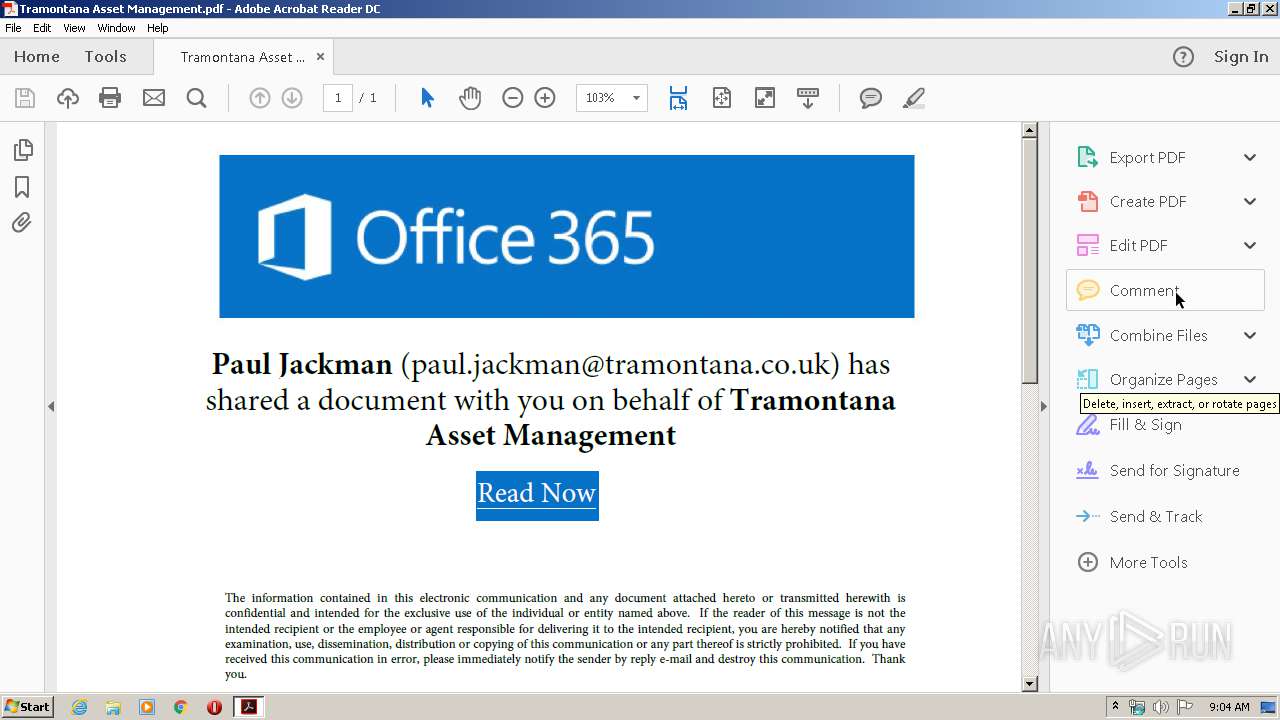
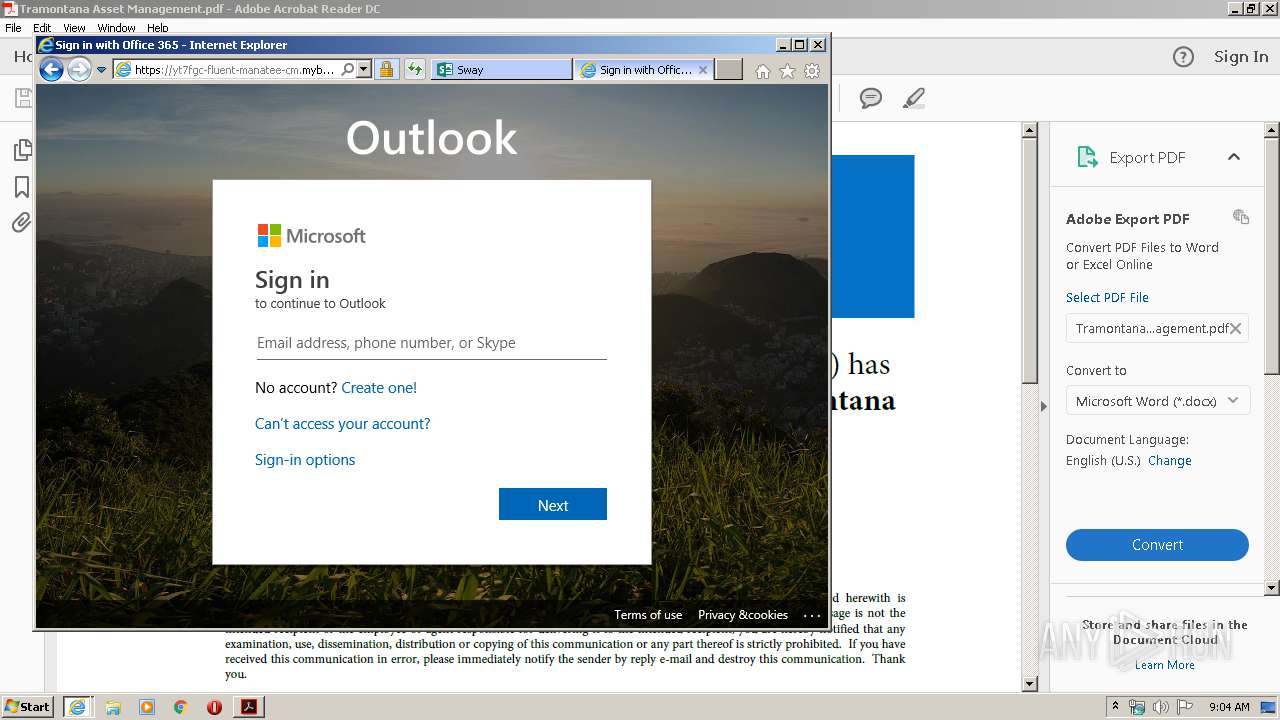
| File name: | Tramontana Asset Management.pdf |
| Full analysis: | https://app.any.run/tasks/2911c8ad-f8bb-44c9-b583-9becb0a398d2 |
| Verdict: | Malicious activity |
| Analysis date: | February 22, 2020, 09:04:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.6 |
| MD5: | DA4C498890916E4E6AB6B584ADBB9150 |
| SHA1: | 9F9AD725613613B03395E0A8BA287748E50E39F4 |
| SHA256: | 217CBDA3D38907B9991C67AA882F195493D2962B6E1D86F4A4D85C6A63CA266D |
| SSDEEP: | 768:v6ktiO2071B8W12rANt/dHLwMC5aJYfb1E37LEBlCsZo31/2TGVekkkkkkkkkkkK:vztiOL5312ENt1HLoaJYh5GsSOTGVK2k |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts Internet Explorer
- AcroRd32.exe (PID: 3200)
Changes IE settings (feature browser emulation)
- AcroRd32.exe (PID: 3200)
Creates files in the program directory
- AdobeARM.exe (PID: 4052)
INFO
Reads Internet Cache Settings
- AcroRd32.exe (PID: 308)
- iexplore.exe (PID: 3264)
- AcroRd32.exe (PID: 3200)
- iexplore.exe (PID: 3104)
- iexplore.exe (PID: 3468)
Changes internet zones settings
- iexplore.exe (PID: 3264)
Reads the hosts file
- RdrCEF.exe (PID: 2668)
Application launched itself
- RdrCEF.exe (PID: 2668)
- iexplore.exe (PID: 3264)
Reads internet explorer settings
- iexplore.exe (PID: 3468)
- iexplore.exe (PID: 3104)
Creates files in the user directory
- iexplore.exe (PID: 3468)
Reads settings of System Certificates
- AcroRd32.exe (PID: 3200)
- iexplore.exe (PID: 3104)
- iexplore.exe (PID: 3468)
- iexplore.exe (PID: 3264)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3264)
Changes settings of System certificates
- iexplore.exe (PID: 3264)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.6 |
|---|---|
| Linearized: | Yes |
| CreateDate: | 2019:12:13 09:22:51Z |
| Creator: | Acrobat Pro DC 19.21.20056 |
| ModifyDate: | 2020:02:21 11:22:31Z |
| Producer: | Acrobat Pro DC 19.21.20056 |
| HasXFA: | No |
| PageCount: | 1 |
XMP
| XMPToolkit: | Adobe XMP Core 5.6-c016 91.163616, 2018/10/29-16:58:49 |
|---|---|
| ModifyDate: | 2020:02:21 11:22:31Z |
| CreateDate: | 2019:12:13 09:22:51Z |
| MetadataDate: | 2020:02:21 11:22:31Z |
| CreatorTool: | Acrobat Pro DC 19.21.20056 |
| Format: | application/pdf |
| DocumentID: | uuid:f410a7e3-620a-0940-96df-702f4a9c5c2c |
| InstanceID: | uuid:7fa4b7e5-945e-1c48-8819-f538ec52f908 |
| Producer: | Acrobat Pro DC 19.21.20056 |
Total processes
44
Monitored processes
10
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Temp\Tramontana Asset Management.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 1688 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="2668.0.1411158325\68462966" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2424 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="2668.1.173659922\619837126" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2668 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 3104 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3264 CREDAT:2692359 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3200 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\Tramontana Asset Management.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
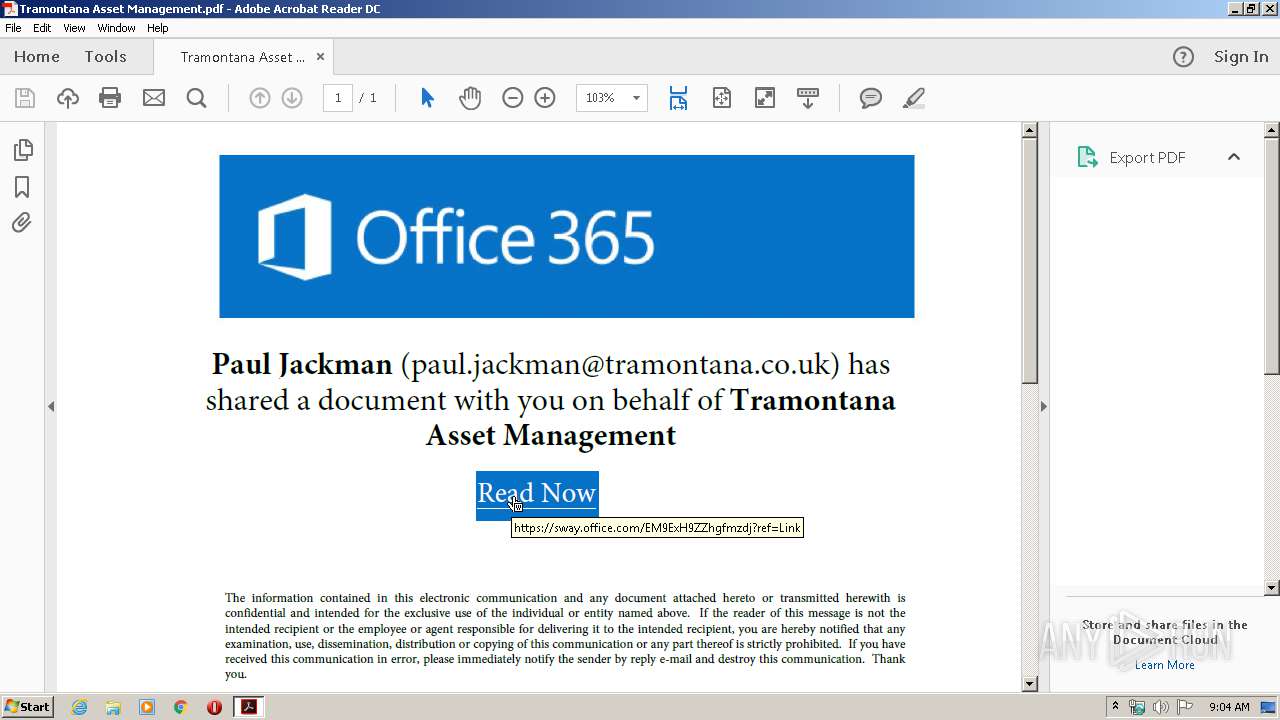
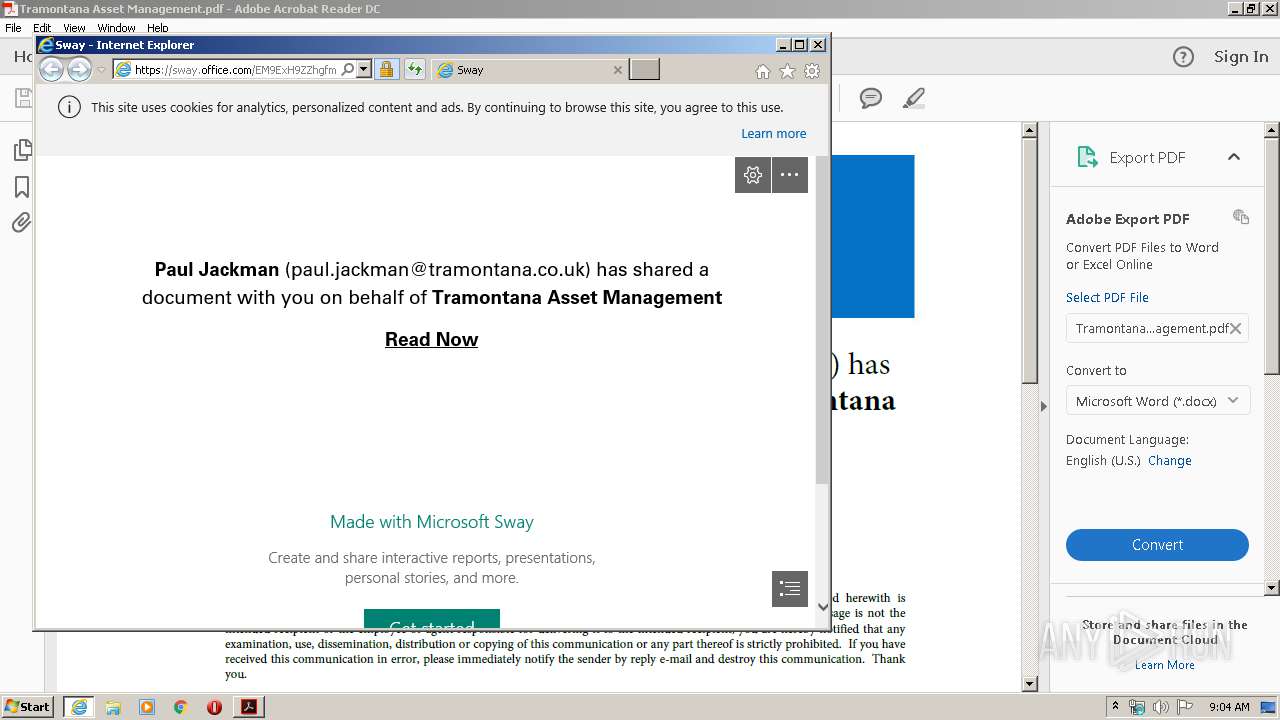
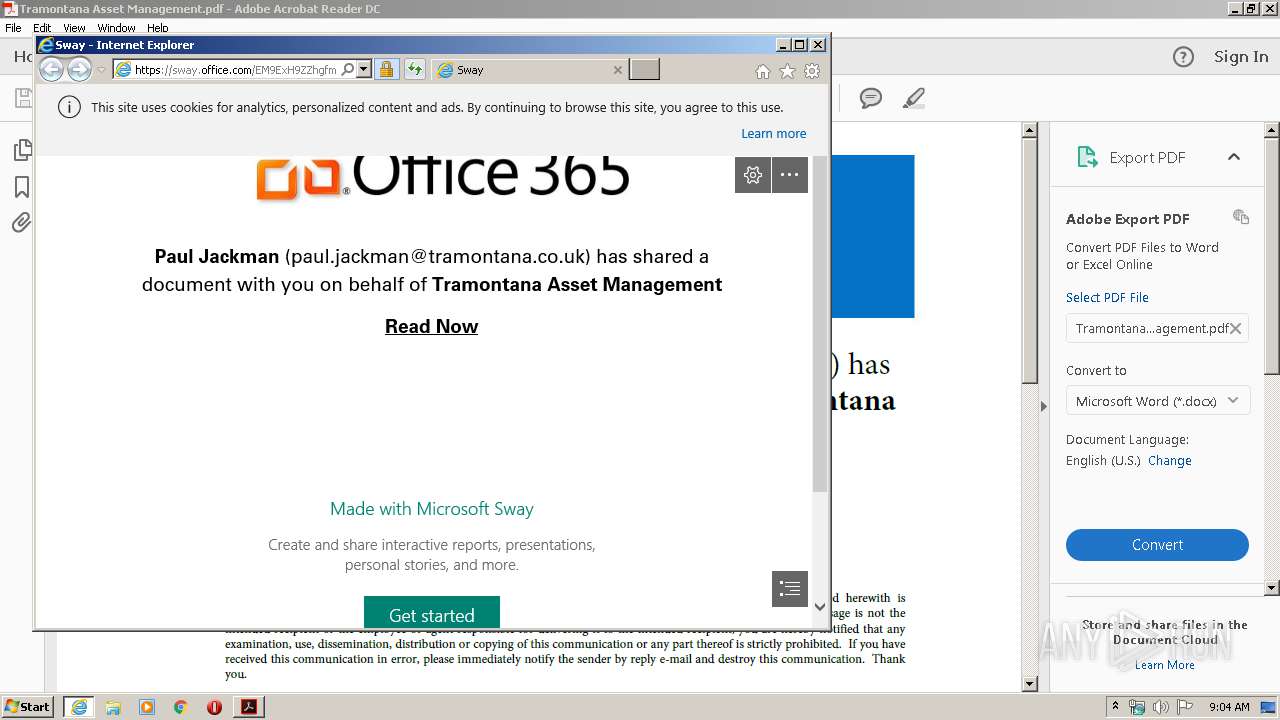
| 3264 | "C:\Program Files\Internet Explorer\iexplore.exe" https://sway.office.com/EM9ExH9ZZhgfmzdj?ref=Link | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3412 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 3468 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3264 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4052 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:15.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.27.2646 Modules
| |||||||||||||||
Total events
6 883
Read events
1 566
Write events
3 600
Delete events
1 717
Modification events
| (PID) Process: | (308) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (308) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Adobe Acrobat\DC\DiskCabs |
| Operation: | write | Name: | bForms_AdhocWorkflowBackup |
Value: 0 | |||
| (PID) Process: | (308) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (308) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\NoTimeOut |
| Operation: | write | Name: | smailto |
Value: 5900 | |||
| (PID) Process: | (3200) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION |
| Operation: | write | Name: | AcroRd32.exe |
Value: 10001 | |||
| (PID) Process: | (3264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 635450533 | |||
| (PID) Process: | (3264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30796127 | |||
| (PID) Process: | (3264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
63
Text files
98
Unknown types
56
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 308 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab810F.tmp | — | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar8110.tmp | — | |
MD5:— | SHA256:— | |||
| 308 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages | sqlite | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_BEB37ABADF39714871232B4792417E04 | binary | |
MD5:— | SHA256:— | |||
| 308 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\UserCache.bin | binary | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\StoryPage[1].css | text | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_BEB37ABADF39714871232B4792417E04 | der | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\Common[1].css | text | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\Resources[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
66
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3200 | AcroRd32.exe | GET | 304 | 2.16.186.57:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
3200 | AcroRd32.exe | GET | 304 | 2.16.186.57:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
3200 | AcroRd32.exe | GET | 304 | 2.16.186.57:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
3200 | AcroRd32.exe | GET | 304 | 2.16.186.57:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
3468 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAiIzVJfGSRETRSlgpHeuVI%3D | US | der | 1.47 Kb | whitelisted |
3104 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.trust-provider.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEENSAj%2F6qJAfE5%2Fj9OXBRE4%3D | US | der | 471 b | whitelisted |
3104 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.trust-provider.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEENSAj%2F6qJAfE5%2Fj9OXBRE4%3D | US | der | 471 b | whitelisted |
3468 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAiIzVJfGSRETRSlgpHeuVI%3D | US | der | 1.47 Kb | whitelisted |
3200 | AcroRd32.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
3104 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYdUvKOeNRji0LOHG2eICEA4422HhXCdOdLbCwzD09Uk%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3468 | iexplore.exe | 52.109.12.50:443 | sway.office.com | Microsoft Corporation | US | whitelisted |
3468 | iexplore.exe | 2.19.38.211:443 | eus-www.sway-cdn.com | Akamai International B.V. | — | whitelisted |
3264 | iexplore.exe | 2.19.38.211:443 | eus-www.sway-cdn.com | Akamai International B.V. | — | whitelisted |
3468 | iexplore.exe | 72.247.225.227:443 | uhf.microsoft.com | Akamai Technologies, Inc. | US | whitelisted |
3200 | AcroRd32.exe | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
3200 | AcroRd32.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3264 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3200 | AcroRd32.exe | 2.16.186.57:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
3104 | iexplore.exe | 104.16.126.175:443 | unpkg.com | Cloudflare Inc | US | shared |
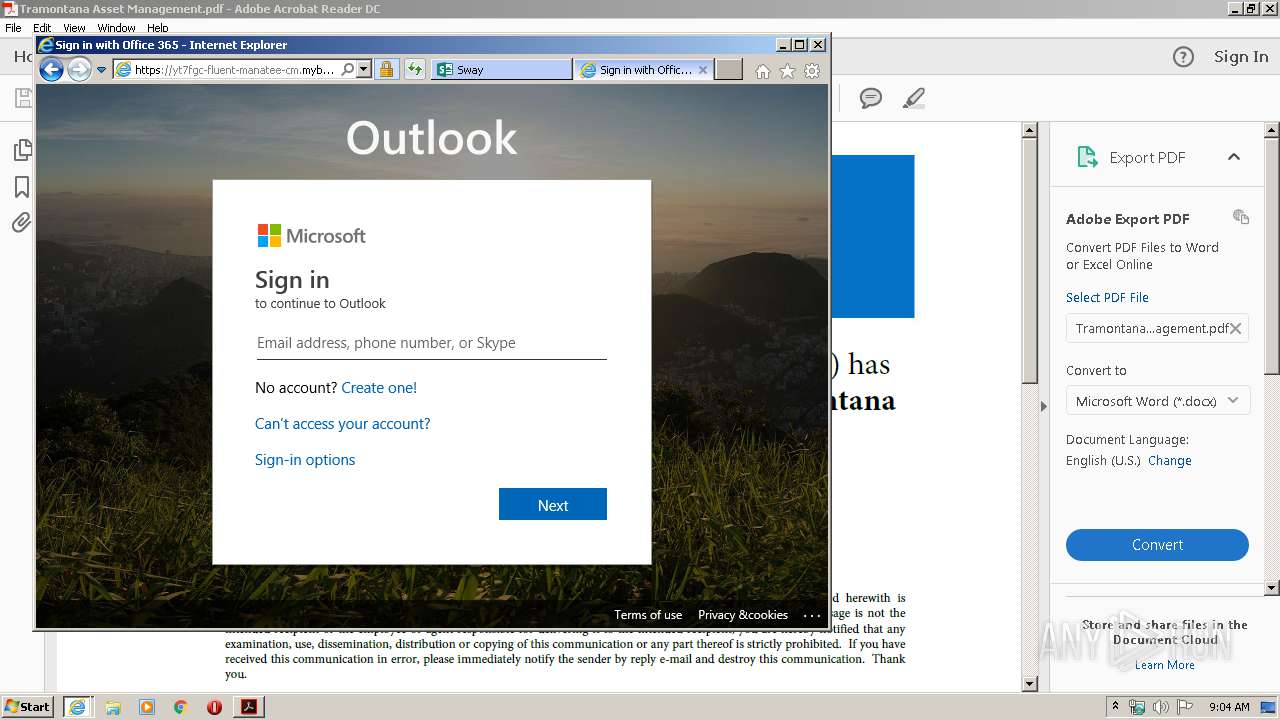
3104 | iexplore.exe | 169.62.254.79:443 | yt7fgc-fluent-manatee-cm.mybluemix.net | — | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sway.office.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
eus-www.sway-cdn.com |
| whitelisted |
uhf.microsoft.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.sway-cdn.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
yt7fgc-fluent-manatee-cm.mybluemix.net |
| suspicious |