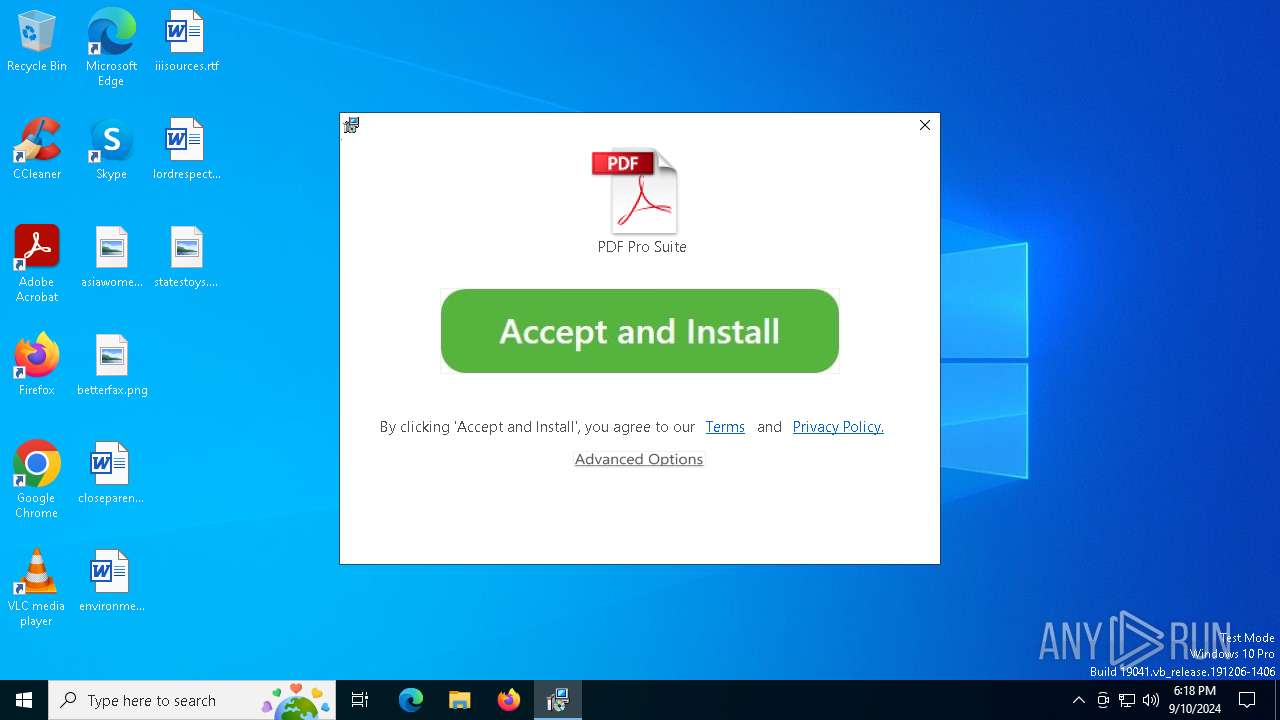
| File name: | easygetpdf.msi |
| Full analysis: | https://app.any.run/tasks/9a6676fe-2693-49d4-b86c-9960035dafac |
| Verdict: | Malicious activity |
| Analysis date: | September 10, 2024, 18:18:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Security: 0, Code page: 1252, Revision Number: {3D5A8A6F-93C8-471F-AC1E-039EAC7E09E4}, Number of Words: 10, Subject: PDFProSuite, Author: PDF Pro Suite, Name of Creating Application: PDFProSuite, Template: ;1033, Comments: This installer database contains the logic and data required to install PDFProSuite., Title: Installation Database, Keywords: Installer, MSI, Database, Create Time/Date: Tue Aug 27 06:08:51 2024, Last Saved Time/Date: Tue Aug 27 06:08:51 2024, Last Printed: Tue Aug 27 06:08:51 2024, Number of Pages: 450 |
| MD5: | AB104750285031F216B8F4A0C10D62A1 |
| SHA1: | 1AA21CF64FDBDCE001072F7F43CCCCCC70333241 |
| SHA256: | 212AFC8586E84E9E30F6C9CC02D620C9DCB08ED150B9012D806C0BEE65870986 |
| SSDEEP: | 98304:FpkF8/t6q6/8VNH9DK+uAtof39GF4yl7iu3RmG6lkaKKHyrKRnBcBAIMeGg:0q4qM |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6004)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 7068)
- msiexec.exe (PID: 2628)
Checks Windows Trust Settings
- msiexec.exe (PID: 7068)
- msiexec.exe (PID: 6004)
Executable content was dropped or overwritten
- rundll32.exe (PID: 4364)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 2628)
The executable file from the user directory is run by the CMD process
- pdfprosuite.exe (PID: 4672)
Node.exe was dropped
- msiexec.exe (PID: 7068)
Executes as Windows Service
- VSSVC.exe (PID: 4344)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1168)
An automatically generated document
- msiexec.exe (PID: 1168)
Checks proxy server information
- msiexec.exe (PID: 1168)
- msiexec.exe (PID: 7068)
Reads Environment values
- msiexec.exe (PID: 7068)
- msiexec.exe (PID: 2628)
- pdfprosuite.exe (PID: 4672)
- pdfprosuite.exe (PID: 2028)
- pdfprosuite.exe (PID: 2088)
Checks supported languages
- msiexec.exe (PID: 7068)
- msiexec.exe (PID: 6004)
- msiexec.exe (PID: 2628)
- pdfprosuite.exe (PID: 2028)
- pdfprosuite.exe (PID: 4672)
- pdfprosuite.exe (PID: 2088)
Creates files or folders in the user directory
- msiexec.exe (PID: 1168)
- msiexec.exe (PID: 6004)
- msiexec.exe (PID: 7068)
- rundll32.exe (PID: 4364)
Reads the software policy settings
- msiexec.exe (PID: 1168)
- msiexec.exe (PID: 7068)
- msiexec.exe (PID: 6004)
Reads the computer name
- msiexec.exe (PID: 2628)
- msiexec.exe (PID: 6004)
- msiexec.exe (PID: 7068)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1168)
- msiexec.exe (PID: 6004)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6004)
- msiexec.exe (PID: 7068)
- msiexec.exe (PID: 2628)
Creates a software uninstall entry
- msiexec.exe (PID: 6004)
The process uses the downloaded file
- msiexec.exe (PID: 2628)
- cmd.exe (PID: 6408)
- cmd.exe (PID: 6152)
- cmd.exe (PID: 5484)
Process checks computer location settings
- msiexec.exe (PID: 2628)
Create files in a temporary directory
- rundll32.exe (PID: 4364)
Manual execution by a user
- cmd.exe (PID: 6152)
- cmd.exe (PID: 5484)
Reads product name
- pdfprosuite.exe (PID: 4672)
- pdfprosuite.exe (PID: 2028)
- pdfprosuite.exe (PID: 2088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {3D5A8A6F-93C8-471F-AC1E-039EAC7E09E4} |
| Words: | 10 |
| Subject: | PDFProSuite |
| Author: | PDF Pro Suite |
| LastModifiedBy: | - |
| Software: | PDFProSuite |
| Template: | ;1033 |
| Comments: | This installer database contains the logic and data required to install PDFProSuite. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| CreateDate: | 2024:08:27 06:08:51 |
| ModifyDate: | 2024:08:27 06:08:51 |
| LastPrinted: | 2024:08:27 06:08:51 |
| Pages: | 450 |
Total processes
148
Monitored processes
20
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1168 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\easygetpdf.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1636 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | pdfprosuite.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1688 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2028 | "C:\Users\admin\AppData\Local\PDFProSuite\pdfprosuite.exe" . | C:\Users\admin\AppData\Local\PDFProSuite\pdfprosuite.exe | — | cmd.exe | |||||||||||
User: admin Company: Node.js Integrity Level: MEDIUM Description: Node.js JavaScript Runtime Exit code: 1 Version: 18.17.1 Modules
| |||||||||||||||
| 2056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | "C:\Users\admin\AppData\Local\PDFProSuite\pdfprosuite.exe" . | C:\Users\admin\AppData\Local\PDFProSuite\pdfprosuite.exe | — | cmd.exe | |||||||||||
User: admin Company: Node.js Integrity Level: MEDIUM Description: Node.js JavaScript Runtime Exit code: 1 Version: 18.17.1 Modules
| |||||||||||||||
| 2628 | C:\Windows\syswow64\MsiExec.exe -Embedding 3D9CC2770C739619FD341664BAED91A6 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4344 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4364 | rundll32.exe "C:\WINDOWS\Installer\MSI779D.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1275828 3284 Utility!Utility.CA.LogComplete | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 563
Read events
17 253
Write events
292
Delete events
18
Modification events
| (PID) Process: | (6004) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 480000000000000056D2E0E2AD03DB0174170000A8030000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6004) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000056D2E0E2AD03DB0174170000A8030000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6004) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000183F21E3AD03DB0174170000A8030000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6004) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000CE8F23E3AD03DB0174170000A8030000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6004) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000003FF425E3AD03DB0174170000A8030000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6004) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000003E5828E3AD03DB0174170000A8030000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6004) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (6004) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 48000000000000005F3491E3AD03DB0174170000A8030000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6004) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000989893E3AD03DB0174170000E0110000E8030000010000000000000000000000AD62CA75643FE84E9EE3DF9E90C6783A00000000000000000000000000000000 | |||
| (PID) Process: | (4344) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000066E1A1E3AD03DB01F81000006C1B0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
25
Suspicious files
40
Text files
23
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6004 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1168 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9CB4373A4252DE8D2212929836304EC5_0EFD07622F9D5CA3C618EB631B824B99 | der | |
MD5:BC362547662532D48804DC5DA8AA69BF | SHA256:6F14157AA9E4A549C54EFF78A518C03935C7AE343E2B9EB46E91CA2064F296A1 | |||
| 1168 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIADED.tmp | executable | |
MD5:421643EE7BB89E6DF092BC4B18A40FF8 | SHA256:D6B89FD5A95071E7B144D8BEDCB09B694E9CD14BFBFAFB782B17CF8413EAC6DA | |||
| 1168 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIABE8.tmp | executable | |
MD5:421643EE7BB89E6DF092BC4B18A40FF8 | SHA256:D6B89FD5A95071E7B144D8BEDCB09B694E9CD14BFBFAFB782B17CF8413EAC6DA | |||
| 1168 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\357F04AD41BCF5FE18FCB69F60C6680F_54E4814457E6B88FC0E5C74B1F0335DA | binary | |
MD5:44DAC2D363EF24A40A79455915B33A01 | SHA256:18B2390B07210A982B23D106776BD68AD27B9ABEDFCA3A04A8F5C33531BCAE6A | |||
| 1168 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIACF2.tmp | executable | |
MD5:421643EE7BB89E6DF092BC4B18A40FF8 | SHA256:D6B89FD5A95071E7B144D8BEDCB09B694E9CD14BFBFAFB782B17CF8413EAC6DA | |||
| 1168 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIAE1D.tmp | executable | |
MD5:421643EE7BB89E6DF092BC4B18A40FF8 | SHA256:D6B89FD5A95071E7B144D8BEDCB09B694E9CD14BFBFAFB782B17CF8413EAC6DA | |||
| 1168 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9CB4373A4252DE8D2212929836304EC5_0EFD07622F9D5CA3C618EB631B824B99 | binary | |
MD5:E88B004F3A7C5FEB0C0A63D6CC114F4E | SHA256:4A4146899ECFF4C5A9EF5316C88DC7C6DE78ED88163D154528317D95307A5010 | |||
| 1168 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIAE6D.tmp | executable | |
MD5:421643EE7BB89E6DF092BC4B18A40FF8 | SHA256:D6B89FD5A95071E7B144D8BEDCB09B694E9CD14BFBFAFB782B17CF8413EAC6DA | |||
| 1168 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIAE3E.tmp | executable | |
MD5:421643EE7BB89E6DF092BC4B18A40FF8 | SHA256:D6B89FD5A95071E7B144D8BEDCB09B694E9CD14BFBFAFB782B17CF8413EAC6DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
37
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7068 | msiexec.exe | GET | 200 | 18.245.65.219:80 | http://ocsp.r2m03.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQqHI%2BsdmapawQncL1rpCEZZ8gTSAQUVdkYX9IczAHhWLS%2Bq9lVQgHXLgICEA%2BjuCOT1x259UHHR62v01I%3D | unknown | — | — | unknown |
1064 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2624 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7068 | msiexec.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | unknown |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1168 | msiexec.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/codesigningrootr45/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEQCBTkI%2BxI6x4NL94uMAHTSA | unknown | — | — | whitelisted |
2624 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1168 | msiexec.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDACP4PKUmHSg8coXrA%3D%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6856 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1168 | msiexec.exe | 104.18.21.226:80 | ocsp.globalsign.com | CLOUDFLARENET | — | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1064 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1064 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |