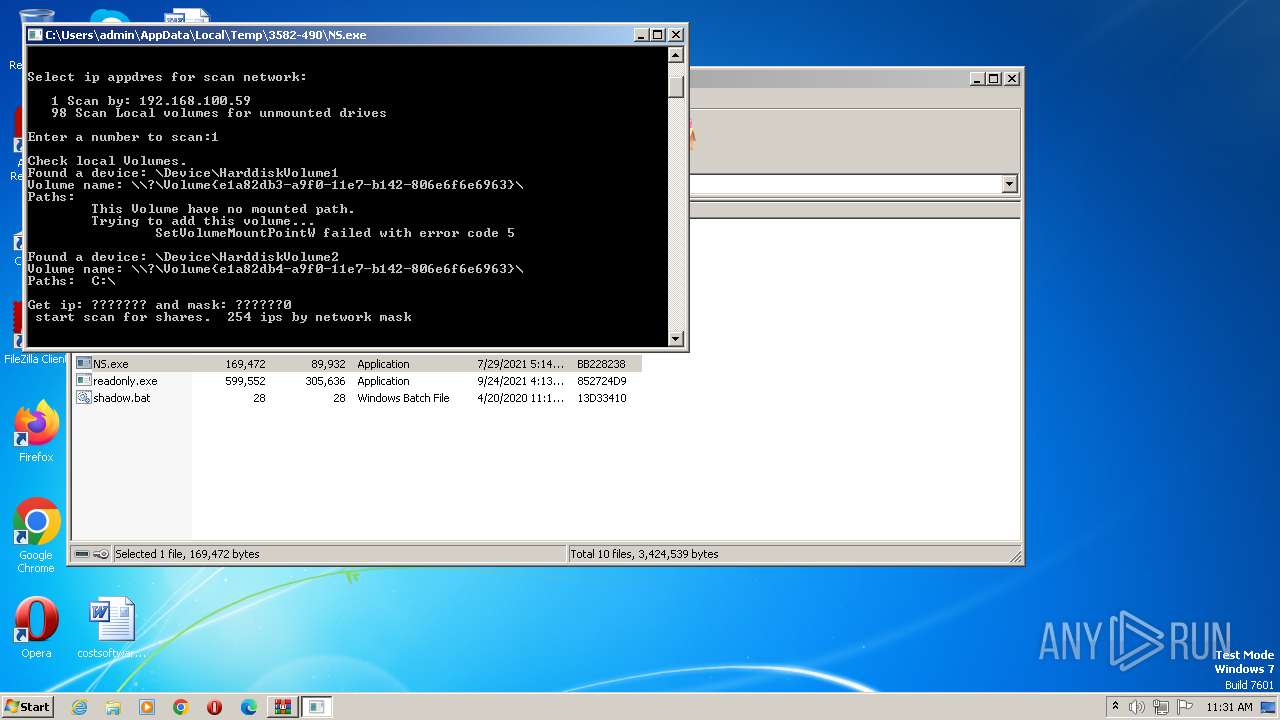
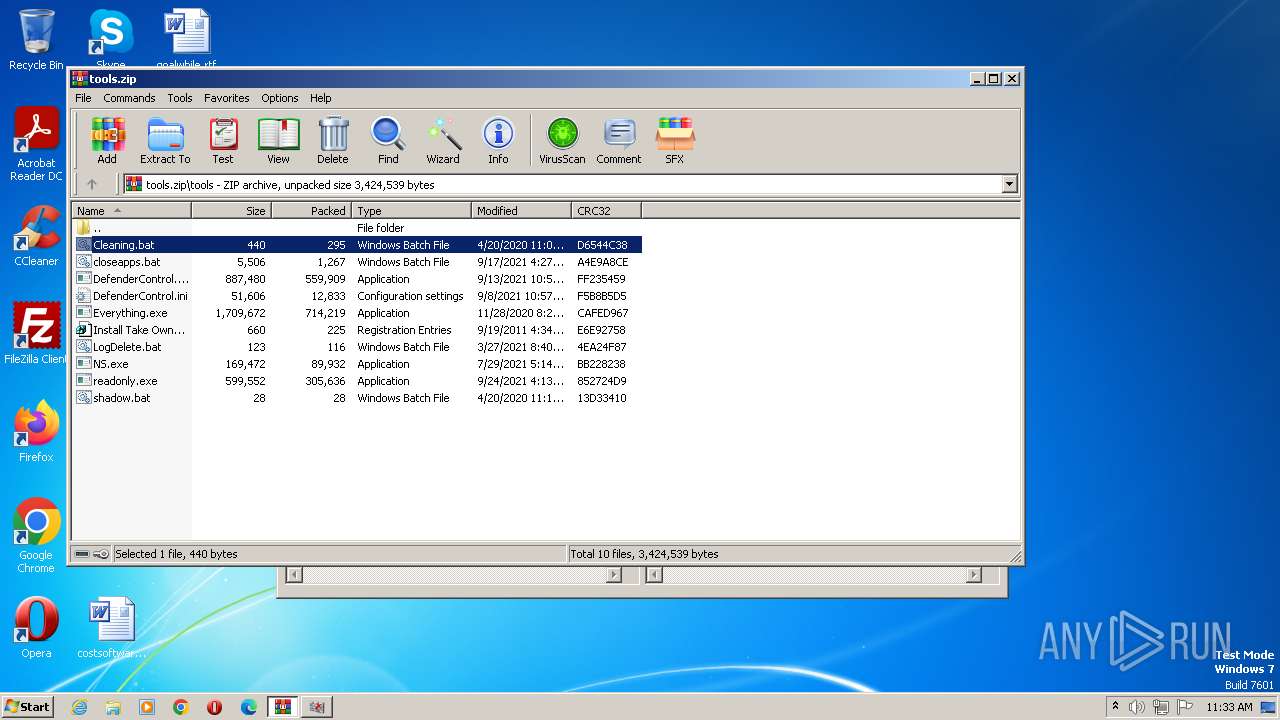
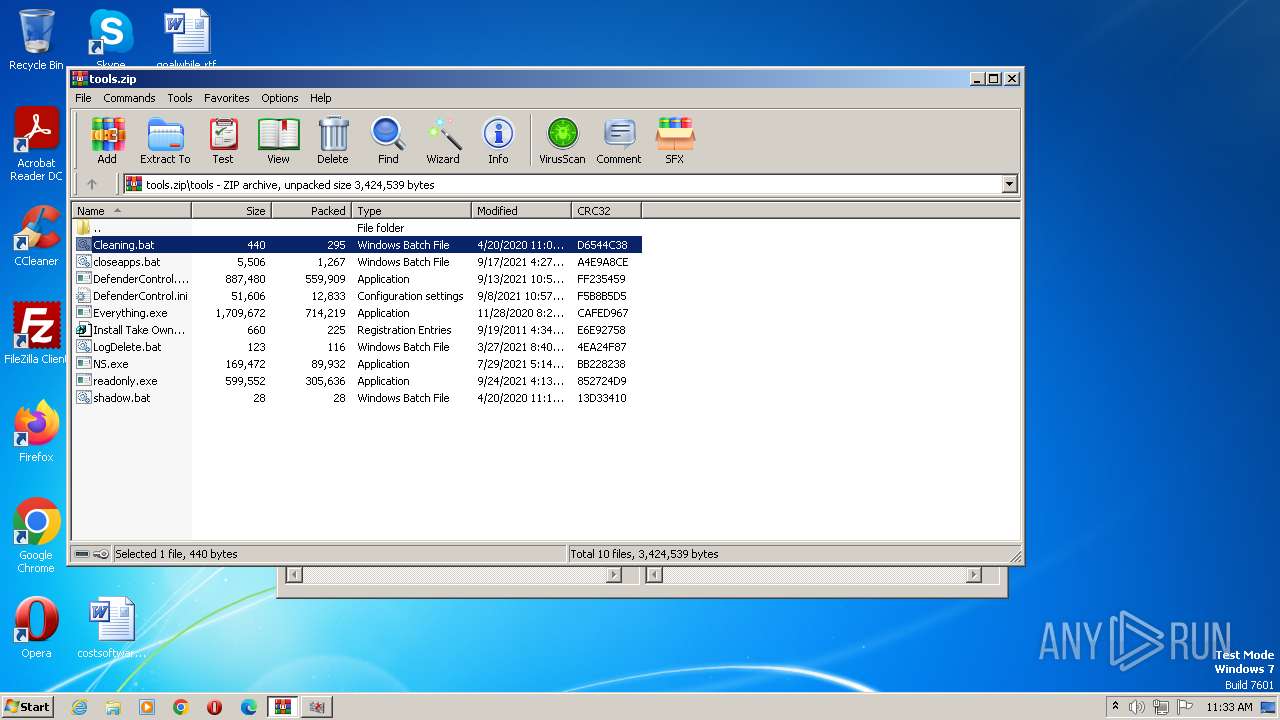
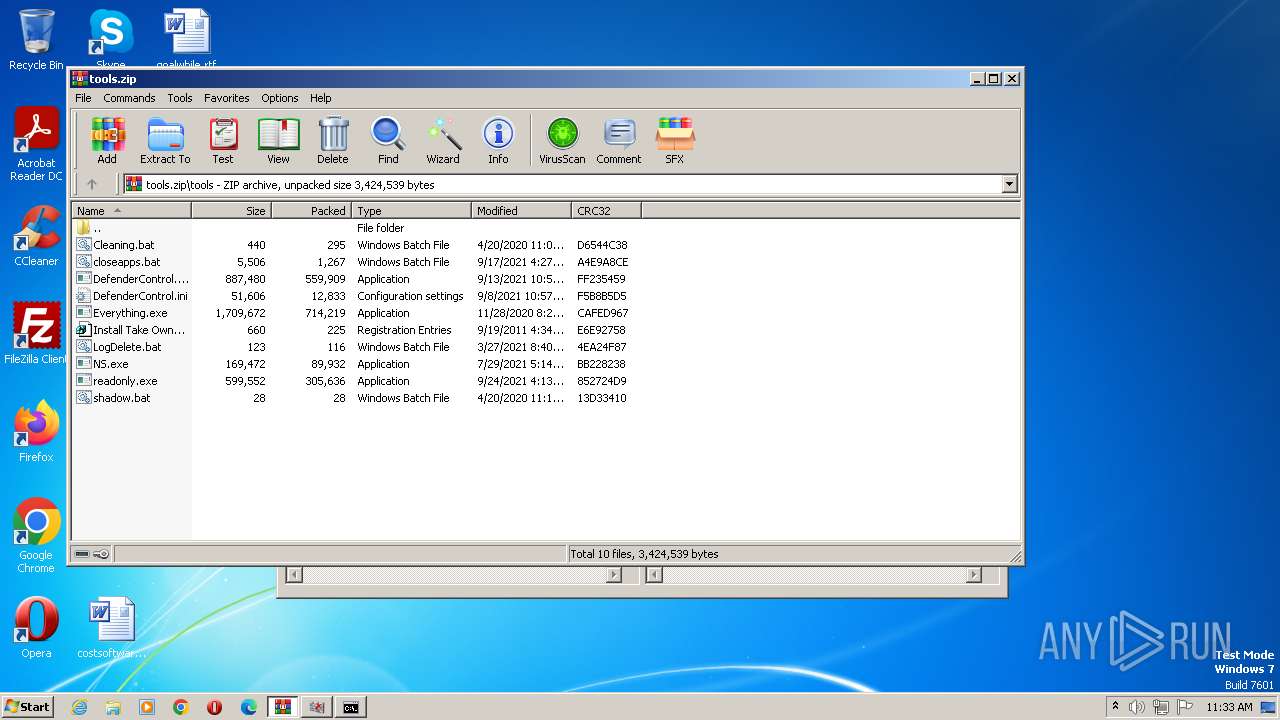
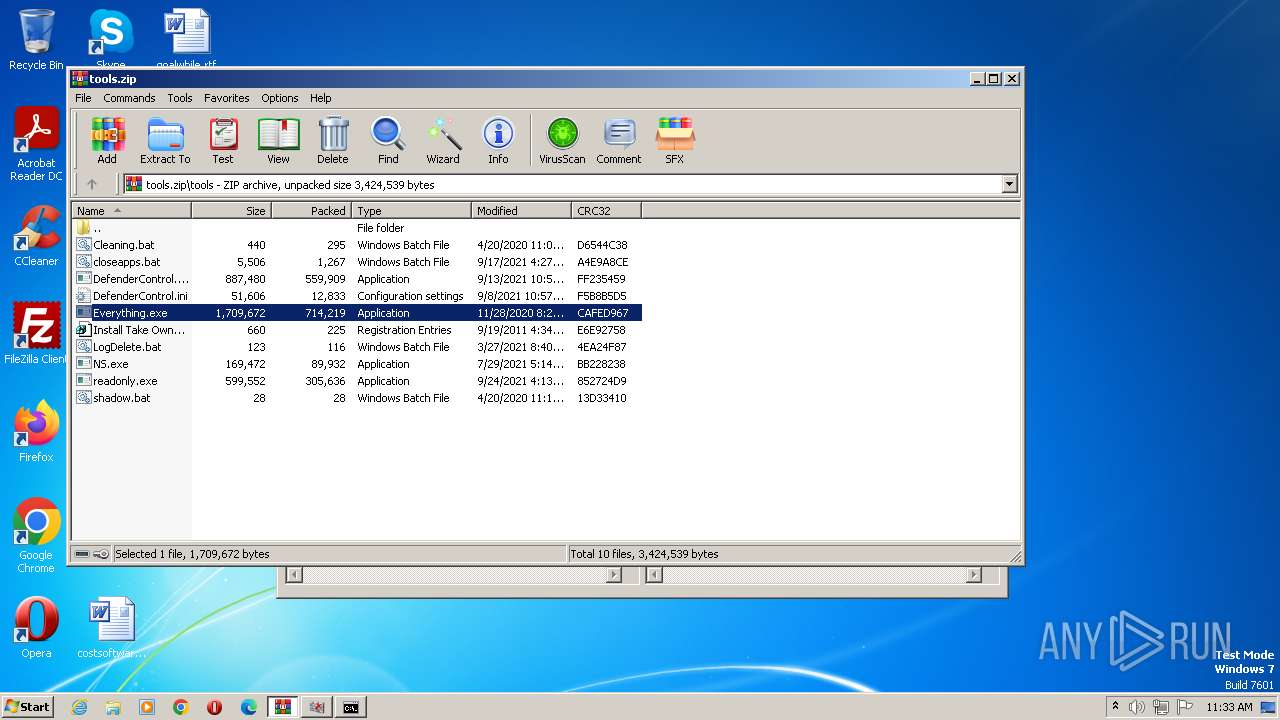
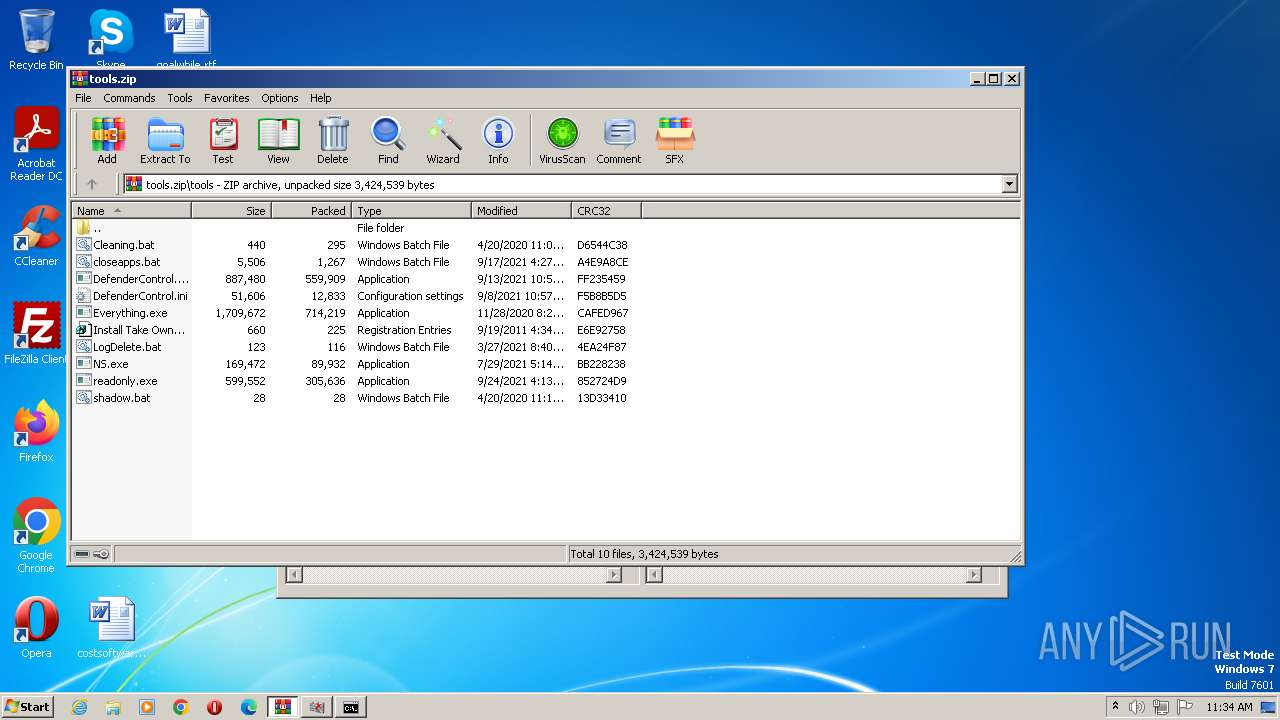
| File name: | tools.zip |
| Full analysis: | https://app.any.run/tasks/4f9d07c7-885a-422a-a5c0-602fccfebe3c |
| Verdict: | Malicious activity |
| Analysis date: | August 21, 2023, 10:30:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | DE1D599F84FBD9416366654893A85C30 |
| SHA1: | 81F43CCEFF73D5F0BBBE62A978C6FD1D9C73B339 |
| SHA256: | 21880C2216C530058A7F63CD6C3FF5896D23000C40DDAADEF35146F2E0632ED4 |
| SSDEEP: | 24576:q/cI8jUyZi+0AdwhshWlnVx6AZoqZ76iIZOyrCDdL8lC/RQzgs8syLS/XXVX8tOz:qEPHZi+bBqn7TaJO/jJQEEEWlXvfq9lY |
MALICIOUS
Application was dropped or rewritten from another process
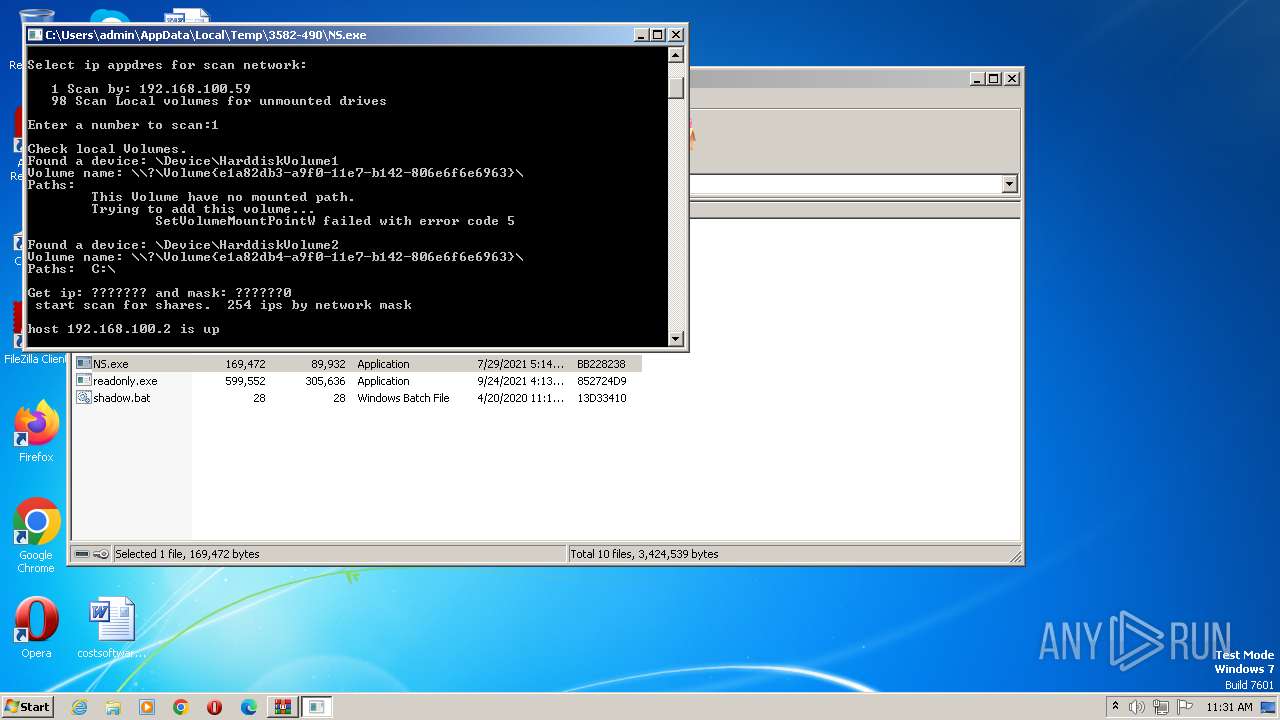
- NS.exe (PID: 460)
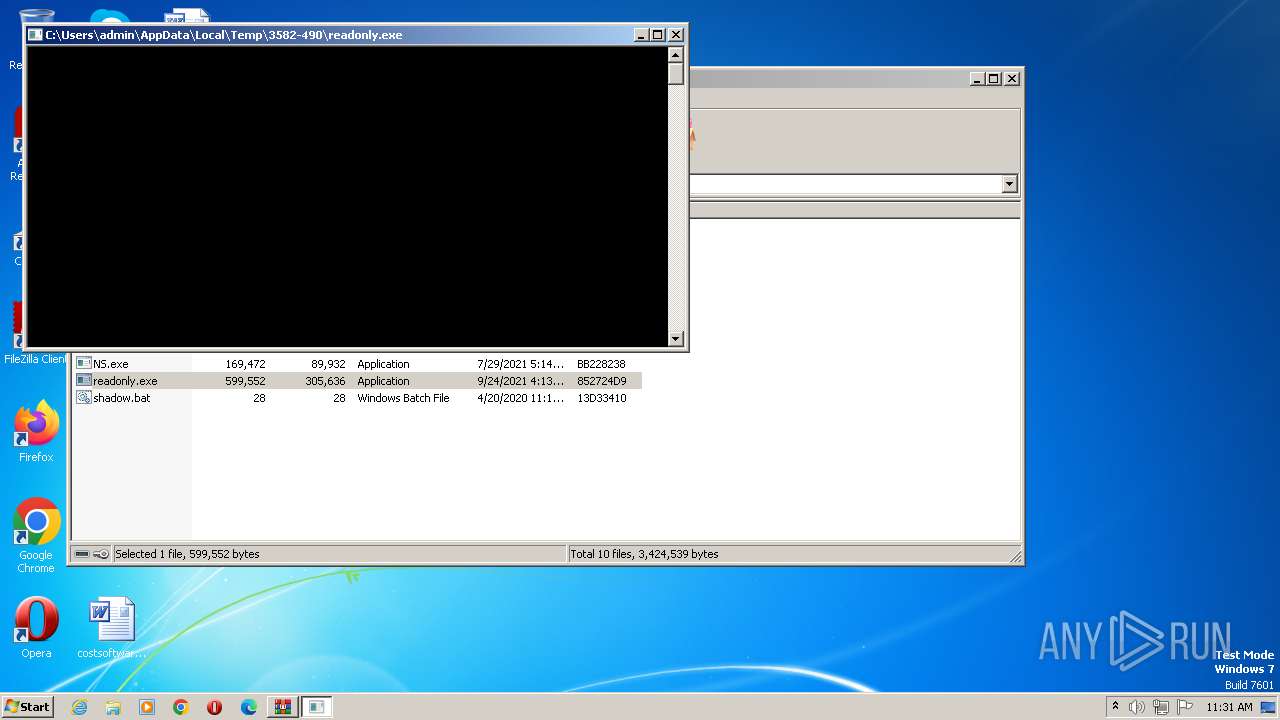
- readonly.exe (PID: 2620)
- readonly.exe (PID: 2648)
- NS.exe (PID: 2724)
Steals credentials from Web Browsers
- readonly.exe (PID: 2648)
Actions looks like stealing of personal data
- NS.exe (PID: 2724)
- readonly.exe (PID: 2648)
SUSPICIOUS
Reads the Internet Settings
- NS.exe (PID: 2724)
- readonly.exe (PID: 2620)
Executable content was dropped or overwritten
- NS.exe (PID: 2724)
- readonly.exe (PID: 2620)
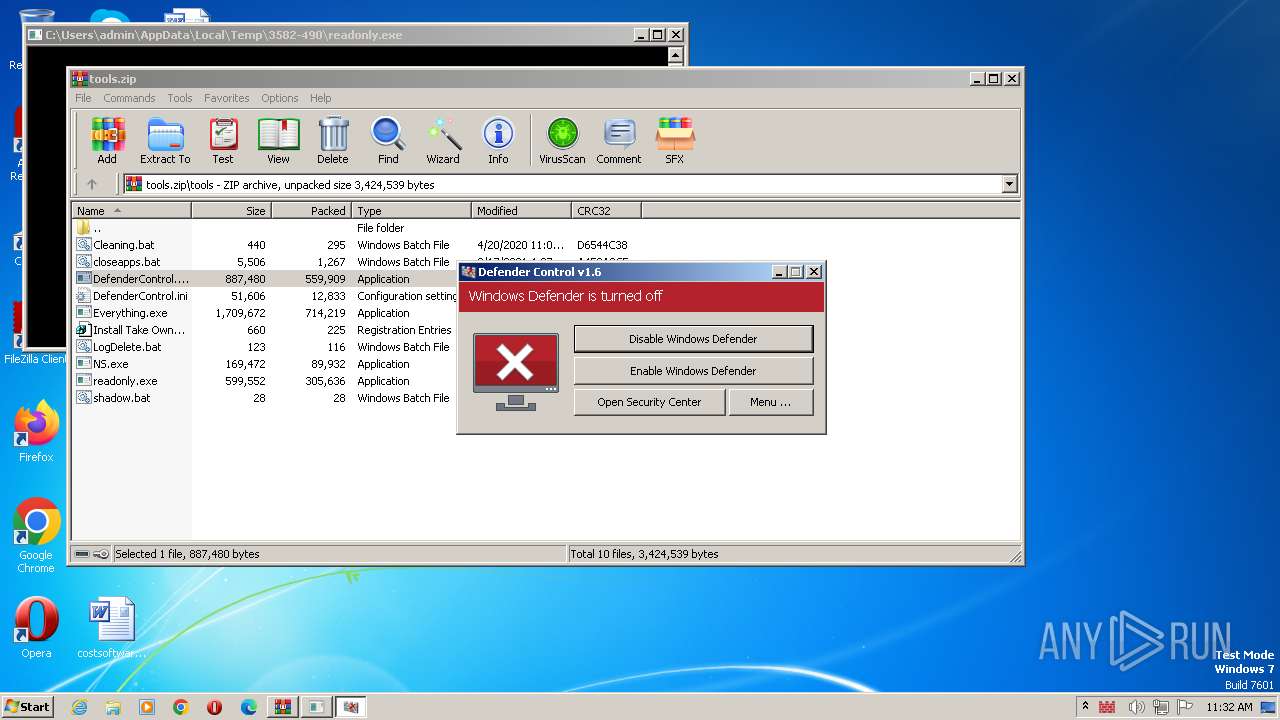
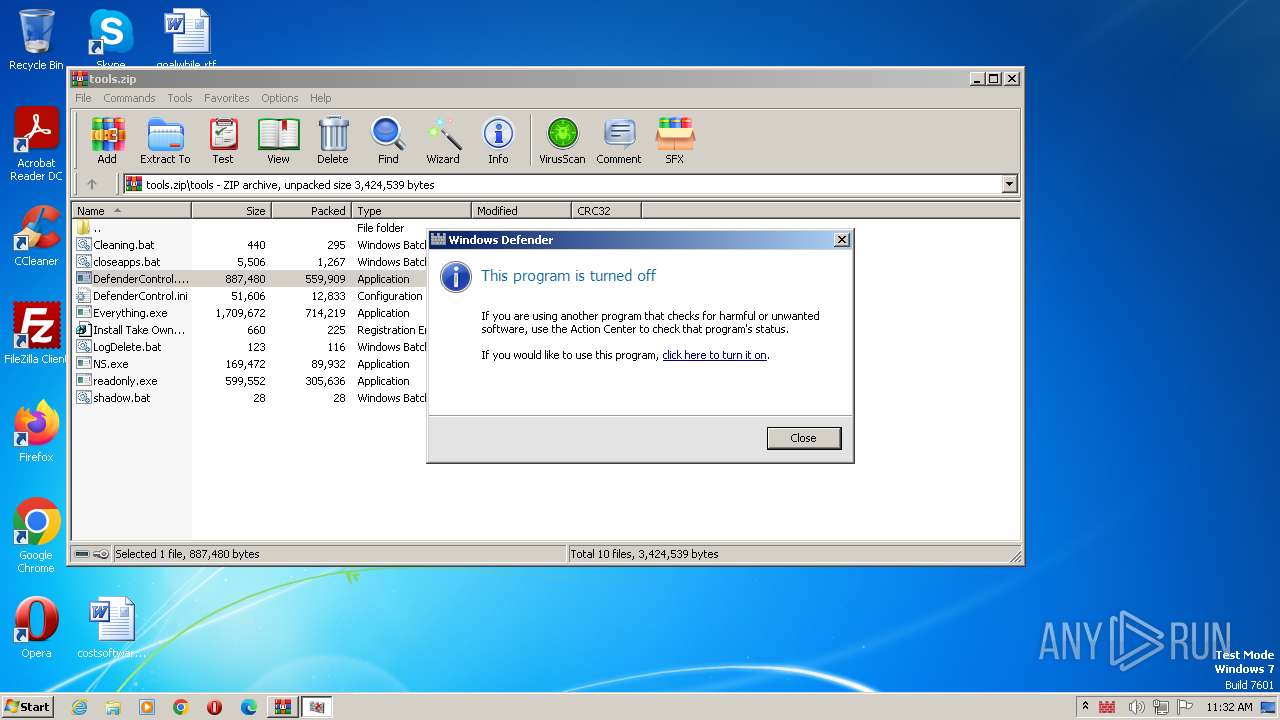
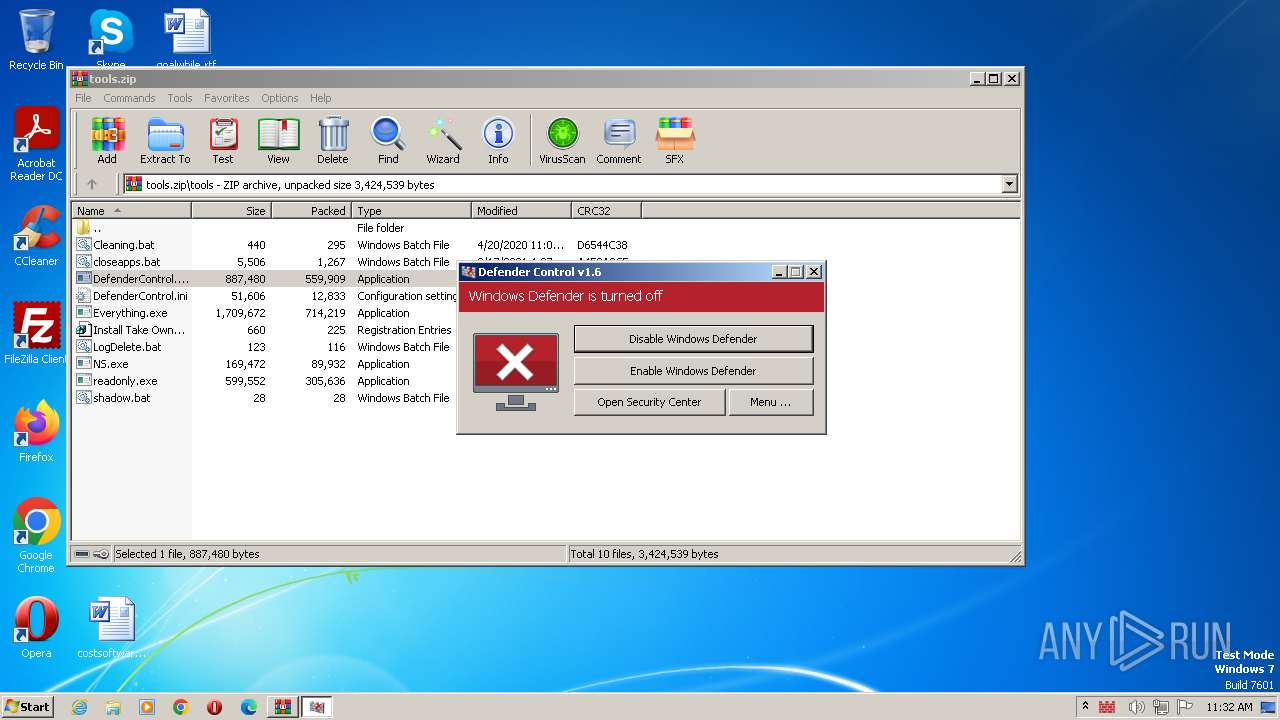
- DefenderControl.exe (PID: 1824)
Application launched itself
- DefenderControl.exe (PID: 4084)
- cmd.exe (PID: 2768)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3492)
- cmd.exe (PID: 2768)
- NS.exe (PID: 460)
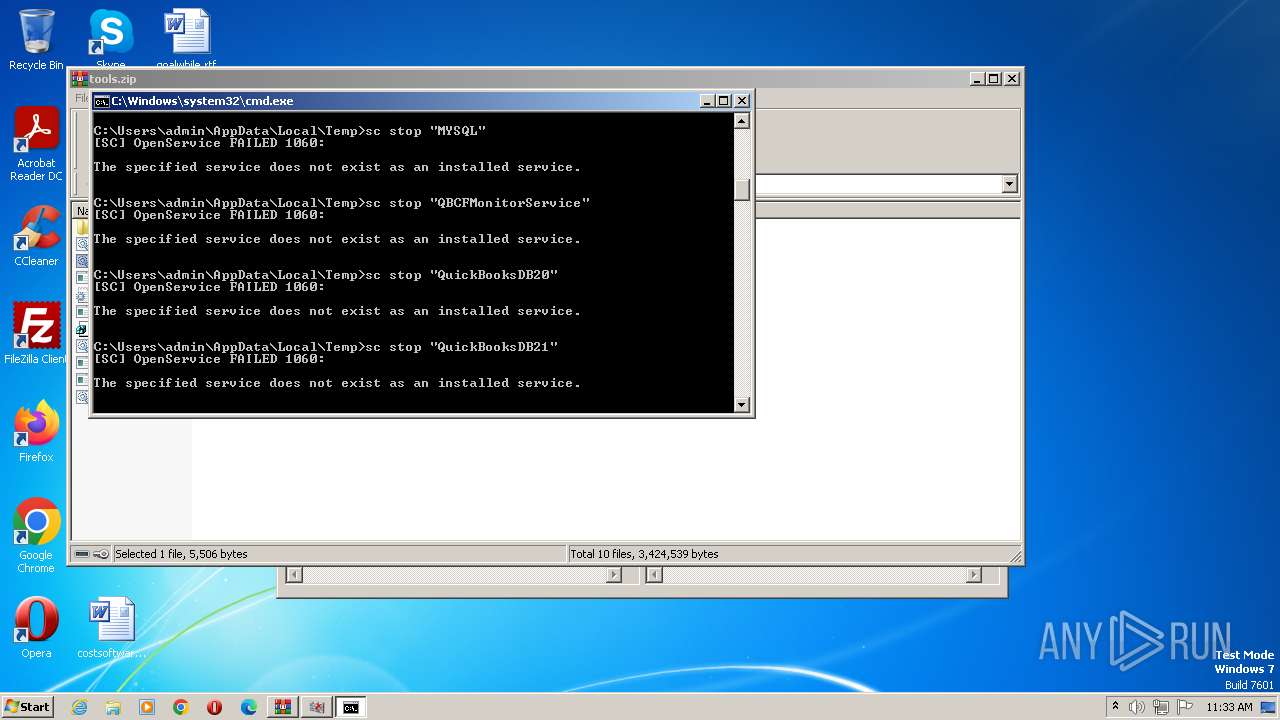
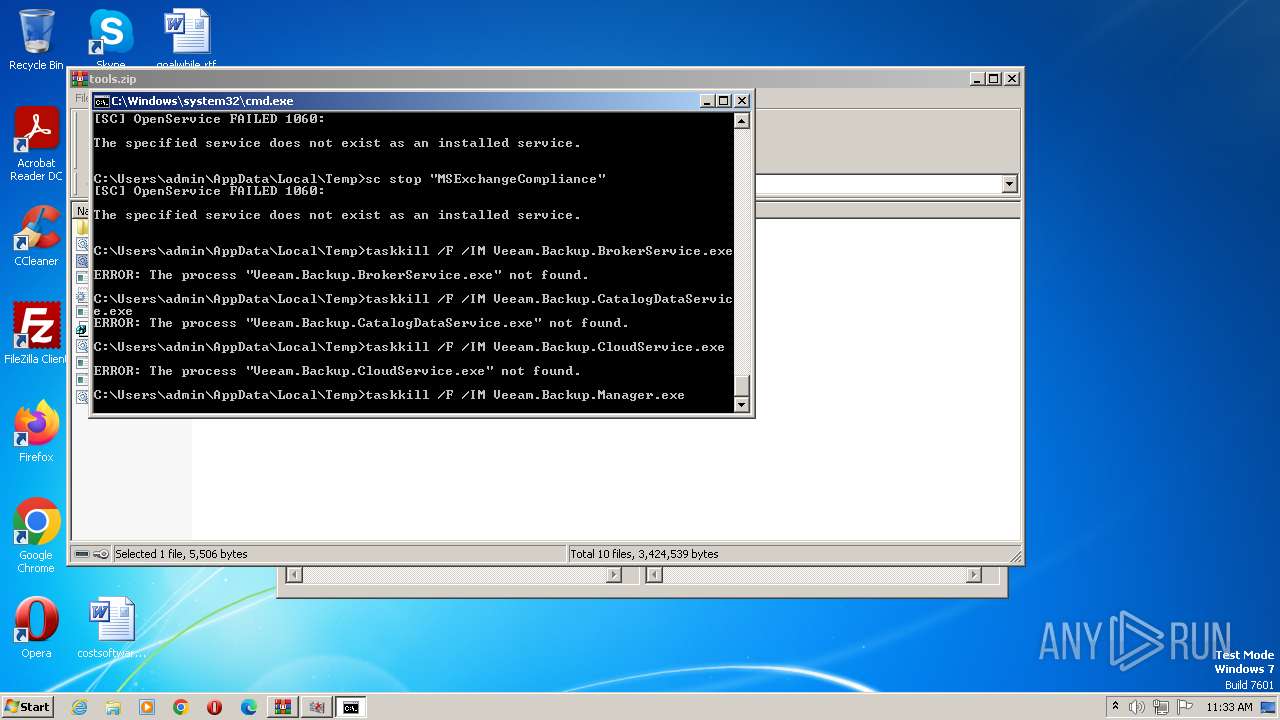
Starts SC.EXE for service management
- cmd.exe (PID: 3688)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 3492)
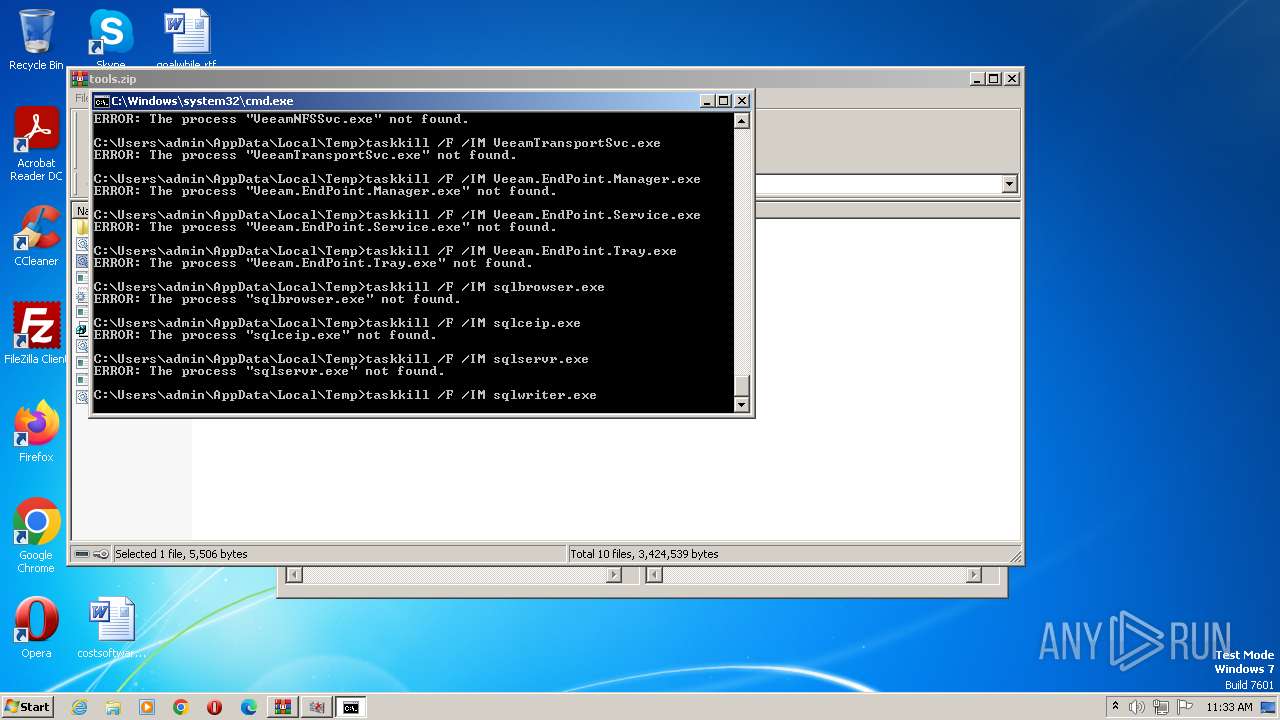
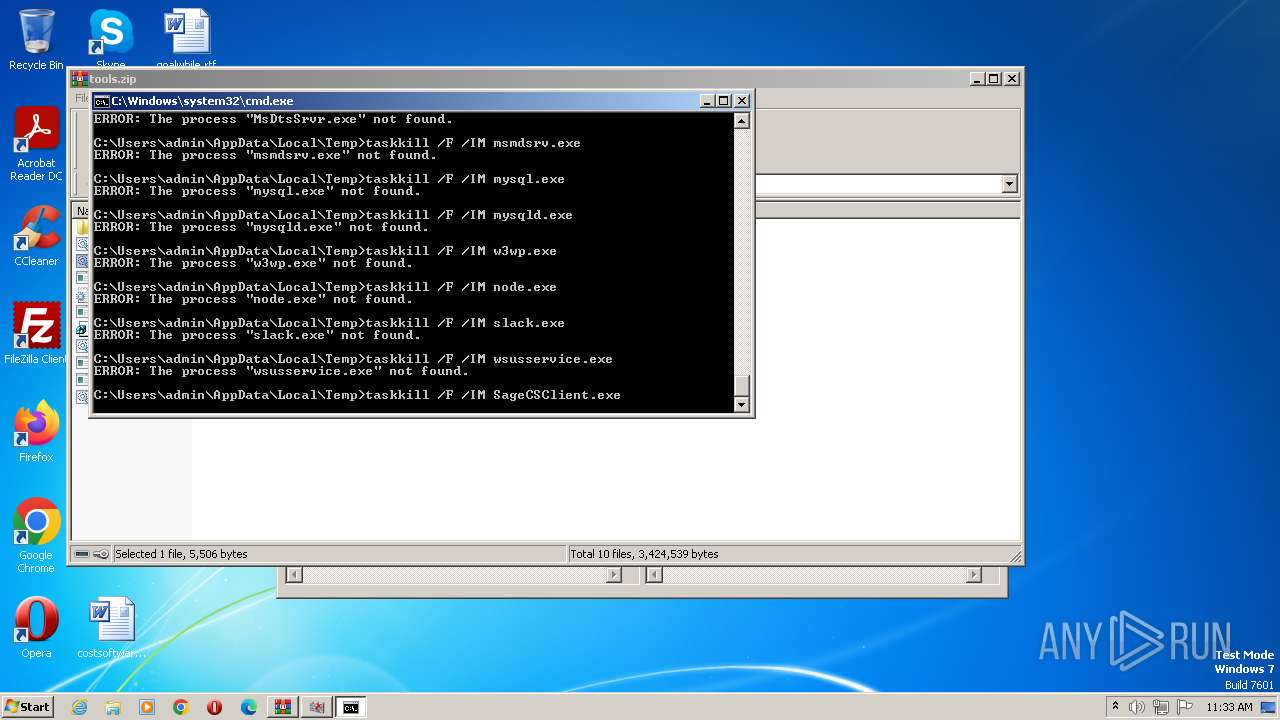
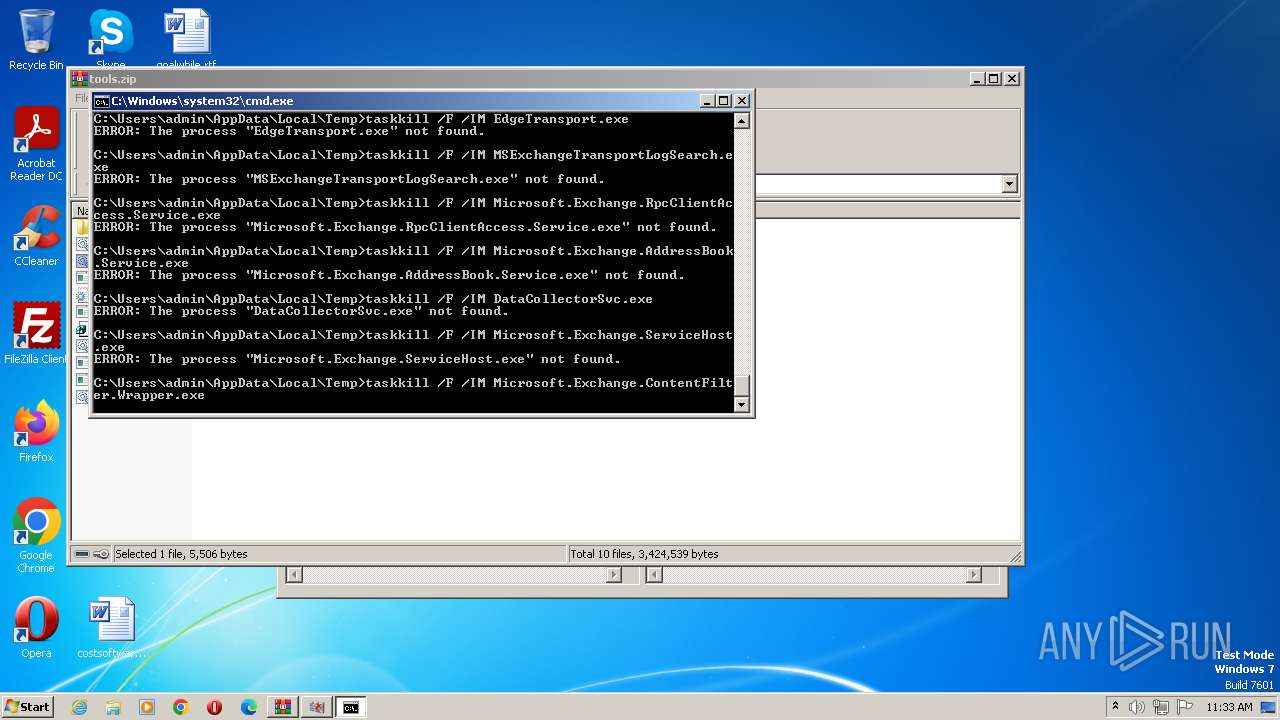
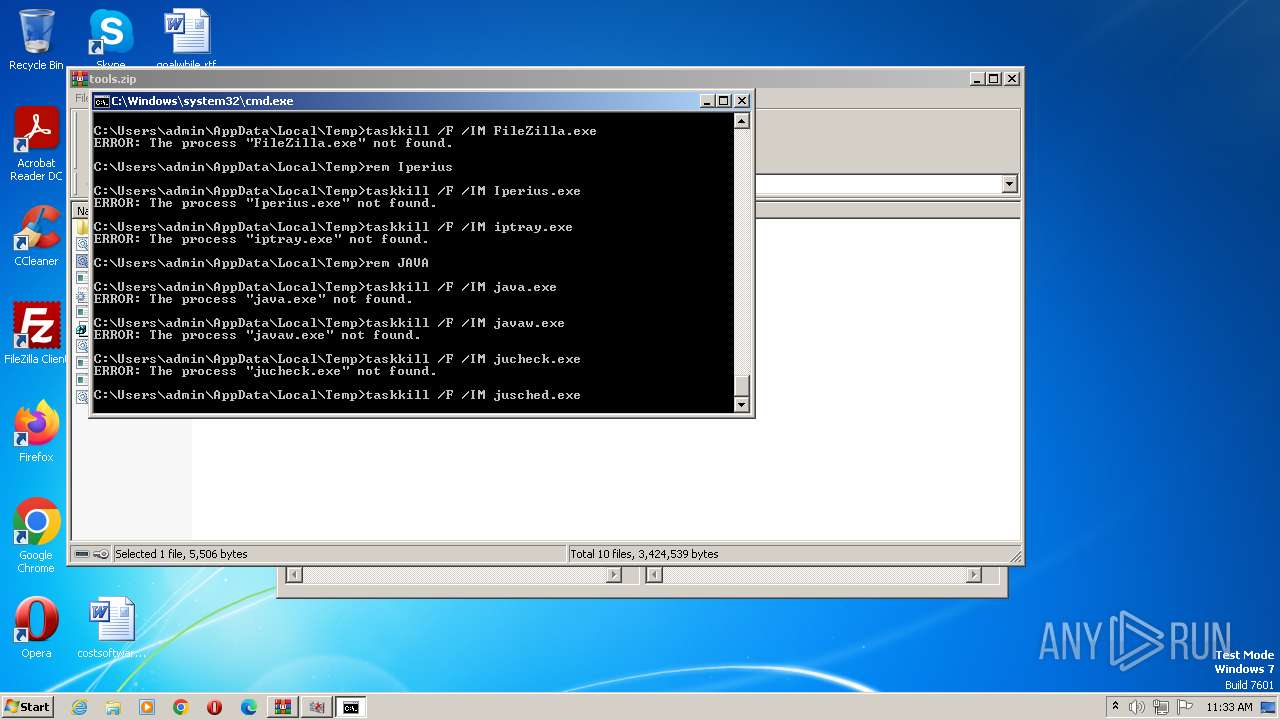
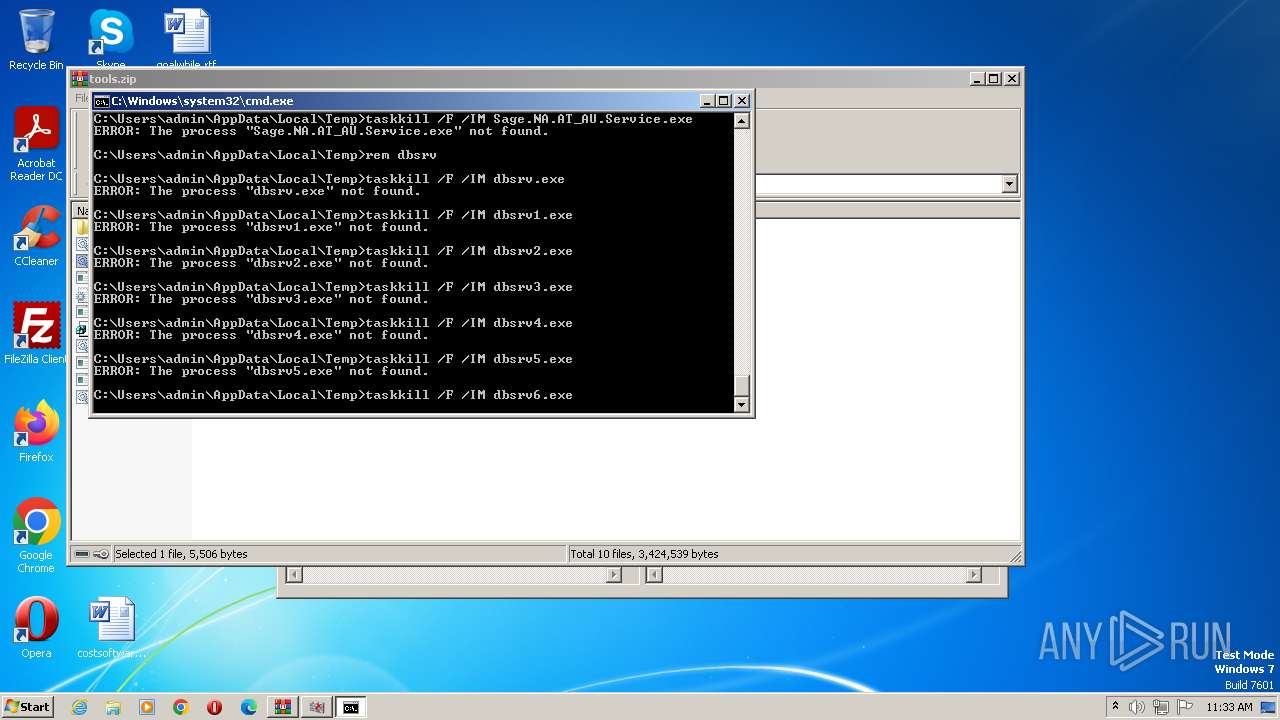
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3688)
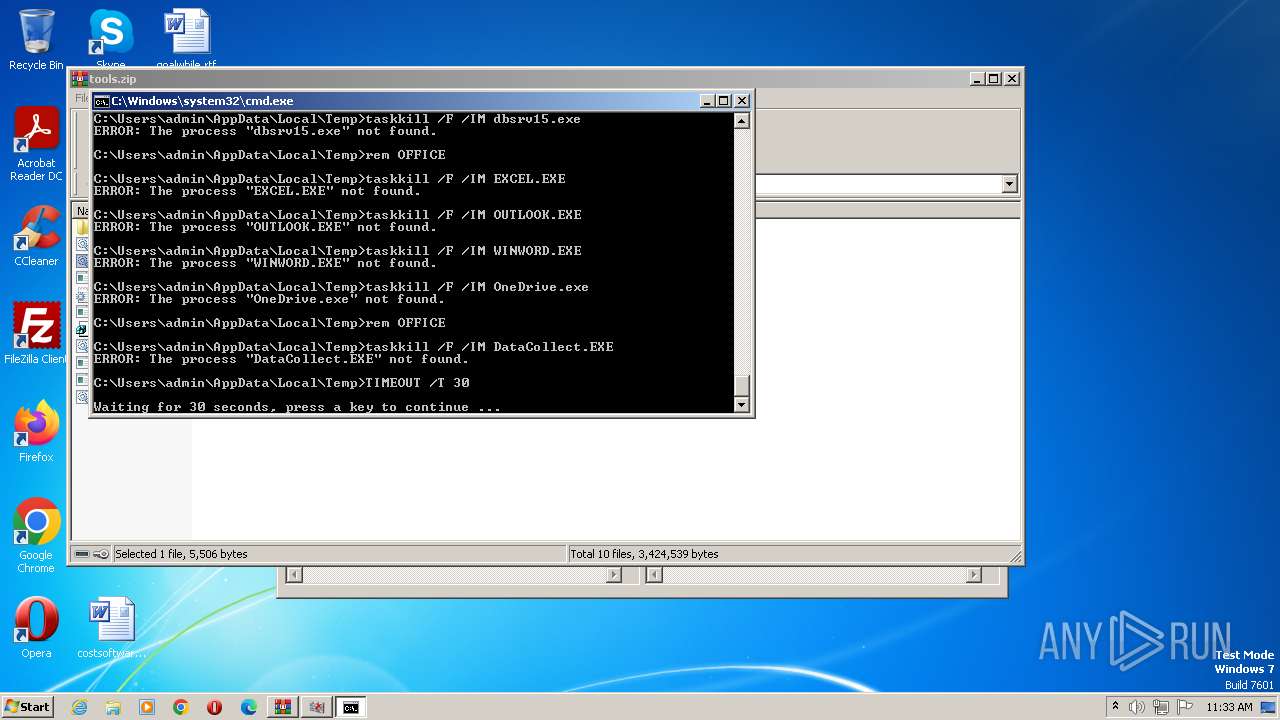
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2768)
INFO
Create files in a temporary directory
- NS.exe (PID: 2724)
- readonly.exe (PID: 2620)
Reads the computer name
- readonly.exe (PID: 2620)
- NS.exe (PID: 2724)
- NS.exe (PID: 460)
Checks supported languages
- NS.exe (PID: 2724)
- NS.exe (PID: 460)
- readonly.exe (PID: 2648)
- readonly.exe (PID: 2620)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3492)
Manual execution by a user
- msedge.exe (PID: 4036)
Application launched itself
- msedge.exe (PID: 3116)
- msedge.exe (PID: 4036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | tools/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2021:10:04 11:46:02 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
226
Monitored processes
179
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 460 | "C:\Users\admin\AppData\Local\Temp\3582-490\NS.exe" | C:\Users\admin\AppData\Local\Temp\3582-490\NS.exe | — | NS.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 460 | sc stop "MSExchangeSubmission" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 476 | sc stop "1C:Enterprise 8.3 Server Agent (x86-64)" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 532 | sc stop "SSISScaleOutWorker140" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 616 | sc stop "VeeamBrokerSvc" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 616 | taskkill /F /IM Veeam.Guest.Interaction.Proxy.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 620 | sc stop "MSExchangeMailboxReplication" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 756 | taskkill /F /IM FileZilla.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 768 | taskkill /F /IM Ssms.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 832 | taskkill /F /IM slack.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
9 137
Read events
9 043
Write events
88
Delete events
6
Modification events
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
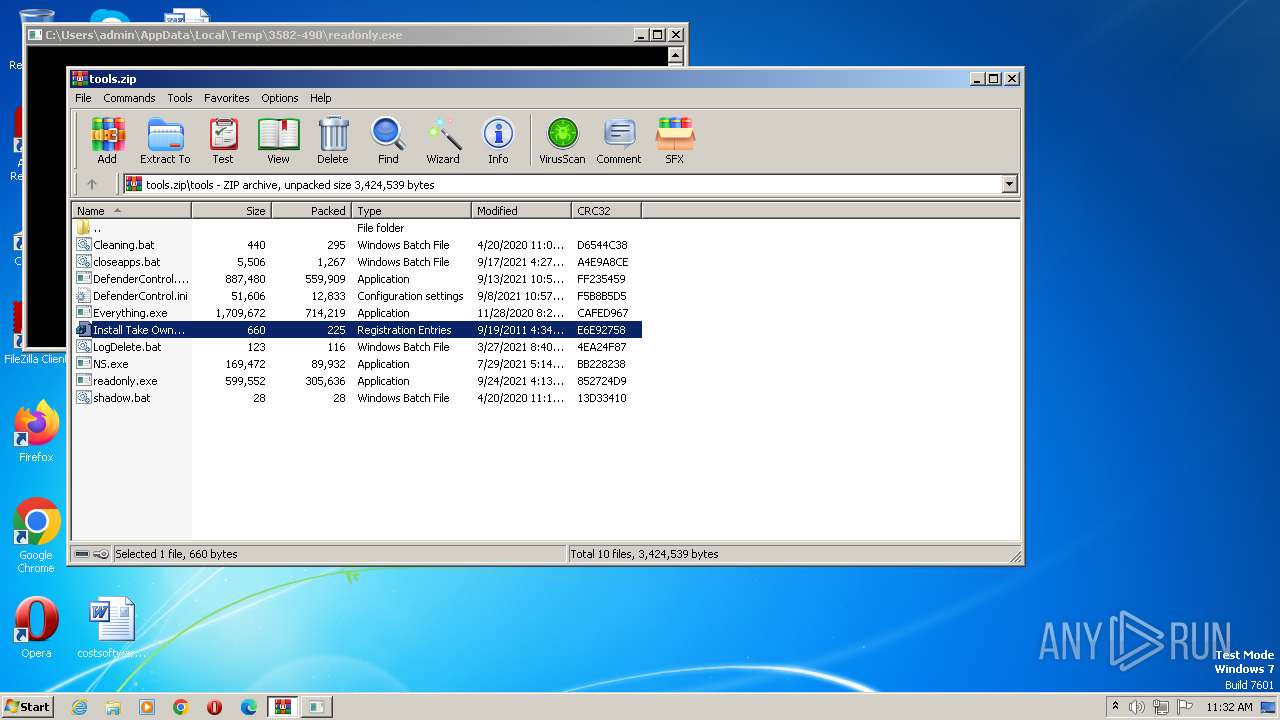
Executable files
35
Suspicious files
34
Text files
93
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3492.37698\tools\Cleaning.bat | text | |
MD5:06E80776FB217571BC837555D5E1728A | SHA256:47759C3C8B65A2F3EBA486E44611209327F4052F67CC3C4A494D1FB0DC4BF4C9 | |||
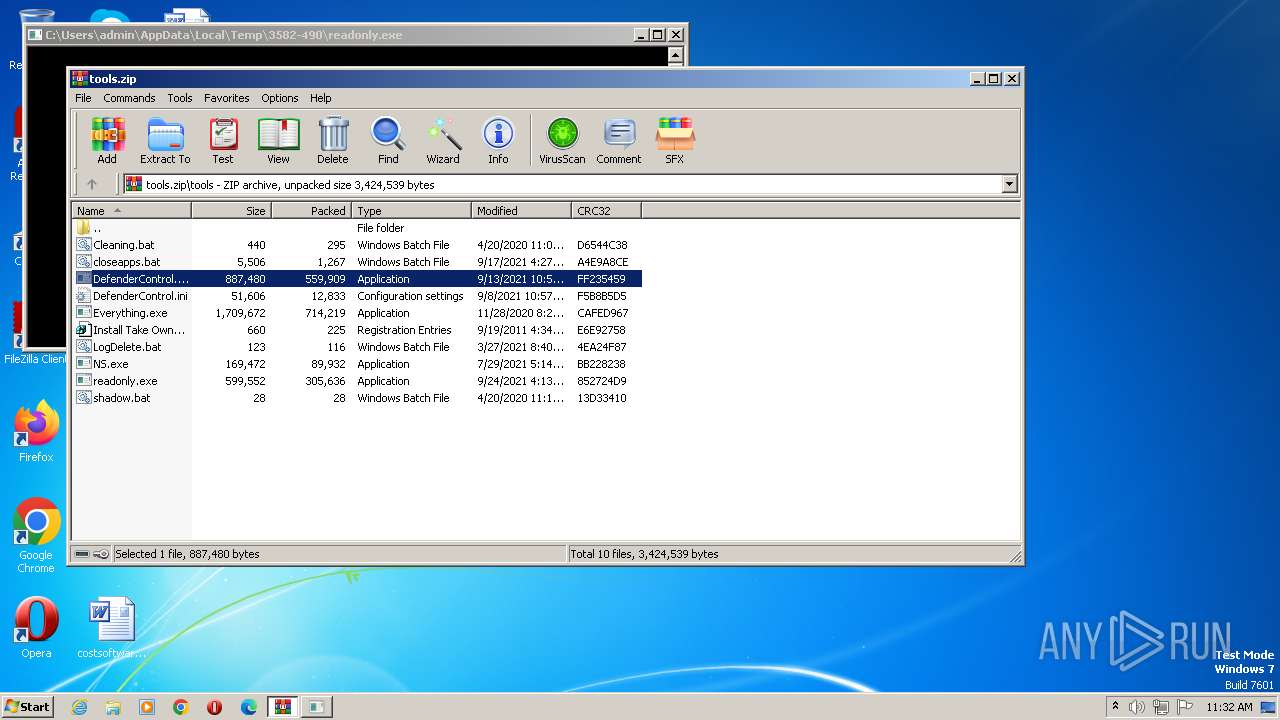
| 3492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3492.37698\tools\DefenderControl.exe | executable | |
MD5:D4531EFA4966994018145F9150545649 | SHA256:CE162D2D3649A13A48510E79EF0046F9A194F9609C5EE0EE340766ABE1D1B565 | |||
| 3492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3492.37698\tools\Everything.exe | executable | |
MD5:123F8F1DA73684D013E87AEE4F2BA16C | SHA256:E2E32FA51F7DFD4B1F6960A09E7466E1FC53BA15A6B1D222A355579DB003203C | |||
| 2724 | NS.exe | C:\MSOCache\All Users\{90140000-006E-0407-0000-0000000FF1CE}-C\DW20.EXE | executable | |
MD5:02EE6A3424782531461FB2F10713D3C1 | SHA256:EAD58C483CB20BCD57464F8A4929079539D634F469B213054BF737D227C026DC | |||
| 2724 | NS.exe | C:\MSOCache\All Users\{90140000-003D-0000-0000-0000000FF1CE}-C\setup.exe | executable | |
MD5:566ED4F62FDC96F175AFEDD811FA0370 | SHA256:E17CD94C08FC0E001A49F43A0801CEA4625FB9AEE211B6DFEBEBEC446C21F460 | |||
| 3492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3492.37698\tools\DefenderControl.ini | text | |
MD5:436BA365F9847A17824226930A0A8C7D | SHA256:294C26956691C3512FFC20C621AD95125341042683BBCE806EEAA33C12E8BBEE | |||
| 3492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3492.37698\tools\NS.exe | executable | |
MD5:B16522C76D4129C5381C2568B1E31581 | SHA256:21F78B4D9829DB5E3E7D21FF3AD03991B9D00DF9D05518FF49B8CDFB2D46E282 | |||
| 3492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3492.37698\tools\closeapps.bat | text | |
MD5:CB44B571A3333F667ADFD0D05D9D8DEA | SHA256:85A1DD61BB9A122BAA1E6B00C58D7F850AF7A20525523151A43545A9FCD8C10E | |||
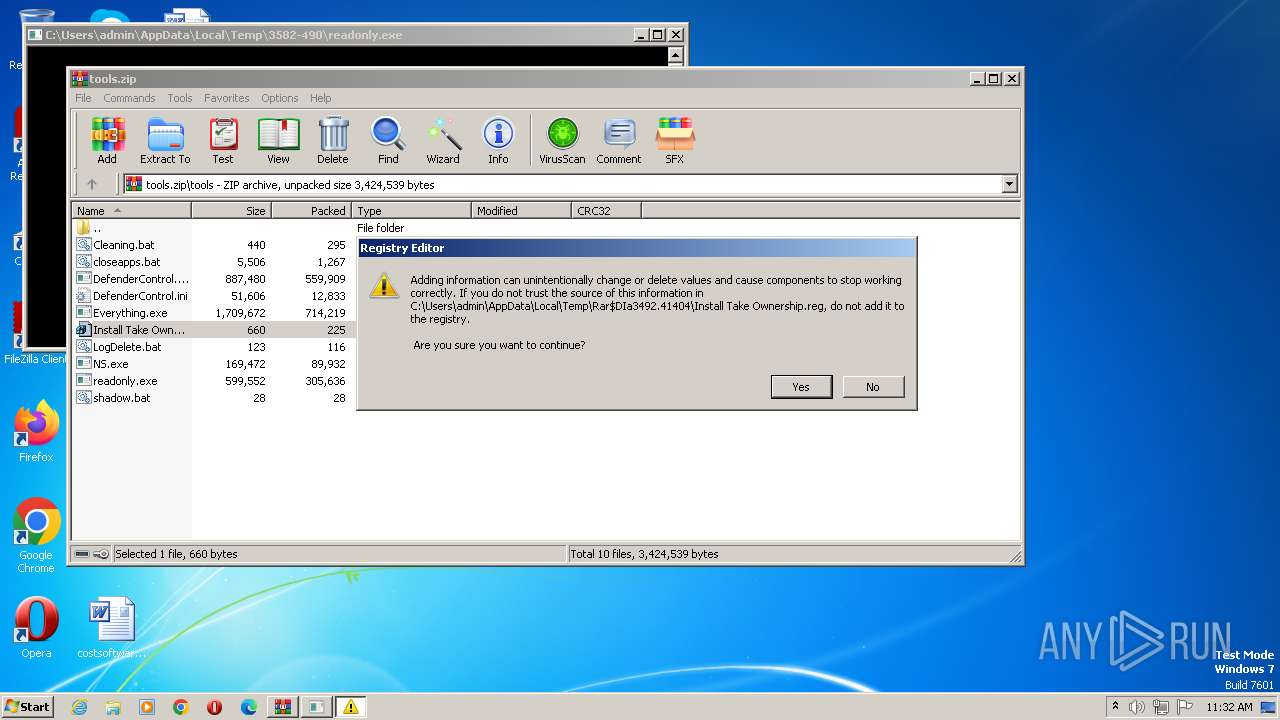
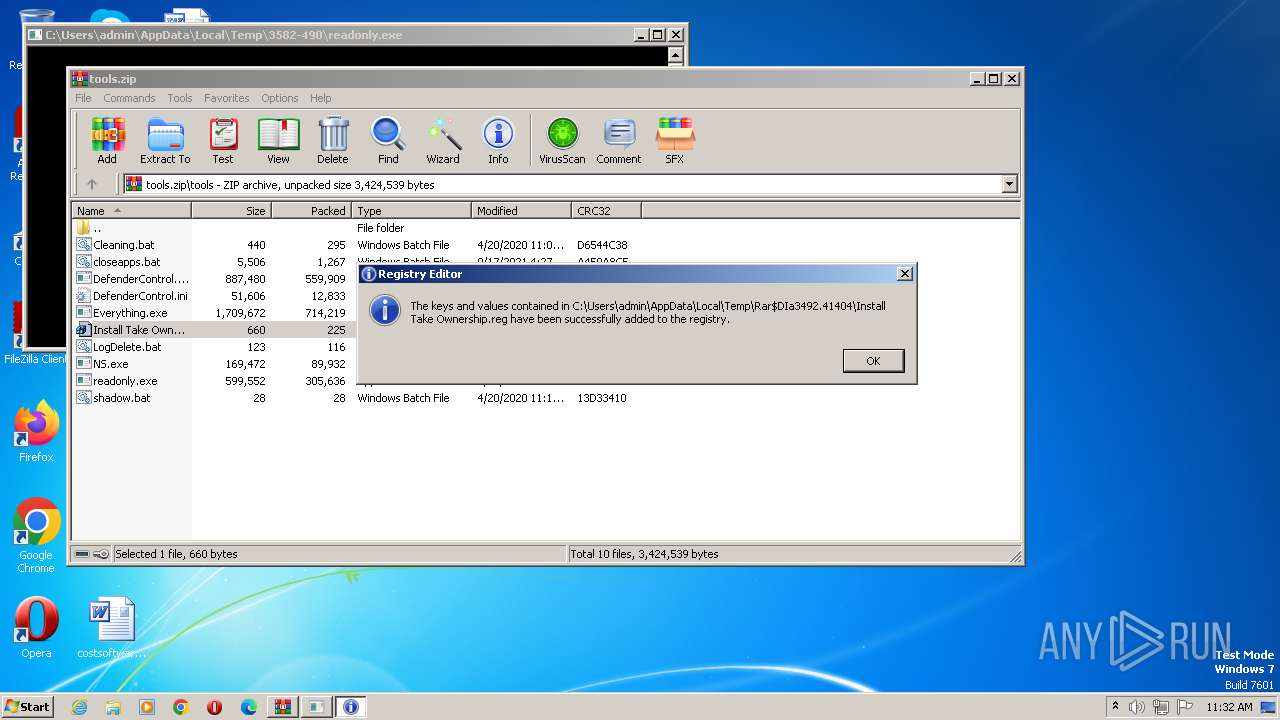
| 3492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3492.37698\tools\Install Take Ownership.reg | text | |
MD5:29896F795D3E250540AE33EB84D0AF71 | SHA256:61FD9430AAC2D0813451326B5CAEB7F463442CEEC46A9D1D52ED34541768C931 | |||
| 3492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3492.37698\tools\readonly.exe | executable | |
MD5:05009F4A981B86A26073E40E358FD1A8 | SHA256:23FA9076055DF20D9D8EE26A2597D850FF2B539014031F27210FC8C34D048F5F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
36
DNS requests
17
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.2:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
— | — | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 185.146.22.240:443 | www.sordum.org | A2HOSTING | US | suspicious |
— | — | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 20.8.16.139:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 8.241.9.252:443 | msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com | LEVEL3 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| malicious |
www.sordum.org |
| suspicious |
edge.microsoft.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
data-edge.smartscreen.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| shared |