| File name: | NPP.exe |
| Full analysis: | https://app.any.run/tasks/6256d929-8818-451f-b81b-6b44e480b335 |
| Verdict: | Malicious activity |
| Analysis date: | March 01, 2024, 09:10:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F3971EE1530693E4CAD9F4CEC4855C9C |
| SHA1: | 4C8BBF48B1295BF46B8DC1C4C15FD825BE98E078 |
| SHA256: | 213F35138BD49A02C744D5A502B215DD65F498063F4BC684DCE2A87C4CC32881 |
| SSDEEP: | 98304:8L9fwcp/iJcehECEkEGEmI64OAiORl8yNsptaekigvELWWP4tVQAL3XZ7DkdVq4P:ZULM |
MALICIOUS
Drops the executable file immediately after the start
- NPP.exe (PID: 3668)
SUSPICIOUS
Reads security settings of Internet Explorer
- NPP.exe (PID: 3668)
- NPP.exe (PID: 1740)
Reads the Internet Settings
- NPP.exe (PID: 3668)
- NPP.exe (PID: 1740)
- WMIC.exe (PID: 3072)
- WMIC.exe (PID: 2488)
- WMIC.exe (PID: 3228)
- WMIC.exe (PID: 2636)
Reads Internet Explorer settings
- NPP.exe (PID: 3668)
- NPP.exe (PID: 1740)
Reads settings of System Certificates
- NPP.exe (PID: 3668)
- NPP.exe (PID: 1740)
Checks Windows Trust Settings
- NPP.exe (PID: 3668)
- NPP.exe (PID: 1740)
Uses WMIC.EXE to obtain desktop monitor information
- NPP.exe (PID: 3668)
- NPP.exe (PID: 1740)
Reads Microsoft Outlook installation path
- NPP.exe (PID: 1740)
- NPP.exe (PID: 3668)
Uses WMIC.EXE to obtain CPU information
- NPP.exe (PID: 1740)
- NPP.exe (PID: 3668)
Searches for installed software
- NPP.exe (PID: 1740)
- NPP.exe (PID: 3668)
INFO
Checks supported languages
- NPP.exe (PID: 3668)
- NPP.exe (PID: 1740)
Creates files in the program directory
- NPP.exe (PID: 3668)
Manual execution by a user
- NPP.exe (PID: 1740)
Creates files or folders in the user directory
- NPP.exe (PID: 3668)
- NPP.exe (PID: 1740)
Reads the computer name
- NPP.exe (PID: 3668)
- NPP.exe (PID: 1740)
Checks proxy server information
- NPP.exe (PID: 3668)
- NPP.exe (PID: 1740)
Reads the machine GUID from the registry
- NPP.exe (PID: 3668)
- NPP.exe (PID: 1740)
Reads the software policy settings
- NPP.exe (PID: 1740)
- NPP.exe (PID: 3668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (3.6) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (1.6) |
| .exe | | | DOS Executable Generic (1.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:11:24 02:45:42+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 3688960 |
| InitializedDataSize: | 1426944 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x17cf2a |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.21.1.202 |
| ProductVersionNumber: | 1.21.1.202 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
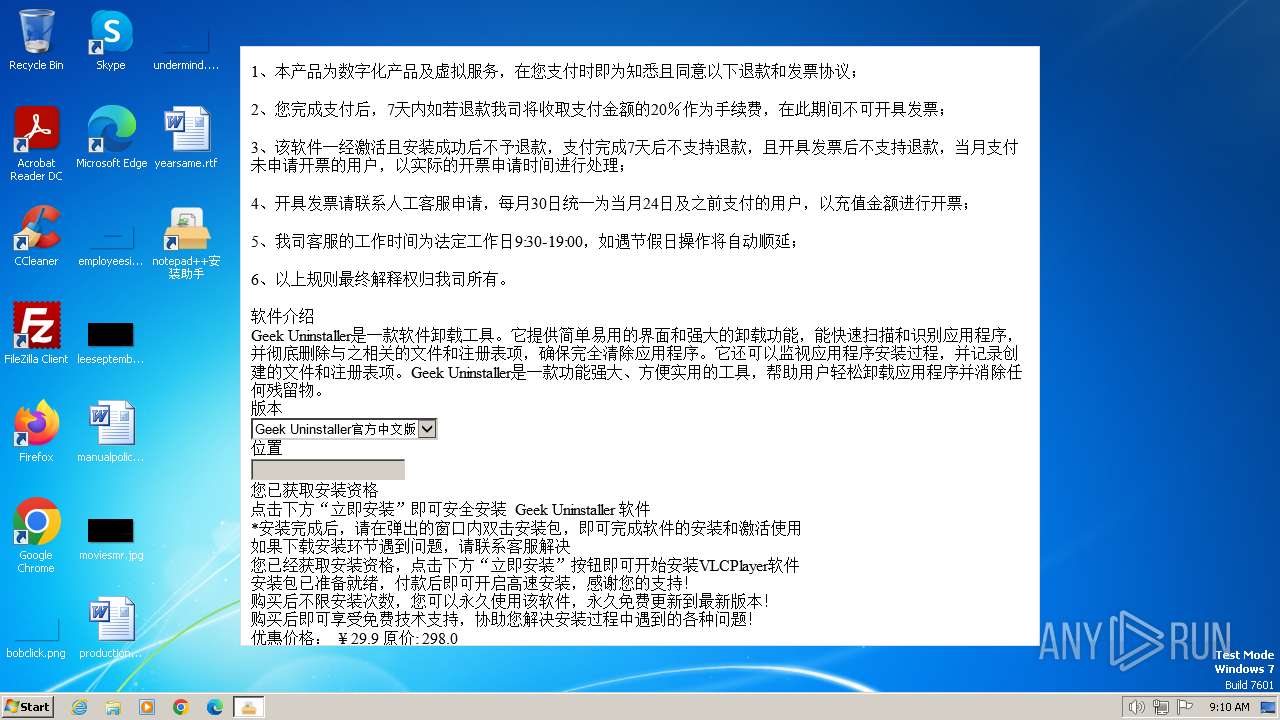
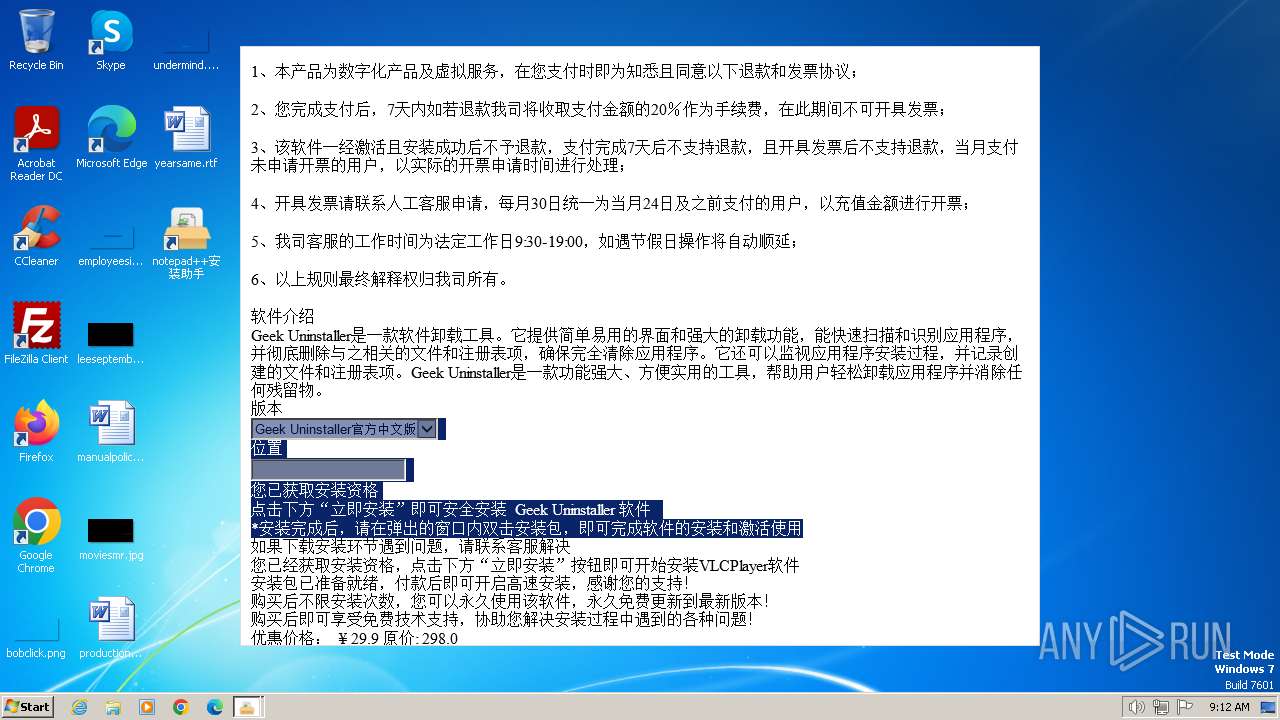
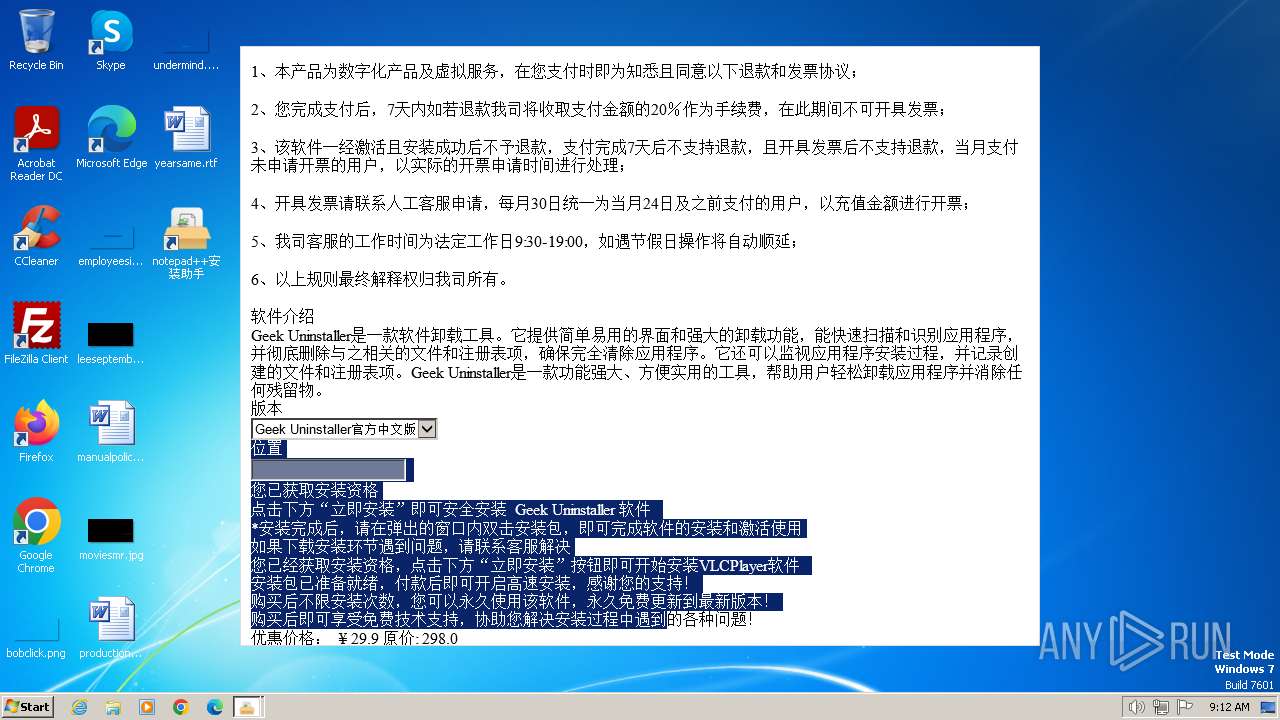
| FileDescription: | notepad++DownLoader |
| FileVersion: | 1.21.1.202 |
| InternalName: | notepad++DownLoader |
| LegalCopyright: | Copyright (C) 2011 |
| OriginalFileName: | notepad++DownLoader |
| ProductName: | notepad++DownLoader |
| ProductVersion: | 1.21.1.202 |
Total processes
52
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1740 | "C:\Users\admin\AppData\Local\Temp\NPP.exe" | C:\Users\admin\AppData\Local\Temp\NPP.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: notepad++DownLoader Exit code: 0 Version: 1.21.1.202 Modules
| |||||||||||||||
| 2488 | wmic cpu get Name | C:\Windows\System32\wbem\WMIC.exe | — | NPP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2636 | wmic cpu get Name | C:\Windows\System32\wbem\WMIC.exe | — | NPP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3072 | wmic desktopmonitor get Name, ScreenHeight, ScreenWidth, PixelsPerXLogicalInch, PixelsPerYLogicalInch /format:csv | C:\Windows\System32\wbem\WMIC.exe | — | NPP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3228 | wmic desktopmonitor get Name, ScreenHeight, ScreenWidth, PixelsPerXLogicalInch, PixelsPerYLogicalInch /format:csv | C:\Windows\System32\wbem\WMIC.exe | — | NPP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3668 | "C:\Users\admin\AppData\Local\Temp\NPP.exe" | C:\Users\admin\AppData\Local\Temp\NPP.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: notepad++DownLoader Exit code: 0 Version: 1.21.1.202 Modules
| |||||||||||||||
Total events
15 967
Read events
15 679
Write events
239
Delete events
49
Modification events
| (PID) Process: | (3668) NPP.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3668) NPP.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3668) NPP.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3668) NPP.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3668) NPP.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3668) NPP.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (3668) NPP.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (3668) NPP.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (3668) NPP.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (3668) NPP.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005C010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
4
Text files
2
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3668 | NPP.exe | C:\Users\admin\Desktop\notepad++安装助手.lnk | binary | |
MD5:0457B1898C625D7771E5BDCC9EEC2BF9 | SHA256:3F4E89D7A279A6CC13D94D5DE1AF5B2760C99B140DBEEAB3BF0E71E60EF90544 | |||
| 3668 | NPP.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:57425C6C130EADC16729D33EDBB53772 | SHA256:1A5896413EC3A6ACE24DA3C72E0BA2757AEC7CDF3BFDA66F33F1BAECEF968593 | |||
| 3668 | NPP.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\14561BF7422BB6F70A9CB14F5AA8A7DA_FFD8C9AD4478E07ED32B6078514A3293 | binary | |
MD5:A72CBC8B5620CD40EB1E19D8B2E2E3B8 | SHA256:9975418E45312B69ACE992B7F35F4E9AA1A056F66BA9F40511FB50B20AAB8D4D | |||
| 3668 | NPP.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\GWZRZI4D.htm | html | |
MD5:2BE0302D39C10E779453DD726329AE65 | SHA256:6D77E8CB7CB0C6E703C4C0E75DD64B7FB78E5DCED02E530CC48978FD08FE1F37 | |||
| 3668 | NPP.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_23FFFDCAABB8E63694AD1202ED02BF57 | binary | |
MD5:EA37557E180B7B175DD56D6DD70C864F | SHA256:98C82391867011D57EAB7BC4E8CE650F438F0486471F4C989E764CD961222C01 | |||
| 1740 | NPP.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\VX6DR34M.htm | html | |
MD5:2BE0302D39C10E779453DD726329AE65 | SHA256:6D77E8CB7CB0C6E703C4C0E75DD64B7FB78E5DCED02E530CC48978FD08FE1F37 | |||
| 3668 | NPP.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\14561BF7422BB6F70A9CB14F5AA8A7DA_FFD8C9AD4478E07ED32B6078514A3293 | binary | |
MD5:36BAFDFF341E4D70BA5C2EBE54F4F145 | SHA256:EA1484E0D3821D2AA42AE22CC3BD64520B9926C8827F6CD0BF027C137DB50F1A | |||
| 3668 | NPP.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_23FFFDCAABB8E63694AD1202ED02BF57 | binary | |
MD5:1638346B708D3E70E075D215E05B3EE2 | SHA256:3440EA235FFC8AEA047E07946F2B986662F212964C71899DB705DF590411AF8C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
9
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3668 | NPP.exe | GET | 304 | 23.32.238.168:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f298ca30347c3779 | unknown | — | — | unknown |
3668 | NPP.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAoFmyX1Sz2HlMxmMUd1OKM%3D | unknown | binary | 471 b | unknown |
3668 | NPP.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQlOydjtpho0%2Bholo77zGjGxETUEQQU8JyF%2FaKffY%2FJaLvV1IlNHb7TkP8CEAZR96tXTGFTGvnYN5aT5lc%3D | unknown | binary | 727 b | unknown |
1080 | svchost.exe | GET | 200 | 23.32.238.201:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?89bca2e7018c82c0 | unknown | compressed | 67.5 Kb | unknown |
1080 | svchost.exe | GET | 304 | 23.32.238.201:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1b8fee253118cbef | unknown | compressed | 67.5 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3668 | NPP.exe | 58.218.215.168:443 | dlnpp.whrszx.com | Chinanet | CN | unknown |
3668 | NPP.exe | 23.32.238.168:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3668 | NPP.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 23.32.238.201:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1740 | NPP.exe | 58.218.215.168:443 | dlnpp.whrszx.com | Chinanet | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dlnpp.whrszx.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
sta-ali-dlwww.whrszx.com |
| unknown |
www.baidu.com |
| whitelisted |