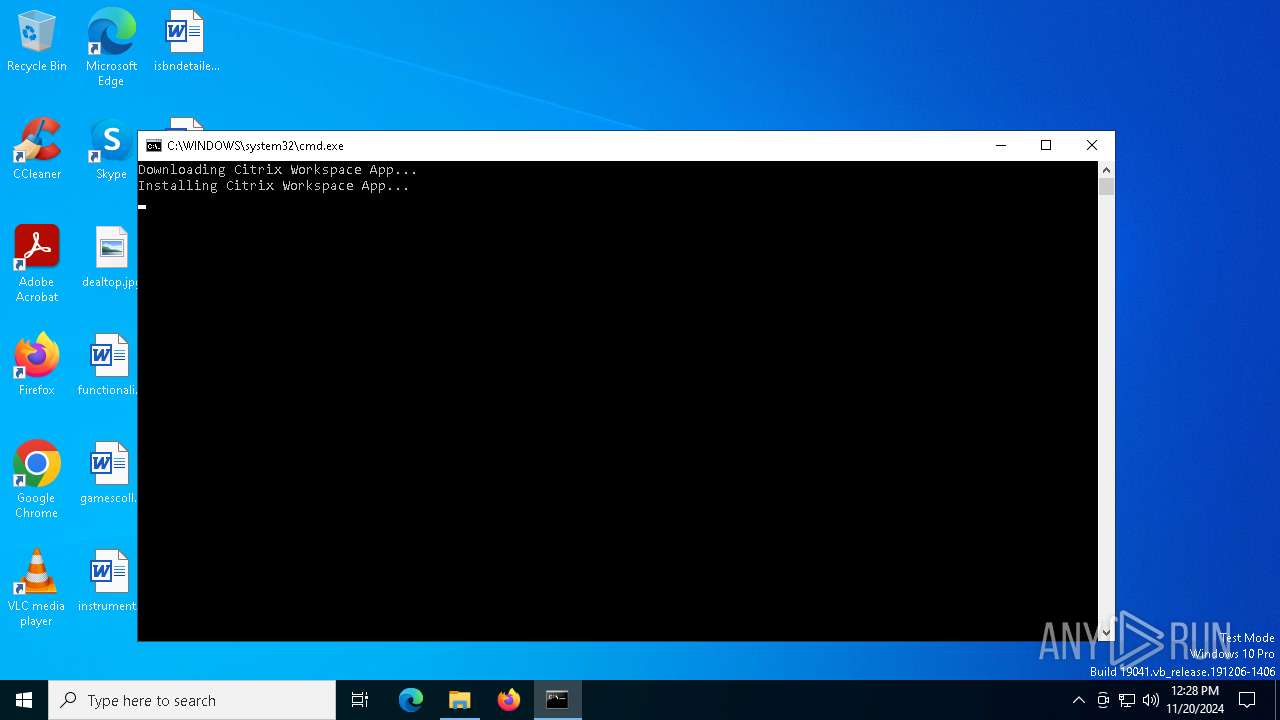
| File name: | install.bat |
| Full analysis: | https://app.any.run/tasks/55c8d5f8-7ef9-4899-a1de-3bf6b7d60bbe |
| Verdict: | Malicious activity |
| Analysis date: | November 20, 2024, 12:25:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | 49C492931CE377F7393D6BC783F1A7B8 |
| SHA1: | 16B7FACE7FDB1A1B7838073520FF87A30D090BFC |
| SHA256: | 21A0E8B0B27D2ADC5DFD2391E1A88A595EA6B62896232D0BBC8B359526BBC6DE |
| SSDEEP: | 12:w7RiqeWlX8DYJyQ980qWAROXyENLfJyDlNOXwRXjWrHtwWFa8NGNADJWFTq68OX0:w7RbeWN8MJyK5AR4TNLfJyxN4wFjSNJl |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5776)
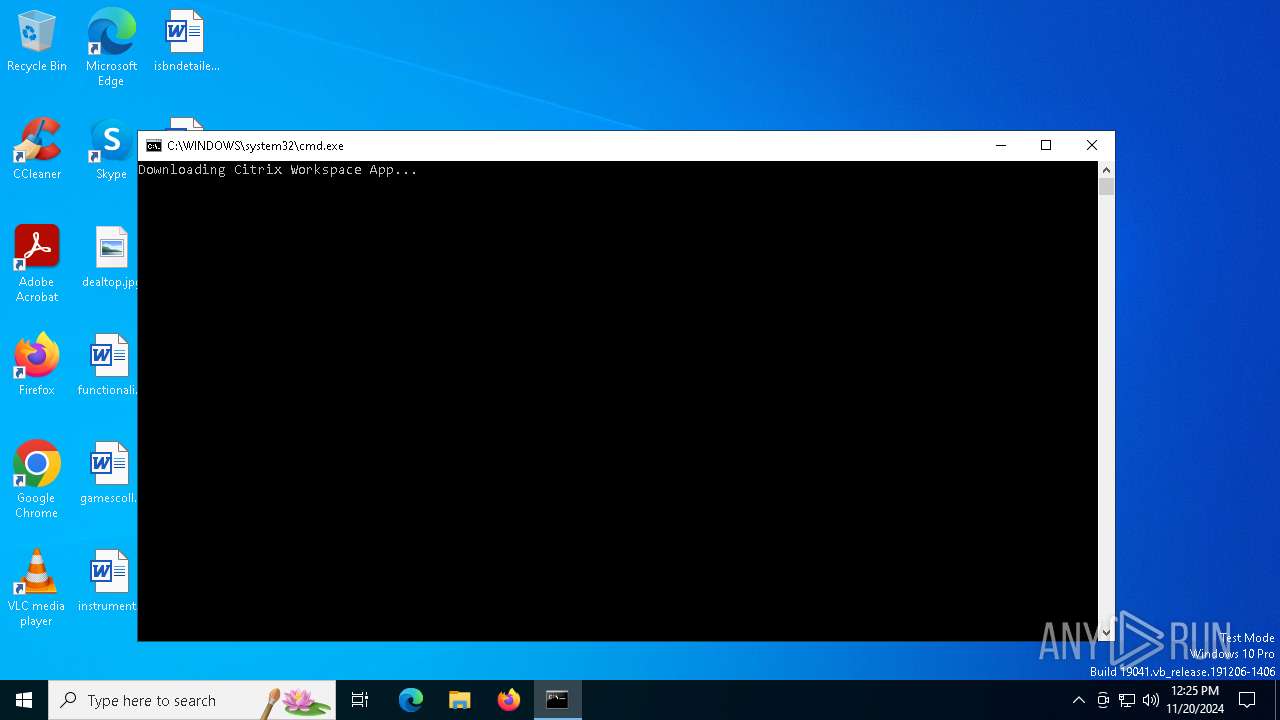
Probably download files using WebClient
- cmd.exe (PID: 5776)
The executable file from the user directory is run by the CMD process
- CitrixWorkspaceApp.exe (PID: 6856)
Process drops legitimate windows executable
- bootstrapperhelper.exe (PID: 6976)
- windowsdesktop-runtime-6.0.25-win-x86.exe (PID: 5404)
- windowsdesktop-runtime-6.0.25-win-x86.exe (PID: 4420)
- windowsdesktop-runtime-6.0.25-win-x86.exe (PID: 3896)
- msiexec.exe (PID: 4988)
- vc_redist.x86.exe (PID: 4968)
- vc_redist.x86.exe (PID: 6220)
- VC_redist.x86.exe (PID: 1076)
- VC_redist.x86.exe (PID: 6744)
- vc_redist.x64.exe (PID: 6888)
- VC_redist.x64.exe (PID: 6560)
- VC_redist.x64.exe (PID: 4280)
- MicrosoftEdgeUpdate.exe (PID: 6156)
- MicrosoftEdgeWebview2Setup.exe (PID: 5308)
- DXSETUP.exe (PID: 6848)
- vc_redist.x64.exe (PID: 6972)
Executable content was dropped or overwritten
- CitrixWorkspaceApp.exe (PID: 6856)
- DotNet6Installer.exe (PID: 7156)
- bootstrapperhelper.exe (PID: 6976)
- DotNet6Installer.exe (PID: 712)
- DotNet6Installer.exe (PID: 5548)
- DotNet6Installer.exe (PID: 5572)
- windowsdesktop-runtime-6.0.25-win-x86.exe (PID: 5404)
- windowsdesktop-runtime-6.0.25-win-x86.exe (PID: 4420)
- windowsdesktop-runtime-6.0.25-win-x86.exe (PID: 3896)
- vc_redist.x86.exe (PID: 4968)
- vc_redist.x64.exe (PID: 6888)
- VC_redist.x86.exe (PID: 1076)
- VC_redist.x86.exe (PID: 1512)
- VC_redist.x86.exe (PID: 6744)
- DotNet6Installer.exe (PID: 7100)
- vc_redist.x86.exe (PID: 6220)
- DXSETUP.exe (PID: 6848)
- VC_redist.x64.exe (PID: 6560)
- VC_redist.x64.exe (PID: 4420)
- vc_redist.x64.exe (PID: 6972)
- MicrosoftEdgeWebview2Setup.exe (PID: 5308)
- VC_redist.x64.exe (PID: 4280)
The process drops C-runtime libraries
- bootstrapperhelper.exe (PID: 6976)
- msiexec.exe (PID: 4988)
Starts itself from another location
- DotNet6Installer.exe (PID: 7156)
- DotNet6Installer.exe (PID: 712)
- DotNet6Installer.exe (PID: 5572)
- DotNet6Installer.exe (PID: 7100)
- windowsdesktop-runtime-6.0.25-win-x86.exe (PID: 5404)
- vc_redist.x86.exe (PID: 6220)
- vc_redist.x64.exe (PID: 6972)
Executes as Windows Service
- VSSVC.exe (PID: 6320)
- UpdaterService.exe (PID: 6356)
Starts a Microsoft application from unusual location
- windowsdesktop-runtime-6.0.25-win-x86.exe (PID: 5404)
- windowsdesktop-runtime-6.0.25-win-x86.exe (PID: 3896)
- VC_redist.x86.exe (PID: 1076)
- vc_redist.x86.exe (PID: 6220)
- vc_redist.x64.exe (PID: 6972)
- VC_redist.x64.exe (PID: 6560)
- MicrosoftEdgeUpdate.exe (PID: 6156)
Application launched itself
- VC_redist.x86.exe (PID: 6836)
- VC_redist.x86.exe (PID: 1512)
- VC_redist.x64.exe (PID: 4420)
- VC_redist.x64.exe (PID: 5404)
INFO
Manages system restore points
- SrTasks.exe (PID: 4392)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
187
Monitored processes
50
Malicious processes
8
Suspicious processes
13
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 244 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 712 | "C:\Users\admin\AppData\Local\Temp\{D32FCBE6-A565-48F3-B14F-CB40AA8F2D8B}\.cr\DotNet6Installer.exe" -burn.clean.room="C:\Program Files (x86)\Citrix\Ctx-644FE573-E3E1-489A-B6DC-0410797B72D3\DotNet6Installer.exe" -burn.filehandle.attached=564 -burn.filehandle.self=560 /silent /norestart /l "C:\Program Files (x86)\Citrix\Logs\CTXPreRequisiteInstallLogs-20241120-122733\CtxInstall-DotNet6Installer-20241120-122733.log" | C:\Users\admin\AppData\Local\Temp\{D32FCBE6-A565-48F3-B14F-CB40AA8F2D8B}\.cr\DotNet6Installer.exe | DotNet6Installer.exe | ||||||||||||
User: admin Company: Citrix Systems, Inc. Integrity Level: HIGH Description: DotNet6Installer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1076 | "C:\WINDOWS\Temp\{74E74165-ED79-4EC3-9EE1-AE5E7064B89D}\.be\VC_redist.x86.exe" -q -burn.elevated BurnPipe.{816DB1C9-3465-4706-9634-D1901CEAA748} {A804BF25-8504-4892-A155-9606215160CD} 6220 | C:\Windows\Temp\{74E74165-ED79-4EC3-9EE1-AE5E7064B89D}\.be\VC_redist.x86.exe | vc_redist.x86.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2022 Redistributable (x86) - 14.40.33810 Exit code: 0 Version: 14.40.33810.0 | |||||||||||||||
| 1512 | "C:\ProgramData\Package Cache\{410c0ee1-00bb-41b6-9772-e12c2828b02f}\VC_redist.x86.exe" -burn.clean.room="C:\ProgramData\Package Cache\{410c0ee1-00bb-41b6-9772-e12c2828b02f}\VC_redist.x86.exe" -burn.filehandle.attached=548 -burn.filehandle.self=568 -uninstall -quiet -burn.related.upgrade -burn.ancestors={47109d57-d746-4f8b-9618-ed6a17cc922b} -burn.filehandle.self=1156 -burn.embedded BurnPipe.{065DD59F-0333-48E2-86D0-9DA52D2BA95A} {6C6CE74C-A4D6-45CB-AA5D-847CF15EA19B} 1076 | C:\ProgramData\Package Cache\{410c0ee1-00bb-41b6-9772-e12c2828b02f}\VC_redist.x86.exe | VC_redist.x86.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2022 Redistributable (x86) - 14.36.32532 Exit code: 0 Version: 14.36.32532.0 | |||||||||||||||
| 2536 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2544 | C:\Windows\syswow64\MsiExec.exe -Embedding 7A93AF8298B24EA7D090FBAF90550E65 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 3896 | "C:\WINDOWS\Temp\{0D5C5AA4-86F6-4AB2-98D3-CC8F0098B766}\.be\windowsdesktop-runtime-6.0.25-win-x86.exe" -q -burn.elevated BurnPipe.{2C432A7C-B455-4BA1-B7CC-9127EE84C8B7} {2BACF646-8ACE-4F81-B26E-AEAD1F5AF97C} 5404 | C:\Windows\Temp\{0D5C5AA4-86F6-4AB2-98D3-CC8F0098B766}\.be\windowsdesktop-runtime-6.0.25-win-x86.exe | windowsdesktop-runtime-6.0.25-win-x86.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Desktop Runtime - 6.0.25 (x86) Exit code: 0 Version: 6.0.25.33020 | |||||||||||||||
| 3940 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4136 | powershell -Command "(New-Object Net.WebClient).DownloadFile('https://downloadplugins.citrix.com/Windows/CitrixWorkspaceApp.exe', 'C:\Users\admin\AppData\Local\Temp\CitrixWorkspaceApp.exe')" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4280 | "C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe" -q -burn.elevated BurnPipe.{0A9D31C1-4CA2-47D2-9E35-12EB5A10D7BA} {B1EE4C3C-4B8F-4B52-8DE9-9E4B11259F3F} 4420 | C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe | VC_redist.x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2022 Redistributable (x64) - 14.36.32532 Exit code: 0 Version: 14.36.32532.0 | |||||||||||||||
Total events
6 829
Read events
6 795
Write events
25
Delete events
9
Modification events
| (PID) Process: | (5548) DotNet6Installer.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000E3A0FA93473BDB01AC150000B0110000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3940) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000E3A0FA93473BDB01640F0000F4080000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3940) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000005DA13894473BDB01640F0000F4080000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3940) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000005DA13894473BDB01640F0000F4080000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3940) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000BD043B94473BDB01640F0000F4080000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3940) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 480000000000000019CD3F94473BDB01640F0000F4080000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3940) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (3940) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000AD93B494473BDB01640F0000F4080000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3940) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000FB5AB994473BDB01640F00008C030000E8030000010000000000000000000000F75FB21E23F16543BE68B2AD42D5328600000000000000000000000000000000 | |||
| (PID) Process: | (6320) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000D94FC594473BDB01B0180000D0170000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
1 943
Suspicious files
286
Text files
290
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6856 | CitrixWorkspaceApp.exe | C:\Users\admin\AppData\Local\Ctx-E2EE2428-01AC-44BC-814A-81D6099BC5E2\CTX_UPDATE_PACKAGE | — | |
MD5:— | SHA256:— | |||
| 6976 | bootstrapperhelper.exe | C:\Program Files (x86)\Citrix\Ctx-644FE573-E3E1-489A-B6DC-0410797B72D3\Localized_fr.xml | xml | |
MD5:2ACDB778EDB87365D41B83AE8A7807CF | SHA256:A237766860DF93517B9D53E3BE8B19554EB03F2C926F29D7D2C3EDA99ED21D55 | |||
| 6976 | bootstrapperhelper.exe | C:\Program Files (x86)\Citrix\Ctx-644FE573-E3E1-489A-B6DC-0410797B72D3\Localized_ja.xml | xml | |
MD5:067B08905D471E9B54B19FF9567EA763 | SHA256:BF12F4C31E8EADD6A14D015D3277AA95B5E43D9407B110512D705EB9C0724FB6 | |||
| 6976 | bootstrapperhelper.exe | C:\Program Files (x86)\Citrix\Ctx-644FE573-E3E1-489A-B6DC-0410797B72D3\Localized_de.xml | xml | |
MD5:0600794CADB5428DFD06989BD533DBA7 | SHA256:880A9F3A46FB1E1BE48813B75AB6A161A1CEABF850E303F2D127326365FA004D | |||
| 6976 | bootstrapperhelper.exe | C:\Program Files (x86)\Citrix\Ctx-644FE573-E3E1-489A-B6DC-0410797B72D3\Localized_zh-TW.xml | xml | |
MD5:7ADE1DA867B1D396D419AF35564D71B5 | SHA256:EAA5107AA88F9DF079BBB64F7C974C06995265F9A00E37449C894920CD8CD47F | |||
| 6976 | bootstrapperhelper.exe | C:\Program Files (x86)\Citrix\Ctx-644FE573-E3E1-489A-B6DC-0410797B72D3\Localized_ko.xml | xml | |
MD5:0063AE93AE4CD5E28147AC902DA0C5C5 | SHA256:72E41BD995E7EA5480D3E5A8FD439126BEC848EF84E5E4155804851833C34A61 | |||
| 6976 | bootstrapperhelper.exe | C:\Program Files (x86)\Citrix\Ctx-644FE573-E3E1-489A-B6DC-0410797B72D3\Localized_nl.xml | xml | |
MD5:BEF9043FF5D13B6F4C29933C4132FB18 | SHA256:C9ECD69CCF621FA2BE2D71C070B4C3929BE2FAA4425E948772B3C648C3A13660 | |||
| 6976 | bootstrapperhelper.exe | C:\Program Files (x86)\Citrix\Ctx-644FE573-E3E1-489A-B6DC-0410797B72D3\Localized_zh-CN.xml | xml | |
MD5:6F6A0530286D4A7213173F92DA0BA508 | SHA256:5336DDD75B782106797214BA602425BBCCDF4B5EFB117E7BC626D79C47110E04 | |||
| 4136 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wmn0iazv.uyr.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6976 | bootstrapperhelper.exe | C:\Program Files (x86)\Citrix\Ctx-644FE573-E3E1-489A-B6DC-0410797B72D3\EULA_de.rtf | text | |
MD5:5C237EF159F7EB42171DF229F6FB9516 | SHA256:EC53E79C9C1669D59225E656EDE4DE3E5A6DF2F382E7F74E987AA54C6150ED0B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
58
DNS requests
33
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/CSPCA.crl | unknown | — | — | whitelisted |
4932 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4932 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6484 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6484 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3280 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAVG%2Fhgj9%2BGUHaOfzhTEYXM%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5656 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4932 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4136 | powershell.exe | 104.102.33.172:443 | downloadplugins.citrix.com | AKAMAI-AS | DE | whitelisted |
4932 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4932 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4932 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.141:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
downloadplugins.citrix.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
CitrixWorkspaceApp.exe | RunPackage: bootstrap install started
|
CitrixWorkspaceApp.exe | CUpdatePackage::Run: Temp Path is C:\Users\admin\AppData\Local
|
CitrixWorkspaceApp.exe | Extracting files to folder with index -1
|
bootstrapperhelper.exe | CreateFolderAndExtactBinary::dualpk does not exist...C:\Program Files (x86)\Citrix\Ctx-644FE573-E3E1-489A-B6DC-0410797B72D3\dualpk.cab
|
bootstrapperhelper.exe | Installing PreRequisite from path C:\Program Files (x86)\Citrix\Ctx-644FE573-E3E1-489A-B6DC-0410797B72D3
|
bootstrapperhelper.exe | CreateFolderAndExtactBinary: User`is an Admin
|
bootstrapperhelper.exe | [C:\tc\work\153426901290c035\Utility\src\Windows\Source\CustomerSpecificBrandingHelper.cpp:154] CustomerSpecificBrandingHelper : Unable to find any BrandPersonalization install info. |
bootstrapperhelper.exe | Launching process from path : C:\Program Files (x86)\Citrix\Ctx-644FE573-E3E1-489A-B6DC-0410797B72D3\PreRequisiteInstaller.exe with cmdline /silent /AutoUpdateCheck=disabled /noreboot DONOTSTARTCC=1
|
bootstrapperhelper.exe | [C:\tc\work\153426901290c035\Utility\src\Windows\Source\CustomerSpecificBrandingHelper.cpp:91] CustomerSpecificBrandingHelper : There is no Admin install. |
PreRequisiteInstaller.exe | Information - CCommandLine::ParseParam(68) - Command Line Parameter: =
|