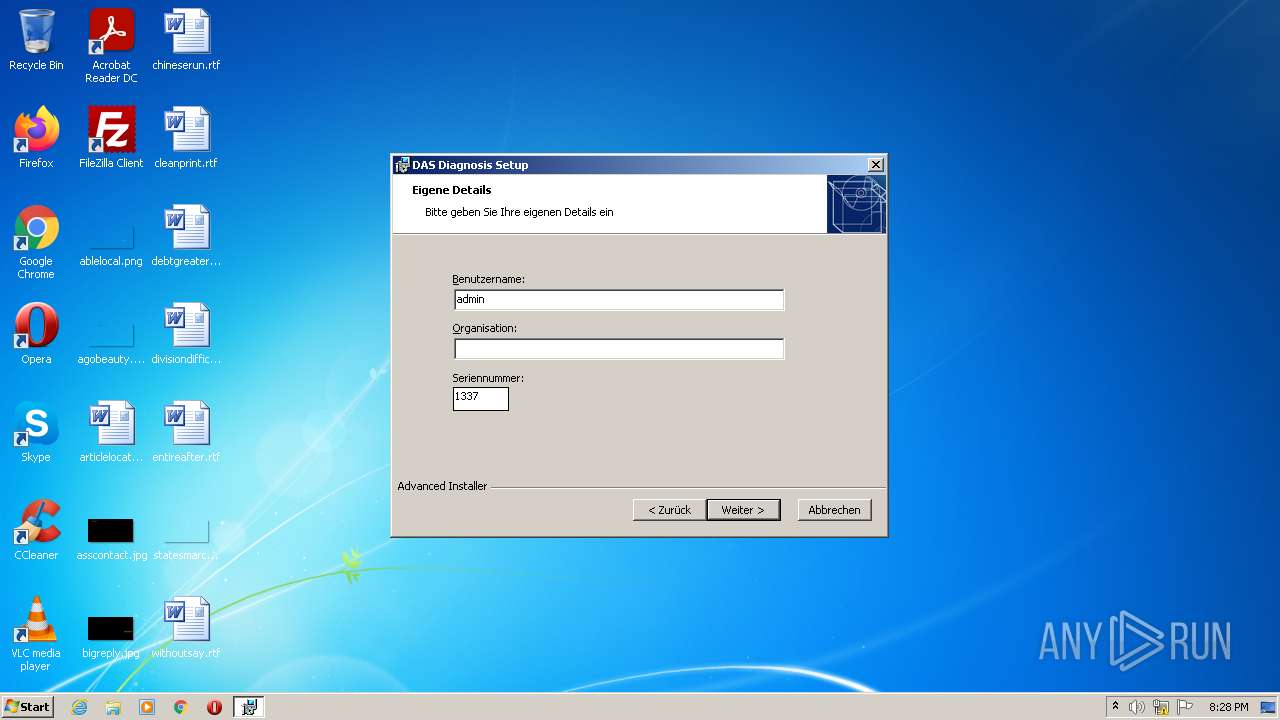
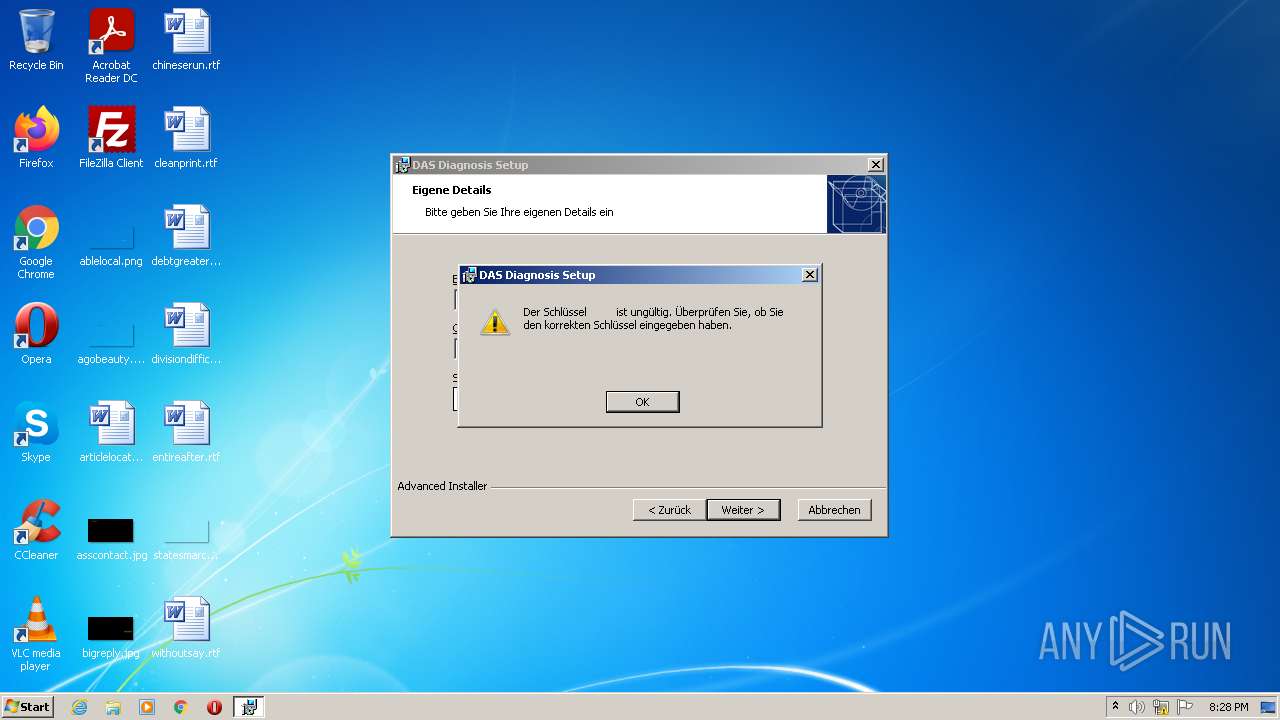
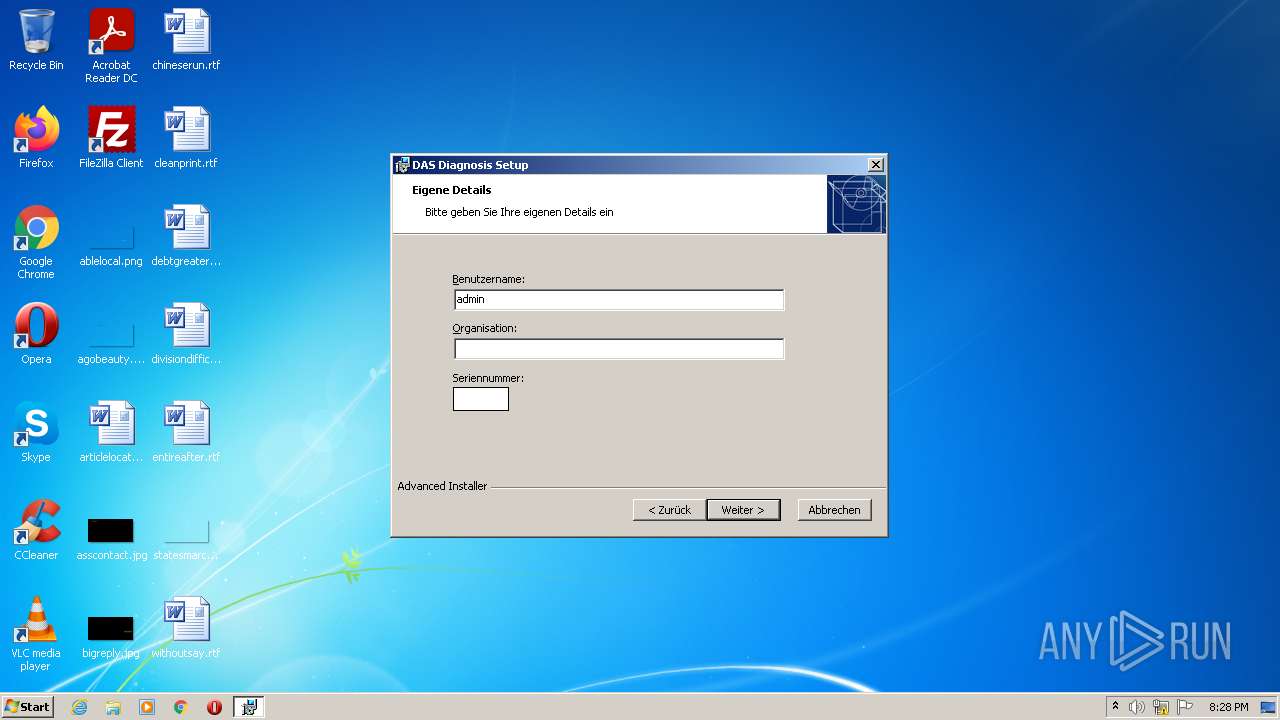
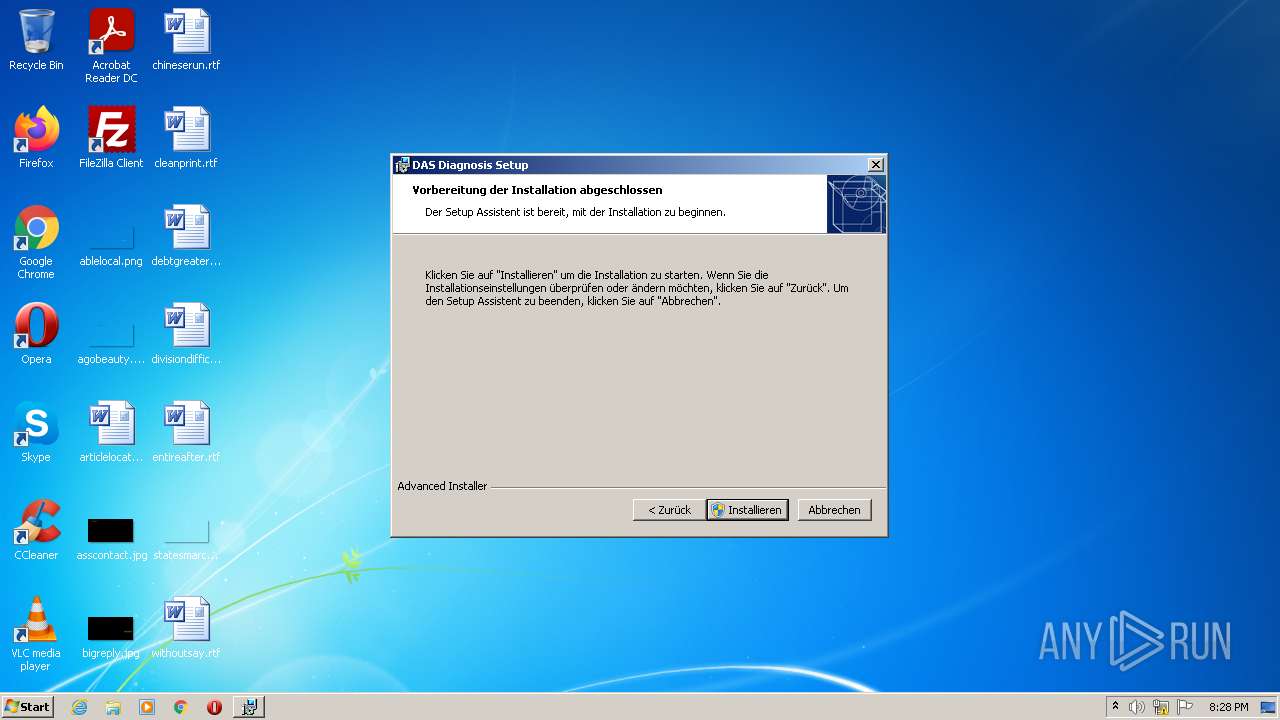
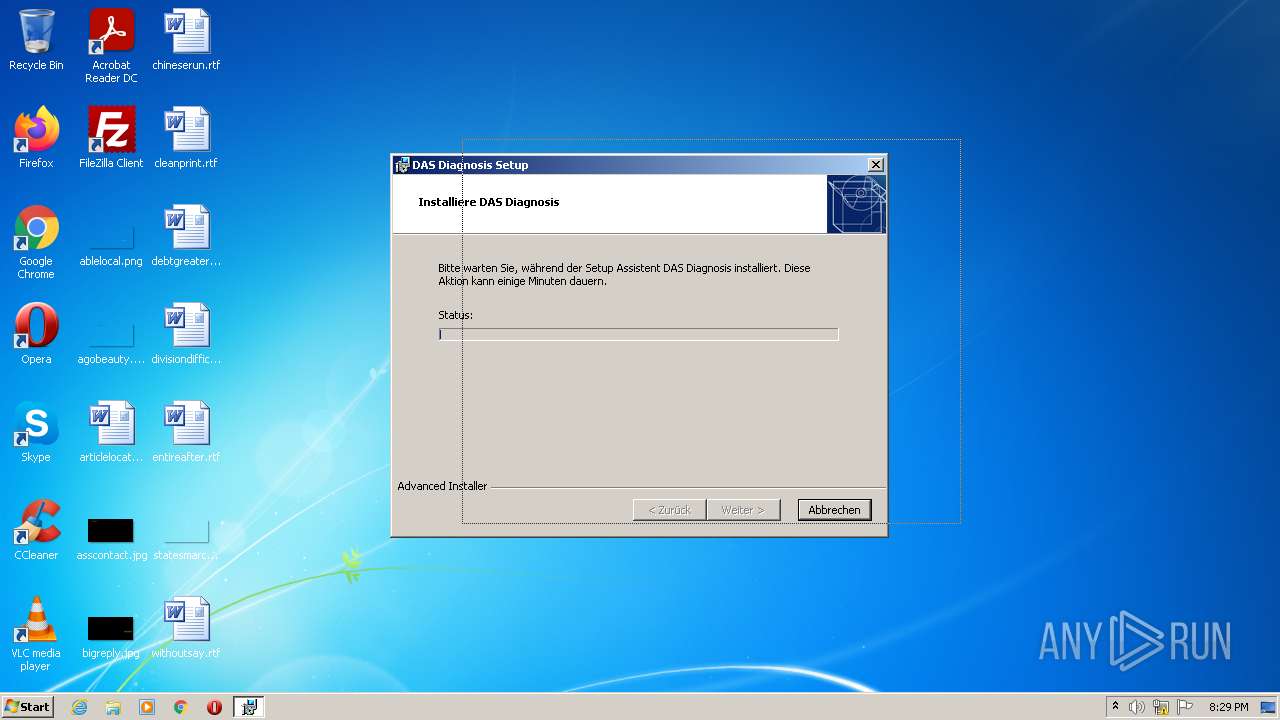
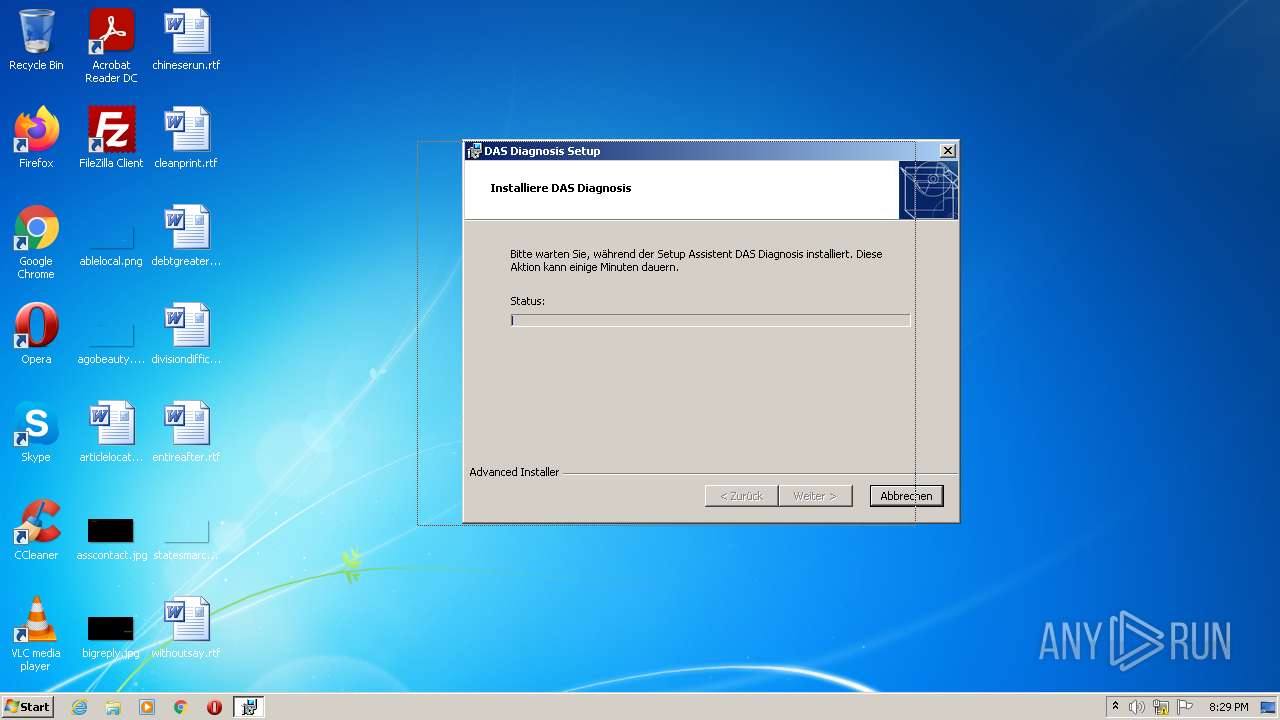
| File name: | Full Fix-Xentry 2022.exe |
| Full analysis: | https://app.any.run/tasks/d132b62d-deb2-4eda-bb15-f6c3952aa95b |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 19:27:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 2C0FA6E8C0EBF78FC7875495D907C5C0 |
| SHA1: | F50A542E49AD33B1A59C5223148B221CED62BC2C |
| SHA256: | 219FB6AF7DA3A7E932A36FFCE9AD67FFF9B4E4AEE3D624514DDE36092E449CDF |
| SSDEEP: | 393216:WKHx59nxhEzDrGNgj1j03Iqf7jAO/cKrn9vC5o:WWtUvGNgR04qf/pncC |
MALICIOUS
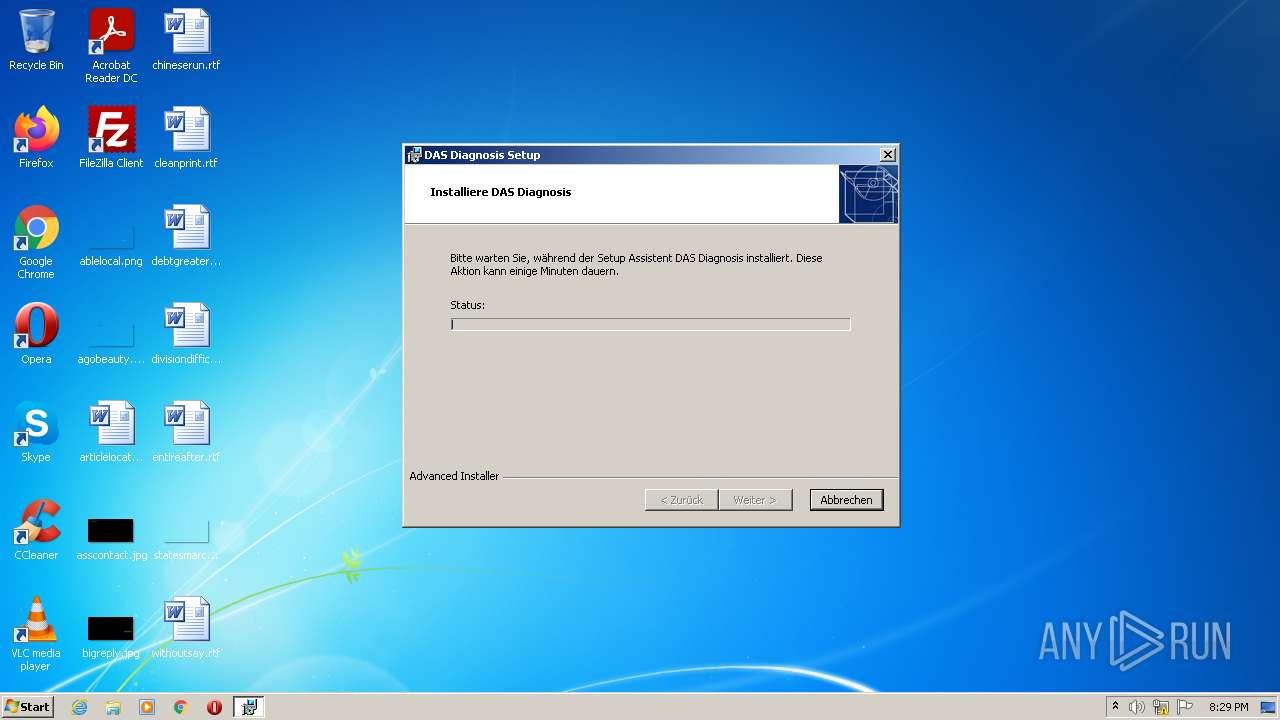
Drops executable file immediately after starts
- Full Fix-Xentry 2022.exe (PID: 1180)
- full fix-xentry 2022.exe (PID: 3652)
- msiexec.exe (PID: 2840)
- msiexec.exe (PID: 280)
- DAS32R2sd.exe (PID: 2084)
- start_Xentry.exe (PID: 1152)
Application was dropped or rewritten from another process
- full fix-xentry 2022.exe (PID: 3652)
Changes AppInit_DLLs value (autorun option)
- msiexec.exe (PID: 280)
Loads the Task Scheduler COM API
- full fix-xentry 2022.exe (PID: 3652)
SUSPICIOUS
Reads the computer name
- Full Fix-Xentry 2022.exe (PID: 1180)
- full fix-xentry 2022.exe (PID: 3652)
- icsys.icn.exe (PID: 3856)
- msiexec.exe (PID: 280)
- MsiExec.exe (PID: 2540)
- MsiExec.exe (PID: 3152)
- MsiExec.exe (PID: 2224)
- icsys.icn.exe (PID: 3660)
- DAS32R2sd.exe (PID: 2084)
- start_Xentry.exe (PID: 1152)
- icsys.icn.exe (PID: 2544)
Checks supported languages
- Full Fix-Xentry 2022.exe (PID: 1180)
- full fix-xentry 2022.exe (PID: 3652)
- icsys.icn.exe (PID: 3856)
- msiexec.exe (PID: 280)
- MsiExec.exe (PID: 3152)
- MsiExec.exe (PID: 2540)
- MsiExec.exe (PID: 2224)
- icsys.icn.exe (PID: 3660)
- cmd.exe (PID: 4032)
- DAS32R2sd.exe (PID: 2084)
- start_Xentry.exe (PID: 1152)
- icsys.icn.exe (PID: 2544)
- start_xentry.exe (PID: 2952)
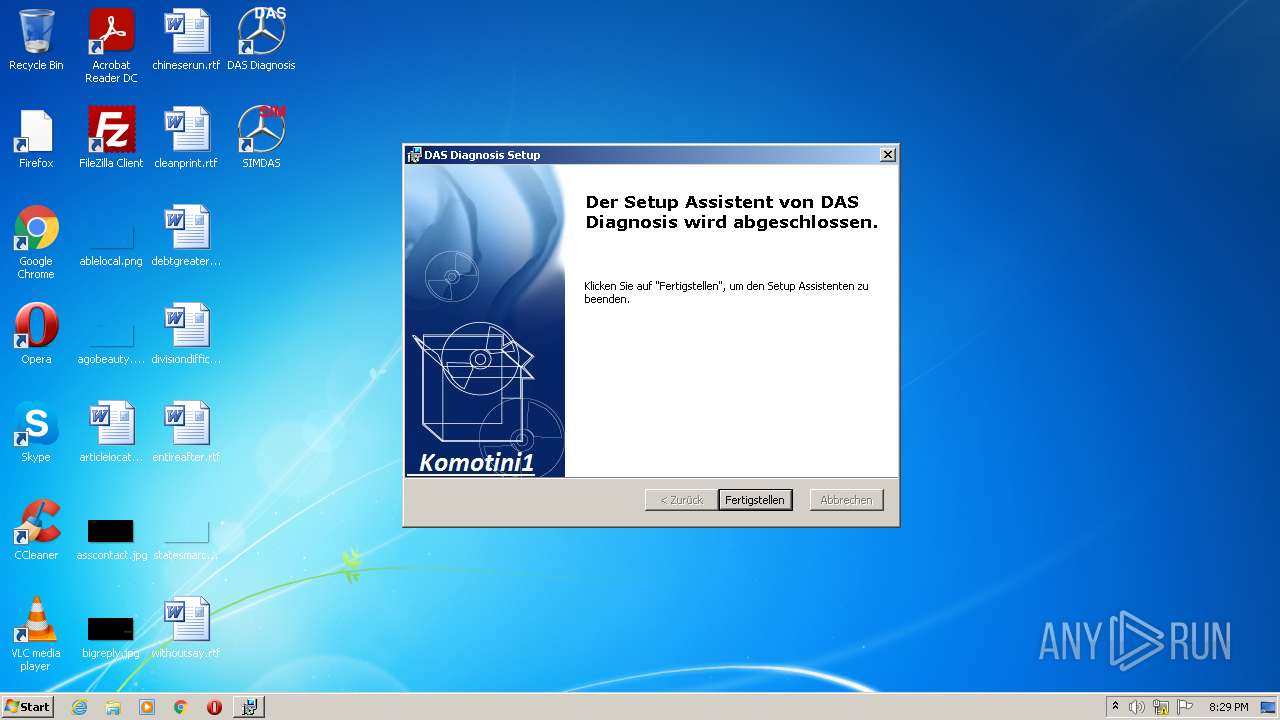
Starts application with an unusual extension
- Full Fix-Xentry 2022.exe (PID: 1180)
- DAS32R2sd.exe (PID: 2084)
- start_Xentry.exe (PID: 1152)
Starts itself from another location
- Full Fix-Xentry 2022.exe (PID: 1180)
- DAS32R2sd.exe (PID: 2084)
- start_Xentry.exe (PID: 1152)
Executable content was dropped or overwritten
- Full Fix-Xentry 2022.exe (PID: 1180)
- full fix-xentry 2022.exe (PID: 3652)
- msiexec.exe (PID: 2840)
- msiexec.exe (PID: 280)
- DAS32R2sd.exe (PID: 2084)
- start_Xentry.exe (PID: 1152)
Drops a file with a compile date too recent
- Full Fix-Xentry 2022.exe (PID: 1180)
- msiexec.exe (PID: 2840)
- full fix-xentry 2022.exe (PID: 3652)
- msiexec.exe (PID: 280)
- DAS32R2sd.exe (PID: 2084)
- start_Xentry.exe (PID: 1152)
Reads Environment values
- full fix-xentry 2022.exe (PID: 3652)
- vssvc.exe (PID: 3772)
Creates files in the user directory
- full fix-xentry 2022.exe (PID: 3652)
- MsiExec.exe (PID: 3152)
Reads Windows owner or organization settings
- full fix-xentry 2022.exe (PID: 3652)
- msiexec.exe (PID: 2840)
- msiexec.exe (PID: 280)
Reads the Windows organization settings
- full fix-xentry 2022.exe (PID: 3652)
- msiexec.exe (PID: 2840)
- msiexec.exe (PID: 280)
Starts Microsoft Installer
- full fix-xentry 2022.exe (PID: 3652)
Executed as Windows Service
- vssvc.exe (PID: 3772)
Creates files in the Windows directory
- msiexec.exe (PID: 280)
Creates a directory in Program Files
- msiexec.exe (PID: 280)
Changes the desktop background image
- msiexec.exe (PID: 280)
Creates files in the program directory
- DAS32R2sd.exe (PID: 2084)
- start_Xentry.exe (PID: 1152)
INFO
Application launched itself
- msiexec.exe (PID: 280)
Reads the computer name
- msiexec.exe (PID: 2840)
- vssvc.exe (PID: 3772)
- explorer.exe (PID: 3696)
Checks supported languages
- msiexec.exe (PID: 2840)
- vssvc.exe (PID: 3772)
- explorer.exe (PID: 3696)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2540)
- MsiExec.exe (PID: 3152)
- MsiExec.exe (PID: 2224)
Creates a software uninstall entry
- msiexec.exe (PID: 280)
Manual execution by user
- cmd.exe (PID: 4032)
- explorer.exe (PID: 3696)
- DAS32R2sd.exe (PID: 2084)
- start_Xentry.exe (PID: 1152)
Creates files in the program directory
- msiexec.exe (PID: 280)
Searches for installed software
- msiexec.exe (PID: 280)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Microsoft Visual Basic 6 (26.5) |
|---|---|---|
| .exe | | | InstallShield setup (13.9) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (10) |
| .exe | | | Win64 Executable (generic) (8.9) |
EXIF
EXE
| OriginalFileName: | Win.exe |
|---|---|
| InternalName: | Win |
| ProductVersion: | 1 |
| FileVersion: | 1 |
| ProductName: | Win |
| CompanyName: | Microsoft |
| CharacterSet: | Unicode |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x0000 |
| ProductVersionNumber: | 1.0.0.0 |
| FileVersionNumber: | 1.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | 1 |
| OSVersion: | 4 |
| EntryPoint: | 0x3670 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 12288 |
| CodeSize: | 176128 |
| LinkerVersion: | 6 |
| PEType: | PE32 |
| TimeStamp: | 2011:06:14 21:01:16+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 14-Jun-2011 19:01:16 |
| Detected languages: |
|
| CompanyName: | Microsoft |
| ProductName: | Win |
| FileVersion: | 1.00 |
| ProductVersion: | 1.00 |
| InternalName: | Win |
| OriginalFilename: | Win.exe |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000B8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 14-Jun-2011 19:01:16 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0002A728 | 0x0002B000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.9472 |
.data | 0x0002C000 | 0x00001B74 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x0002E000 | 0x00001000 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.95655 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.12197 | 500 | Unicode (UTF 16LE) | English - United States | RT_VERSION |
30001 | 3.78952 | 3280 | Unicode (UTF 16LE) | UNKNOWN | RT_ICON |
Imports
MSVBVM60.DLL |
Total processes
59
Monitored processes
17
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
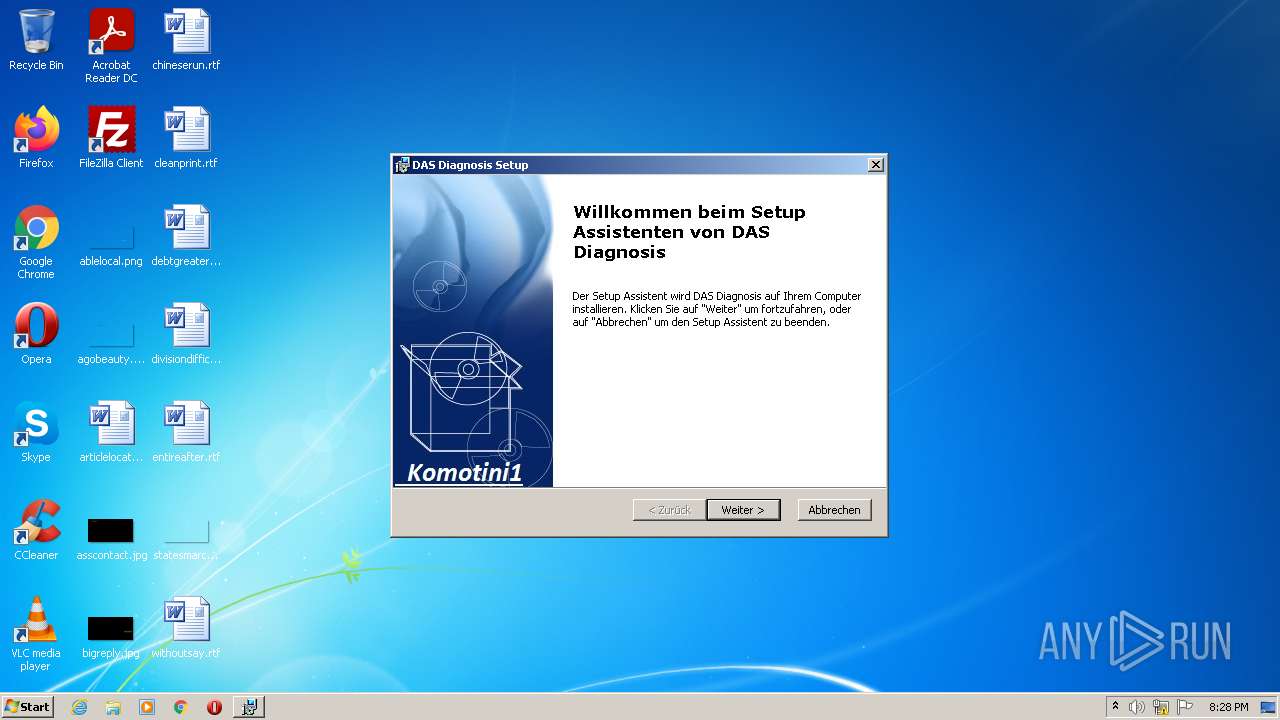
| 1152 | "C:\Program Files\Mercedes-Benz\Xentry\XD_MB\start_Xentry.exe" | C:\Program Files\Mercedes-Benz\Xentry\XD_MB\start_Xentry.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1180 | "C:\Users\admin\AppData\Local\Temp\Full Fix-Xentry 2022.exe" | C:\Users\admin\AppData\Local\Temp\Full Fix-Xentry 2022.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2084 | "C:\Program Files\Mercedes-Benz\DAS\bin\DAS32R2sd.exe" | C:\Program Files\Mercedes-Benz\DAS\bin\DAS32R2sd.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2224 | C:\Windows\system32\MsiExec.exe -Embedding 33A40B2463A4B1524791D1A7DD5DD052 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2444 | "c:\program files\mercedes-benz\das\bin\das32r2sd.exe " | c:\program files\mercedes-benz\das\bin\das32r2sd.exe | — | DAS32R2sd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3222601730 Modules
| |||||||||||||||
| 2540 | C:\Windows\system32\MsiExec.exe -Embedding 0E713C331C178500594EF2386C4D8CA7 C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2544 | C:\Users\admin\AppData\Local\icsys.icn.exe | C:\Users\admin\AppData\Local\icsys.icn.exe | — | start_Xentry.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2840 | "C:\Windows\system32\msiexec.exe" /i "C:\Users\admin\AppData\Roaming\Mercedes\DAS Diagnosis 2022\install\Full Fix-Xentry 2022.msi" AI_SETUPEXEPATH="c:\users\admin\appdata\local\temp\full fix-xentry 2022.exe " SETUPEXEDIR=c:\users\admin\appdata\local\temp\ EXE_CMD_LINE="/exenoupdates /forcecleanup /wintime 1653073835 " ALLUSERS="1" | C:\Windows\system32\msiexec.exe | full fix-xentry 2022.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2952 | "c:\program files\mercedes-benz\xentry\xd_mb\start_xentry.exe " | c:\program files\mercedes-benz\xentry\xd_mb\start_xentry.exe | — | start_Xentry.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2148734720 Modules
| |||||||||||||||
Total events
5 044
Read events
4 710
Write events
321
Delete events
13
Modification events
| (PID) Process: | (1180) Full Fix-Xentry 2022.exe | Key: | HKEY_CURRENT_USER\Software\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (3856) icsys.icn.exe | Key: | HKEY_CURRENT_USER\Software\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (280) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000002E4EA2D97F6CD801180100009C0D0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (280) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 40000000000000002E4EA2D97F6CD801180100009C0D0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (280) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 69 | |||
| (PID) Process: | (280) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000004CD308DA7F6CD801180100009C0D0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (280) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000004CD308DA7F6CD8011801000060070000E8030000010000000000000000000000EAAD8CCCA784DF4380F1853D1694A7EA0000000000000000 | |||
| (PID) Process: | (3772) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000001CE61BDA7F6CD801BC0E000068080000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3772) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000001CE61BDA7F6CD801BC0E0000BC0D0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3772) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000001CE61BDA7F6CD801BC0E000008090000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
31
Suspicious files
17
Text files
33
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3652 | full fix-xentry 2022.exe | C:\Users\admin\AppData\Roaming\Mercedes\DAS Diagnosis 2022\install\holder0.aiph | — | |
MD5:— | SHA256:— | |||
| 280 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3652 | full fix-xentry 2022.exe | C:\Users\admin\AppData\Roaming\Mercedes\DAS Diagnosis 2022\install\Full Fix-Xentry 2022.x64.msi | executable | |
MD5:— | SHA256:— | |||
| 3652 | full fix-xentry 2022.exe | C:\Users\admin\AppData\Roaming\Mercedes\DAS Diagnosis 2022\install\Full Fix-Xentry 20221.cab | — | |
MD5:— | SHA256:— | |||
| 3652 | full fix-xentry 2022.exe | C:\Users\admin\AppData\Roaming\Mercedes\DAS Diagnosis 2022\install\Full Fix-Xentry 2022.msi | executable | |
MD5:— | SHA256:— | |||
| 2840 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIC03A.tmp | executable | |
MD5:— | SHA256:— | |||
| 280 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{cc8cadea-84a7-43df-80f1-853d1694a7ea}_OnDiskSnapshotProp | binary | |
MD5:— | SHA256:— | |||
| 280 | msiexec.exe | C:\Windows\Installer\10e997.msi | executable | |
MD5:— | SHA256:— | |||
| 280 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:— | SHA256:— | |||
| 1180 | Full Fix-Xentry 2022.exe | C:\Users\admin\AppData\Local\icsys.icn.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report