| File name: | Patch.exe |
| Full analysis: | https://app.any.run/tasks/4492082c-3e49-4112-a95a-3a54bca8d481 |
| Verdict: | Malicious activity |
| Analysis date: | March 19, 2024, 22:06:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | 2E97802DD27ECAEDFD7B576AFE9267CF |
| SHA1: | 1D4DDC971DC5BA6201B414D86E37B99523B0D85C |
| SHA256: | 220C8084BBED37F54FBBA4C5D50D8CEEB3099BAC0EF4041F56AB725678213ABC |
| SSDEEP: | 49152:wIhpWDpUfZEOW6T9kxql+/XuGmvh1/1/485Y:wIhpxfuvI9Wq2erfq85Y |
MALICIOUS
Drops the executable file immediately after the start
- Patch.exe (PID: 3996)
SUSPICIOUS
Reads the Internet Settings
- Patch.exe (PID: 3996)
Executable content was dropped or overwritten
- Patch.exe (PID: 3996)
INFO
Checks supported languages
- Patch.exe (PID: 3996)
Reads the computer name
- Patch.exe (PID: 3996)
Reads the machine GUID from the registry
- Patch.exe (PID: 3996)
Manual execution by a user
- WinRAR.exe (PID: 2112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .scr | | | Windows screen saver (60.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (20.8) |
| .exe | | | Generic Win/DOS Executable (9.2) |
| .exe | | | DOS Executable Generic (9.2) |
| .vxd | | | VXD Driver (0.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:06:18 14:49:18+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 3194880 |
| InitializedDataSize: | 225280 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x46250e |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.1.0 |
| ProductVersionNumber: | 1.3.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | H Hayat |
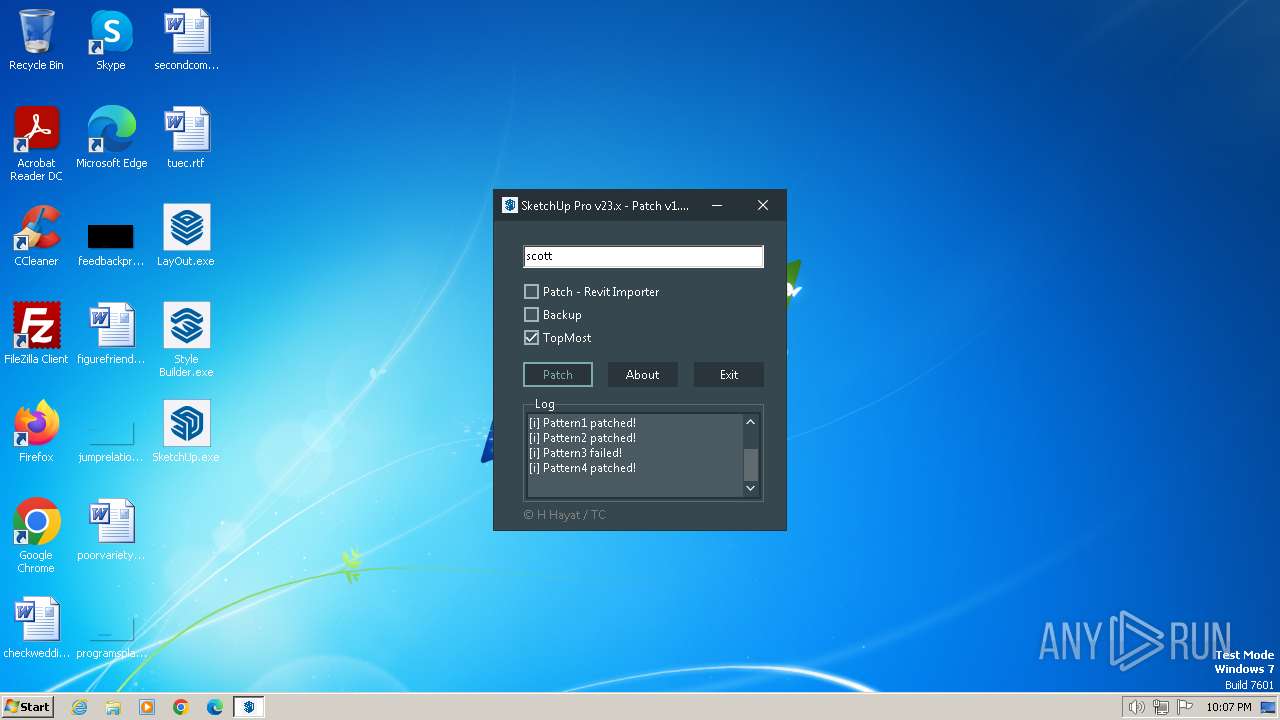
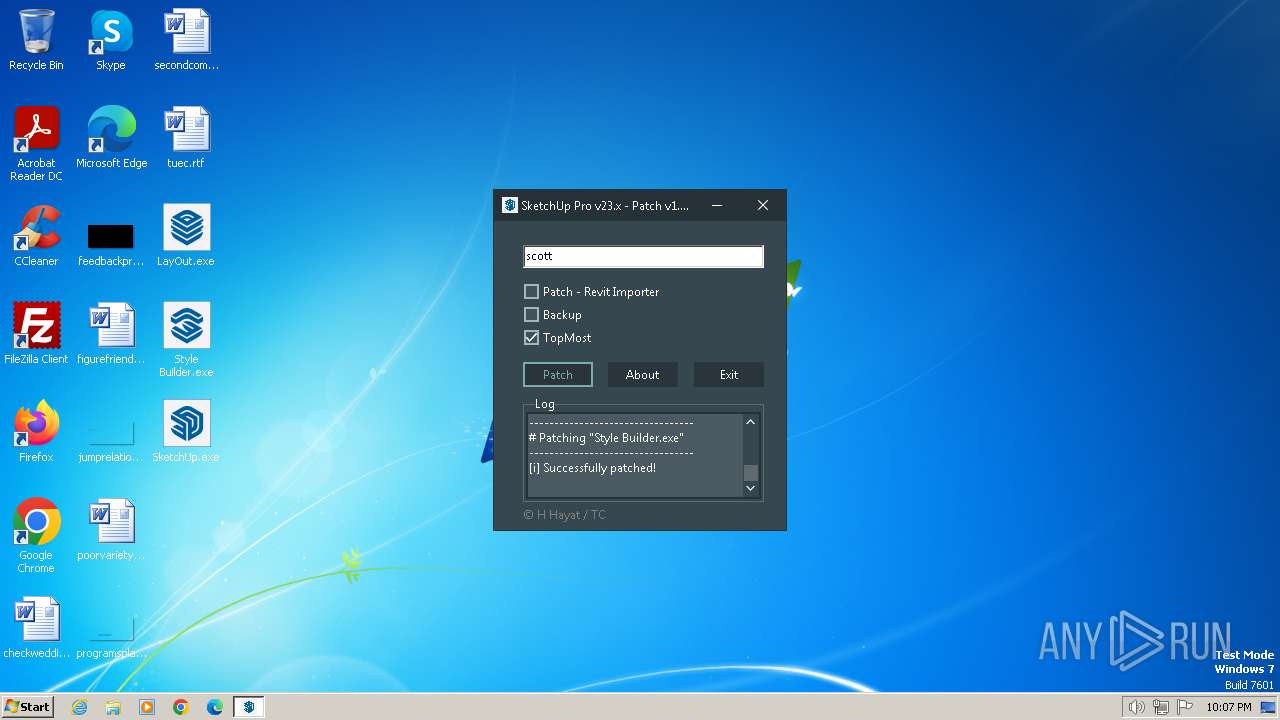
| FileDescription: | SketchUp Pro v23.x [Patch v1.3.1] |
| FileVersion: | 1.3.1.0 |
| InternalName: | Patch.exe |
| LegalCopyright: | Copyright (C) 2023 H Hayat |
| OriginalFileName: | Patch.exe |
| ProductName: | SketchUp Pro v23.x [Patch v1.3.1] |
| ProductVersion: | 1.3.1.0 |
Total processes
48
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
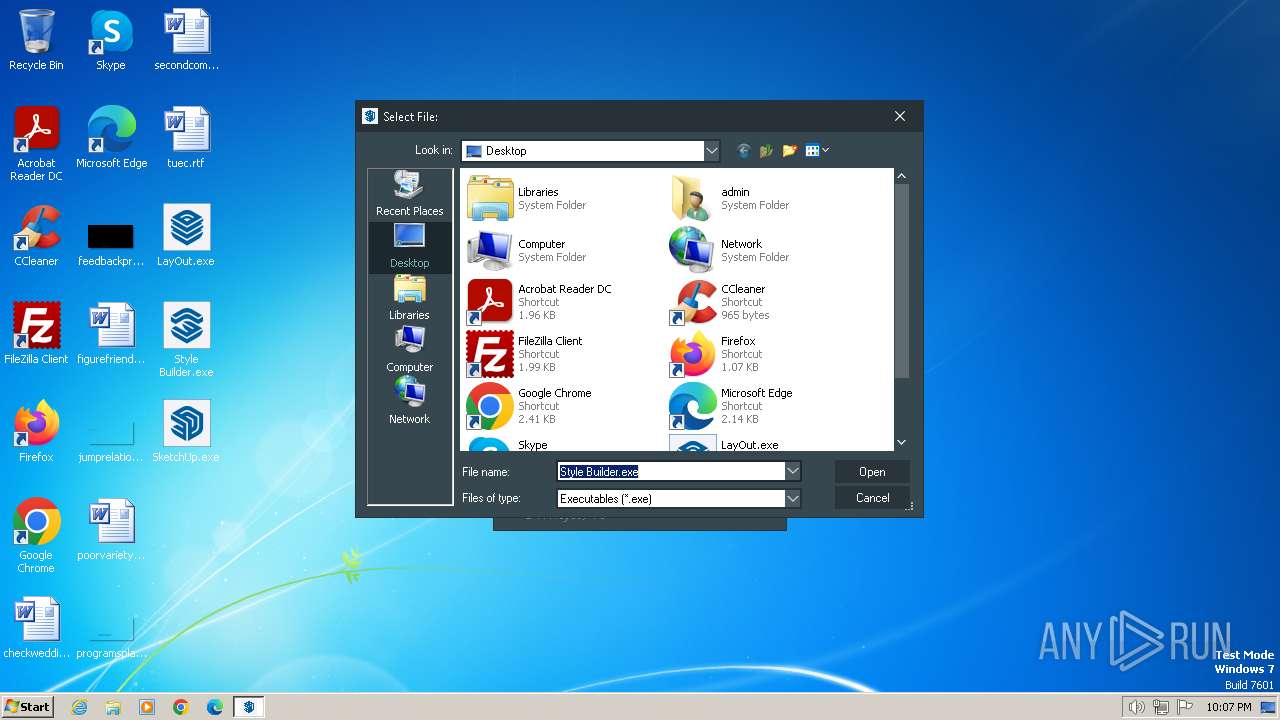
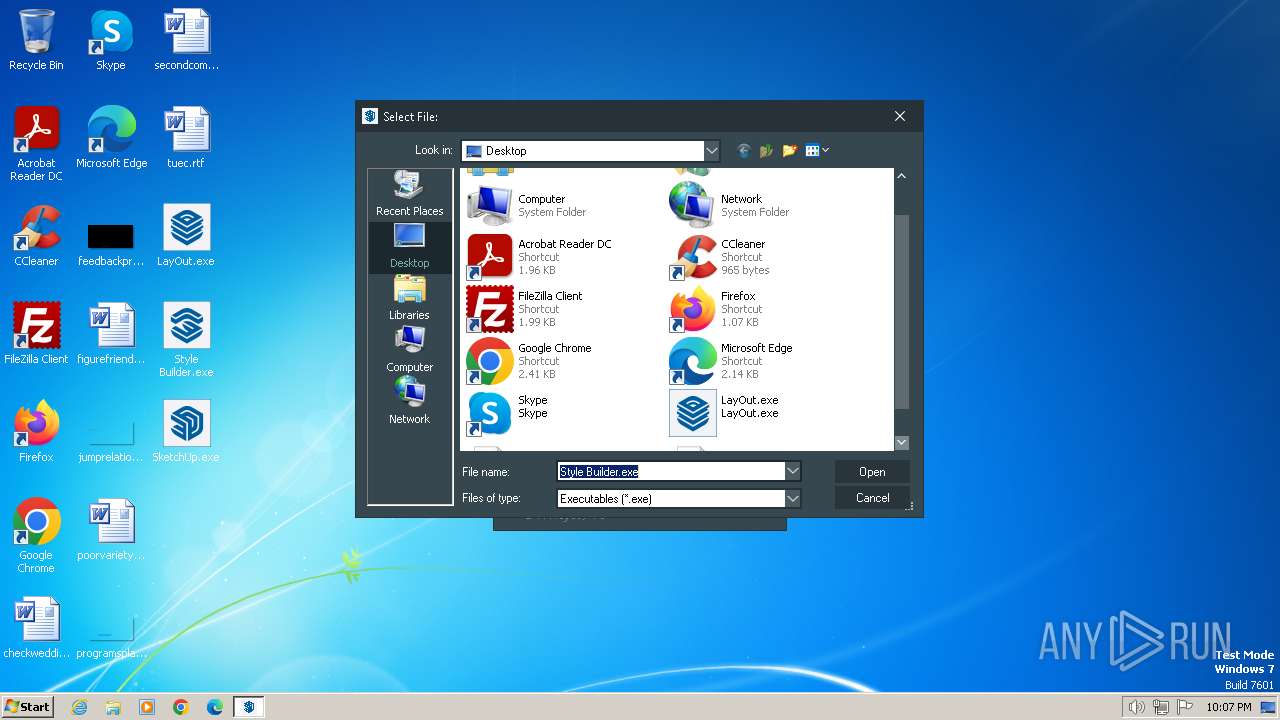
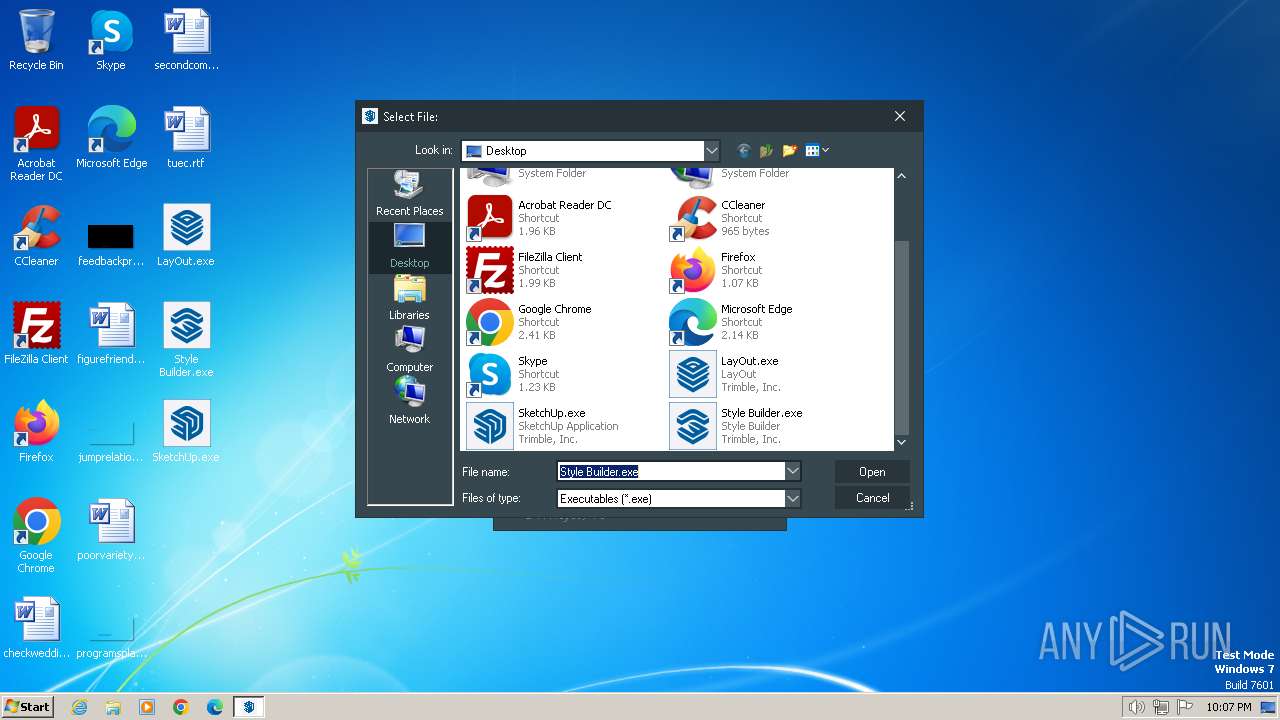
| 2112 | "C:\Program Files\WinRAR\WinRAR.exe" a -ep1 -scul -r0 -iext -- . C:\Users\admin\Desktop\SketchUp.exe C:\Users\admin\Desktop\LayOut.exe "C:\Users\admin\Desktop\Style Builder.exe" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2124 | "C:\Users\admin\AppData\Local\Temp\Patch.exe" | C:\Users\admin\AppData\Local\Temp\Patch.exe | — | explorer.exe | |||||||||||
User: admin Company: H Hayat Integrity Level: MEDIUM Description: SketchUp Pro v23.x [Patch v1.3.1] Exit code: 3221226540 Version: 1.3.1.0 Modules
| |||||||||||||||
| 3996 | "C:\Users\admin\AppData\Local\Temp\Patch.exe" | C:\Users\admin\AppData\Local\Temp\Patch.exe | explorer.exe | ||||||||||||
User: admin Company: H Hayat Integrity Level: HIGH Description: SketchUp Pro v23.x [Patch v1.3.1] Exit code: 0 Version: 1.3.1.0 Modules
| |||||||||||||||
Total events
6 604
Read events
6 408
Write events
166
Delete events
30
Modification events
| (PID) Process: | (3996) Patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3996) Patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3996) Patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 02000000070000000100000006000000000000000B0000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3996) Patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlgLegacy |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (3996) Patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlgLegacy |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (3996) Patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlgLegacy |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (3996) Patch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRULegacy |
| Operation: | write | Name: | 2 |
Value: 500061007400630068002E00650078006500000014001F4225481E03947BC34DB131E946B44C8DD5740000001A00EEBBFE23000010007DB10D7BD29C934A973346CC89022E7C00002A0000000000EFBE000000200000000000000000000000000000000000000000000000000100000020002A0000001900EFBE7E47B3FBE4C93B4BA2BAD3F5D3CD46F98207BA827A5B6945B5D7EC83085F08CC20000000 | |||
| (PID) Process: | (3996) Patch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRULegacy |
| Operation: | write | Name: | MRUListEx |
Value: 020000000000000001000000FFFFFFFF | |||
| (PID) Process: | (3996) Patch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\exe |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (3996) Patch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\exe |
| Operation: | write | Name: | 0 |
Value: 14001F4225481E03947BC34DB131E946B44C8DD5740000001A00EEBBFE23000010007DB10D7BD29C934A973346CC89022E7C00002A0000000000EFBE000000200000000000000000000000000000000000000000000000000100000020002A0000001900EFBE7E47B3FBE4C93B4BA2BAD3F5D3CD46F98207BA827A5B6945B5D7EC83085F08CC20009D0300009703811914106D03200000004840000000000000000000000000000000000000000000000000000000006F0000003153505330F125B7EF471A10A5F102608C9EEBAC2D0000000A000000001F0000000D00000053006B006500740063006800550070002E0065007800650000000000150000000C00000000150000000000000000000000110000000D000000001300000080000000000000005C02000031535053A66A63283D95D211B5D600C04FD918D01100000019000000001300000077014840E5010000200000000011100000D101000014001F50E04FD020EA3A6910A2D808002B30309D19002F433A5C000000000000000000000000000000000000007400310000000000454B314E1100557365727300600008000400EFBEEE3AA314454B314E2A0000005A01000000000100000000000000000036000000000055007300650072007300000040007300680065006C006C00330032002E0064006C006C002C002D0032003100380031003300000014004C003100000000001C4D9960100061646D696E00380008000400EFBE454B804A1C4D99602A0000002D000000000004000000000000000000000000000000610064006D0069006E000000140080003100000000008F57C43E1100444F43554D457E310000680008000400EFBE454B814A8F57C43E2A0000007A0100000000020000000000000000003E000000000044006F00630075006D0065006E0074007300000040007300680065006C006C00330032002E0064006C006C002C002D0032003100370037003000000018006200320000000000000000008000536B6574636855702E6578650000460008000400EFBE00000000000000002A0000000000000000000000000000000000000000000000000053006B006500740063006800550070002E0065007800650000001C0000000000002D00000018000000001F0000000D00000053006B006500740063006800550070002E00650078006500000000001D0000000B000000001F000000050000002E0065007800650000000000000000009E0000003153505340E83E1E2BBC6C4782372ACD1A839B225D00000008000000001F0000002600000043003A005C00550073006500720073005C00610064006D0069006E005C0044006F00630075006D0065006E00740073005C0053006B006500740063006800550070002E0065007800650000002500000003000000001F1000000100000008000000700072006F006700720061006D000000000000000000000000000000 | |||
Executable files
3
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3996 | Patch.exe | C:\Users\admin\Desktop\SketchUp.exe | executable | |
MD5:BA1EAC86C724AA1CB012840C235936EA | SHA256:9F58D1880D52C49BBFAB70C7844BDE28C3C6C60DE62BB4B698A9282D467BBA74 | |||
| 3996 | Patch.exe | C:\Users\admin\Desktop\Style Builder.exe | executable | |
MD5:B148AF4FDF6062ACF8C224342A7310A8 | SHA256:95C4BDE6F302149F74879CCB1A78F2EC99854DBEA8E7CC3797995F2CDCF7E99F | |||
| 3996 | Patch.exe | C:\Users\admin\Desktop\LayOut.exe | executable | |
MD5:A7EB3274969B21E3BB2273B82A7DB2D9 | SHA256:175ACD942156EBAF451B998074EFA8B5E9027A7C0924BA02FC155EC8F67C7AE1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |