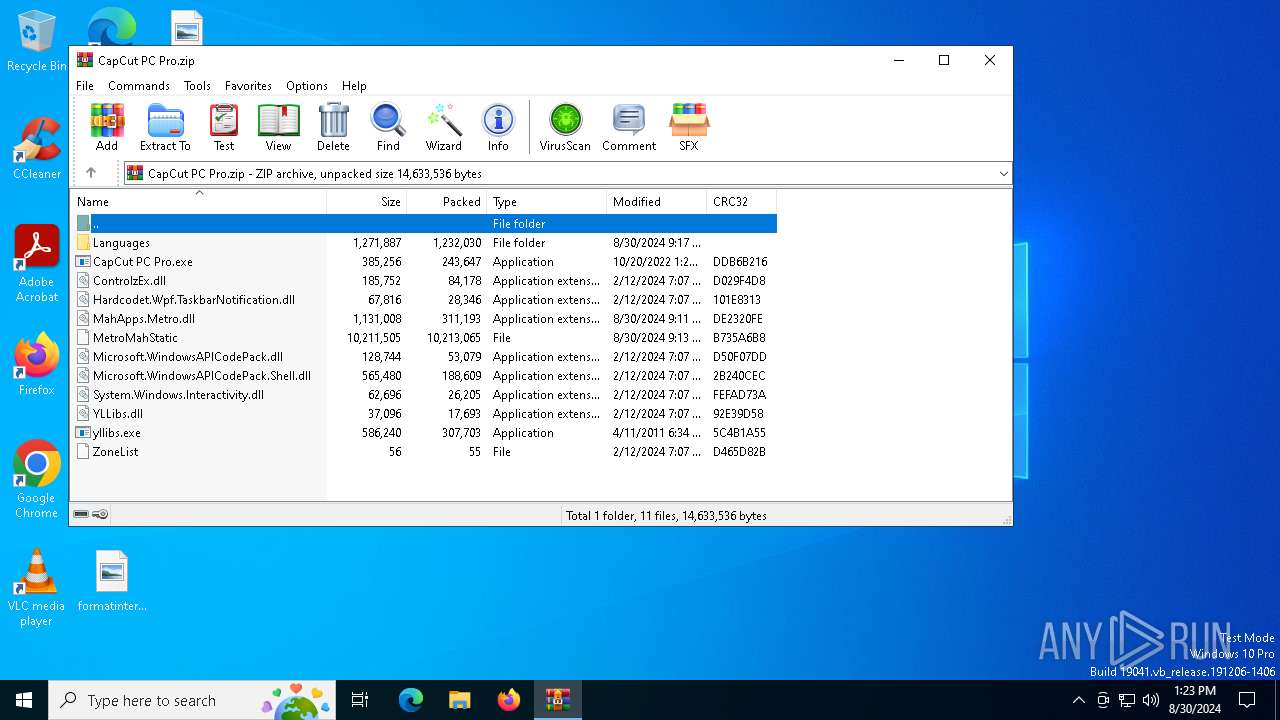
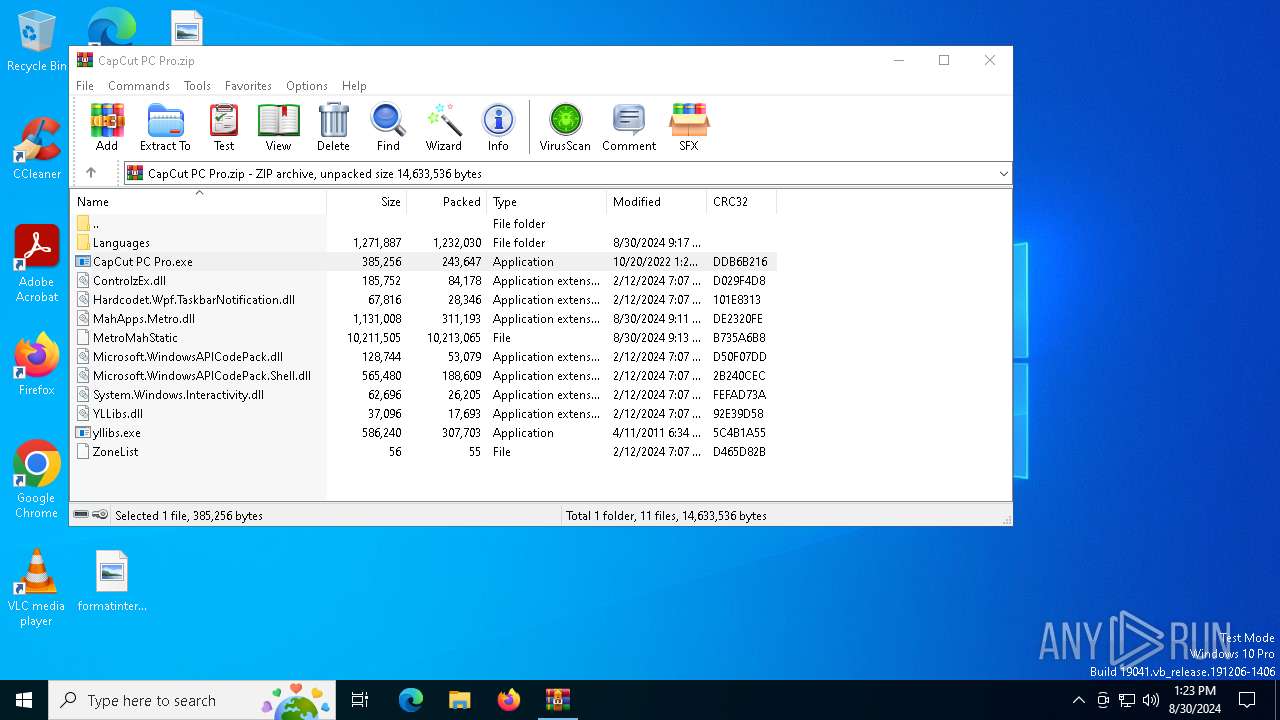
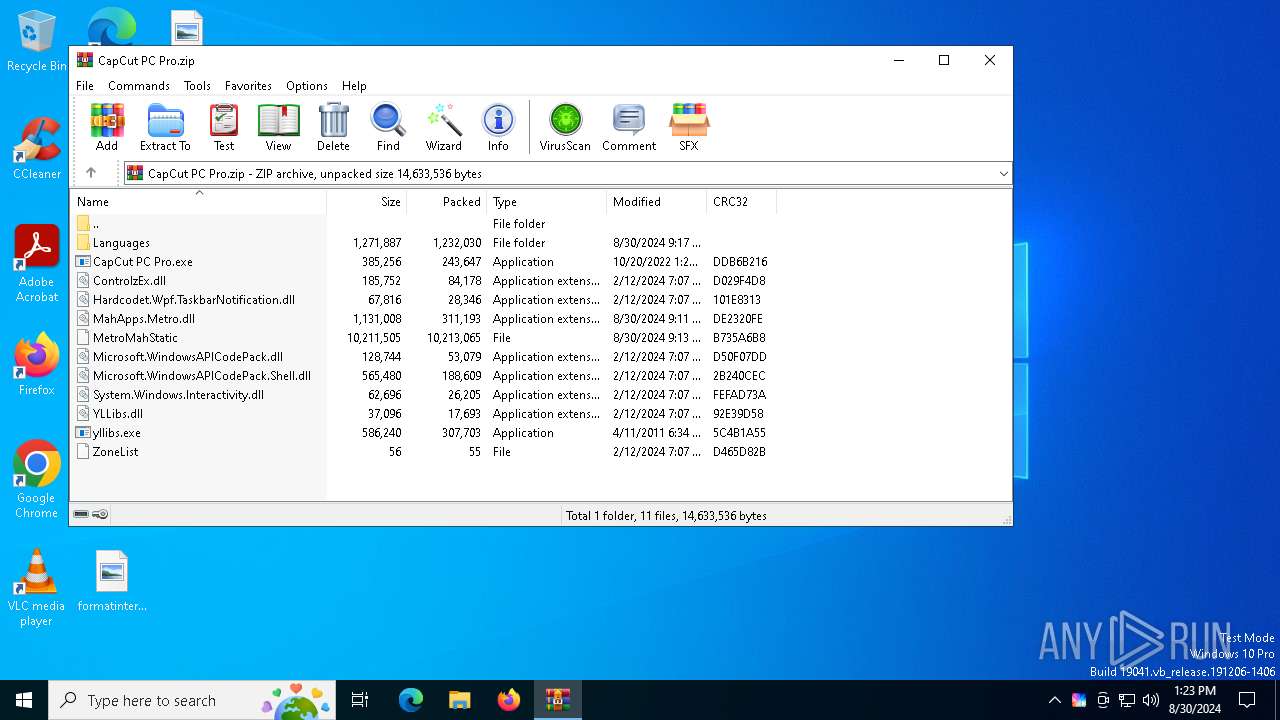
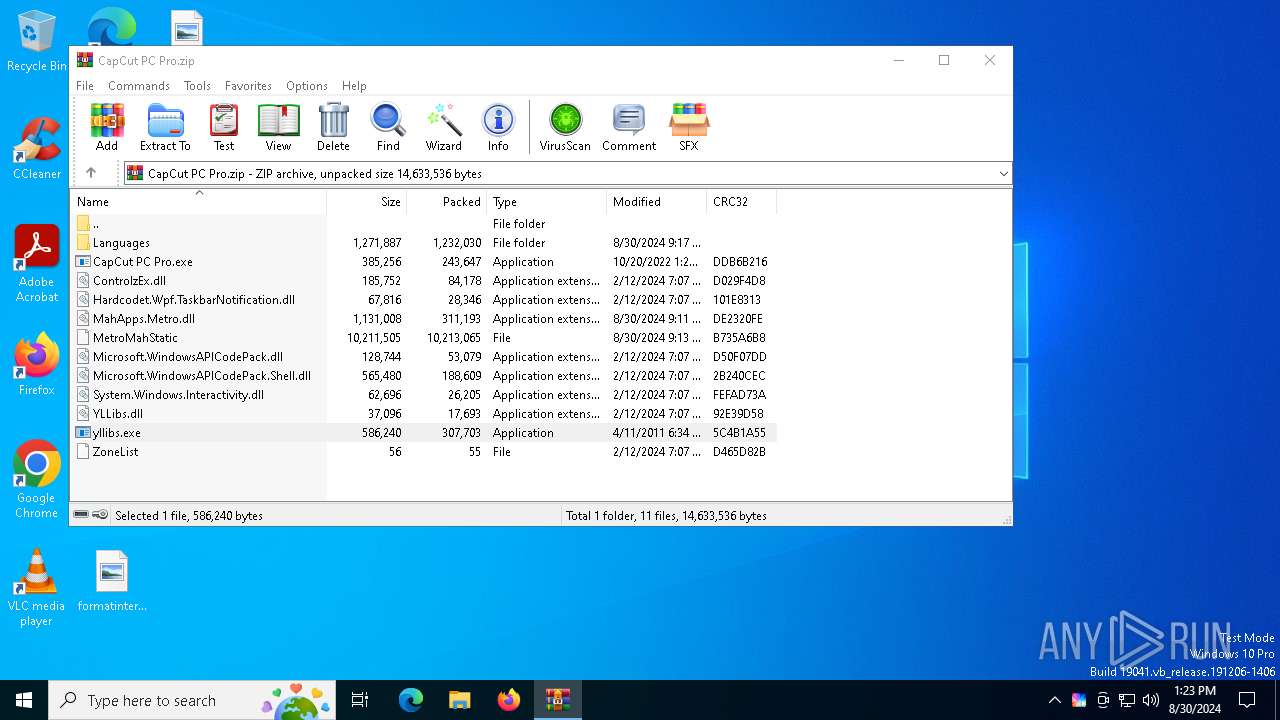
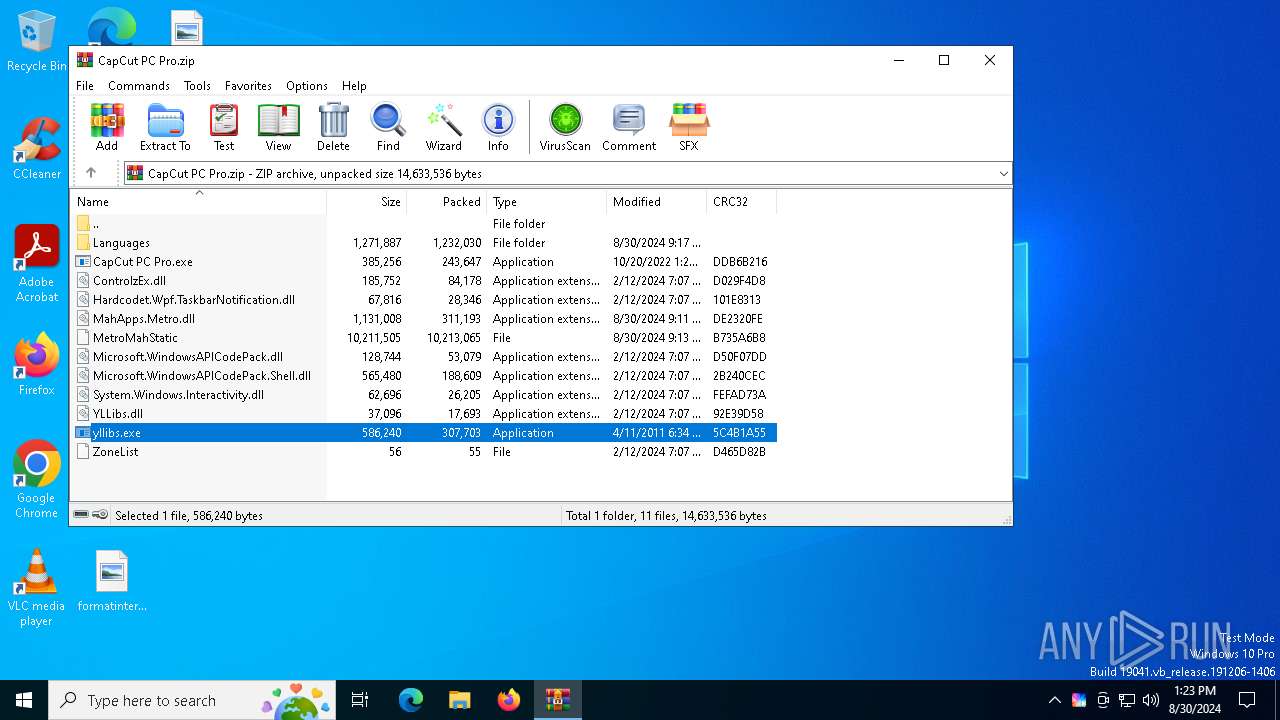
| File name: | CapCut PC Pro.zip |
| Full analysis: | https://app.any.run/tasks/592212ff-6fdf-4904-b36e-297db13e72b0 |
| Verdict: | Malicious activity |
| Analysis date: | August 30, 2024, 13:22:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 01292BA331765CEE436F037FE5843124 |
| SHA1: | 4AFCED06844B2AB6EAC9BAF5DB23E2285867E211 |
| SHA256: | 20CBA51B0CEA3E386186B46F848ED942DF8EC5AE64526457D3BFC06901018CE9 |
| SSDEEP: | 98304:LCK4TdpZC8KPWjdwJOYMTIOKGo0poAz0Ackhh061aavC64Hb1qU55cDSNzQXeZa9:M5j+rB/rE7l6iGg3B1LNsUNRPV5j |
MALICIOUS
Changes powershell execution policy (Bypass)
- CapCut PC Pro.exe (PID: 6420)
Bypass execution policy to execute commands
- powershell.exe (PID: 1124)
Run PowerShell with an invisible window
- powershell.exe (PID: 1124)
SUSPICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6884)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6884)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6884)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6884)
- CapCut PC Pro.exe (PID: 6420)
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 6884)
Starts POWERSHELL.EXE for commands execution
- CapCut PC Pro.exe (PID: 6420)
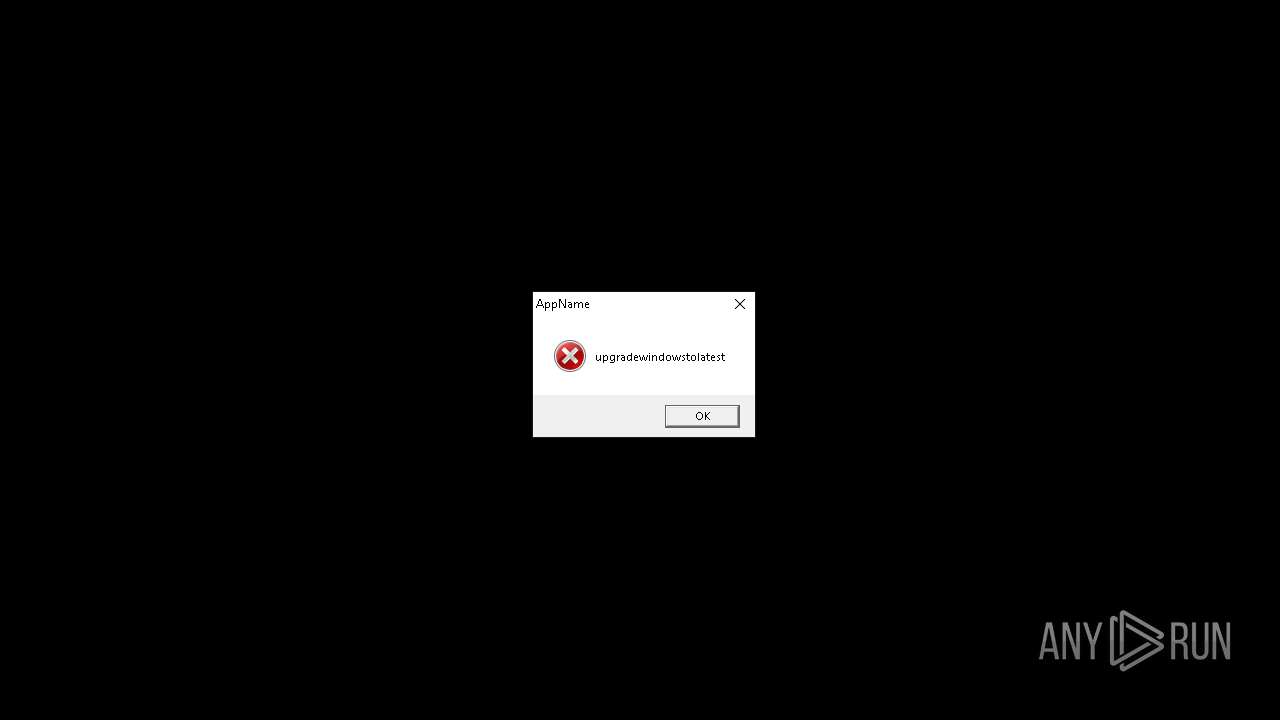
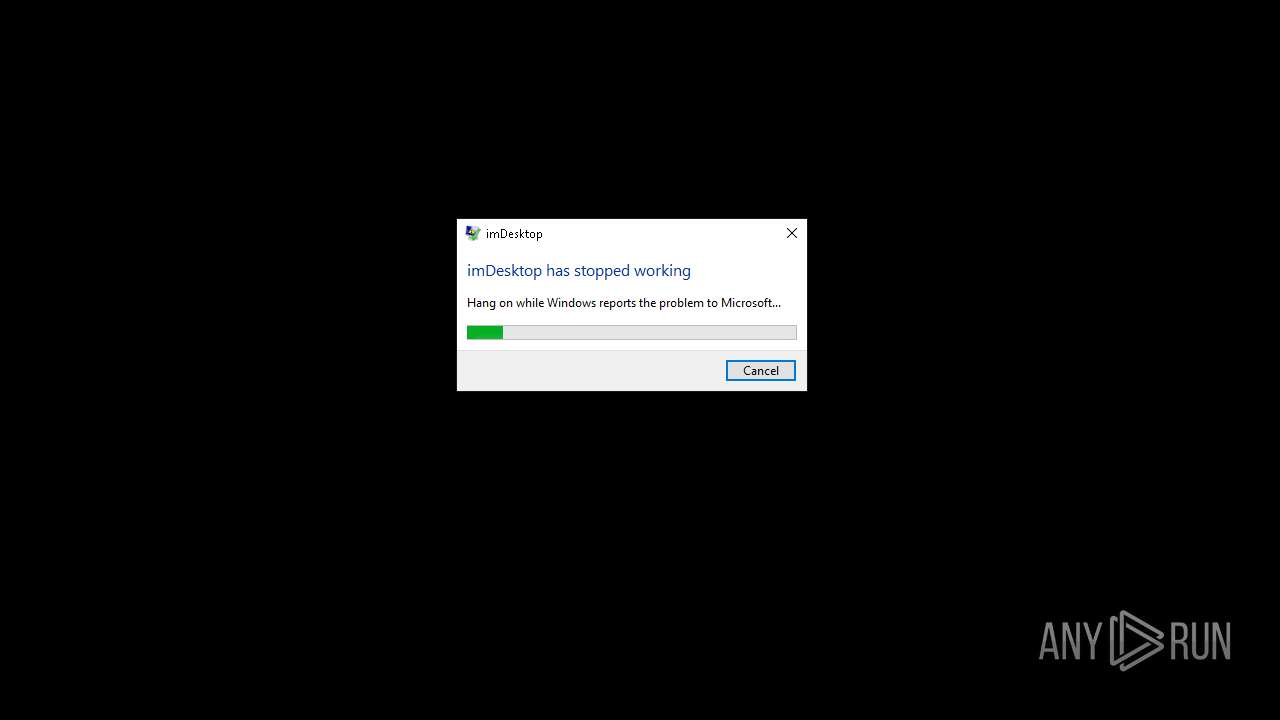
Executes application which crashes
- CapCut PC Pro.exe (PID: 6420)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6884)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6884)
Reads the machine GUID from the registry
- CapCut PC Pro.exe (PID: 6420)
Creates files or folders in the user directory
- CapCut PC Pro.exe (PID: 6420)
- WerFault.exe (PID: 236)
- WerFault.exe (PID: 3908)
Reads the computer name
- CapCut PC Pro.exe (PID: 6420)
Checks supported languages
- CapCut PC Pro.exe (PID: 6420)
- yllibs.exe (PID: 4020)
Reads the software policy settings
- WerFault.exe (PID: 236)
Checks proxy server information
- WerFault.exe (PID: 3908)
- WerFault.exe (PID: 236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (33.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:10:20 20:24:16 |
| ZipCRC: | 0xddb6b216 |
| ZipCompressedSize: | 243647 |
| ZipUncompressedSize: | 385256 |
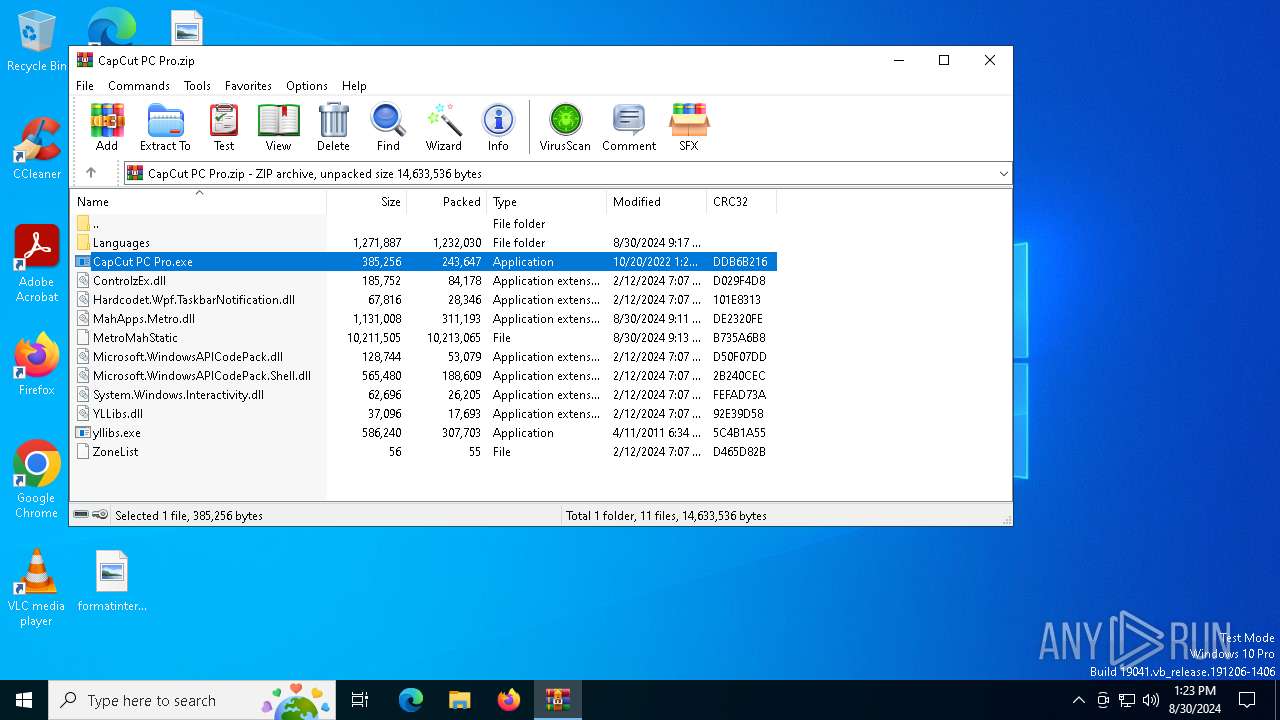
| ZipFileName: | CapCut PC Pro.exe |
Total processes
130
Monitored processes
8
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | C:\WINDOWS\system32\WerFault.exe -u -p 6420 -s 2800 | C:\Windows\System32\WerFault.exe | CapCut PC Pro.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1124 | "powershell.exe" -WindowStyle Hidden -ExecutionPolicy Bypass -Command "(Get-CimInstance -ClassName Win32_VideoController).Caption;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | CapCut PC Pro.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3908 | C:\WINDOWS\system32\WerFault.exe -u -p 6420 -s 2700 | C:\Windows\System32\WerFault.exe | — | CapCut PC Pro.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4020 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6884.2003\yllibs.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6884.2003\yllibs.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Exit code: 0 Version: 9.21 beta Modules
| |||||||||||||||
| 6128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | yllibs.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6420 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6884.49667\CapCut PC Pro.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6884.49667\CapCut PC Pro.exe | WinRAR.exe | ||||||||||||
User: admin Company: YL Computing Integrity Level: MEDIUM Description: imDesktop Exit code: 3221226525 Version: 2.0.0.0 Modules
| |||||||||||||||
| 6884 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\CapCut PC Pro.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 102
Read events
21 060
Write events
41
Delete events
1
Modification events
| (PID) Process: | (6884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\CapCut PC Pro.zip | |||
| (PID) Process: | (6884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
18
Suspicious files
6
Text files
38
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6884.49667\MetroMahStatic | — | |
MD5:— | SHA256:— | |||
| 6884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6884.49667\Hardcodet.Wpf.TaskbarNotification.dll | executable | |
MD5:D5D708E9E7625AB2C4AC1C1FAA099350 | SHA256:F6FADF0375D22512B2B3F075362433C0DE173ADFB290B4D8999CDCB7ACEDB0B2 | |||
| 6884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6884.49667\Microsoft.WindowsAPICodePack.Shell.dll | executable | |
MD5:18A46202A1636B985208E2183D756617 | SHA256:513D386FC084AD355D1A8668D8B4E43CC3B21F135AC3EABBC6B96ADEB3EE9E84 | |||
| 6884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6884.49667\MahApps.Metro.dll | executable | |
MD5:D52FA1E2F08ECEEB8DBE5AD0BE0DAE4E | SHA256:54F2B67E0AAE73B4C82142145E57CBEE07C710D37CC26FBCFB2399CC84EA062A | |||
| 6884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6884.49667\CapCut PC Pro.exe | executable | |
MD5:A8BC7FB55A324F1BA1C7807B7C1C4F29 | SHA256:F17B6DC2F1DC25B982D1D3DA8601121A1F21E16BE3FE406D3CFF62100CF7562B | |||
| 6884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6884.49667\ControlzEx.dll | executable | |
MD5:2D5035CB5A3678F2C2F5A889BD384813 | SHA256:424CBE8F24A62C330149DBE0B80E214A984950C3B79B067058671608229FC2ED | |||
| 6884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6884.49667\Languages\English.png | image | |
MD5:00214D9E4E6155A04E3997D121641C98 | SHA256:1037BB804C8DA171FB1869872BCD24AA1F0C96AD8CE783861DFF91D3174D12A7 | |||
| 6884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6884.49667\Languages\Polish.png | image | |
MD5:464A2897BC125872878D68AEF0EF18BF | SHA256:5400F9D9FF3272227E66A840AEB52A8489393B04E32BD7E03C1BFE6A9A832A6B | |||
| 6884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6884.49667\System.Windows.Interactivity.dll | executable | |
MD5:E991D47605BC04629AF29939AC2CC9B5 | SHA256:EDA12487C479FF31202A3C60F88F1F0E2BF7392919099315D0D951683F14609C | |||
| 6884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6884.49667\Languages\Dombe.txt | text | |
MD5:5F946AE17824CF7673E431B0F4D354F2 | SHA256:D0022EE6BAF18F8F1787820E157F87A4D59DE0936DBE4DCAF4E928DE2877467D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
27
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1828 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4056 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4056 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
6232 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6020 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1828 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1828 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6232 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |