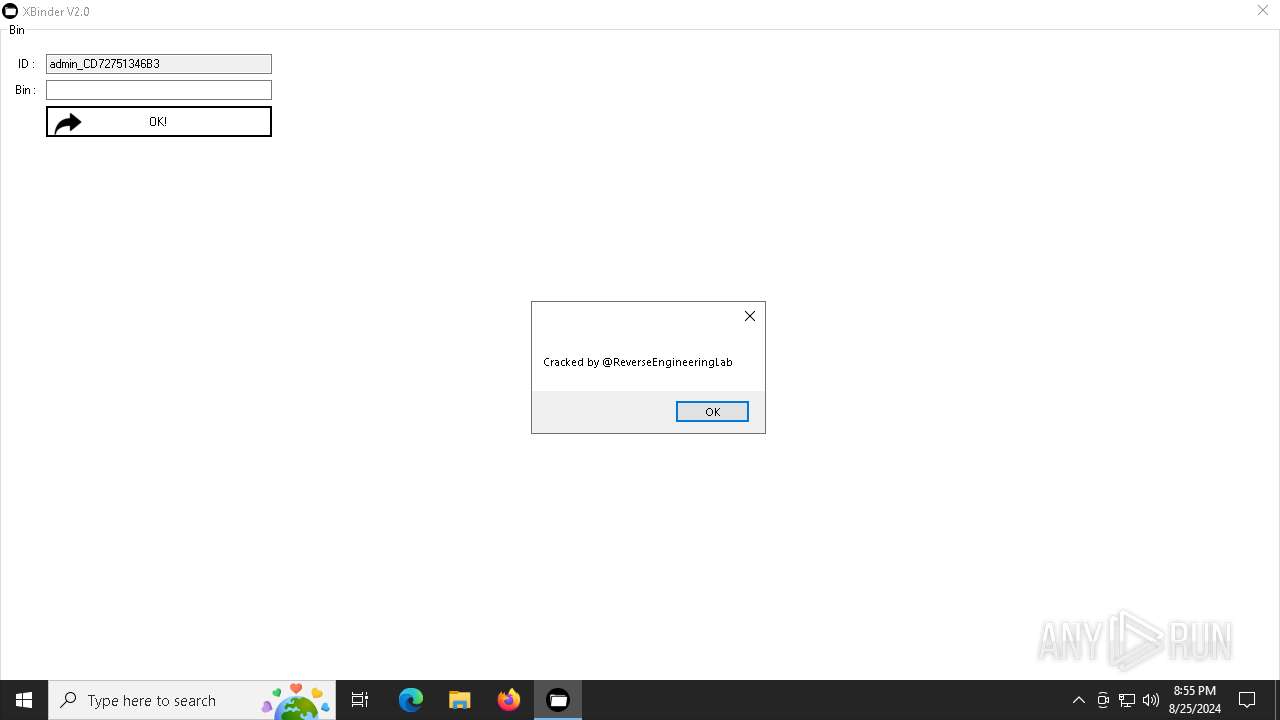
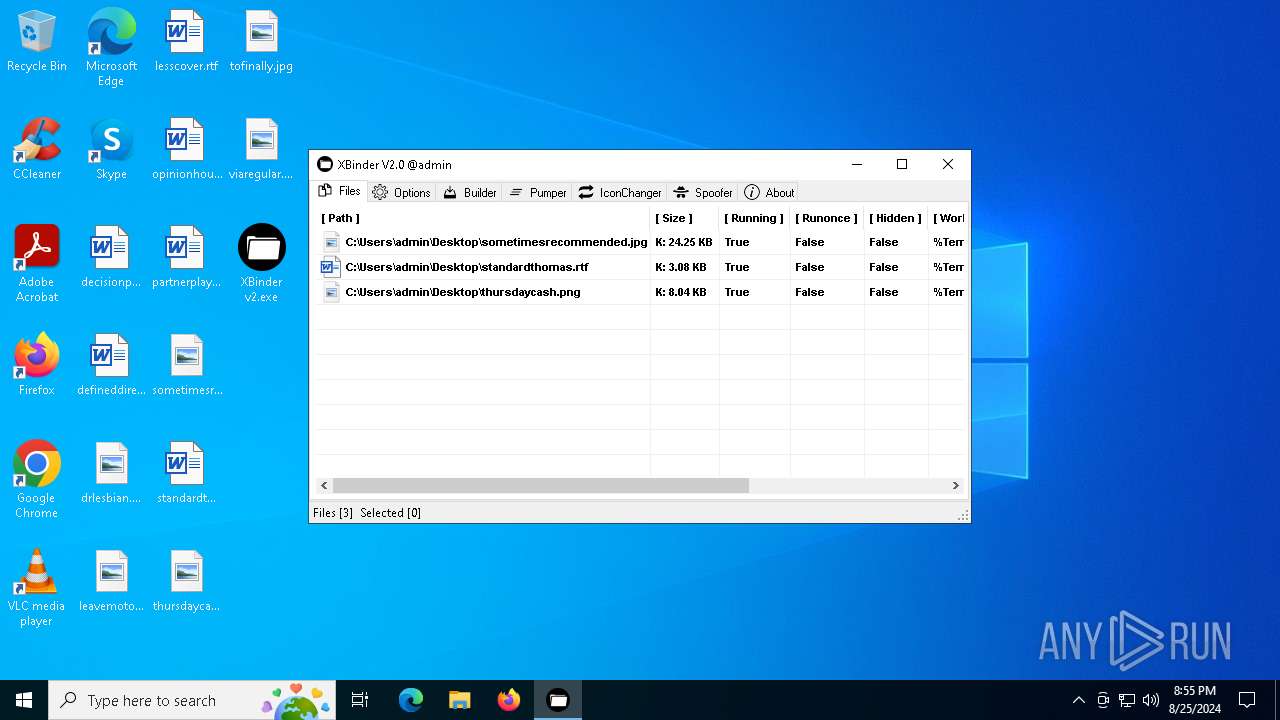
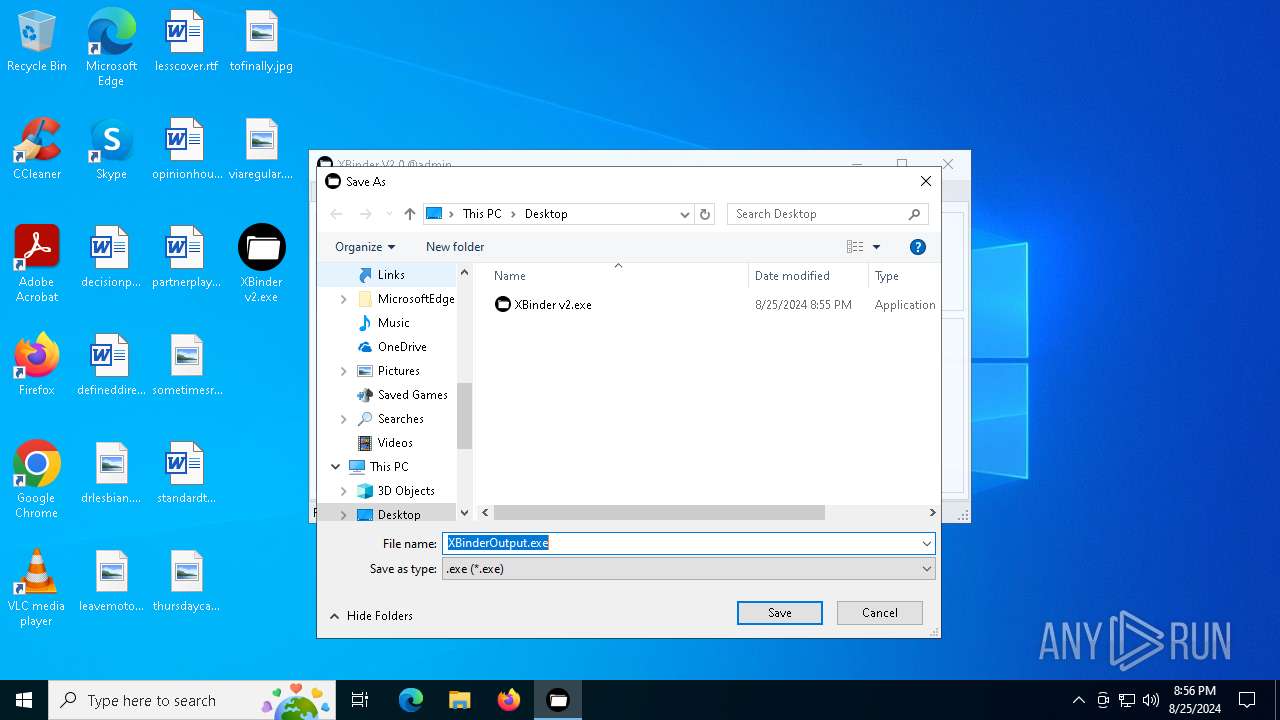
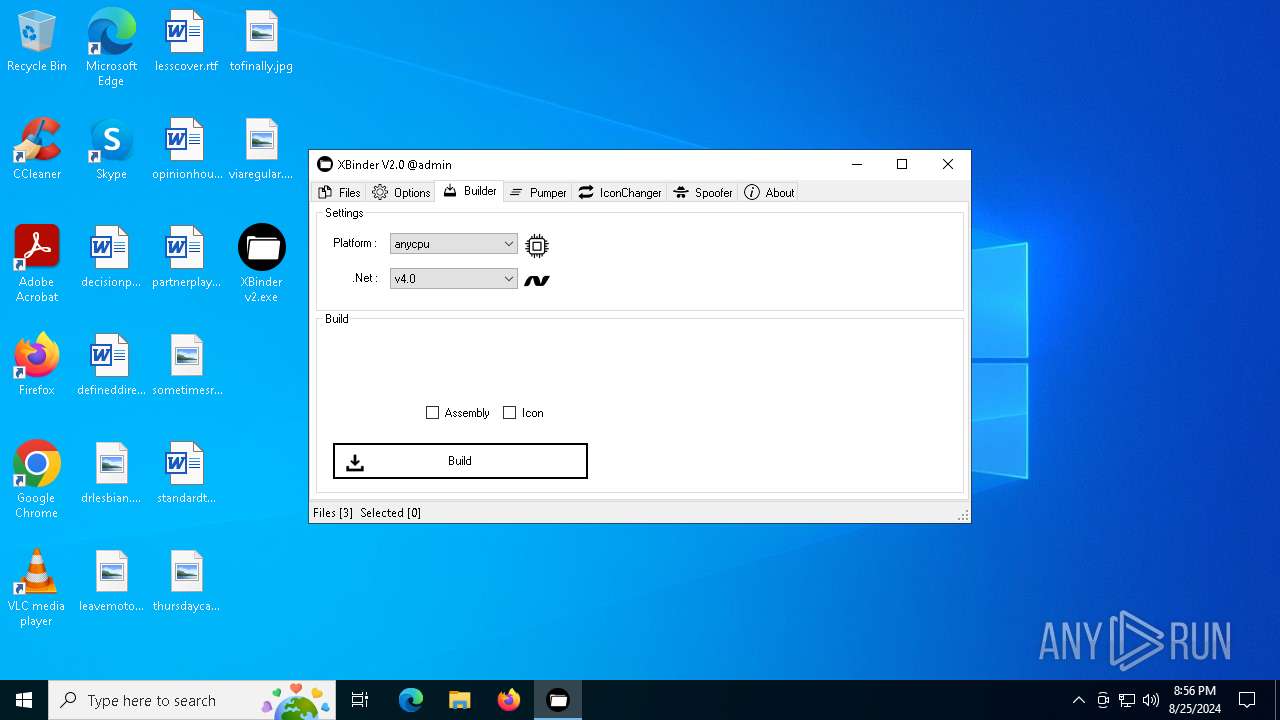
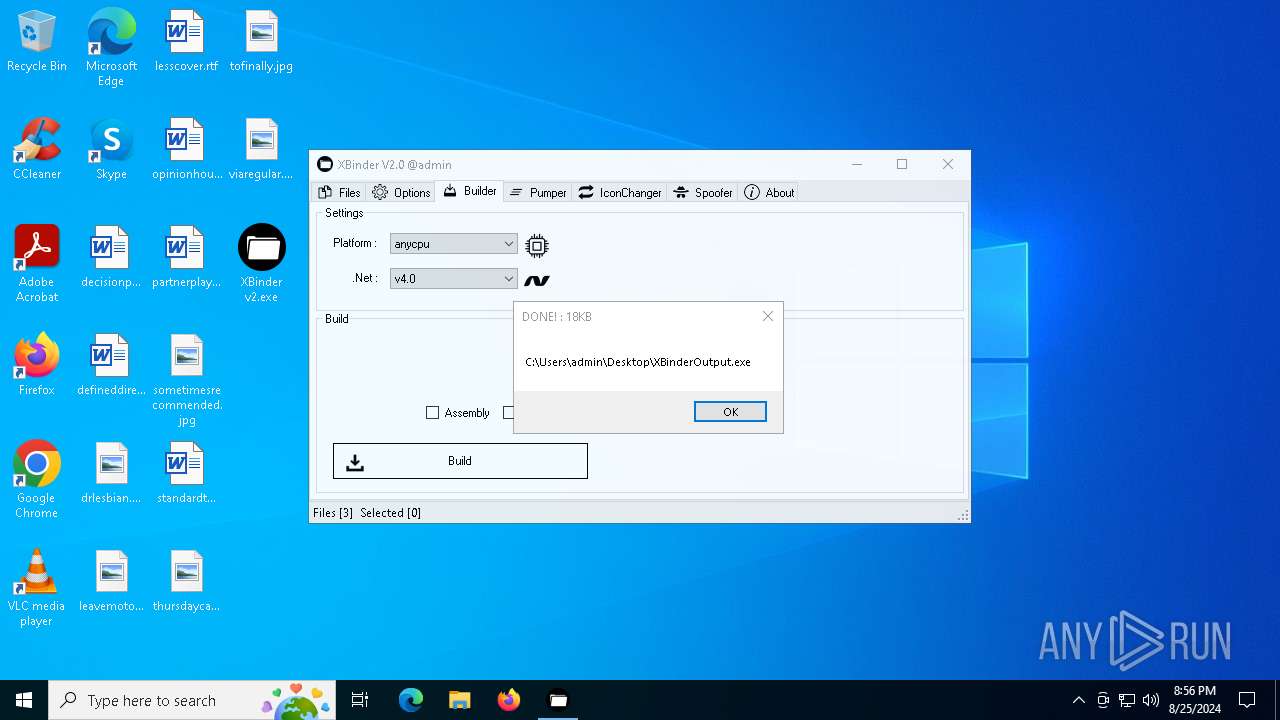
| File name: | XBinder v2.exe |
| Full analysis: | https://app.any.run/tasks/3a568089-a273-4f58-951f-31e207ffe8e4 |
| Verdict: | Malicious activity |
| Analysis date: | August 25, 2024, 20:55:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows |
| MD5: | A98358EB7F4953AA6D60015CCD8506CE |
| SHA1: | D9BE0C9D6D968C1BAEF11027A7ACE6A0E869E75A |
| SHA256: | 21E0CC9EF715CC2147B9EC481B3FB876DBAE8A4491367B478513128D7F7B8555 |
| SSDEEP: | 24576:yxxxSxWxx7xxxxbfWfkNmePfTwjBZMt7+NI+6Vrw7id7:t8NmePfM66+d7 |
MALICIOUS
XORed URL has been found (YARA)
- XBinder v2.exe (PID: 6828)
SUSPICIOUS
Drops the executable file immediately after the start
- XBinder v2.exe (PID: 6828)
- vbc.exe (PID: 6324)
Reads security settings of Internet Explorer
- XBinder v2.exe (PID: 6828)
- XBinderOutput.exe (PID: 6408)
There is functionality for capture public ip (YARA)
- XBinder v2.exe (PID: 6828)
Executable content was dropped or overwritten
- vbc.exe (PID: 6324)
Reads the date of Windows installation
- XBinderOutput.exe (PID: 6408)
INFO
Reads the computer name
- XBinder v2.exe (PID: 6828)
- XBinderOutput.exe (PID: 6408)
Checks supported languages
- XBinder v2.exe (PID: 6828)
- vbc.exe (PID: 6324)
- cvtres.exe (PID: 6532)
- XBinderOutput.exe (PID: 6408)
Create files in a temporary directory
- vbc.exe (PID: 6324)
- XBinder v2.exe (PID: 6828)
- cvtres.exe (PID: 6532)
- XBinderOutput.exe (PID: 6408)
Reads the machine GUID from the registry
- vbc.exe (PID: 6324)
- XBinder v2.exe (PID: 6828)
- XBinderOutput.exe (PID: 6408)
Manual execution by a user
- XBinderOutput.exe (PID: 6408)
Reads Microsoft Office registry keys
- XBinderOutput.exe (PID: 6408)
Process checks computer location settings
- XBinderOutput.exe (PID: 6408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2022:09:15 00:32:03+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 48 |
| CodeSize: | 3605504 |
| InitializedDataSize: | 106496 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | XCoder |
| CompanyName: | - |
| FileDescription: | XBinder |
| FileVersion: | 2.0.0.0 |
| InternalName: | XBinder.exe |
| LegalCopyright: | Copyright © 2022 |
| LegalTrademarks: | - |
| OriginalFileName: | XBinder.exe |
| ProductName: | XBinder |
| ProductVersion: | 2.0.0.0 |
| AssemblyVersion: | 2.0.0.0 |
Total processes
141
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5048 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "0C37A25C-40E9-45B8-B9EE-E6D85C4D6483" "ED11DA3B-8D07-4B44-B275-267EDAEDE2F1" "6392" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 6304 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\AppData\Local\Temp\sometimesrecommended.jpg" | C:\Windows\System32\mspaint.exe | — | XBinderOutput.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6324 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\vbc.exe" /noconfig @"C:\Users\admin\AppData\Local\Temp\3gmu5hb4.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\vbc.exe | XBinder v2.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 14.8.9037.0 Modules
| |||||||||||||||
| 6392 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\standardthomas.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | XBinderOutput.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6408 | "C:\Users\admin\Desktop\XBinderOutput.exe" | C:\Users\admin\Desktop\XBinderOutput.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6496 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | vbc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6532 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES525E.tmp" "C:\Users\admin\AppData\Local\Temp\vbc8F6EE870AE294ACE9E3F175216A3E2E.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | vbc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 6708 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\AppData\Local\Temp\thursdaycash.png" | C:\Windows\System32\mspaint.exe | — | XBinderOutput.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6828 | "C:\Users\admin\Desktop\XBinder v2.exe" | C:\Users\admin\Desktop\XBinder v2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: XBinder Version: 2.0.0.0 Modules
| |||||||||||||||
Total events
39 416
Read events
39 049
Write events
341
Delete events
26
Modification events
| (PID) Process: | (6828) XBinder v2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\XBinder |
| Operation: | write | Name: | License |
Value: | |||
| (PID) Process: | (6828) XBinder v2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | write | Name: | 5 |
Value: 5800420069006E006400650072002000760032002E00650078006500000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000 | |||
| (PID) Process: | (6828) XBinder v2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6828) XBinder v2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0400000000000000030000000E0000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (6828) XBinder v2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 010000000000000004000000050000000200000003000000FFFFFFFF | |||
| (PID) Process: | (6828) XBinder v2.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (6828) XBinder v2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 93 | |||
| (PID) Process: | (6828) XBinder v2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6828) XBinder v2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6828) XBinder v2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
1
Suspicious files
15
Text files
9
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6828 | XBinder v2.exe | C:\Users\admin\AppData\Local\Temp\tmp505A.tmp | binary | |
MD5:31094BC59A89A67965CB9B1CB96E1C39 | SHA256:F0BC27B0FB0055A0E7F151D117BBB6FE83E1CB64CEE330770AC4887C5A8A1010 | |||
| 6408 | XBinderOutput.exe | C:\Users\admin\AppData\Local\Temp\sometimesrecommended.jpg | image | |
MD5:4CEDFE171B794CE90E3D841D236D68E2 | SHA256:B9A3592465EC35883F065F4BC721F0D8478E576CF512DEAA2A1A98207816AC21 | |||
| 6828 | XBinder v2.exe | C:\Users\admin\AppData\Local\Temp\3gmu5hb4.0.vb | text | |
MD5:484372D1CFB270B86F593AA9695B6EFB | SHA256:AD2C74B4F3EA1E429E4615B04798304C12A1F0CB1B87034D595E0A80A578165D | |||
| 6324 | vbc.exe | C:\Users\admin\AppData\Local\Temp\3gmu5hb4.out | text | |
MD5:AC585A7FA071C11FB6A6CAEDF27AE63B | SHA256:EE171874E8387DAD7AD6A0F7DA76879B4F3FA99C6D592AF5D519BA510EE89777 | |||
| 6324 | vbc.exe | C:\Users\admin\Desktop\XBinderOutput.exe | executable | |
MD5:007BCC8229A3850582B50CACB60DA24C | SHA256:2E8FC5CF1F85AD8D4A13253F9DA9533427A7F21A0EBEE15A182FE8F76E085065 | |||
| 6324 | vbc.exe | C:\Users\admin\AppData\Local\Temp\vbc8F6EE870AE294ACE9E3F175216A3E2E.TMP | binary | |
MD5:CE7EE761D5F0A9CCC4E37A527ACE11D6 | SHA256:D8DB9A7547590C3AFDB024EA67EC9026F367DC18C4D944F4980397628036108E | |||
| 6324 | vbc.exe | C:\Users\admin\AppData\Local\Temp\vbc578843A5761847F18A5BE1B29D14AEBF.TMP | binary | |
MD5:D343A1E04F223DE18D3851A66C4DC953 | SHA256:D8B69FF0240575C7D41D28DC1C2C0EA79D74B189E4E89810038B4C129B466FCB | |||
| 6408 | XBinderOutput.exe | C:\Users\admin\AppData\Local\Temp\thursdaycash.png | image | |
MD5:99AEA552030535D531D2823D294542A8 | SHA256:1106FDEB28ED26259E11B190F9FF26D88F955E323A0F47251303EB9C41002CC0 | |||
| 6408 | XBinderOutput.exe | C:\Users\admin\AppData\Local\Temp\standardthomas.rtf | text | |
MD5:E0FF4306451FD48C1EEBF92A9C72D03E | SHA256:2584EF737C6693C2D34931EE5C486E43C3D7D4299350C06D7850241A45B27FB7 | |||
| 6392 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:61E8A78D4F887294D8951D474A01F333 | SHA256:E9FBB8CCD697313371E8A99149164BCFECF33ABDB6574484B2E17FAB3F6D5220 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
27
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3276 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6392 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3584 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3244 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3276 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3276 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6356 | SIHClient.exe | 40.127.169.103:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6356 | SIHClient.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6356 | SIHClient.exe | 13.95.31.18:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|