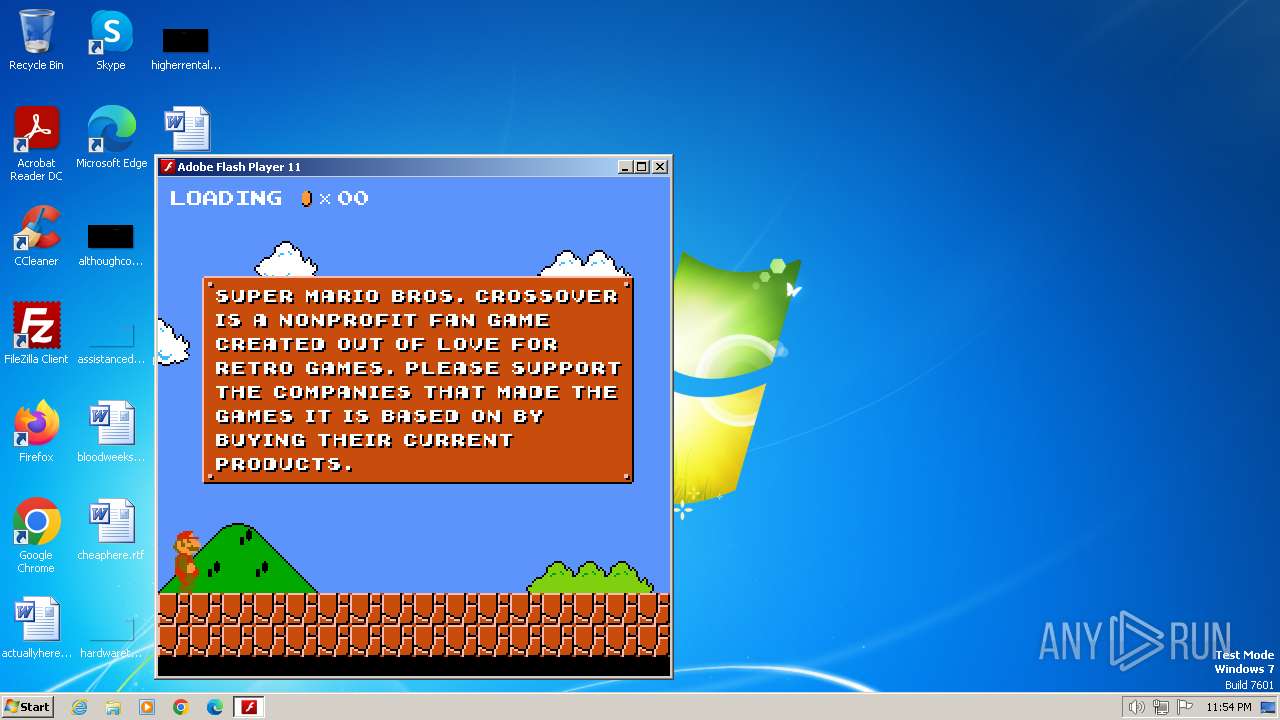
| File name: | Super Mario Bros Crossover 3.exe |
| Full analysis: | https://app.any.run/tasks/a597e118-45d8-490f-8e1d-b6b721609c03 |
| Verdict: | Malicious activity |
| Analysis date: | February 12, 2024, 23:54:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 4D290FDDC056081C58FE1A62DB559FF6 |
| SHA1: | 4335933015851A785D5F551C0460D5AA6019602D |
| SHA256: | 220CC1EF9EB8B4240751D7A0911209CD0EDAEE14DD08FC4615F58BA511901DBB |
| SSDEEP: | 98304:m1Kj0zPdklGggWFsiBq7L0+ycfhmix1EwnmpKbfbC6eR33eb7tGZoAd3OqghR5Pp:myZ7UKsuILs3pOnjUVfEDf2QN |
MALICIOUS
Drops the executable file immediately after the start
- Super Mario Bros Crossover 3.exe (PID: 3864)
SUSPICIOUS
Checks Windows Trust Settings
- Super Mario Bros Crossover 3.exe (PID: 3864)
Reads the Internet Settings
- Super Mario Bros Crossover 3.exe (PID: 3864)
Reads security settings of Internet Explorer
- Super Mario Bros Crossover 3.exe (PID: 3864)
Reads settings of System Certificates
- Super Mario Bros Crossover 3.exe (PID: 3864)
INFO
Checks proxy server information
- Super Mario Bros Crossover 3.exe (PID: 3864)
Creates files or folders in the user directory
- Super Mario Bros Crossover 3.exe (PID: 3864)
Reads CPU info
- Super Mario Bros Crossover 3.exe (PID: 3864)
Checks supported languages
- Super Mario Bros Crossover 3.exe (PID: 3864)
Reads the computer name
- Super Mario Bros Crossover 3.exe (PID: 3864)
Reads the machine GUID from the registry
- Super Mario Bros Crossover 3.exe (PID: 3864)
Reads the software policy settings
- Super Mario Bros Crossover 3.exe (PID: 3864)
Create files in a temporary directory
- Super Mario Bros Crossover 3.exe (PID: 3864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:09:23 23:15:46+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 6029312 |
| InitializedDataSize: | 2939904 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x596afc |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.1.152 |
| ProductVersionNumber: | 11.0.1.152 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Adobe Systems, Inc. |
| FileDescription: | Adobe Flash Player 11.0 r1 |
| FileVersion: | 11,0,1,152 |
| InternalName: | Adobe Flash Player 11.0 |
| LegalCopyright: | Adobe® Flash® Player. Copyright © 1996-2011 Adobe Systems Incorporated. All Rights Reserved. Adobe and Flash are either trademarks or registered trademarks in the United States and/or other countries. |
| LegalTrademarks: | Adobe Flash Player |
| OriginalFileName: | SAFlashPlayer.exe |
| ProductName: | Shockwave Flash |
| ProductVersion: | 11,0,1,152 |
| Debugger: | - |
Total processes
37
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3864 | "C:\Users\admin\AppData\Local\Temp\Super Mario Bros Crossover 3.exe" | C:\Users\admin\AppData\Local\Temp\Super Mario Bros Crossover 3.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems, Inc. Integrity Level: MEDIUM Description: Adobe Flash Player 11.0 r1 Exit code: 0 Version: 11,0,1,152 Modules
| |||||||||||||||
Total events
5 627
Read events
5 586
Write events
35
Delete events
6
Modification events
| (PID) Process: | (3864) Super Mario Bros Crossover 3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Super Mario Bros Crossover 3.exe | |||
| (PID) Process: | (3864) Super Mario Bros Crossover 3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3864) Super Mario Bros Crossover 3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3864) Super Mario Bros Crossover 3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3864) Super Mario Bros Crossover 3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3864) Super Mario Bros Crossover 3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (3864) Super Mario Bros Crossover 3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (3864) Super Mario Bros Crossover 3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (3864) Super Mario Bros Crossover 3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (3864) Super Mario Bros Crossover 3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005C010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
6
Text files
1
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3864 | Super Mario Bros Crossover 3.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sol | sol | |
MD5:4E442C66F85325FE25C83EE8855432CA | SHA256:C1F7F9394B37899EC9EFE36DD2C26C80837F357D86F20F67DC13F6491F0CFEA9 | |||
| 3864 | Super Mario Bros Crossover 3.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\data.txt[1].htm | html | |
MD5:17C0146FED83513DBEDCA9C8D9DA7D2D | SHA256:756F6CB87EE380D7076C631B6D38D29C5B38AFDB6E4F50D93EC59E1931B8C58E | |||
| 3864 | Super Mario Bros Crossover 3.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\708D759065B285903EA957BEE6FEF2AB | binary | |
MD5:4C03CD9507CC71D7AF73C37157FCD9E6 | SHA256:EFE9D46CD66C6238F7A248F2DA21D73163522C7C4F2103EC8E75627FCF4578C6 | |||
| 3864 | Super Mario Bros Crossover 3.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sxx | sol | |
MD5:4E442C66F85325FE25C83EE8855432CA | SHA256:C1F7F9394B37899EC9EFE36DD2C26C80837F357D86F20F67DC13F6491F0CFEA9 | |||
| 3864 | Super Mario Bros Crossover 3.exe | C:\Users\admin\AppData\Local\Temp\Tar1653.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 3864 | Super Mario Bros Crossover 3.exe | C:\Users\admin\AppData\Local\Temp\Cab1652.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 3864 | Super Mario Bros Crossover 3.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:06295825D16708A44B45117B9D8A002B | SHA256:7BB3A3F93AE4ACD90AF3D9BF718B23BFB8CA3093D187A7F98950DD77AB7650BD | |||
| 3864 | Super Mario Bros Crossover 3.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:56DBE2ADC711EAC1781427AAB4A9C008 | SHA256:5F0AD3A4FF3547207F6CA4B2A2D5247A6A07EA6535F9664FF68E953BEBDDB1D2 | |||
| 3864 | Super Mario Bros Crossover 3.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\708D759065B285903EA957BEE6FEF2AB | binary | |
MD5:A4147183D74A61CD539D423B34A5F359 | SHA256:D7762C9C4901DBBBA4581D329F5353EA60CE3F1BB74869CE60281EFFC81FC464 | |||
| 3864 | Super Mario Bros Crossover 3.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:51C434A4E796F97F9048DCD6B669E651 | SHA256:7DFC458287D558EB1F94734993E23DE7404E185B3DE0213E65E029883E9CB7B0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
10
DNS requests
7
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3864 | Super Mario Bros Crossover 3.exe | GET | 200 | 23.35.209.170:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3864 | Super Mario Bros Crossover 3.exe | GET | 304 | 80.239.138.112:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6cade2c3fa8f3050 | unknown | — | — | unknown |
1080 | svchost.exe | GET | 304 | 173.222.108.195:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3e412f7b4eff0943 | unknown | — | — | unknown |
3864 | Super Mario Bros Crossover 3.exe | GET | 200 | 95.101.75.47:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgNmDIrcWub569F2soKnQn5VqQ%3D%3D | unknown | binary | 503 b | unknown |
3864 | Super Mario Bros Crossover 3.exe | GET | 301 | 161.35.142.62:80 | http://data.explodingrabbit.com/super-mario-bros-crossover/data.txt.gz | unknown | html | 359 b | unknown |
3864 | Super Mario Bros Crossover 3.exe | GET | 200 | 80.239.138.112:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?dbf555d235bb05aa | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3864 | Super Mario Bros Crossover 3.exe | 161.35.142.62:80 | data.explodingrabbit.com | DIGITALOCEAN-ASN | US | unknown |
3864 | Super Mario Bros Crossover 3.exe | 161.35.142.62:443 | data.explodingrabbit.com | DIGITALOCEAN-ASN | US | unknown |
3864 | Super Mario Bros Crossover 3.exe | 80.239.138.112:80 | ctldl.windowsupdate.com | Telia Company AB | DE | unknown |
3864 | Super Mario Bros Crossover 3.exe | 23.35.209.170:80 | x1.c.lencr.org | AKAMAI-AS | CA | unknown |
3864 | Super Mario Bros Crossover 3.exe | 95.101.75.47:80 | r3.o.lencr.org | Akamai International B.V. | NL | unknown |
1080 | svchost.exe | 173.222.108.195:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
data.explodingrabbit.com |
| unknown |
explodingrabbit.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3864 | Super Mario Bros Crossover 3.exe | Potential Corporate Privacy Violation | ET POLICY Outdated Flash Version M1 |
1 ETPRO signatures available at the full report