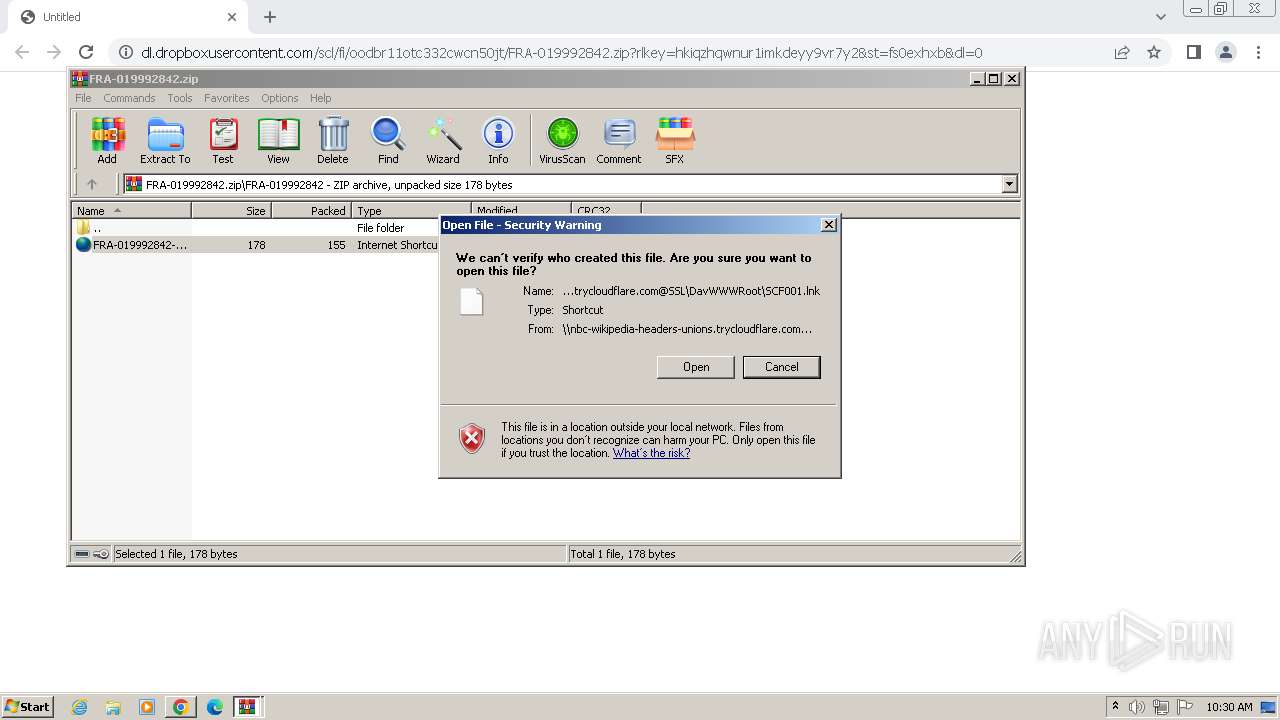
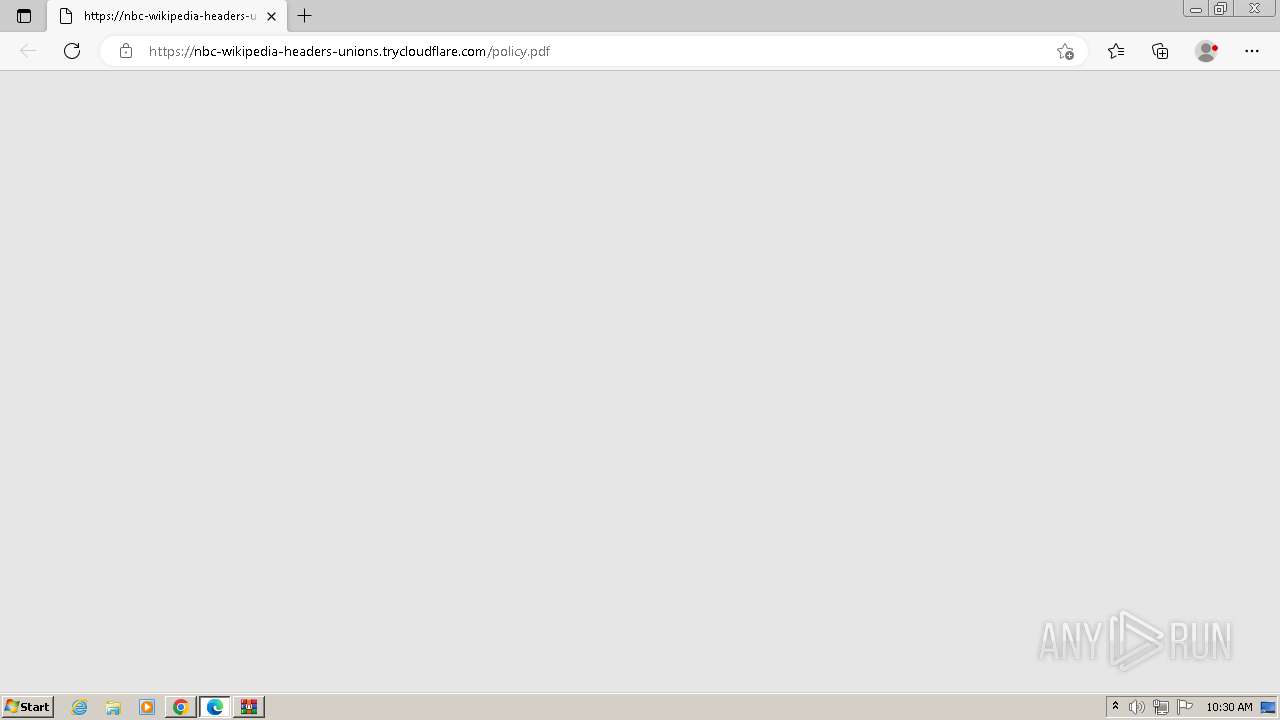
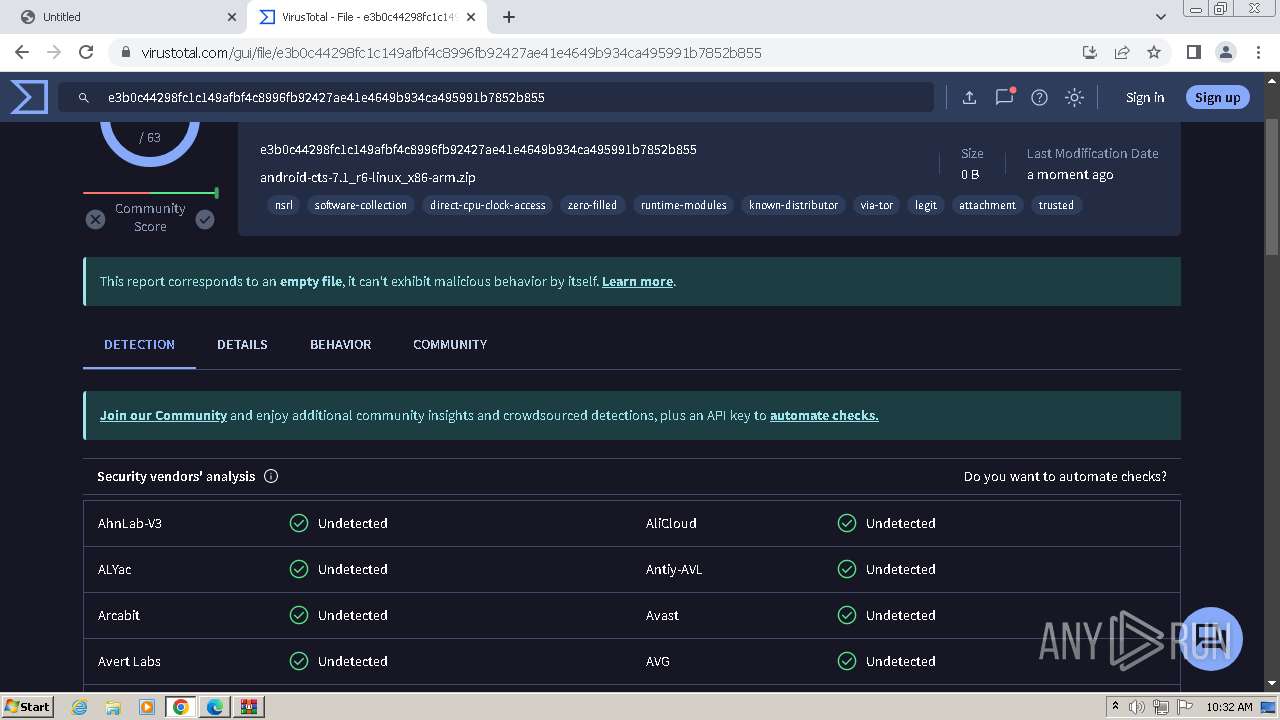
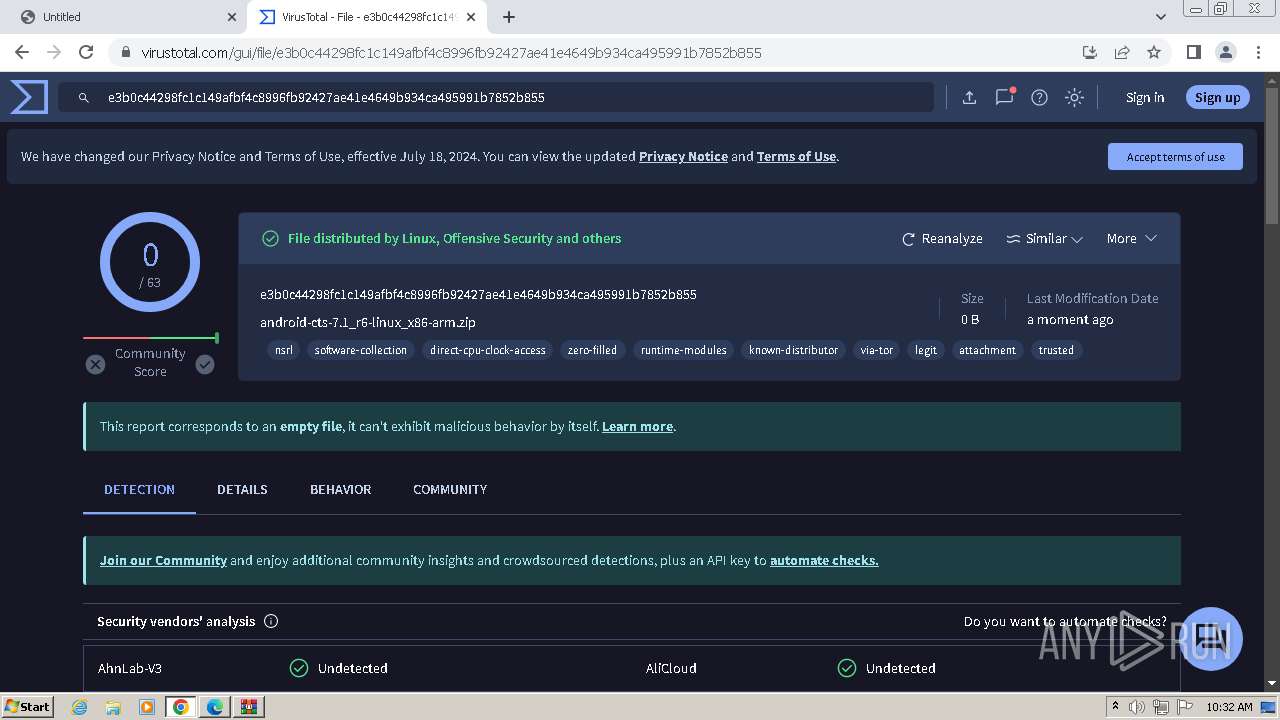
| URL: | https://dl.dropboxusercontent.com/scl/fi/oodbr11otc332cwcn50jt/FRA-019992842.zip?rlkey=hkiqzhqwnur1imkdeyy9vr7y2&st=fs0exhxb&dl=0 |
| Full analysis: | https://app.any.run/tasks/fc53728b-61f8-4146-b136-4aa5dcbf37a6 |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2024, 09:30:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
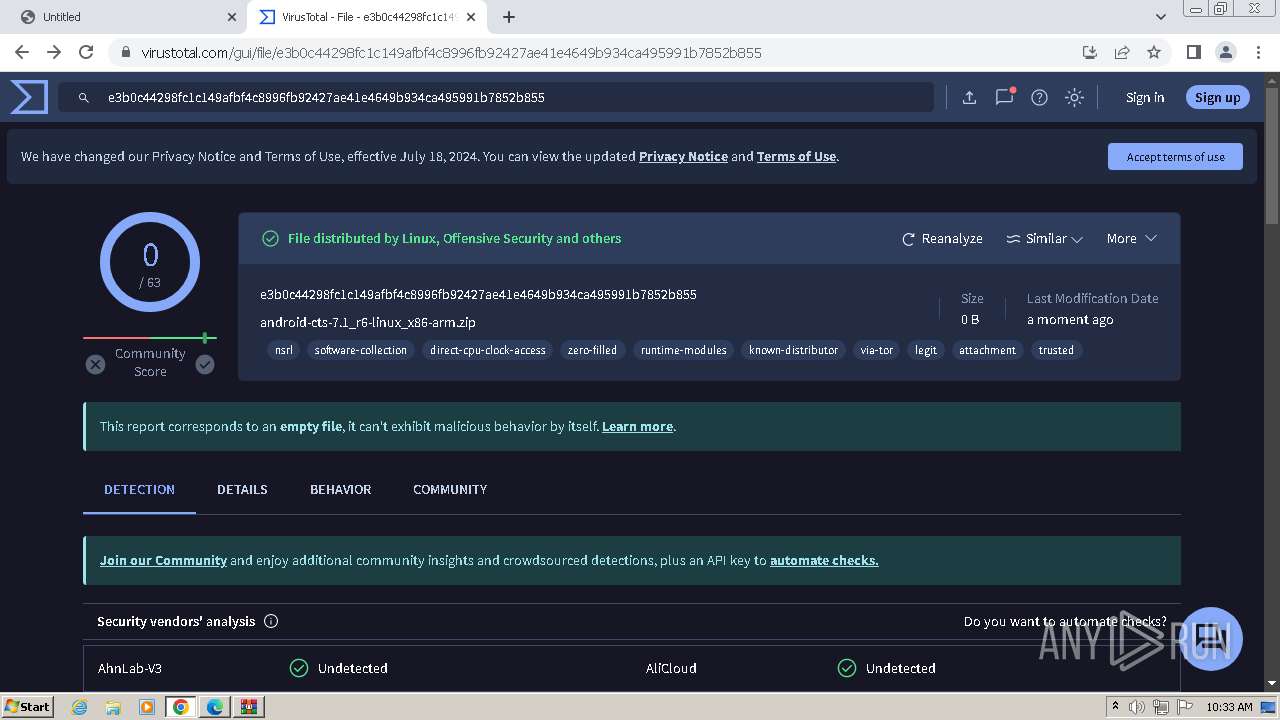
| MD5: | BBE9C7446E3FCCF3A7652213C577BD6F |
| SHA1: | 5CF2F2C28208E940138BCDB7E38F0D635BF35584 |
| SHA256: | 21C88012F90D128C06BB3068A4653761E865819CB19FA5FF422B92E13260885F |
| SSDEEP: | 3:N8RdNcvALtGTU6n3XsQc3kIVmcNRbfDZOAcYc1GzIkVTW+35A:27NFGgIqrw5Yc1GJThA |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 2400)
PHISHING has been detected (SURICATA)
- powershell.exe (PID: 2444)
- msedge.exe (PID: 3112)
SUSPICIOUS
Reads settings of System Certificates
- WinRAR.exe (PID: 444)
Checks Windows Trust Settings
- WinRAR.exe (PID: 444)
Starts POWERSHELL.EXE for commands execution
- WinRAR.exe (PID: 444)
- cmd.exe (PID: 2872)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 444)
Powershell scripting: start process
- WinRAR.exe (PID: 444)
Reads the Internet Settings
- powershell.exe (PID: 2400)
- cmd.exe (PID: 2872)
- powershell.exe (PID: 2444)
Executing commands from a ".bat" file
- powershell.exe (PID: 2400)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2400)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2872)
Request a resource from the Internet using PowerShell's cmdlet
- cmd.exe (PID: 2872)
Downloads file from URI
- powershell.exe (PID: 2444)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 2444)
INFO
The process uses the downloaded file
- chrome.exe (PID: 736)
- WinRAR.exe (PID: 444)
Checks supported languages
- wmpnscfg.exe (PID: 2648)
Reads the computer name
- wmpnscfg.exe (PID: 2648)
Checks proxy server information
- WinRAR.exe (PID: 444)
- powershell.exe (PID: 2400)
Manual execution by a user
- wmpnscfg.exe (PID: 2648)
Reads the software policy settings
- WinRAR.exe (PID: 444)
Application launched itself
- chrome.exe (PID: 3976)
- msedge.exe (PID: 2796)
Drops the executable file immediately after the start
- chrome.exe (PID: 1660)
Executable content was dropped or overwritten
- chrome.exe (PID: 1660)
Disables trace logs
- powershell.exe (PID: 2444)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
84
Monitored processes
45
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 112 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4400 --field-trial-handle=1356,i,8253569677731861839,7490229184985195150,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 304 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2016 --field-trial-handle=1144,i,13539599199737919351,5092840889132813259,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 444 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\FRA-019992842.zip" | C:\Program Files\WinRAR\WinRAR.exe | chrome.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3532 --field-trial-handle=1144,i,13539599199737919351,5092840889132813259,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 860 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=2272 --field-trial-handle=1144,i,13539599199737919351,5092840889132813259,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 956 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=756 --field-trial-handle=1144,i,13539599199737919351,5092840889132813259,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1280 --field-trial-handle=1144,i,13539599199737919351,5092840889132813259,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1044 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4360 --field-trial-handle=1356,i,8253569677731861839,7490229184985195150,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1136 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1508 --field-trial-handle=1144,i,13539599199737919351,5092840889132813259,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1432 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4180 --field-trial-handle=1356,i,8253569677731861839,7490229184985195150,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
35 282
Read events
35 055
Write events
200
Delete events
27
Modification events
| (PID) Process: | (3976) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3976) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3976) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3976) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3976) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3976) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3976) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3976) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3976) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3976) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
2
Suspicious files
168
Text files
69
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF103b36.TMP | — | |
MD5:— | SHA256:— | |||
| 3976 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3976 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 3976 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:9F941EA08DBDCA2EB3CFA1DBBBA6F5DC | SHA256:127F71DF0D2AD895D4F293E62284D85971AE047CA15F90B87BF6335898B0B655 | |||
| 3976 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\164853cb-2cb6-4d3a-be1e-89447f4c00ed.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 3976 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:FA25AF7098FC1571F24F200A9D105D58 | SHA256:4F40C87070B7A151FB241CCF36E7027AA703C15CA0ACB0A1759DA07B2C318574 | |||
| 3976 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old~RF104122.TMP | — | |
MD5:— | SHA256:— | |||
| 3976 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3976 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF103d2a.TMP | text | |
MD5:AD0DB8476493577A67FA94A162B646C4 | SHA256:304FB5B4FD83D4A9FF1EF4CF20232A1783169C148297BFE37ED24A1D22A74F2B | |||
| 3976 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:456D3EF989973A7C218E338A6CFFAD25 | SHA256:75631D994431F254B94255C50038A3657BFC45D76FCE9D794D514E57CA678872 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
66
DNS requests
73
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
444 | WinRAR.exe | GET | 200 | 23.32.238.201:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?49fbcf7755c03e5c | unknown | — | — | unknown |
884 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTBmQUFZUHRkSkgtb01uSGNvRHZ2Tm5HQQ/1.0.0.15_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | unknown |
884 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTBmQUFZUHRkSkgtb01uSGNvRHZ2Tm5HQQ/1.0.0.15_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
884 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1036 | chrome.exe | 142.250.145.84:443 | accounts.google.com | GOOGLE | US | unknown |
3976 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
1036 | chrome.exe | 162.125.69.15:443 | dl.dropboxusercontent.com | DROPBOX | US | unknown |
3976 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
1036 | chrome.exe | 142.250.185.78:443 | sb-ssl.google.com | GOOGLE | US | whitelisted |
1036 | chrome.exe | 216.58.206.36:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
dl.dropboxusercontent.com |
| shared |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| whitelisted |
nbc-wikipedia-headers-unions.trycloudflare.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
www.googleapis.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1036 | chrome.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
1088 | svchost.exe | Potentially Bad Traffic | ET POLICY Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
2444 | powershell.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Cloudflare Domain Abuse for Phishing or OpenDir Purposes (RGDA) |
3112 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Cloudflare Domain Abuse for Phishing or OpenDir Purposes (RGDA) |
3112 | msedge.exe | Potentially Bad Traffic | ET POLICY Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
3112 | msedge.exe | Potentially Bad Traffic | ET POLICY Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
3112 | msedge.exe | Potentially Bad Traffic | ET POLICY Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
3112 | msedge.exe | Potentially Bad Traffic | ET POLICY Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
3112 | msedge.exe | Potentially Bad Traffic | ET POLICY Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |