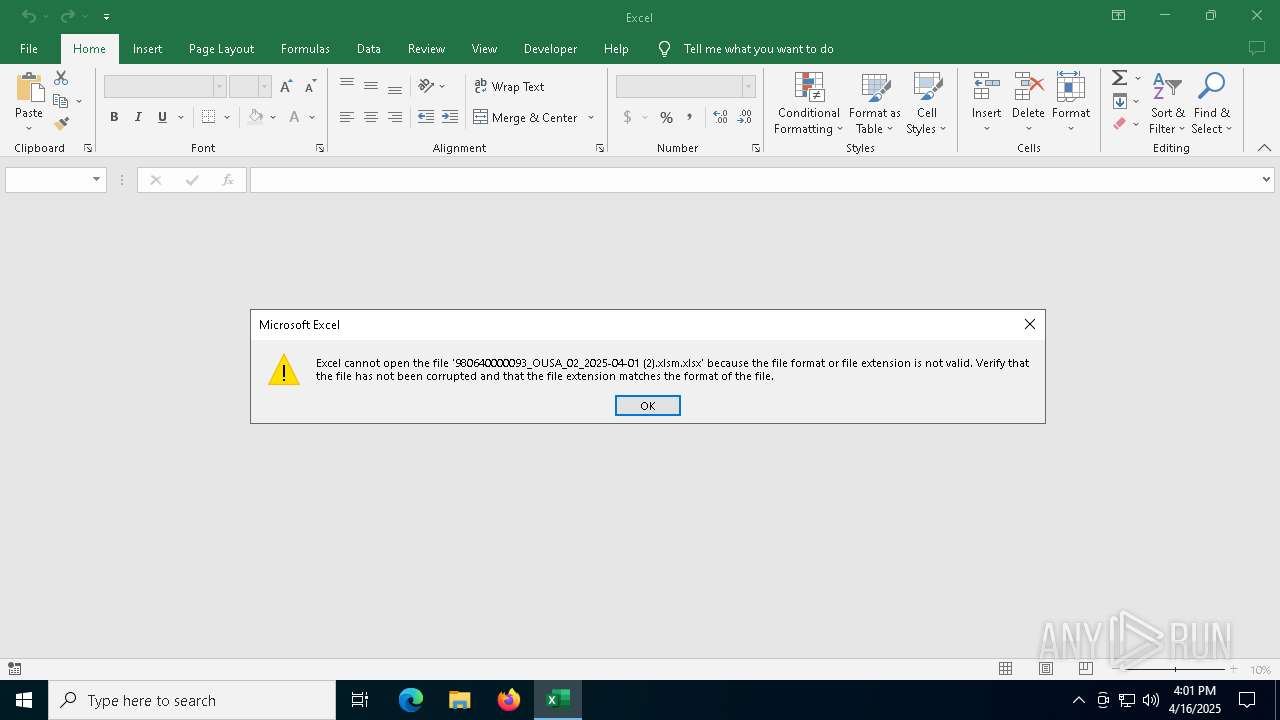
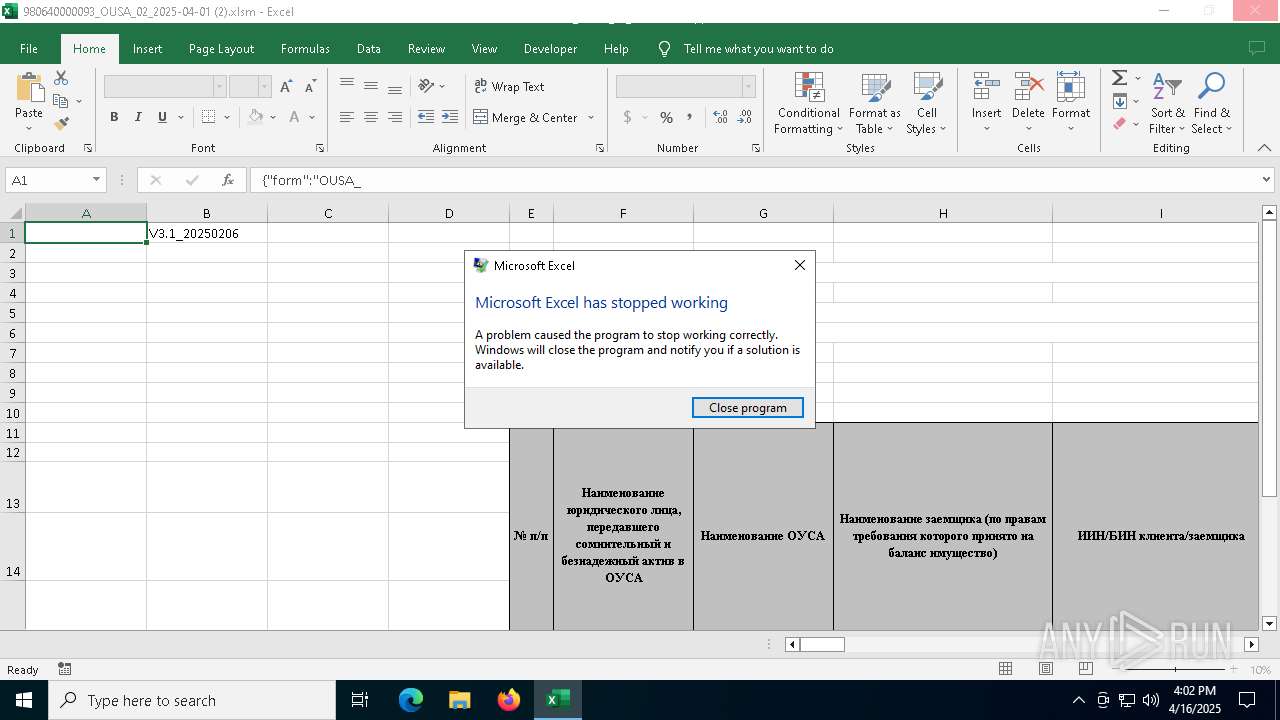
| File name: | 980640000093_OUSA_02_2025-04-01 (2).xlsm |
| Full analysis: | https://app.any.run/tasks/e2125fd2-6077-49f6-8d8c-51d27afb6c7a |
| Verdict: | Malicious activity |
| Analysis date: | April 16, 2025, 16:01:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | F55681AF94BCCEFFCDA233F123865CB0 |
| SHA1: | 17463BFCD07B2810D7133584F10E09A841AA31ED |
| SHA256: | 21663CAF3BD82844E66FFB18819FA63B657A424B68F3040AD83AD3502A7B95B0 |
| SSDEEP: | 98304:PWYWjUxoje6FNdFqTOMY4W3hKr+U/+nIgFk2FIe61ZN0m7jgQSXpLh/PDfWdERQN:OGT45R0 |
MALICIOUS
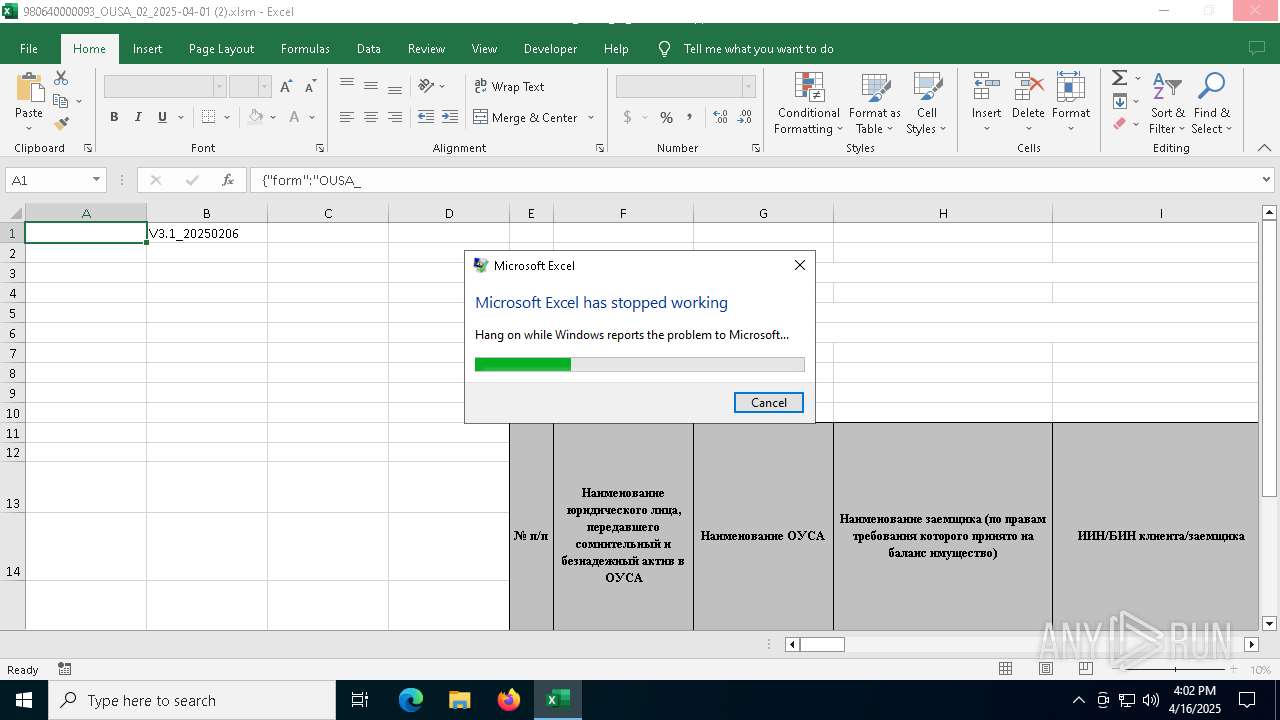
Unusual execution from MS Office
- EXCEL.EXE (PID: 2392)
SUSPICIOUS
Sets XML DOM element text (SCRIPT)
- splwow64.exe (PID: 4120)
There is functionality for taking screenshot (YARA)
- SOUNDMAN.EXE (PID: 7492)
INFO
Reads security settings of Internet Explorer
- splwow64.exe (PID: 4120)
Reads mouse settings
- EXCEL.EXE (PID: 2392)
Creates files in the program directory
- DWWIN.EXE (PID: 5008)
Manual execution by a user
- EXCEL.EXE (PID: 2392)
- DWWIN.EXE (PID: 8052)
- SOUNDMAN.EXE (PID: 7492)
- splwow64.exe (PID: 7572)
- splwow64.exe (PID: 7452)
- DWWIN.EXE (PID: 6268)
- DWWIN.EXE (PID: 7976)
Checks proxy server information
- DWWIN.EXE (PID: 5008)
- slui.exe (PID: 7448)
Reads Microsoft Office registry keys
- DWWIN.EXE (PID: 5008)
Creates files or folders in the user directory
- DWWIN.EXE (PID: 5008)
Reads the software policy settings
- DWWIN.EXE (PID: 5008)
- slui.exe (PID: 7448)
Checks supported languages
- SOUNDMAN.EXE (PID: 7492)
Compiled with Borland Delphi (YARA)
- SOUNDMAN.EXE (PID: 7492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlam | | | Excel Macro-enabled Open XML add-in (42.4) |
|---|---|---|
| .xlsm | | | Excel Microsoft Office Open XML Format document (with Macro) (29.2) |
| .xlsx | | | Excel Microsoft Office Open XML Format document (17.3) |
| .zip | | | Open Packaging Conventions container (8.9) |
| .zip | | | ZIP compressed archive (2) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:16 16:13:08 |
| ZipCRC: | 0x9ea46726 |
| ZipCompressedSize: | 235 |
| ZipUncompressedSize: | 603 |
| ZipFileName: | _rels/.rels |
XML
| Application: | Microsoft Excel |
|---|---|
| DocSecurity: | None |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | form |
| Company: | SPecialiST RePack |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16.03 |
| CreateDate: | 2017:04:11 06:35:05Z |
| LastModifiedBy: | Бауыржан Байшолаков |
| LastPrinted: | 2017:04:24 09:44:10Z |
| ModifyDate: | 2025:02:06 18:48:38Z |
XMP
| Creator: | Бауыржан Байшолаков |
|---|
Total processes
152
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2392 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\Desktop\980640000093_OUSA_02_2025-04-01 (2).xlsm" | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 4 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 4120 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5008 | C:\WINDOWS\system32\dwwin.exe -x -s 4100 | C:\Windows\System32\DWWIN.EXE | EXCEL.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Error Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6268 | "C:\Windows\System32\DWWIN.EXE" | C:\Windows\System32\DWWIN.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Error Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7208 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\Desktop\980640000093_OUSA_02_2025-04-01 (2).xlsm.xlsx" | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7388 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7448 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7452 | "C:\Windows\splwow64.exe" | C:\Windows\splwow64.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7492 | "C:\Windows\SOUNDMAN.EXE" | C:\Windows\SOUNDMAN.EXE | — | explorer.exe | |||||||||||
User: admin Company: Realtek Semiconductor Corp. Integrity Level: MEDIUM Description: Realtek Sound Manager Version: 6, 0, 0, 5 Modules
| |||||||||||||||
| 7572 | "C:\Windows\splwow64.exe" | C:\Windows\splwow64.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Print driver host for applications Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 480
Read events
13 174
Write events
270
Delete events
36
Modification events
| (PID) Process: | (7208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (7208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\EXCEL\7208 |
| Operation: | write | Name: | 0 |
Value: 0B0E104FF75D8D3AF69A448E98ACCE96E54FDA230046D0FB86978DDDEBED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511A838D2120965007800630065006C002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (7208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (7208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (7208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (7208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (7208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (7208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (7208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
1
Suspicious files
31
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Diagnostics\EXCEL\App1744819293217080600_8D5DF74F-F63A-449A-8E98-ACCE96E54FDA.log | — | |
MD5:— | SHA256:— | |||
| 7208 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:343BDEF4552D4A0339E076134267EB95 | SHA256:9E975C64391FC625E42D3080691922C254C74C58D5056C8B00ADFA68F72F02AA | |||
| 7208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\0039A3B8-AC8F-438A-8A80-004F885E813E | xml | |
MD5:95C2E36BF768E162F11E5771F2D93BEF | SHA256:78F59AAFE1DBCC0E997C83143B616FABFC6D2C9D517BA68A5244AED668A1835B | |||
| 7208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Floodgate\Excel.Settings.json | binary | |
MD5:E4E83F8123E9740B8AA3C3DFA77C1C04 | SHA256:6034F27B0823B2A6A76FE296E851939FD05324D0AF9D55F249C79AF118B0EB31 | |||
| 7208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:AE9EB83EA7DAEB0C60114F8F66EBBD34 | SHA256:AE34326D5B930660A85BFFB5ADC8AE6FD3F919B0D7D074B67B3A703906A67A7D | |||
| 7208 | EXCEL.EXE | C:\Users\admin\Desktop\~$980640000093_OUSA_02_2025-04-01 (2).xlsm.xlsx | binary | |
MD5:21E5D64E6DD2C94C577A61B0A25DE7A4 | SHA256:657F0604A7C1F6CFDC4E8A224F59BD6E1900A4A4DD8B3F61A20F67DEBE41F209 | |||
| 7208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Floodgate\Excel.GovernedChannelStates.json | binary | |
MD5:F5A0FBF6DB5254A1E882E09C78B6A0EB | SHA256:C3338F7C5CD465788643D4A5D5EB920A8411DBF2A1C9CDC8EFA361D277E3AC49 | |||
| 7208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Floodgate\Excel.CampaignStates.json | binary | |
MD5:F1B59332B953B3C99B3C95A44249C0D2 | SHA256:138E49660D259061D8152137ABD8829ACDFB78B69179890BEB489FE3FFE23E0C | |||
| 7208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Floodgate\Excel.SurveyEventActivityStats.json | binary | |
MD5:6CA4960355E4951C72AA5F6364E459D5 | SHA256:88301F0B7E96132A2699A8BCE47D120855C7F0A37054540019E3204D6BCBABA3 | |||
| 7208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Floodgate\Excel.SurveyHistoryStats.json | binary | |
MD5:6CA4960355E4951C72AA5F6364E459D5 | SHA256:88301F0B7E96132A2699A8BCE47D120855C7F0A37054540019E3204D6BCBABA3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
33
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.191:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7208 | EXCEL.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6808 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6808 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5008 | DWWIN.EXE | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5008 | DWWIN.EXE | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.191:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7208 | EXCEL.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |