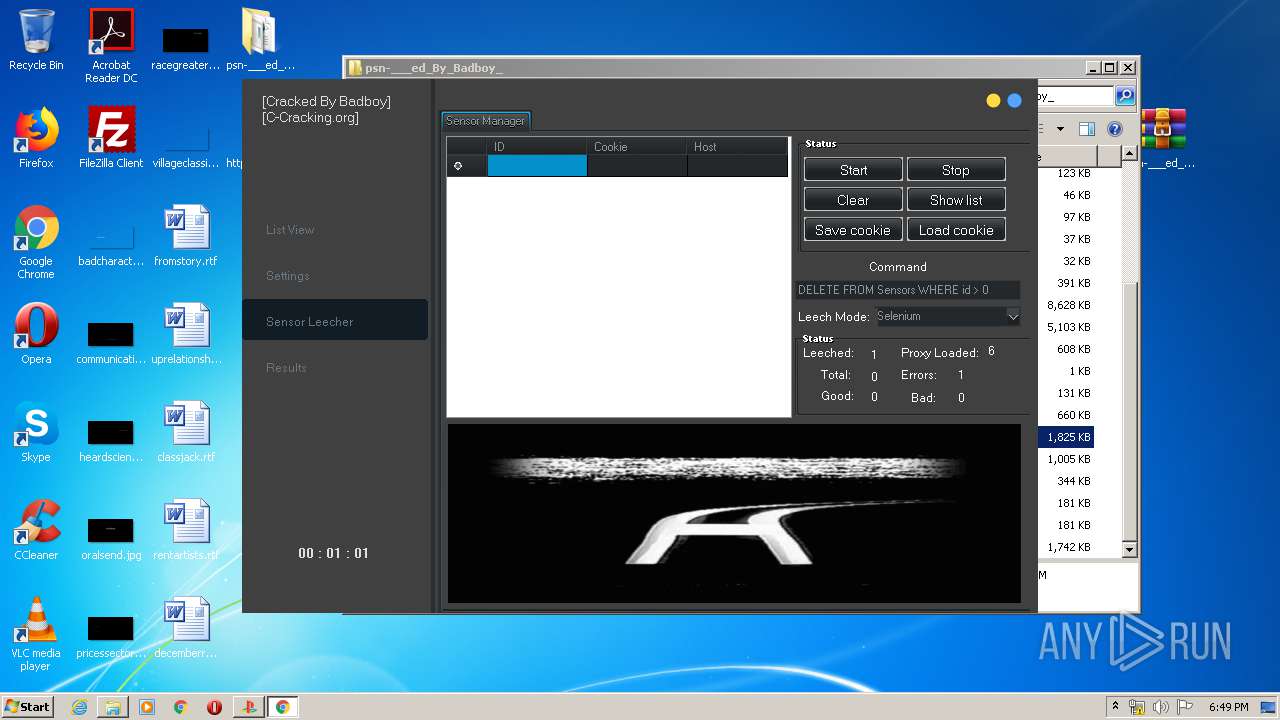
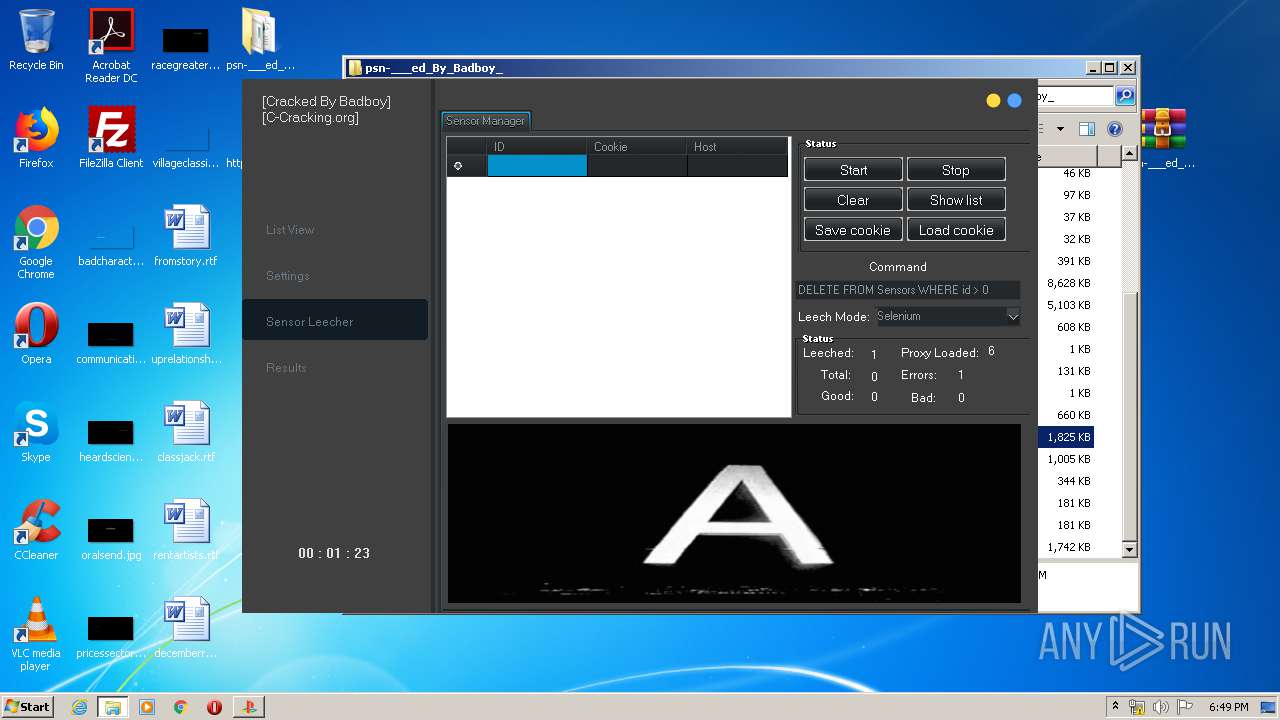
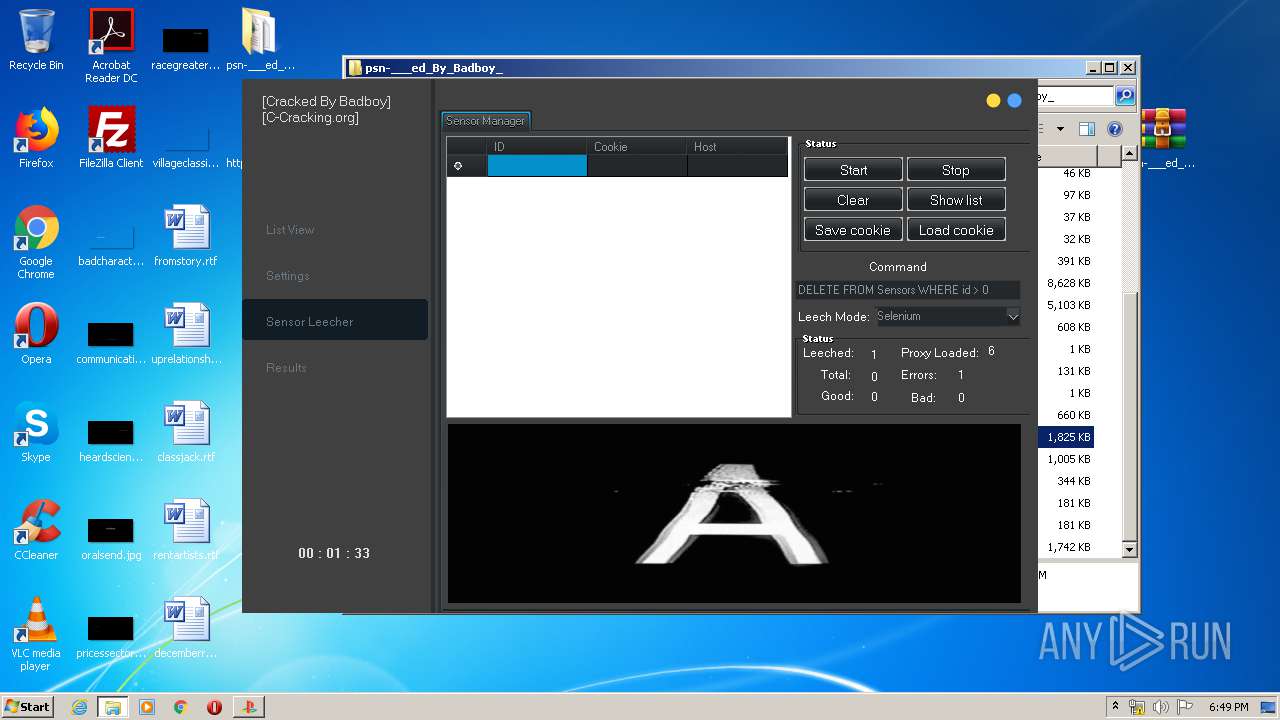
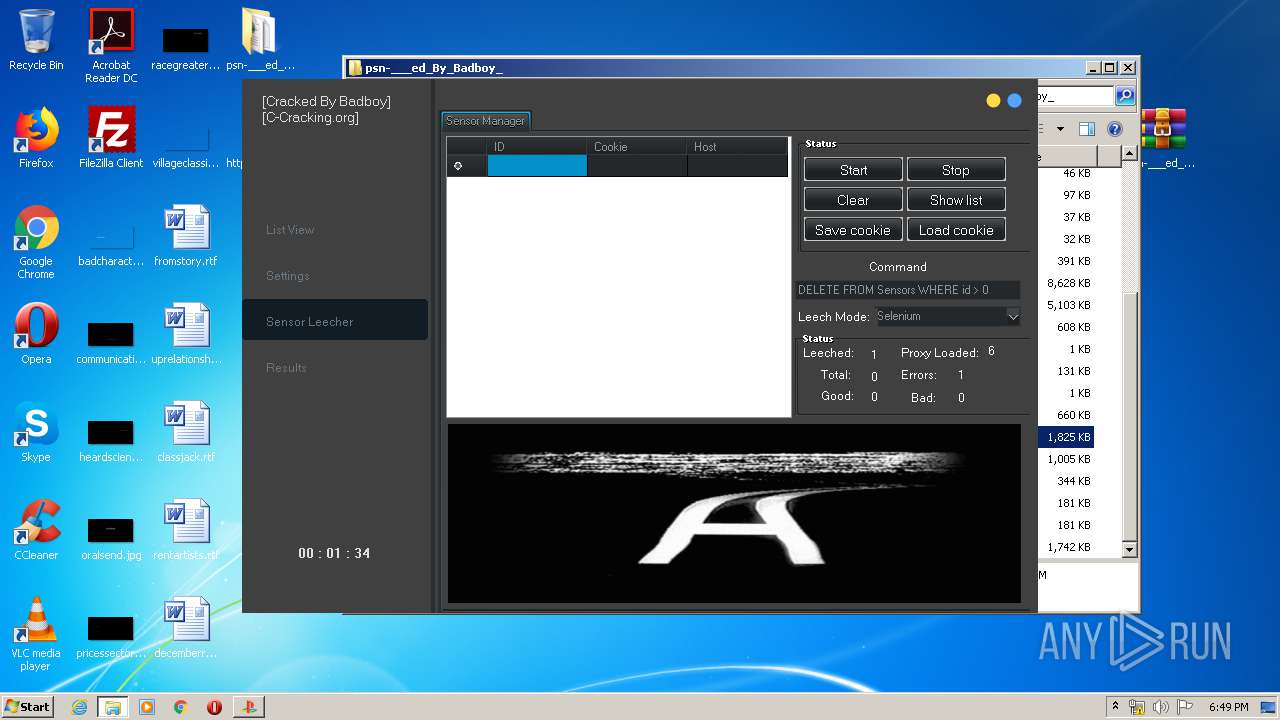
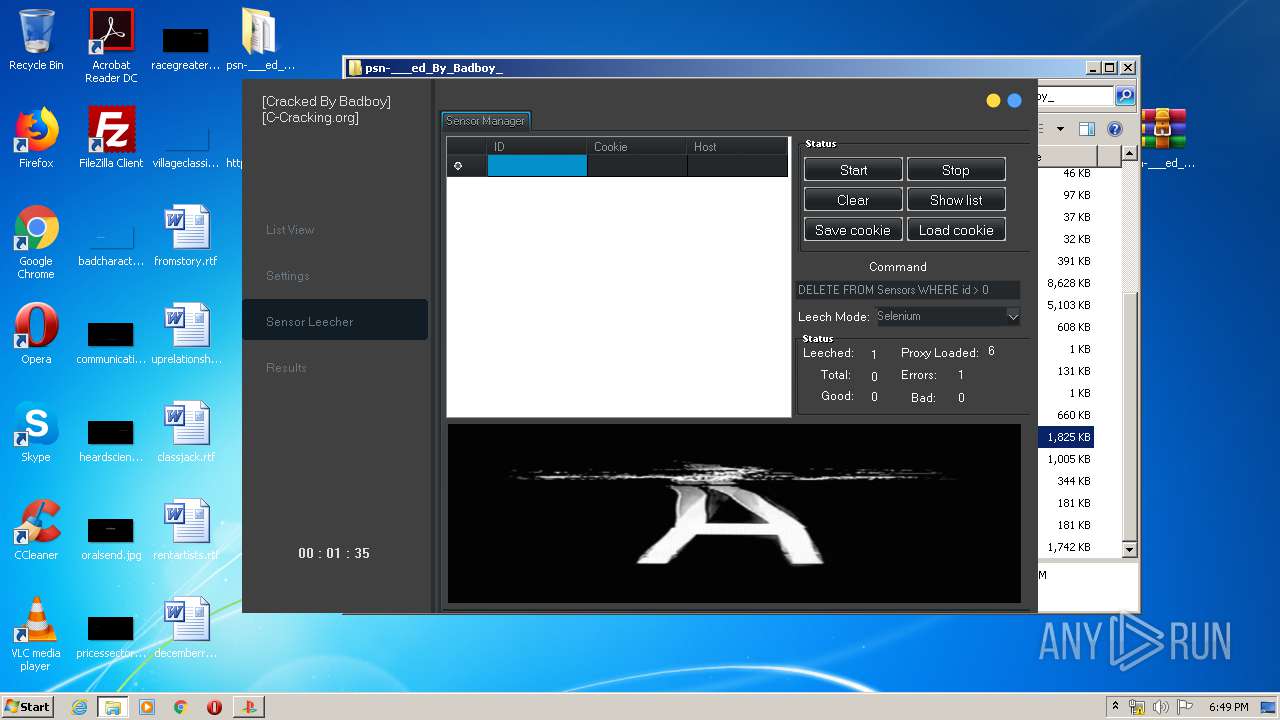
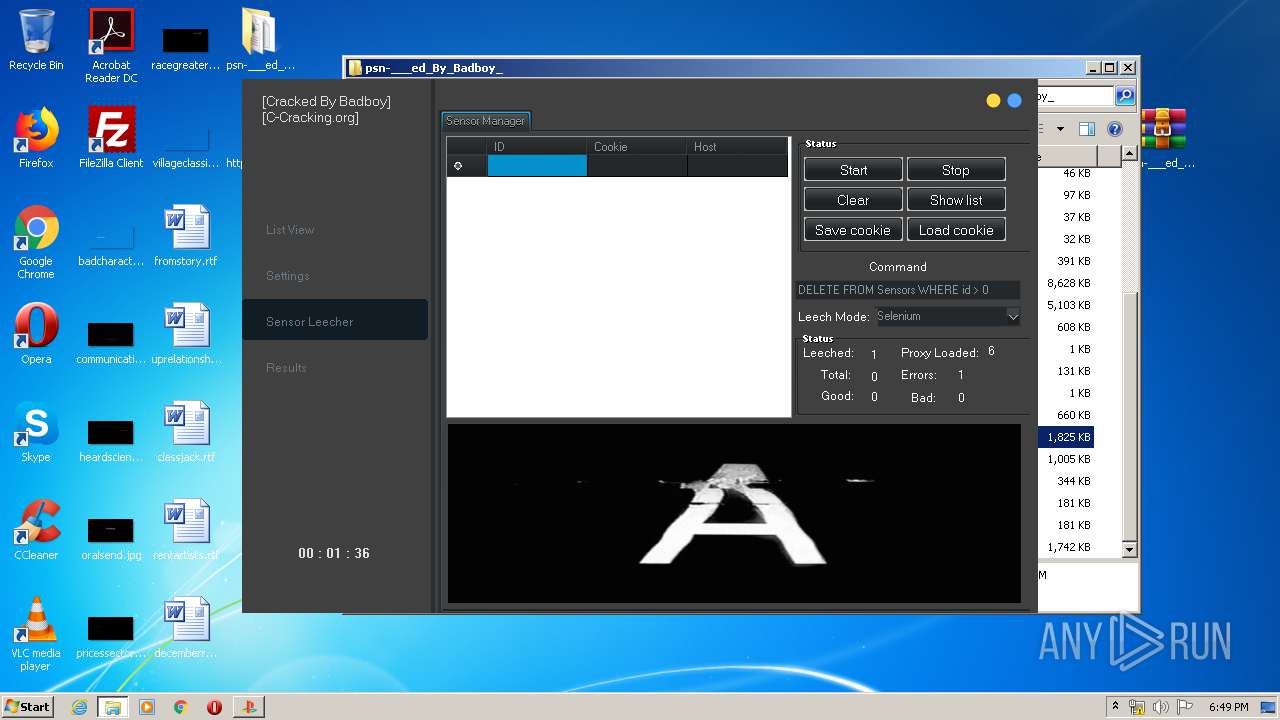
| URL: | https://www.upload.ee/files/10980764/psn-___ed_By_Badboy_.rar.html |
| Full analysis: | https://app.any.run/tasks/bc9c3c04-5891-434f-9c39-2c6b5848f475 |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2020, 18:44:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 43750E6A50D5FDD46EA65DD22F53CC7B |
| SHA1: | 556D4C4C94EA2716F2AB084DCD9EC094B77F2E22 |
| SHA256: | 222F45EF00711FE10119A82DB0B76F5D89CF6CD2738823876D266B5E5530BC49 |
| SSDEEP: | 3:N8DSLr7MJmU6OOMH6QLnaGn:2OLr0OOO8TaGn |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3548)
- PlayStation Checker - [Cracked By Badboy].exe (PID: 940)
Application was dropped or rewritten from another process
- chromedriver.exe (PID: 608)
- chromedriver.exe (PID: 3796)
- chromedriver.exe (PID: 2580)
- PlayStation Checker - [Cracked By Badboy].exe (PID: 940)
- chromedriver.exe (PID: 1352)
- chromedriver.exe (PID: 2988)
- chromedriver.exe (PID: 2708)
- chromedriver.exe (PID: 3360)
- chromedriver.exe (PID: 3892)
- chromedriver.exe (PID: 3684)
- chromedriver.exe (PID: 1504)
- chromedriver.exe (PID: 3760)
- chromedriver.exe (PID: 1904)
- chromedriver.exe (PID: 1440)
- chromedriver.exe (PID: 3956)
- chromedriver.exe (PID: 8020)
- chromedriver.exe (PID: 7804)
- chromedriver.exe (PID: 7400)
- chromedriver.exe (PID: 4364)
- chromedriver.exe (PID: 6072)
- chromedriver.exe (PID: 7700)
- chromedriver.exe (PID: 4528)
- chromedriver.exe (PID: 4556)
- chromedriver.exe (PID: 880)
- chromedriver.exe (PID: 1064)
- chromedriver.exe (PID: 3228)
- chromedriver.exe (PID: 4508)
- chromedriver.exe (PID: 5400)
- chromedriver.exe (PID: 7428)
- chromedriver.exe (PID: 6744)
- chromedriver.exe (PID: 4908)
- chromedriver.exe (PID: 1760)
SUSPICIOUS
Creates files in the program directory
- firefox.exe (PID: 2808)
- chrome.exe (PID: 4308)
Executable content was dropped or overwritten
- PlayStation Checker - [Cracked By Badboy].exe (PID: 940)
- WinRAR.exe (PID: 2248)
INFO
Application launched itself
- firefox.exe (PID: 2808)
- firefox.exe (PID: 2976)
- chrome.exe (PID: 4080)
- chrome.exe (PID: 2900)
- chrome.exe (PID: 3380)
- chrome.exe (PID: 2864)
- chrome.exe (PID: 3132)
- chrome.exe (PID: 1136)
- chrome.exe (PID: 1704)
- chrome.exe (PID: 2716)
- chrome.exe (PID: 1688)
- chrome.exe (PID: 2128)
- chrome.exe (PID: 2668)
- chrome.exe (PID: 2520)
- chrome.exe (PID: 2448)
- chrome.exe (PID: 956)
- chrome.exe (PID: 4084)
- chrome.exe (PID: 3372)
- chrome.exe (PID: 7356)
- chrome.exe (PID: 3052)
- chrome.exe (PID: 7608)
- chrome.exe (PID: 2944)
- chrome.exe (PID: 7392)
Reads CPU info
- firefox.exe (PID: 2808)
Manual execution by user
- WinRAR.exe (PID: 2248)
- PlayStation Checker - [Cracked By Badboy].exe (PID: 940)
Reads Internet Cache Settings
- firefox.exe (PID: 2808)
- pingsender.exe (PID: 3888)
Creates files in the user directory
- firefox.exe (PID: 2808)
Reads the hosts file
- chrome.exe (PID: 4080)
- chrome.exe (PID: 3380)
- chrome.exe (PID: 2864)
- chrome.exe (PID: 1688)
- chrome.exe (PID: 2716)
- chrome.exe (PID: 2128)
- chrome.exe (PID: 956)
- chrome.exe (PID: 2668)
- chrome.exe (PID: 3132)
- chrome.exe (PID: 1136)
- chrome.exe (PID: 2520)
- chrome.exe (PID: 2448)
- chrome.exe (PID: 2900)
- chrome.exe (PID: 1704)
- chrome.exe (PID: 4084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
223
Monitored processes
144
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 604 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2808.20.703282185\1653837285" -childID 3 -isForBrowser -prefsHandle 3728 -prefMapHandle 3864 -prefsLen 7129 -prefMapSize 191824 -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 2808 "\\.\pipe\gecko-crash-server-pipe.2808" 3876 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 608 | "C:\Users\admin\Desktop\psn-___ed_By_Badboy_\chromedriver.exe" --port=52031 | C:\Users\admin\Desktop\psn-___ed_By_Badboy_\chromedriver.exe | PlayStation Checker - [Cracked By Badboy].exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 820 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler --user-data-dir=C:\Users\admin\AppData\Local\Temp\scoped_dir3684_288225812 /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler --database=C:\Users\admin\AppData\Local\Temp\scoped_dir3684_288225812\Crashpad --metrics-dir=C:\Users\admin\AppData\Local\Temp\scoped_dir3684_288225812 --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x80,0x84,0x88,0x7c,0x8c,0x6d36a9d0,0x6d36a9e0,0x6d36a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 880 | "C:\Users\admin\Desktop\psn-___ed_By_Badboy_\chromedriver.exe" --port=53528 | C:\Users\admin\Desktop\psn-___ed_By_Badboy_\chromedriver.exe | — | PlayStation Checker - [Cracked By Badboy].exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
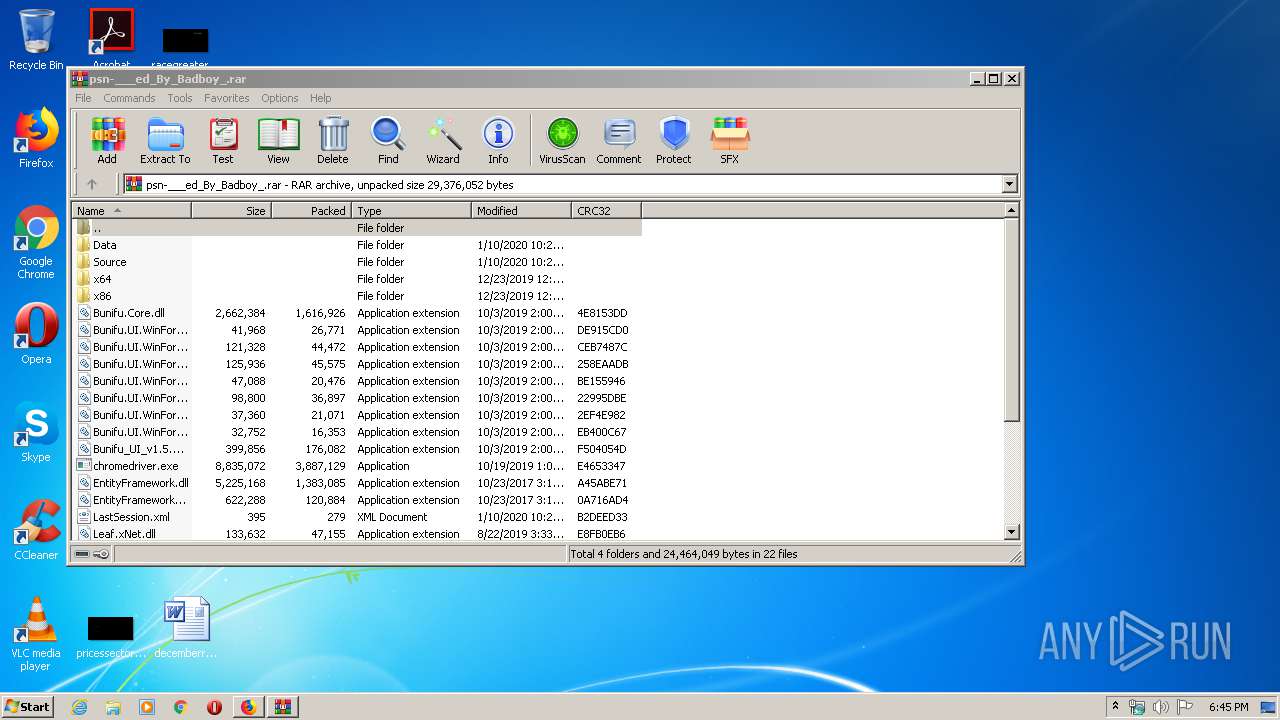
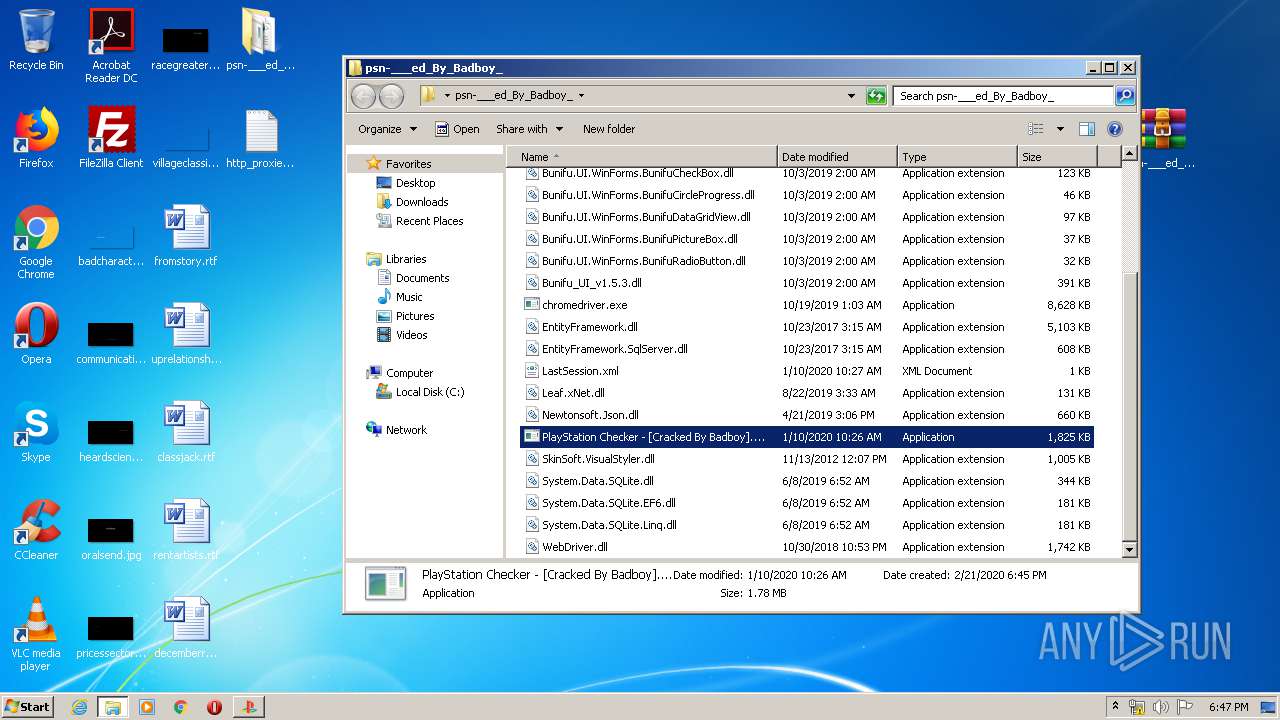
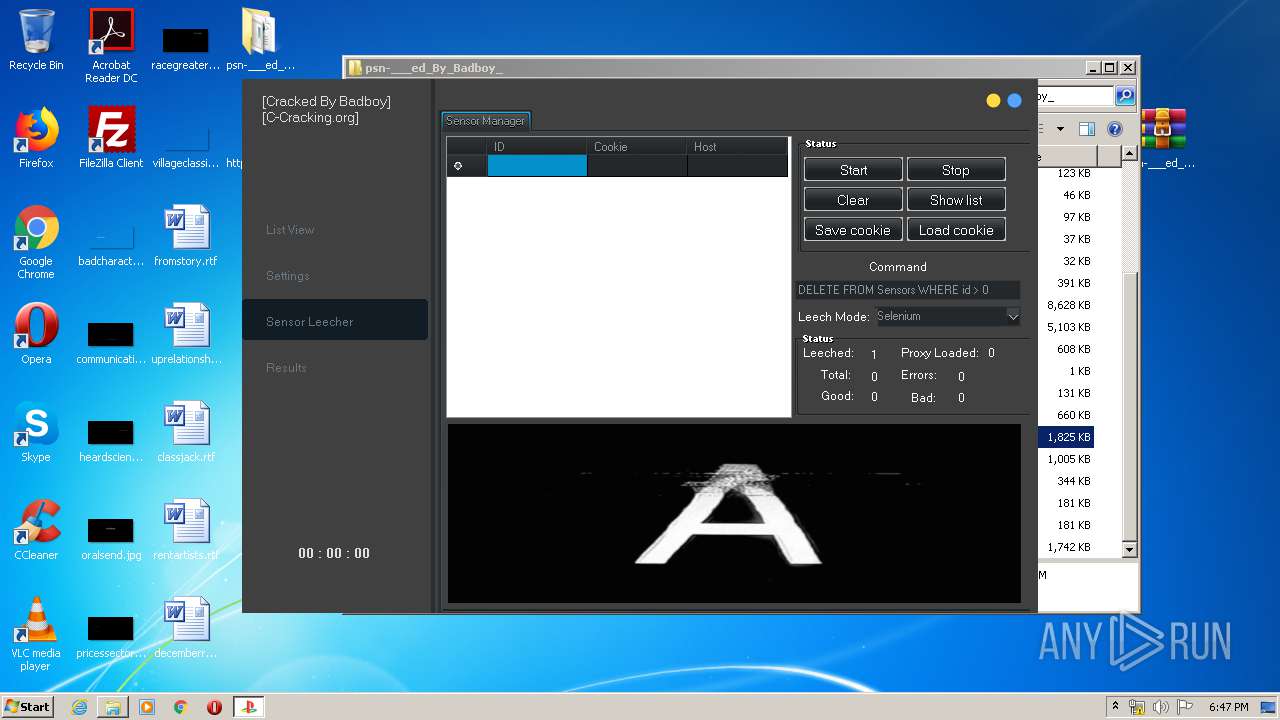
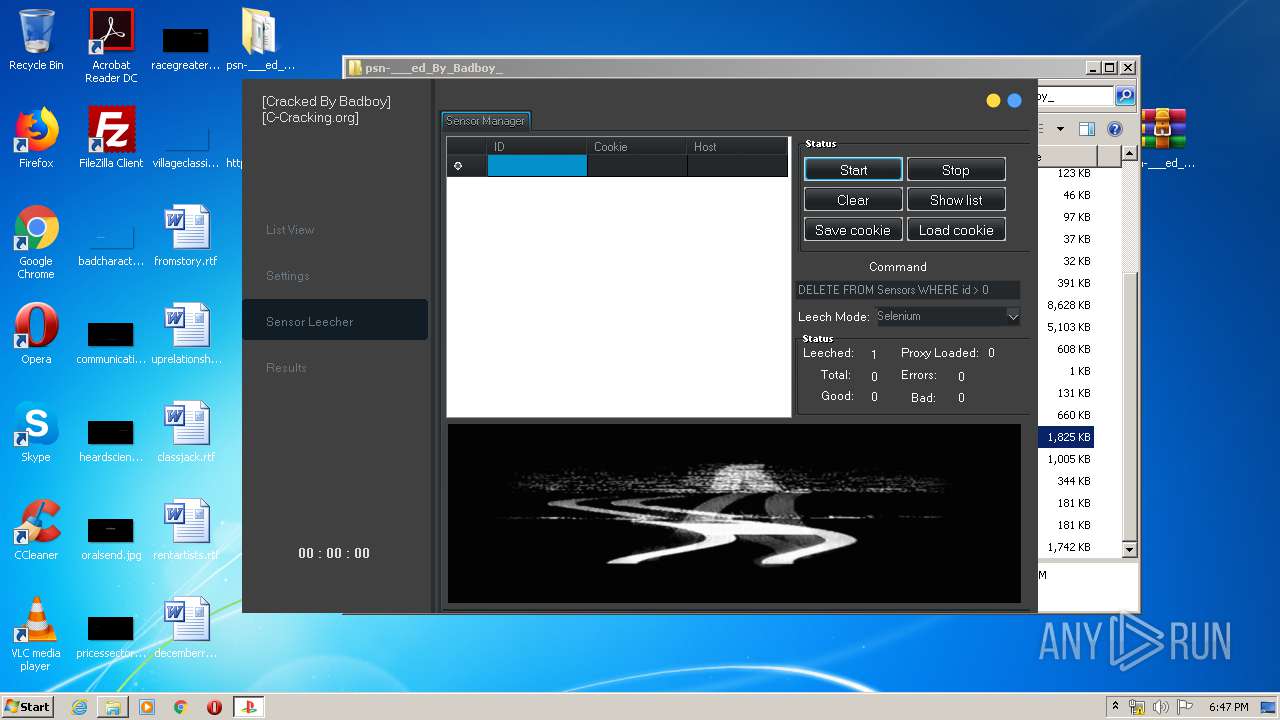
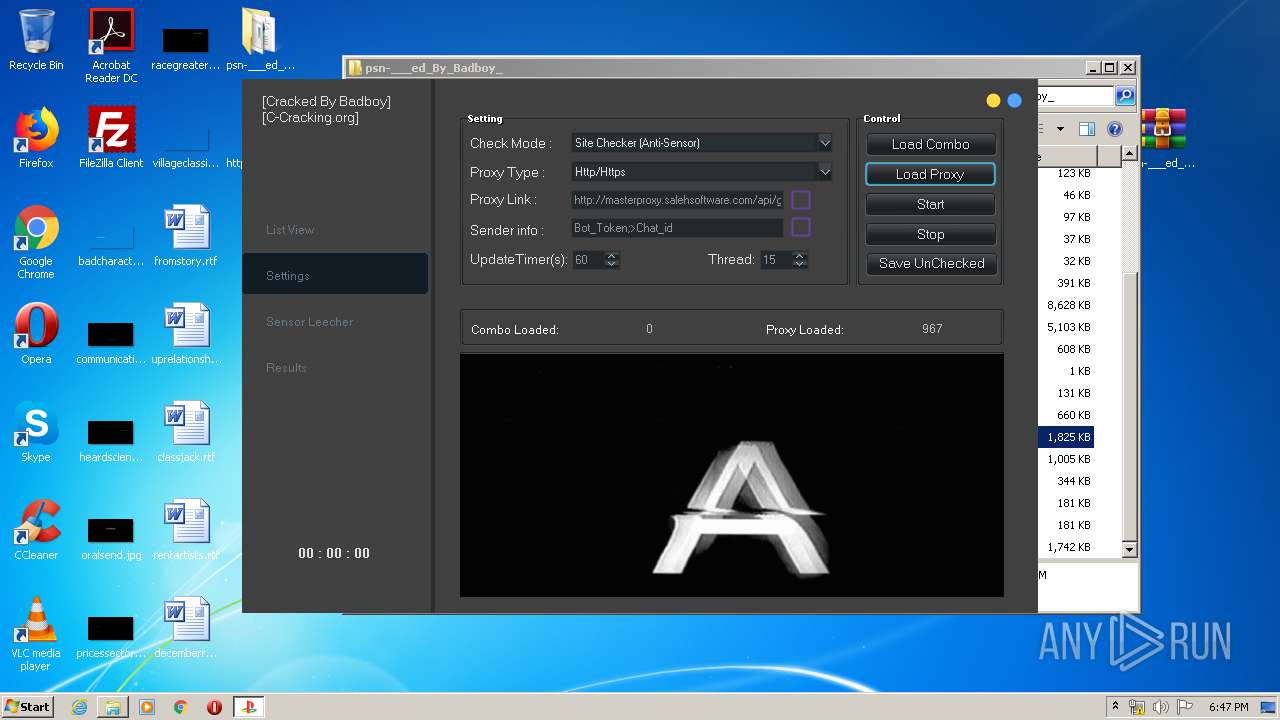
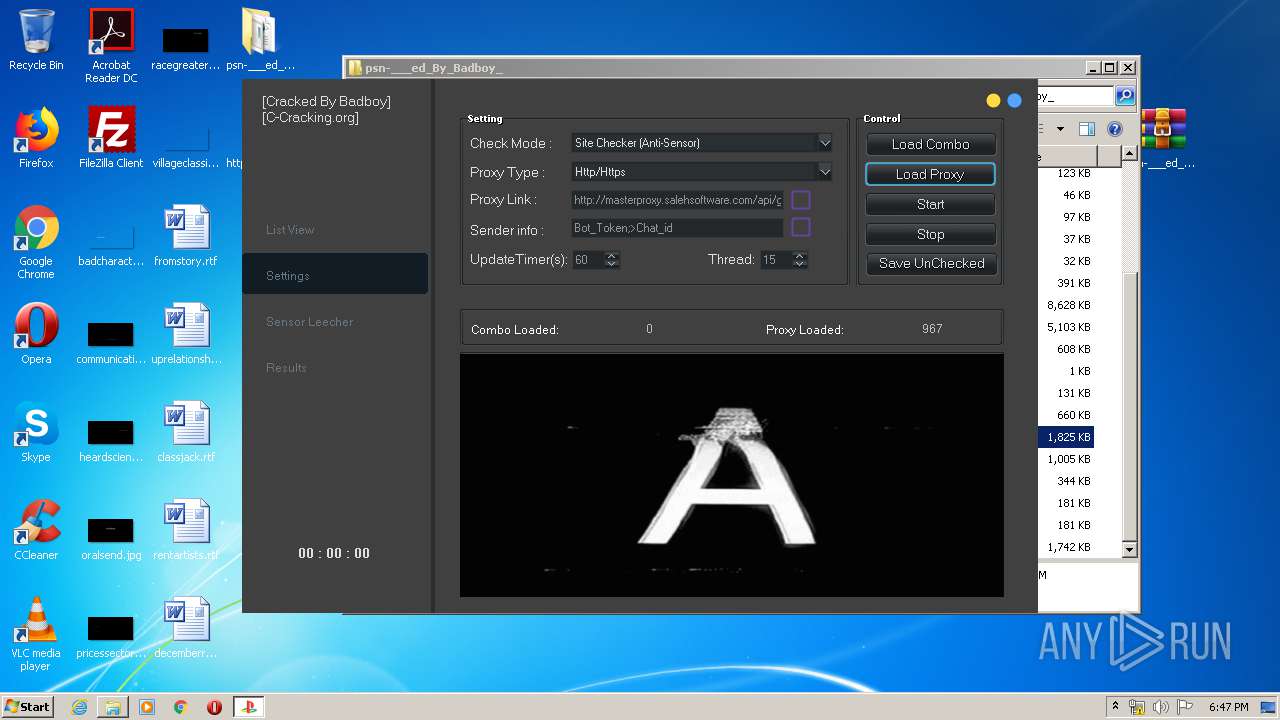
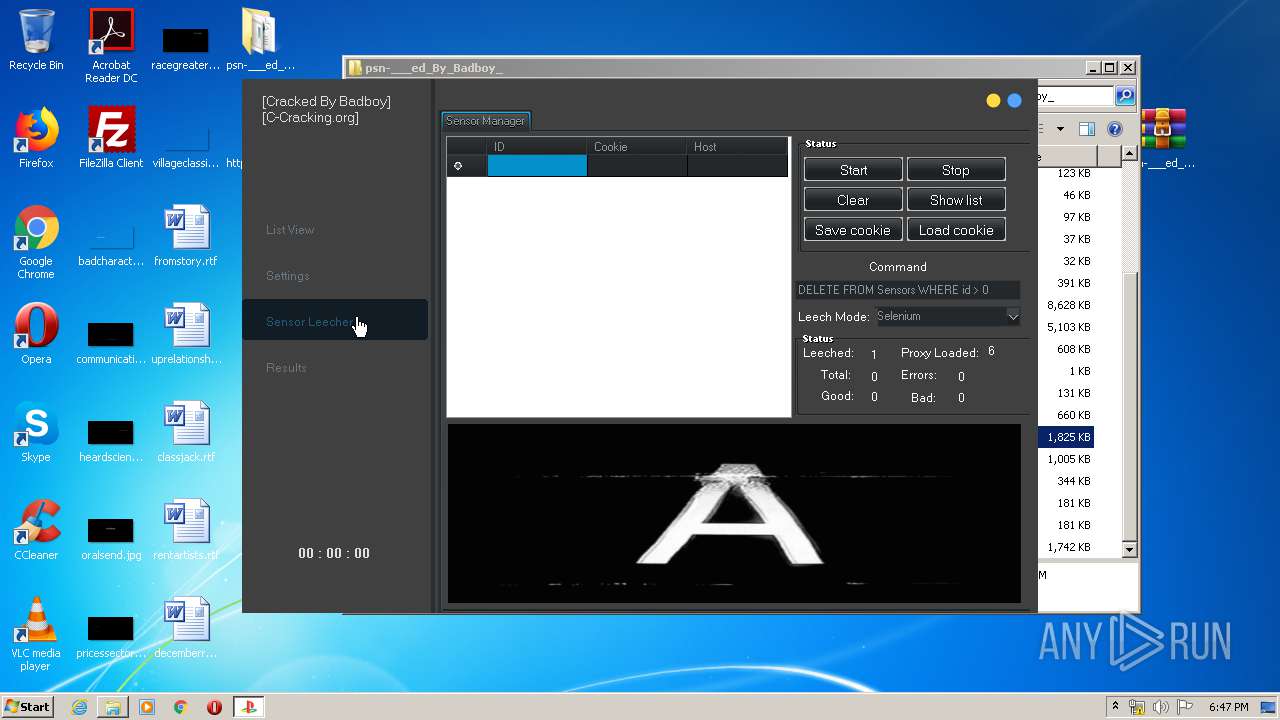
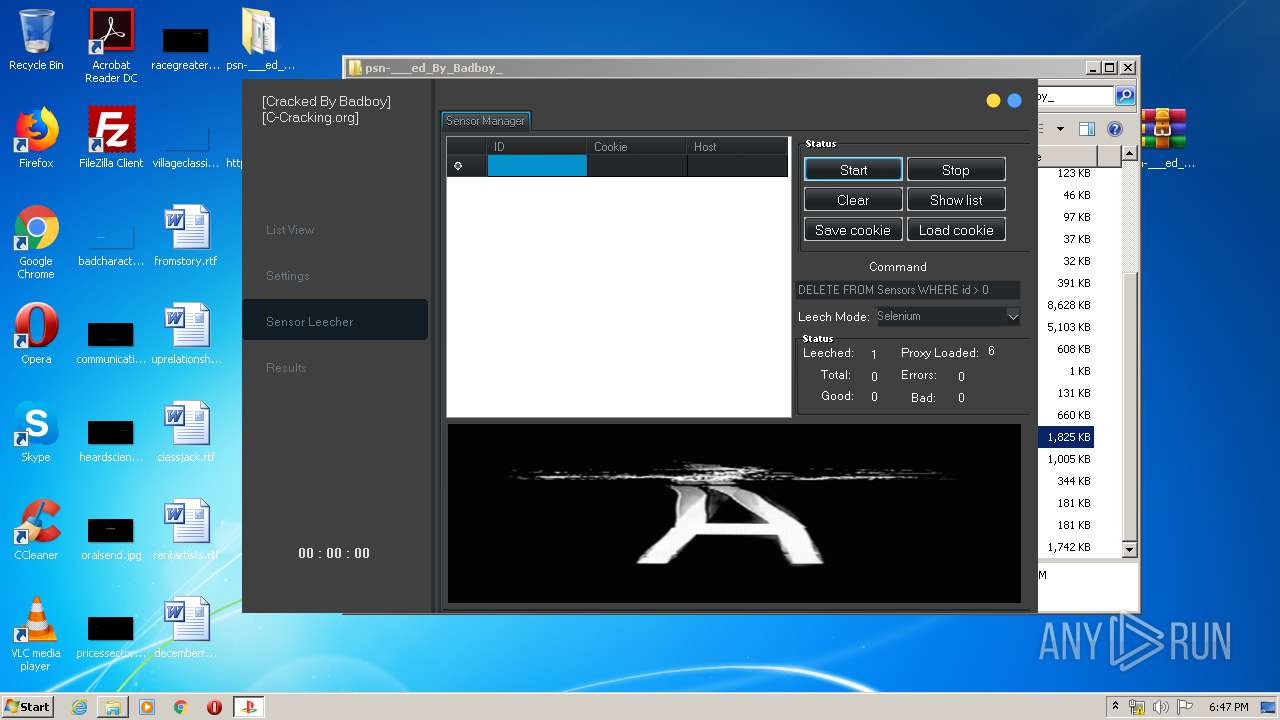
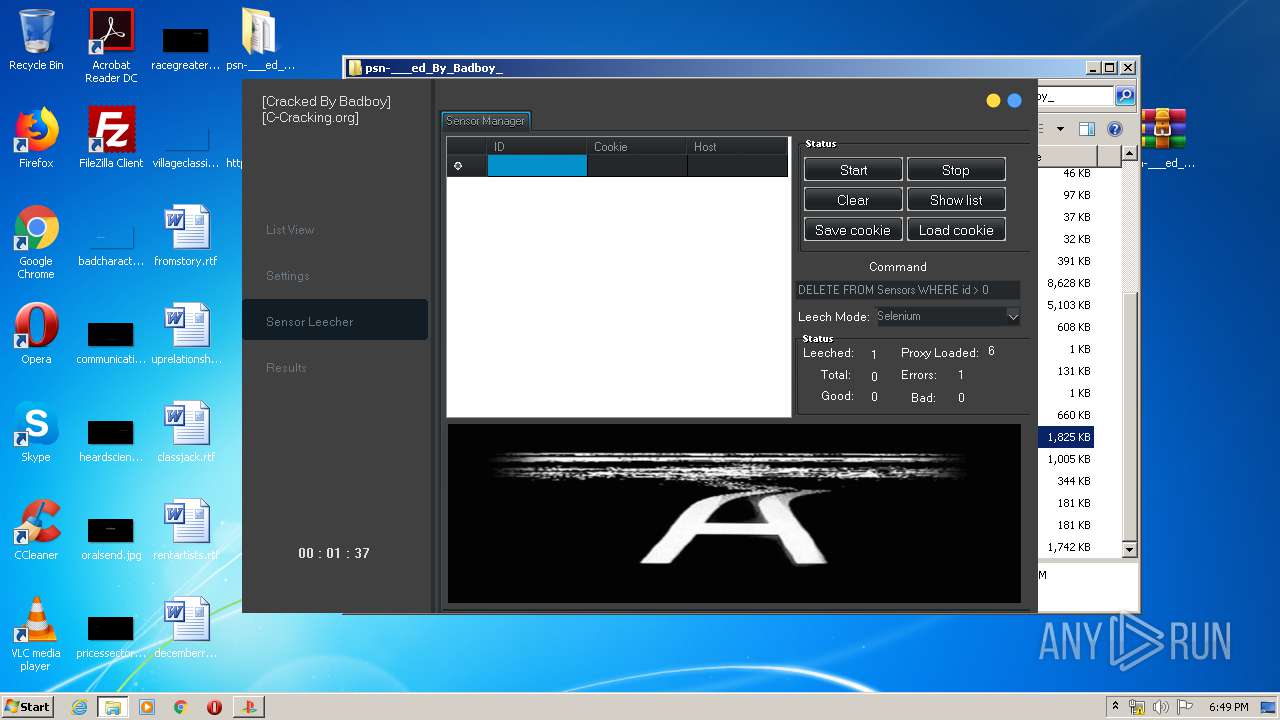
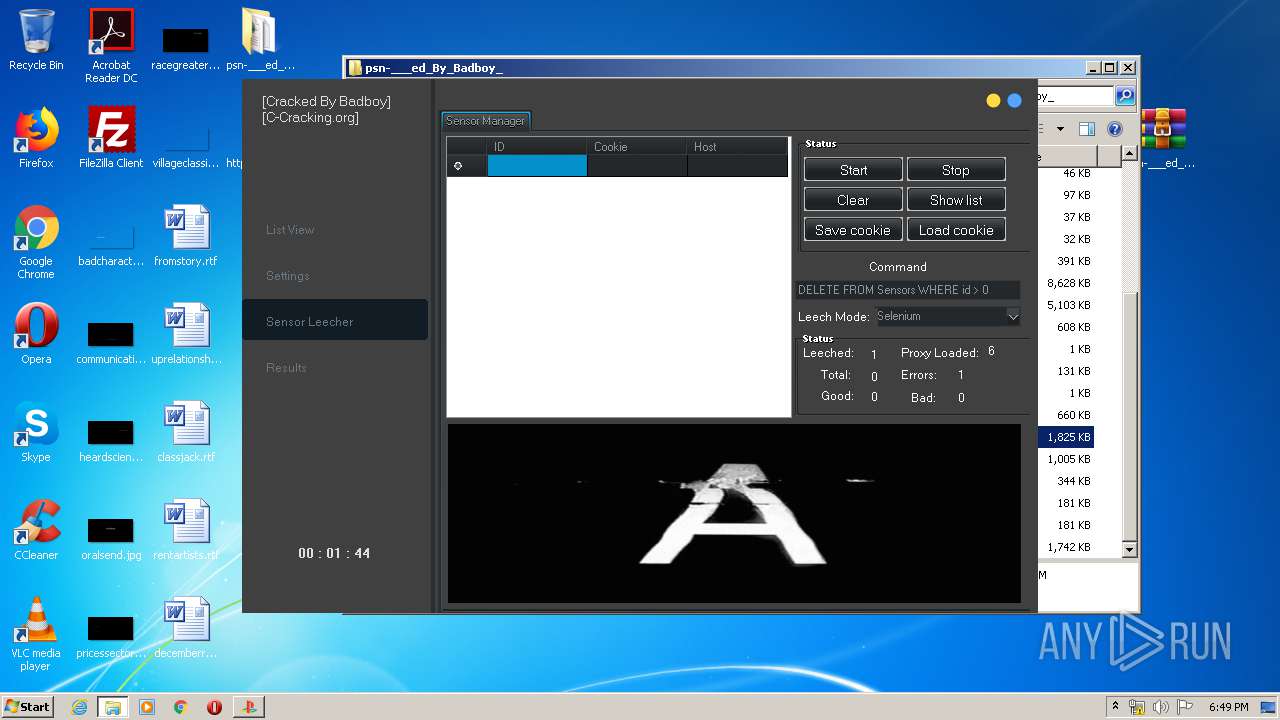
| 940 | "C:\Users\admin\Desktop\psn-___ed_By_Badboy_\PlayStation Checker - [Cracked By Badboy].exe" | C:\Users\admin\Desktop\psn-___ed_By_Badboy_\PlayStation Checker - [Cracked By Badboy].exe | explorer.exe | ||||||||||||
User: admin Company: jokerTM Integrity Level: HIGH Description: PlayStation Checker by BLJ Exit code: 0 Version: 4.2.0.0 Modules
| |||||||||||||||
| 956 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disable-background-networking --disable-client-side-phishing-detection --disable-default-apps --disable-hang-monitor --disable-popup-blocking --disable-prompt-on-repost --disable-sync --enable-blink-features=ShadowDOMV0 --enable-logging --force-fieldtrials --ignore-certificate-errors --load-extension="C:\Users\admin\AppData\Local\Temp\scoped_dir1760_1864277144\internal" --log-level=0 --no-first-run --password-store=basic --proxy-server=192.241.245.207:3128 --remote-debugging-port=0 --start-maximized --test-type=webdriver --use-mock-keychain --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.97 Safari/537.36" --user-data-dir="C:\Users\admin\AppData\Local\Temp\scoped_dir1760_650822921" data:, | C:\Program Files\Google\Chrome\Application\chrome.exe | chromedriver.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1064 | "C:\Users\admin\Desktop\psn-___ed_By_Badboy_\chromedriver.exe" --port=53533 | C:\Users\admin\Desktop\psn-___ed_By_Badboy_\chromedriver.exe | — | PlayStation Checker - [Cracked By Badboy].exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1136 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disable-background-networking --disable-client-side-phishing-detection --disable-default-apps --disable-hang-monitor --disable-popup-blocking --disable-prompt-on-repost --disable-sync --enable-blink-features=ShadowDOMV0 --enable-logging --force-fieldtrials --ignore-certificate-errors --load-extension="C:\Users\admin\AppData\Local\Temp\scoped_dir3360_2144804208\internal" --log-level=0 --no-first-run --password-store=basic --proxy-server=192.241.245.207:3128 --remote-debugging-port=0 --start-maximized --test-type=webdriver --use-mock-keychain --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.97 Safari/537.36" --user-data-dir="C:\Users\admin\AppData\Local\Temp\scoped_dir3360_529560365" data:, | C:\Program Files\Google\Chrome\Application\chrome.exe | chromedriver.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1140 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler --user-data-dir=C:\Users\admin\AppData\Local\Temp\scoped_dir2580_1469276866 /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler --database=C:\Users\admin\AppData\Local\Temp\scoped_dir2580_1469276866\Crashpad --metrics-dir=C:\Users\admin\AppData\Local\Temp\scoped_dir2580_1469276866 --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x84,0x88,0x8c,0x80,0x90,0x6d36a9d0,0x6d36a9e0,0x6d36a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1352 | "C:\Users\admin\Desktop\psn-___ed_By_Badboy_\chromedriver.exe" --port=52032 | C:\Users\admin\Desktop\psn-___ed_By_Badboy_\chromedriver.exe | PlayStation Checker - [Cracked By Badboy].exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
5 550
Read events
5 220
Write events
307
Delete events
23
Modification events
| (PID) Process: | (2808) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 0B137AED08000000 | |||
| (PID) Process: | (2976) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: A49C76ED08000000 | |||
| (PID) Process: | (2808) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 1 | |||
| (PID) Process: | (2808) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2808) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2808) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2808) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2808) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithProgids |
| Operation: | write | Name: | WinRAR |
Value: | |||
| (PID) Process: | (2856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
23
Suspicious files
348
Text files
419
Unknown types
161
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2808 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 2808 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 2808 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 2808 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 2808 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 2808 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 2808 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4.tmp | — | |
MD5:— | SHA256:— | |||
| 2808 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:— | SHA256:— | |||
| 2808 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-child-current.bin | binary | |
MD5:— | SHA256:— | |||
| 2808 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
104
DNS requests
191
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2808 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
2808 | firefox.exe | POST | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/ | US | der | 472 b | whitelisted |
2808 | firefox.exe | POST | 200 | 172.217.22.99:80 | http://ocsp.pki.goog/gts1o1 | US | der | 471 b | whitelisted |
2808 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 279 b | whitelisted |
2808 | firefox.exe | POST | 200 | 195.138.255.16:80 | http://ocsp.int-x3.letsencrypt.org/ | DE | der | 527 b | whitelisted |
2808 | firefox.exe | POST | 200 | 172.217.22.99:80 | http://ocsp.pki.goog/gts1o1 | US | der | 472 b | whitelisted |
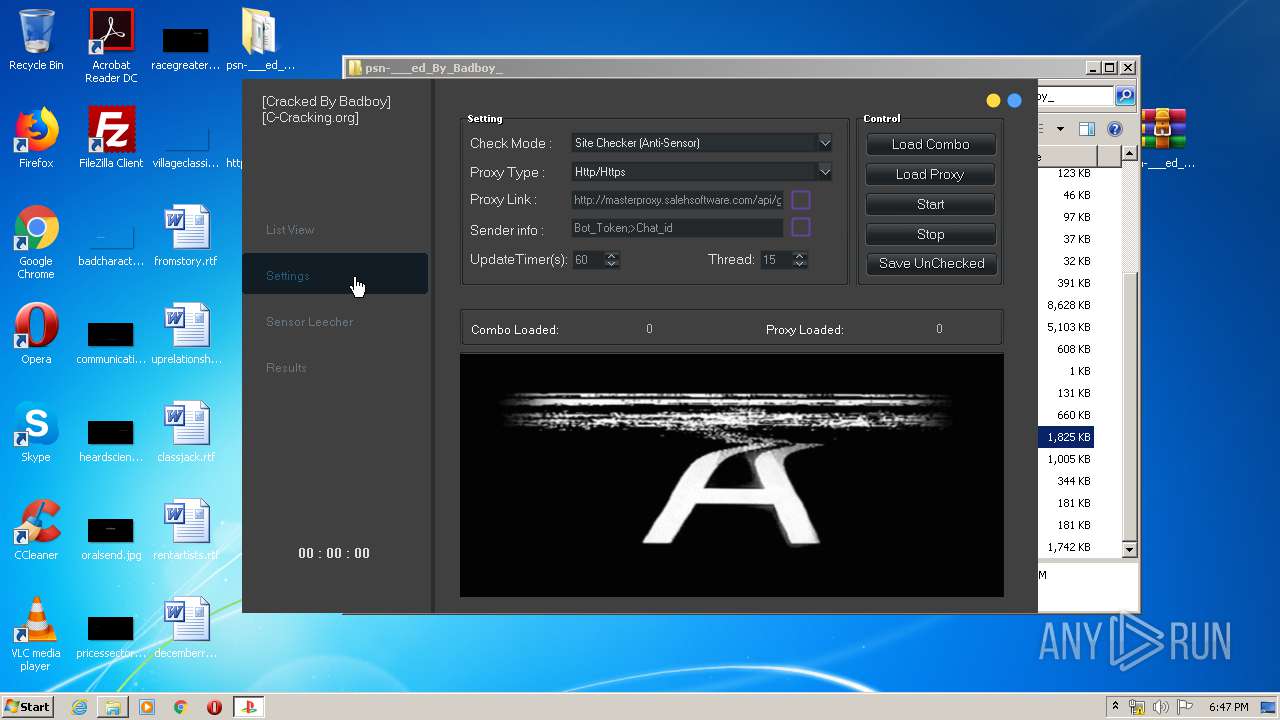
940 | PlayStation Checker - [Cracked By Badboy].exe | GET | 404 | 195.201.88.195:80 | http://masterproxy.salehsoftware.com/api/getproxy?apikey=70c3e54b69762cb06c42f3937494cf48&service=3&type=http | RU | text | 19 b | unknown |
2808 | firefox.exe | POST | 200 | 172.217.22.99:80 | http://ocsp.pki.goog/gts1o1 | US | der | 472 b | whitelisted |
2808 | firefox.exe | POST | 200 | 172.217.22.99:80 | http://ocsp.pki.goog/gts1o1 | US | der | 472 b | whitelisted |
2808 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://status.rapidssl.com/ | US | der | 471 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2808 | firefox.exe | 2.16.186.50:80 | detectportal.firefox.com | Akamai International B.V. | — | whitelisted |
2808 | firefox.exe | 37.187.167.53:443 | www.upload.ee | OVH SAS | FR | suspicious |
2808 | firefox.exe | 93.184.220.29:80 | status.rapidssl.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2808 | firefox.exe | 13.35.253.14:443 | snippets.cdn.mozilla.net | — | US | unknown |
2808 | firefox.exe | 35.190.74.92:443 | www.tradeadexchange.com | Google Inc. | US | whitelisted |
2808 | firefox.exe | 2.18.232.15:443 | s7.addthis.com | Akamai International B.V. | — | whitelisted |
2808 | firefox.exe | 172.217.22.42:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
2808 | firefox.exe | 52.13.239.123:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
2808 | firefox.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
2808 | firefox.exe | 172.217.22.99:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
www.upload.ee |
| whitelisted |
a1089.dscd.akamai.net |
| whitelisted |
node1.upload.ee |
| suspicious |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
push.services.mozilla.com |
| whitelisted |
autopush.prod.mozaws.net |
| whitelisted |
status.rapidssl.com |
| shared |
cs9.wac.phicdn.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1052 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
Process | Message |
|---|---|
PlayStation Checker - [Cracked By Badboy].exe | Native library pre-loader is trying to load native SQLite library "C:\Users\admin\Desktop\psn-___ed_By_Badboy_\x86\SQLite.Interop.dll"...
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\scoped_dir2580_1469276866 directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\scoped_dir1352_20528967 directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\scoped_dir608_1897558335 directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\scoped_dir3796_2127336678 directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\scoped_dir2708_1583779955 directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\scoped_dir2988_1078762886 directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\scoped_dir3360_529560365 directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\scoped_dir3956_386364805 directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\scoped_dir1504_549718976 directory exists )
|