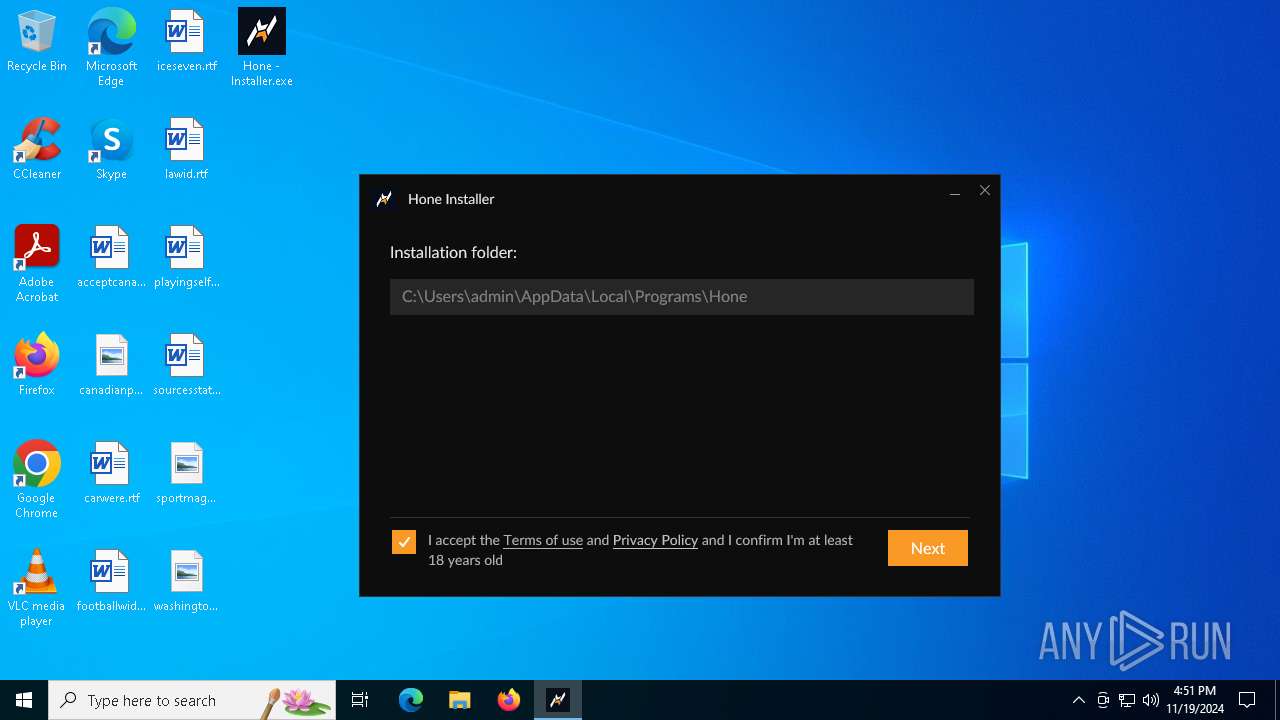
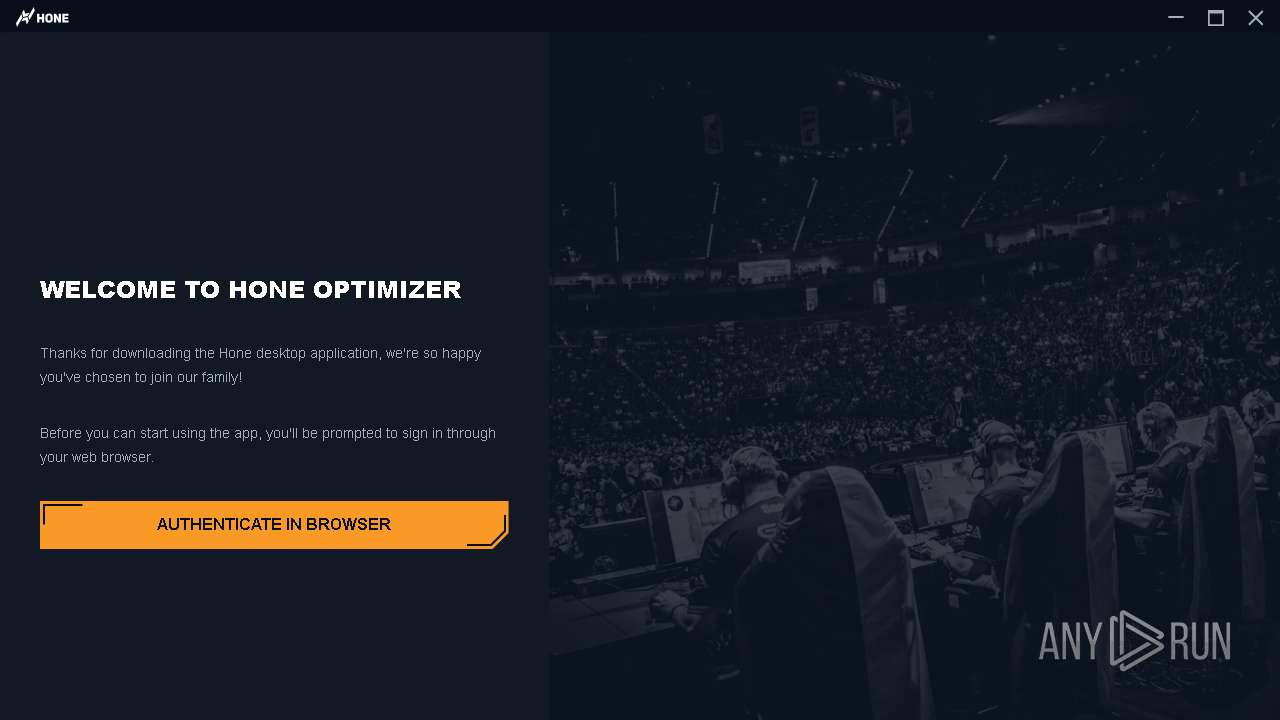
| File name: | Hone - Installer.exe |
| Full analysis: | https://app.any.run/tasks/df98d585-e526-483d-ab04-65779c928ade |
| Verdict: | Malicious activity |
| Analysis date: | November 19, 2024, 16:50:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 41094D1268D0A14C949592F589ABA11B |
| SHA1: | 51C6F64ED9FDA444816B4FBBD18A7DE4C89B7101 |
| SHA256: | 211FFA3CEBA28892895D763C47B4CD6B28EBC5C9E2B64F16ED6F8E9D72444E55 |
| SSDEEP: | 98304:N/d5kO4fJ/A9nGcRa1xXcVsy3RxeLLCIJgap176MVhAuMdehHtW3FRgpXNhW2Geo:xZT |
MALICIOUS
Executing a file with an untrusted certificate
- ow-electron-setup.exe (PID: 6624)
- Hone.exe (PID: 6952)
- Hone.exe (PID: 7080)
- Hone.exe (PID: 5916)
- Hone.exe (PID: 2672)
- Hone.exe (PID: 2876)
- Hone.exe (PID: 5096)
- Hone.exe (PID: 6740)
- Hone.exe (PID: 1020)
- gamefinder472.exe (PID: 68)
- HoneStartup.exe (PID: 1140)
- HoneStartup.exe (PID: 2072)
- HoneStartup.exe (PID: 7296)
- gamefinder472.exe (PID: 7288)
- Hone.exe (PID: 6632)
- Hone.exe (PID: 7256)
- Hone.exe (PID: 5344)
- Hone.exe (PID: 6864)
- gamefinder472.exe (PID: 6756)
- Hone.exe (PID: 4036)
- Hone.exe (PID: 4704)
- HoneStartup.exe (PID: 3732)
- gamefinder472.exe (PID: 8088)
Changes powershell execution policy (Unrestricted)
- Hone.exe (PID: 7080)
- Hone.exe (PID: 7256)
Bypass execution policy to execute commands
- powershell.exe (PID: 7520)
- powershell.exe (PID: 7664)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 5572)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 7476)
- cmd.exe (PID: 7620)
- cmd.exe (PID: 8088)
- cmd.exe (PID: 6324)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- Hone - Installer.exe (PID: 5796)
- Hone - Installer.exe (PID: 3988)
- ow-electron-setup.exe (PID: 6624)
Drops 7-zip archiver for unpacking
- Hone - Installer.exe (PID: 5796)
- Hone - Installer.exe (PID: 3988)
- ow-electron-setup.exe (PID: 6624)
Executable content was dropped or overwritten
- Hone - Installer.exe (PID: 5796)
- Hone - Installer.exe (PID: 3988)
- ow-electron-setup.exe (PID: 6624)
- Hone.exe (PID: 1020)
The process creates files with name similar to system file names
- Hone - Installer.exe (PID: 5796)
Reads security settings of Internet Explorer
- Hone - Installer.exe (PID: 5796)
Application launched itself
- Hone - Installer.exe (PID: 5796)
- Hone.exe (PID: 7080)
- Hone.exe (PID: 7256)
Get information on the list of running processes
- ow-electron-setup.exe (PID: 6624)
- cmd.exe (PID: 6668)
Starts CMD.EXE for commands execution
- ow-electron-setup.exe (PID: 6624)
- Hone.exe (PID: 7080)
- Hone.exe (PID: 7256)
Process drops legitimate windows executable
- ow-electron-setup.exe (PID: 6624)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6724)
- cmd.exe (PID: 188)
- cmd.exe (PID: 1808)
- cmd.exe (PID: 1300)
- cmd.exe (PID: 7572)
- cmd.exe (PID: 8056)
- cmd.exe (PID: 5176)
The process drops C-runtime libraries
- ow-electron-setup.exe (PID: 6624)
Drops a system driver (possible attempt to evade defenses)
- ow-electron-setup.exe (PID: 6624)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 644)
- cmd.exe (PID: 6476)
- Hone.exe (PID: 7080)
- cmd.exe (PID: 7620)
- cmd.exe (PID: 7876)
- cmd.exe (PID: 7476)
- cmd.exe (PID: 8088)
- Hone.exe (PID: 7256)
- cmd.exe (PID: 7888)
- cmd.exe (PID: 6324)
The process executes Powershell scripts
- cmd.exe (PID: 644)
- cmd.exe (PID: 6476)
- cmd.exe (PID: 7476)
- cmd.exe (PID: 7620)
- cmd.exe (PID: 7876)
- cmd.exe (PID: 8088)
- cmd.exe (PID: 7888)
- cmd.exe (PID: 6324)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 7476)
- Hone.exe (PID: 7080)
- cmd.exe (PID: 7620)
- cmd.exe (PID: 8088)
- Hone.exe (PID: 7256)
- cmd.exe (PID: 6324)
The process hide an interactive prompt from the user
- cmd.exe (PID: 7476)
- cmd.exe (PID: 7620)
- cmd.exe (PID: 8088)
- cmd.exe (PID: 6324)
Executes script without checking the security policy
- powershell.exe (PID: 7520)
- powershell.exe (PID: 7664)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 5572)
The process hides Powershell's copyright startup banner
- Hone.exe (PID: 7080)
- cmd.exe (PID: 7476)
- cmd.exe (PID: 7620)
- cmd.exe (PID: 8088)
- Hone.exe (PID: 7256)
- cmd.exe (PID: 6324)
INFO
Checks supported languages
- Hone - Installer.exe (PID: 5796)
Process checks computer location settings
- Hone - Installer.exe (PID: 5796)
Reads the computer name
- Hone - Installer.exe (PID: 5796)
Create files in a temporary directory
- Hone - Installer.exe (PID: 5796)
Manual execution by a user
- Hone.exe (PID: 6952)
- Hone.exe (PID: 7080)
- Hone.exe (PID: 7256)
- msedge.exe (PID: 7308)
- Hone.exe (PID: 6632)
Application launched itself
- msedge.exe (PID: 8008)
- msedge.exe (PID: 1020)
- msedge.exe (PID: 7308)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:57:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 186880 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x352d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.265.0.3 |
| ProductVersionNumber: | 2.265.0.3 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Overwolf Ltd. |
| FileDescription: | Hone |
| FileVersion: | 2.265.0.3 |
| LegalCopyright: | Copyright (C) 2021 Overwolf Ltd. All Rights Reserved. |
| LegalTrademarks: | - |
| ProductName: | Hone |
| ProductVersion: | 2.265.0.3 |
Total processes
282
Monitored processes
155
Malicious processes
7
Suspicious processes
27
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 68 | C:\Users\admin\AppData\Local\Programs\Hone\resources\assets\hone-resources\gamefinder472.exe --installed-only | C:\Users\admin\AppData\Local\Programs\Hone\resources\assets\hone-resources\gamefinder472.exe | — | Hone.exe | |||||||||||
User: admin Integrity Level: HIGH Description: gamedetector Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 188 | C:\WINDOWS\system32\cmd.exe /d /s /c "reg add "hklm\Software\Classes\hone" /f" | C:\Windows\System32\cmd.exe | — | Hone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | powershell.exe -NoProfile -NoLogo -InputFormat Text -NoExit -ExecutionPolicy Unrestricted -Command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Hone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5168 --field-trial-handle=2348,i,1087101748530012736,10431871760091650114,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 492 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2612 --field-trial-handle=2404,i,16068810708192912264,2980063131053318776,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 556 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5672 --field-trial-handle=2536,i,16377982981174702405,16859187986150763786,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 644 | C:\WINDOWS\system32\cmd.exe /d /s /c ""C:\WINDOWS\System32\WindowsPowershell\v1.0\powershell.exe" -Command "Unblock-File -Path 'c:\ProgramData\Microsoft\ee72ed43-9ea4-44ce-82dd-abe19a3f4b2a.ps1'"" | C:\Windows\System32\cmd.exe | — | Hone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | "C:\Users\admin\AppData\Local\Programs\Hone\Hone.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\Hone" --standard-schemes=owepm --secure-schemes=owepm --bypasscsp-schemes=owepm --fetch-schemes=owepm --streaming-schemes=owepm --app-user-model-id=Hone --app-path="C:\Users\admin\AppData\Local\Programs\Hone\resources\app.asar" --no-sandbox --no-zygote --node-integration-in-worker --no-sandbox --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=3912,i,11615441294353820390,6341495006499368325,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=3904 --uid=mgkabooemhaamambocobpeoeelpadcjhjgbcfhlc --package-folder="C:\Users\admin\AppData\Roaming\ow-electron" --app-root="C:\Users\admin\AppData\Local\Programs\Hone\resources\app.asar" --muid=bb926e54-e3ca-40fd-ae90-2764341e7792 --phase=43 --owepm-config="{\"phasing\":100}" --js-flags=--expose-gc /prefetch:1 | C:\Users\admin\AppData\Local\Programs\Hone\Hone.exe | Hone.exe | ||||||||||||
User: admin Company: AuraSide Inc Integrity Level: HIGH Description: Hone Exit code: 0 Version: 1.1.36 Modules
| |||||||||||||||
| 1020 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 | |||||||||||||||
| 1076 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3252 --field-trial-handle=2348,i,1087101748530012736,10431871760091650114,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
Total events
24 765
Read events
24 700
Write events
45
Delete events
20
Modification events
| (PID) Process: | (3988) Hone - Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3988) Hone - Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3988) Hone - Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3716) OWInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\OverwolfPersist |
| Operation: | write | Name: | MUIDV2 |
Value: aee532ee-156f-4323-a2dc-3a18a932248b | |||
| (PID) Process: | (3716) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\OverwolfPersist |
| Operation: | write | Name: | MUIDV2 |
Value: aee532ee-156f-4323-a2dc-3a18a932248b | |||
| (PID) Process: | (3716) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Overwolf |
| Operation: | write | Name: | MUID |
Value: bb926e54-e3ca-40fd-ae90-2764341e7792 | |||
| (PID) Process: | (3716) OWInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\OverwolfElectron |
| Operation: | write | Name: | MUID |
Value: bb926e54-e3ca-40fd-ae90-2764341e7792 | |||
| (PID) Process: | (3716) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\OWinstaller_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3716) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\OWinstaller_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (3716) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\OWinstaller_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
132
Suspicious files
382
Text files
265
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5796 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsu9315.tmp\Newtonsoft.Json.dll | executable | |
MD5:98CBB64F074DC600B23A2EE1A0F46448 | SHA256:7B44639CBFBC8DDAC8C7A3DE8FFA97A7460BEBB0D54E9FF2E1CCDC3A742C2B13 | |||
| 5796 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsu9315.tmp\nsProcess.dll | executable | |
MD5:10E47E822B85D2A12FA4727001612182 | SHA256:D530589A90918334B8E08D7355630892DD62F41333D948A860735D5BECFCB391 | |||
| 5796 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsu9315.tmp\uac.dll | executable | |
MD5:861F7E800BB28F68927E65719869409C | SHA256:10A0E8CF46038AB3B2C3CF5DCE407B9A043A631CBDE9A5C8BCF0A54B2566C010 | |||
| 5796 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsu9315.tmp\app\cmp.html | html | |
MD5:D7B8B31B190E552677589CFD4CBB5D8E | SHA256:6C21E8C07CE28327DCA05F873D73FE85D5473F9B22A751A4D3D28931F5D0C74F | |||
| 5796 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsu9315.tmp\OWInstaller.exe | executable | |
MD5:1B49AA2792BAE165B1A8EDB20CB5D675 | SHA256:522A50B813B24EACA425DBF17CF4ABFAD8ACF75AC3071D4D0569EFDC8F5F4F92 | |||
| 5796 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsu9315.tmp\SharpRaven.dll | executable | |
MD5:F2F1CD4E9B1F772B7B7955C3310A126A | SHA256:A8CD61FC4478DA0464967F5C74B6ECC6A880E879F49BA552F7C3056D3D0D562A | |||
| 5796 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsu9315.tmp\log4net.dll | executable | |
MD5:F15C8A9E2876568B3910189B2D493706 | SHA256:AE9C8073C3357C490F5D1C64101362918357C568F6B9380A60B09A4A4C1FF309 | |||
| 5796 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsu9315.tmp\CommandLine.dll | executable | |
MD5:6D11C677CAE02CAA249A4F7F35FFF112 | SHA256:DDE08C1DB1FF43B08C7DE59AE14045CB6FEC13BEC7AC65E142142453B8AB1AD4 | |||
| 5796 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsu9315.tmp\websocket-sharp.dll | executable | |
MD5:BD907F40168A3BC1590EE1F22BE99014 | SHA256:0C55480EF4020FDDB567CF4487C5A44077A966EC6079B19FAECD3E69DD991AD4 | |||
| 5796 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsu9315.tmp\partner-custom-asset.png | image | |
MD5:BAE604C0326ED9356CFD21E41C7840E2 | SHA256:F242F6BFD1181F07F91756350B4433D8E6D8D04A3F5F71915692E657CFDB7A84 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
141
DNS requests
126
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3988 | Hone - Installer.exe | GET | 200 | 13.225.78.115:80 | http://analyticsnew.overwolf.com/analytics/Counter?Name=installer_uac_action&Value=1&&Extra=%5b%7b%22Name%22%3a%22installer_version%22%2c%22Value%22%3a%222.265.0.3%22%7d%5d | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3716 | OWInstaller.exe | GET | 200 | 142.250.186.174:80 | http://www.google-analytics.com/__utm.gif?utmwv=4.7.2&utmn=511965185&utmhn=&utmcs=UTF-8&utmsr=-&utmsc=-&utmul=-&utmje=0&utmfl=-&utmdt=&utmhid=27560244&utmr=/&utmp=/&utmac=UA-80584726-1&utmcc=__utma%3D0.1139529084.1732035055.1732035055.1732035055.2%3B%2B__utmz%3D0.1732035055.1.1.utmcsr%3D%28direct%29%7Cutmccn%3D%7Cutmcmd%3D%3B&utme=5%28Funnel2%2AInstaller%20Launched%2A%29%28%29&gaq=1&utmt=event | unknown | — | — | whitelisted |
3716 | OWInstaller.exe | GET | 200 | 142.250.186.174:80 | http://www.google-analytics.com/__utm.gif?utmwv=4.7.2&utmn=978749746&utmhn=&utmcs=UTF-8&utmsr=-&utmsc=-&utmul=-&utmje=0&utmfl=-&utmdt=&utmhid=303608179&utmr=/&utmp=/&utmac=UA-18298709-8&utmcc=__utma%3D0.1139529084.1732035055.1732035055.1732035055.2%3B%2B__utmz%3D0.1732035055.1.1.utmcsr%3D%28direct%29%7Cutmccn%3D%7Cutmcmd%3D%3B&utme=5%28Funnel2%2AInstaller%20Launched%2A%29%28%29&gaq=1&utmt=event | unknown | — | — | whitelisted |
3716 | OWInstaller.exe | GET | 200 | 18.66.142.79:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkpLy9ROx7U76vGUhC06D6E%3D | unknown | — | — | unknown |
3716 | OWInstaller.exe | GET | 200 | 18.66.142.79:80 | http://ocsp.rootca3.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRkNawYMzz%2BjKSfYbTyFR0AXuhs6QQUq7bb1waeN6wwhgeRcMecxBmxeMACEwdzEm3iwvr9LEetiLFWbgGCBG0%3D | unknown | — | — | unknown |
3716 | OWInstaller.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
3716 | OWInstaller.exe | GET | 200 | 142.250.184.195:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4932 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
544 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.209.148:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
analyticsnew.overwolf.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
content.overwolf.com |
| whitelisted |
ocsp.rootca3.amazontrust.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3988 | Hone - Installer.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2 ETPRO signatures available at the full report