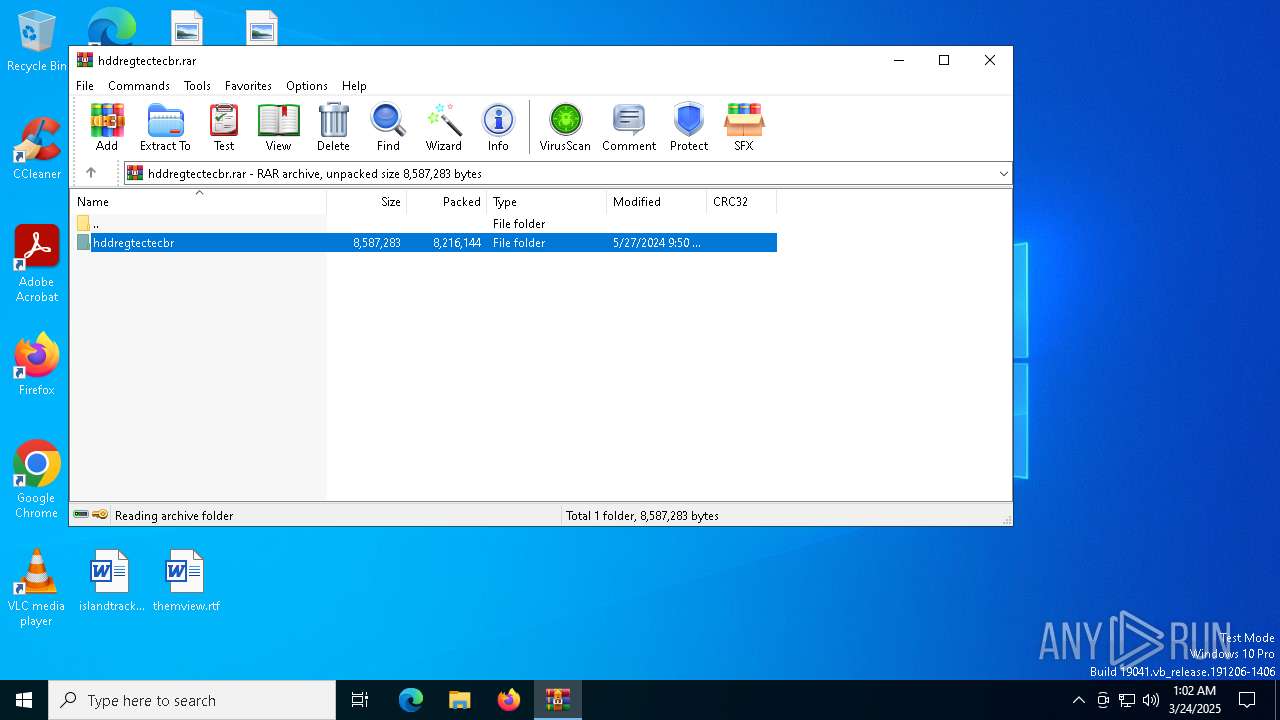
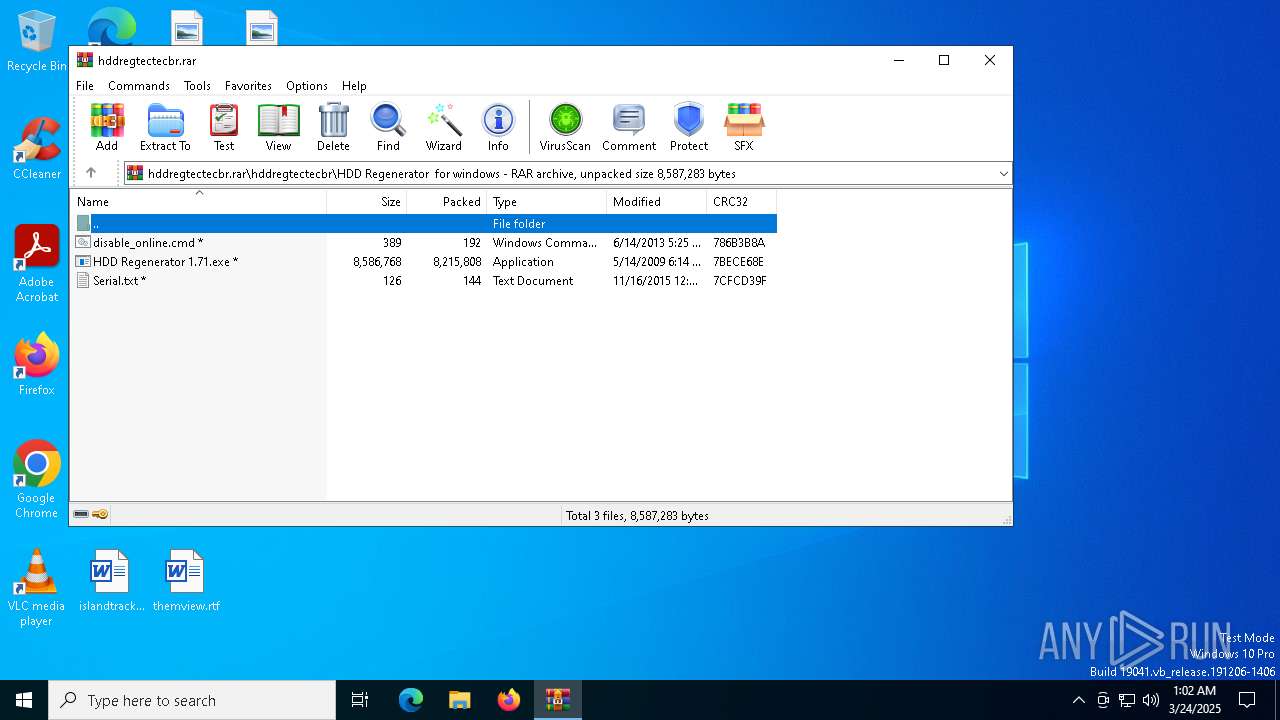
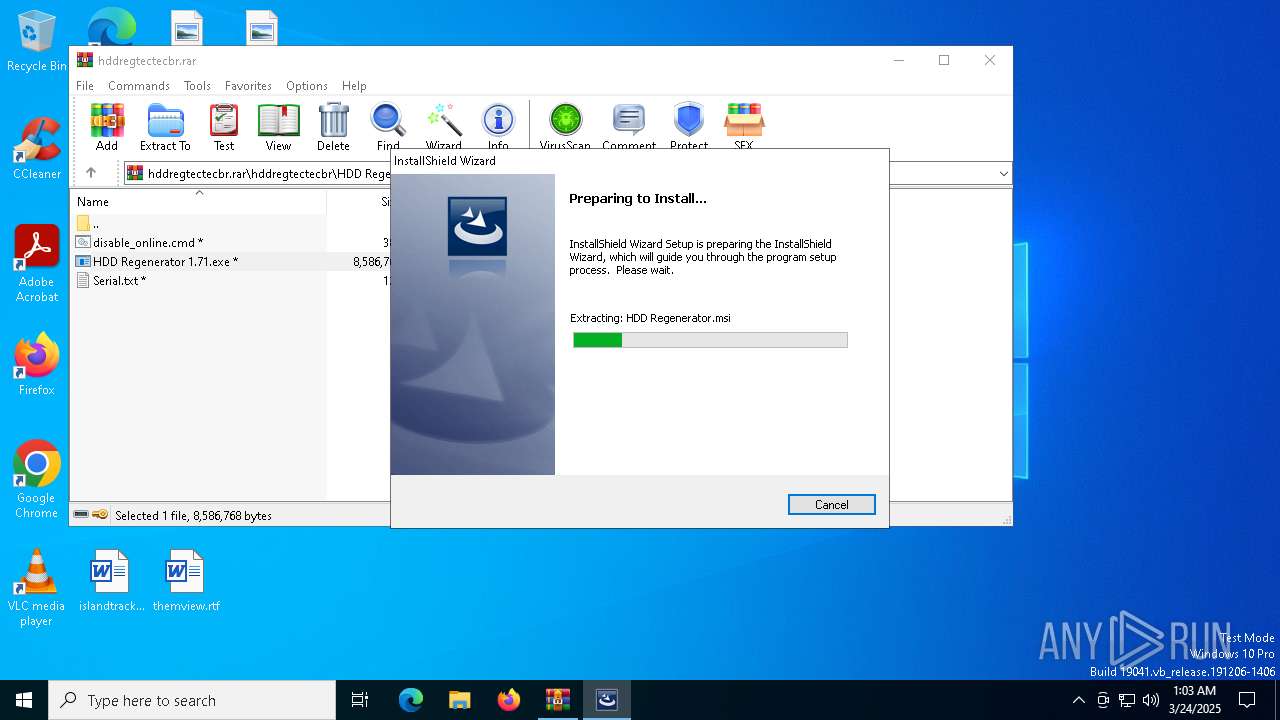
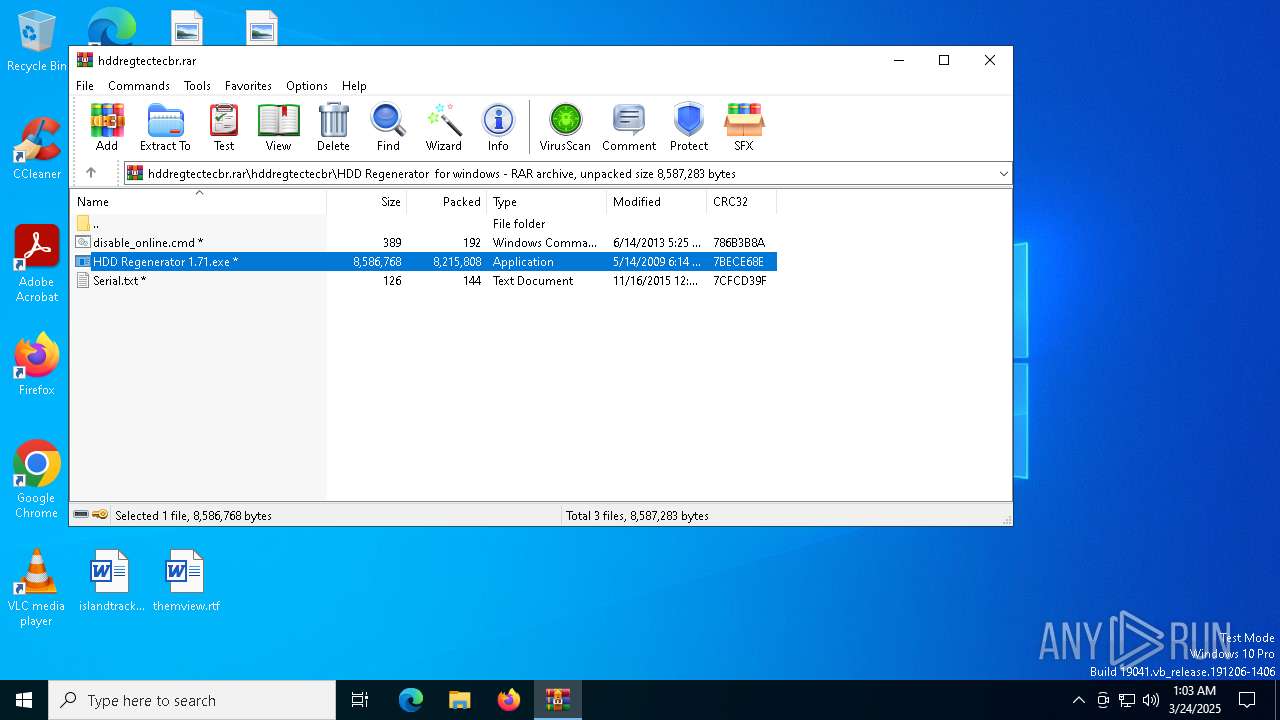
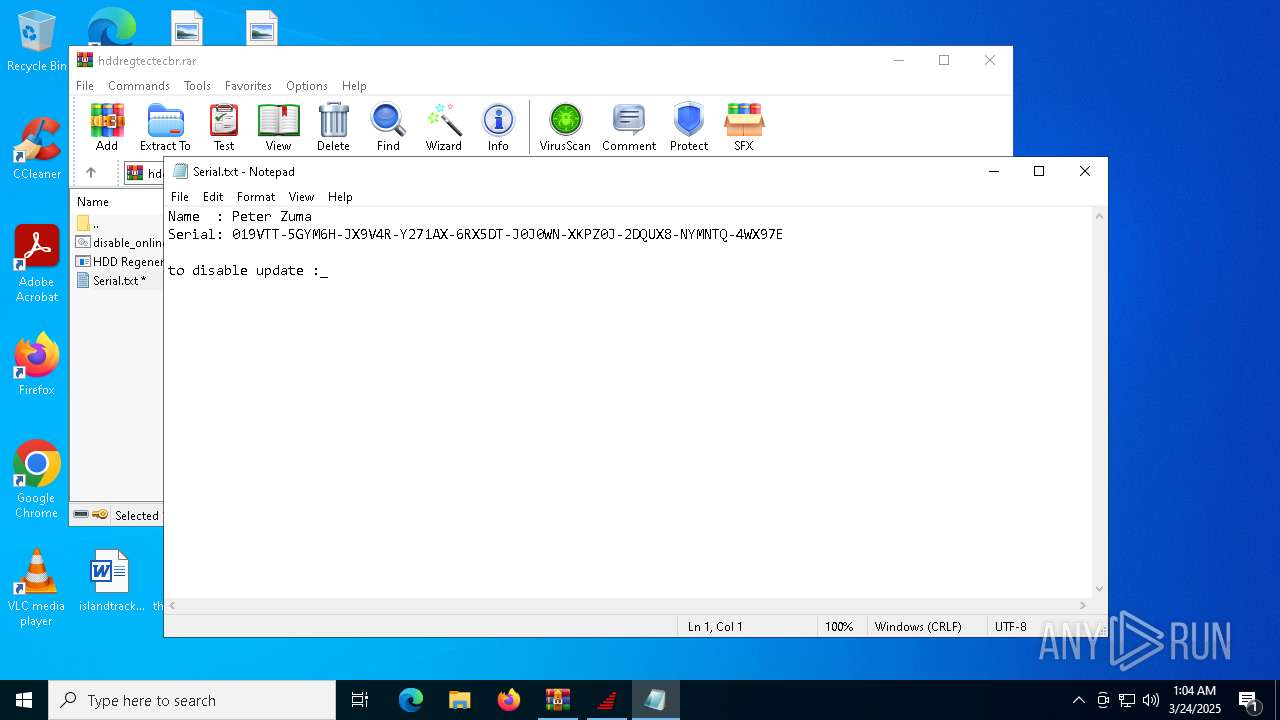
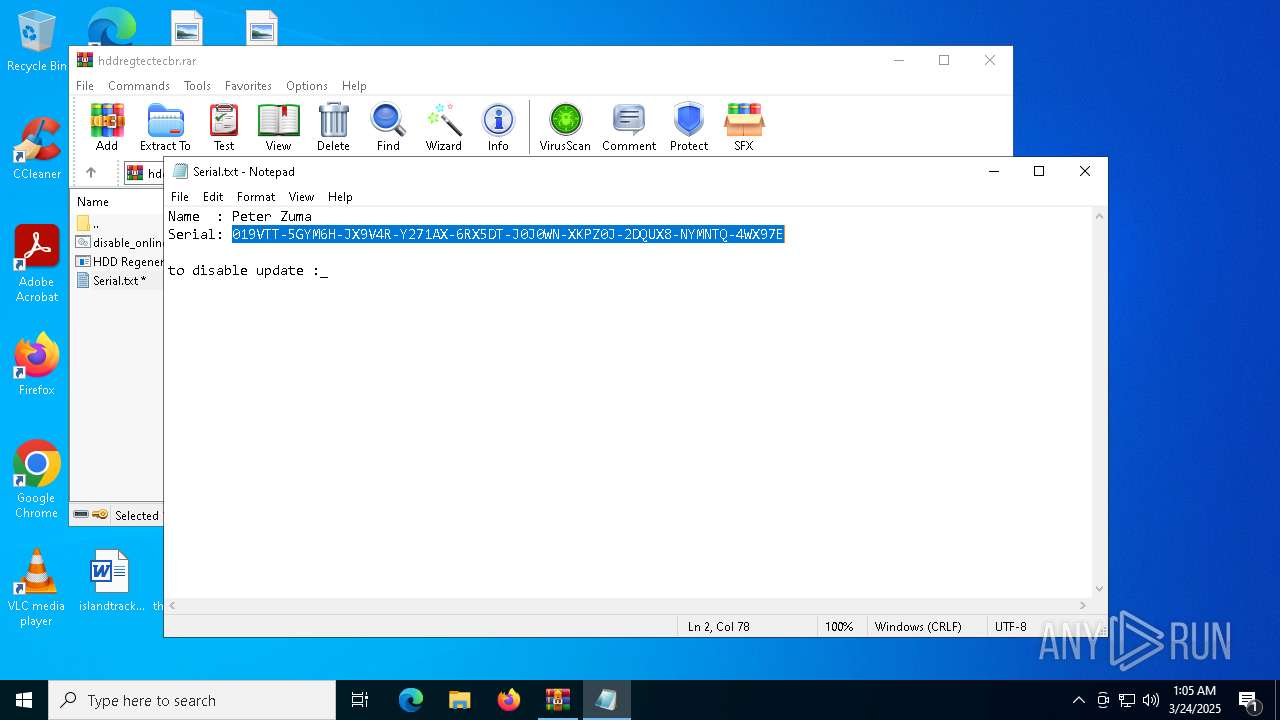
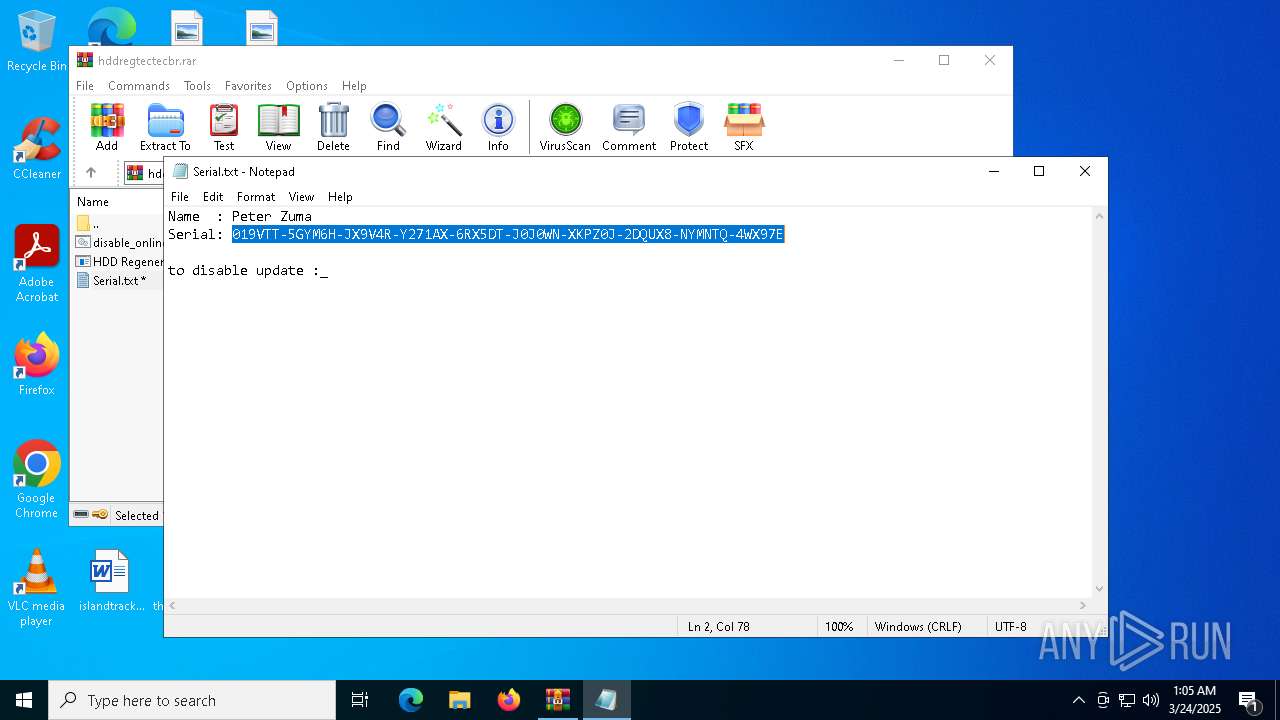
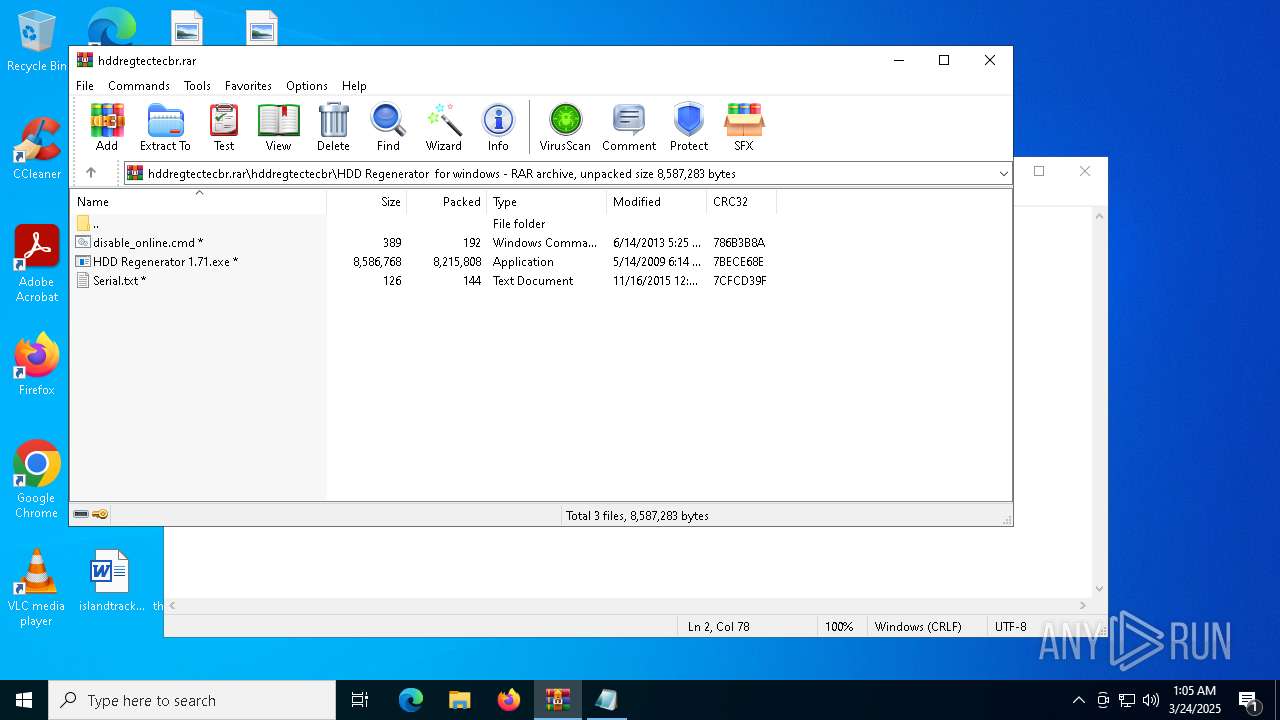
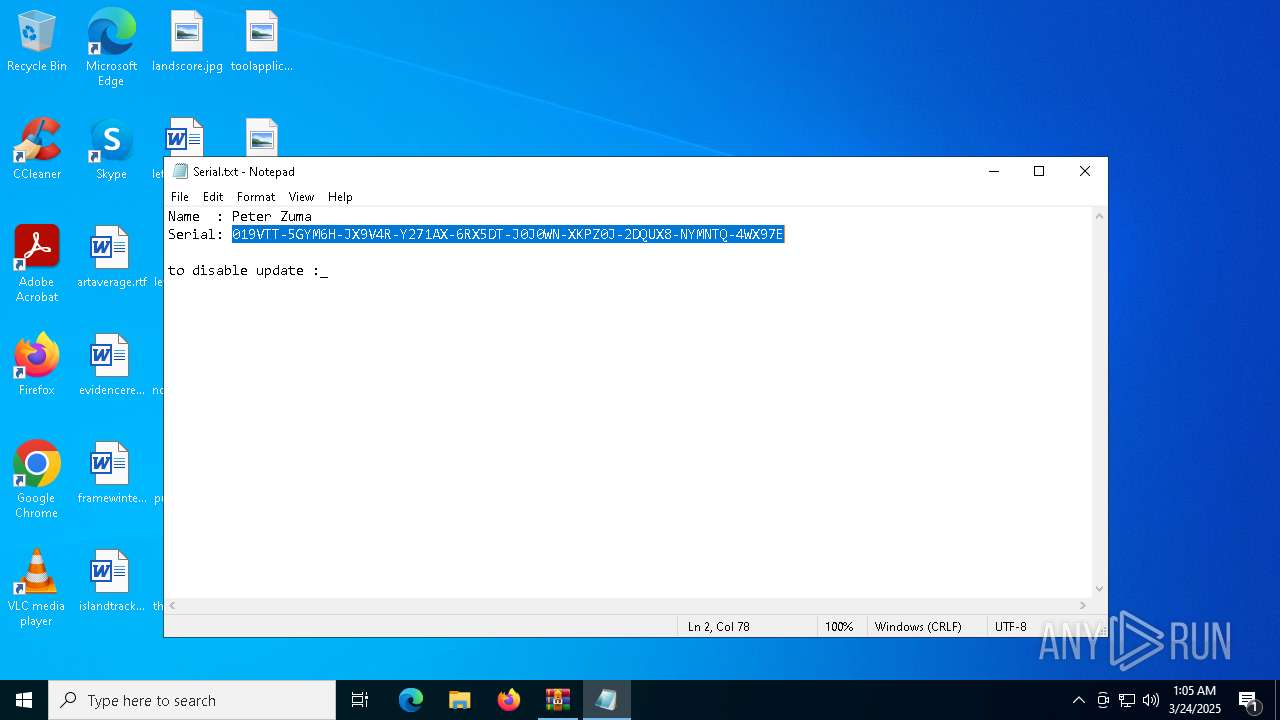
| File name: | hddregtectecbr.rar |
| Full analysis: | https://app.any.run/tasks/f70eeb2d-561d-4612-b2d6-7b1aeec67e27 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 01:02:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | DFF04004F3DF606B307F49F190A12890 |
| SHA1: | 0253E4736F53921581F19CA828BEDF921B18FBFC |
| SHA256: | 212F9E268EAC298460769A6A27546F4894B5A871251FC468859F70D8339FA751 |
| SSDEEP: | 98304:vg6zJBvuaM4Pk8XNtVHTiJVfiAaMJtK7hRvOSDrftYNWqiIiiBLUqYROnh6yyg02:b6eKjpxhukbYEo74NJ |
MALICIOUS
Executing a file with an untrusted certificate
- HDD Regenerator 1.71.exe (PID: 6268)
- HDD Regenerator 1.71.exe (PID: 1052)
- HDD Regenerator.exe (PID: 6964)
- HDD Regenerator.exe (PID: 5956)
- HDD Regenerator.exe (PID: 5556)
- HDD Regenerator.exe (PID: 4152)
- HDD Regenerator.exe (PID: 6256)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6488)
- ShellExperienceHost.exe (PID: 3304)
- msiexec.exe (PID: 2152)
- HDD Regenerator.exe (PID: 5956)
- HDD Regenerator.exe (PID: 5556)
Adds/modifies Windows certificates
- msiexec.exe (PID: 5304)
There is functionality for taking screenshot (YARA)
- HDD Regenerator 1.71.exe (PID: 6268)
Executes as Windows Service
- VSSVC.exe (PID: 3176)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 1388)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 1388)
- HDD Regenerator.exe (PID: 5956)
Application launched itself
- HDD Regenerator.exe (PID: 6964)
- HDD Regenerator.exe (PID: 6256)
- hddreg.exe (PID: 2140)
Detected use of alternative data streams (AltDS)
- HDD Regenerator.exe (PID: 5956)
- HDD Regenerator.exe (PID: 5556)
- hddreg.exe (PID: 1300)
Reads the BIOS version
- HDD Regenerator.exe (PID: 5956)
- HDD Regenerator.exe (PID: 5556)
- hddreg.exe (PID: 1300)
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 6488)
Reads Internet Explorer settings
- HDD Regenerator.exe (PID: 5556)
Reads Microsoft Outlook installation path
- HDD Regenerator.exe (PID: 5556)
INFO
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 5256)
- BackgroundTransferHost.exe (PID: 1600)
- BackgroundTransferHost.exe (PID: 208)
- BackgroundTransferHost.exe (PID: 5756)
- BackgroundTransferHost.exe (PID: 1852)
- msiexec.exe (PID: 5304)
- notepad.exe (PID: 5304)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 5256)
- slui.exe (PID: 2136)
- msiexec.exe (PID: 1388)
- msiexec.exe (PID: 5304)
- slui.exe (PID: 4244)
- HDD Regenerator.exe (PID: 5556)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 5256)
- HDD Regenerator 1.71.exe (PID: 6268)
- msiexec.exe (PID: 5304)
- HDD Regenerator.exe (PID: 5556)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 5256)
- msiexec.exe (PID: 5304)
- slui.exe (PID: 4244)
- HDD Regenerator.exe (PID: 5956)
- HDD Regenerator.exe (PID: 5556)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6488)
- msiexec.exe (PID: 5304)
- msiexec.exe (PID: 1388)
Checks supported languages
- HDD Regenerator 1.71.exe (PID: 6268)
- msiexec.exe (PID: 1388)
- msiexec.exe (PID: 2152)
- ShellExperienceHost.exe (PID: 3304)
- HDD Regenerator.exe (PID: 6964)
- HDD Regenerator.exe (PID: 5956)
- HDD Regenerator.exe (PID: 6256)
- HDD Regenerator.exe (PID: 5556)
- hddreg.exe (PID: 1300)
- hddreg.exe (PID: 2140)
The sample compiled with english language support
- WinRAR.exe (PID: 6488)
- msiexec.exe (PID: 5304)
- msiexec.exe (PID: 1388)
Reads the computer name
- HDD Regenerator 1.71.exe (PID: 6268)
- msiexec.exe (PID: 2152)
- msiexec.exe (PID: 1388)
- ShellExperienceHost.exe (PID: 3304)
- HDD Regenerator.exe (PID: 5956)
- HDD Regenerator.exe (PID: 5556)
- hddreg.exe (PID: 1300)
Create files in a temporary directory
- HDD Regenerator 1.71.exe (PID: 6268)
Manages system restore points
- SrTasks.exe (PID: 4304)
Reads the machine GUID from the registry
- msiexec.exe (PID: 1388)
- HDD Regenerator.exe (PID: 5556)
Process checks computer location settings
- msiexec.exe (PID: 2152)
Creates a software uninstall entry
- msiexec.exe (PID: 1388)
Creates files in the program directory
- HDD Regenerator.exe (PID: 5956)
- HDD Regenerator.exe (PID: 5556)
- hddreg.exe (PID: 1300)
Compiled with Borland Delphi (YARA)
- slui.exe (PID: 4244)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6488)
Manual execution by a user
- HDD Regenerator.exe (PID: 6256)
- HDD Regenerator.exe (PID: 4152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|
Total processes
170
Monitored processes
27
Malicious processes
8
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
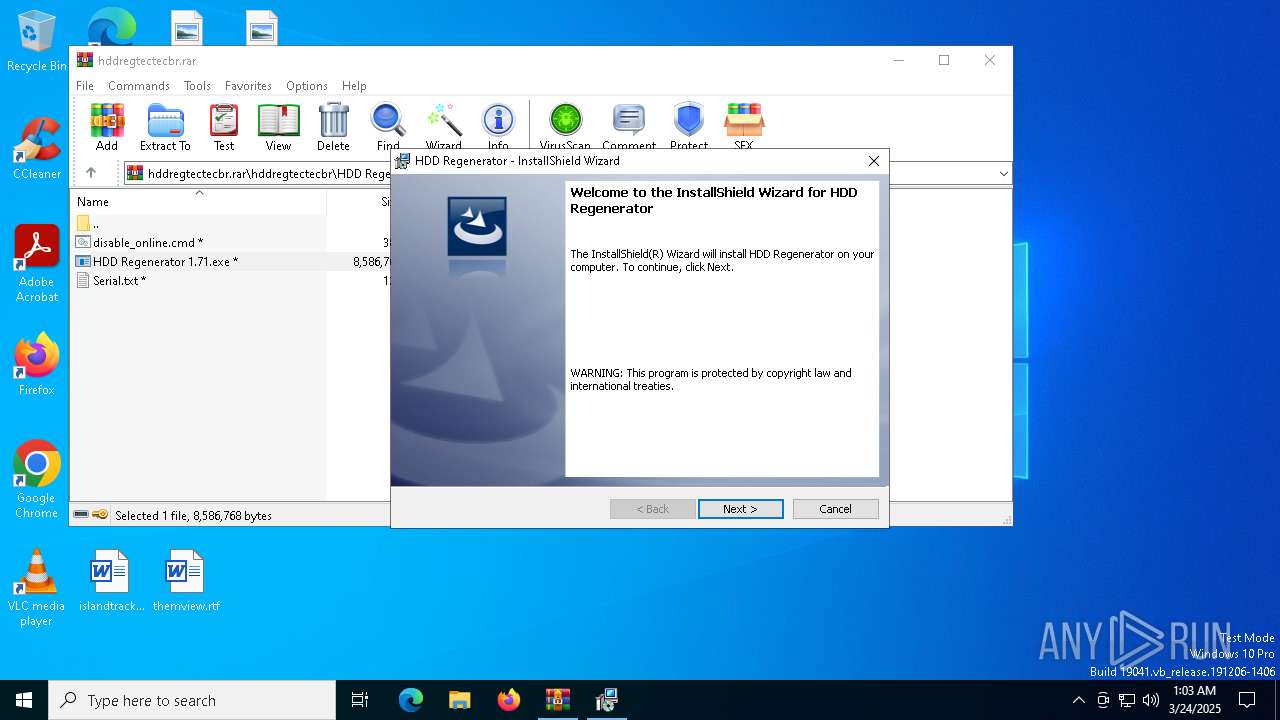
| 1052 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb6488.49076\hddregtectecbr\HDD Regenerator for windows\HDD Regenerator 1.71.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb6488.49076\hddregtectecbr\HDD Regenerator for windows\HDD Regenerator 1.71.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Abstradrome Integrity Level: MEDIUM Description: Setup Launcher Unicode Exit code: 3221226540 Version: 1.71.0012 Modules
| |||||||||||||||
| 1300 | hddreg 0 49 49 75 124 | C:\Program Files (x86)\HDD Regenerator\hddreg.exe | — | hddreg.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1388 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1600 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1852 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | hddreg 0 49 49 75 124 | C:\Program Files (x86)\HDD Regenerator\hddreg.exe | — | HDD Regenerator.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2152 | C:\Windows\syswow64\MsiExec.exe -Embedding 82C50FBD25A29F8ADCF1C08A3F200F17 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3176 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 184
Read events
20 826
Write events
337
Delete events
21
Modification events
| (PID) Process: | (1600) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1600) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1600) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (208) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (208) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (208) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5256) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5256) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5256) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5756) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
18
Suspicious files
45
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5256 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | — | |
MD5:— | SHA256:— | |||
| 5256 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\2bef3c6b-ed3f-4855-99a6-af24cfab4733.down_data | — | |
MD5:— | SHA256:— | |||
| 6268 | HDD Regenerator 1.71.exe | C:\Users\admin\AppData\Local\Temp\_is5545.tmp | — | |
MD5:— | SHA256:— | |||
| 6268 | HDD Regenerator 1.71.exe | C:\Users\admin\AppData\Local\Temp\{039F881B-E804-40F1-B8FF-8D4EF83F5253}\HDD Regenerator.msi | — | |
MD5:— | SHA256:— | |||
| 6268 | HDD Regenerator 1.71.exe | C:\Users\admin\AppData\Local\Downloaded Installations\{228F06BD-CBEE-4656-AC2A-CB927745EDED}\HDD Regenerator.msi | — | |
MD5:— | SHA256:— | |||
| 5256 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\5e0b3f16-e8e5-4329-a7d5-5a224956a9a6.up_meta_secure | binary | |
MD5:596AB94E30F0EEC0C275C6045DA75118 | SHA256:B0095B3517ABA9C21B31D67EAA7BB5A8FF47B4F370269BEF81AFB2159B13A363 | |||
| 6268 | HDD Regenerator 1.71.exe | C:\Users\admin\AppData\Local\Temp\{039F881B-E804-40F1-B8FF-8D4EF83F5253}\Setup.INI | text | |
MD5:2554BFC5A3B46AE0F717897C971819B8 | SHA256:DA0A899E1375D50755E387976A2E8C3815875FA986EFC83E7AE6477CCEC2EA3E | |||
| 5256 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\5e0b3f16-e8e5-4329-a7d5-5a224956a9a6.aa3cf0e7-6052-4a30-8384-40791214e36b.down_meta | binary | |
MD5:52F6609F315C1CF2E9B40272BA32ABE9 | SHA256:7DF4ACFA08A3C4254B249292D45F0D6F8AE08D83A1681B4371C3F2A1CB72442A | |||
| 6268 | HDD Regenerator 1.71.exe | C:\Users\admin\AppData\Local\Temp\_is5418.tmp | binary | |
MD5:8343DE539C5A2741AFF7F91D330B4AB4 | SHA256:ABB5FF3385F1A1C3CCC29A6E40A8A2B13158CA77FE41E944434AA71E920067ED | |||
| 1388 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
45
DNS requests
30
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4724 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5256 | BackgroundTransferHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4244 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4244 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5304 | msiexec.exe | GET | 200 | 184.30.131.114:80 | http://crl.verisign.com/pca3.crl | unknown | — | — | whitelisted |
5304 | msiexec.exe | GET | 200 | 184.30.131.114:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FxkCfyHfJr7GQ6M658NRZ4SHo%2FAQUCPVR6Pv%2BPT1kNnxoz1t4qN%2B5xTcCEBEQMhPZ4tSh0avCknEynU0%3D | unknown | — | — | whitelisted |
5304 | msiexec.exe | GET | 200 | 184.30.131.114:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FxkCfyHfJr7GQ6M658NRZ4SHo%2FAQUCPVR6Pv%2BPT1kNnxoz1t4qN%2B5xTcCEBEQMhPZ4tSh0avCknEynU0%3D | unknown | — | — | whitelisted |
1388 | msiexec.exe | GET | 200 | 184.30.131.114:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FxkCfyHfJr7GQ6M658NRZ4SHo%2FAQUCPVR6Pv%2BPT1kNnxoz1t4qN%2B5xTcCEBEQMhPZ4tSh0avCknEynU0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4724 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4724 | backgroundTaskHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |