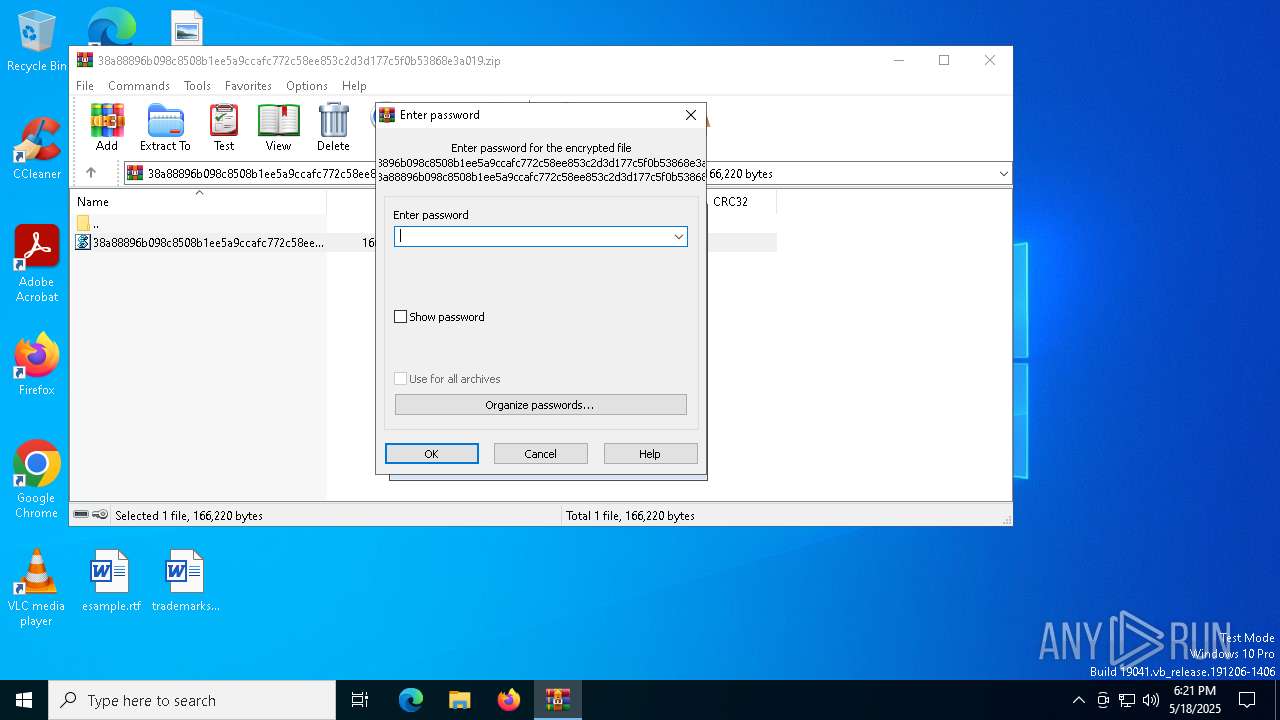
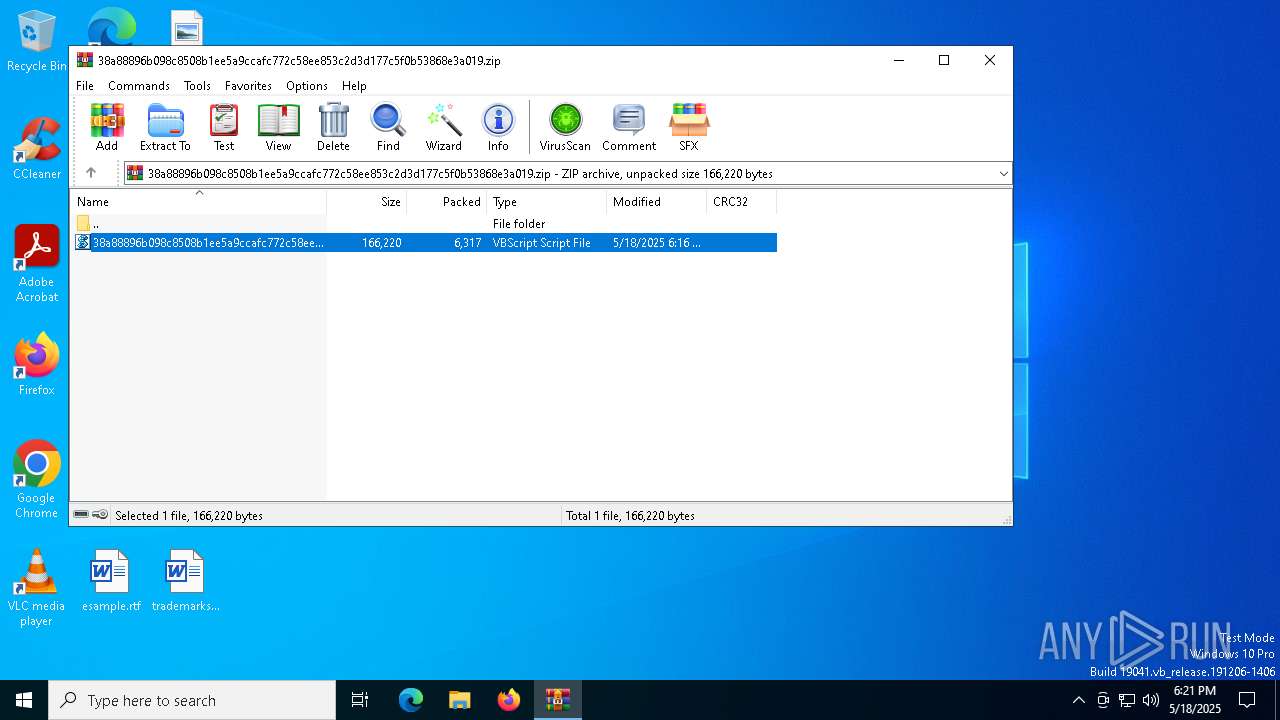
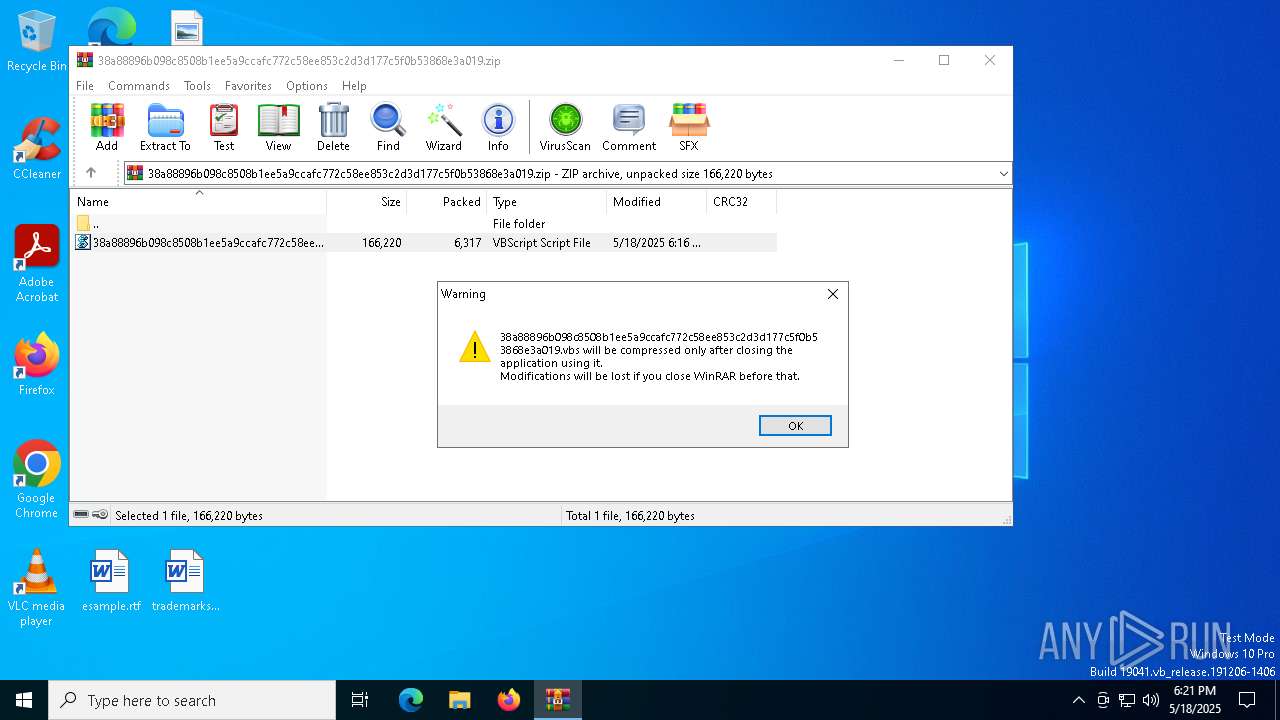
| File name: | 38a88896b098c8508b1ee5a9ccafc772c58ee853c2d3d177c5f0b53868e3a019.zip |
| Full analysis: | https://app.any.run/tasks/527d2a12-cc29-4c0b-ae34-a8890149ce74 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 18:20:50 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | DC2C64C56DE23D1117F9D3F9F092474F |
| SHA1: | 2C2BD51543C6FA84DE44EF2D91D0B9D7B415C975 |
| SHA256: | 217355AC71E74109781470A3205DC2D47817D5423915C5B6F6932E72B9486A22 |
| SSDEEP: | 192:N4DEIHLnLBXCoi5lzJTxZQchg/F7BDGsZ4p5HwGvRtBxA:urNO5Dx0XyLTRi |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1676)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 6372)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 6372)
Bypass execution policy to execute commands
- powershell.exe (PID: 4208)
- powershell.exe (PID: 6372)
Adds path to the Windows Defender exclusion list
- powershell.exe (PID: 4208)
Changes Windows Defender settings
- powershell.exe (PID: 4208)
Starts CMD.EXE for self-deleting
- powershell.exe (PID: 4208)
Create files in the Startup directory
- cmd.exe (PID: 5728)
SUSPICIOUS
The process executes VB scripts
- WinRAR.exe (PID: 1676)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1676)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 728)
Runs shell command (SCRIPT)
- wscript.exe (PID: 728)
Base64-obfuscated command line is found
- wscript.exe (PID: 728)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 728)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 6372)
- powershell.exe (PID: 4208)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 728)
- powershell.exe (PID: 5176)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 6372)
- powershell.exe (PID: 4208)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 5176)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 6372)
Application launched itself
- powershell.exe (PID: 5176)
- powershell.exe (PID: 6372)
- powershell.exe (PID: 4208)
The process executes Powershell scripts
- powershell.exe (PID: 5176)
- powershell.exe (PID: 6372)
Probably download files using WebClient
- powershell.exe (PID: 5176)
Hides errors and continues executing the command without stopping
- powershell.exe (PID: 6372)
Get information on the list of running processes
- powershell.exe (PID: 5176)
Script adds exclusion path to Windows Defender
- powershell.exe (PID: 4208)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 6972)
- cmd.exe (PID: 4220)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 5728)
- cmd.exe (PID: 4736)
- cmd.exe (PID: 6184)
- cmd.exe (PID: 2088)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4428)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 4208)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 1676)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5176)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 5176)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 4208)
Reads the software policy settings
- powershell.exe (PID: 6372)
Create files in a temporary directory
- powershell.exe (PID: 6372)
Reads security settings of Internet Explorer
- powershell.exe (PID: 6372)
Checks proxy server information
- powershell.exe (PID: 6372)
- powershell.exe (PID: 4208)
Disables trace logs
- powershell.exe (PID: 6372)
- powershell.exe (PID: 4208)
Creates a new folder
- cmd.exe (PID: 3676)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 3300)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 3300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:18 18:16:14 |
| ZipCRC: | 0xab22557f |
| ZipCompressedSize: | 6317 |
| ZipUncompressedSize: | 166220 |
| ZipFileName: | 38a88896b098c8508b1ee5a9ccafc772c58ee853c2d3d177c5f0b53868e3a019.vbs |
Total processes
168
Monitored processes
39
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | ping 127.0.0.1 -n 1 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | ping 127.0.0.1 -n 1 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIb1676.27235\38a88896b098c8508b1ee5a9ccafc772c58ee853c2d3d177c5f0b53868e3a019.vbs" | C:\Windows\System32\wscript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 896 | ping 127.0.0.1 -n C:\Users\admin\AppData\Local\Temp\Rar$DIb1676.27235\38a88896b098c8508b1ee5a9ccafc772c58ee853c2d3d177c5f0b53868e3a019.vbs | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | ping 127.0.0.1 -n 1 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | ping 127.0.0.1 -n 1 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\38a88896b098c8508b1ee5a9ccafc772c58ee853c2d3d177c5f0b53868e3a019.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1852 | cmd.exe /c del "C:\Users\admin\AppData\Local\Temp\Rar$DIb1676.27235\38a88896b098c8508b1ee5a9ccafc772c58ee853c2d3d177c5f0b53868e3a019.vbs" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | cmd.exe /c ping 127.0.0.1 -n 1 & copy "C:\Users\admin\AppData\Local\Temp\Rar$DIb1676.27235\38a88896b098c8508b1ee5a9ccafc772c58ee853c2d3d177c5f0b53868e3a019.vbs" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\38a88896b098c8508b1ee5a9ccafc772c58ee853c2d3d177c5f0b53868e3a019.vbs" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | cmd.exe /c ping 127.0.0.1 -n C:\Users\admin\AppData\Local\Temp\Rar$DIb1676.27235\38a88896b098c8508b1ee5a9ccafc772c58ee853c2d3d177c5f0b53868e3a019.vbs & del "1" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
29 107
Read events
29 097
Write events
10
Delete events
0
Modification events
| (PID) Process: | (1676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\38a88896b098c8508b1ee5a9ccafc772c58ee853c2d3d177c5f0b53868e3a019.zip | |||
| (PID) Process: | (1676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
Executable files
0
Suspicious files
2
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5176 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uap4hbx5.bri.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb1676.27235\38a88896b098c8508b1ee5a9ccafc772c58ee853c2d3d177c5f0b53868e3a019.vbs | text | |
MD5:7670B3C3B05613000677C09ACAFF72E8 | SHA256:38A88896B098C8508B1EE5A9CCAFC772C58EE853C2D3D177C5F0B53868E3A019 | |||
| 6372 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xsa53qaj.3xu.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6372 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3aybp0dx.hv3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4208 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_krfjo4ky.us4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6372 | powershell.exe | C:\Users\admin\AppData\Local\Temp\dll02.txt | text | |
MD5:F4F8C44510A36E76D5AE4AFEE447162D | SHA256:195C61ED85B683A10B2BB80189C37B15731C059D41B1647AEFAFA85EED895312 | |||
| 3332 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_41atvva3.dru.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5176 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cdcxzgnp.p4g.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4208 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_g4bz4oet.mnk.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6372 | powershell.exe | C:\Users\admin\AppData\Local\Temp\dll03.ps1 | binary | |
MD5:475C84E67521AFC2F9EC8BF91CAAE409 | SHA256:99869FDCD37C5D81B8069C7FFCBFC28236E5B81BB4E8ABA54EF52D0CBD4D5982 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
25
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2420 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2420 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.5:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.pastery.net |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |