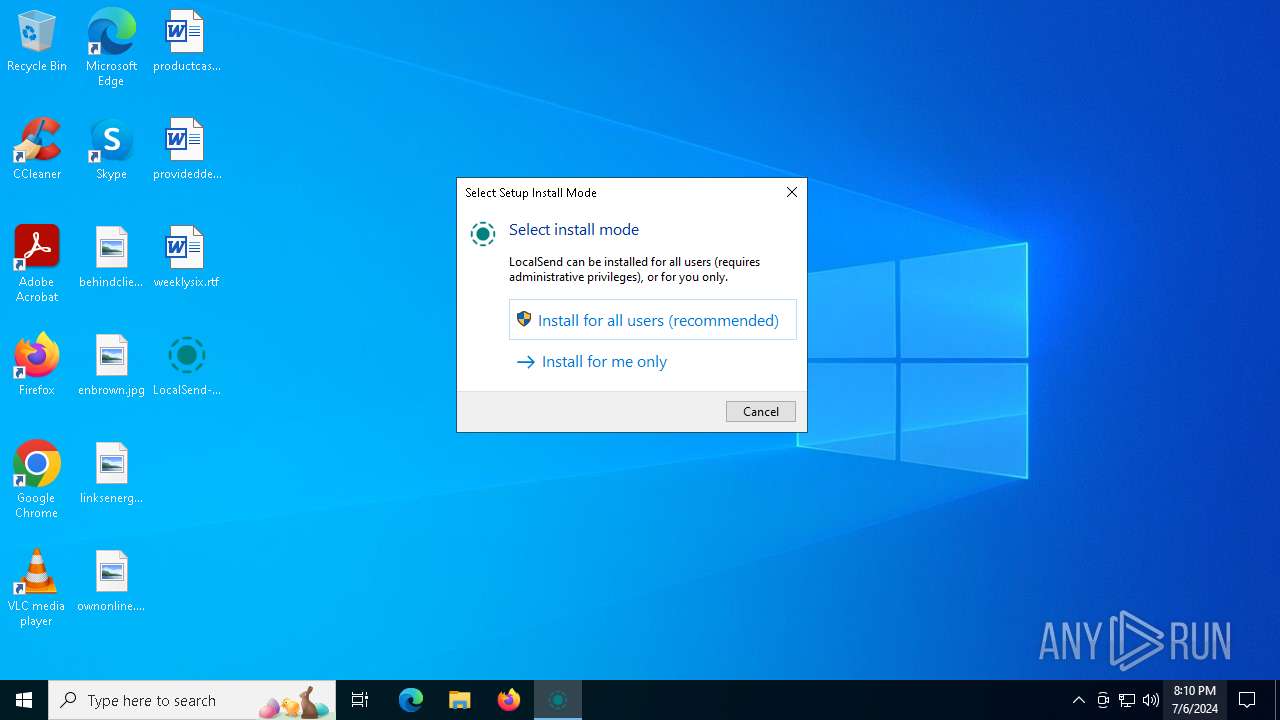
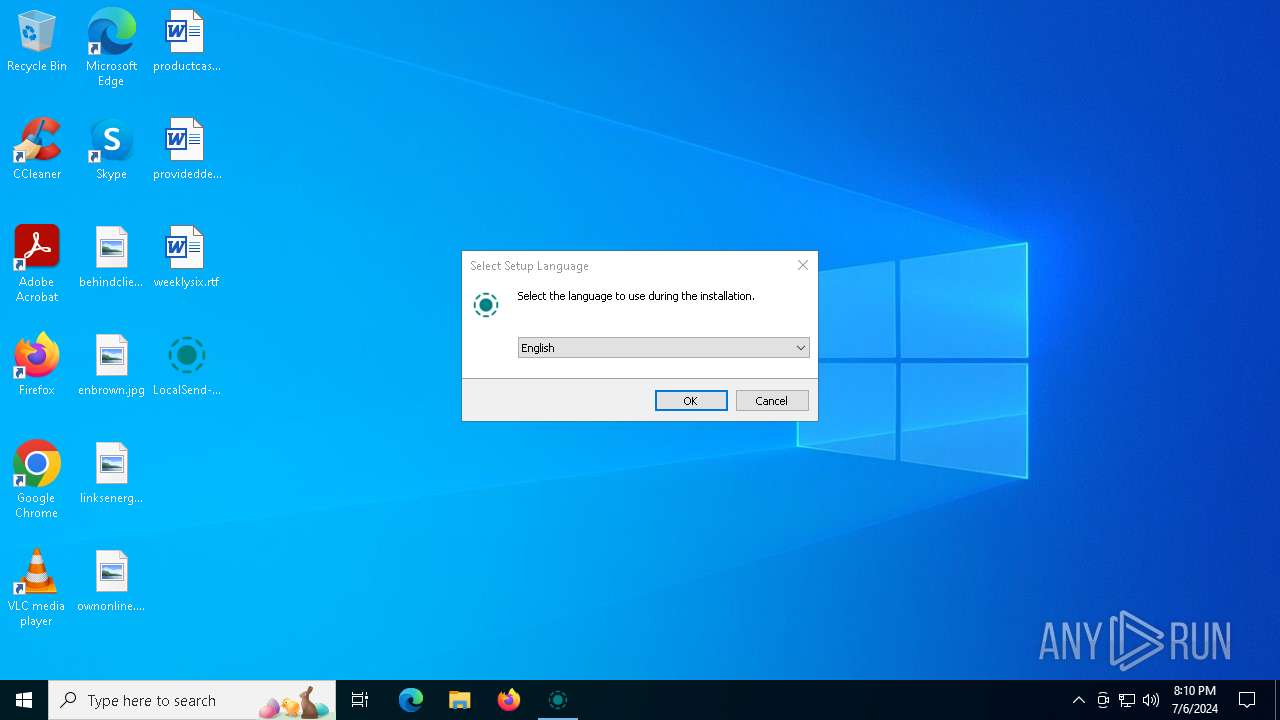
| File name: | LocalSend-1.14.0-windows-x86-64.exe |
| Full analysis: | https://app.any.run/tasks/ce45daf9-a949-40b8-8b9d-c4d47f43063d |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2024, 20:10:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C044EE4A8685FE32937E995DDE654511 |
| SHA1: | 45C05A60BC2E8BD770148DC2C52867A540434B8E |
| SHA256: | 22023DF4CF010D66C11DEF61B183CF6387922CB9AB6E4AB95A1695C56C9AB6DC |
| SSDEEP: | 98304:m+cD4dn2lO4MSSJHtxVOFKB/SZeC+8x9hpFAZv+bE4o5m1hLKmZEAPNx74hucmak:NJEKMG3/d7DfDKBA2LSYFt |
MALICIOUS
Drops the executable file immediately after the start
- LocalSend-1.14.0-windows-x86-64.exe (PID: 1228)
- LocalSend-1.14.0-windows-x86-64.exe (PID: 5004)
- LocalSend-1.14.0-windows-x86-64.tmp (PID: 1120)
SUSPICIOUS
Reads security settings of Internet Explorer
- LocalSend-1.14.0-windows-x86-64.tmp (PID: 5432)
Executable content was dropped or overwritten
- LocalSend-1.14.0-windows-x86-64.exe (PID: 1228)
- LocalSend-1.14.0-windows-x86-64.tmp (PID: 1120)
- LocalSend-1.14.0-windows-x86-64.exe (PID: 5004)
Reads the date of Windows installation
- LocalSend-1.14.0-windows-x86-64.tmp (PID: 5432)
Reads the Windows owner or organization settings
- LocalSend-1.14.0-windows-x86-64.tmp (PID: 1120)
There is functionality for taking screenshot (YARA)
- localsend_app.exe (PID: 4628)
INFO
Checks supported languages
- LocalSend-1.14.0-windows-x86-64.exe (PID: 1228)
- LocalSend-1.14.0-windows-x86-64.tmp (PID: 5432)
- LocalSend-1.14.0-windows-x86-64.exe (PID: 5004)
- LocalSend-1.14.0-windows-x86-64.tmp (PID: 1120)
- localsend_app.exe (PID: 4628)
Reads the computer name
- LocalSend-1.14.0-windows-x86-64.tmp (PID: 5432)
- LocalSend-1.14.0-windows-x86-64.tmp (PID: 1120)
- localsend_app.exe (PID: 4628)
Process checks computer location settings
- LocalSend-1.14.0-windows-x86-64.tmp (PID: 5432)
Create files in a temporary directory
- LocalSend-1.14.0-windows-x86-64.exe (PID: 1228)
- LocalSend-1.14.0-windows-x86-64.exe (PID: 5004)
- LocalSend-1.14.0-windows-x86-64.tmp (PID: 1120)
Creates files in the program directory
- LocalSend-1.14.0-windows-x86-64.tmp (PID: 1120)
Creates a software uninstall entry
- LocalSend-1.14.0-windows-x86-64.tmp (PID: 1120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 138240 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Tien Do Nam |
| FileDescription: | LocalSend Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | LocalSend |
| ProductVersion: | 1.14.0 |
Total processes
128
Monitored processes
5
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1120 | "C:\Users\admin\AppData\Local\Temp\is-OLJRB.tmp\LocalSend-1.14.0-windows-x86-64.tmp" /SL5="$50300,11430850,881152,C:\Users\admin\Desktop\LocalSend-1.14.0-windows-x86-64.exe" /SPAWNWND=$602A2 /NOTIFYWND=$5025A /ALLUSERS | C:\Users\admin\AppData\Local\Temp\is-OLJRB.tmp\LocalSend-1.14.0-windows-x86-64.tmp | LocalSend-1.14.0-windows-x86-64.exe | ||||||||||||
User: admin Company: Tien Do Nam Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1228 | "C:\Users\admin\Desktop\LocalSend-1.14.0-windows-x86-64.exe" | C:\Users\admin\Desktop\LocalSend-1.14.0-windows-x86-64.exe | explorer.exe | ||||||||||||
User: admin Company: Tien Do Nam Integrity Level: MEDIUM Description: LocalSend Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 4628 | "C:\Program Files\LocalSend\localsend_app.exe" | C:\Program Files\LocalSend\localsend_app.exe | LocalSend-1.14.0-windows-x86-64.tmp | ||||||||||||
User: admin Company: org.localsend Integrity Level: MEDIUM Description: localsend_app Version: 1.14.0+45 Modules
| |||||||||||||||
| 5004 | "C:\Users\admin\Desktop\LocalSend-1.14.0-windows-x86-64.exe" /SPAWNWND=$602A2 /NOTIFYWND=$5025A /ALLUSERS | C:\Users\admin\Desktop\LocalSend-1.14.0-windows-x86-64.exe | LocalSend-1.14.0-windows-x86-64.tmp | ||||||||||||
User: admin Company: Tien Do Nam Integrity Level: HIGH Description: LocalSend Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 5432 | "C:\Users\admin\AppData\Local\Temp\is-PUGBF.tmp\LocalSend-1.14.0-windows-x86-64.tmp" /SL5="$5025A,11430850,881152,C:\Users\admin\Desktop\LocalSend-1.14.0-windows-x86-64.exe" | C:\Users\admin\AppData\Local\Temp\is-PUGBF.tmp\LocalSend-1.14.0-windows-x86-64.tmp | — | LocalSend-1.14.0-windows-x86-64.exe | |||||||||||
User: admin Company: Tien Do Nam Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
2 411
Read events
2 376
Write events
29
Delete events
6
Modification events
| (PID) Process: | (1120) LocalSend-1.14.0-windows-x86-64.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 60040000D6DE3B93E0CFDA01 | |||
| (PID) Process: | (1120) LocalSend-1.14.0-windows-x86-64.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: F5670871FBF65E531F1025A84E77C335AF1A7F90481620AA3138F4A98A354074 | |||
| (PID) Process: | (1120) LocalSend-1.14.0-windows-x86-64.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (1120) LocalSend-1.14.0-windows-x86-64.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\LocalSend\localsend_app.exe | |||
| (PID) Process: | (1120) LocalSend-1.14.0-windows-x86-64.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: C9AB8BAD1244F6922711FDEB043B6E1C26B1241E20C1BFB159BD9773742F9D10 | |||
| (PID) Process: | (1120) LocalSend-1.14.0-windows-x86-64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{00809252-FEC6-448E-83B4-E7F55AE7E47D}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.2 | |||
| (PID) Process: | (1120) LocalSend-1.14.0-windows-x86-64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{00809252-FEC6-448E-83B4-E7F55AE7E47D}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\LocalSend | |||
| (PID) Process: | (1120) LocalSend-1.14.0-windows-x86-64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{00809252-FEC6-448E-83B4-E7F55AE7E47D}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\LocalSend\ | |||
| (PID) Process: | (1120) LocalSend-1.14.0-windows-x86-64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{00809252-FEC6-448E-83B4-E7F55AE7E47D}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: (Default) | |||
| (PID) Process: | (1120) LocalSend-1.14.0-windows-x86-64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{00809252-FEC6-448E-83B4-E7F55AE7E47D}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
33
Suspicious files
32
Text files
36
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1228 | LocalSend-1.14.0-windows-x86-64.exe | C:\Users\admin\AppData\Local\Temp\is-PUGBF.tmp\LocalSend-1.14.0-windows-x86-64.tmp | executable | |
MD5:2B60E089AD04332EFDB1052917C6DB3A | SHA256:4835CC82A47927F31D300DB2FB51C31F66BC3865B77118E758D973DBFEEF1A97 | |||
| 1120 | LocalSend-1.14.0-windows-x86-64.tmp | C:\Program Files\LocalSend\unins000.exe | executable | |
MD5:2B60E089AD04332EFDB1052917C6DB3A | SHA256:4835CC82A47927F31D300DB2FB51C31F66BC3865B77118E758D973DBFEEF1A97 | |||
| 5004 | LocalSend-1.14.0-windows-x86-64.exe | C:\Users\admin\AppData\Local\Temp\is-OLJRB.tmp\LocalSend-1.14.0-windows-x86-64.tmp | executable | |
MD5:2B60E089AD04332EFDB1052917C6DB3A | SHA256:4835CC82A47927F31D300DB2FB51C31F66BC3865B77118E758D973DBFEEF1A97 | |||
| 1120 | LocalSend-1.14.0-windows-x86-64.tmp | C:\Program Files\LocalSend\is-LIH6D.tmp | executable | |
MD5:E65954F42D10180D281BFB3D059582E9 | SHA256:566E64EDCFC1AC49365F1FD3EFCD827526DD6B6E2F66DAB3B52F0E1BC248FF4A | |||
| 1120 | LocalSend-1.14.0-windows-x86-64.tmp | C:\Program Files\LocalSend\connectivity_plus_plugin.dll | executable | |
MD5:E65954F42D10180D281BFB3D059582E9 | SHA256:566E64EDCFC1AC49365F1FD3EFCD827526DD6B6E2F66DAB3B52F0E1BC248FF4A | |||
| 1120 | LocalSend-1.14.0-windows-x86-64.tmp | C:\Program Files\LocalSend\localsend_app.exe | executable | |
MD5:821FF9DCD94908850D254579F3168847 | SHA256:42265B18327115957F629C707CDBE7B95A3030BE7AF8FBF1CC0469675AC2E4FB | |||
| 1120 | LocalSend-1.14.0-windows-x86-64.tmp | C:\Program Files\LocalSend\is-BFAGD.tmp | executable | |
MD5:9E8D93805F8670C87B23D479749F40FF | SHA256:B300FA025F370619E5631A75179B9E6DDB44D4BE2152D80CD48D68B78A4FA381 | |||
| 1120 | LocalSend-1.14.0-windows-x86-64.tmp | C:\Users\admin\AppData\Local\Temp\is-HNMAS.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 1120 | LocalSend-1.14.0-windows-x86-64.tmp | C:\Program Files\LocalSend\desktop_drop_plugin.dll | executable | |
MD5:9E8D93805F8670C87B23D479749F40FF | SHA256:B300FA025F370619E5631A75179B9E6DDB44D4BE2152D80CD48D68B78A4FA381 | |||
| 1120 | LocalSend-1.14.0-windows-x86-64.tmp | C:\Program Files\LocalSend\dynamic_color_plugin.dll | executable | |
MD5:6171C7BCEC51C71E83A34FECC48C349A | SHA256:13F646A497605AF15BAAD9281578AE84CADEA8BB8AA4EACD9A4F1159039093D0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
30
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1452 | RUXIMICS.exe | GET | 200 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1972 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1452 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1972 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | POST | 200 | 13.89.179.10:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
— | — | GET | 200 | 92.123.104.34:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=r&setlang=en-US&cc=US&nohs=1&qfm=1&cp=1&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=8217ecd434a24e319c68e41132cd851d | unknown | binary | 6.81 Kb | unknown |
— | — | GET | 200 | 92.123.104.40:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=rege&setlang=en-US&cc=US&nohs=1&qfm=1&cp=4&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=9e5ca3b8609c45288674b78f53cdefa2 | unknown | binary | 4.99 Kb | unknown |
— | — | GET | 200 | 92.123.104.11:443 | https://www.bing.com/rb/18/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DyIrb3t-gQF4cnWyAbUBK6UBK7gB&or=w | unknown | s | 21.3 Kb | unknown |
— | — | GET | 200 | 92.123.104.28:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=regedi&setlang=en-US&cc=US&nohs=1&qfm=1&cp=6&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=46856f19730442d7bfc8a588e4a577aa | unknown | binary | 4.02 Kb | unknown |
— | — | GET | 200 | 92.123.104.33:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=re&setlang=en-US&cc=US&nohs=1&qfm=1&cp=2&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=886f7dfaf8a943d7ac515843550c84b9 | unknown | binary | 6.60 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1928 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1452 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1972 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1452 | RUXIMICS.exe | 23.48.23.194:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1972 | MoUsoCoreWorker.exe | 23.48.23.194:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1452 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1972 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6004 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |