| File name: | C:\Users\admin\Downloads\apex.jnlp |
| Full analysis: | https://app.any.run/tasks/9e8f1586-d45f-44cb-9ad8-371210495ce3 |
| Verdict: | Malicious activity |
| Analysis date: | September 16, 2021, 08:38:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/xml |
| File info: | XML 1.0 document, ASCII text, with very long lines, with no line terminators |
| MD5: | FA192666B2C2E09FE776A5B318244928 |
| SHA1: | 22E628A733FE1B2A8A64923F898E7D5873239D58 |
| SHA256: | 21AA2D96F23ED009D2B5FB5AF086579C345E8B5004C9EFC9E9D33F5394142997 |
| SSDEEP: | 48:czl6av6FEXvNunPf1YS+H1D8IsIaHOLB6aaf4/UNA5:W28FePiH98VI4OhCXi |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks supported languages
- javaws.exe (PID: 3680)
- javaw.exe (PID: 3856)
- javaw.exe (PID: 2200)
- javaw.exe (PID: 2672)
- jp2launcher.exe (PID: 3900)
- javaws.exe (PID: 3160)
- jp2launcher.exe (PID: 1072)
Check for Java to be installed
- javaws.exe (PID: 3680)
- javaw.exe (PID: 3856)
- javaw.exe (PID: 2200)
- javaw.exe (PID: 2672)
- jp2launcher.exe (PID: 3900)
- jp2launcher.exe (PID: 1072)
Reads the computer name
- javaw.exe (PID: 3856)
- javaw.exe (PID: 2200)
- javaw.exe (PID: 2672)
- jp2launcher.exe (PID: 3900)
- jp2launcher.exe (PID: 1072)
Executes JAVA applets
- javaws.exe (PID: 3680)
Creates files in the program directory
- javaw.exe (PID: 3856)
Uses ICACLS.EXE to modify access control list
- javaw.exe (PID: 3856)
Application launched itself
- javaws.exe (PID: 3680)
- jp2launcher.exe (PID: 3900)
INFO
Reads the computer name
- icacls.exe (PID: 3036)
Checks supported languages
- icacls.exe (PID: 3036)
Reads settings of System Certificates
- jp2launcher.exe (PID: 3900)
- jp2launcher.exe (PID: 1072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jnlp | | | Java Web Start application descriptor (88.3) |
|---|---|---|
| .xml | | | Generic XML (ASCII) (11.6) |
EXIF
XMP
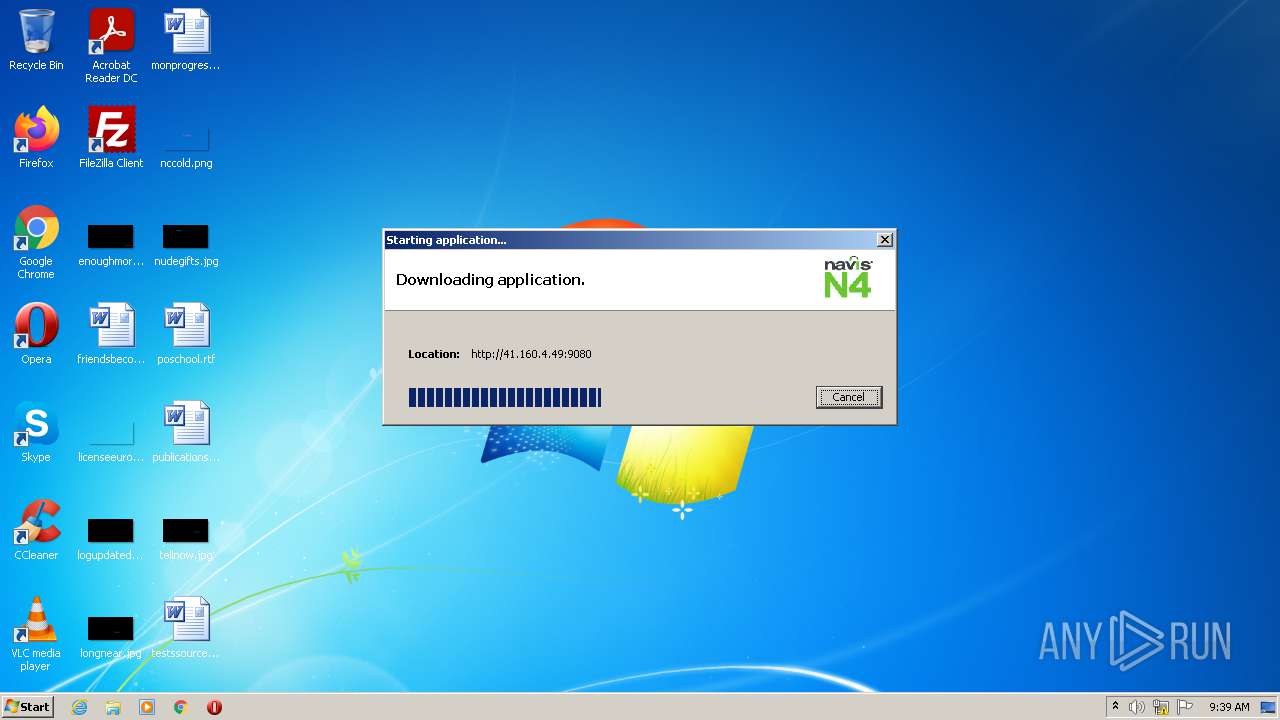
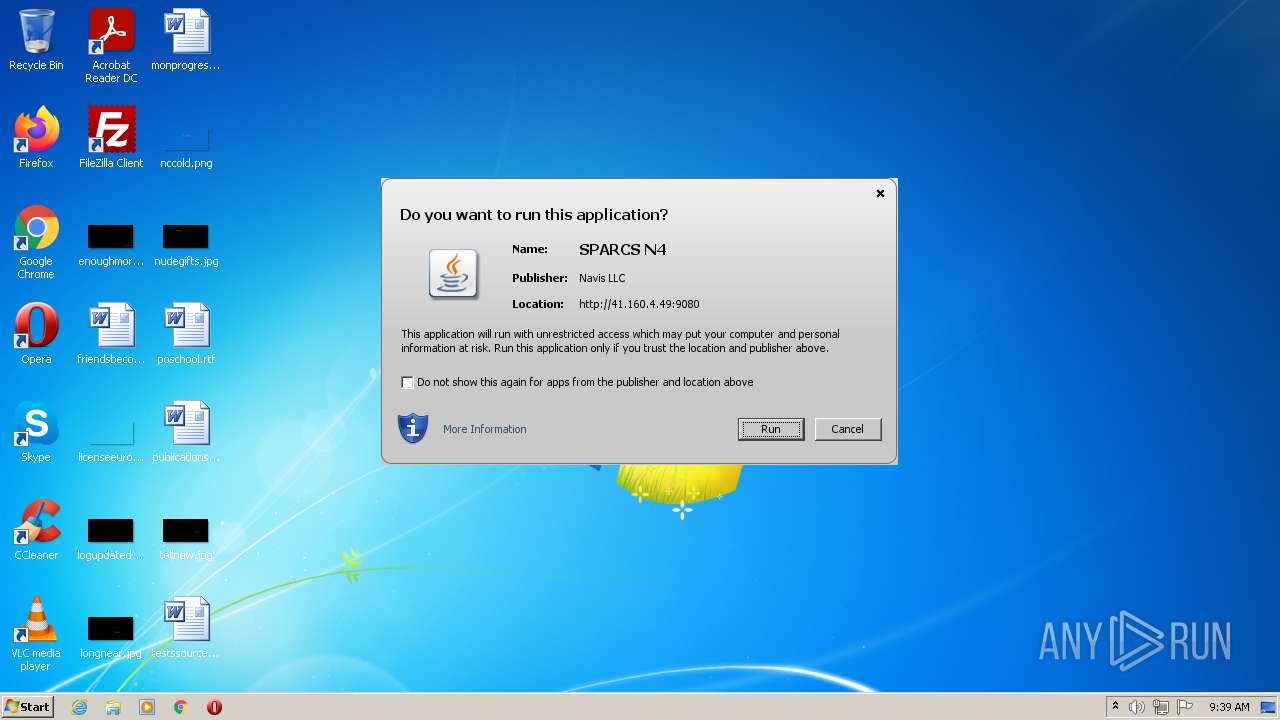
| JnlpApplication-descArgument: | url-string=http://41.160.4.49:9080/apex/ulc |
|---|---|
| JnlpApplication-descMain-class: | com.navis.framework.ulc.client.jnlp.CarinaJnlpLauncher |
| JnlpResourcesPropertyValue: | on |
| JnlpResourcesPropertyName: | navis-lookandfeel |
| JnlpResourcesJarMain: | |
| JnlpResourcesJarHref: | lib/ulc-framework-client-signed.jar |
| JnlpResourcesJ2seHref: | http://java.sun.com/products/autodl/j2se |
| JnlpResourcesJ2seMax-heap-size: | 768m |
| JnlpResourcesJ2seVersion: | 1.8+ |
| JnlpSecurityAll-permissions: | - |
| JnlpInformationIconHeight: | 64 |
| JnlpInformationIconWidth: | 64 |
| JnlpInformationIconHref: | n4_64.jpg |
| JnlpInformationHomepageHref: | http://www.navis.com |
| JnlpInformationDescription: | SPARCS N4 Application |
| JnlpInformationVendor: | Navis LLC |
| JnlpInformationTitle: | SPARCS N4 |
| JnlpHref: | apex.jnlp |
| JnlpCodebase: | http://41.160.4.49:9080/apex |
| JnlpSpec: | 1.0+ |
Total processes
43
Monitored processes
8
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1072 | "C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_271" -vma LVhteDc2OG0ALURuYXZpcy1sb29rYW5kZmVlbD1vbgAtRGFwcGxlLmF3dC5zaG93R3Jvd0JveD1mYWxzZQAtRGFwcGxlLmF3dC5hbnRpYWxpYXNpbmc9b2ZmAC1EYXBwbGUuYXd0LnRleHRhbnRpYWxpYXNpbmc9b24ALURmaWxlLmVuY29kaW5nPVVURi04AC1YYm9vdGNsYXNzcGF0aC9hOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcbGliXGphdmF3cy5qYXI7QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxsaWJcZGVwbG95LmphcjtDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxwbHVnaW4uamFyAC1Eam5scC50az1hd3QALWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxkZXBsb3kuamFyAC1Eam5scHgudm1hcmdzPUxWaHRlRGMyT0cwQUxVUnVZWFpwY3kxc2IyOXJZVzVrWm1WbGJEMXZiZ0F0UkdGd2NHeGxMbUYzZEM1emFHOTNSM0p2ZDBKdmVEMW1ZV3h6WlFBdFJHRndjR3hsTG1GM2RDNWhiblJwWVd4cFlYTnBibWM5YjJabUFDMUVZWEJ3YkdVdVlYZDBMblJsZUhSaGJuUnBZV3hwWVhOcGJtYzliMjRBTFVSbWFXeGxMbVZ1WTI5a2FXNW5QVlZVUmkwNEFBPT0ALURqbmxweC5qdm09QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxiaW5camF2YXcuZXhlAC1Eam5scHguc3BsYXNocG9ydD01NTMwOQAtRGpubHB4LmhvbWU9QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxiaW4ALURqbmxweC5yZW1vdmU9ZmFsc2UALURqbmxweC5vZmZsaW5lPWZhbHNlAC1Eam5scHgucmVsYXVuY2g9dHJ1ZQAtRGpubHB4LnNlc3Npb24uZGF0YT1DOlxVc2Vyc1xhZG1pblxBcHBEYXRhXExvY2FsXFRlbXBcc2Vzc2lvbjgwNTMyODg0NjEwMTQ5NjE1OTAALURqbmxweC5oZWFwc2l6ZT0tMSw4MDUzMDYzNjgALURqYXZhLnNlY3VyaXR5LnBvbGljeT1maWxlOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcbGliXHNlY3VyaXR5XGphdmF3cy5wb2xpY3kALUR0cnVzdFByb3h5PXRydWUALVh2ZXJpZnk6cmVtb3RlAC1Eam5scHgub3JpZ0ZpbGVuYW1lQXJnPUM6XFVzZXJzXGFkbWluXEFwcERhdGFcTG9jYWxcVGVtcFxhcGV4LmpubHAALURzdW4uYXd0Lndhcm11cD10cnVlAC1EamF2YS5zZWN1cml0eS5tYW5hZ2VyAA== -ma LXNlY3VyZQBDOlxVc2Vyc1xhZG1pblxBcHBEYXRhXExvY2FsTG93XFN1blxKYXZhXERlcGxveW1lbnRcY2FjaGVcNi4wXDI1XDM5N2ZiNzU5LTI2MDMyN2Q4AA== -ta LURuYXZpcy1sb29rYW5kZmVlbD1vbgAtRGFwcGxlLmF3dC5zaG93R3Jvd0JveD1mYWxzZQAtRGFwcGxlLmF3dC5hbnRpYWxpYXNpbmc9b2ZmAC1EYXBwbGUuYXd0LnRleHRhbnRpYWxpYXNpbmc9b24ALURmaWxlLmVuY29kaW5nPVVURi04AA== -checkParent | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | jp2launcher.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 2200 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.timestamp.11.271.2" "1631781574" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2672 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.suppression.11.271.2" "false" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3036 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\system32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3160 | JavaWSSplashScreen -splash 55308 "C:\Program Files\Java\jre1.8.0_271\lib\deploy\splash.gif" | C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 3680 | "C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe" "C:\Users\admin\AppData\Local\Temp\apex.jnlp" | C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 3856 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.11.271.2" "later" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3900 | "C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_271" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxkZXBsb3kuamFyAC1EamF2YS5zZWN1cml0eS5wb2xpY3k9ZmlsZTpDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxzZWN1cml0eVxqYXZhd3MucG9saWN5AC1EdHJ1c3RQcm94eT10cnVlAC1YdmVyaWZ5OnJlbW90ZQAtRGpubHB4LmhvbWU9QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURqbmxweC5vcmlnRmlsZW5hbWVBcmc9QzpcVXNlcnNcYWRtaW5cQXBwRGF0YVxMb2NhbFxUZW1wXGFwZXguam5scAAtRGpubHB4LnJlbW92ZT1mYWxzZQAtRHN1bi5hd3Qud2FybXVwPXRydWUALVhib290Y2xhc3NwYXRoL2E6QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxsaWJcamF2YXdzLmphcjtDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxkZXBsb3kuamFyO0M6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcbGliXHBsdWdpbi5qYXIALVhteDc2OG0ALURqbmxweC5oZWFwc2l6ZT1OVUxMLDc2OG0ALURqbmxweC5zcGxhc2hwb3J0PTU1MzA5AC1Eam5scHguanZtPUM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcYmluXGphdmF3LmV4ZQ== -ma QzpcVXNlcnNcYWRtaW5cQXBwRGF0YVxMb2NhbFxUZW1wXGFwZXguam5scA== | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
Total events
5 343
Read events
5 203
Write events
129
Delete events
11
Modification events
| (PID) Process: | (3856) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3856) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.modified.timestamp |
Value: 1604367352626 | |||
| (PID) Process: | (3856) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.roaming.profile |
Value: false | |||
| (PID) Process: | (3856) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.version |
Value: 8 | |||
| (PID) Process: | (3856) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.expired.version |
Value: 11.271.2 | |||
| (PID) Process: | (3856) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.browser.path |
Value: C:\Program Files\Internet Explorer\iexplore.exe | |||
| (PID) Process: | (3856) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.expiration.decision.11.271.2 |
Value: later | |||
| (PID) Process: | (2200) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2200) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.expiration.decision.11.271.2 |
Value: later | |||
| (PID) Process: | (2200) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.modified.timestamp |
Value: 1631781574353 | |||
Executable files
12
Suspicious files
10
Text files
14
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3856 | javaw.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\deployment.properties | text | |
MD5:— | SHA256:— | |||
| 3856 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:— | SHA256:— | |||
| 3900 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\25\397fb759-260327d8-temp | xml | |
MD5:— | SHA256:— | |||
| 3900 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\25\397fb759-260327d8 | xml | |
MD5:— | SHA256:— | |||
| 3856 | javaw.exe | C:\Users\admin\AppData\Local\Temp\JavaDeployReg.log | text | |
MD5:— | SHA256:— | |||
| 3900 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\34\44f51962-59410f01-temp | java | |
MD5:— | SHA256:— | |||
| 3900 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\38\255c2e6-570e429f.idx | abr | |
MD5:7A2B2A6A7418160B22D307F5BEA63383 | SHA256:F7118AFB02DDEAC1D903751E9E0F252CA7BDE1B5357CE966C777D471D1E1E50D | |||
| 3900 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\38\255c2e6-570e429f-temp | java | |
MD5:— | SHA256:— | |||
| 3900 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\25\397fb759-edb1a84e2d9431638727edced0eb7ea253f9d12a2f1a052b520c5adbadd0cdfe-6.0.lap | text | |
MD5:— | SHA256:— | |||
| 3900 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\38\255c2e6-570e429f | java | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
9
DNS requests
1
Threats
22
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3900 | jp2launcher.exe | GET | — | 41.160.4.49:9080 | http://41.160.4.49:9080/apex/lib/ulc-framework-client-signed.jar | ZA | — | — | suspicious |
3900 | jp2launcher.exe | GET | — | 41.160.4.49:9080 | http://41.160.4.49:9080/apex/lib/ulc-core-client-signed.jar | ZA | — | — | suspicious |
3900 | jp2launcher.exe | GET | — | 41.160.4.49:9080 | http://41.160.4.49:9080/apex/lib/jh-signed.jar | ZA | — | — | suspicious |
1072 | jp2launcher.exe | POST | 200 | 41.160.4.49:9080 | http://41.160.4.49:9080/apex/ulc | ZA | pz | 12 b | suspicious |
1072 | jp2launcher.exe | POST | 200 | 41.160.4.49:9080 | http://41.160.4.49:9080/apex/ulc | ZA | pz | 58 b | suspicious |
1072 | jp2launcher.exe | POST | 200 | 41.160.4.49:9080 | http://41.160.4.49:9080/apex/ulc | ZA | pz | 12 b | suspicious |
1072 | jp2launcher.exe | POST | 200 | 41.160.4.49:9080 | http://41.160.4.49:9080/apex/ulc | ZA | pz | 4.38 Kb | suspicious |
3900 | jp2launcher.exe | GET | 200 | 41.160.4.49:9080 | http://41.160.4.49:9080/apex/lib/jgoodies-common-signed.jar | ZA | compressed | 35.2 Kb | suspicious |
3900 | jp2launcher.exe | GET | 200 | 41.160.4.49:9080 | http://41.160.4.49:9080/apex/apex.jnlp | ZA | xml | 2.28 Kb | suspicious |
3900 | jp2launcher.exe | GET | 200 | 41.160.4.49:9080 | http://41.160.4.49:9080/apex/lib/jgoodies-looks-signed.jar | ZA | compressed | 422 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3900 | jp2launcher.exe | 41.160.4.49:9080 | — | Neotel Pty Ltd | ZA | suspicious |
3900 | jp2launcher.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1072 | jp2launcher.exe | 41.160.4.49:9080 | — | Neotel Pty Ltd | ZA | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3900 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
3900 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
3900 | jp2launcher.exe | Potentially Bad Traffic | ET INFO Java .jar request to dotted-quad domain |
3900 | jp2launcher.exe | Potentially Bad Traffic | ET INFO Java .jar request to dotted-quad domain |
3900 | jp2launcher.exe | Potentially Bad Traffic | ET INFO Java .jar request to dotted-quad domain |
3900 | jp2launcher.exe | Potentially Bad Traffic | ET INFO Java .jar request to dotted-quad domain |
3900 | jp2launcher.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download By Vulnerable Client |
3900 | jp2launcher.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download By Vulnerable Client |
3900 | jp2launcher.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download By Vulnerable Client |
3900 | jp2launcher.exe | Potentially Bad Traffic | ET INFO Java .jar request to dotted-quad domain |
7 ETPRO signatures available at the full report