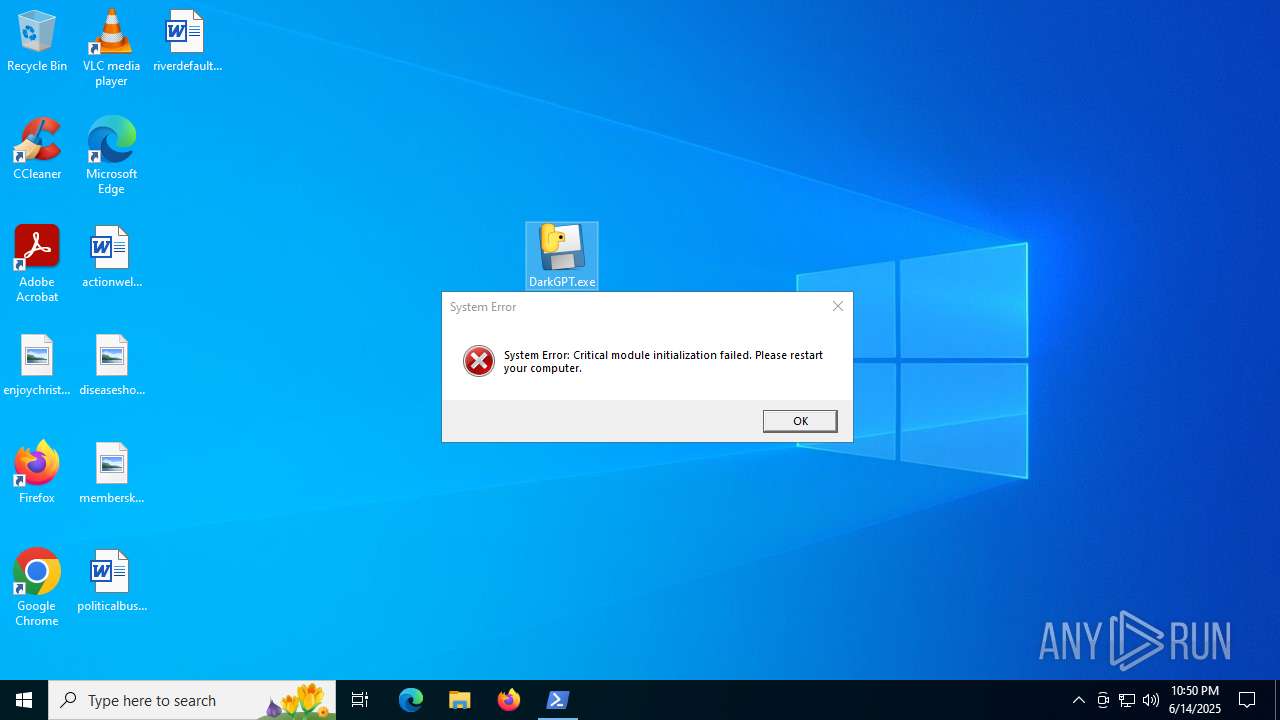
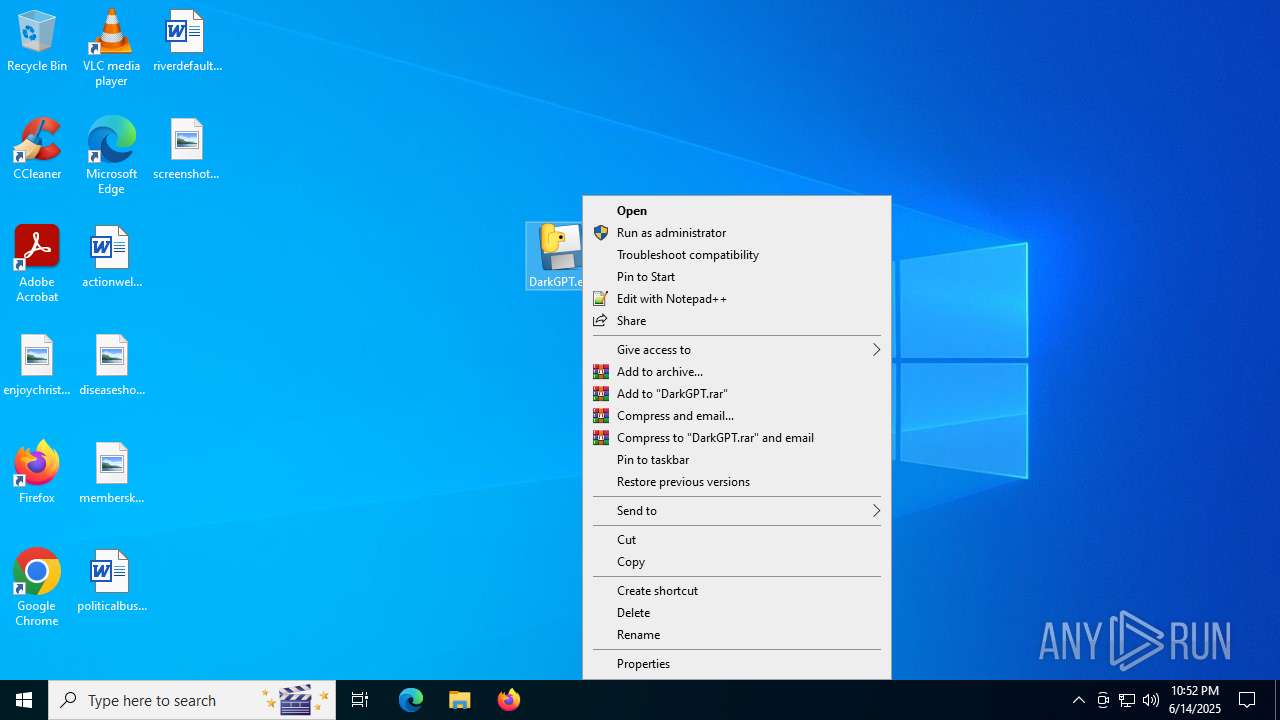
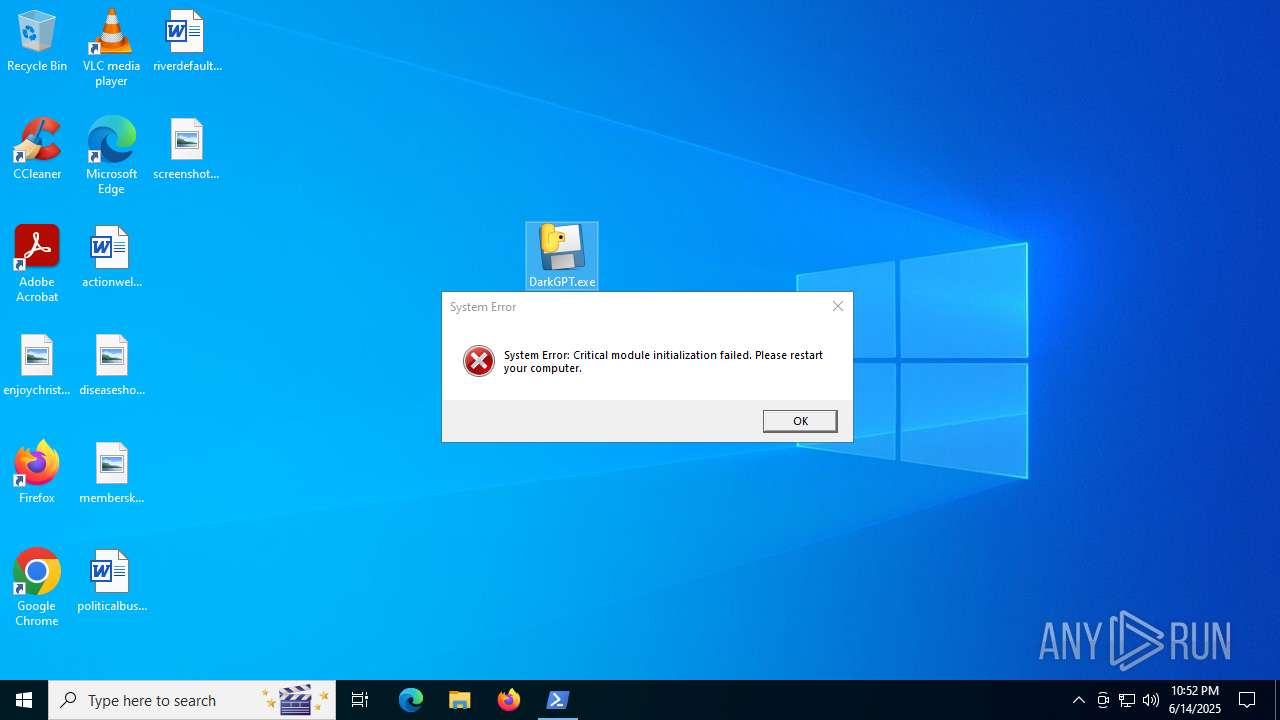
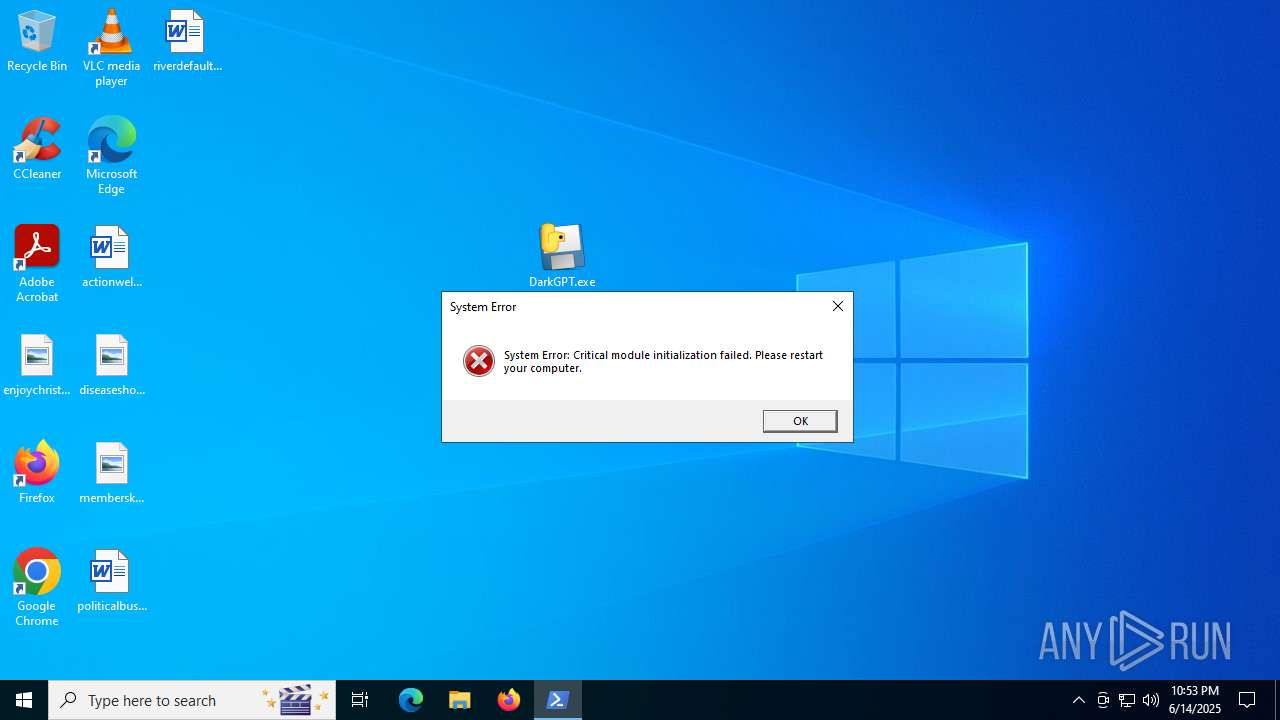
| File name: | DarkGPT.exe |
| Full analysis: | https://app.any.run/tasks/c99fbb89-6da0-4d64-815c-ec51505073ea |
| Verdict: | Malicious activity |
| Analysis date: | June 14, 2025, 22:50:13 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 442EA7FE46D650EAE6632E7A722DF057 |
| SHA1: | 9EC5BFE591DB7EF9D6695C64ADECDCA72979CCF3 |
| SHA256: | 222C34C660C30ACECED08095711D8CAD9FDF787C16F610C4CB69124AC470DF44 |
| SSDEEP: | 98304:+jsuTax0O0u7LtIf8unp4Y8IVOvge6XL8aH3JQDvTz28OrSUQqfP3gUa6KOAe/3r:jZS6jSFYGy9TlaCDqWHQqw |
MALICIOUS
Create files in the Startup directory
- DarkGPT.exe (PID: 5504)
- DarkGPT.exe (PID: 3924)
Changes the autorun value in the registry
- reg.exe (PID: 620)
- reg.exe (PID: 4552)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 3980)
- cmd.exe (PID: 6348)
- cmd.exe (PID: 5568)
- cmd.exe (PID: 7056)
- cmd.exe (PID: 2436)
SUSPICIOUS
Process drops legitimate windows executable
- DarkGPT.exe (PID: 1484)
- DarkGPT.exe (PID: 1324)
- DarkGPT.exe (PID: 6444)
- DarkGPT.exe (PID: 6640)
- DarkGPT.exe (PID: 6896)
Executable content was dropped or overwritten
- DarkGPT.exe (PID: 1484)
- DarkGPT.exe (PID: 1324)
- DarkGPT.exe (PID: 5504)
- DarkGPT.exe (PID: 3924)
- DarkGPT.exe (PID: 6444)
- DarkGPT.exe (PID: 6640)
- DarkGPT.exe (PID: 6732)
- DarkGPT.exe (PID: 6420)
- DarkGPT.exe (PID: 952)
- DarkGPT.exe (PID: 6896)
Process drops python dynamic module
- DarkGPT.exe (PID: 1484)
- DarkGPT.exe (PID: 1324)
- DarkGPT.exe (PID: 6444)
- DarkGPT.exe (PID: 6640)
- DarkGPT.exe (PID: 6896)
The process drops C-runtime libraries
- DarkGPT.exe (PID: 1484)
- DarkGPT.exe (PID: 1324)
- DarkGPT.exe (PID: 6444)
- DarkGPT.exe (PID: 6640)
- DarkGPT.exe (PID: 6896)
Loads Python modules
- DarkGPT.exe (PID: 5504)
- DarkGPT.exe (PID: 3924)
There is functionality for taking screenshot (YARA)
- DarkGPT.exe (PID: 1484)
- DarkGPT.exe (PID: 1324)
- DarkGPT.exe (PID: 5504)
Application launched itself
- DarkGPT.exe (PID: 1484)
- DarkGPT.exe (PID: 1324)
- updater.exe (PID: 3544)
- DarkGPT.exe (PID: 6444)
- DarkGPT.exe (PID: 6640)
- DarkGPT.exe (PID: 6896)
Starts CMD.EXE for commands execution
- DarkGPT.exe (PID: 5504)
- DarkGPT.exe (PID: 3924)
- DarkGPT.exe (PID: 6732)
- DarkGPT.exe (PID: 6420)
- DarkGPT.exe (PID: 952)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1132)
- cmd.exe (PID: 1180)
- cmd.exe (PID: 6292)
- cmd.exe (PID: 2120)
- cmd.exe (PID: 7120)
- cmd.exe (PID: 6880)
- cmd.exe (PID: 6956)
- cmd.exe (PID: 1196)
- cmd.exe (PID: 1708)
- cmd.exe (PID: 7032)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 7164)
- cmd.exe (PID: 6304)
- cmd.exe (PID: 5432)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 6856)
- cmd.exe (PID: 6944)
- cmd.exe (PID: 4624)
- cmd.exe (PID: 6772)
- cmd.exe (PID: 6176)
- cmd.exe (PID: 660)
Get information on the list of running processes
- DarkGPT.exe (PID: 5504)
- cmd.exe (PID: 6672)
- cmd.exe (PID: 4864)
- cmd.exe (PID: 3780)
- DarkGPT.exe (PID: 3924)
- cmd.exe (PID: 2320)
- cmd.exe (PID: 5060)
- cmd.exe (PID: 2348)
- DarkGPT.exe (PID: 6732)
- cmd.exe (PID: 920)
- cmd.exe (PID: 3548)
- DarkGPT.exe (PID: 6420)
- cmd.exe (PID: 3860)
- cmd.exe (PID: 6220)
- cmd.exe (PID: 4904)
- cmd.exe (PID: 6156)
- DarkGPT.exe (PID: 952)
- cmd.exe (PID: 2632)
- cmd.exe (PID: 3184)
- cmd.exe (PID: 4016)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4832)
- cmd.exe (PID: 3676)
- cmd.exe (PID: 6428)
- cmd.exe (PID: 948)
- cmd.exe (PID: 4348)
Possible usage of Discord/Telegram API has been detected (YARA)
- DarkGPT.exe (PID: 5504)
- DarkGPT.exe (PID: 3924)
INFO
Checks supported languages
- DarkGPT.exe (PID: 1484)
- DarkGPT.exe (PID: 1324)
- DarkGPT.exe (PID: 5504)
- DarkGPT.exe (PID: 3924)
The sample compiled with english language support
- DarkGPT.exe (PID: 1484)
- DarkGPT.exe (PID: 1324)
- DarkGPT.exe (PID: 6444)
- DarkGPT.exe (PID: 6640)
- DarkGPT.exe (PID: 6896)
- firefox.exe (PID: 6428)
Create files in a temporary directory
- DarkGPT.exe (PID: 1484)
- DarkGPT.exe (PID: 1324)
Reads the computer name
- DarkGPT.exe (PID: 1484)
- DarkGPT.exe (PID: 1324)
- DarkGPT.exe (PID: 5504)
- DarkGPT.exe (PID: 3924)
Reads the machine GUID from the registry
- DarkGPT.exe (PID: 5504)
- DarkGPT.exe (PID: 3924)
Checks operating system version
- DarkGPT.exe (PID: 5504)
- DarkGPT.exe (PID: 3924)
- DarkGPT.exe (PID: 6732)
- DarkGPT.exe (PID: 6420)
- DarkGPT.exe (PID: 952)
Manual execution by a user
- DarkGPT.exe (PID: 1324)
- svchost.exe (PID: 1036)
- svchost.exe (PID: 1068)
- svchost.exe (PID: 1280)
- svchost.exe (PID: 1148)
- svchost.exe (PID: 1172)
- svchost.exe (PID: 1208)
- svchost.exe (PID: 928)
- svchost.exe (PID: 1460)
- svchost.exe (PID: 1584)
- svchost.exe (PID: 1772)
- svchost.exe (PID: 1652)
- svchost.exe (PID: 1752)
- svchost.exe (PID: 1760)
- svchost.exe (PID: 1780)
- svchost.exe (PID: 1908)
- svchost.exe (PID: 1992)
- svchost.exe (PID: 1948)
- svchost.exe (PID: 2004)
- svchost.exe (PID: 2068)
- svchost.exe (PID: 2164)
- svchost.exe (PID: 1328)
- svchost.exe (PID: 1356)
- svchost.exe (PID: 1468)
- upfc.exe (PID: 1644)
- svchost.exe (PID: 2488)
- svchost.exe (PID: 2332)
- svchost.exe (PID: 2412)
- svchost.exe (PID: 2404)
- svchost.exe (PID: 2460)
- sppsvc.exe (PID: 2312)
- svchost.exe (PID: 2544)
- svchost.exe (PID: 2560)
- svchost.exe (PID: 2552)
- svchost.exe (PID: 2572)
- spoolsv.exe (PID: 2672)
- svchost.exe (PID: 2772)
- svchost.exe (PID: 2904)
- svchost.exe (PID: 2968)
- svchost.exe (PID: 2996)
- svchost.exe (PID: 3004)
- svchost.exe (PID: 3012)
- OfficeClickToRun.exe (PID: 3024)
- svchost.exe (PID: 2612)
- svchost.exe (PID: 2860)
- svchost.exe (PID: 2444)
- svchost.exe (PID: 3884)
- svchost.exe (PID: 3964)
- svchost.exe (PID: 4008)
- svchost.exe (PID: 4028)
- svchost.exe (PID: 4036)
- svchost.exe (PID: 4056)
- svchost.exe (PID: 812)
- svchost.exe (PID: 2176)
- svchost.exe (PID: 4188)
- svchost.exe (PID: 4212)
- svchost.exe (PID: 2796)
- svchost.exe (PID: 2560)
- svchost.exe (PID: 3112)
- svchost.exe (PID: 3420)
- svchost.exe (PID: 3828)
- svchost.exe (PID: 5388)
- svchost.exe (PID: 5736)
- svchost.exe (PID: 5884)
- DarkGPT.exe (PID: 6444)
- svchost.exe (PID: 6452)
- DarkGPT.exe (PID: 6640)
- svchost.exe (PID: 4760)
- svchost.exe (PID: 4444)
- TrustedInstaller.exe (PID: 4968)
- svchost.exe (PID: 2124)
- svchost.exe (PID: 5812)
- svchost.exe (PID: 6564)
- DarkGPT.exe (PID: 6896)
- firefox.exe (PID: 6332)
- svchost.exe (PID: 7448)
- svchost.exe (PID: 7344)
- svchost.exe (PID: 7668)
- svchost.exe (PID: 7484)
- uhssvc.exe (PID: 7616)
- svchost.exe (PID: 7732)
- svchost.exe (PID: 1816)
- svchost.exe (PID: 7820)
- svchost.exe (PID: 7988)
PyInstaller has been detected (YARA)
- DarkGPT.exe (PID: 1484)
- DarkGPT.exe (PID: 1324)
- DarkGPT.exe (PID: 5504)
Launching a file from the Startup directory
- DarkGPT.exe (PID: 5504)
- DarkGPT.exe (PID: 3924)
Launching a file from a Registry key
- reg.exe (PID: 620)
- reg.exe (PID: 4552)
Creates files or folders in the user directory
- DarkGPT.exe (PID: 5504)
- DarkGPT.exe (PID: 3924)
Attempting to use instant messaging service
- svchost.exe (PID: 2164)
- DarkGPT.exe (PID: 6732)
- DarkGPT.exe (PID: 952)
Application launched itself
- msedge.exe (PID: 7092)
- firefox.exe (PID: 6332)
- firefox.exe (PID: 6428)
Executable content was dropped or overwritten
- firefox.exe (PID: 6428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:14 18:04:24+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.32 |
| CodeSize: | 165888 |
| InitializedDataSize: | 154112 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xafa0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
467
Monitored processes
276
Malicious processes
10
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 304 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | DarkGPT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 308 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 5584 -prefsLen 39068 -prefMapHandle 5588 -prefMapSize 272997 -jsInitHandle 5592 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 5600 -initialChannelId {9b53b779-1954-4cec-8890-7450cfca9acc} -parentPid 6428 -crashReporter "\\.\pipe\gecko-crash-server-pipe.6428" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 7 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 136.0 Modules
| |||||||||||||||
| 368 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 620 | reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v SystemService /t REG_SZ /d "python \"C:\Users\admin\AppData\Local\sys_9be1f5e634f4eb73.py\"" /f | C:\Windows\System32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 656 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | C:\WINDOWS\system32\cmd.exe /c "attrib +h +s "C:\Users\admin\AppData\Local\sys_1fa26b23b4b8409e.py"" | C:\Windows\System32\cmd.exe | — | DarkGPT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 724 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | sihost.exe | C:\Windows\System32\sihost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Shell Infrastructure Host Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | C:\WINDOWS\system32\svchost.exe -k UnistackSvcGroup -s CDPUserSvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
202 186
Read events
184 573
Write events
17 341
Delete events
272
Modification events
| (PID) Process: | (620) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | SystemService |
Value: python "C:\Users\admin\AppData\Local\sys_9be1f5e634f4eb73.py" | |||
| (PID) Process: | (4552) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | SystemService |
Value: python "C:\Users\admin\AppData\Local\sys_d4b8588dd891bfed.py" | |||
| (PID) Process: | (1036) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\DsmSvc\State |
| Operation: | write | Name: | SessionNumber |
Value: 42000000 | |||
| (PID) Process: | (1328) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\EventLog\State |
| Operation: | delete value | Name: | LastRestoreId |
Value: | |||
| (PID) Process: | (1328) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\EventLog\State |
| Operation: | write | Name: | 6005BT |
Value: 40106FDE7EDDDB01 | |||
| (PID) Process: | (1328) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Reliability |
| Operation: | write | Name: | LastAliveStamp |
Value: D0BAAD0B | |||
| (PID) Process: | (1584) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\mpssvc\Parameters\PortKeywords\DHCP |
| Operation: | write | Name: | Collection |
Value: | |||
| (PID) Process: | (1584) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip6\Parameters |
| Operation: | write | Name: | Dhcpv6DUID |
Value: 000100012FDFB5621891C52B0EE3 | |||
| (PID) Process: | (1584) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters\Interfaces\{d950ca8d-448e-4ca2-89de-a65a1ac2b2a6} |
| Operation: | delete value | Name: | DhcpClassIdBin |
Value: | |||
| (PID) Process: | (1584) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters |
| Operation: | delete value | Name: | DhcpNameServer |
Value: | |||
Executable files
289
Suspicious files
3 879
Text files
262
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1484 | DarkGPT.exe | C:\Users\admin\AppData\Local\Temp\_MEI14842\PIL\_imagingtk.cp310-win_amd64.pyd | executable | |
MD5:B933B29AC15227F8B6851D30841C0FC5 | SHA256:E59553C74D4374752E536F41CC352B520C18FA4BF8F0B689262C93DB509FD5BF | |||
| 1484 | DarkGPT.exe | C:\Users\admin\AppData\Local\Temp\_MEI14842\PIL\_imagingcms.cp310-win_amd64.pyd | executable | |
MD5:4CFF38E4A1613D9E86D453A5D8D74BE6 | SHA256:FDAF3833C1A97B69AFBAE5368700964127C9F851CDBE95F2EF464CFA04F9A4A4 | |||
| 1484 | DarkGPT.exe | C:\Users\admin\AppData\Local\Temp\_MEI14842\PIL\_webp.cp310-win_amd64.pyd | executable | |
MD5:C0A2A9D24002BCB64602AEFAE20D50DF | SHA256:AB66A03F87D2D251A687ECB793AEA01CD6A127922972894B23AB9FFBA0889138 | |||
| 1484 | DarkGPT.exe | C:\Users\admin\AppData\Local\Temp\_MEI14842\PIL\_imaging.cp310-win_amd64.pyd | executable | |
MD5:66DFB3FC790A5C300BBFF1BA50B664F0 | SHA256:A25E90A4EA75A77A21F1C25D456B20C1220EC453894A0FDE427AFD351F093696 | |||
| 1484 | DarkGPT.exe | C:\Users\admin\AppData\Local\Temp\_MEI14842\_bz2.pyd | executable | |
MD5:A4B636201605067B676CC43784AE5570 | SHA256:F178E29921C04FB68CC08B1E5D1181E5DF8CE1DE38A968778E27990F4A69973C | |||
| 1484 | DarkGPT.exe | C:\Users\admin\AppData\Local\Temp\_MEI14842\VCRUNTIME140.dll | executable | |
MD5:F12681A472B9DD04A812E16096514974 | SHA256:D66C3B47091CEB3F8D3CC165A43D285AE919211A0C0FCB74491EE574D8D464F8 | |||
| 1484 | DarkGPT.exe | C:\Users\admin\AppData\Local\Temp\_MEI14842\_asyncio.pyd | executable | |
MD5:6EB3C9FC8C216CEA8981B12FD41FBDCD | SHA256:3B0661EF2264D6566368B677C732BA062AC4688EF40C22476992A0F9536B0010 | |||
| 1484 | DarkGPT.exe | C:\Users\admin\AppData\Local\Temp\_MEI14842\_hashlib.pyd | executable | |
MD5:49CE7A28E1C0EB65A9A583A6BA44FA3B | SHA256:1BE5CFD06A782B2AE8E4629D9D035CBC487074E8F63B9773C85E317BE29C0430 | |||
| 1484 | DarkGPT.exe | C:\Users\admin\AppData\Local\Temp\_MEI14842\_ctypes.pyd | executable | |
MD5:87596DB63925DBFE4D5F0F36394D7AB0 | SHA256:92D7954D9099762D81C1AE2836C11B6BA58C1883FDE8EEEFE387CC93F2F6AFB4 | |||
| 1484 | DarkGPT.exe | C:\Users\admin\AppData\Local\Temp\_MEI14842\_lzma.pyd | executable | |
MD5:B5FBC034AD7C70A2AD1EB34D08B36CF8 | SHA256:80A6EBE46F43FFA93BBDBFC83E67D6F44A44055DE1439B06E4DD2983CB243DF6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
198
DNS requests
247
Threats
25
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4868 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4868 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7020 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5812 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1264 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:K0xrx12V-vIW5e-e3kipsf_Xo-rLzImSVLG0ivFhOnE&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1088 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5168 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2228 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5504 | DarkGPT.exe | 162.159.138.232:443 | discord.com | CLOUDFLARENET | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
discord.com |
| whitelisted |
gateway.discord.gg |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
5504 | DarkGPT.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
5504 | DarkGPT.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
2200 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
2200 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (gateway .discord .gg) |
5504 | DarkGPT.exe | Misc activity | ET INFO Observed Discord Service Domain (gateway .discord .gg) in TLS SNI |
3924 | DarkGPT.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
3924 | DarkGPT.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
3924 | DarkGPT.exe | Misc activity | ET INFO Observed Discord Service Domain (gateway .discord .gg) in TLS SNI |
2164 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |