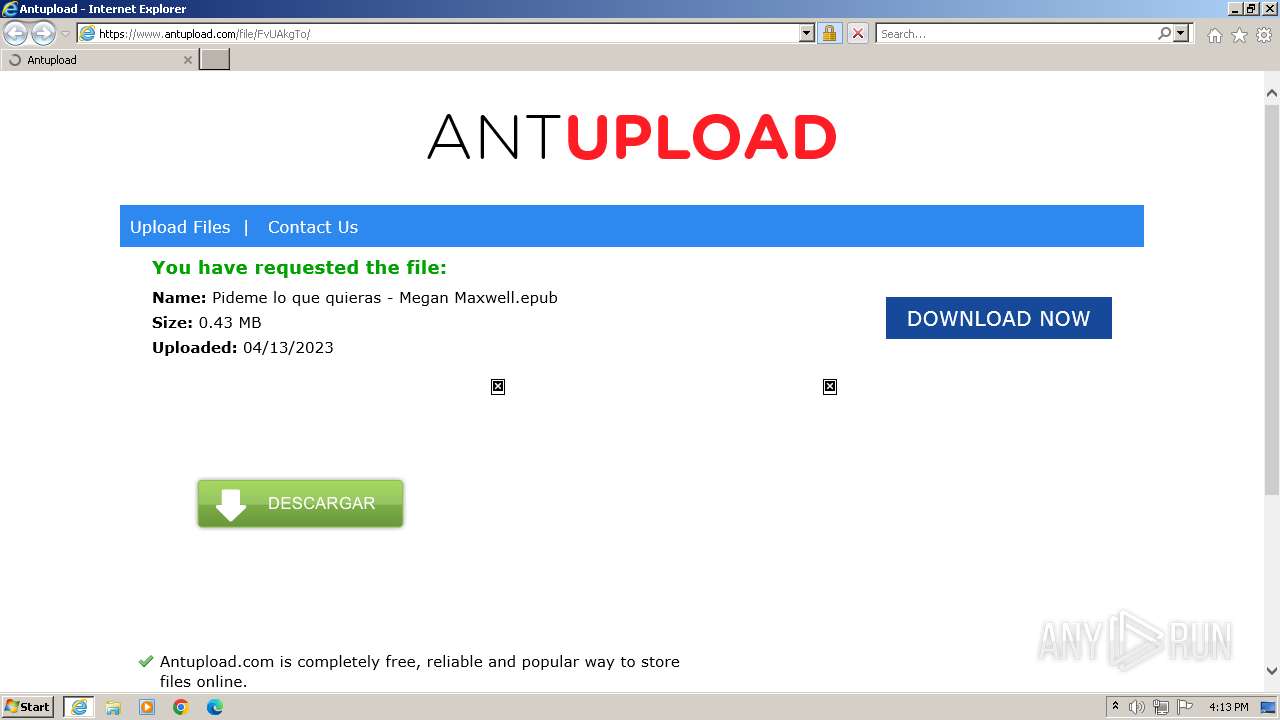
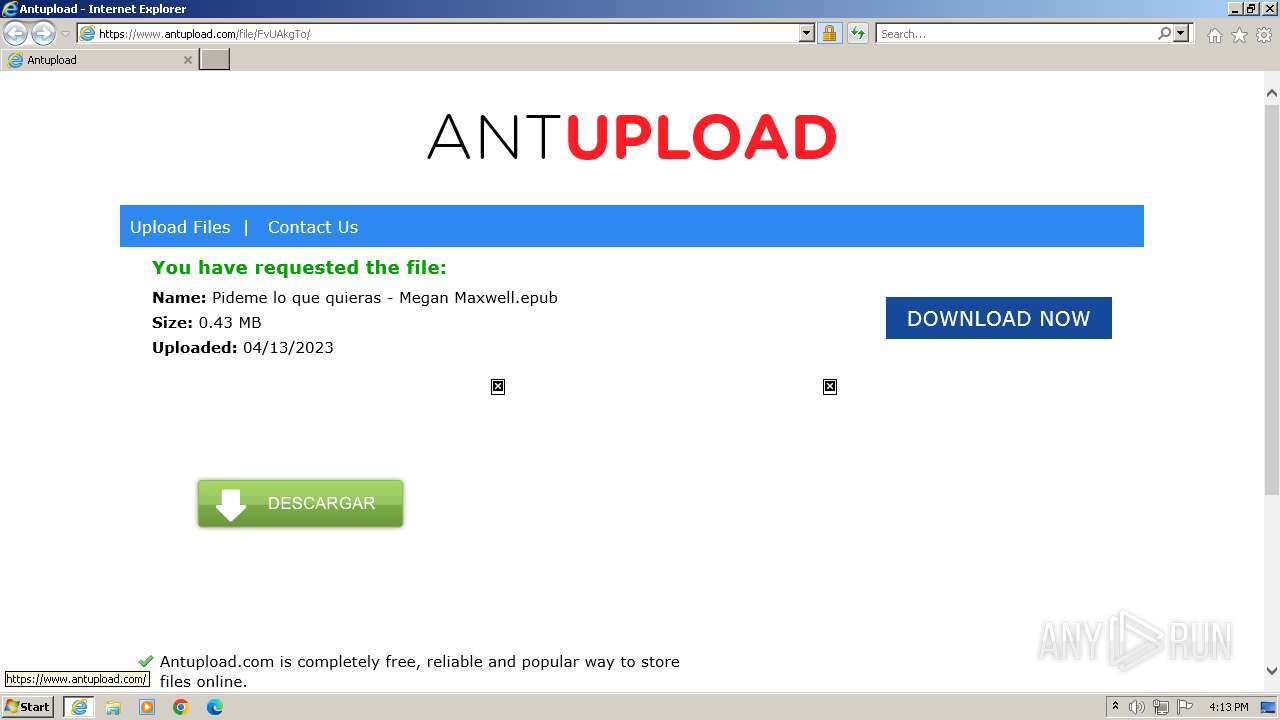
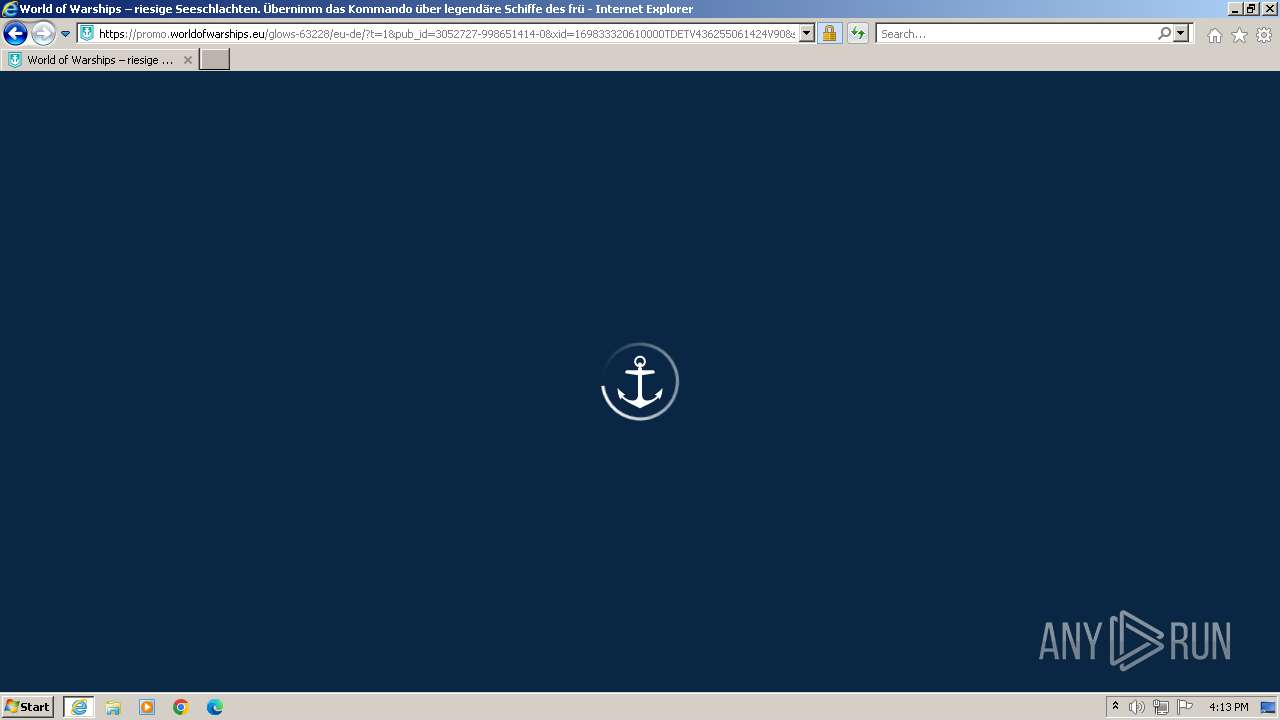
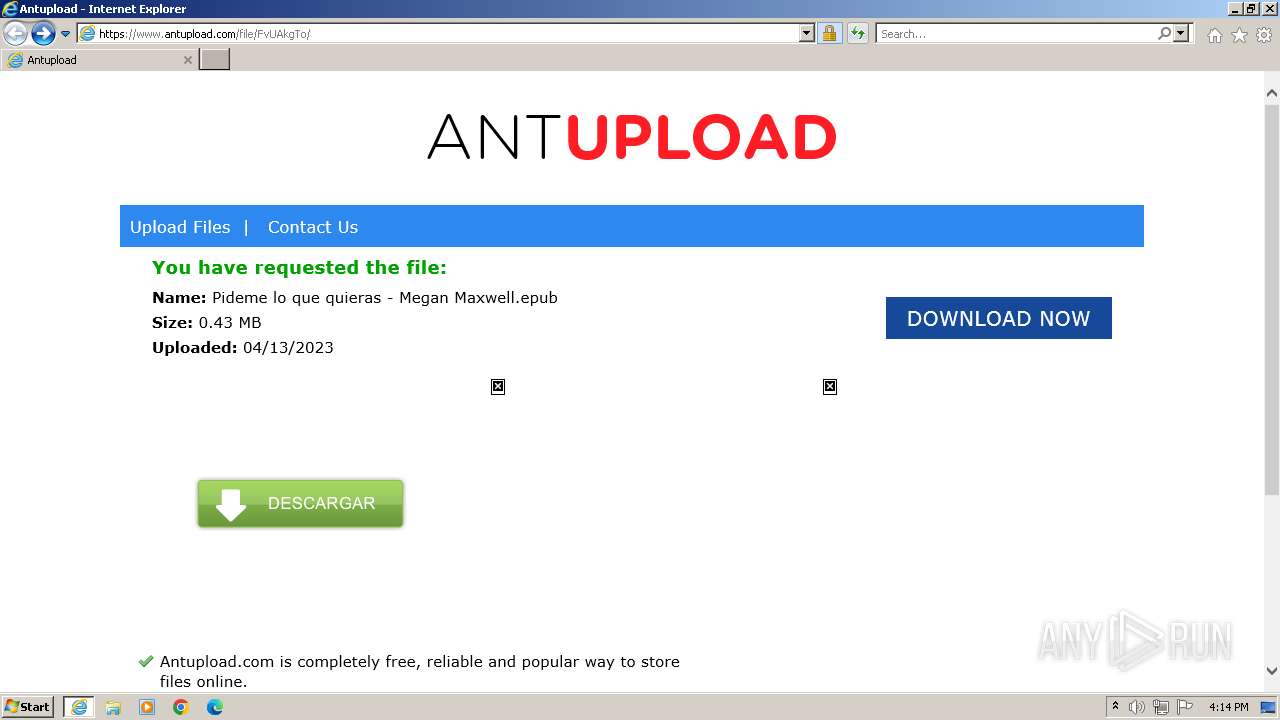
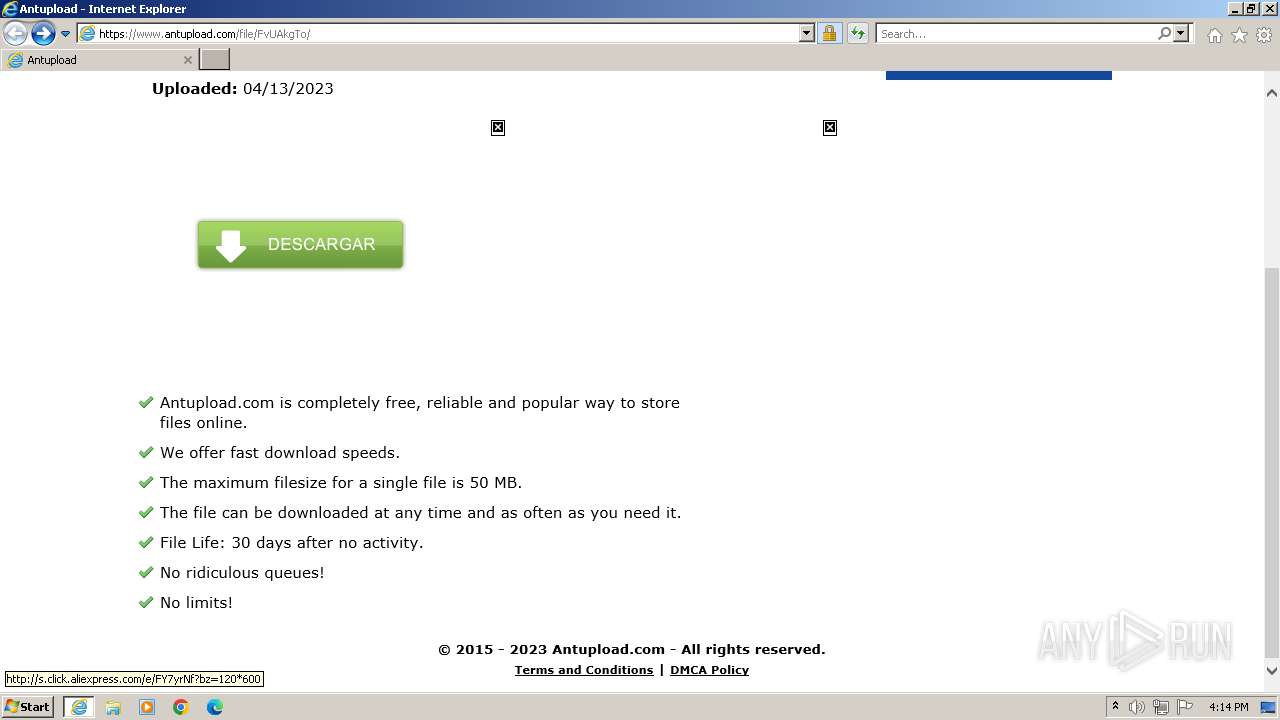
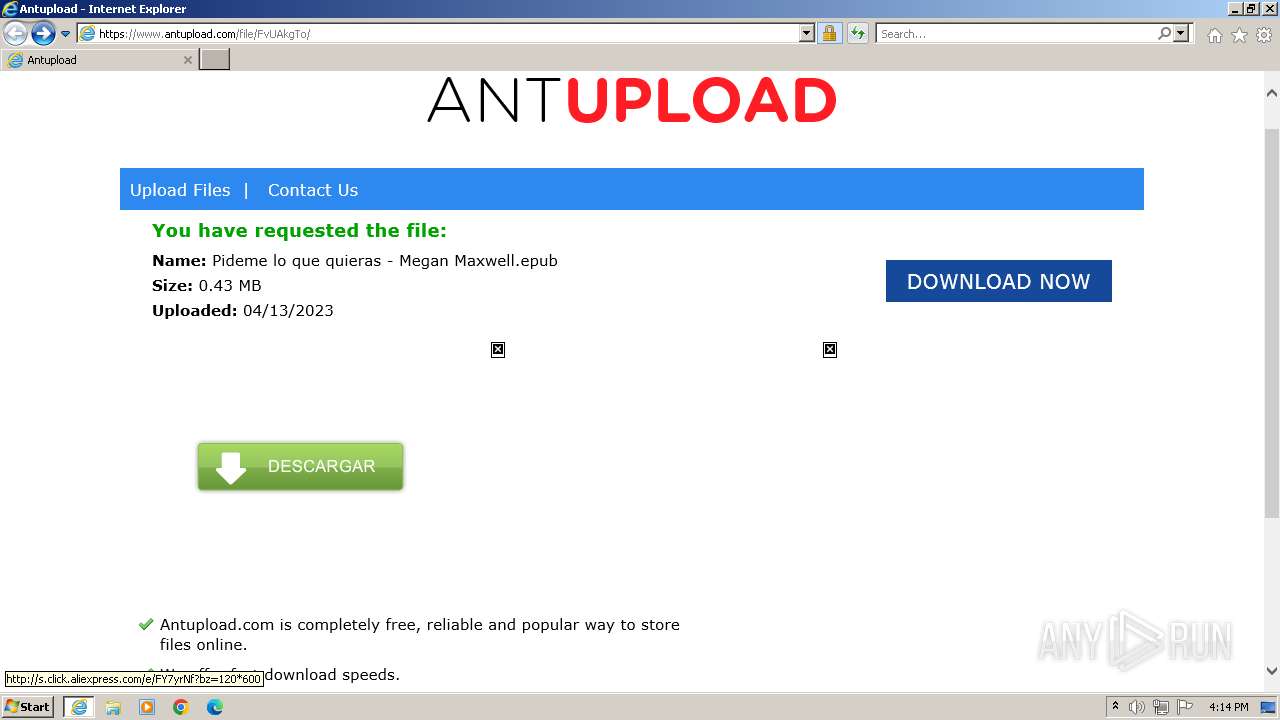
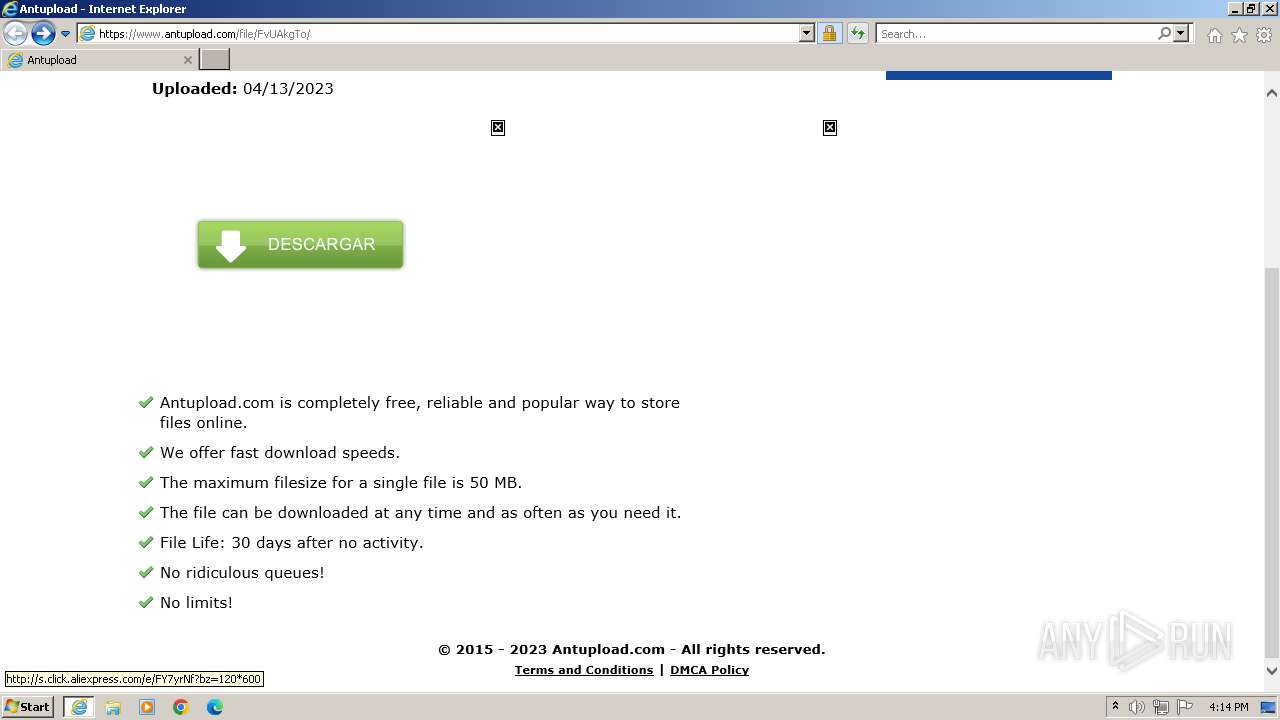
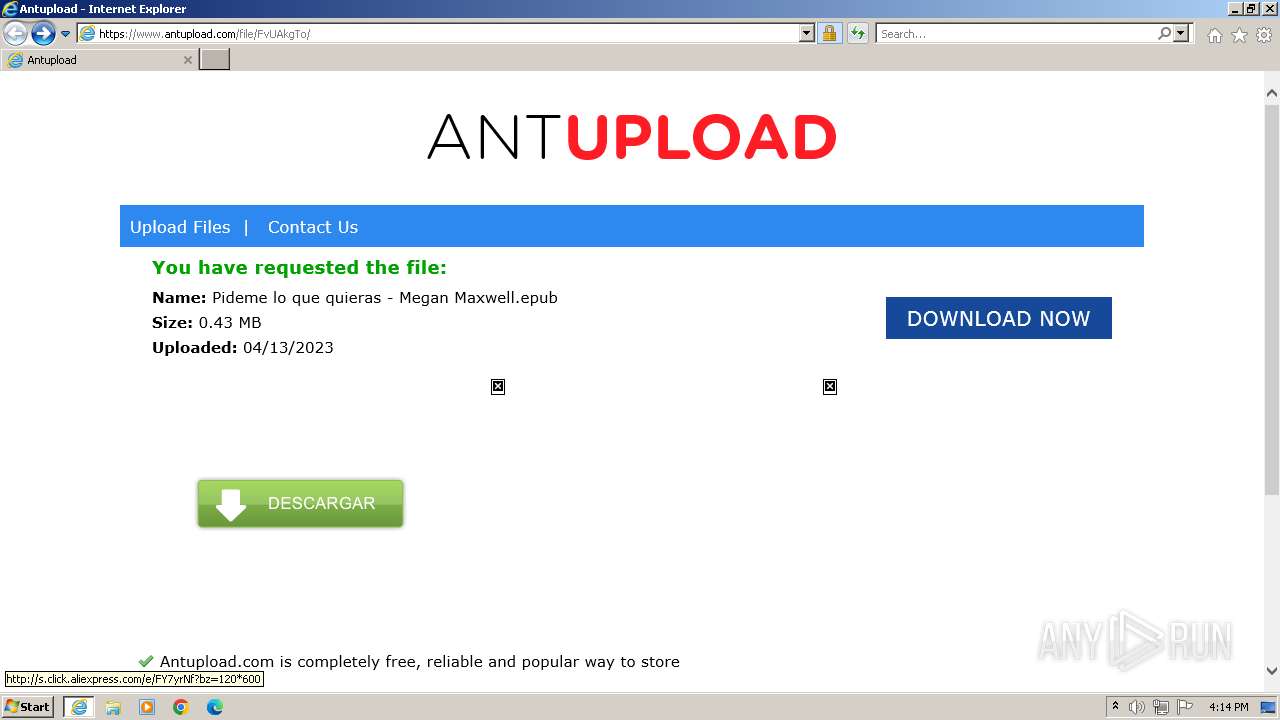
| URL: | https://www.antupload.com/file/FvUAkgTo/ |
| Full analysis: | https://app.any.run/tasks/7ffb5fa2-2dc0-4d85-a580-44a65cb7e5f0 |
| Verdict: | Malicious activity |
| Analysis date: | October 26, 2023, 15:13:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | AB9E7722458E9D2588DBF726C2059FC509C59CE3 |
| SHA256: | 219CE9C9E050FF62AC24DAE5A6D82EF7B59A3BF128B8E819D02980D8EBE8B63B |
| SSDEEP: | 3:N8DSL/UXokOCLn:2OLspOCL |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 2472)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2472 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.antupload.com/file/FvUAkgTo/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3232 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2472 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3872 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2472 CREDAT:2823469 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
27 951
Read events
27 869
Write events
80
Delete events
2
Modification events
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
77
Text files
107
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:DC739507643AA6DB92E8707E33DF0E03 | SHA256:4AF827349042911D4244C17C49F42D5B9DD30AFA6F1147966BF9D0877E59CFFF | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:7C12D5154509EF4DF59444AE869985FA | SHA256:4D3603D227FC262350823BB17E44F489E1EC3B7910B0F8EE0DA44B49021BAAA7 | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:95F9817D1BFA9274F67A2788E6C4FA93 | SHA256:B4BB3382BD0323147BDCC991420610465AD4F8CB49FA660F7E1A6D3DBD05D5F3 | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:57A8DD92CC60C00E586B768355B071EF | SHA256:99EF3B8F84C4D6E454B1FFCA0212EED5B5B71E2544E7DAE1E9E25C17E43AE076 | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\main[1].css | text | |
MD5:FE548D728561608402B6C503DA990670 | SHA256:73CC9DB5646C5D2996A2D7BA96084A25B33C6A6C4F8FA61813FEBEC968A871FA | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\normalize[1].css | text | |
MD5:F54EE73AC4013E166A57781B01A08F10 | SHA256:0BAA2625178BC5EBC538F20E295742058EFC73CBB6E517717D6BFA4CE6CC820E | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\descarga[1].jpg | image | |
MD5:28B83AACEF70072E18D61079E7EB6349 | SHA256:C1E0B19563A3B9A614DBE89B0E1283B4B3C93E836ADCF29644883F38ADFA8FDC | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\FvUAkgTo[1].htm | html | |
MD5:156C01F9310AA954E24690BC0318BDDD | SHA256:3EEADF7D39845ED1567E82BE27ABD5DF3DB64F9A63875D4CFAEB3D1552114C91 | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\main[1].js | text | |
MD5:0571B81662126FF590A0171B9E8D484F | SHA256:B17335606AE04B68820B177DF969A930200FD985742754293D98E7C99CFC658C | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\G5GVFMXN.txt | text | |
MD5:3CDC0C7587D5C862076B4ABF069623FA | SHA256:BD15CCD3C651B954FFB449F1B1313CD7460225DA8367B0921D247EC31C126469 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
110
DNS requests
51
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3232 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
3232 | iexplore.exe | GET | 200 | 67.27.159.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?b8865199ad6826af | unknown | compressed | 61.6 Kb | unknown |
3232 | iexplore.exe | GET | 200 | 67.27.159.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e56ecb57428c0960 | unknown | compressed | 61.6 Kb | unknown |
2472 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
3232 | iexplore.exe | GET | 200 | 23.212.210.158:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3232 | iexplore.exe | GET | 200 | 23.212.210.158:80 | http://x2.c.lencr.org/ | unknown | binary | 300 b | unknown |
3232 | iexplore.exe | GET | 200 | 67.27.159.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ab121734c4c30a79 | unknown | compressed | 4.66 Kb | unknown |
3232 | iexplore.exe | GET | 200 | 67.27.159.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ab9eb2291d8ac70b | unknown | compressed | 4.66 Kb | unknown |
3232 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3232 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEAp7mVqqBJlqgugcXJUsNZo%3D | unknown | der | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3232 | iexplore.exe | 67.27.159.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | malicious |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3232 | iexplore.exe | 142.250.185.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3232 | iexplore.exe | 188.114.97.3:443 | www.ejdr22.com | CLOUDFLARENET | NL | unknown |
3232 | iexplore.exe | 47.246.48.251:443 | ae01.alicdn.com | Zhejiang Taobao Network Co.,Ltd | NL | unknown |
3232 | iexplore.exe | 151.101.2.133:80 | ocsp.globalsign.com | FASTLY | US | unknown |
3232 | iexplore.exe | 104.20.9.31:443 | s10.histats.com | CLOUDFLARENET | — | unknown |
3232 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ae01.alicdn.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
s10.histats.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
s4.histats.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |