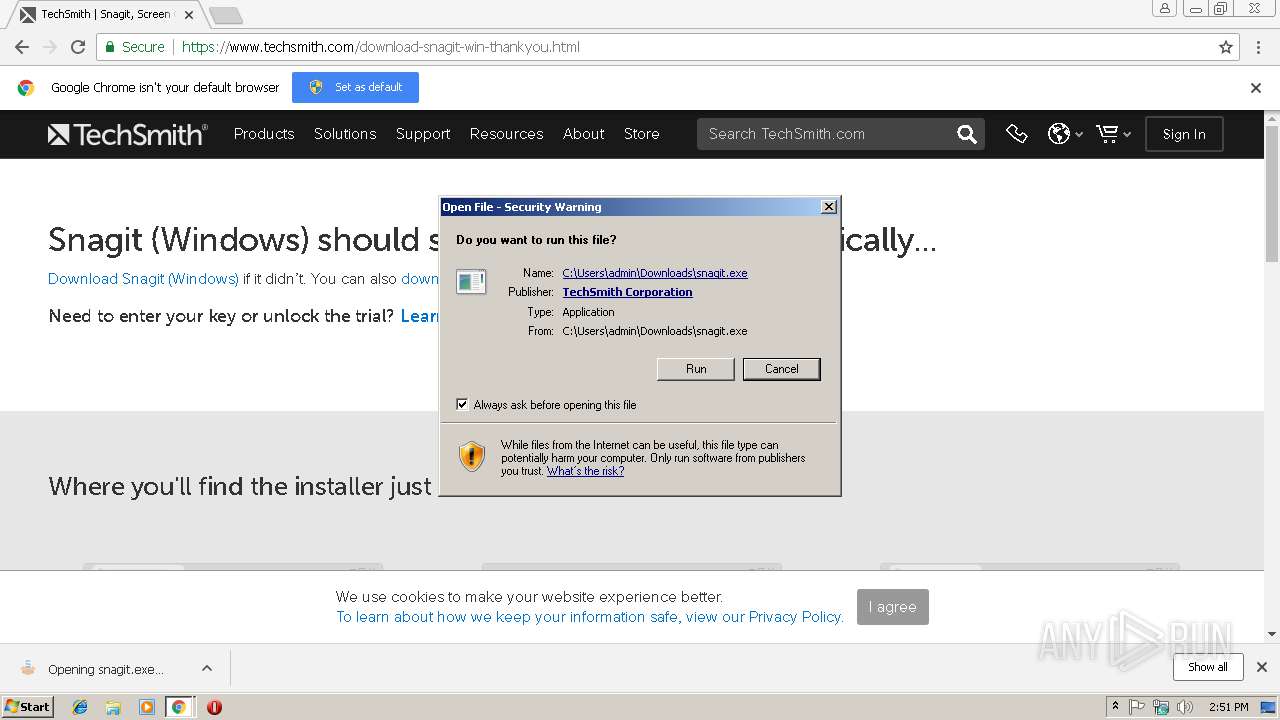
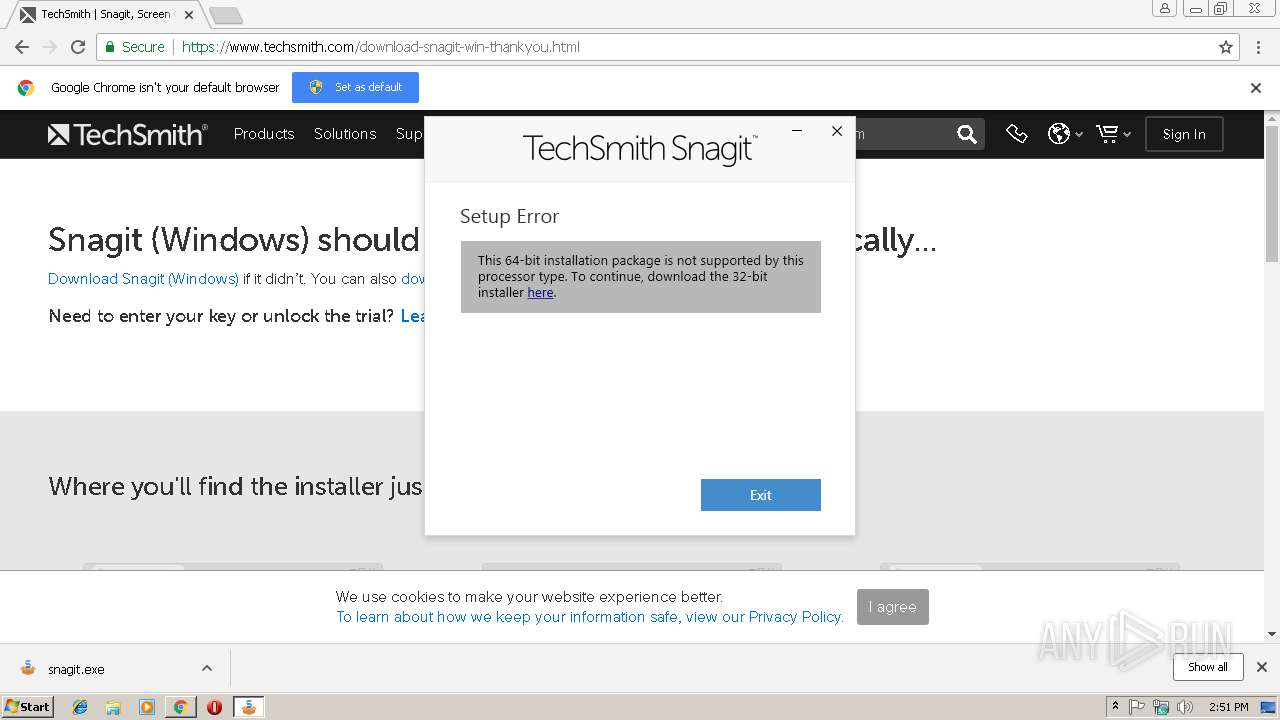
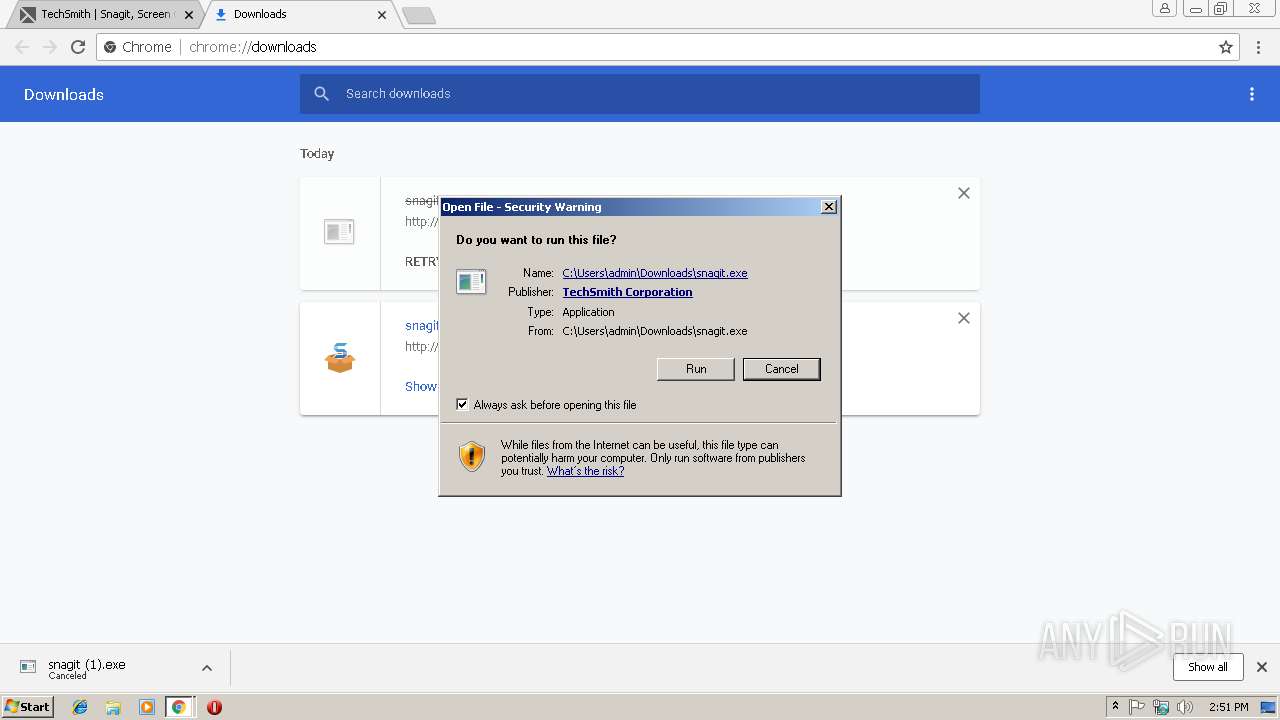
| URL: | https://www.techsmith.com/download/snagit/?utm_source=trial&utm_medium=email&utm_content=sndl&utm_campaign=snagit&spMailingID=58092606&spUserID=MzkzNDAzNjY0MzIxS0&spJobID=1580440473&spReportId=MTU4MDQxMjY5OAS2 |
| Full analysis: | https://app.any.run/tasks/72a13352-5c47-44b9-b063-4f63ca4800bf |
| Verdict: | Malicious activity |
| Analysis date: | February 04, 2019, 14:50:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A66581124CFB66D81C2F18BF534E8C94 |
| SHA1: | DC3FFDFB3E80266EAB2942C8D57C651BCDF44FBF |
| SHA256: | 21EAE0859C24FAADBFD93BE6B809B0C465F7A55F5E8AAA54FB274B9FA1410318 |
| SSDEEP: | 6:2OLrE88NiWTsSQdXJDhNmAxrv8leyfK2kAVT008H:2P88RpQdZDDmqoleyC2kwOH |
MALICIOUS
Application was dropped or rewritten from another process
- snagit.exe (PID: 2536)
- snagit.exe (PID: 3936)
- snagit.exe (PID: 4084)
- snagit.exe (PID: 2840)
- snagit.exe (PID: 2428)
- snagit.exe (PID: 2320)
- snagit.exe (PID: 1604)
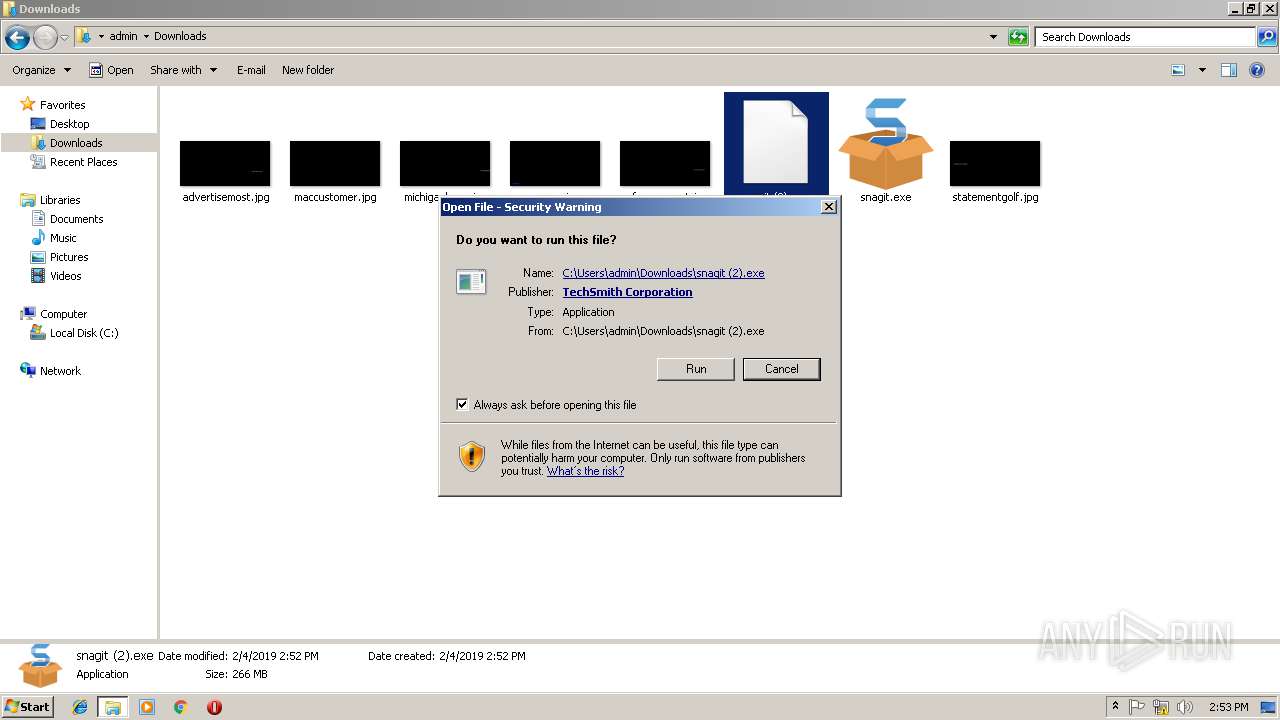
- snagit (2).exe (PID: 3284)
- Bootstrapper.exe (PID: 640)
- snagit.exe (PID: 3196)
- ExtraSteps.exe (PID: 3608)
Loads dropped or rewritten executable
- snagit.exe (PID: 3936)
- snagit.exe (PID: 4084)
- snagit (2).exe (PID: 3284)
- snagit.exe (PID: 2428)
- snagit.exe (PID: 1604)
- rundll32.exe (PID: 3380)
- rundll32.exe (PID: 4020)
- spoolsv.exe (PID: 1196)
- regsvr32.exe (PID: 3600)
- Snagit32.exe (PID: 3496)
- Snagit32.exe (PID: 2296)
- SnagitPI.exe (PID: 3104)
- MsiExec.exe (PID: 676)
- Snagit32.exe (PID: 3736)
- Snagit32.exe (PID: 2156)
- regsvr32.exe (PID: 1144)
Changes the autorun value in the registry
- Bootstrapper.exe (PID: 640)
Registers / Runs the DLL via REGSVR32.EXE
- msiexec.exe (PID: 2264)
Starts NET.EXE for service management
- regsvr32.exe (PID: 1144)
SUSPICIOUS
Executable content was dropped or overwritten
- snagit.exe (PID: 2536)
- snagit.exe (PID: 3936)
- chrome.exe (PID: 2984)
- snagit.exe (PID: 4084)
- snagit.exe (PID: 2840)
- snagit.exe (PID: 3196)
- snagit.exe (PID: 2320)
- snagit.exe (PID: 1604)
- snagit (2).exe (PID: 3284)
- snagit.exe (PID: 2428)
- snagit (2).exe (PID: 2308)
- Bootstrapper.exe (PID: 640)
- rundll32.exe (PID: 3380)
- SnagitPI.exe (PID: 3104)
- spoolsv.exe (PID: 1196)
- msiexec.exe (PID: 2264)
- Snagit32.exe (PID: 2296)
Starts Internet Explorer
- snagit.exe (PID: 4084)
- Snagit32.exe (PID: 3736)
Starts itself from another location
- snagit (2).exe (PID: 3284)
Searches for installed software
- Bootstrapper.exe (PID: 640)
Creates a software uninstall entry
- Bootstrapper.exe (PID: 640)
Creates files in the program directory
- Bootstrapper.exe (PID: 640)
- TSCUpdClt.exe (PID: 3092)
- SearchIndexer.exe (PID: 3588)
- UploaderService.exe (PID: 2168)
- Snagit32.exe (PID: 2296)
Uses RUNDLL32.EXE to load library
- MsiExec.exe (PID: 3832)
Modifies the open verb of a shell class
- msiexec.exe (PID: 2264)
- MsiExec.exe (PID: 3832)
Changes IE settings (feature browser emulation)
- msiexec.exe (PID: 2264)
Changes the autorun value in the registry
- msiexec.exe (PID: 2264)
Creates COM task schedule object
- MsiExec.exe (PID: 360)
- regsvr32.exe (PID: 1144)
- MsiExec.exe (PID: 676)
- regsvr32.exe (PID: 3428)
- regsvr32.exe (PID: 3600)
Removes files from Windows directory
- SnagitPI.exe (PID: 3104)
- spoolsv.exe (PID: 1196)
Creates files in the Windows directory
- SnagitPI.exe (PID: 3104)
- spoolsv.exe (PID: 1196)
Reads Environment values
- Snagit32.exe (PID: 2296)
- Snagit32.exe (PID: 3736)
Creates files in the user directory
- Snagit32.exe (PID: 2296)
- Snagit32.exe (PID: 3736)
INFO
Application launched itself
- chrome.exe (PID: 2984)
- iexplore.exe (PID: 4012)
- msiexec.exe (PID: 2264)
- iexplore.exe (PID: 3520)
Reads Internet Cache Settings
- iexplore.exe (PID: 4012)
- iexplore.exe (PID: 2940)
- chrome.exe (PID: 2984)
- iexplore.exe (PID: 1732)
Reads settings of System Certificates
- iexplore.exe (PID: 4012)
- iexplore.exe (PID: 3520)
Changes internet zones settings
- iexplore.exe (PID: 4012)
- iexplore.exe (PID: 3520)
Creates files in the user directory
- iexplore.exe (PID: 2940)
- iexplore.exe (PID: 1732)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2324)
- iexplore.exe (PID: 3520)
Adds / modifies Windows certificates
- iexplore.exe (PID: 4012)
- DrvInst.exe (PID: 3856)
Changes settings of System certificates
- iexplore.exe (PID: 4012)
- DrvInst.exe (PID: 3856)
Low-level read access rights to disk partition
- vssvc.exe (PID: 2524)
Creates a software uninstall entry
- msiexec.exe (PID: 2264)
Dropped object may contain Bitcoin addresses
- Snagit32.exe (PID: 3736)
- msiexec.exe (PID: 2264)
Reads internet explorer settings
- iexplore.exe (PID: 1732)
Creates files in the program directory
- msiexec.exe (PID: 2264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
112
Monitored processes
64
Malicious processes
18
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 256 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Downloads\snagit | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 304 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2988 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 360 | "C:\Windows\system32\MsiExec.exe" /Y "C:\Program Files\TechSmith\Snagit 2019\SnagitET.dll" | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
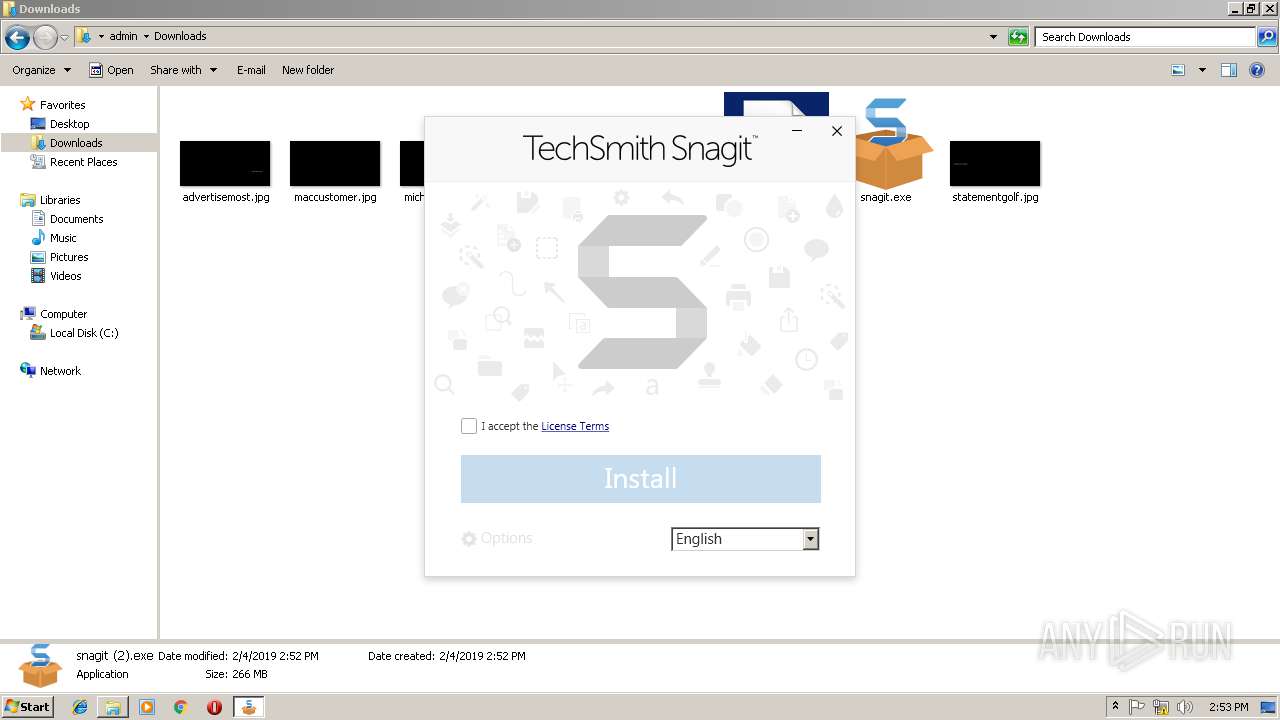
| 640 | "C:\Users\admin\AppData\Local\Temp\{5CE155F4-2610-4463-9AD9-C036DF8BBB92}\.be\Bootstrapper.exe" -q -burn.elevated BurnPipe.{C6E58FAD-2FDB-42D8-AD89-B300FA3FC0C6} {CB566C97-C6E0-4610-92DD-CC28374A3264} 3284 | C:\Users\admin\AppData\Local\Temp\{5CE155F4-2610-4463-9AD9-C036DF8BBB92}\.be\Bootstrapper.exe | snagit (2).exe | ||||||||||||
User: admin Company: TechSmith Corporation Integrity Level: HIGH Description: Snagit 2019 Exit code: 0 Version: 19.1.0.2653 Modules
| |||||||||||||||
| 676 | "C:\Windows\system32\MsiExec.exe" /Y "C:\Program Files\TechSmith\Snagit 2019\AnimatedGIFSource.dll" | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 872 | C:\Windows\system32\net1 stop wsearch /y | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 940 | C:\Windows\system32\MsiExec.exe -Embedding A071A55EF418D5D9E1A16ABB17DC31C1 M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1144 | regsvr32.exe /s "C:\Program Files\TechSmith\Snagit 2019\PdfProperty.dll" | C:\Windows\system32\regsvr32.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1196 | C:\Windows\System32\spoolsv.exe | C:\Windows\System32\spoolsv.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Spooler SubSystem App Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1604 | "C:\Users\admin\AppData\Local\Temp\{7588768E-4B27-47CB-93F8-E70910F2FA0D}\.cr\snagit.exe" -burn.clean.room="C:\Users\admin\Downloads\snagit.exe" -burn.filehandle.attached=148 -burn.filehandle.self=156 | C:\Users\admin\AppData\Local\Temp\{7588768E-4B27-47CB-93F8-E70910F2FA0D}\.cr\snagit.exe | snagit.exe | ||||||||||||
User: admin Company: TechSmith Corporation Integrity Level: MEDIUM Description: Snagit 2019 Exit code: 0 Version: 19.1.0.2653 Modules
| |||||||||||||||
Total events
8 511
Read events
4 647
Write events
3 645
Delete events
219
Modification events
| (PID) Process: | (304) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2984-13193765462398250 |
Value: 259 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2984-13193765462398250 |
Value: 259 | |||
| (PID) Process: | (2984) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
333
Suspicious files
4 276
Text files
496
Unknown types
81
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\2e5ed6a7-327d-44ce-b7c1-e08e013b1c7e.tmp | — | |
MD5:— | SHA256:— | |||
| 2984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\70e1a6f8-f6fd-431f-bafc-6245c8a6c602.tmp | — | |
MD5:— | SHA256:— | |||
| 2984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old~RF20e999.TMP | text | |
MD5:— | SHA256:— | |||
| 2984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF20e9d7.TMP | text | |
MD5:— | SHA256:— | |||
| 2984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Thumbnails\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
75
DNS requests
53
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2984 | chrome.exe | GET | — | 184.31.86.228:80 | http://download.techsmith.com/snagit/enu/snagit.exe | NL | — | — | suspicious |
2984 | chrome.exe | GET | 200 | 2.16.186.56:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 55.2 Kb | whitelisted |
2984 | chrome.exe | GET | 200 | 52.85.188.251:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2984 | chrome.exe | 45.60.124.187:443 | www.techsmith.com | — | US | unknown |
2984 | chrome.exe | 172.217.21.227:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2984 | chrome.exe | 172.217.23.141:443 | accounts.google.com | Google Inc. | US | whitelisted |
2984 | chrome.exe | 216.58.207.67:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2984 | chrome.exe | 184.31.86.228:443 | assets.techsmith.com | Akamai International B.V. | NL | whitelisted |
2984 | chrome.exe | 216.58.207.72:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
2984 | chrome.exe | 208.118.62.70:443 | www.upsellit.com | Alchemy Communications, Inc. | US | unknown |
2984 | chrome.exe | 18.204.70.187:443 | techsmith.onfastspring.com | — | US | unknown |
2984 | chrome.exe | 152.199.19.160:443 | az416426.vo.msecnd.net | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2984 | chrome.exe | 2.16.186.56:80 | www.download.windowsupdate.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.techsmith.com |
| unknown |
www.gstatic.com |
| whitelisted |
accounts.google.com |
| shared |
use.typekit.net |
| whitelisted |
d1f8f9xcsvx3ha.cloudfront.net |
| whitelisted |
assets.techsmith.com |
| whitelisted |
techsmith.onfastspring.com |
| unknown |
www.googletagmanager.com |
| whitelisted |
az416426.vo.msecnd.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2984 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2984 | chrome.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
Process | Message |
|---|---|
regsvr32.exe | ***L_AllocThreadData
|
regsvr32.exe | ***InitThreadData
|
regsvr32.exe | ***L_FreeThreadData
|
Snagit32.exe | ***L_AllocThreadData
|
Snagit32.exe | ***InitThreadData
|
Snagit32.exe | ***L_FreeThreadData
|
Snagit32.exe | ***L_AllocThreadData
|
Snagit32.exe | ***InitThreadData
|
Snagit32.exe | ***L_AllocThreadData
@濮҆轄鸠벙ǔ濂҆***L_AllocThreadData
|
Snagit32.exe | ***L_AllocThreadData
|