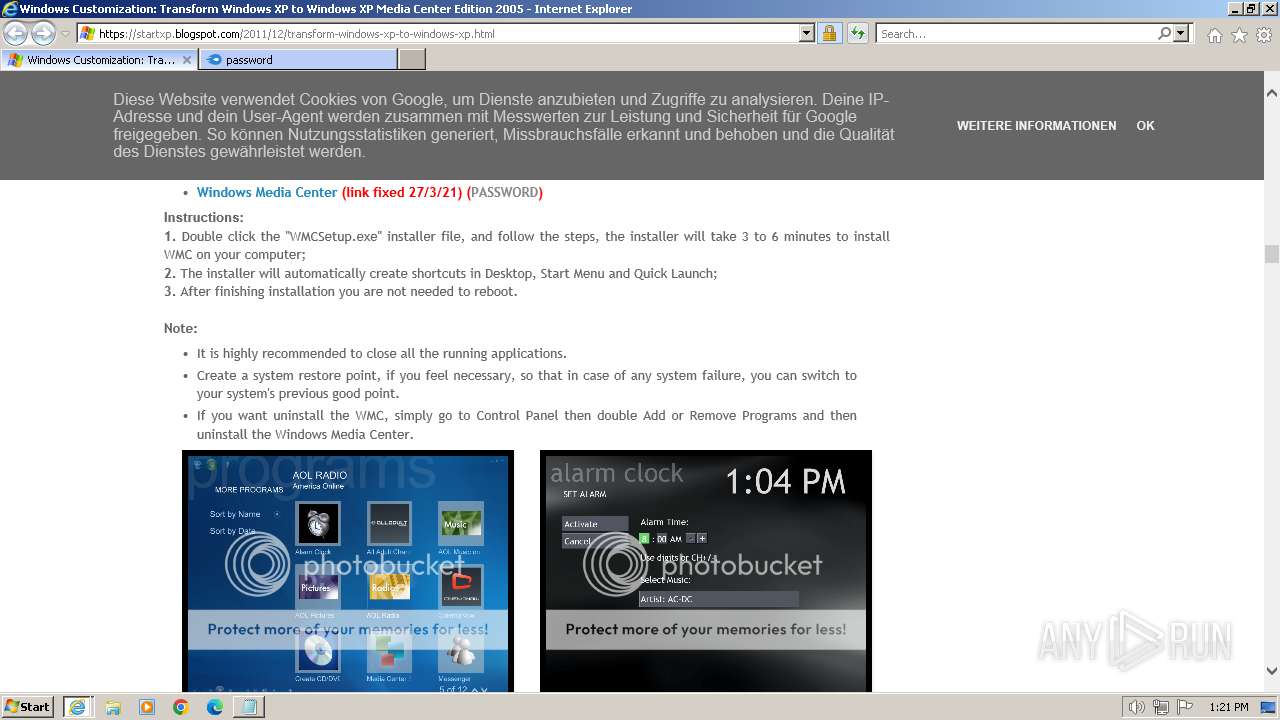
| URL: | https://startxp.blogspot.com/2011/12/transform-windows-xp-to-windows-xp.html |
| Full analysis: | https://app.any.run/tasks/752c8f4a-857e-401e-83ac-c1dbc998c522 |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2024, 13:21:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | FBDFC5F24AC3EC82F423B06571B91755 |
| SHA1: | 76983AB9F2ADD916C60303023CDF86DB9BDF615A |
| SHA256: | 2204EF703CF9D338249705AA0A535BD46310BC59649352A8ED0D07CF40768070 |
| SSDEEP: | 3:N8cWCSKMjMJMYkLM1JhuJ:2c+KJ+VAhuJ |
MALICIOUS
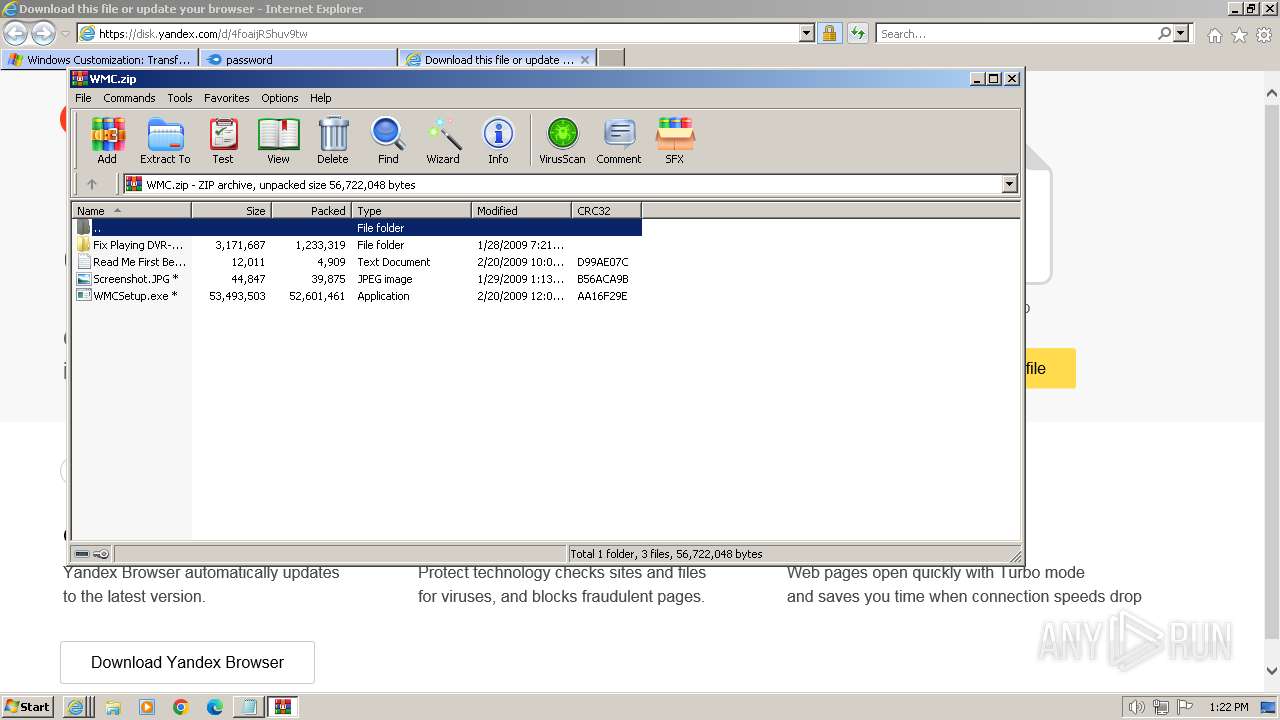
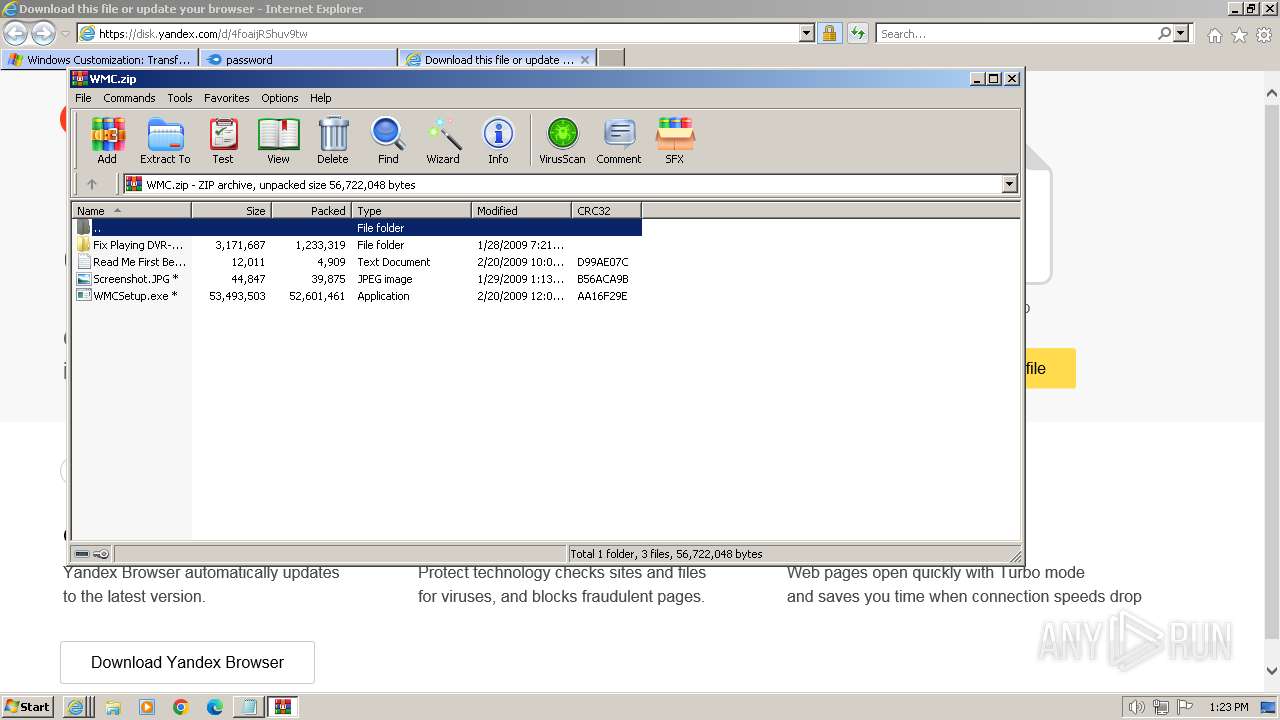
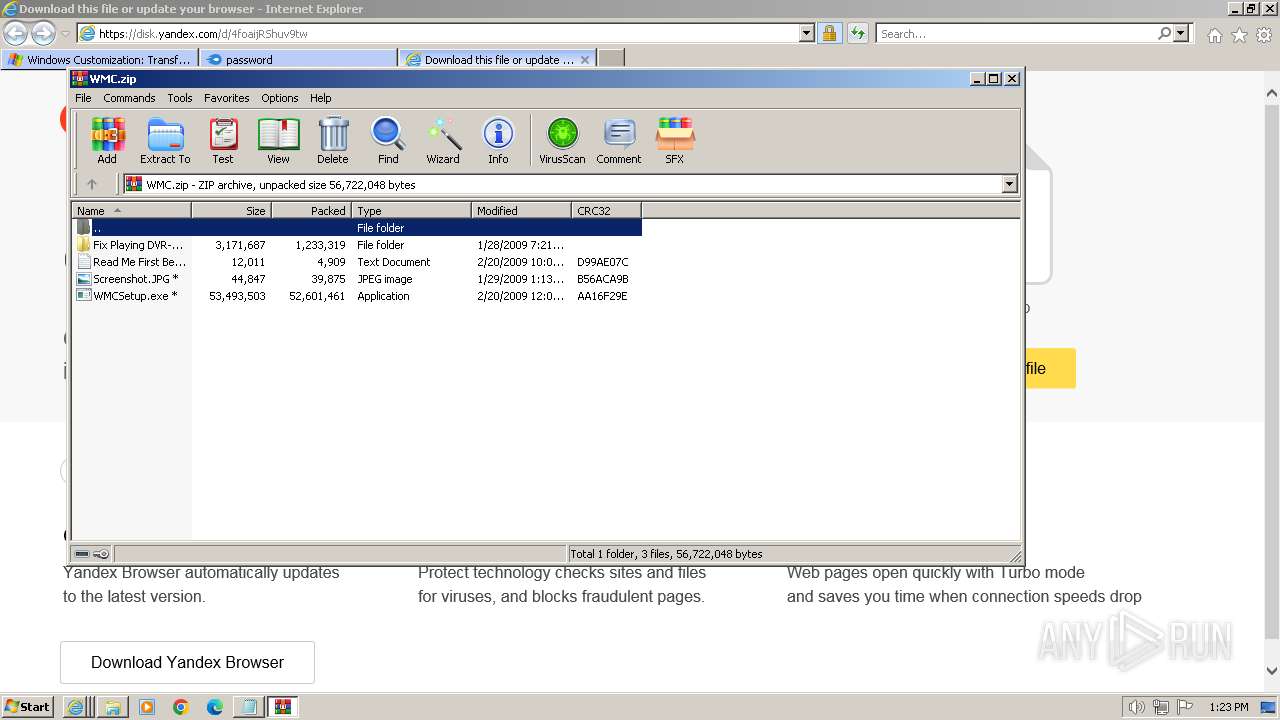
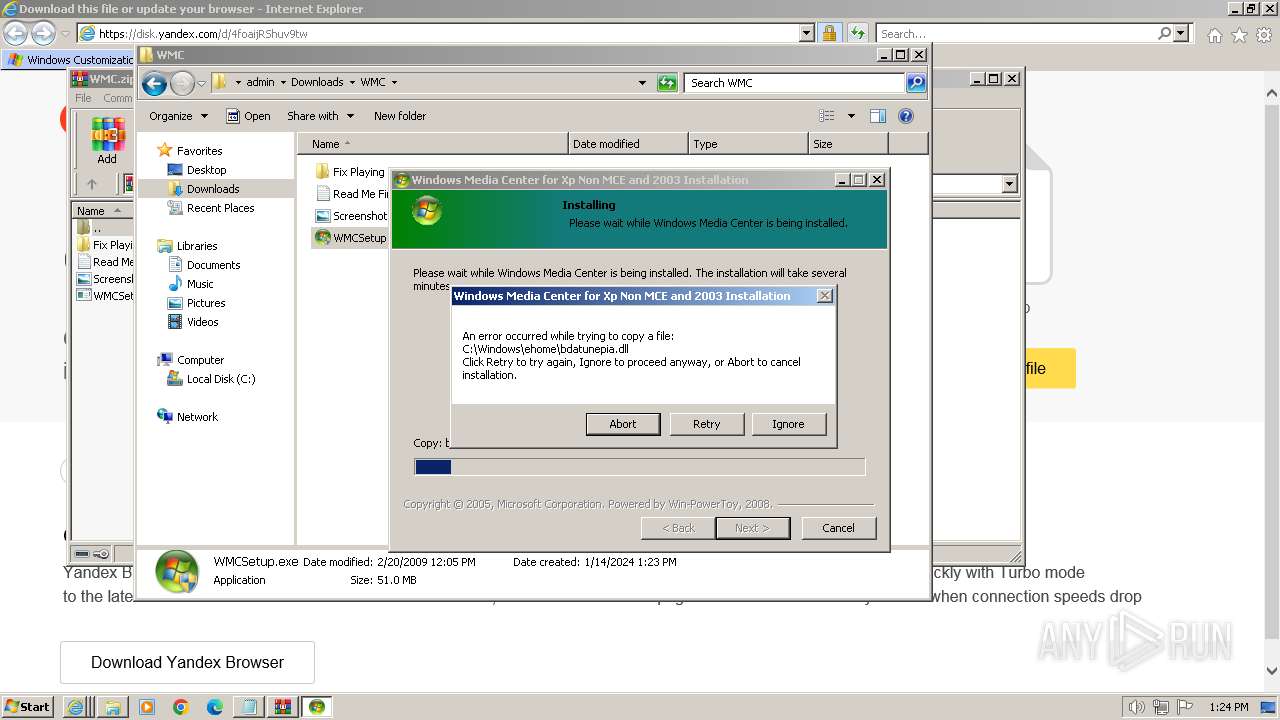
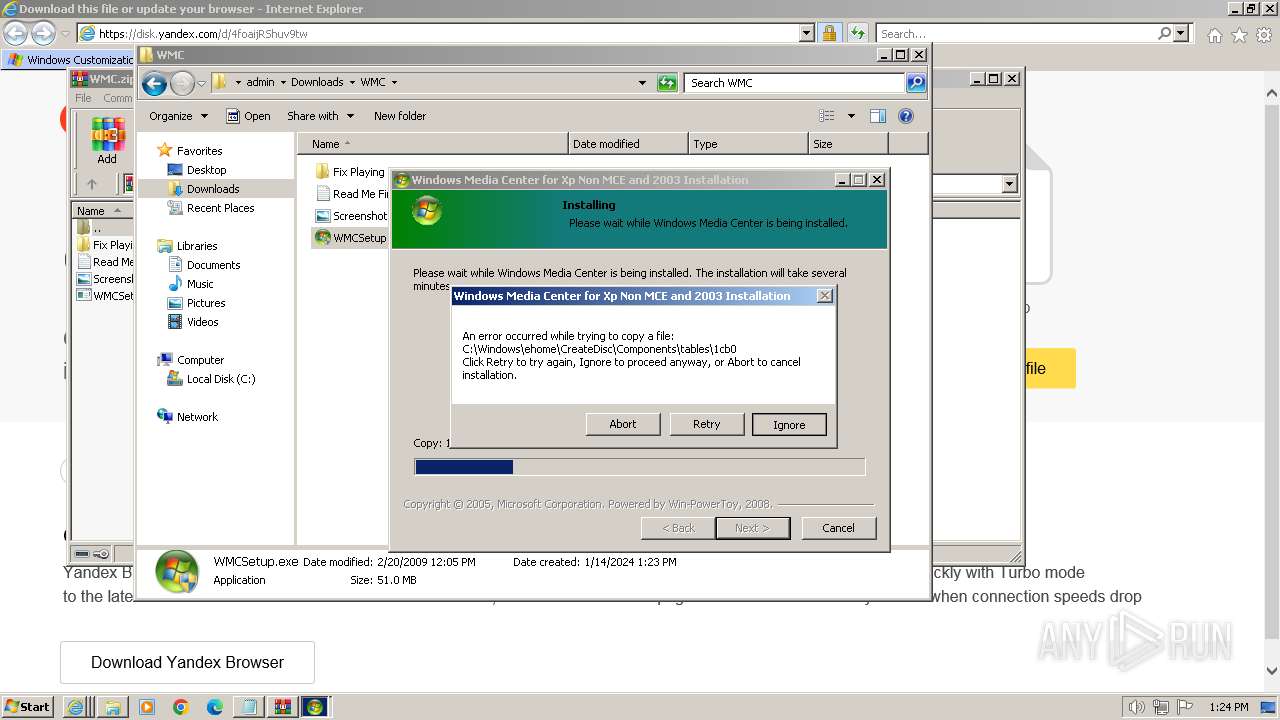
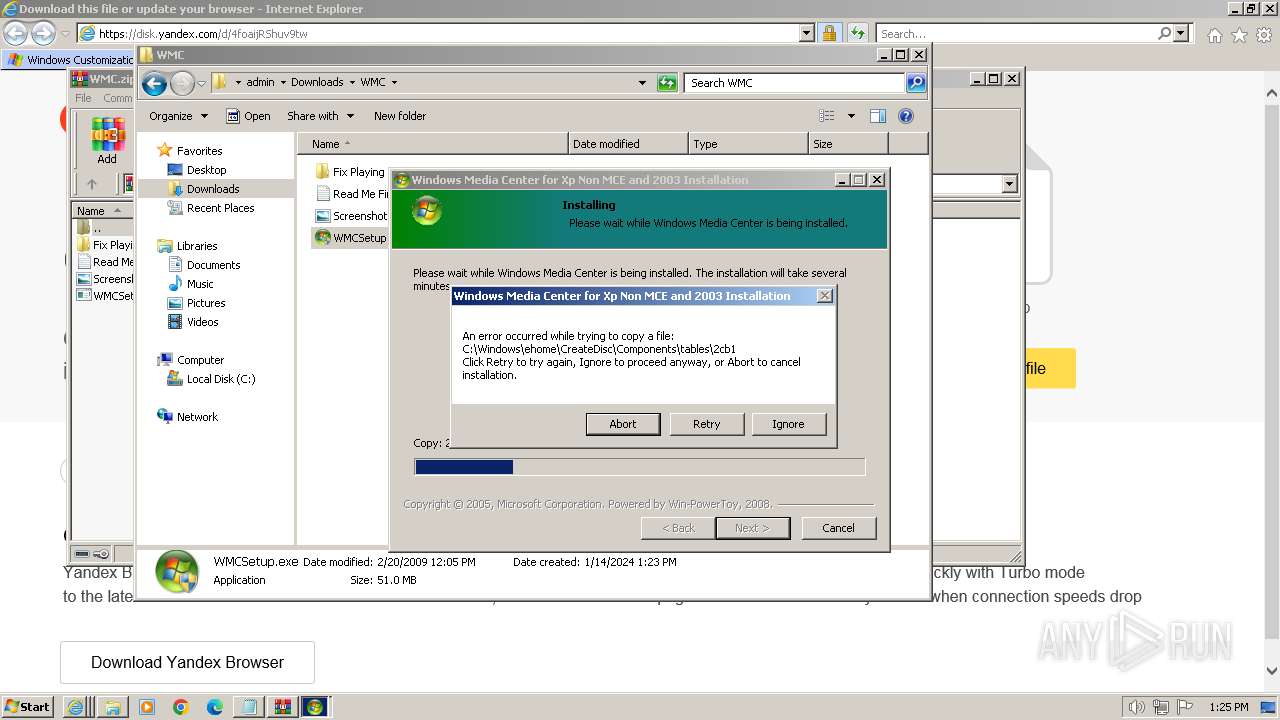
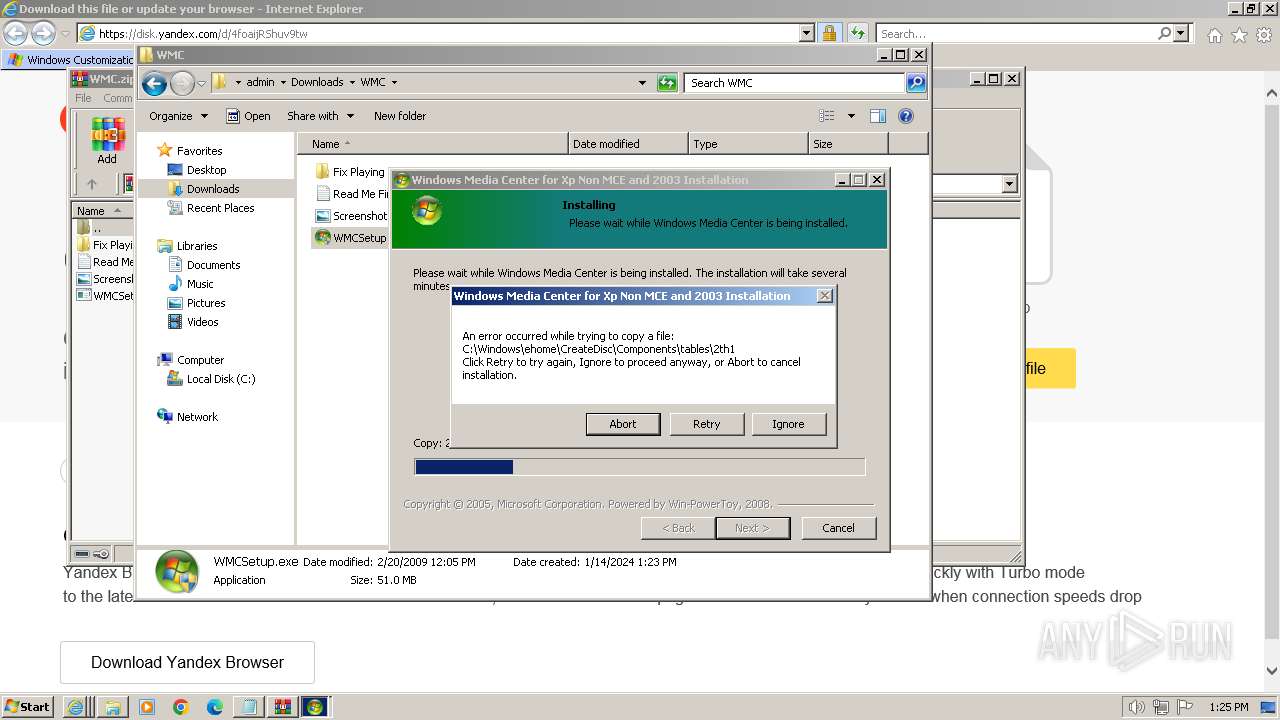
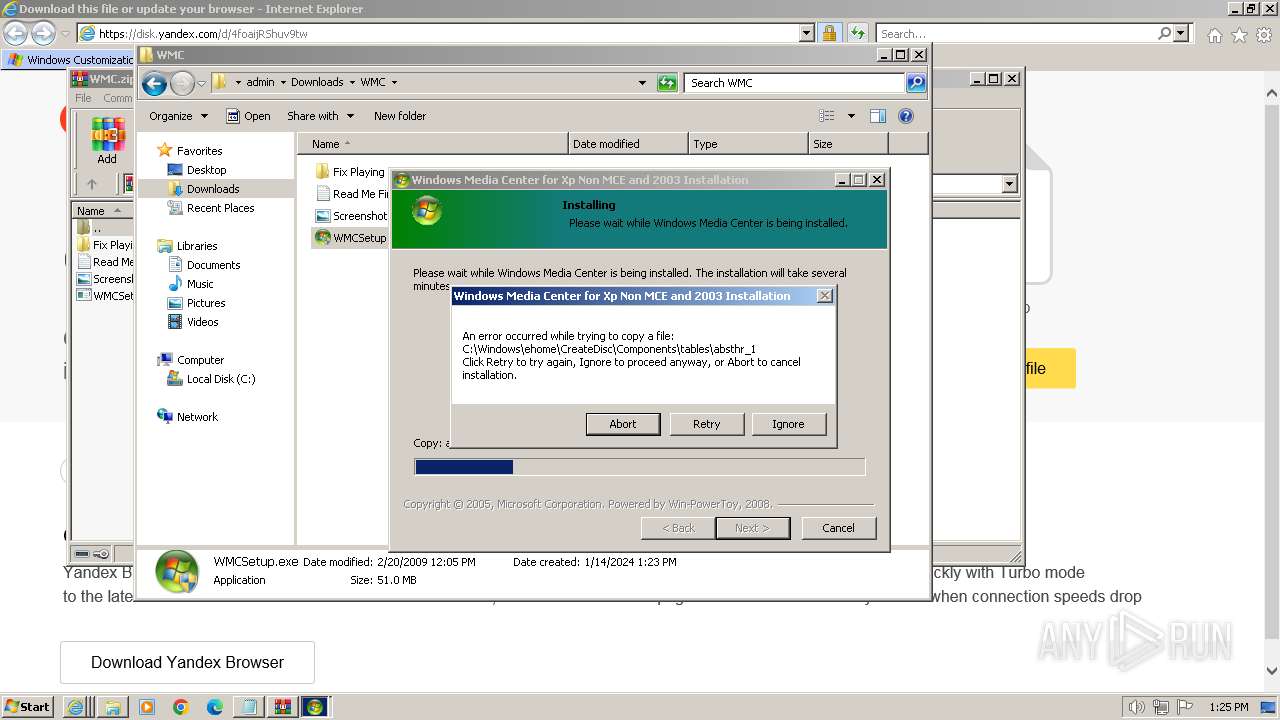
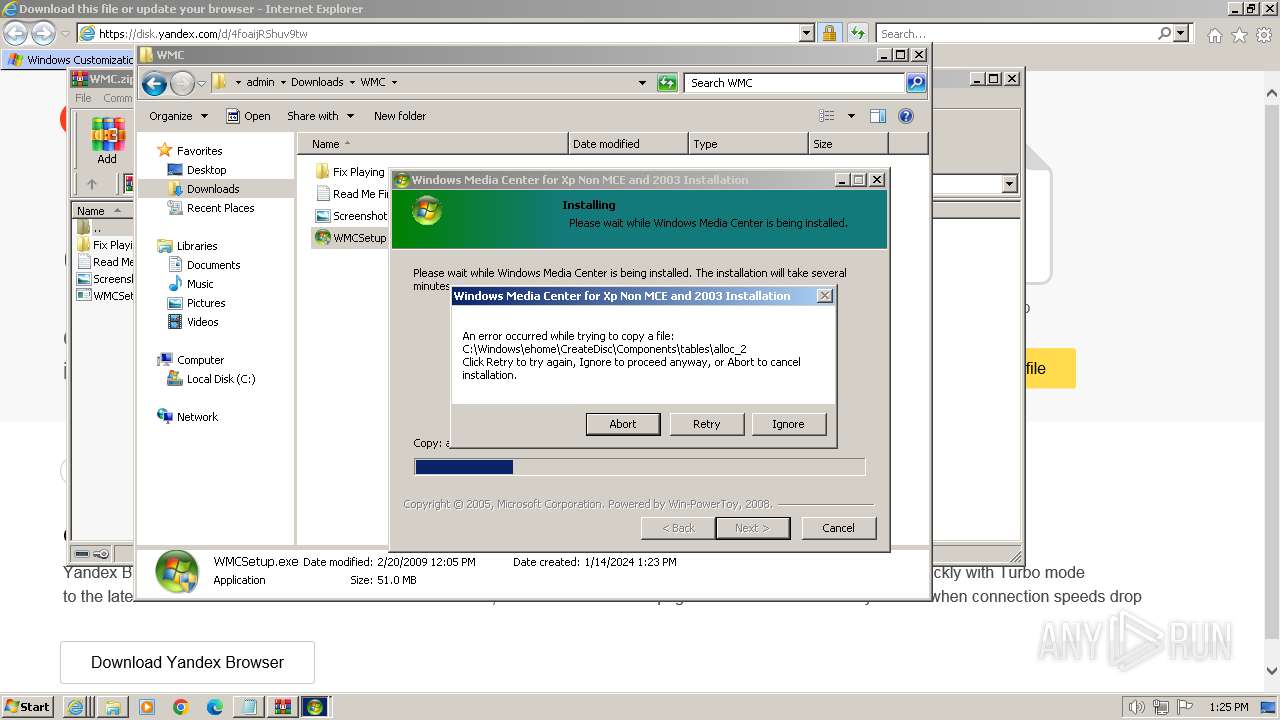
Drops the executable file immediately after the start
- WMCSetup.exe (PID: 3544)
- WMCSetup.exe (PID: 532)
Creates a writable file in the system directory
- WMCSetup.exe (PID: 3544)
- WMCSetup.exe (PID: 532)
SUSPICIOUS
Process drops legitimate windows executable
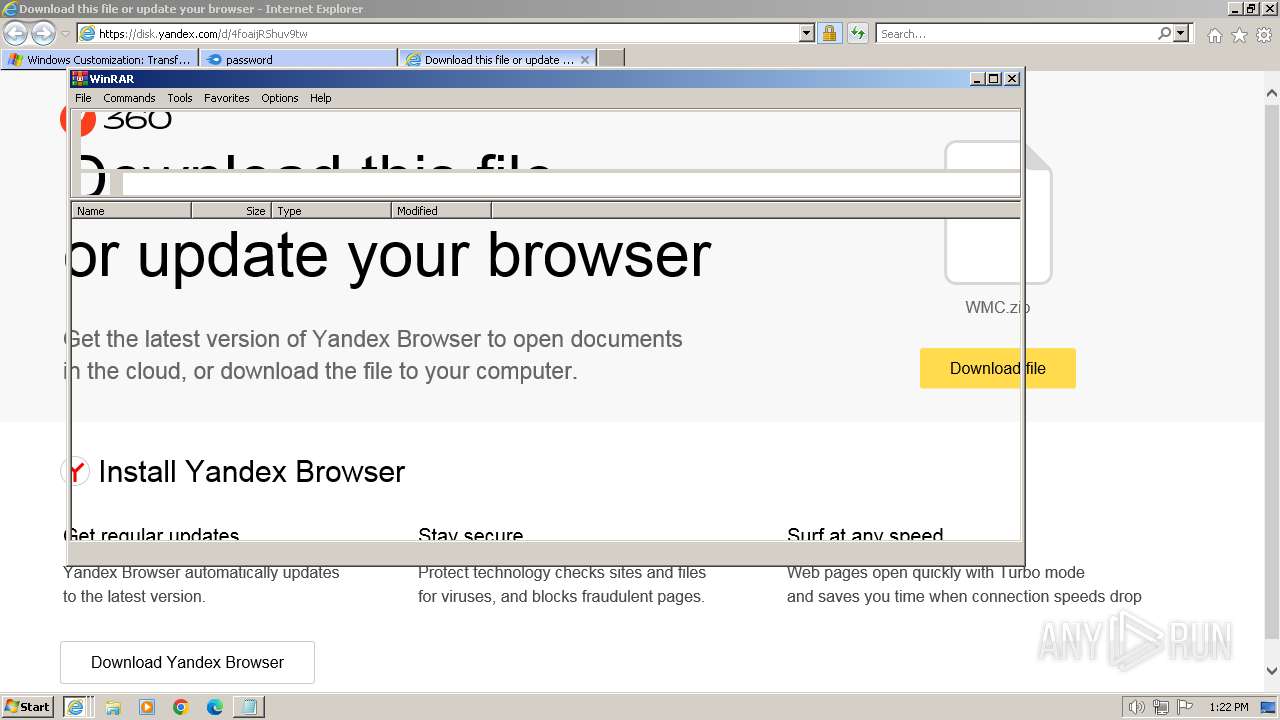
- WinRAR.exe (PID: 3072)
- WMCSetup.exe (PID: 3544)
- WMCSetup.exe (PID: 532)
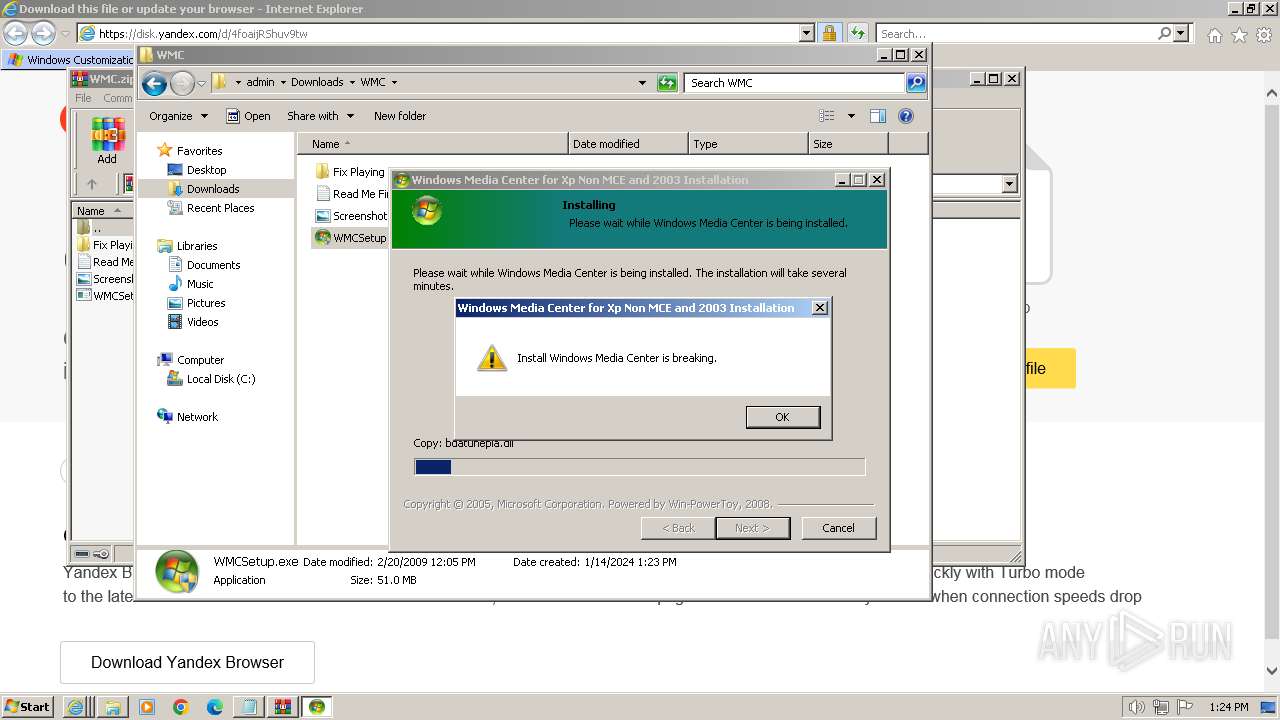
Uses TASKKILL.EXE to kill process
- WMCSetup.exe (PID: 3544)
- WMCSetup.exe (PID: 532)
Reads the Internet Settings
- WMCSetup.exe (PID: 3544)
- WMCSetup.exe (PID: 532)
Executable content was dropped or overwritten
- WMCSetup.exe (PID: 3544)
- WMCSetup.exe (PID: 532)
The process drops C-runtime libraries
- WMCSetup.exe (PID: 3544)
INFO
Application launched itself
- iexplore.exe (PID: 116)
The process uses the downloaded file
- WinRAR.exe (PID: 3072)
- iexplore.exe (PID: 116)
Manual execution by a user
- explorer.exe (PID: 2824)
- WMCSetup.exe (PID: 3352)
- WMCSetup.exe (PID: 3544)
- WMCSetup.exe (PID: 2836)
- WMCSetup.exe (PID: 3948)
- WMCSetup.exe (PID: 3316)
- WMCSetup.exe (PID: 532)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3072)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3072)
Checks supported languages
- WMCSetup.exe (PID: 3544)
- WMCSetup.exe (PID: 3948)
- WMCSetup.exe (PID: 532)
Create files in a temporary directory
- WMCSetup.exe (PID: 3544)
- WMCSetup.exe (PID: 3948)
- WMCSetup.exe (PID: 532)
Reads the computer name
- WMCSetup.exe (PID: 3544)
- WMCSetup.exe (PID: 532)
Creates files in the program directory
- WMCSetup.exe (PID: 3544)
- WMCSetup.exe (PID: 532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
123
Monitored processes
45
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://startxp.blogspot.com/2011/12/transform-windows-xp-to-windows-xp.html" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
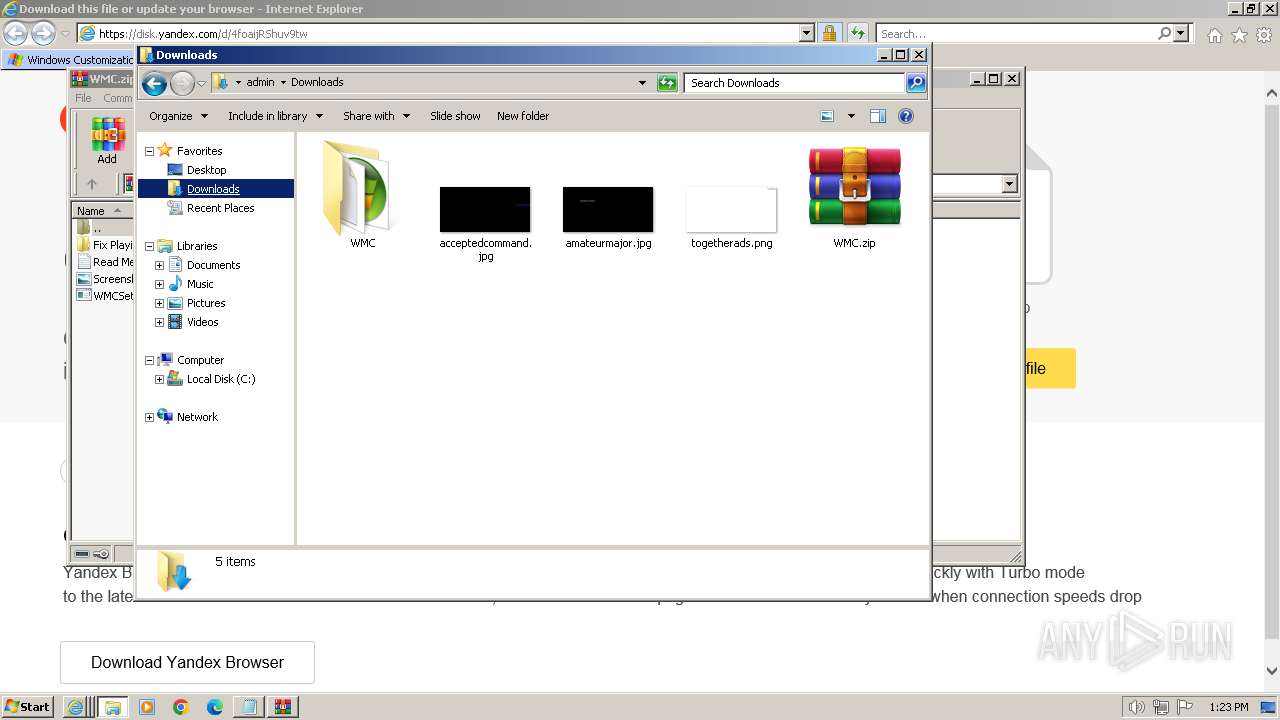
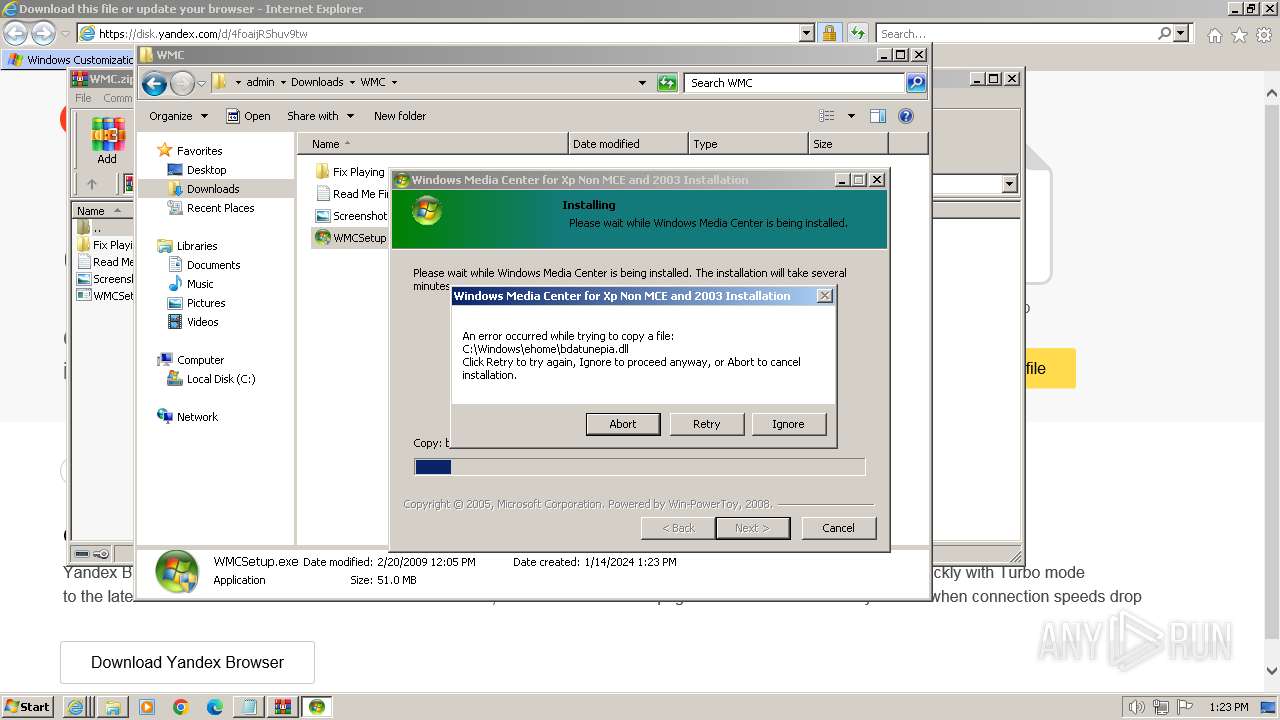
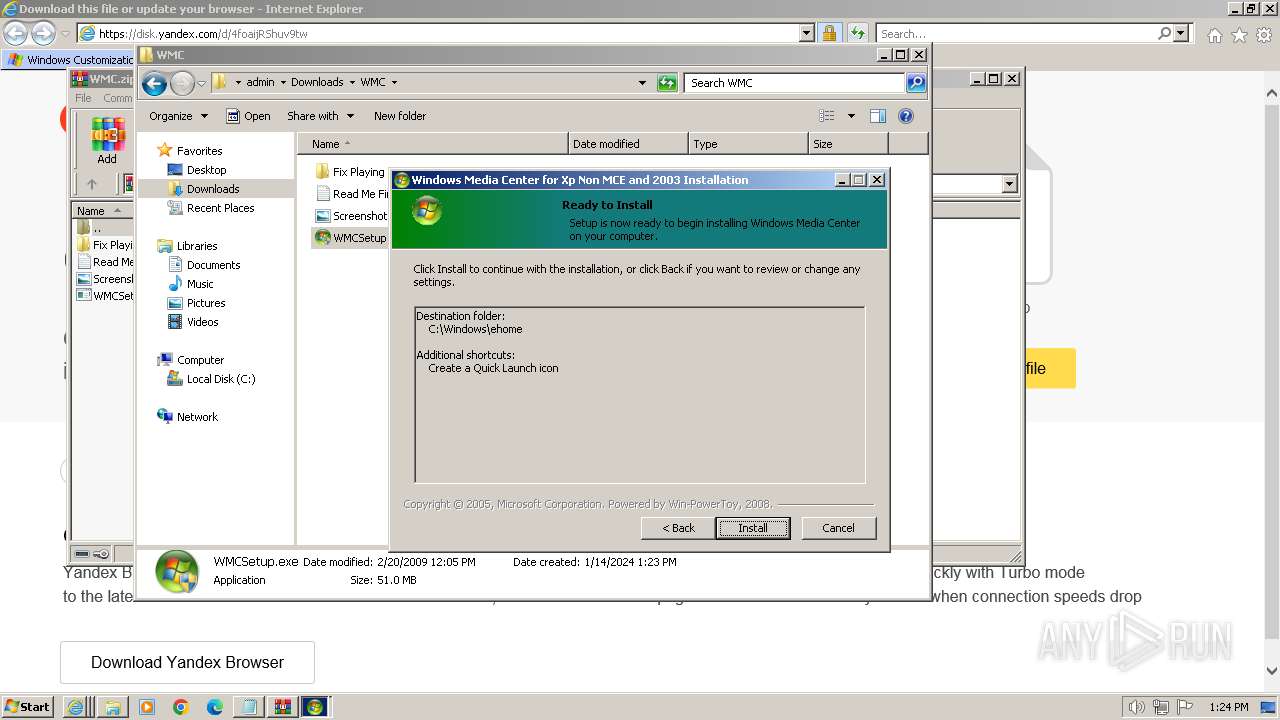
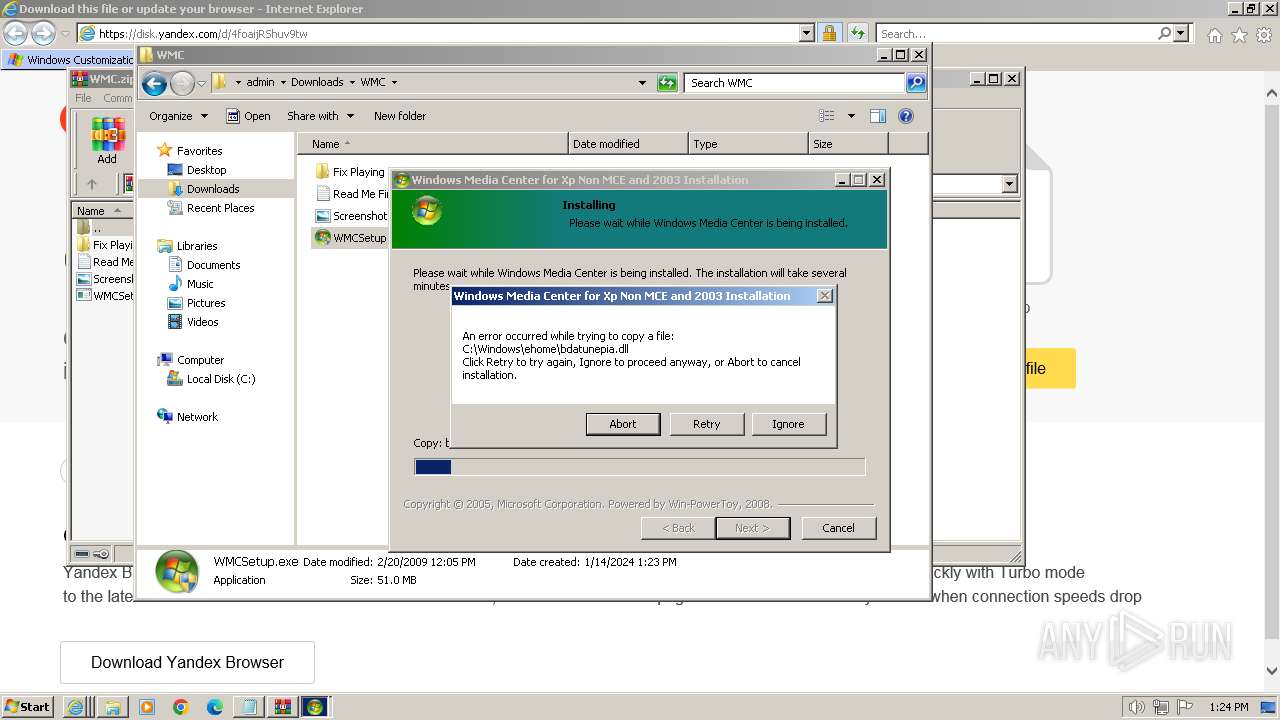
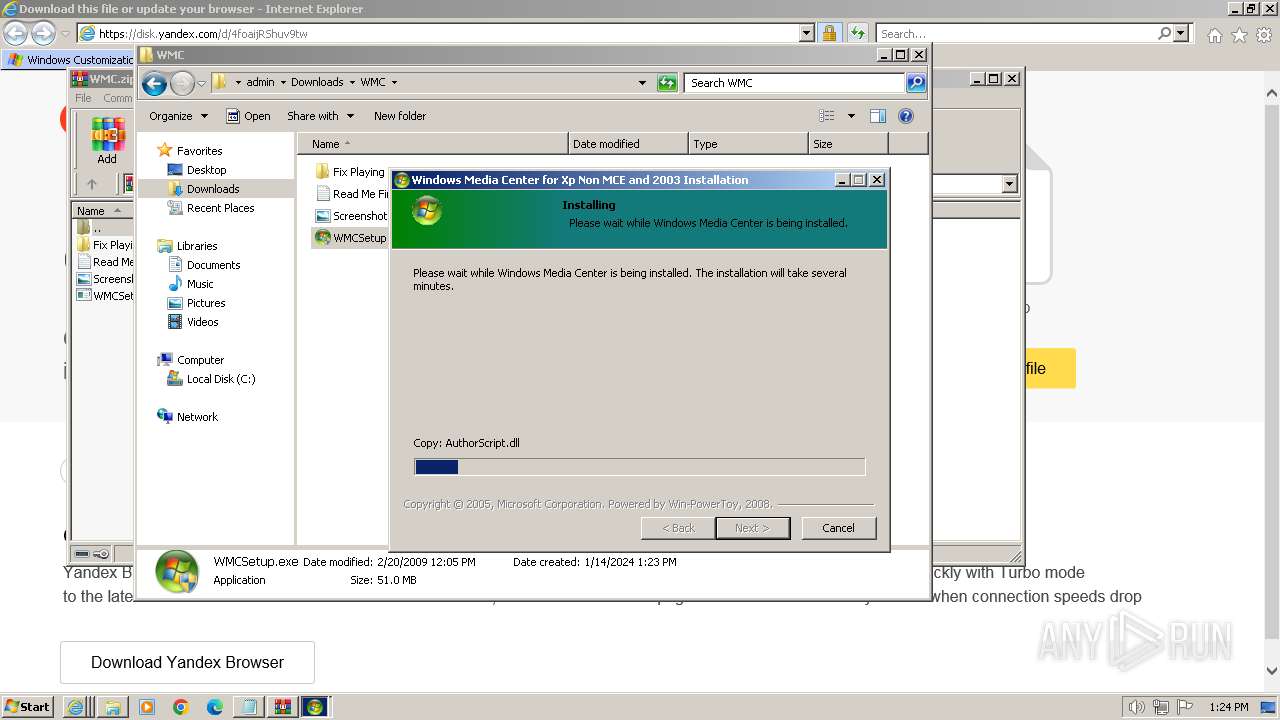
| 532 | "C:\Users\admin\Downloads\WMC\WMCSetup.exe" | C:\Users\admin\Downloads\WMC\WMCSetup.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Media Center 5.1.2715.2883 Installation Exit code: 0 Version: 5.1.2715.2883 Modules
| |||||||||||||||
| 548 | "C:\Windows\system32\taskkill.exe" /IM PlaylistEditor2.EXE /F | C:\Windows\System32\taskkill.exe | — | WMCSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 604 | "C:\Windows\system32\taskkill.exe" /IM ehmsas.exe /F | C:\Windows\System32\taskkill.exe | — | WMCSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 632 | "C:\Windows\system32\taskkill.exe" /IM ehSched.exe /F | C:\Windows\System32\taskkill.exe | — | WMCSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
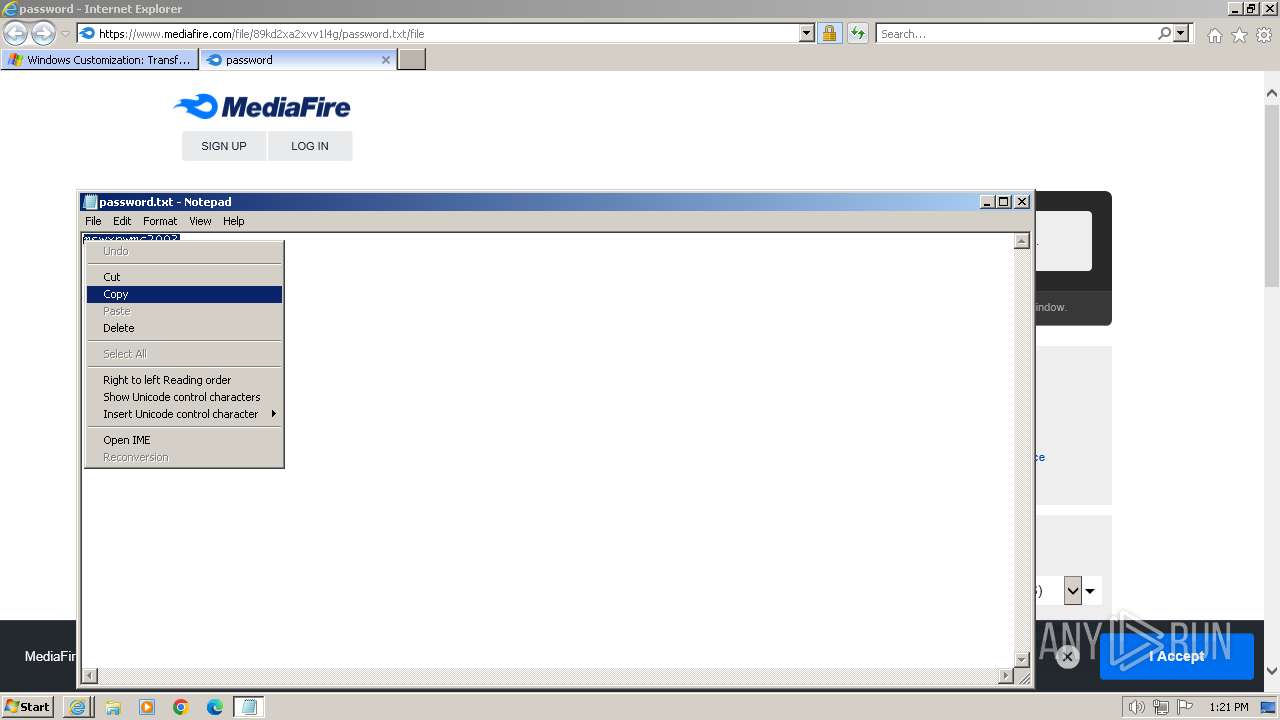
| 876 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\password.txt | C:\Windows\System32\notepad.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1020 | "C:\Windows\system32\taskkill.exe" /IM ehRecvr.exe /F | C:\Windows\System32\taskkill.exe | — | WMCSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1124 | "C:\Windows\system32\taskkill.exe" /IM ehtray.exe /F | C:\Windows\System32\taskkill.exe | — | WMCSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1192 | "C:\Windows\system32\taskkill.exe" /IM MCAlarmClock2.EXE /F | C:\Windows\System32\taskkill.exe | — | WMCSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1344 | "C:\Windows\system32\taskkill.exe" /IM ehtray.exe /F | C:\Windows\System32\taskkill.exe | — | WMCSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
41 036
Read events
40 891
Write events
139
Delete events
6
Modification events
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
43
Suspicious files
128
Text files
192
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:8875F2AE6B79E9FE4345B51B979C2EE4 | SHA256:BA7148E8B4B723405FF820C1821A654AD9644AF72D030511A00D771C2C7FA6E4 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:D54F8FE4A2AF7A244A87165235149D1E | SHA256:033A7CC897501229031A840916C83E209AA5C284463D65F31717E3AC3C5B5554 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\57646_orig[1].gif | image | |
MD5:9FE227C4190C4E1C4ACBB7F1043F5CAB | SHA256:4166E0BE497B1B3CEDAC45616E94E21A01C2AD5E7563E449BE72A4645D993EC6 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\cookienotice[1].js | text | |
MD5:A705132A2174F88E196EC3610D68FAA8 | SHA256:068FFE90977F2B5B2DC2EF18572166E85281BD0ECB31C4902464B23DB54D2568 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\mce[1].gif | image | |
MD5:8EDDC281A6D5BF3A436CC32ADF621627 | SHA256:73828B14956D072C35BBB133A90A94DD347A7D06843311D52A27874E53980595 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F07644E38ED7C9F37D11EEC6D4335E02_9D33622E5AB2773AF26A81395E3DD2B8 | binary | |
MD5:3F42944D51AE91646F4D8C20822D758B | SHA256:EBB2F1A4C1AB0FF2B894502F360F53F7CD5D2B19E08C5F95DE5EEC64F2619085 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:DB09F325205B08FDF125A2888AA48843 | SHA256:73D160BD691CDDF6ABB842AB070CA8B3402B310A52002EDB3DC7926598C40686 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:20CE1CBD35EB79A2357DC2B632E64CED | SHA256:CEAE62B00544ED92D4A3B5C2B15B181EBFC8AF1030B2E55FDAE5204FB341B762 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
162
DNS requests
73
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2204 | iexplore.exe | GET | 200 | 184.24.77.182:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?53bfb7cf8a6cf97e | unknown | compressed | 4.66 Kb | unknown |
2204 | iexplore.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | binary | 1.49 Kb | unknown |
2204 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQD2CljflQhiLwnqCuPAdwck | unknown | binary | 472 b | unknown |
2204 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDbnyPw2K%2B4Tgq%2FJDNLmp40 | unknown | binary | 472 b | unknown |
2204 | iexplore.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkpLy9ROx7U76vGUhC06D6E%3D | unknown | binary | 1.37 Kb | unknown |
2204 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCc21SZGmxMgAqM79mihzX3 | unknown | binary | 472 b | unknown |
2204 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCAPCRpfvazdAnzYNtm9aj3 | unknown | binary | 472 b | unknown |
2204 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCc21SZGmxMgAqM79mihzX3 | unknown | binary | 472 b | unknown |
116 | iexplore.exe | GET | 304 | 184.24.77.182:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ce83dcf70518f919 | unknown | — | — | unknown |
2204 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECbzjAowsPTyEMLulIc7EGw%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2204 | iexplore.exe | 142.250.184.193:443 | startxp.blogspot.com | GOOGLE | US | whitelisted |
2204 | iexplore.exe | 184.24.77.182:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2204 | iexplore.exe | 142.250.186.163:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2204 | iexplore.exe | 172.217.18.105:443 | www.blogger.com | GOOGLE | US | unknown |
2204 | iexplore.exe | 143.204.215.89:443 | i897.photobucket.com | AMAZON-02 | US | unknown |
2204 | iexplore.exe | 142.250.184.238:443 | apis.google.com | GOOGLE | US | whitelisted |
2204 | iexplore.exe | 216.58.206.33:443 | 1.bp.blogspot.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
startxp.blogspot.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.blogger.com |
| shared |
apis.google.com |
| whitelisted |
i897.photobucket.com |
| unknown |
1.bp.blogspot.com |
| whitelisted |
2.bp.blogspot.com |
| whitelisted |
resources.blogblog.com |
| whitelisted |
blogger.googleusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |