| File name: | GamezBDO.exe |
| Full analysis: | https://app.any.run/tasks/f6625dfd-450d-4cfb-b121-2fdcb1fe1ba2 |
| Verdict: | Malicious activity |
| Analysis date: | September 11, 2019, 07:58:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | BE40497054DD589E7CBEC7F5DACFDCCB |
| SHA1: | 8EAFACEDF876900BA5CBC4E003C3E7E39338458D |
| SHA256: | 21252CDD6C6B258E02B9B9DA1D9FE16B932EDDA7DF55C0BE90DDF1F94F2E483C |
| SSDEEP: | 196608:izyEftidD/WCVAx4nT8SAd+94vDXEDXUwheEDLKlHsDFchBC+Bv:iFAD/WC84Yjd+94vDXEDXUwheEDLKlHj |
MALICIOUS
Changes settings of System certificates
- GamezBDO.exe (PID: 3732)
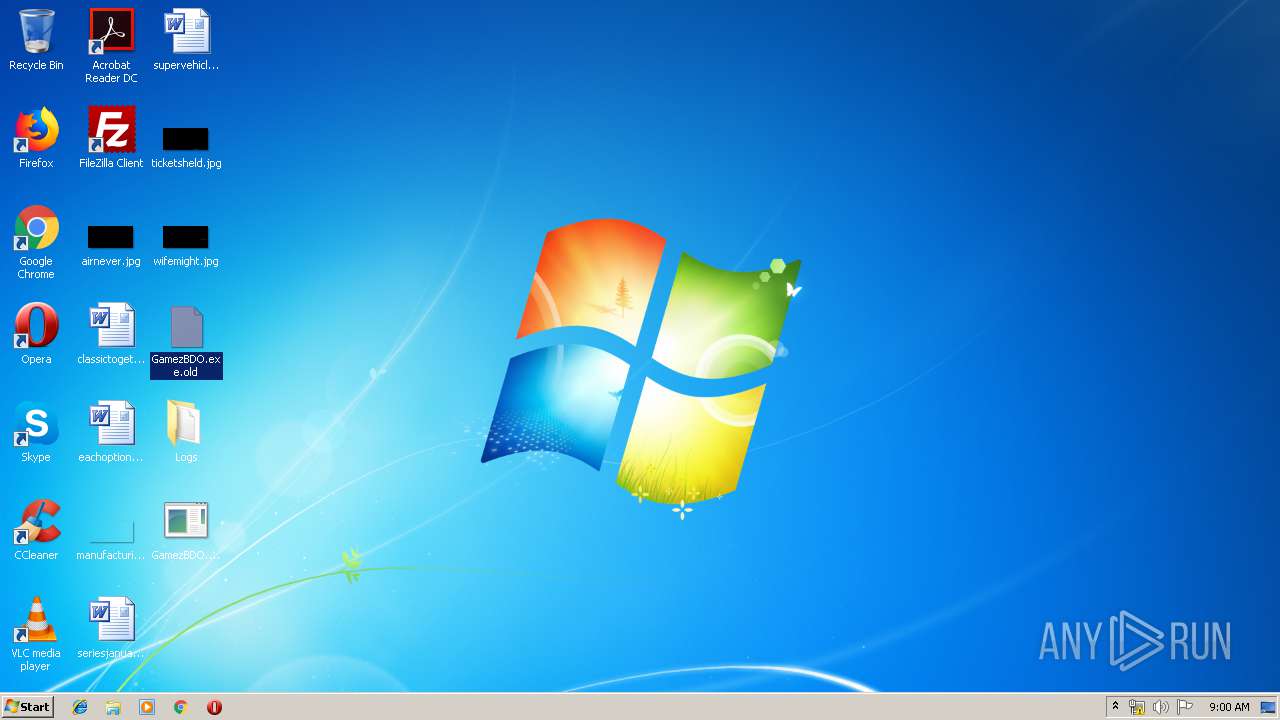
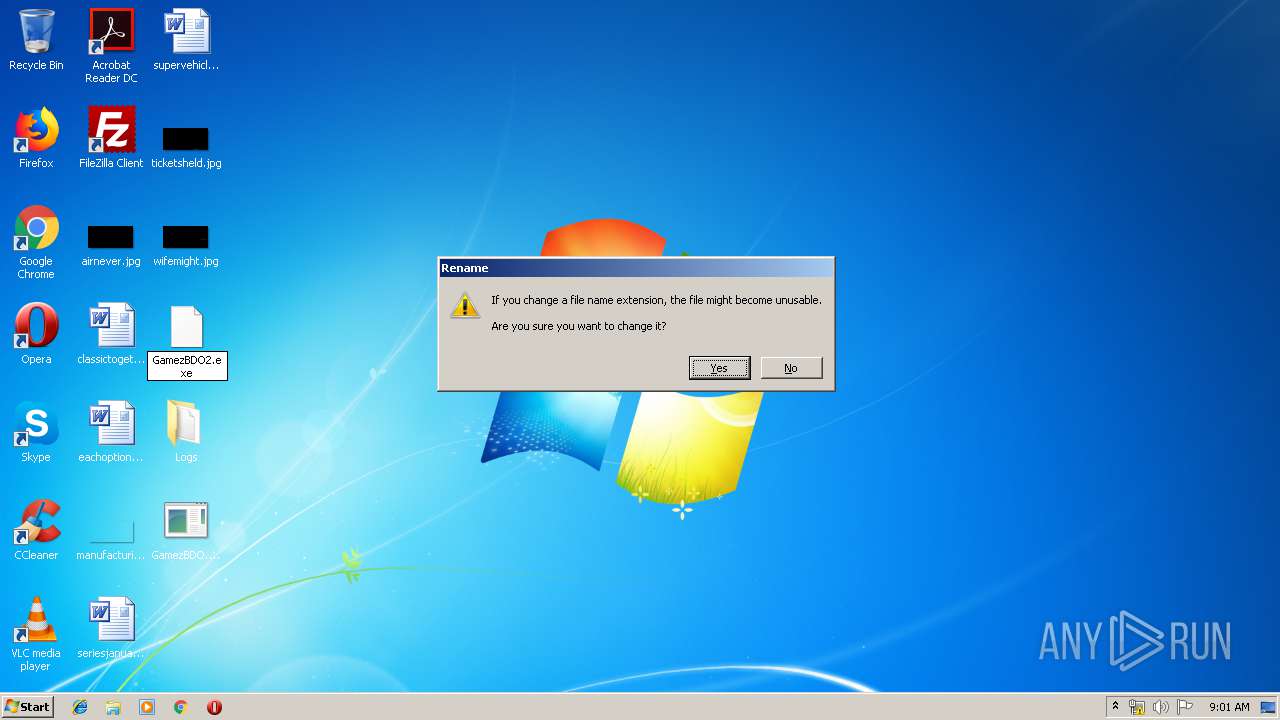
Renames files like Ransomware
- GamezBDO.exe (PID: 3732)
SUSPICIOUS
Reads Environment values
- GamezBDO.exe (PID: 3732)
Modifies the open verb of a shell class
- GamezBDO.exe (PID: 3732)
Adds / modifies Windows certificates
- GamezBDO.exe (PID: 3732)
Executable content was dropped or overwritten
- GamezBDO.exe (PID: 3732)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (35.3) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.5) |
| .exe | | | Win64 Executable (generic) (23.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.5) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:08:08 23:58:41+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 9022976 |
| InitializedDataSize: | 637440 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x93e00a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | GamezBDO Game Launcher |
| CompanyName: | GamezBDO |
| FileDescription: | GamezBDO |
| FileVersion: | 1.0.0.0 |
| InternalName: | GamezBDO.exe |
| LegalCopyright: | Copyright GamezNetwork © 2019 |
| LegalTrademarks: | - |
| OriginalFileName: | GamezBDO.exe |
| ProductName: | GamezBDO |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.7159.32360 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 08-Aug-2019 21:58:41 |
| Comments: | GamezBDO Game Launcher |
| CompanyName: | GamezBDO |
| FileDescription: | GamezBDO |
| FileVersion: | 1.0.0.0 |
| InternalName: | GamezBDO.exe |
| LegalCopyright: | Copyright GamezNetwork © 2019 |
| LegalTrademarks: | - |
| OriginalFilename: | GamezBDO.exe |
| ProductName: | GamezBDO |
| ProductVersion: | 1.0.0.0 |
| Assembly Version: | 1.0.7159.32360 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 08-Aug-2019 21:58:41 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
=4f\x038vq/l$\x08 | 0x00002000 | 0x0008246C | 0x00082600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99965 |
.text | 0x00086000 | 0x0089AB58 | 0x0089AC00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.3266 |
.rsrc | 0x00922000 | 0x00019038 | 0x00019200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.89264 |
.reloc | 0x0093C000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.0980042 |
0x0093E000 | 0x00000010 | 0x00000200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0.142636 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.11544 | 1392 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 5.0171 | 16936 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 5.14408 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 5.49047 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 5.76433 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 2.80283 | 76 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
43
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
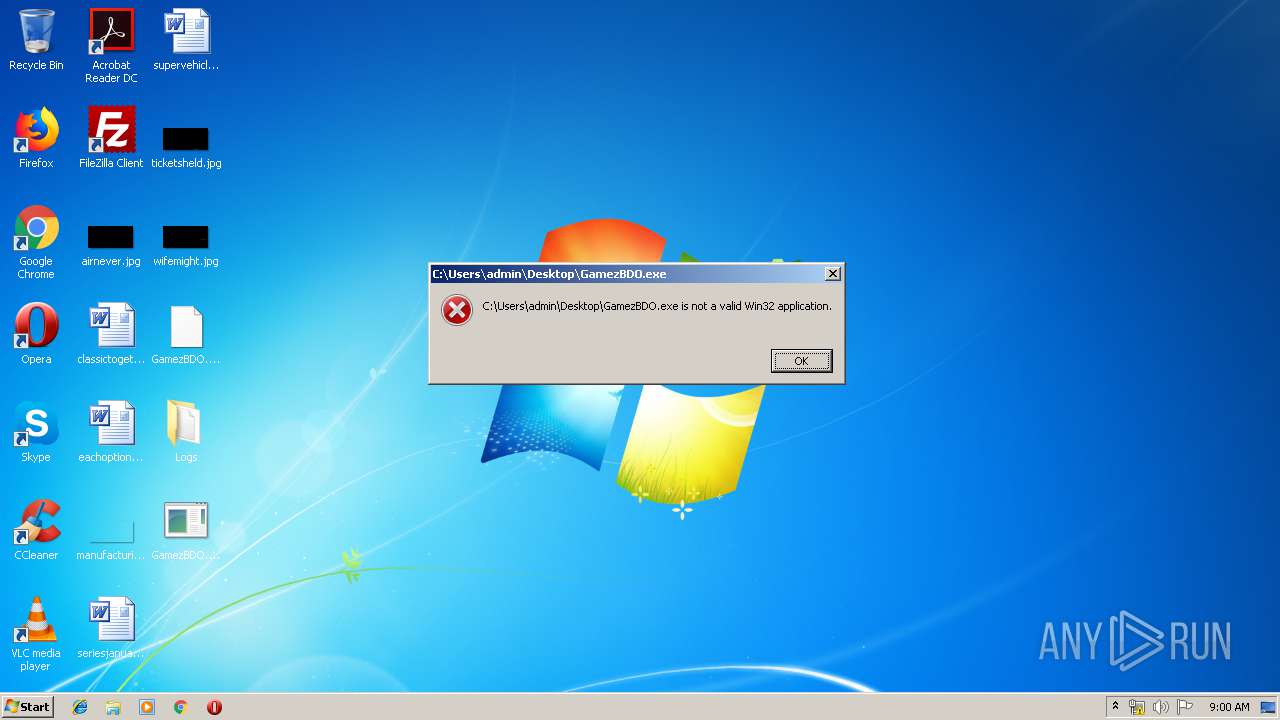
| 2516 | "C:\Users\admin\Desktop\GamezBDO.exe" | C:\Users\admin\Desktop\GamezBDO.exe | — | explorer.exe | |||||||||||
User: admin Company: GamezBDO Integrity Level: MEDIUM Description: GamezBDO Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2752 | "bcdedit.exe" -set loadoptions ENABLE_INTEGRITY_CHECKS | C:\Windows\system32\bcdedit.exe | — | GamezBDO.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2840 | "bcdedit.exe" -set TESTSIGNING OFF | C:\Windows\system32\bcdedit.exe | — | GamezBDO.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3732 | "C:\Users\admin\Desktop\GamezBDO.exe" | C:\Users\admin\Desktop\GamezBDO.exe | explorer.exe | ||||||||||||
User: admin Company: GamezBDO Integrity Level: HIGH Description: GamezBDO Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
103
Read events
68
Write events
35
Delete events
0
Modification events
| (PID) Process: | (3732) GamezBDO.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3732) GamezBDO.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3732) GamezBDO.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2752) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\12000030 |
| Operation: | write | Name: | Element |
Value: ENABLE_INTEGRITY_CHECKS | |||
| (PID) Process: | (2840) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\16000049 |
| Operation: | write | Name: | Element |
Value: 00 | |||
| (PID) Process: | (3732) GamezBDO.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\AFE5D244A8D1194230FF479FE2F897BBCD7A8CB4 |
| Operation: | write | Name: | Blob |
Value: 0F0000000100000030000000761613F4CD8607508C3D520FBEFE68773735FC73746F42A9FD6254BA3B72F0047994E5AF57677CF6D2C1965984965DF1090000000100000054000000305206082B0601050507030106082B0601050507030206082B0601050507030406082B0601050507030306082B06010505070308060A2B0601040182370A030406082B0601050507030606082B060105050703070B000000010000003A0000005300650063007400690067006F002000280066006F0072006D00650072006C007900200043006F006D006F0064006F002000430041002900000053000000010000002600000030243022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C062000000010000002000000052F0E1C4E58EC629291B60317F074671B85D7EA80D5B07273463534B32B40234140000000100000014000000BBAF7E023DFAA6F13C848EADEE3898ECD93232D41D0000000100000010000000CB39C3D4272CDF63774E1DB810C5A89E030000000100000014000000AFE5D244A8D1194230FF479FE2F897BBCD7A8CB42000000001000000DC050000308205D8308203C0A00302010202104CAAF9CADB636FE01FF74ED85B03869D300D06092A864886F70D01010C0500308185310B3009060355040613024742311B30190603550408131247726561746572204D616E636865737465723110300E0603550407130753616C666F7264311A3018060355040A1311434F4D4F444F204341204C696D69746564312B302906035504031322434F4D4F444F205253412043657274696669636174696F6E20417574686F72697479301E170D3130303131393030303030305A170D3338303131383233353935395A308185310B3009060355040613024742311B30190603550408131247726561746572204D616E636865737465723110300E0603550407130753616C666F7264311A3018060355040A1311434F4D4F444F204341204C696D69746564312B302906035504031322434F4D4F444F205253412043657274696669636174696F6E20417574686F7269747930820222300D06092A864886F70D01010105000382020F003082020A028202010091E85492D20A56B1AC0D24DDC5CF446774992B37A37D23700071BC53DFC4FA2A128F4B7F1056BD9F7072B7617FC94B0F17A73DE3B00461EEFF1197C7F4863E0AFA3E5CF993E6347AD9146BE79CB385A0827A76AF7190D7ECFD0DFA9C6CFADFB082F4147EF9BEC4A62F4F7F997FB5FC674372BD0C00D689EB6B2CD3ED8F981C14AB7EE5E36EFCD8A8E49224DA436B62B855FDEAC1BC6CB68BF30E8D9AE49B6C6999F878483045D5ADE10D3C4560FC32965127BC67C3CA2EB66BEA46C7C720A0B11F65DE4808BAA44EA9F283463784EBE8CC814843674E722A9B5CBD4C1B288A5C227BB4AB98D9EEE05183C309464E6D3E99FA9517DA7C3357413C8D51ED0BB65CAF2C631ADF57C83FBCE95DC49BAF4599E2A35A24B4BAA9563DCF6FAAFF4958BEF0A8FFF4B8ADE937FBBAB8F40B3AF9E843421E89D884CB13F1D9BBE18960B88C2856AC141D9C0AE771EBCF0EDD3DA996A148BD3CF7AFB50D224CC01181EC563BF6D3A2E25BB7B204225295809369E88E4C65F191032D707402EA8B671529695202BBD7DF506A5546BFA0A328617F70D0C3A2AA2C21AA47CE289C064576BF821827B4D5AEB4CB50E66BF44C867130E9A6DF1686E0D8FF40DDFBD042887FA3333A2E5C1E41118163CE18716B2BECA68AB7315C3A6A47E0C37959D6201AAFF26A98AA72BC574AD24B9DBB10FCB04C41E5ED1D3D5E289D9CCCBFB351DAA747E584530203010001A3423040301D0603551D0E04160414BBAF7E023DFAA6F13C848EADEE3898ECD93232D4300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF300D06092A864886F70D01010C050003820201000AF1D54684B7AE51BB6CB24D411400934C9CCBE5C054CFA0258E02F9FDB0A20DF520983C132DAC56A2B0D67E1192E92EBA9E2E9A72B1BD19446C6135A29AB41612695A8CE1D73EA41AE82F03F4AE611D101B2AA48B7AC5FE05A6E1C0D6C8FE9EAE8F2BBA3D99F8D8730958466EA69CF4D727D395DA3783721CD373E0A2479903385DD5497900291CC7EC9B201C0724695778B239FC3A84A0B59C7C8DBF2E936227B739DA1718AEBD3C0968FF849B3CD5D60B03E3579E14F7D1EB4FC8BD8723B7B6494379855CBAEB920BA1C6E868A84C16B11A990AE8532C92BBA10918750C65A87BCB23B71AC22885C31BFFD02B62EFA47B099198678C1401CD68066A6321750380888A6E81C685F2A9A42DE7F4A524104783CACDF48D7958B1069BE71A2AD99D01D7947DED034ACAF0DBE8A9013EF55699C91E8E493DBBE509B9E04F49923D168240CCCC59C6E63AED122E693C6C95B1FDAA1D7B7F86BE1E0E3246FBFB138F757F4C8B4B4663FE00344070C1C3B9A1DDA670E204B341BCE98091EA649C7AE12203A99C6E6F0E654F6C87875EF36EA0F975A59B40E853B2279D4AB9C077218DFF87F2DEBC8CEF17DFB7490BD1F26E300B1A0E4E76ED11FCF5E956B27DBFC76D0A938CA5D0C0B61DBE3A4E94A2D76E6C0BC28A7CFA20F3C4E4E5CD0DA8CB9192B17C85ECB51469660E82E7CDCEC82DA6517F21C1355385064A5D9FADBB1B5F74 | |||
| (PID) Process: | (3732) GamezBDO.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\AFE5D244A8D1194230FF479FE2F897BBCD7A8CB4 |
| Operation: | write | Name: | Blob |
Value: 19000000010000001000000082218FFB91733E64136BE5719F57C3A1030000000100000014000000AFE5D244A8D1194230FF479FE2F897BBCD7A8CB41D0000000100000010000000CB39C3D4272CDF63774E1DB810C5A89E140000000100000014000000BBAF7E023DFAA6F13C848EADEE3898ECD93232D462000000010000002000000052F0E1C4E58EC629291B60317F074671B85D7EA80D5B07273463534B32B4023453000000010000002600000030243022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C00B000000010000003A0000005300650063007400690067006F002000280066006F0072006D00650072006C007900200043006F006D006F0064006F0020004300410029000000090000000100000054000000305206082B0601050507030106082B0601050507030206082B0601050507030406082B0601050507030306082B06010505070308060A2B0601040182370A030406082B0601050507030606082B060105050703070F0000000100000030000000761613F4CD8607508C3D520FBEFE68773735FC73746F42A9FD6254BA3B72F0047994E5AF57677CF6D2C1965984965DF12000000001000000DC050000308205D8308203C0A00302010202104CAAF9CADB636FE01FF74ED85B03869D300D06092A864886F70D01010C0500308185310B3009060355040613024742311B30190603550408131247726561746572204D616E636865737465723110300E0603550407130753616C666F7264311A3018060355040A1311434F4D4F444F204341204C696D69746564312B302906035504031322434F4D4F444F205253412043657274696669636174696F6E20417574686F72697479301E170D3130303131393030303030305A170D3338303131383233353935395A308185310B3009060355040613024742311B30190603550408131247726561746572204D616E636865737465723110300E0603550407130753616C666F7264311A3018060355040A1311434F4D4F444F204341204C696D69746564312B302906035504031322434F4D4F444F205253412043657274696669636174696F6E20417574686F7269747930820222300D06092A864886F70D01010105000382020F003082020A028202010091E85492D20A56B1AC0D24DDC5CF446774992B37A37D23700071BC53DFC4FA2A128F4B7F1056BD9F7072B7617FC94B0F17A73DE3B00461EEFF1197C7F4863E0AFA3E5CF993E6347AD9146BE79CB385A0827A76AF7190D7ECFD0DFA9C6CFADFB082F4147EF9BEC4A62F4F7F997FB5FC674372BD0C00D689EB6B2CD3ED8F981C14AB7EE5E36EFCD8A8E49224DA436B62B855FDEAC1BC6CB68BF30E8D9AE49B6C6999F878483045D5ADE10D3C4560FC32965127BC67C3CA2EB66BEA46C7C720A0B11F65DE4808BAA44EA9F283463784EBE8CC814843674E722A9B5CBD4C1B288A5C227BB4AB98D9EEE05183C309464E6D3E99FA9517DA7C3357413C8D51ED0BB65CAF2C631ADF57C83FBCE95DC49BAF4599E2A35A24B4BAA9563DCF6FAAFF4958BEF0A8FFF4B8ADE937FBBAB8F40B3AF9E843421E89D884CB13F1D9BBE18960B88C2856AC141D9C0AE771EBCF0EDD3DA996A148BD3CF7AFB50D224CC01181EC563BF6D3A2E25BB7B204225295809369E88E4C65F191032D707402EA8B671529695202BBD7DF506A5546BFA0A328617F70D0C3A2AA2C21AA47CE289C064576BF821827B4D5AEB4CB50E66BF44C867130E9A6DF1686E0D8FF40DDFBD042887FA3333A2E5C1E41118163CE18716B2BECA68AB7315C3A6A47E0C37959D6201AAFF26A98AA72BC574AD24B9DBB10FCB04C41E5ED1D3D5E289D9CCCBFB351DAA747E584530203010001A3423040301D0603551D0E04160414BBAF7E023DFAA6F13C848EADEE3898ECD93232D4300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF300D06092A864886F70D01010C050003820201000AF1D54684B7AE51BB6CB24D411400934C9CCBE5C054CFA0258E02F9FDB0A20DF520983C132DAC56A2B0D67E1192E92EBA9E2E9A72B1BD19446C6135A29AB41612695A8CE1D73EA41AE82F03F4AE611D101B2AA48B7AC5FE05A6E1C0D6C8FE9EAE8F2BBA3D99F8D8730958466EA69CF4D727D395DA3783721CD373E0A2479903385DD5497900291CC7EC9B201C0724695778B239FC3A84A0B59C7C8DBF2E936227B739DA1718AEBD3C0968FF849B3CD5D60B03E3579E14F7D1EB4FC8BD8723B7B6494379855CBAEB920BA1C6E868A84C16B11A990AE8532C92BBA10918750C65A87BCB23B71AC22885C31BFFD02B62EFA47B099198678C1401CD68066A6321750380888A6E81C685F2A9A42DE7F4A524104783CACDF48D7958B1069BE71A2AD99D01D7947DED034ACAF0DBE8A9013EF55699C91E8E493DBBE509B9E04F49923D168240CCCC59C6E63AED122E693C6C95B1FDAA1D7B7F86BE1E0E3246FBFB138F757F4C8B4B4663FE00344070C1C3B9A1DDA670E204B341BCE98091EA649C7AE12203A99C6E6F0E654F6C87875EF36EA0F975A59B40E853B2279D4AB9C077218DFF87F2DEBC8CEF17DFB7490BD1F26E300B1A0E4E76ED11FCF5E956B27DBFC76D0A938CA5D0C0B61DBE3A4E94A2D76E6C0BC28A7CFA20F3C4E4E5CD0DA8CB9192B17C85ECB51469660E82E7CDCEC82DA6517F21C1355385064A5D9FADBB1B5F74 | |||
| (PID) Process: | (3732) GamezBDO.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\GamezBDO_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3732) GamezBDO.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\GamezBDO_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3732) GamezBDO.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\GamezBDO_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
Executable files
2
Suspicious files
4
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3732 | GamezBDO.exe | C:\Users\admin\AppData\Local\Temp\CabFA72.tmp | — | |
MD5:— | SHA256:— | |||
| 3732 | GamezBDO.exe | C:\Users\admin\AppData\Local\Temp\TarFA73.tmp | — | |
MD5:— | SHA256:— | |||
| 3732 | GamezBDO.exe | C:\Users\admin\AppData\Local\Temp\CabFA83.tmp | — | |
MD5:— | SHA256:— | |||
| 3732 | GamezBDO.exe | C:\Users\admin\AppData\Local\Temp\TarFA84.tmp | — | |
MD5:— | SHA256:— | |||
| 3732 | GamezBDO.exe | C:\Users\admin\AppData\Local\Temp\CabFAF3.tmp | — | |
MD5:— | SHA256:— | |||
| 3732 | GamezBDO.exe | C:\Users\admin\AppData\Local\Temp\TarFAF4.tmp | — | |
MD5:— | SHA256:— | |||
| 3732 | GamezBDO.exe | C:\Users\admin\AppData\Local\GamezBDO\GamezBDO.exe_Url_ghlvvni3qwjtmpzwa01iqzt4jnz0nugr\1.0.7159.32360\10lqvc0u.newcfg | — | |
MD5:— | SHA256:— | |||
| 3732 | GamezBDO.exe | C:\Users\admin\AppData\Local\GamezBDO\GamezBDO.exe_Url_ghlvvni3qwjtmpzwa01iqzt4jnz0nugr\1.0.7159.32360\1ji5ppln.newcfg | — | |
MD5:— | SHA256:— | |||
| 3732 | GamezBDO.exe | C:\Users\admin\AppData\Local\GamezBDO\GamezBDO.exe_Url_ghlvvni3qwjtmpzwa01iqzt4jnz0nugr\1.0.7159.32360\e3q35oz2.newcfg | — | |
MD5:— | SHA256:— | |||
| 3732 | GamezBDO.exe | C:\Users\admin\AppData\Local\GamezBDO\GamezBDO.exe_Url_ghlvvni3qwjtmpzwa01iqzt4jnz0nugr\1.0.7159.32360\user.config | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
3
DNS requests
3
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3732 | GamezBDO.exe | GET | — | 104.28.7.186:80 | http://play.gamezbd.net/launcher/GamezBDO.exe | US | — | — | suspicious |
3732 | GamezBDO.exe | GET | 200 | 104.28.7.186:80 | http://play.gamezbd.net/launcher/update.xml | US | xml | 8.93 Kb | suspicious |
3732 | GamezBDO.exe | GET | 200 | 104.28.7.186:80 | http://play.gamezbd.net/launcher/launcher.xml | US | xml | 1.16 Kb | suspicious |
3732 | GamezBDO.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.0 Kb | whitelisted |
3732 | GamezBDO.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/AFE5D244A8D1194230FF479FE2F897BBCD7A8CB4.crt | US | der | 1.46 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3732 | GamezBDO.exe | 91.199.212.52:80 | crt.comodoca.com | Comodo CA Ltd | GB | suspicious |
3732 | GamezBDO.exe | 104.28.7.186:80 | play.gamezbd.net | Cloudflare Inc | US | shared |
3732 | GamezBDO.exe | 93.184.221.240:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crt.comodoca.com |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
play.gamezbd.net |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3732 | GamezBDO.exe | A Network Trojan was detected | ET POLICY User-Agent (Launcher) |
3732 | GamezBDO.exe | A Network Trojan was detected | ET POLICY User-Agent (Launcher) |
3732 | GamezBDO.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3732 | GamezBDO.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |