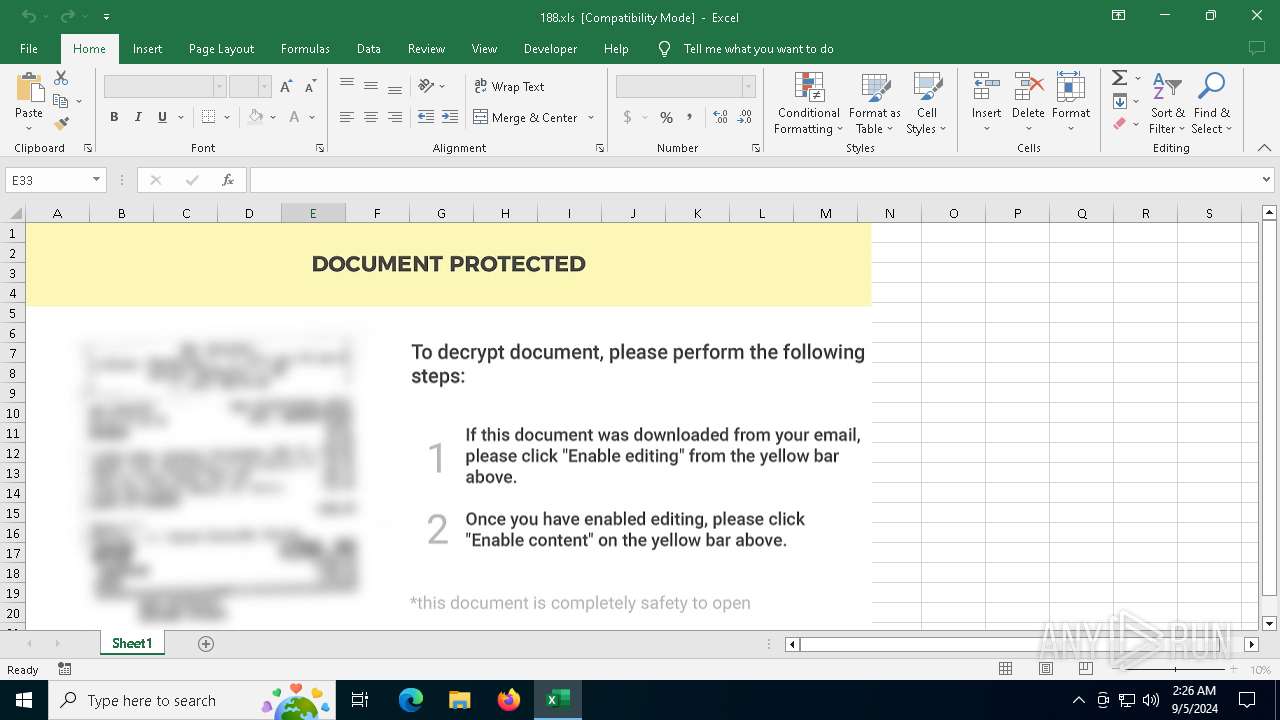
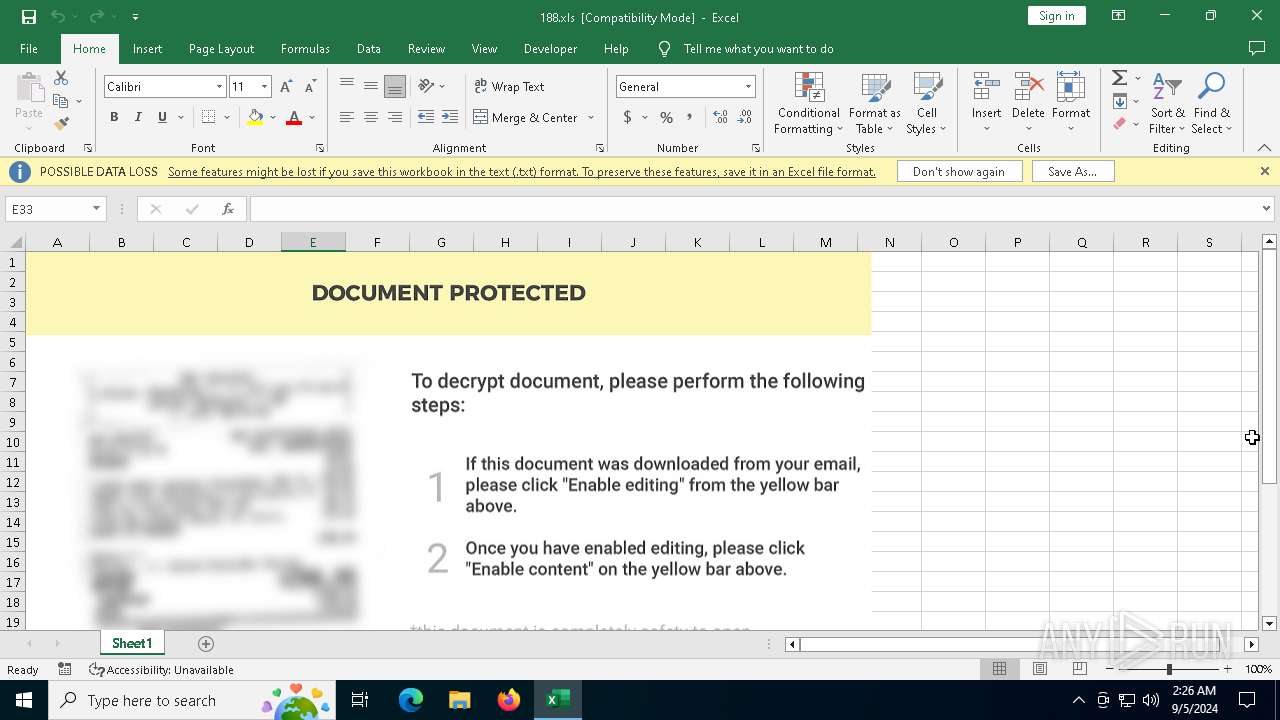
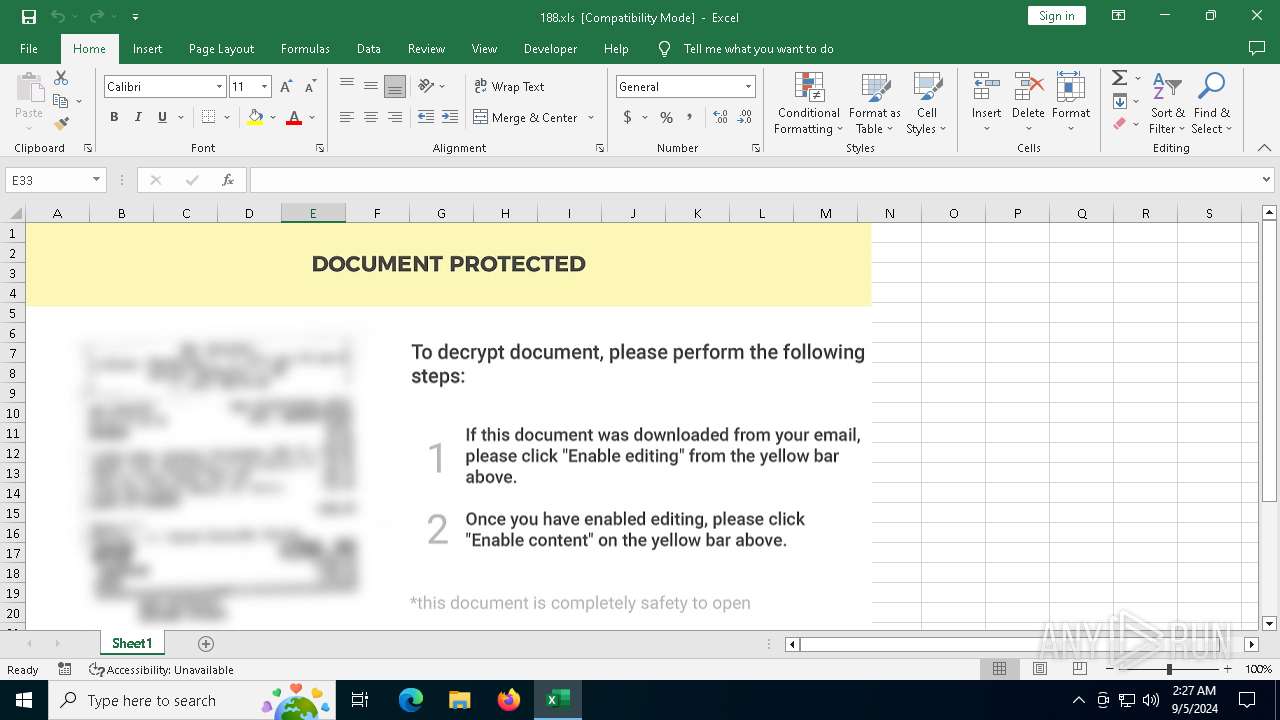
| File name: | sample01.xls |
| Full analysis: | https://app.any.run/tasks/f13027ea-80d9-475c-a0ca-ff3937abd73d |
| Verdict: | Malicious activity |
| Analysis date: | September 05, 2024, 02:26:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | CDFV2 Microsoft Excel |
| MD5: | 81EE2ACBD483C6B6F45519B3DB68A11B |
| SHA1: | D37D2BA6E5CD78D5DA1183FD0DCE8C1E71D91547 |
| SHA256: | 218FAA25C16A291BE863A226F12DF6B91E152189029ACA0439B357BB10FDB320 |
| SSDEEP: | 3072:1KZ55TxH4sz2F/HrkU/C5wKBAVVaXch6KORNogf:4Z55T54sgIEC5wK8cMMKO |
MALICIOUS
Calls Win API functions (MACROS)
- EXCEL.EXE (PID: 6920)
Uses sleep, probably for evasion (MACROS)
- EXCEL.EXE (PID: 6920)
Unusual execution from MS Office
- EXCEL.EXE (PID: 6920)
SUSPICIOUS
Writes data into a file (MACROS)
- EXCEL.EXE (PID: 6920)
Opens a file (MACROS)
- EXCEL.EXE (PID: 6920)
Reads data from a file (MACROS)
- EXCEL.EXE (PID: 6920)
Likely accesses (executes) a file from the Public directory
- certutil.exe (PID: 6664)
- certutil.exe (PID: 7056)
- rundll32.exe (PID: 2612)
- rundll32.exe (PID: 236)
Decoding a file from Base64 using CertUtil
- EXCEL.EXE (PID: 6920)
Executable content was dropped or overwritten
- certutil.exe (PID: 7056)
Uses RUNDLL32.EXE to load library
- EXCEL.EXE (PID: 6920)
INFO
The process uses the downloaded file
- EXCEL.EXE (PID: 6920)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 236)
Checks proxy server information
- rundll32.exe (PID: 236)
Creates files in the program directory
- rundll32.exe (PID: 236)
Reads the software policy settings
- slui.exe (PID: 2016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| CompObjUserTypeLen: | 31 |
|---|---|
| CompObjUserType: | Microsoft Excel 2003 Worksheet |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
Total processes
142
Monitored processes
10
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Windows\System32\rundll32.exe" C:\Users\Public\188.dll,D | C:\Windows\SysWOW64\rundll32.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2016 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2612 | "C:\Windows\System32\rundll32.exe" C:\Users\Public\188.dll,D | C:\Windows\System32\rundll32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4076 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4284 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4760 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6596 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6664 | "C:\Windows\System32\certutil.exe" -decode C:\Users\Public\188.txt C:\Users\Public\188a.txt | C:\Windows\System32\certutil.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6920 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" C:\Users\admin\AppData\Local\Temp\sample01.xls | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7056 | "C:\Windows\System32\certutil.exe" -decodehex C:\Users\Public\188a.txt C:\Users\Public\188.dll | C:\Windows\System32\certutil.exe | EXCEL.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 095
Read events
7 802
Write events
261
Delete events
32
Modification events
| (PID) Process: | (6920) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (6920) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\EXCEL\6920 |
| Operation: | write | Name: | 0 |
Value: 0B0E10DB5BAD1F316B014BA184585A4741B3D0230046CBDBDA87B0E7BFED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5118836D2120965007800630065006C002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6920) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6920) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6920) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6920) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6920) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6920) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6920) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6920) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
2
Suspicious files
18
Text files
5
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6920 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:2C99AA5C647C8D46FBDA855D550FA755 | SHA256:FB72BE57AC222EFE89EB4C39C2E124DC4B816A4F77418B99449C6B77F4D08322 | |||
| 6920 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\B3A427C0-78A1-4833-AC94-89CB7CC0E004 | xml | |
MD5:A944073836C2AD4A6F346008E309FC88 | SHA256:6C8FA05C5A187AF7C4D0151AD5566D7057CB2CC7DEA85659EF62947D757FF836 | |||
| 7056 | certutil.exe | C:\Users\Public\188.dll | executable | |
MD5:B4164149FFC43C2BF55CB66922E738B0 | SHA256:800E1192E5EC3D2D9B17A3E2D8996CADBDD96AC6D8C59DFCF989264A956EB8D4 | |||
| 6920 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\188.txt.LNK | lnk | |
MD5:29FAEFB1DDD2AC4BF30F7AF332C77104 | SHA256:E439442F55AFD710892DB5F1028059F7E25A16003BC3EBC305DEE247F7C9BAD4 | |||
| 6920 | EXCEL.EXE | C:\Users\Public\188.txt | text | |
MD5:E84023EBFD146132098F192D8B537C3E | SHA256:6165F068F3D5FC8E9800B6C1AD7009CDD543A9044729FD5A0AD9D2450F84AAC4 | |||
| 6920 | EXCEL.EXE | C:\Users\Public\188.xls | text | |
MD5:BEA07E6D2B8DCE396FE21BAA61B34956 | SHA256:2E08D1F6000AEF541797D008C05AC36F4DBEBFB36CBAC5615788E6FCC5B300A7 | |||
| 6920 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:F941393F843D35A68345EF028C5FC475 | SHA256:FAF69A3FADCCC8304A0D416FCD995C5F63B6D8C10C026C0BA7EECFC478BF6B3D | |||
| 6920 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:072118D932ACA5DE1245CB59AC8850BF | SHA256:6CD5D3ADA360B0B8CF46F95B5A186C8AF555F93361DB2B62F966CD0B3089DF78 | |||
| 6920 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DFAF15E00377AB8436.TMP | binary | |
MD5:FF06A2E5876E0EE857D265FCD3C940F5 | SHA256:C032BBAEB4609DFF41DA7C5CB047205E775533E8E36A7BA9C1B9858383227CDD | |||
| 6920 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\188.xls.LNK | lnk | |
MD5:4D90D7314D0DEB5D8A2FBF433766BF9C | SHA256:4D1AC302B5A60B3AE9063D37918DD6375BB9882A8DDBFA2274F4CBD5F669B41A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
40
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4132 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6920 | EXCEL.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1764 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6320 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4132 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4132 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4132 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6920 | EXCEL.EXE | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6920 | EXCEL.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6920 | EXCEL.EXE | 52.111.243.31:443 | nexusrules.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6920 | EXCEL.EXE | 184.28.90.27:443 | fs.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
messaging.engagement.office.com |
| whitelisted |
login.live.com |
| whitelisted |