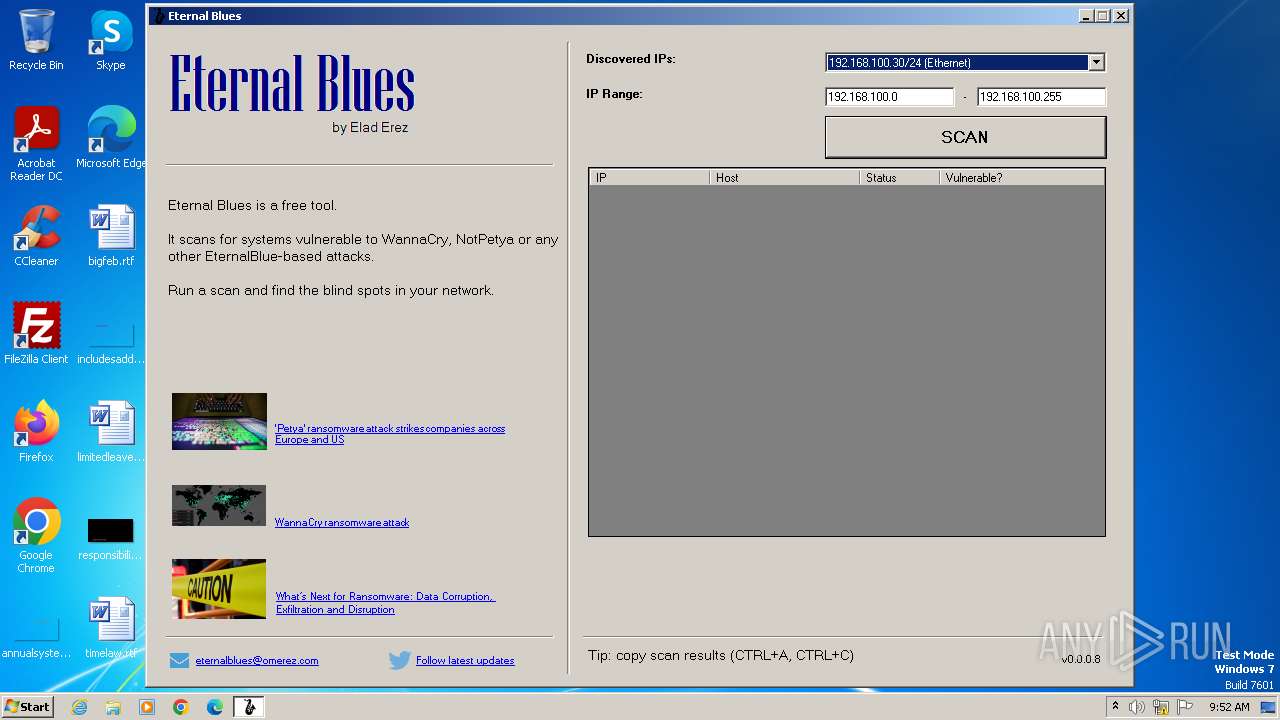
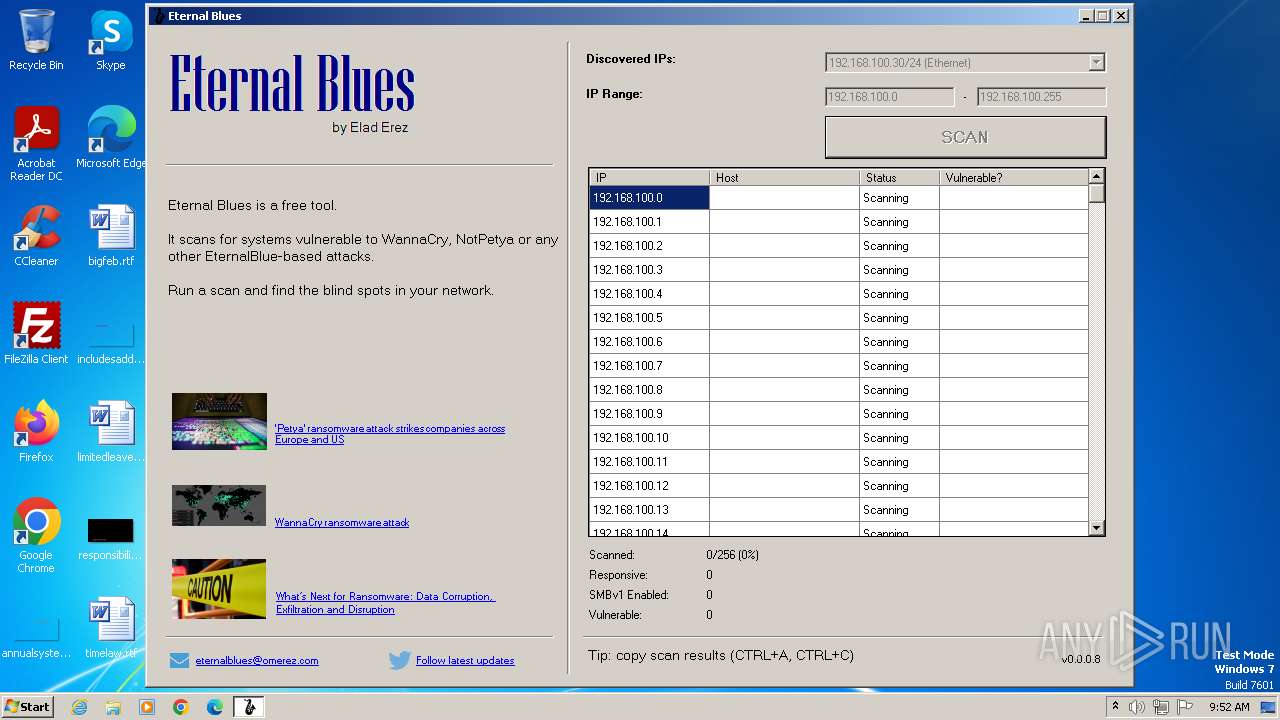
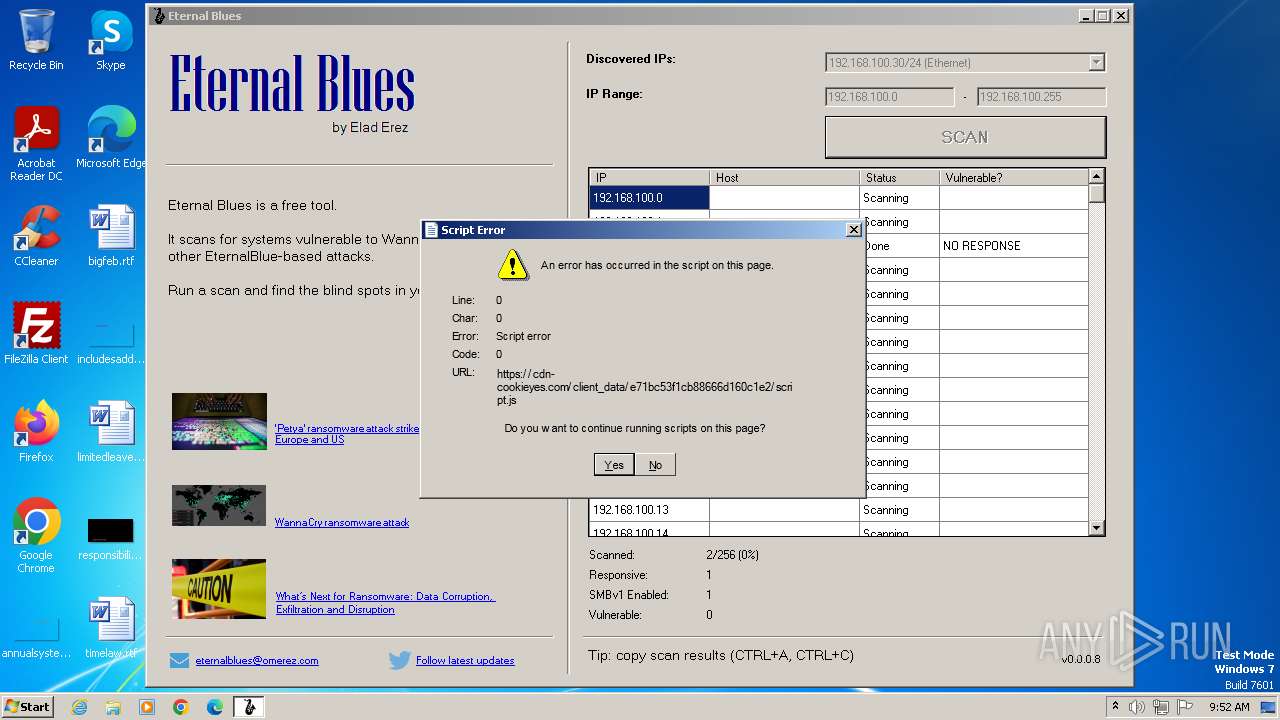
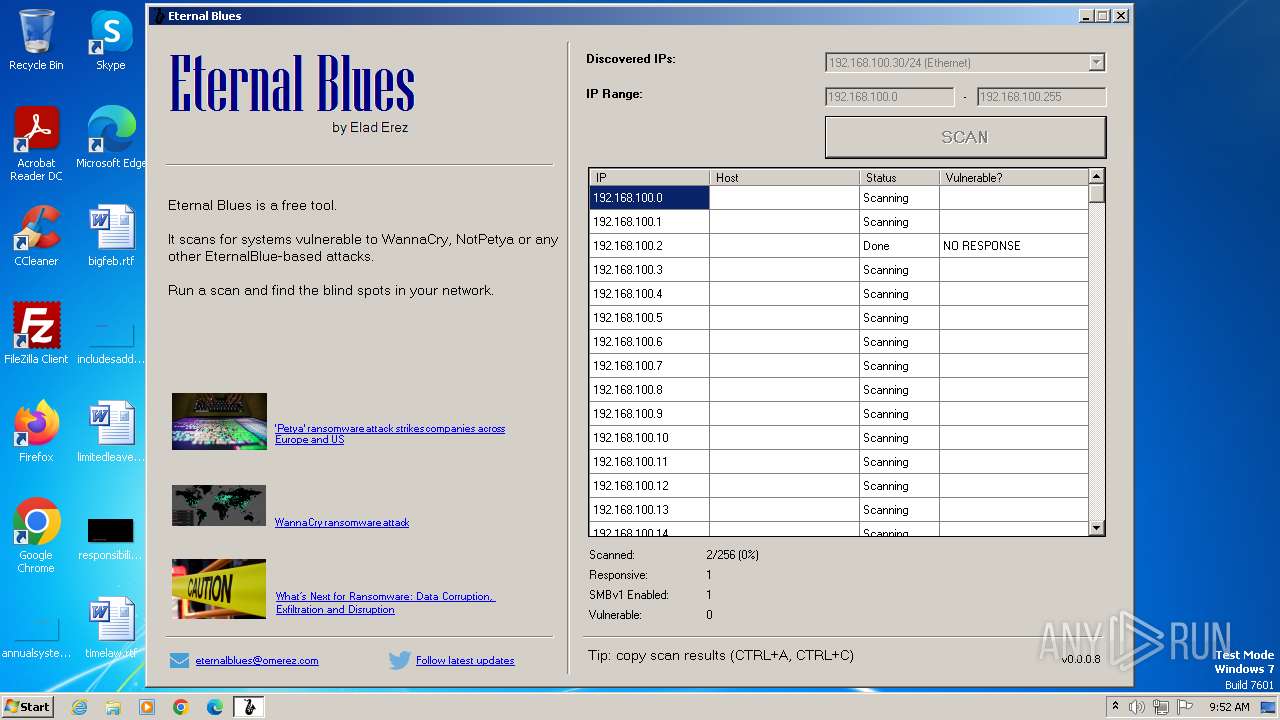
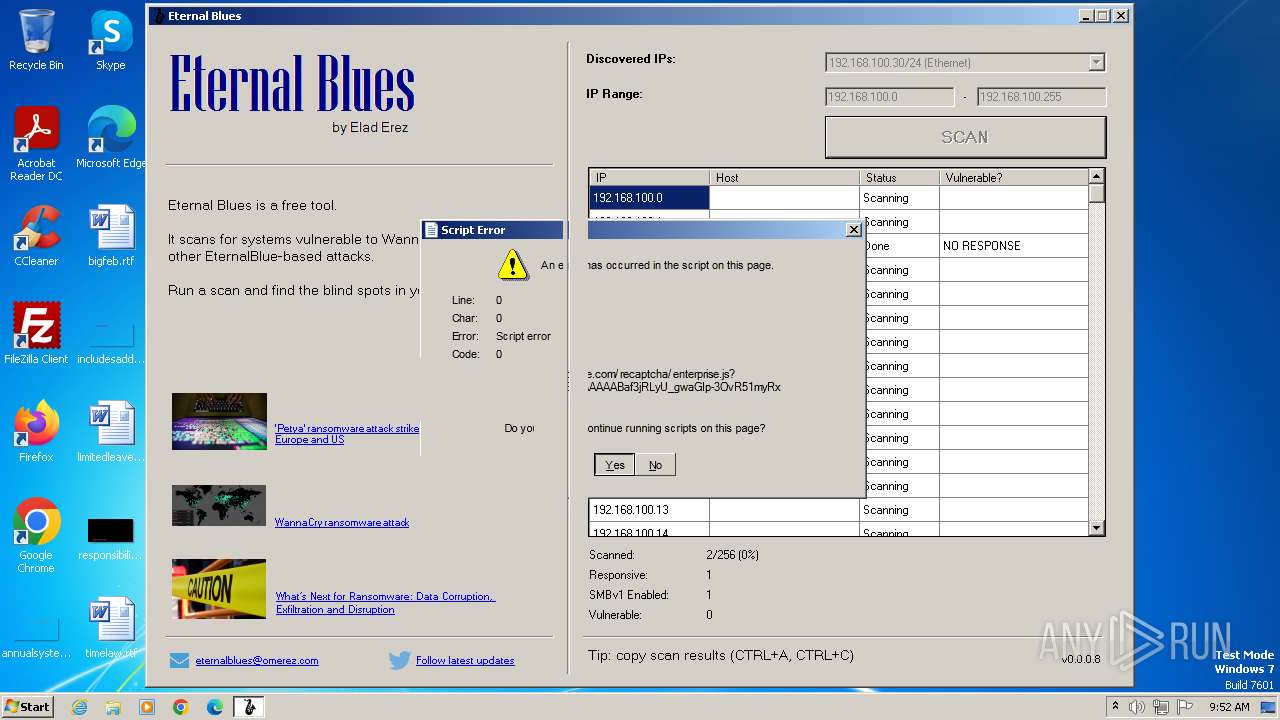
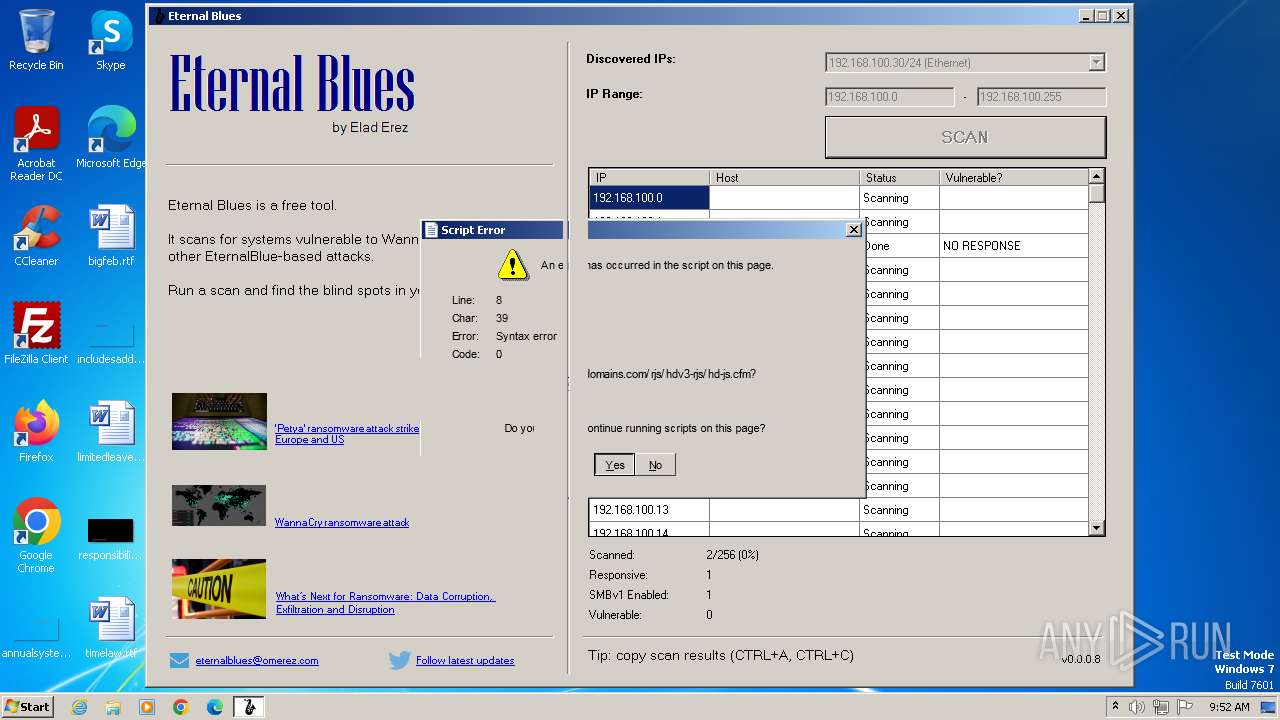
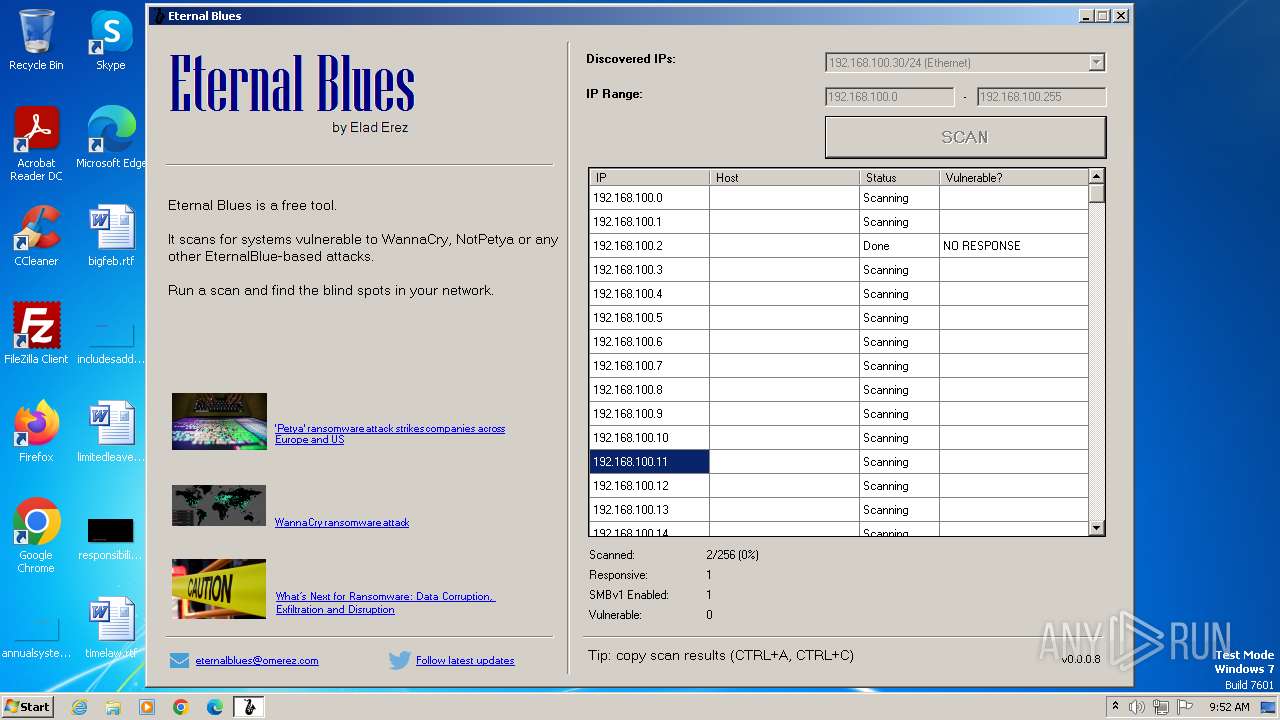
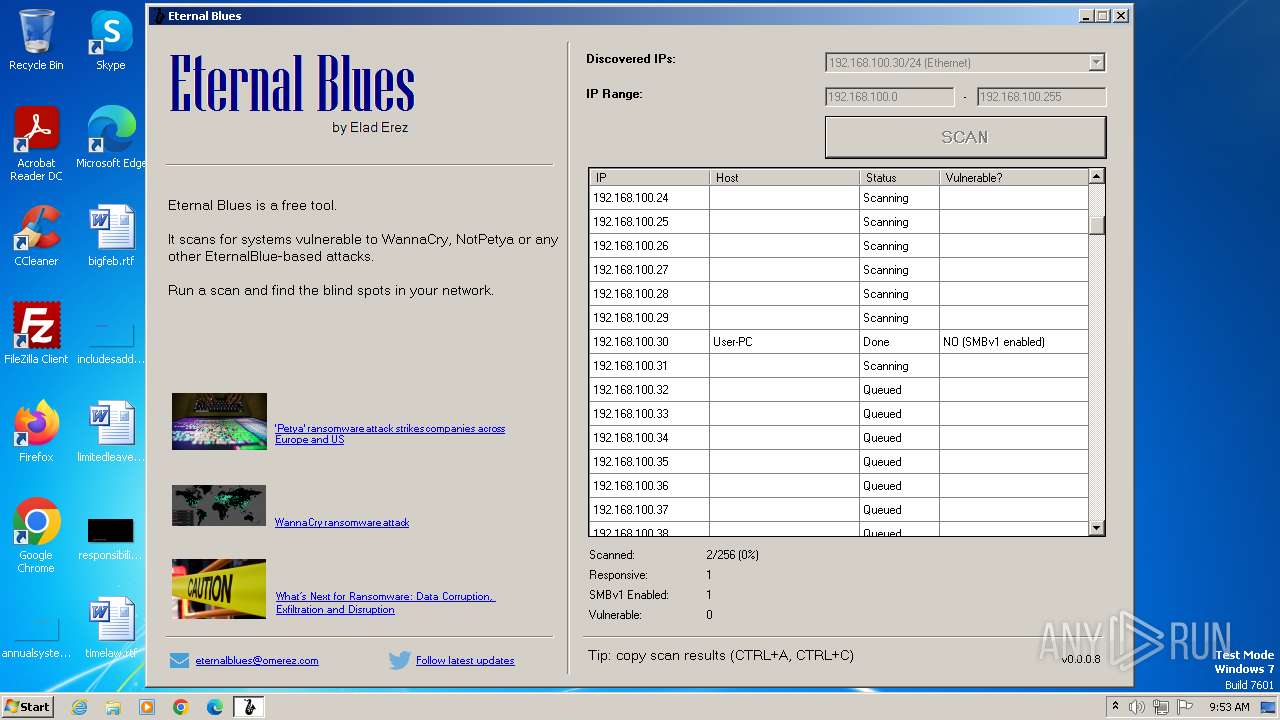
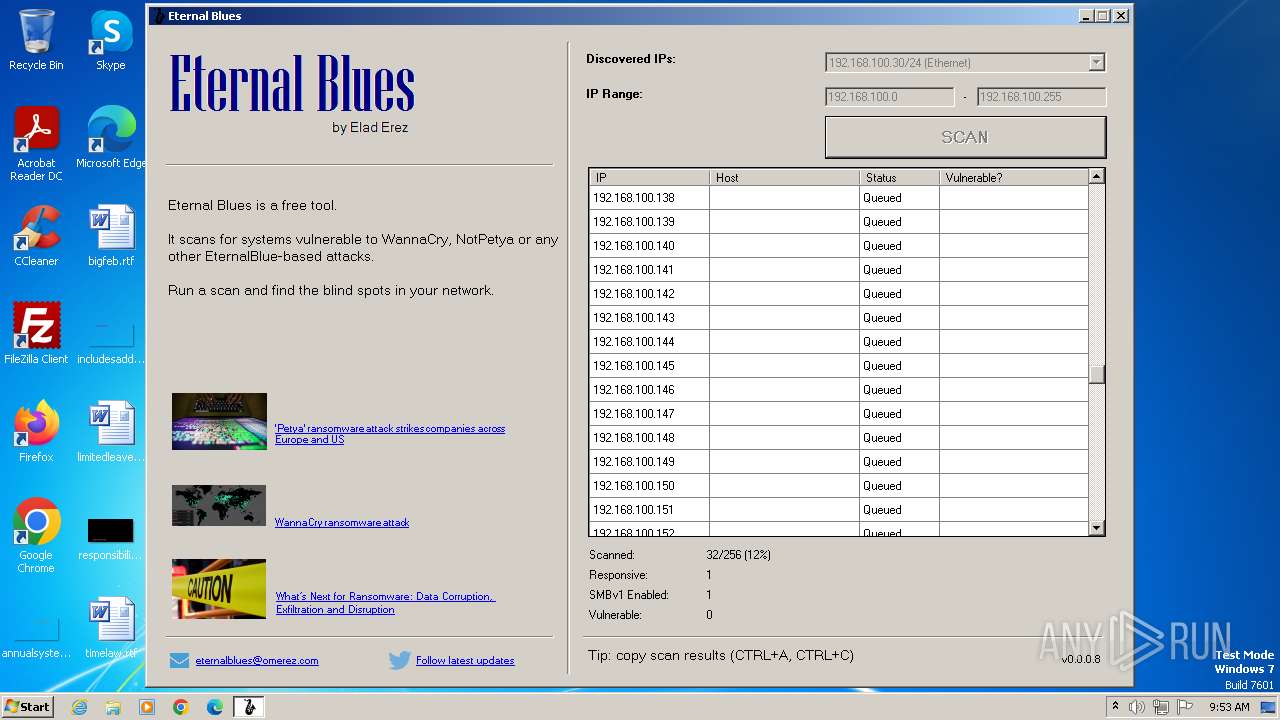
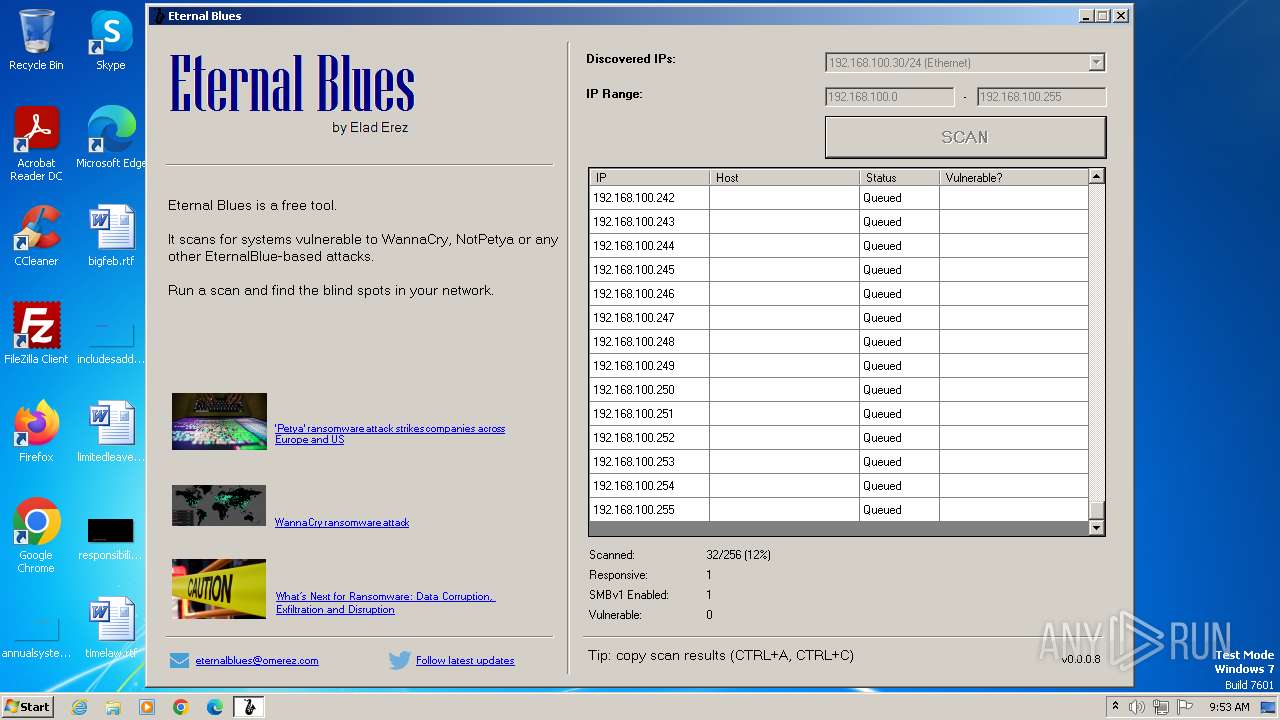
| File name: | EternalBlue.exe |
| Full analysis: | https://app.any.run/tasks/9a17d316-ffd3-4fbc-8d32-e6c0a80a9f6a |
| Verdict: | Malicious activity |
| Analysis date: | May 27, 2024, 08:52:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | D8DE3742220386DD5DB15E9407E70CCC |
| SHA1: | 77290344EE77F1F9F5F66B4C4D96EB2189F64867 |
| SHA256: | 21CC36E60E661613F0C05E73B9496BF2D456931686B0693112842D91D7E64E78 |
| SSDEEP: | 49152:Xw3jPfNCp4ze2jx7xfGmWWox8SlTrMuK+edTxxty/UsrVEn9iWJgJ9p1x0HcvcVR:XU9xxuhWox5vxK+exNzuVEEAgTp1Ocvm |
MALICIOUS
Drops the executable file immediately after the start
- EternalBlue.exe (PID: 3984)
SUSPICIOUS
Reads settings of System Certificates
- EternalBlue.exe (PID: 3984)
Checks Windows Trust Settings
- EternalBlue.exe (PID: 3984)
Reads the Internet Settings
- EternalBlue.exe (PID: 3984)
Reads security settings of Internet Explorer
- EternalBlue.exe (PID: 3984)
Reads Microsoft Outlook installation path
- EternalBlue.exe (PID: 3984)
Reads Internet Explorer settings
- EternalBlue.exe (PID: 3984)
INFO
Reads the computer name
- EternalBlue.exe (PID: 3984)
- wmpnscfg.exe (PID: 4060)
Reads the machine GUID from the registry
- EternalBlue.exe (PID: 3984)
Reads the software policy settings
- EternalBlue.exe (PID: 3984)
Reads Environment values
- EternalBlue.exe (PID: 3984)
Disables trace logs
- EternalBlue.exe (PID: 3984)
Checks supported languages
- EternalBlue.exe (PID: 3984)
- wmpnscfg.exe (PID: 4060)
Manual execution by a user
- wmpnscfg.exe (PID: 4060)
Checks proxy server information
- EternalBlue.exe (PID: 3984)
Creates files or folders in the user directory
- EternalBlue.exe (PID: 3984)
Create files in a temporary directory
- EternalBlue.exe (PID: 3984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:07:10 14:54:59+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 1459712 |
| InitializedDataSize: | 47616 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16644e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.8 |
| ProductVersionNumber: | 0.0.0.8 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Elad Erez |
| FileDescription: | EternalBlues |
| FileVersion: | 0.0.0.8 |
| InternalName: | EternalBlues.exe |
| LegalCopyright: | Copyright © Elad Erez |
| LegalTrademarks: | - |
| OriginalFileName: | EternalBlues.exe |
| ProductName: | Eternal Blues |
| ProductVersion: | 0.0.0.8 |
| AssemblyVersion: | 0.0.0.8 |
Total processes
34
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3984 | "C:\Users\admin\AppData\Local\Temp\EternalBlue.exe" | C:\Users\admin\AppData\Local\Temp\EternalBlue.exe | explorer.exe | ||||||||||||
User: admin Company: Elad Erez Integrity Level: MEDIUM Description: EternalBlues Version: 0.0.0.8 Modules
| |||||||||||||||
| 4060 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
10 022
Read events
9 970
Write events
46
Delete events
6
Modification events
| (PID) Process: | (3984) EternalBlue.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EternalBlue_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3984) EternalBlue.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EternalBlue_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3984) EternalBlue.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EternalBlue_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3984) EternalBlue.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EternalBlue_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3984) EternalBlue.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EternalBlue_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3984) EternalBlue.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EternalBlue_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3984) EternalBlue.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EternalBlue_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3984) EternalBlue.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EternalBlue_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3984) EternalBlue.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EternalBlue_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3984) EternalBlue.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\EternalBlue_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
0
Suspicious files
24
Text files
45
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3984 | EternalBlue.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\QZUN6I8V.txt | text | |
MD5:A738BC1E4E544A03F8075413A7BCAF12 | SHA256:35091FD52CBCF7056E94DF61EADB9BAE842493C73B3453E730302D9F241B04BA | |||
| 3984 | EternalBlue.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\style[1].css | text | |
MD5:65760E3B3B198746B7E73E4DE28EFEA1 | SHA256:10E40EA3A2AD69C08D13E194CF13EB4A28A093C939758A17A6A775EF603AC4FC | |||
| 3984 | EternalBlue.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\hd-header-logo-v3[1].svg | image | |
MD5:D4E44251F8E9314A0DEC5EDDD6B1C64E | SHA256:097A98ECCD043B5DF15A66409D32EF16F7570776625D0E0B4D1054BE26A31A00 | |||
| 3984 | EternalBlue.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\reboot.min[1].css | text | |
MD5:51B8B71098EEED2C55A4534E48579A16 | SHA256:BD78E3BCC569D029E7C709144E4038DEDE4D92A143E77BC46E4F15913769758B | |||
| 3984 | EternalBlue.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:801791647DA1DD55901254C4DABAEF83 | SHA256:8239990EFA43103A3F2E22744B13E030F6ECC13EFEB9FF8FCCFA71FC8FA5ECB9 | |||
| 3984 | EternalBlue.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\hd-style[1].css | text | |
MD5:E6BECE7897F67C0DD9542C90BB582D99 | SHA256:D2673334CC6DB9E20B9CEA18BCE2685CEB107C31CCAC7D3B8FABA2FB10B9210E | |||
| 3984 | EternalBlue.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\3FKIQECJ.txt | text | |
MD5:2B9B6736B91C0FCFC9983F9F145D529E | SHA256:5E60C6FA853AF9FB07BC4C523D4C4A49E1563E9D6D58B0B0F2B6E64E33A9ACBD | |||
| 3984 | EternalBlue.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\05DDC6AA91765AACACDB0A5F96DF8199 | der | |
MD5:8D1040B12A663CA4EC7277CFC1CE44F0 | SHA256:3086094D4198A5BBD12938B0D2D5F696C4DFC77E1EAE820ADDED346A59AA8727 | |||
| 3984 | EternalBlue.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\script[1].js | text | |
MD5:BFC517188E31C284E6F920185EF9581F | SHA256:2CB9E929560926259750C4D840710FBF0A7D2C8DA9A9A886EE478BC362829E7E | |||
| 3984 | EternalBlue.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:2B79576931F7278028F9FCC700D932D2 | SHA256:990697F2EED9D44971A4EAEEC7C0DDD2822C683683BEC33DFF51AC1FCC07B059 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
35
DNS requests
23
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
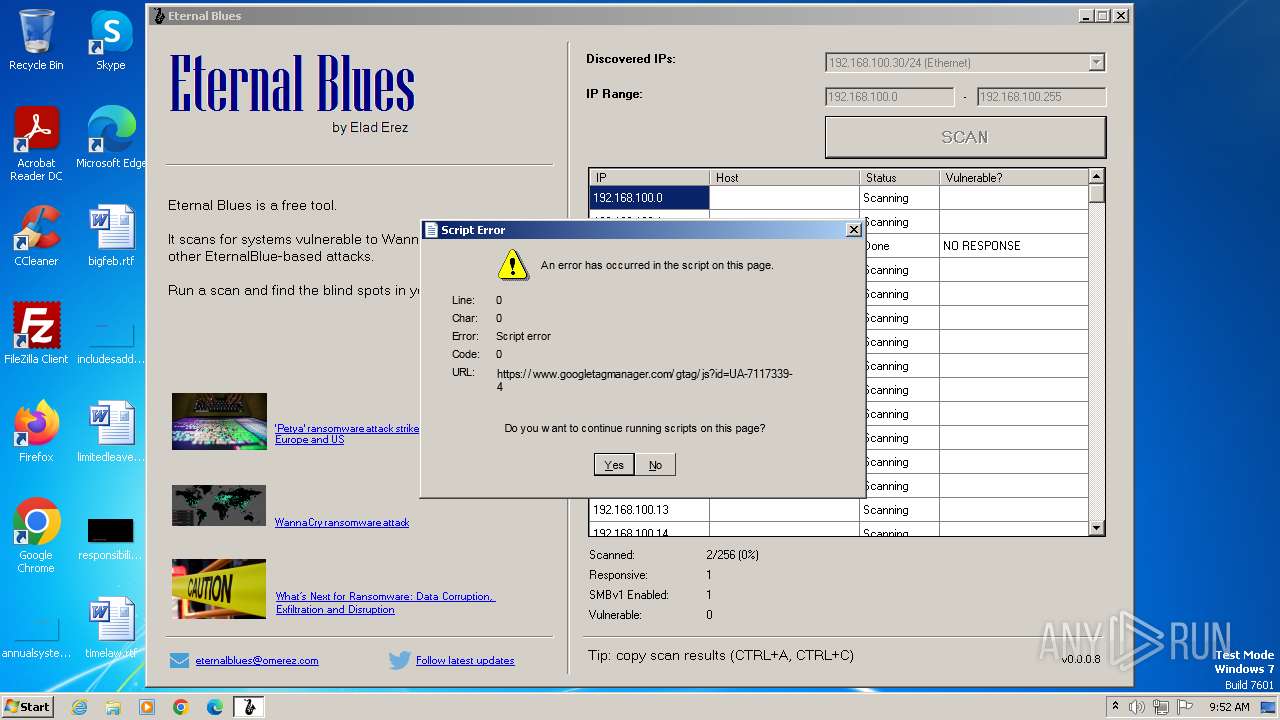
3984 | EternalBlue.exe | GET | 302 | 3.130.204.160:80 | http://omerez.com/repository/pages/eternalblues-report.html?id=1297319125&startScan=256&version=0.0.0.8 | unknown | — | — | unknown |
3984 | EternalBlue.exe | GET | 302 | 3.130.204.160:80 | http://omerez.com/repository/eternalblues-version.txt | unknown | — | — | unknown |
3984 | EternalBlue.exe | GET | 304 | 213.155.157.168:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e948317888637db8 | unknown | — | — | unknown |
3984 | EternalBlue.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | — | — | unknown |
3984 | EternalBlue.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
3984 | EternalBlue.exe | GET | 200 | 142.250.181.227:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | unknown |
3984 | EternalBlue.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEH6HwqMlsnS7%2BryQ1sUoZV4%3D | unknown | — | — | unknown |
3984 | EternalBlue.exe | GET | 200 | 142.250.181.227:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQDcoc6fqZ4zlBD%2FfhdqltwL | unknown | — | — | unknown |
3984 | EternalBlue.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | unknown |
3984 | EternalBlue.exe | GET | 200 | 142.250.181.227:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQCQcQ4QWW%2BJahKAwoVwd4m6 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3984 | EternalBlue.exe | 3.130.204.160:80 | omerez.com | AMAZON-02 | US | unknown |
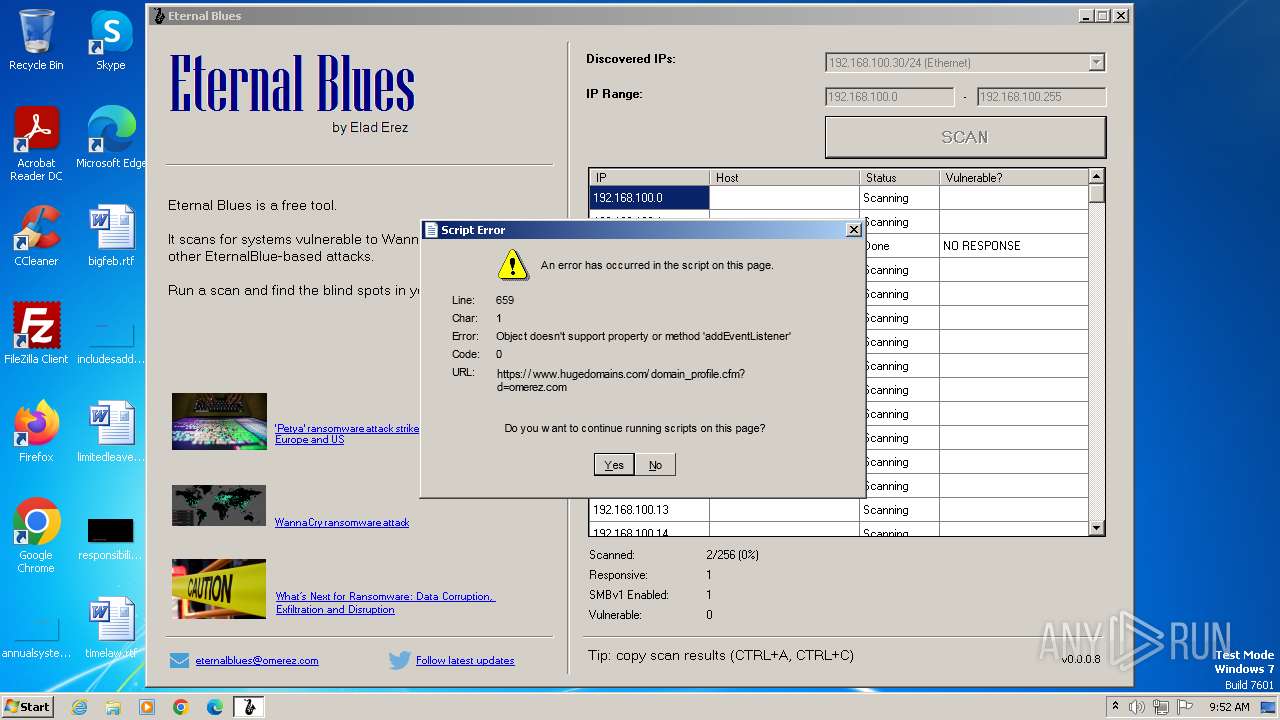
3984 | EternalBlue.exe | 172.67.70.191:443 | www.hugedomains.com | CLOUDFLARENET | US | unknown |
3984 | EternalBlue.exe | 192.168.100.2:445 | — | — | — | whitelisted |
3984 | EternalBlue.exe | 192.168.100.4:445 | — | — | — | unknown |
3984 | EternalBlue.exe | 192.168.100.1:445 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3984 | EternalBlue.exe | 213.155.157.168:80 | ctldl.windowsupdate.com | Telia Company AB | SE | unknown |
3984 | EternalBlue.exe | 142.250.181.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3984 | EternalBlue.exe | 142.250.184.202:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
3984 | EternalBlue.exe | 172.67.20.8:443 | cdn-cookieyes.com | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
omerez.com |
| unknown |
www.hugedomains.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
use.typekit.net |
| whitelisted |
static.hugedomains.com |
| unknown |
fonts.googleapis.com |
| whitelisted |
cdn-cookieyes.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
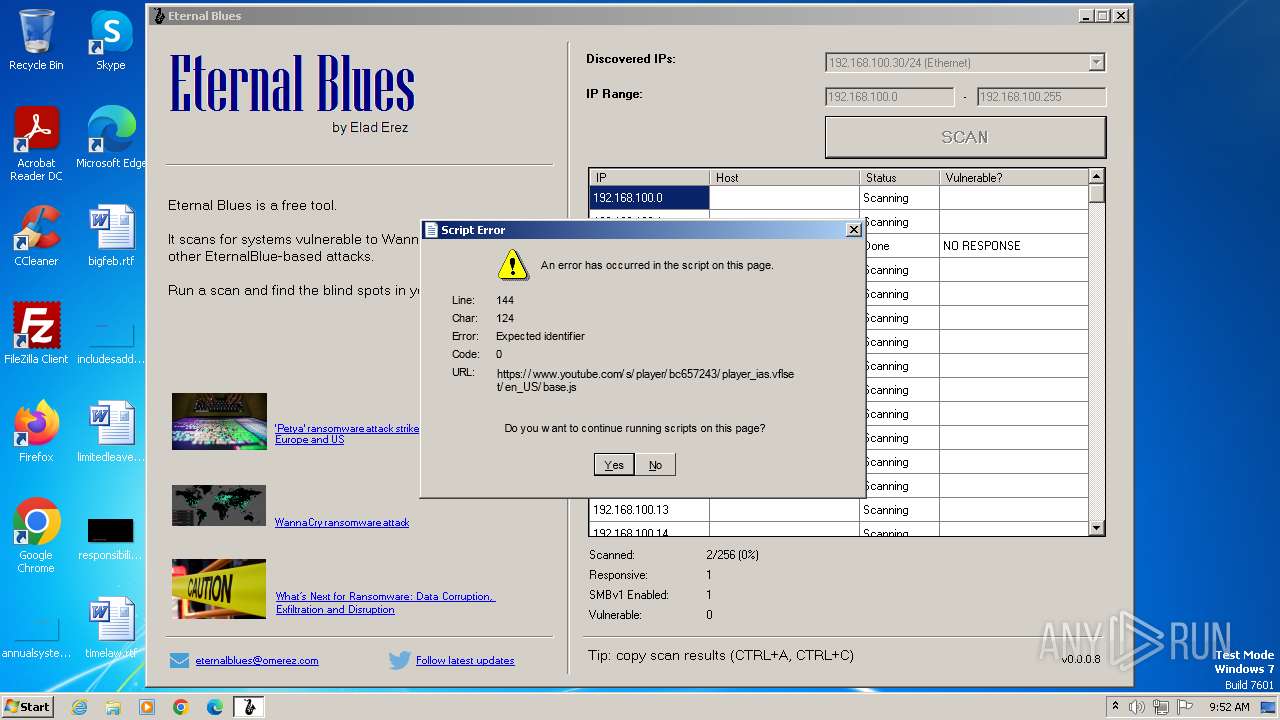
3984 | EternalBlue.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
1 ETPRO signatures available at the full report