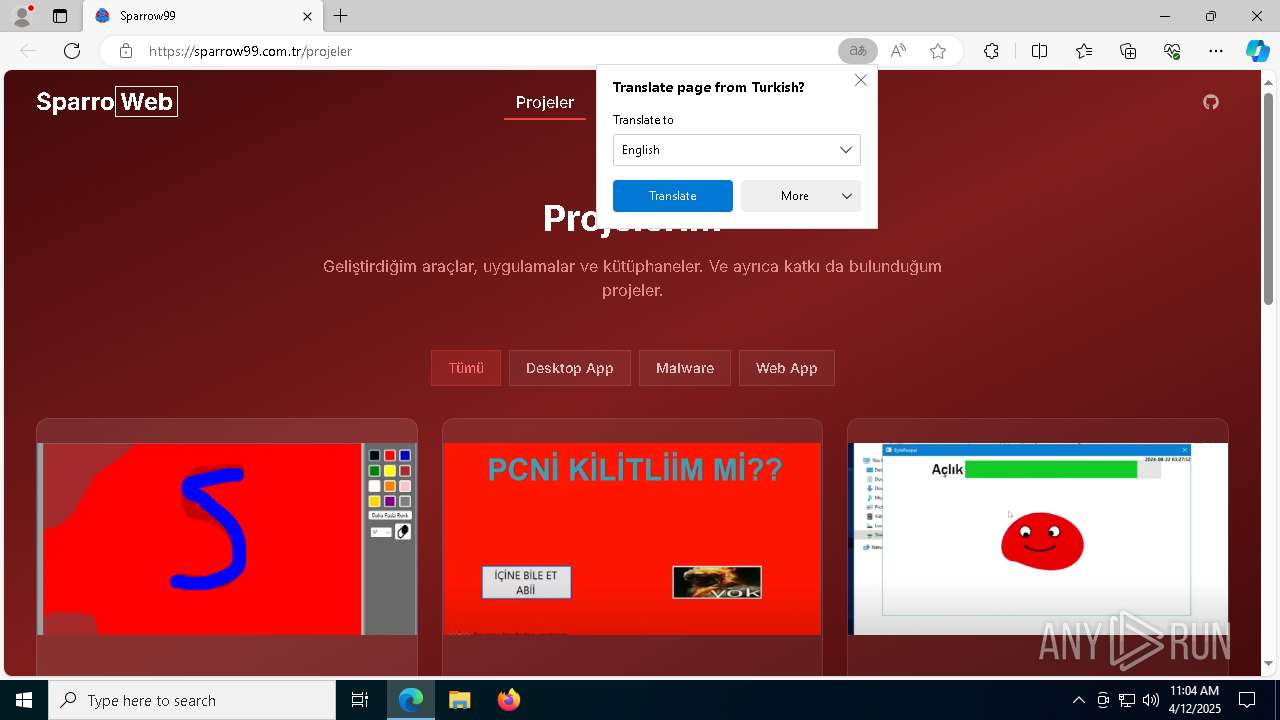
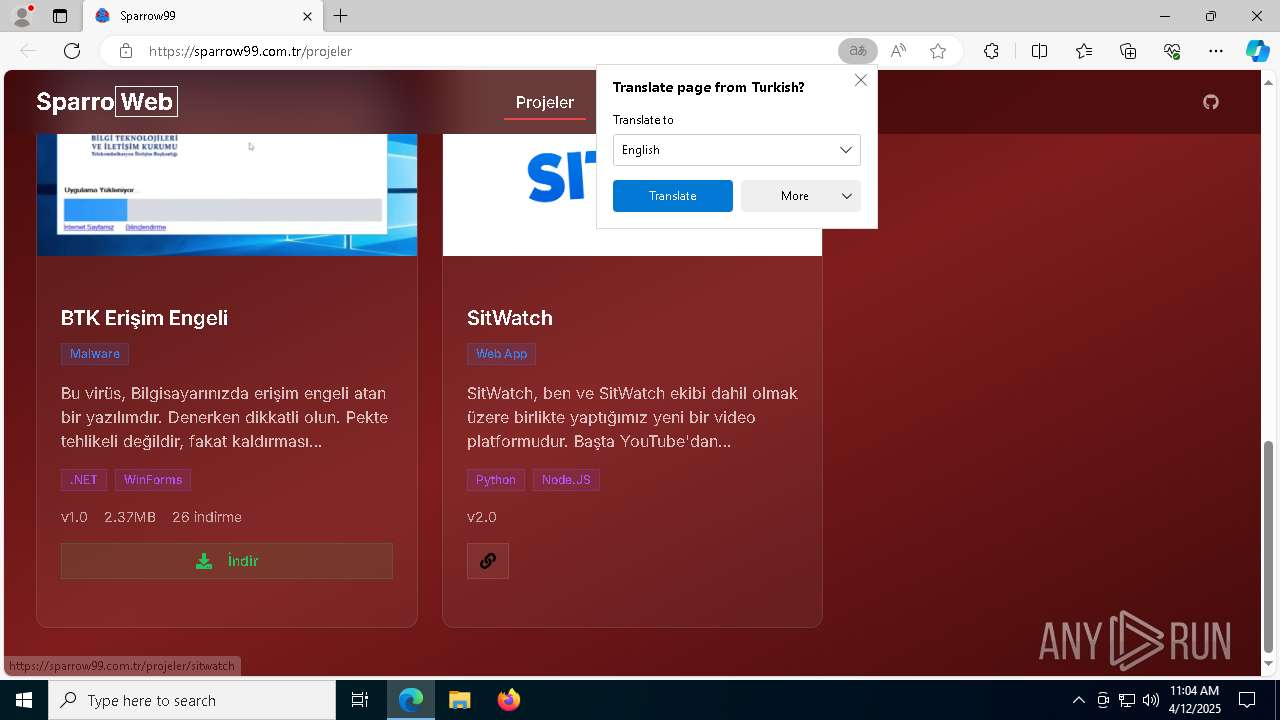
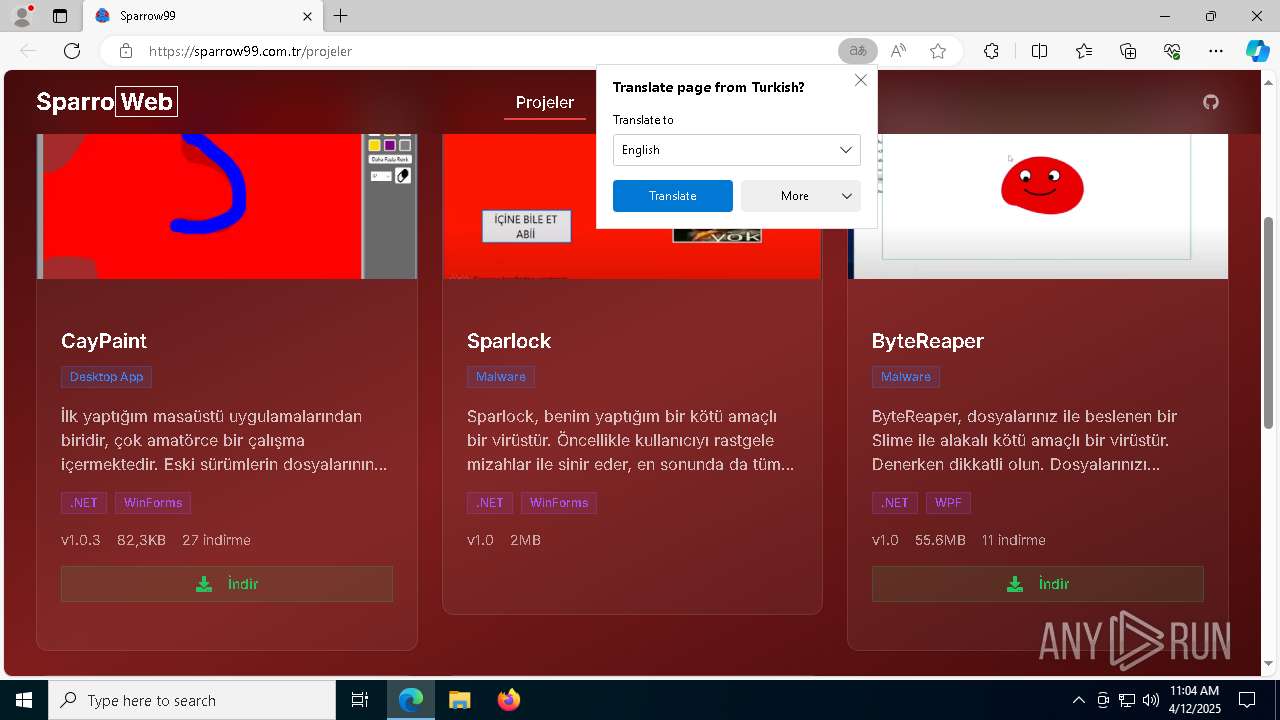
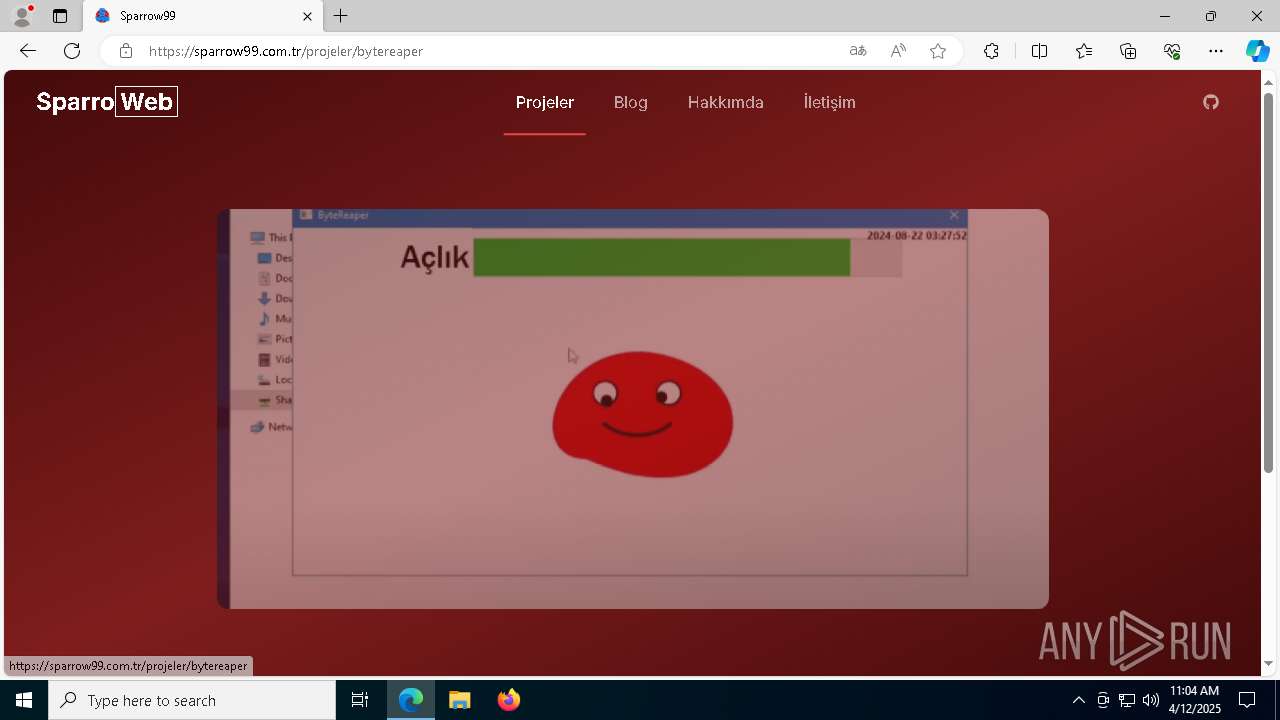
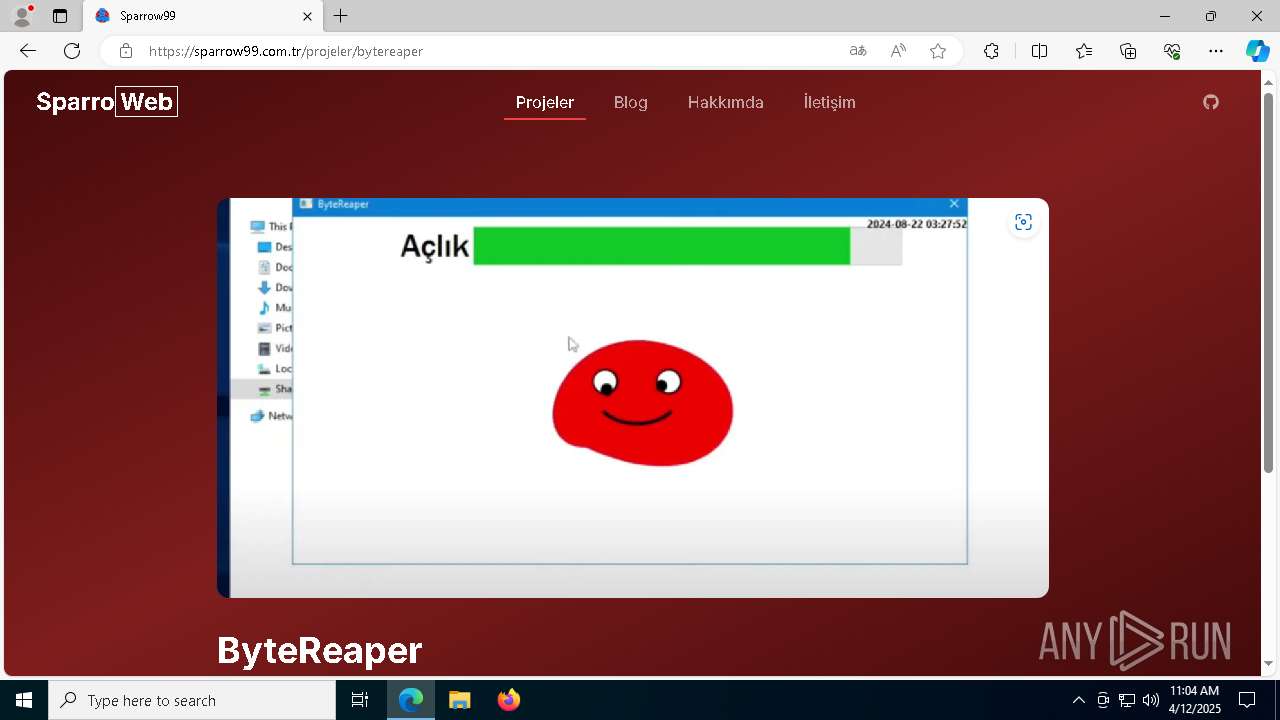
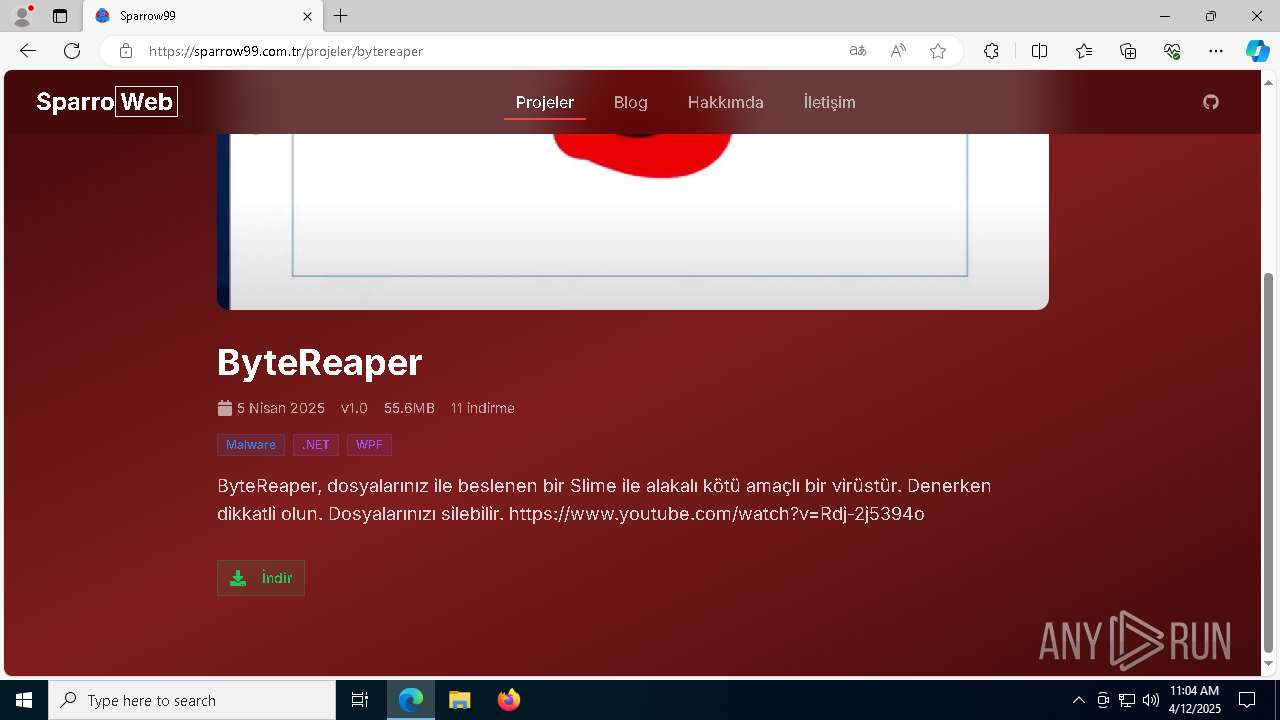
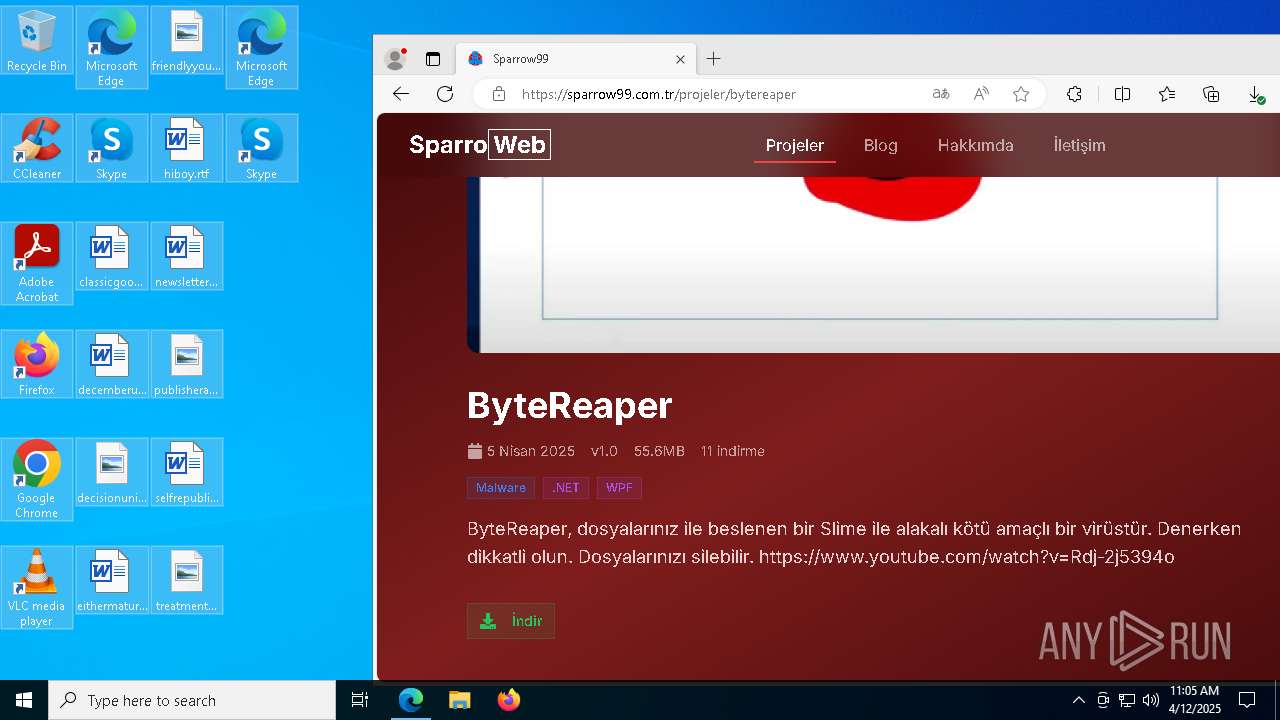
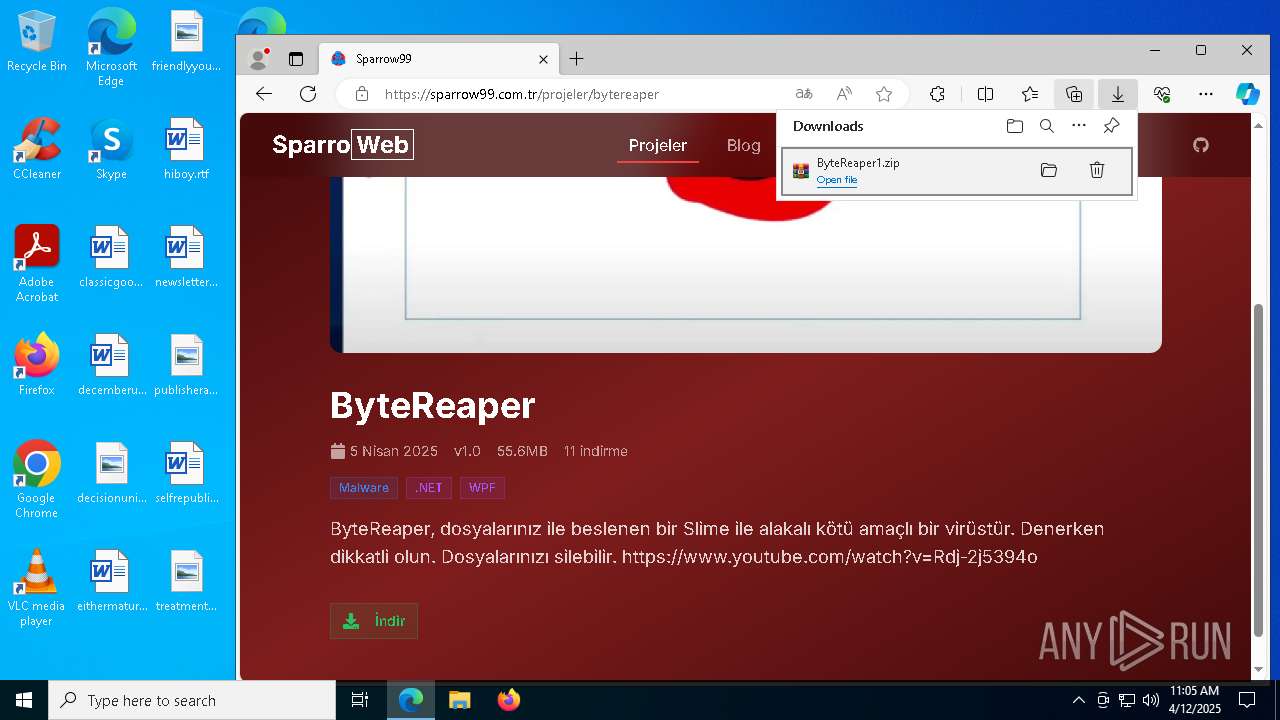
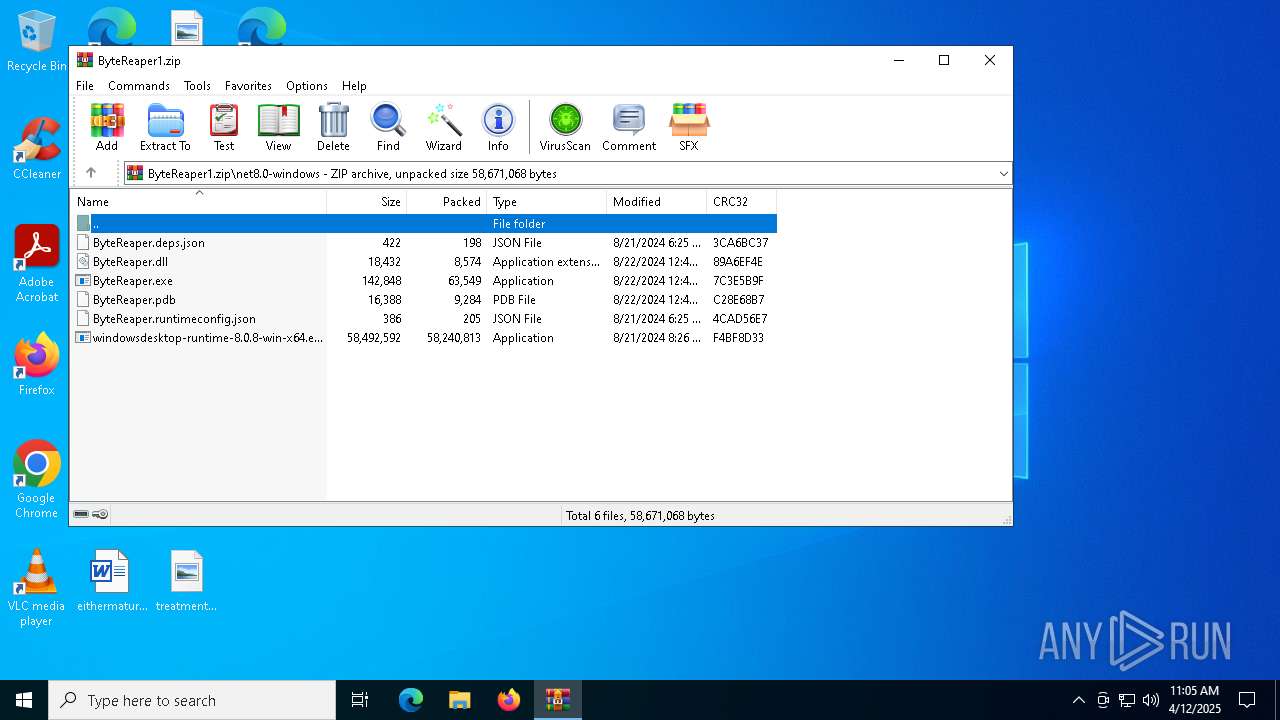
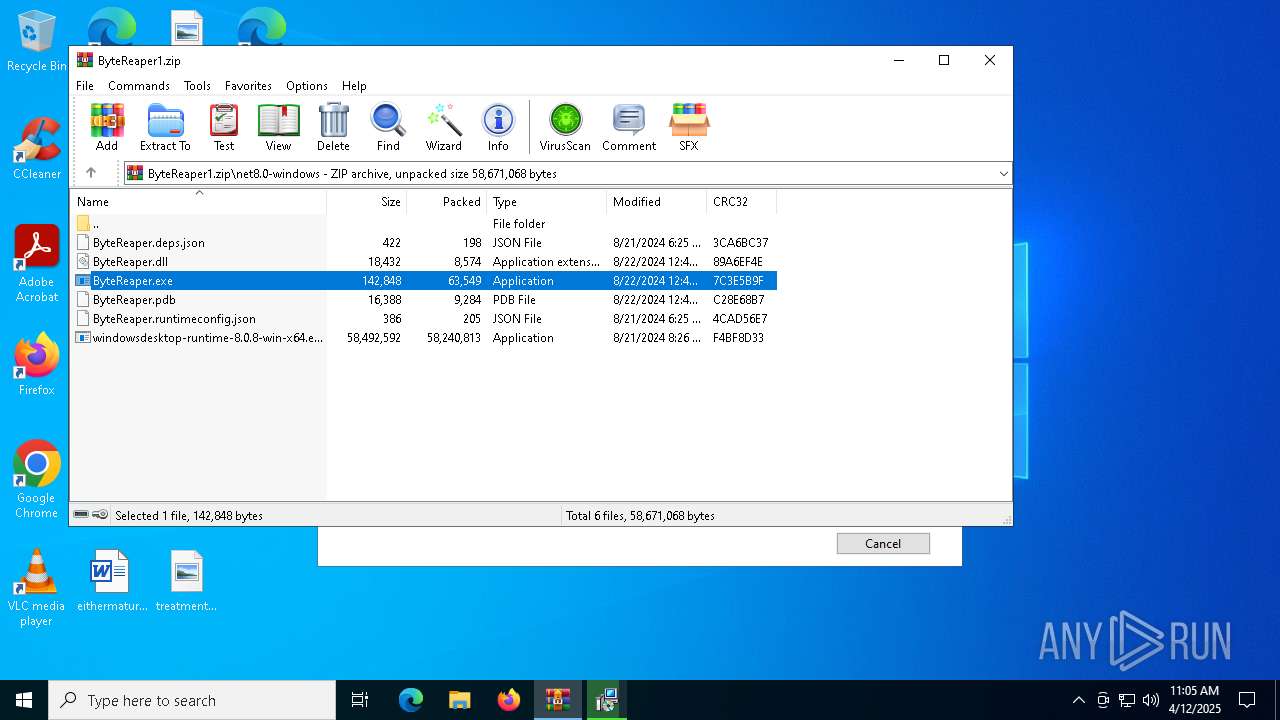
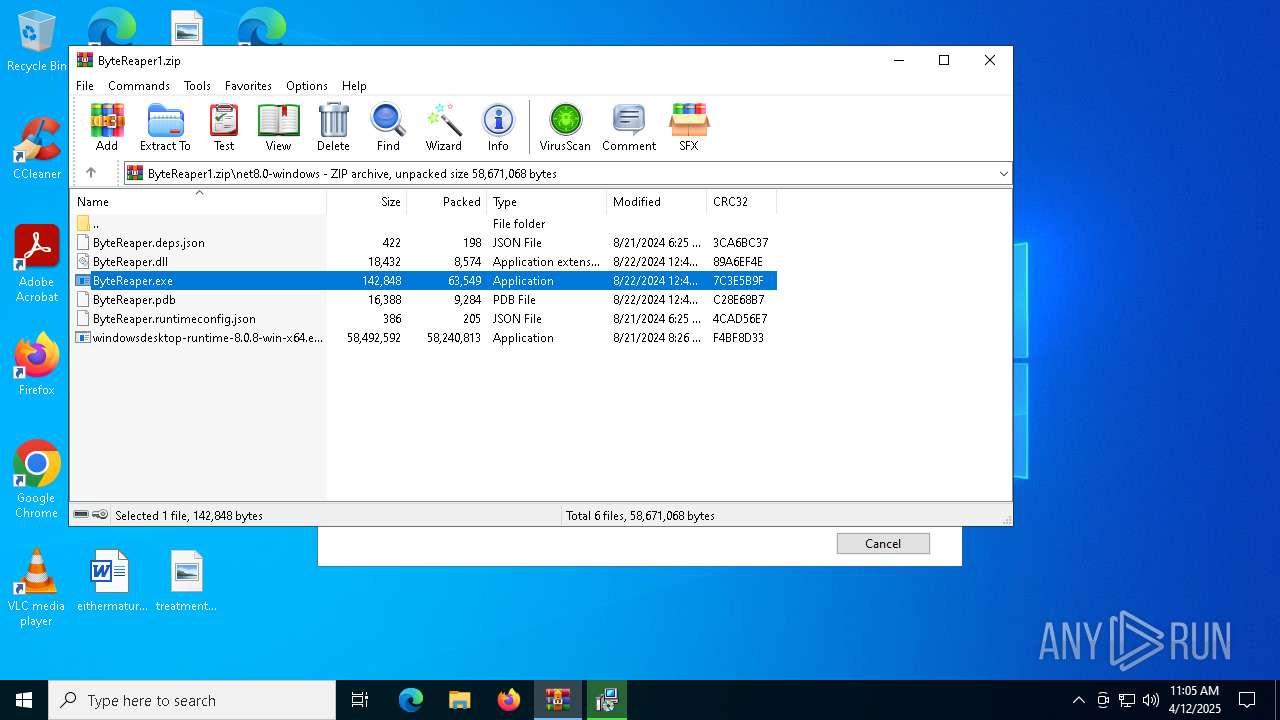
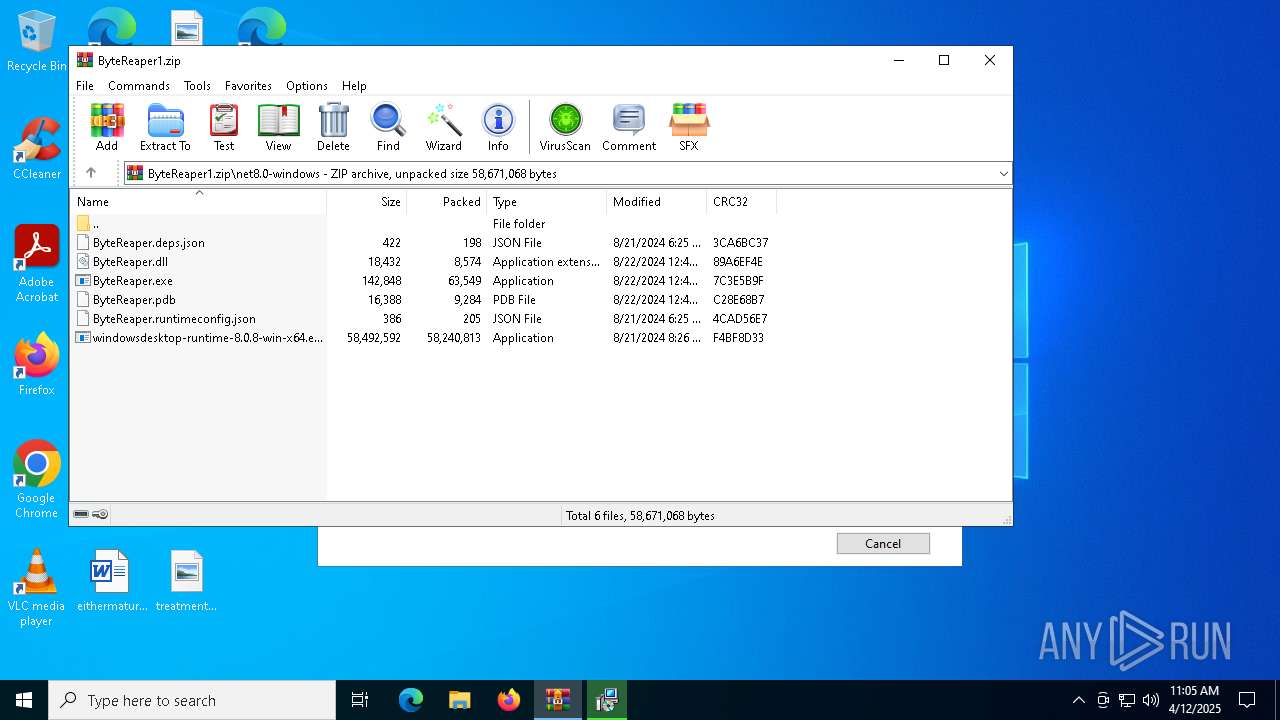
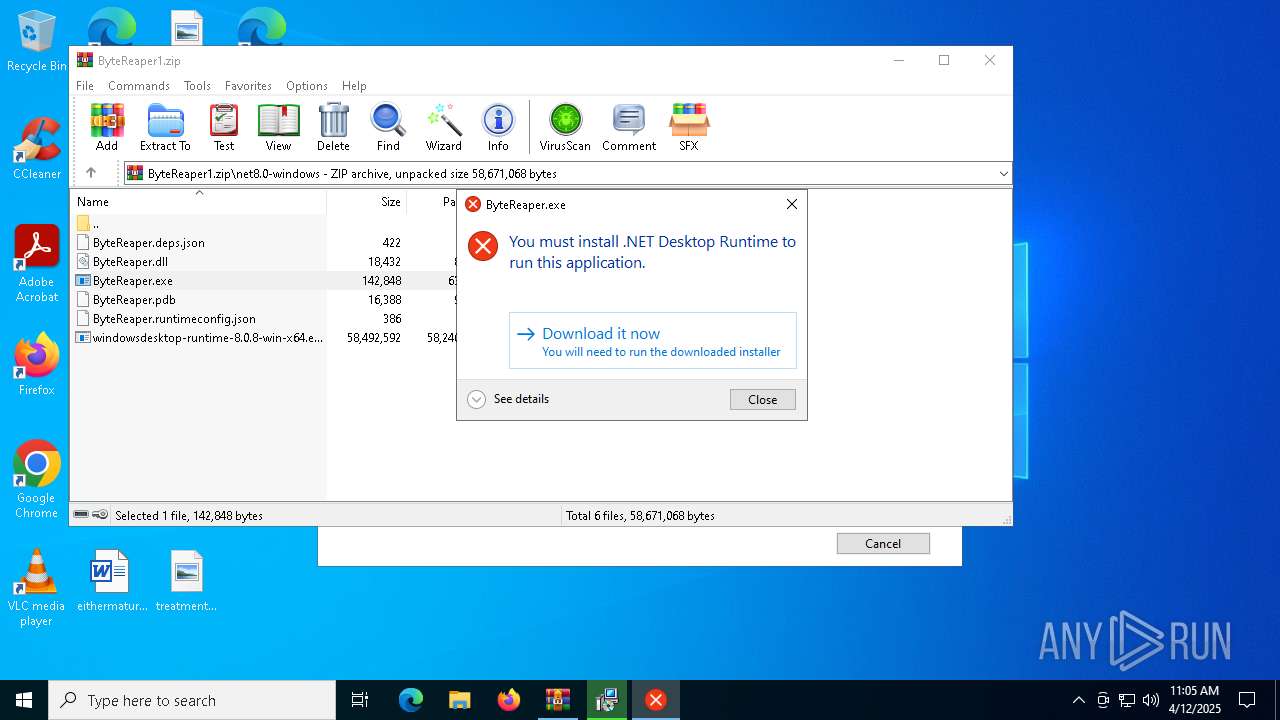
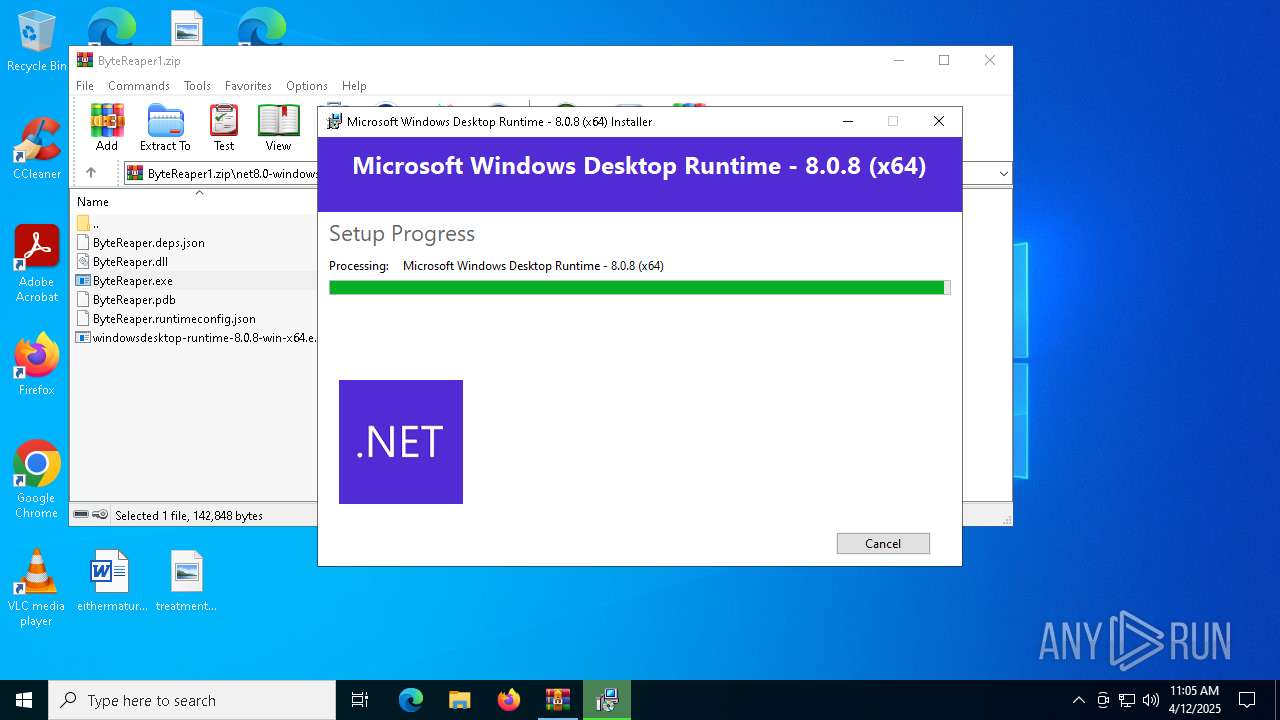
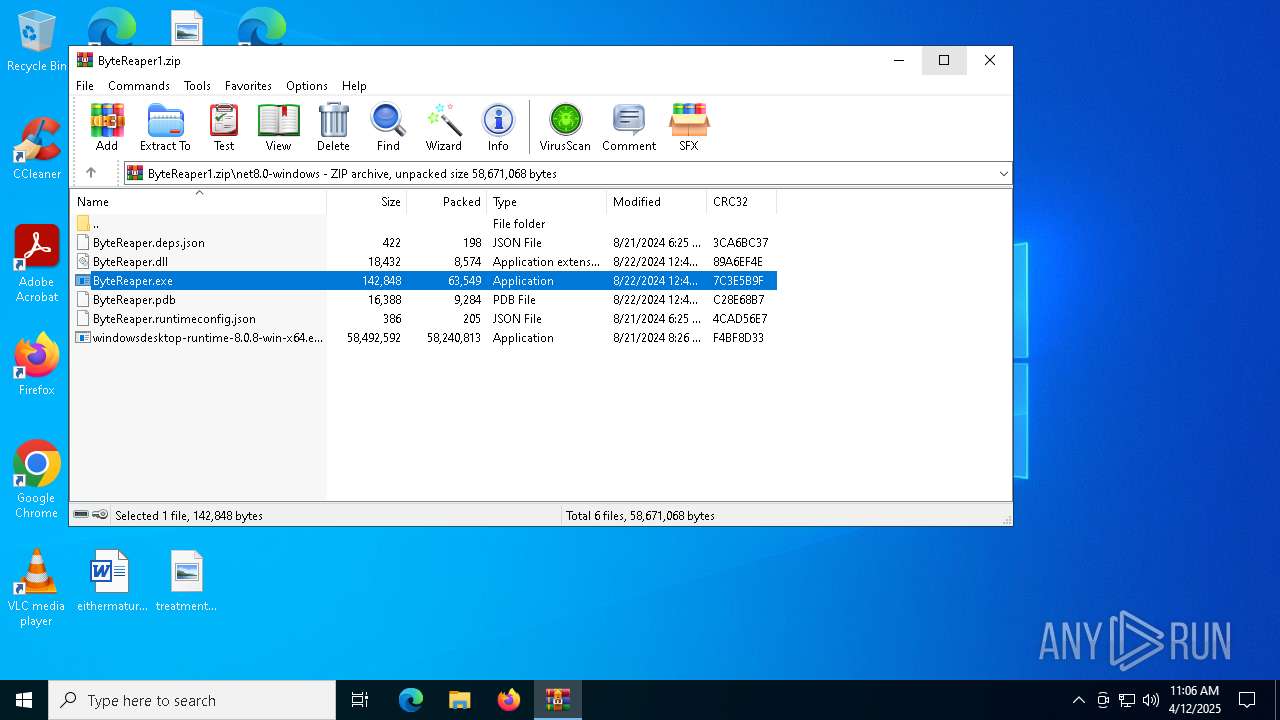
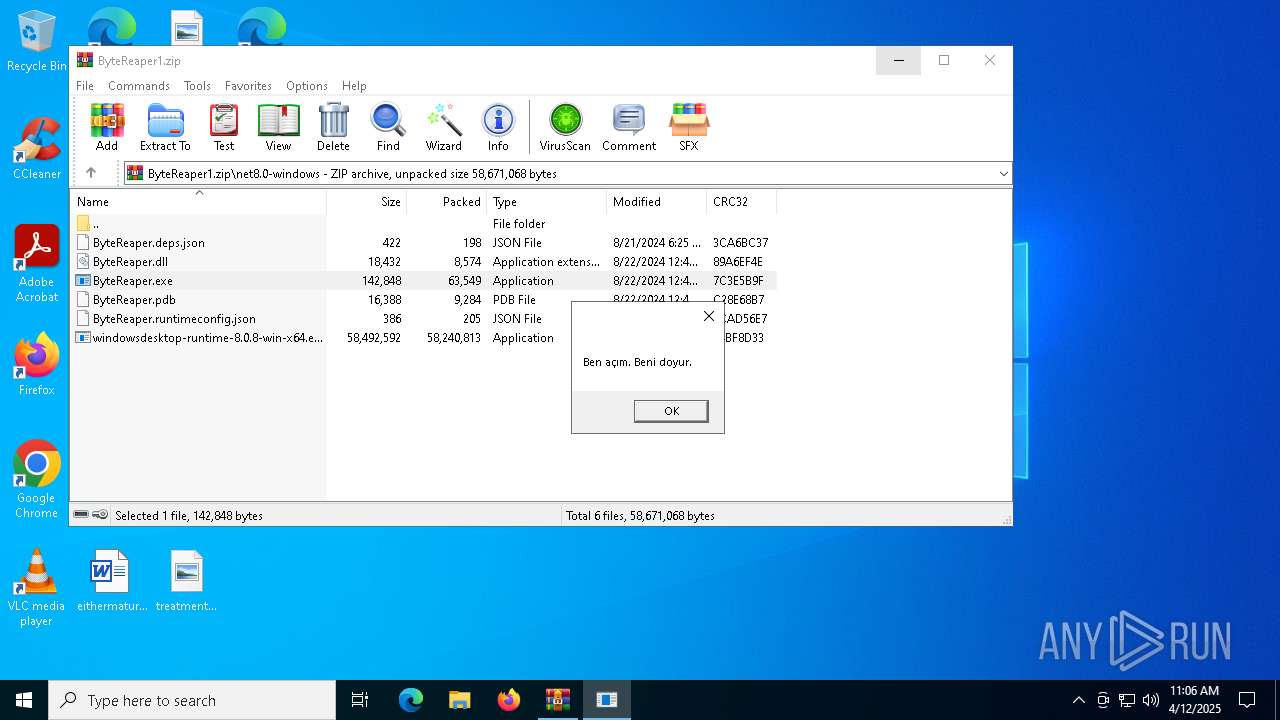
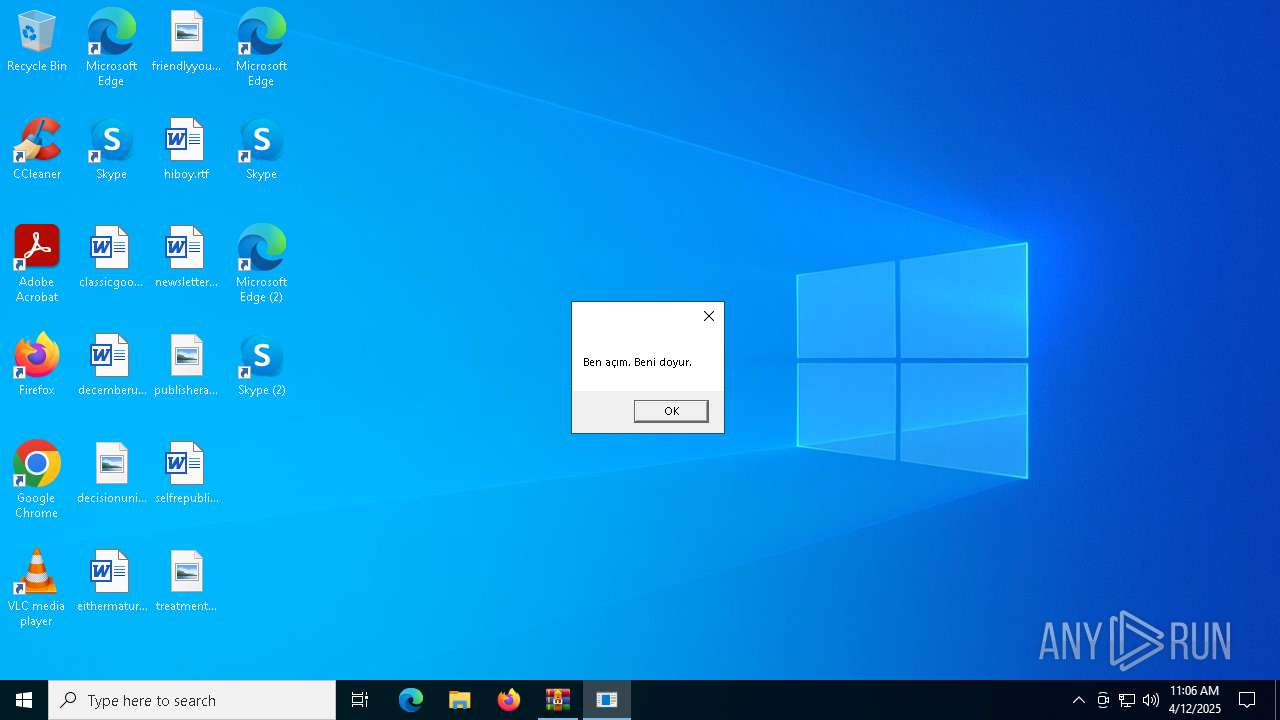
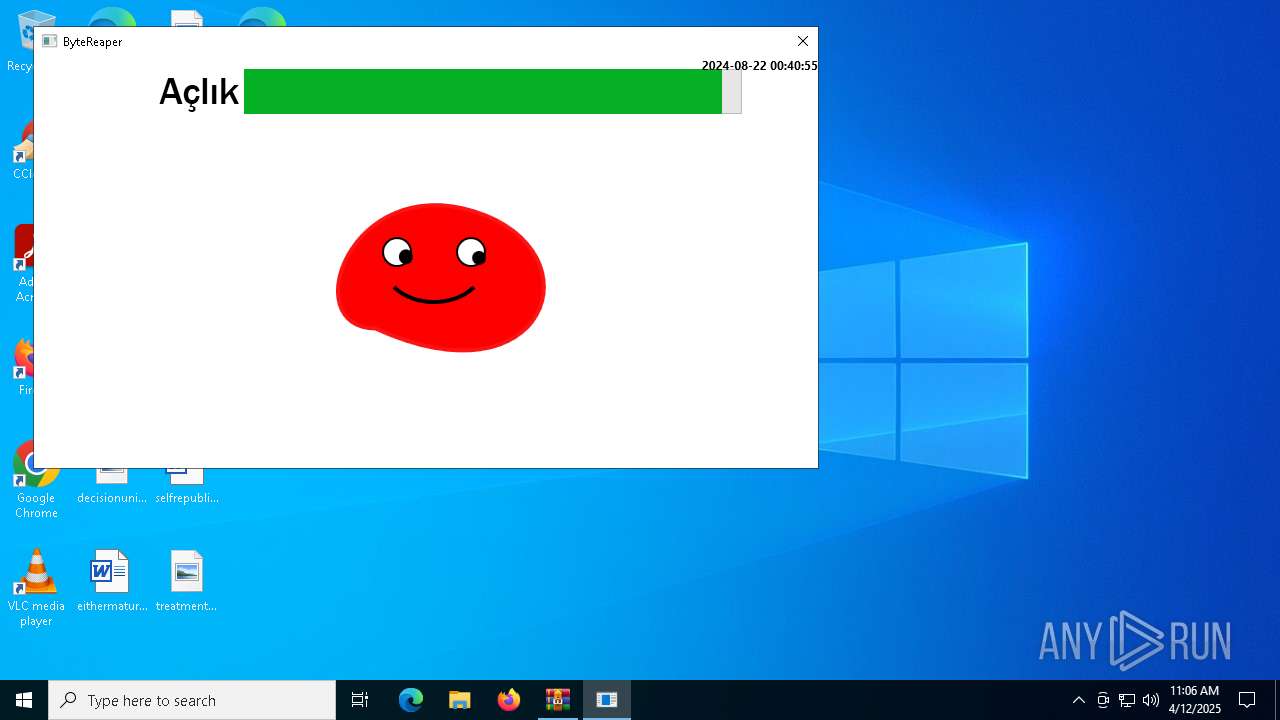
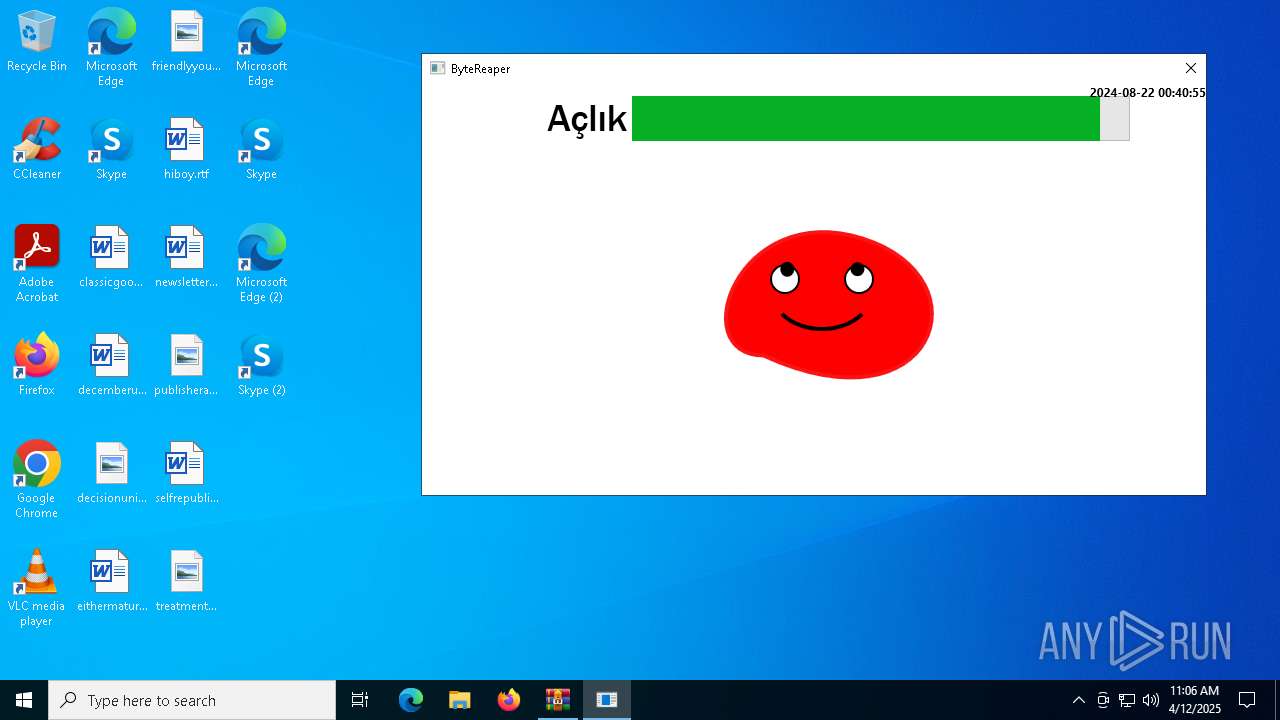
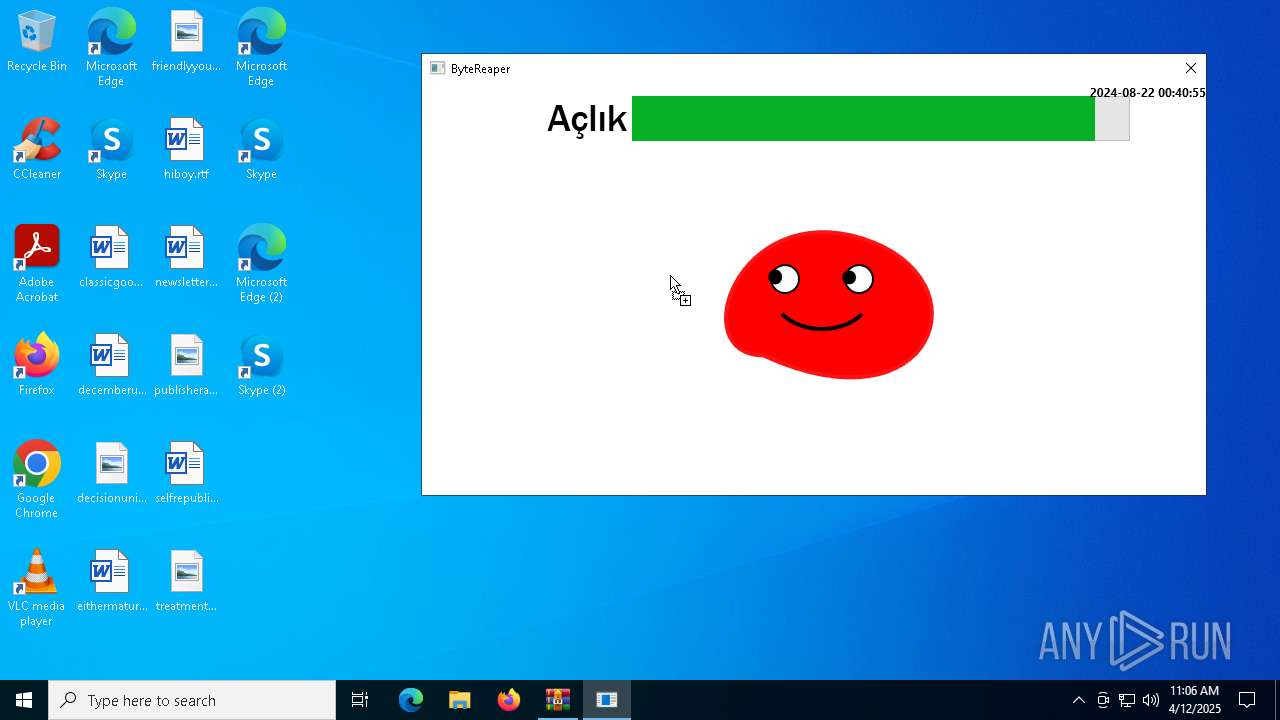
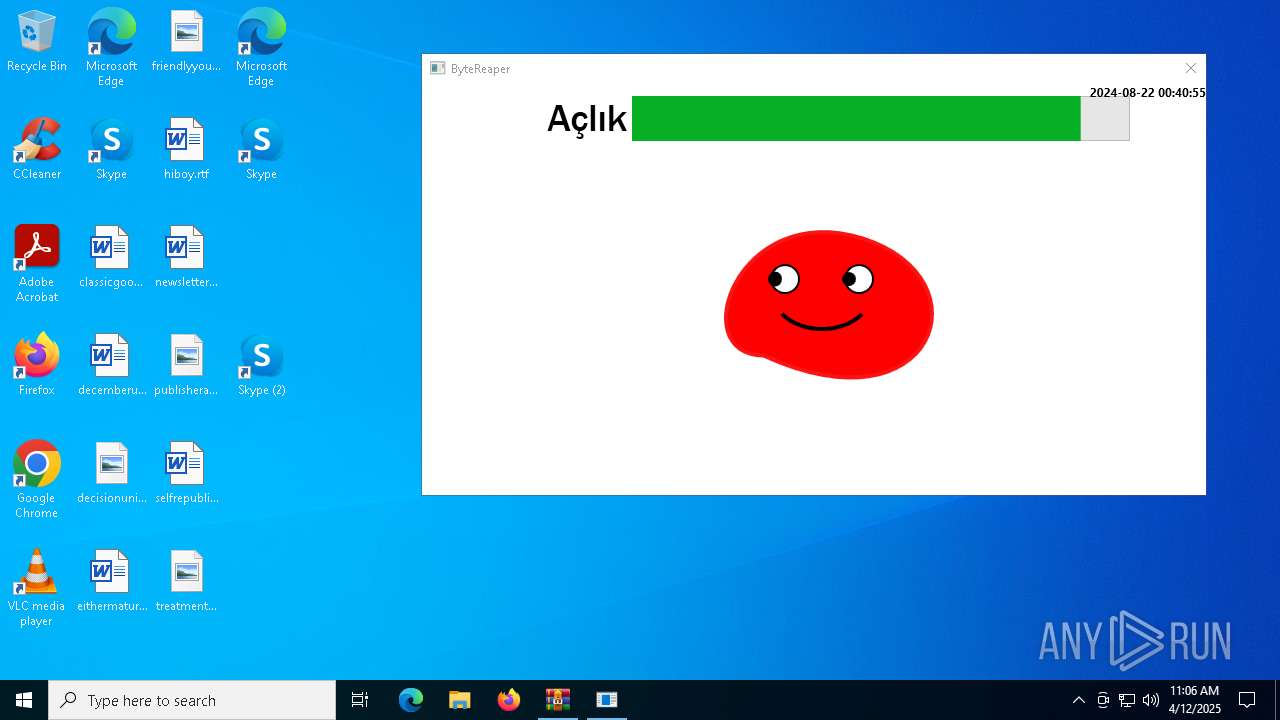
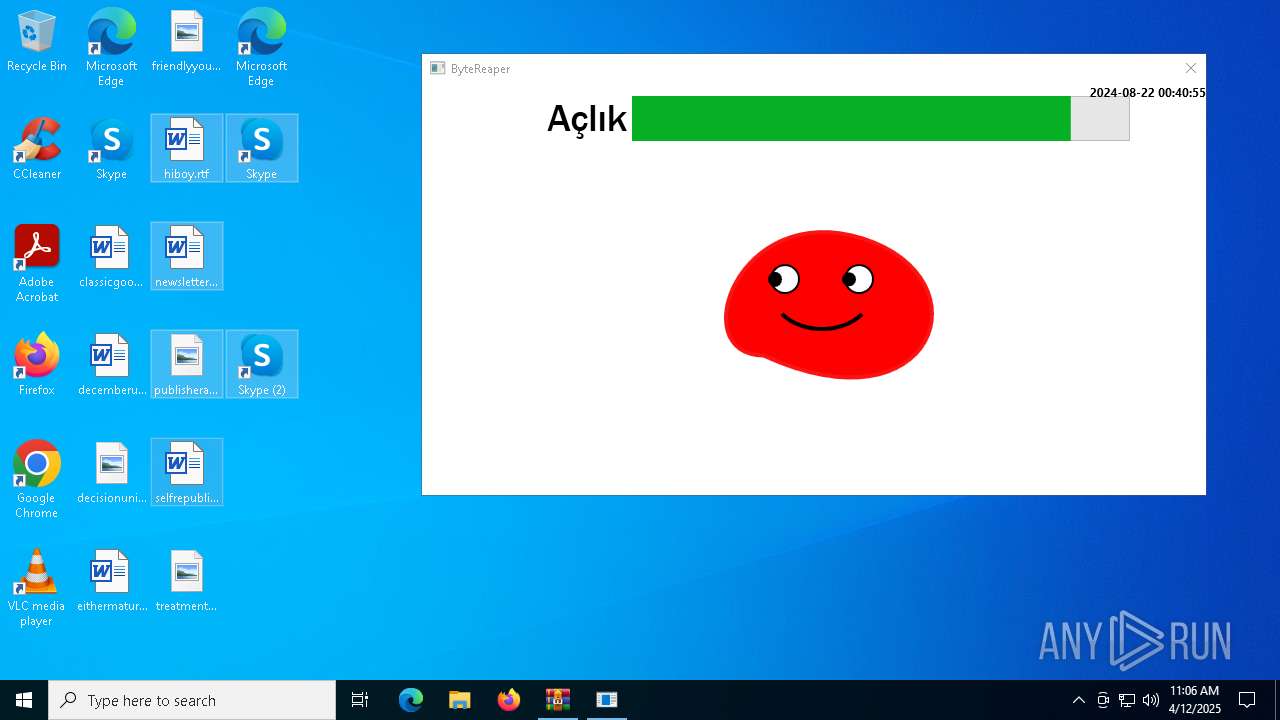
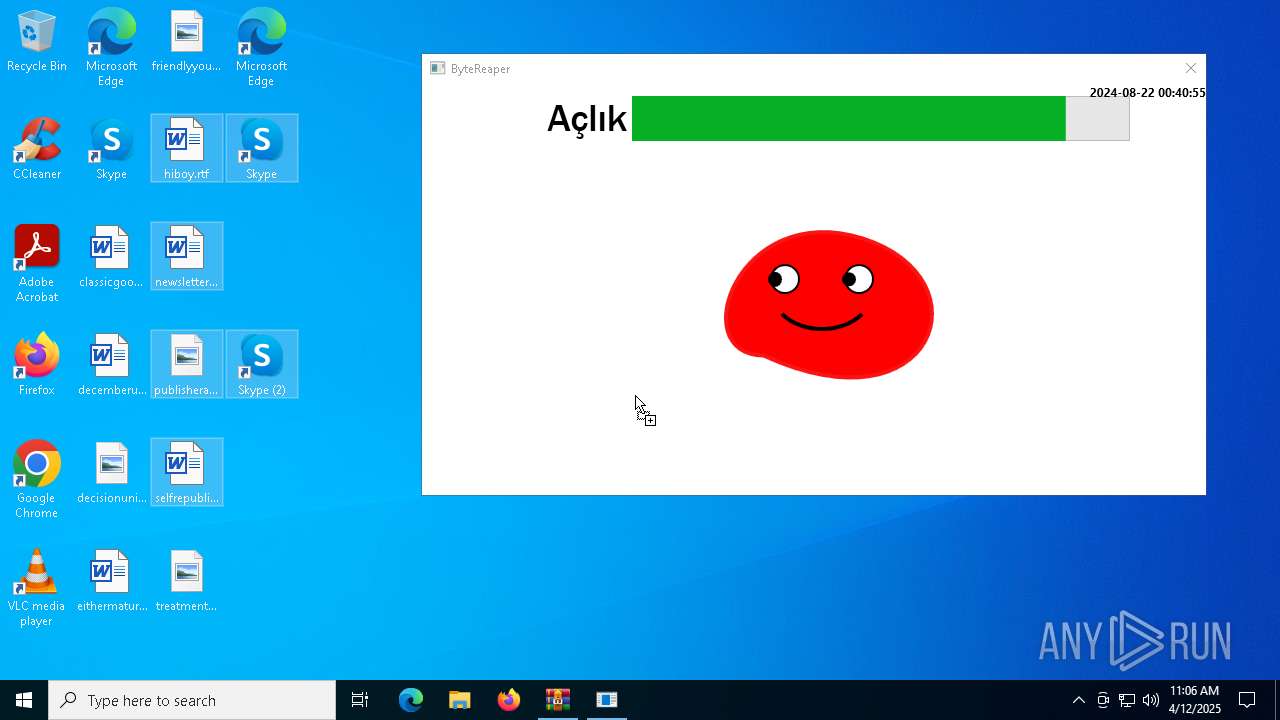
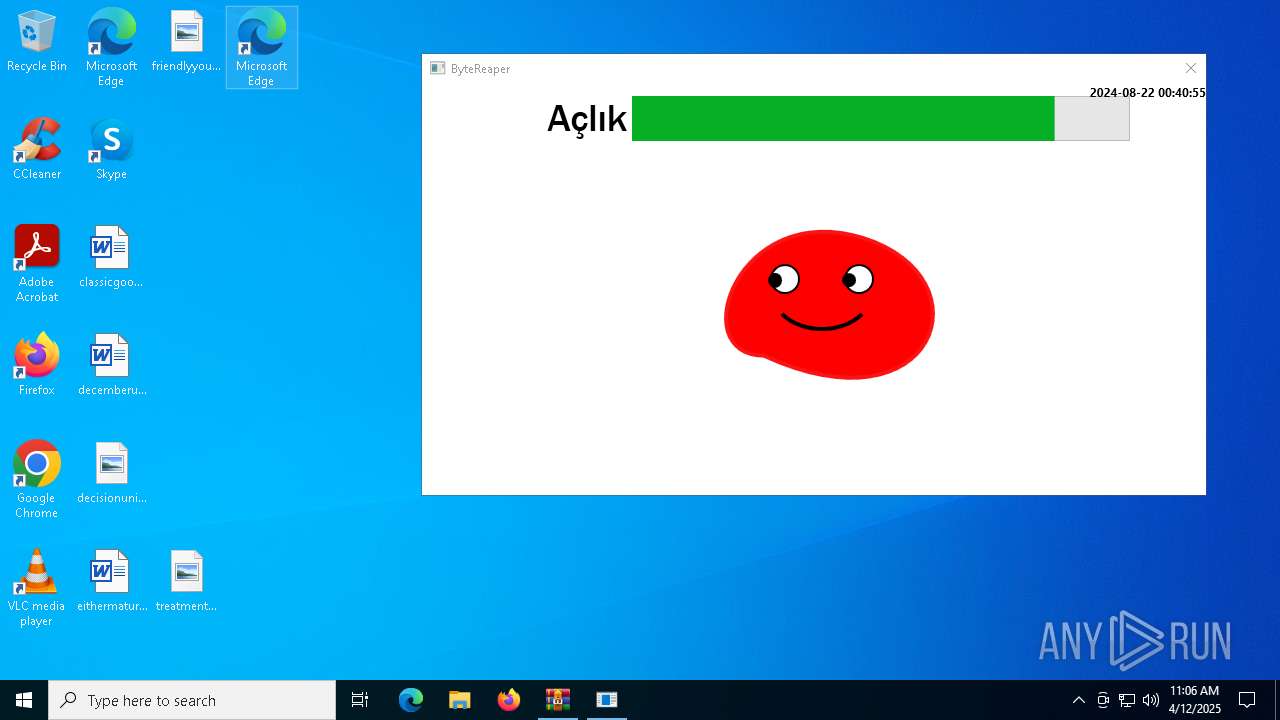
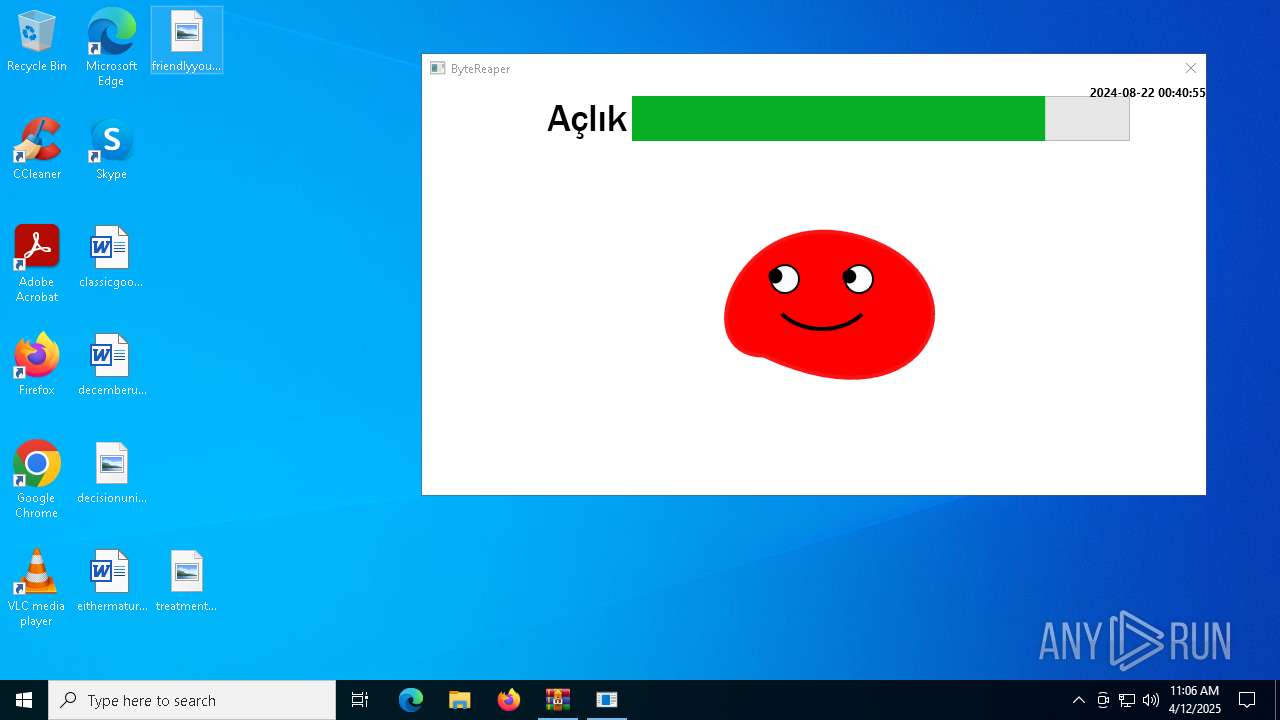
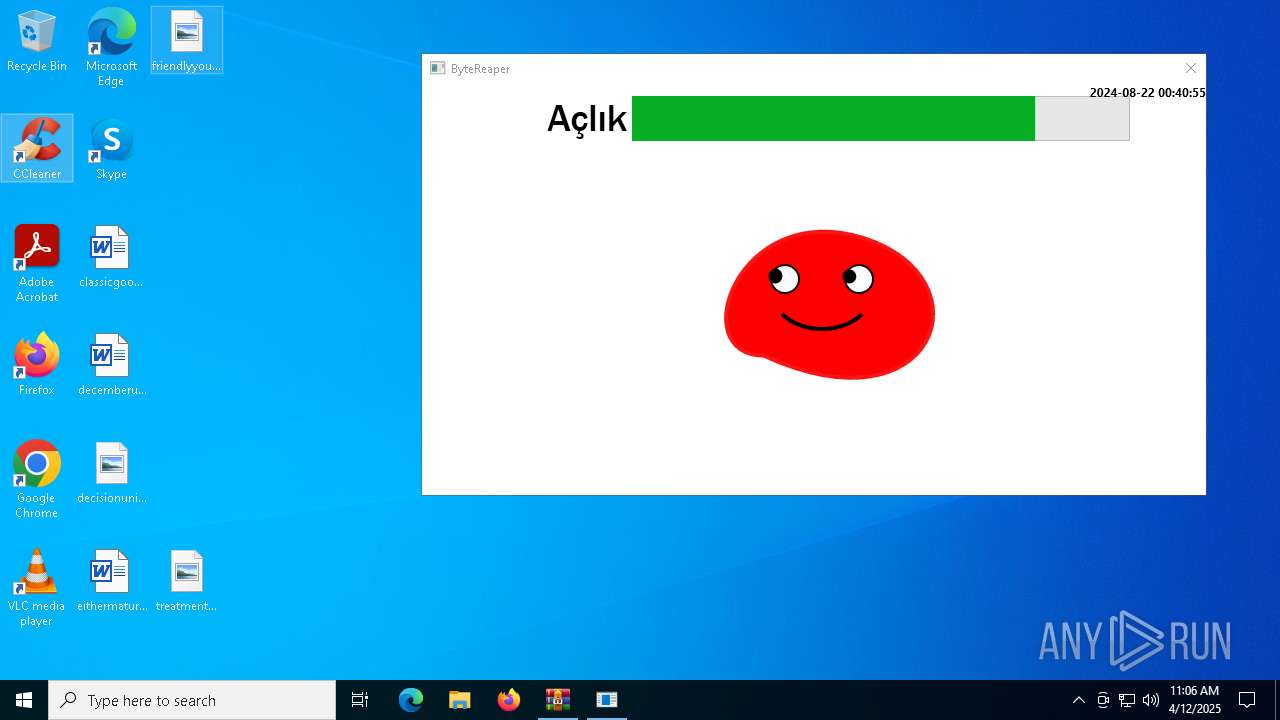
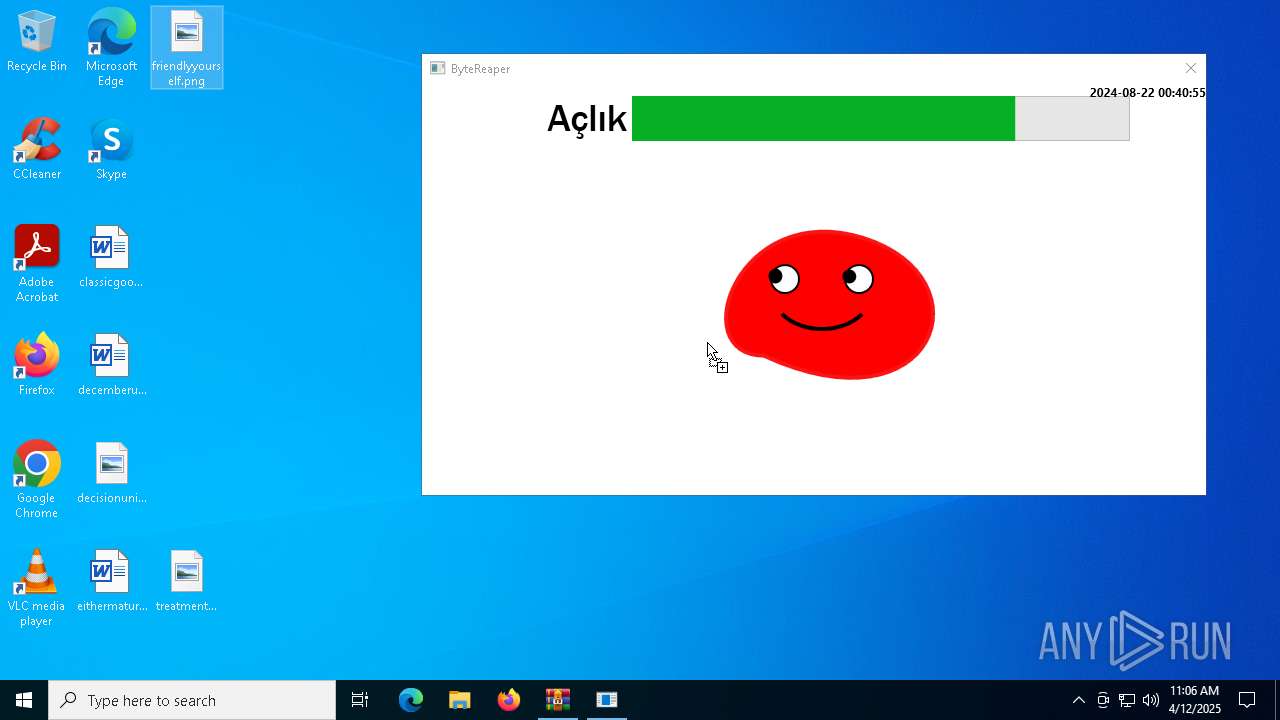
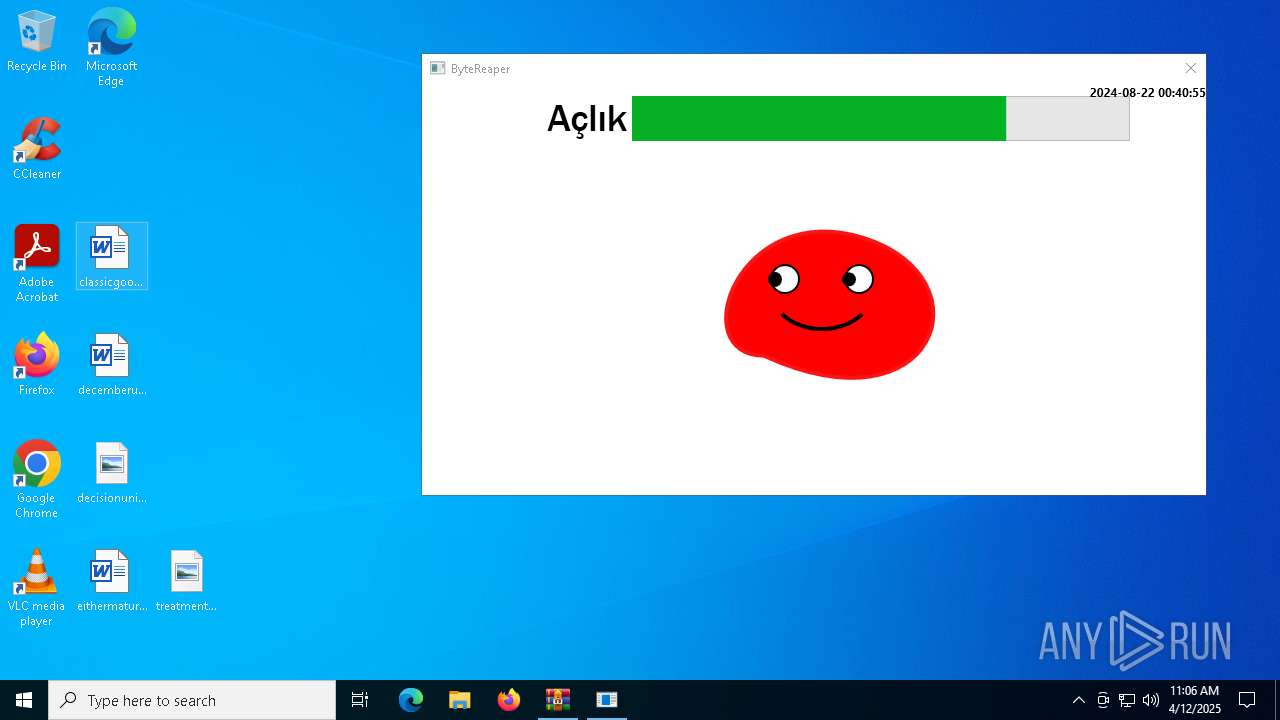
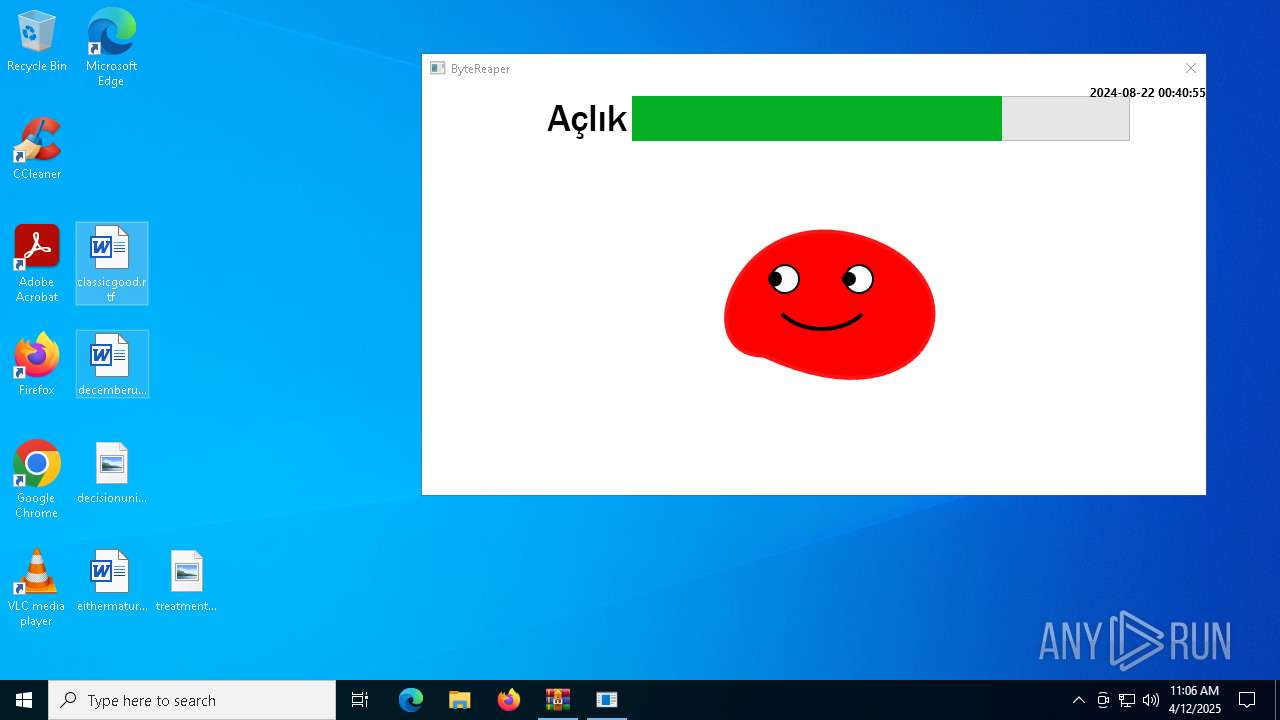
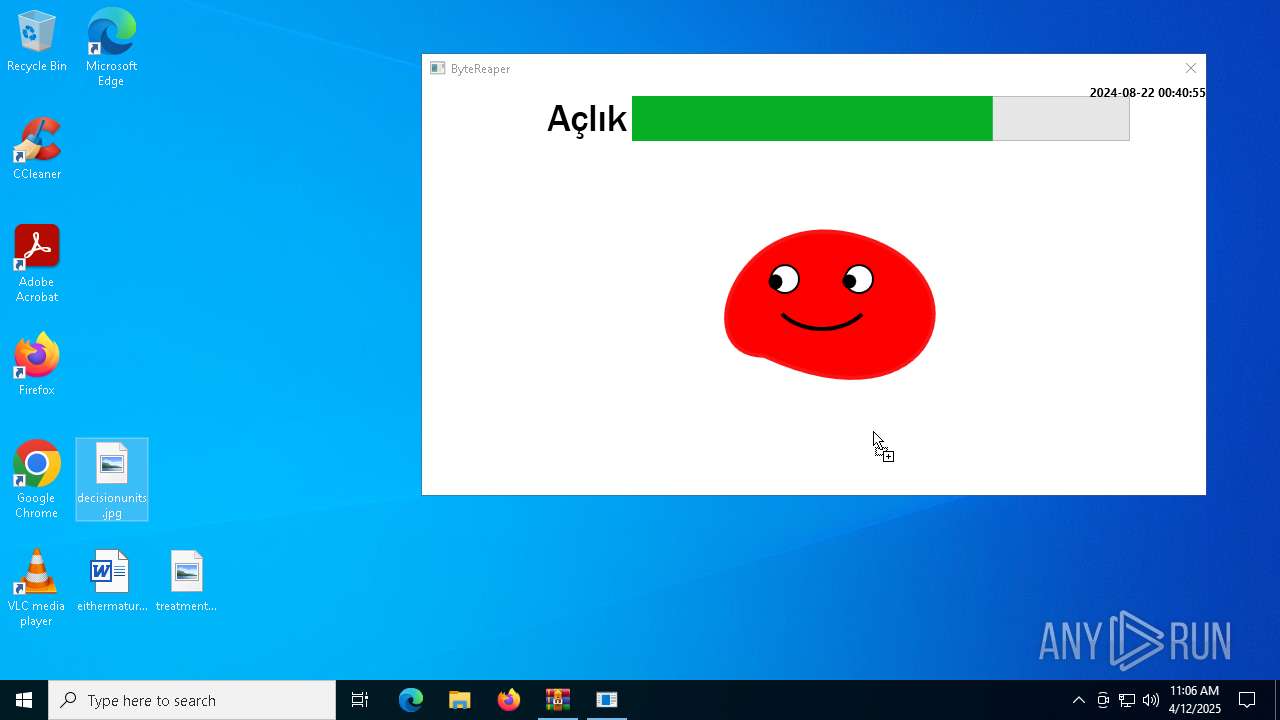
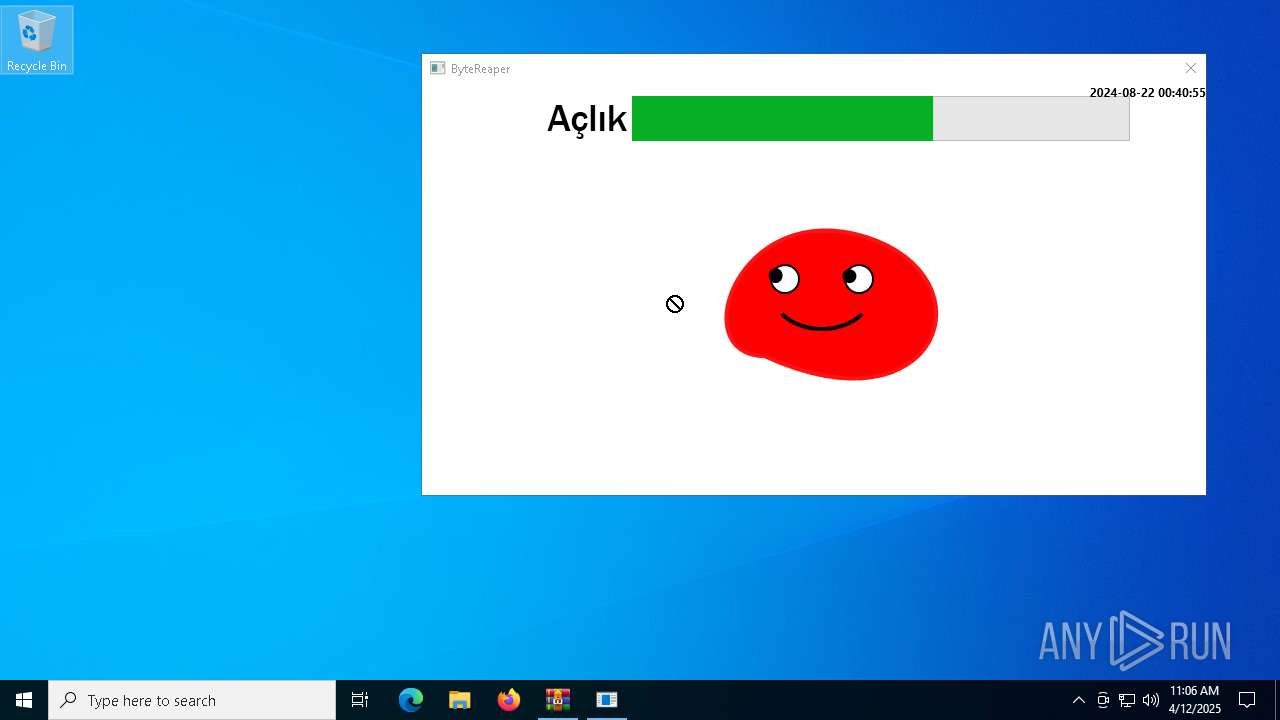
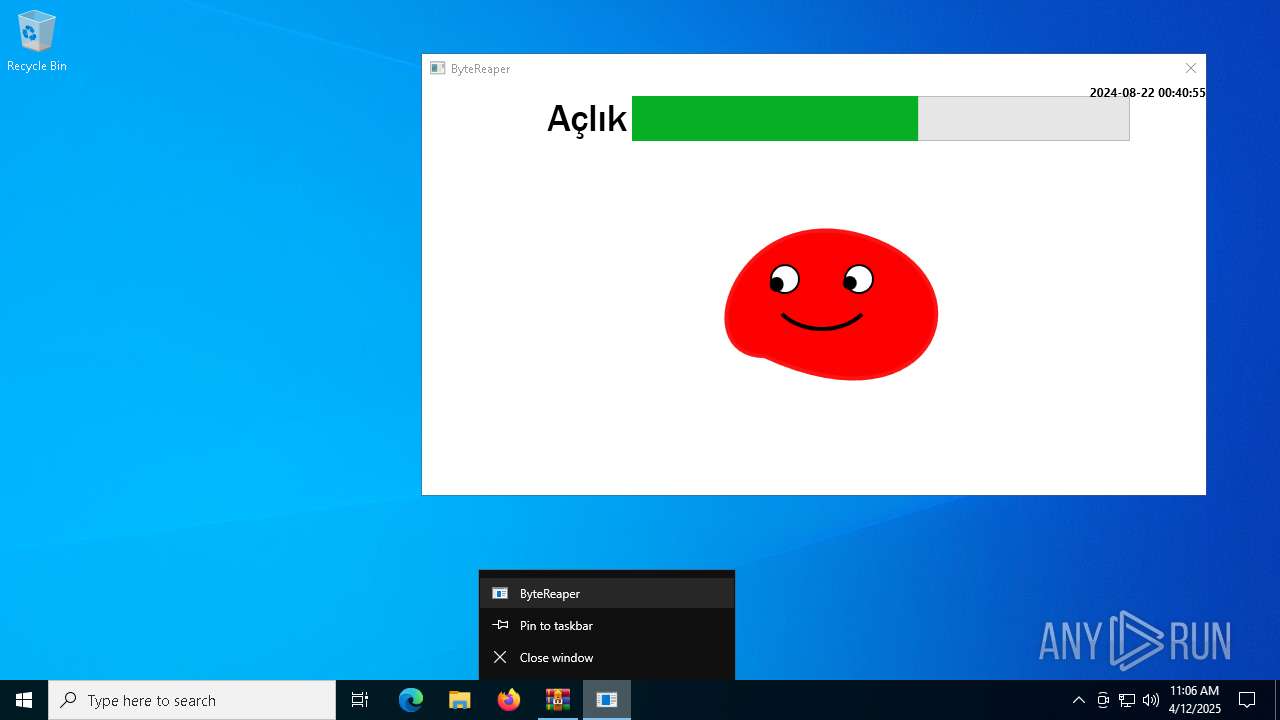
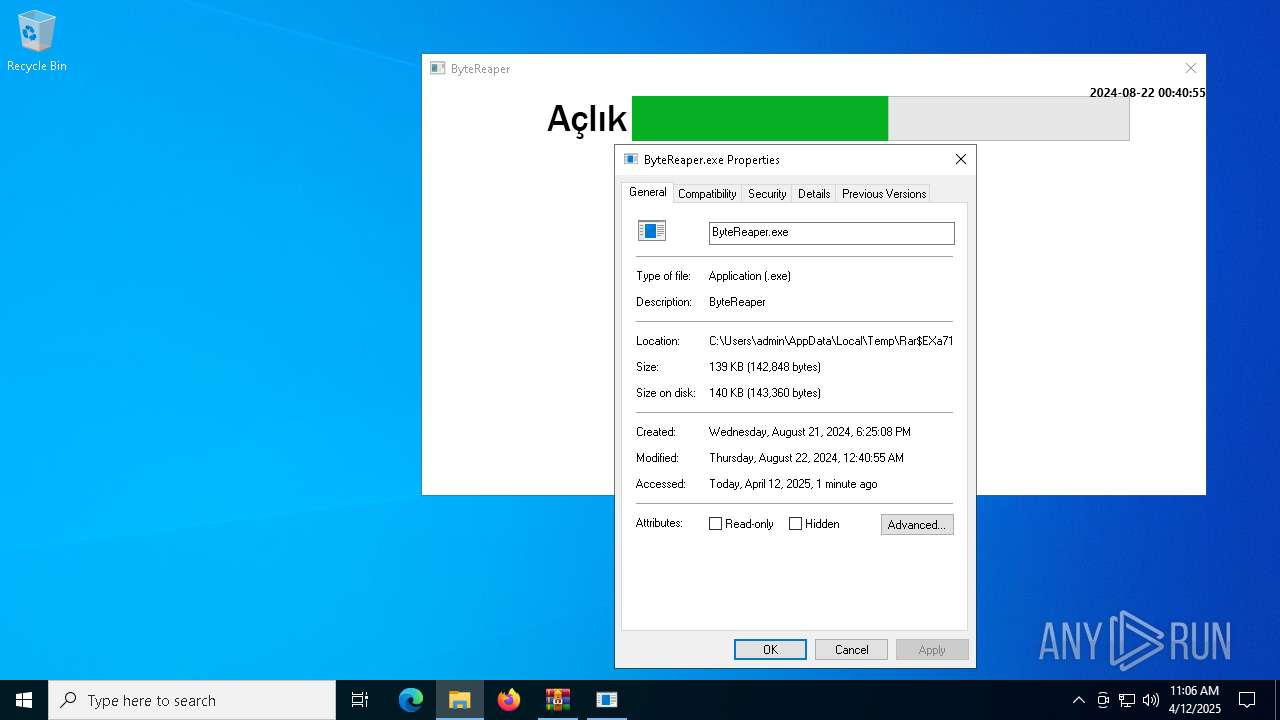
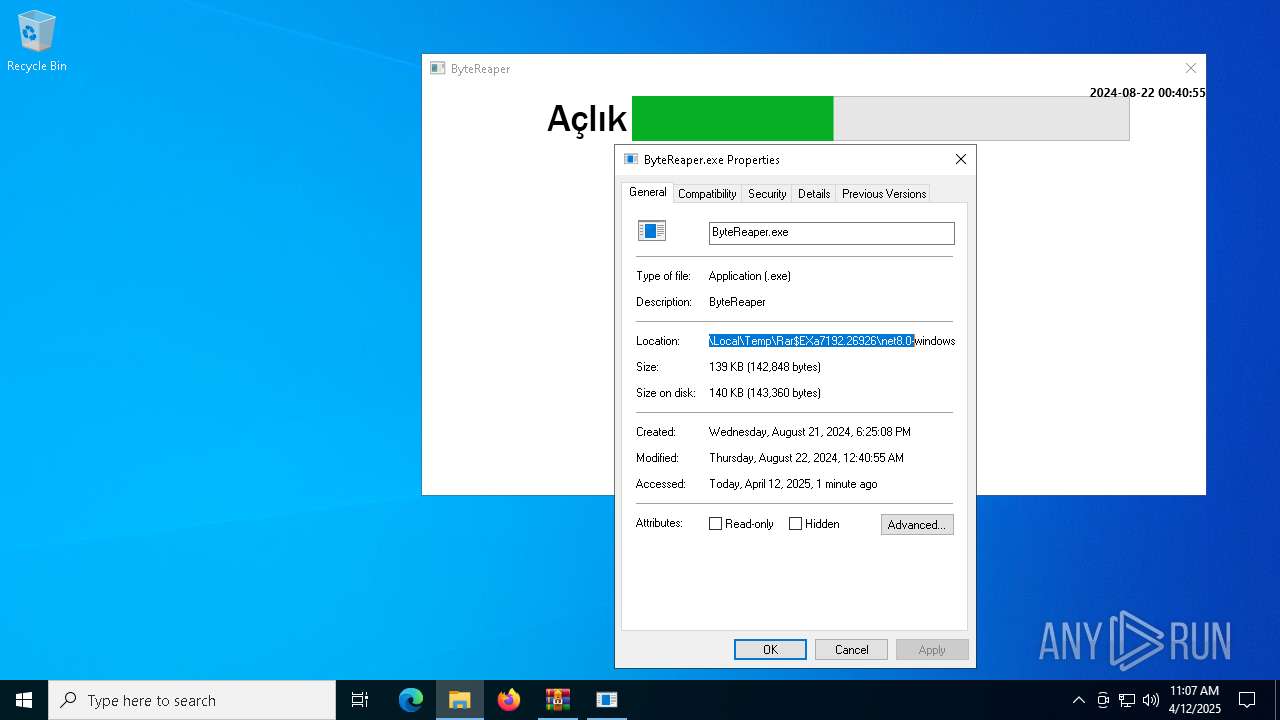
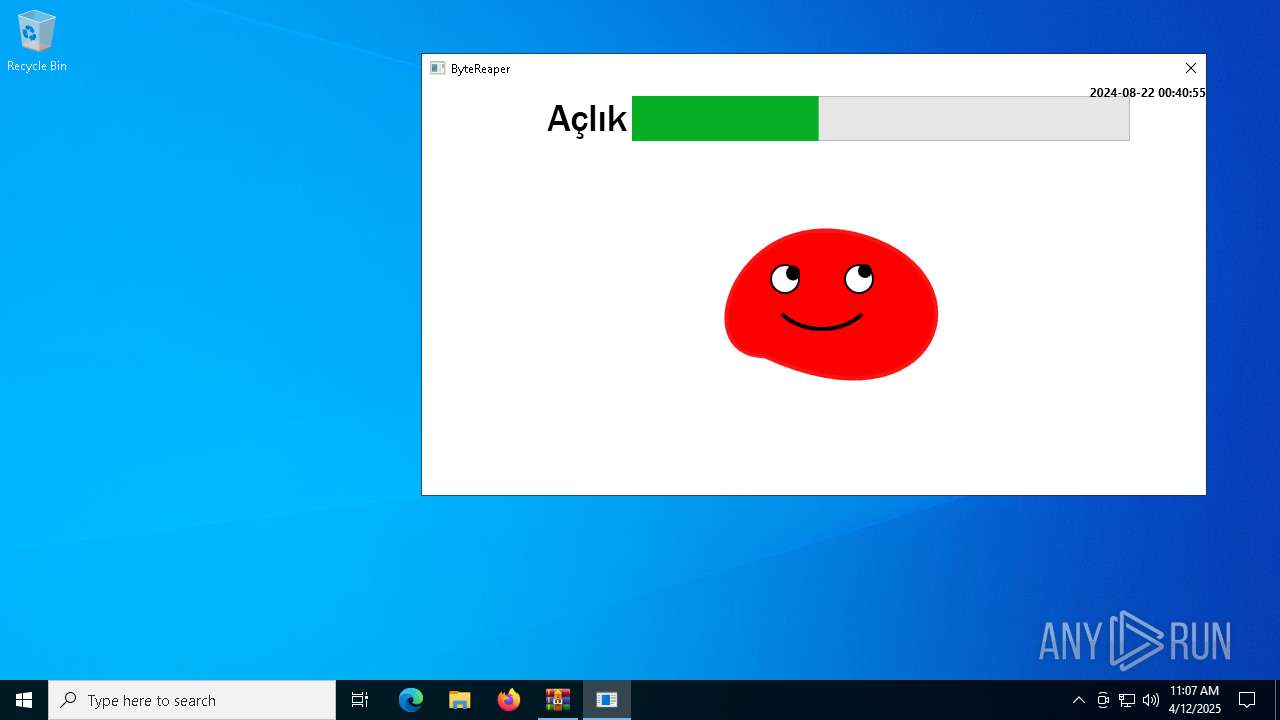
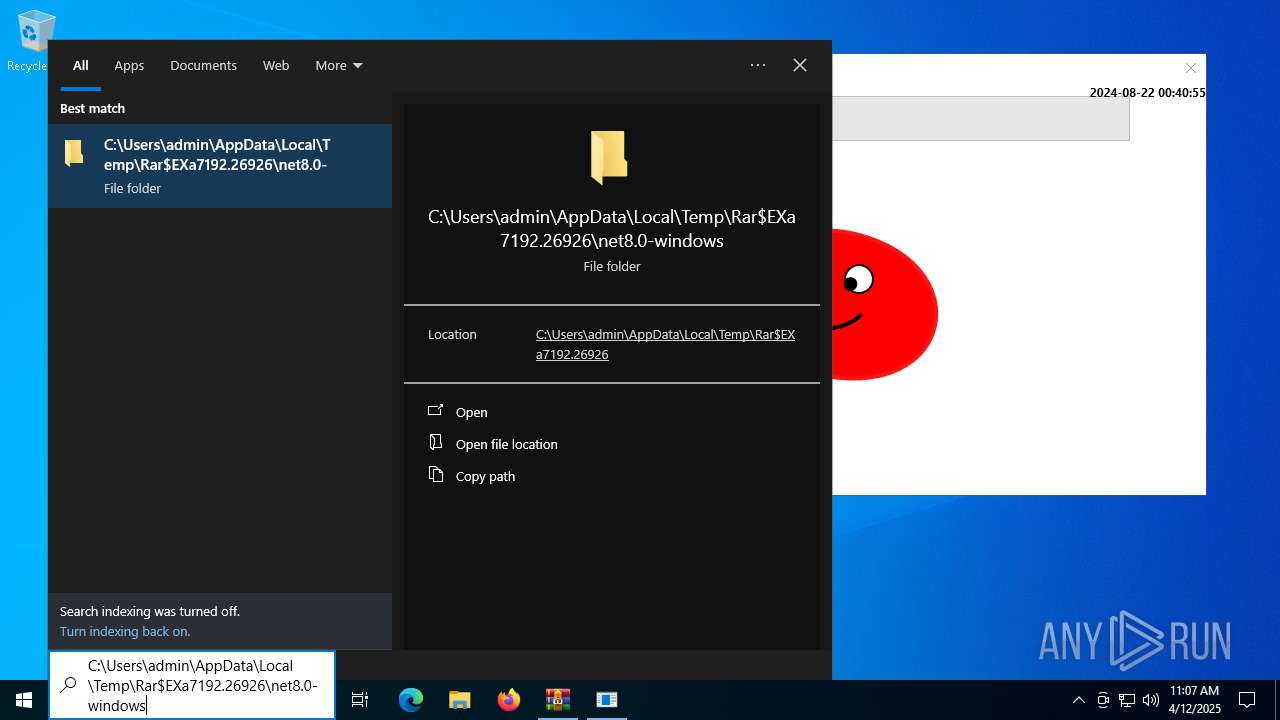
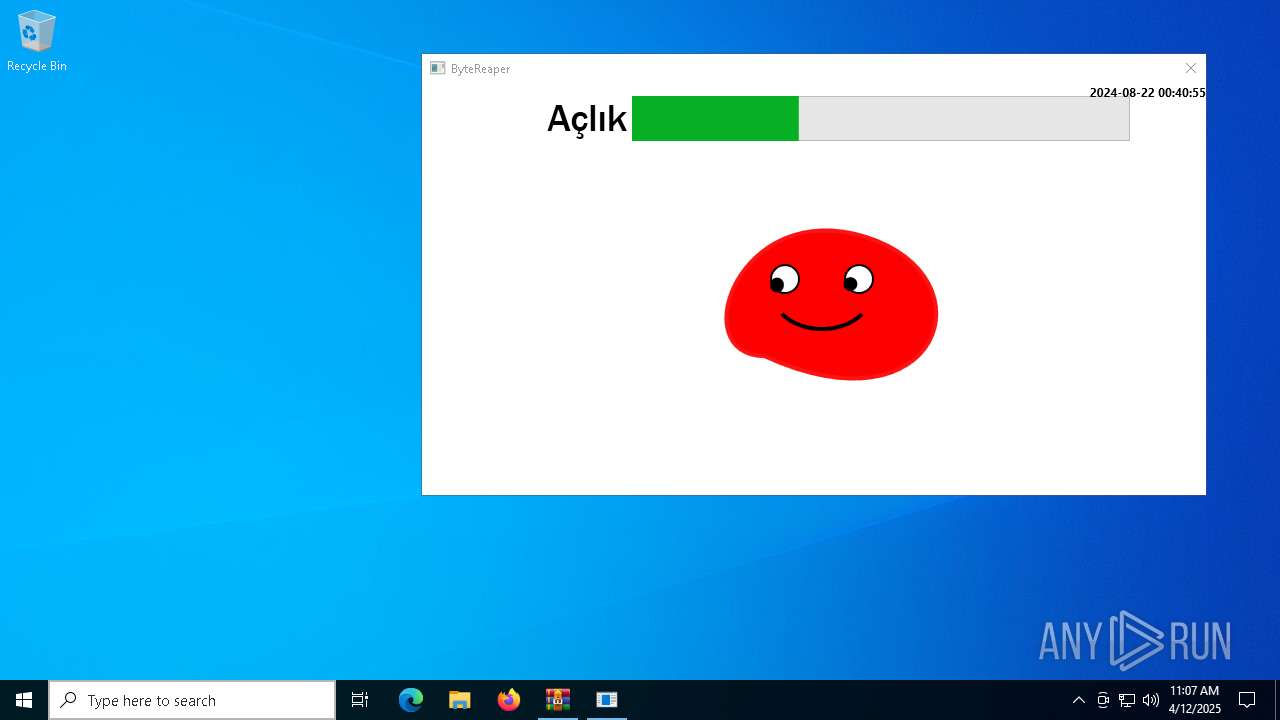
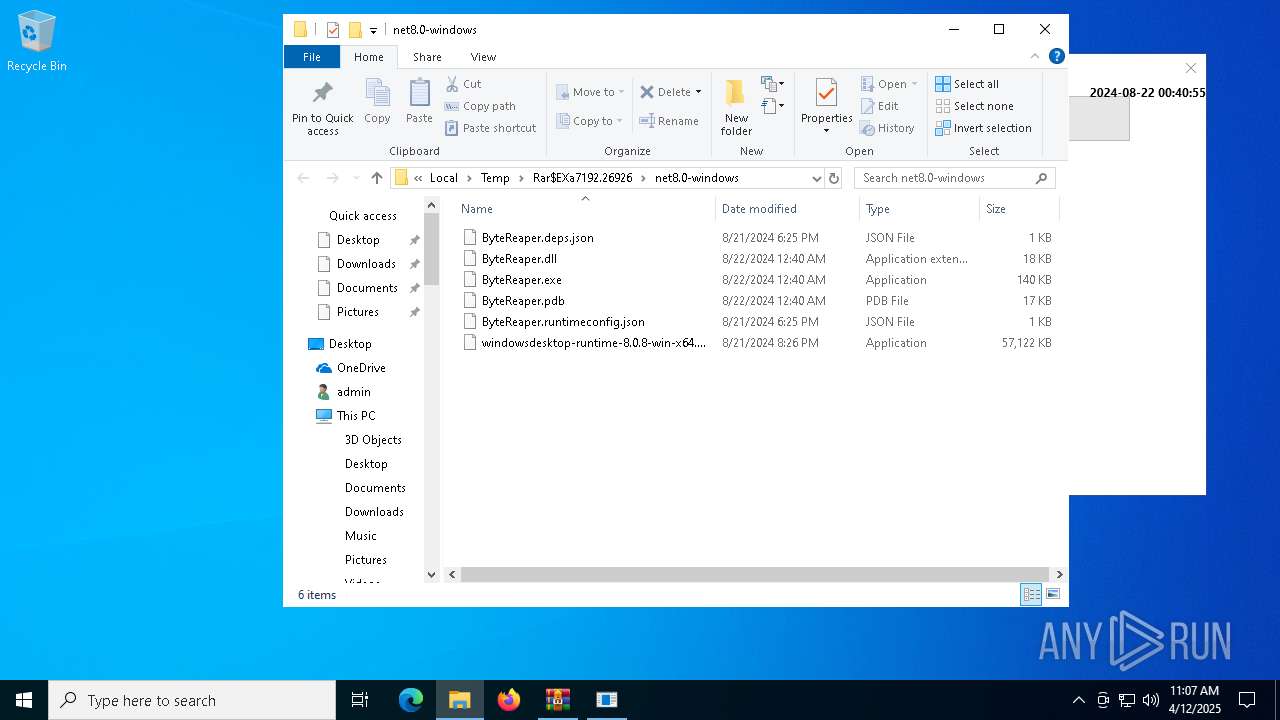
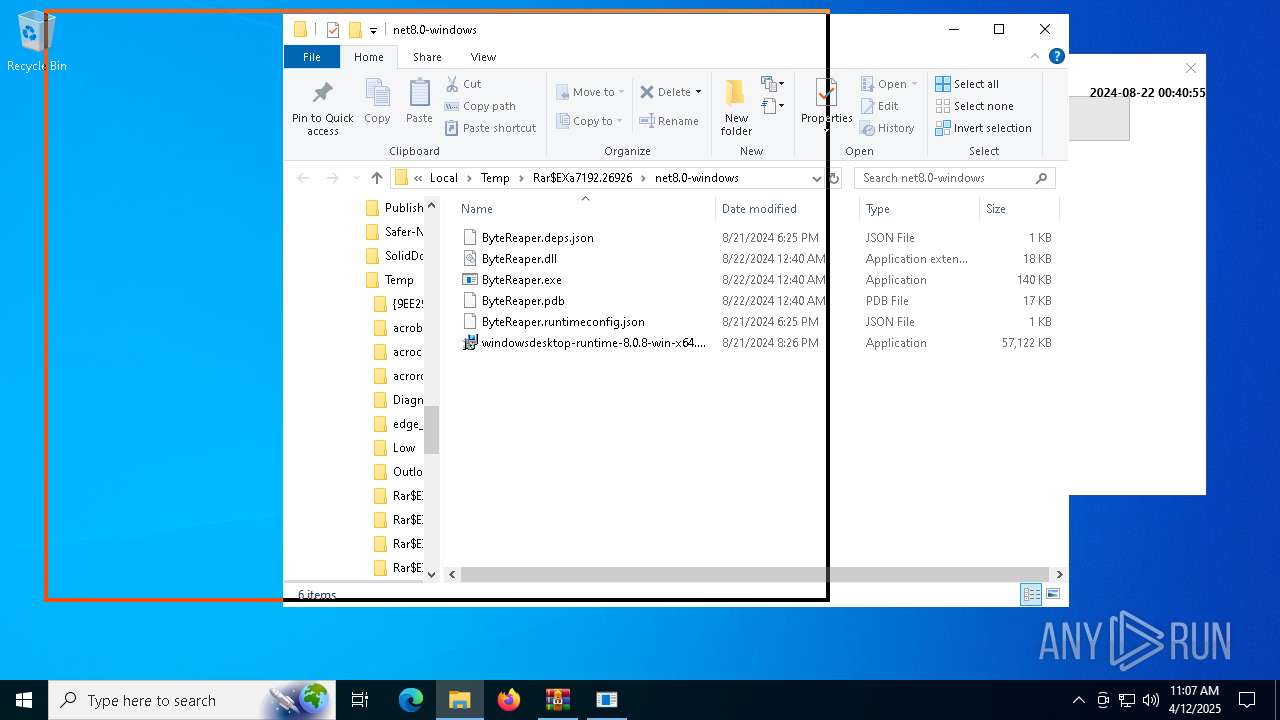
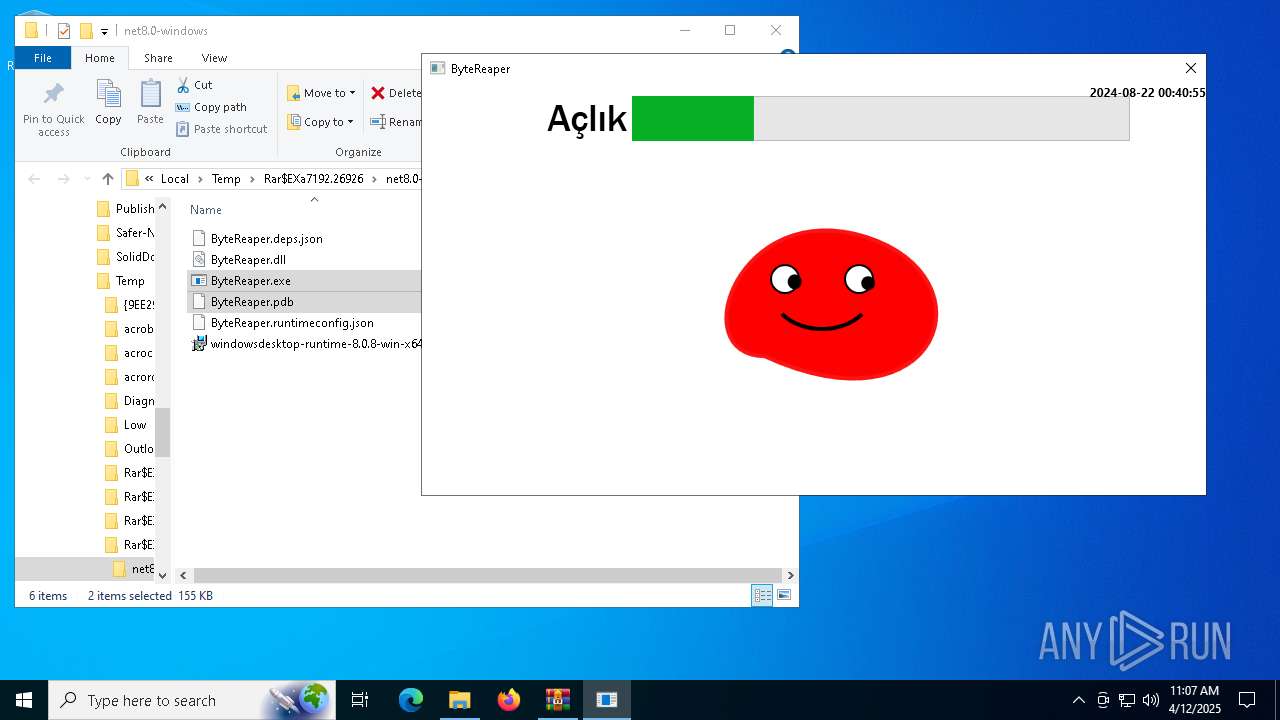
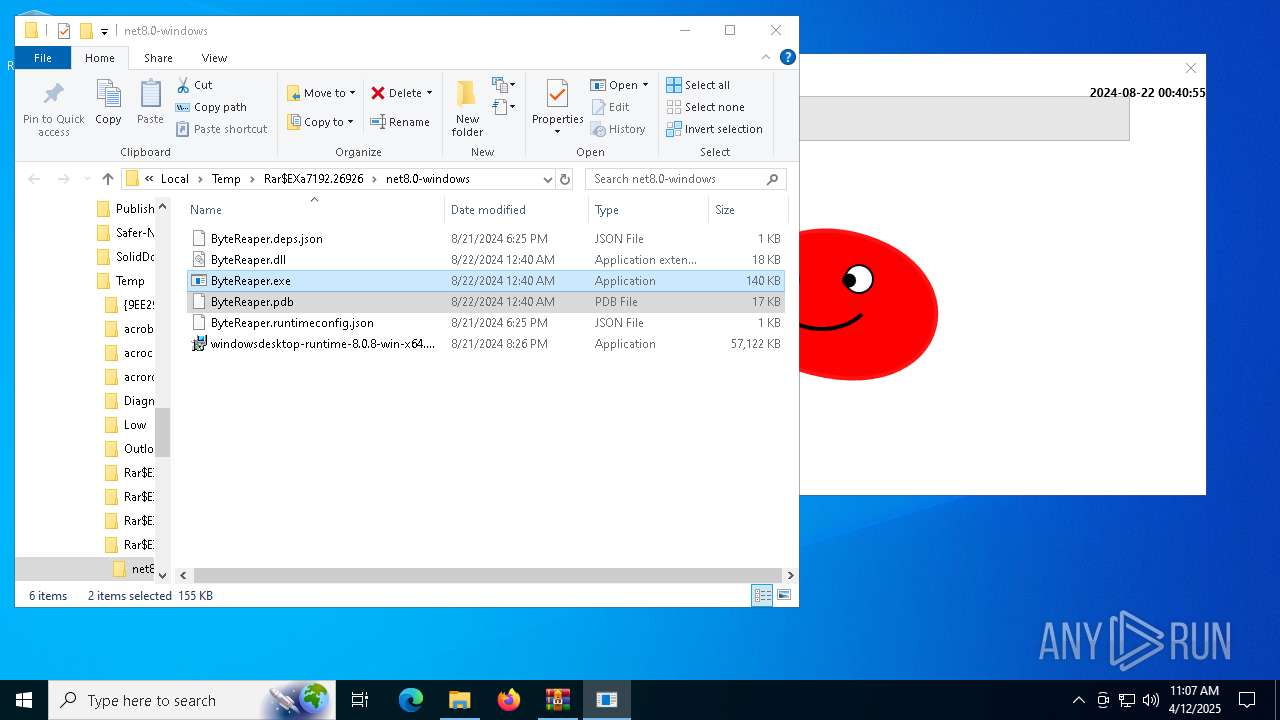
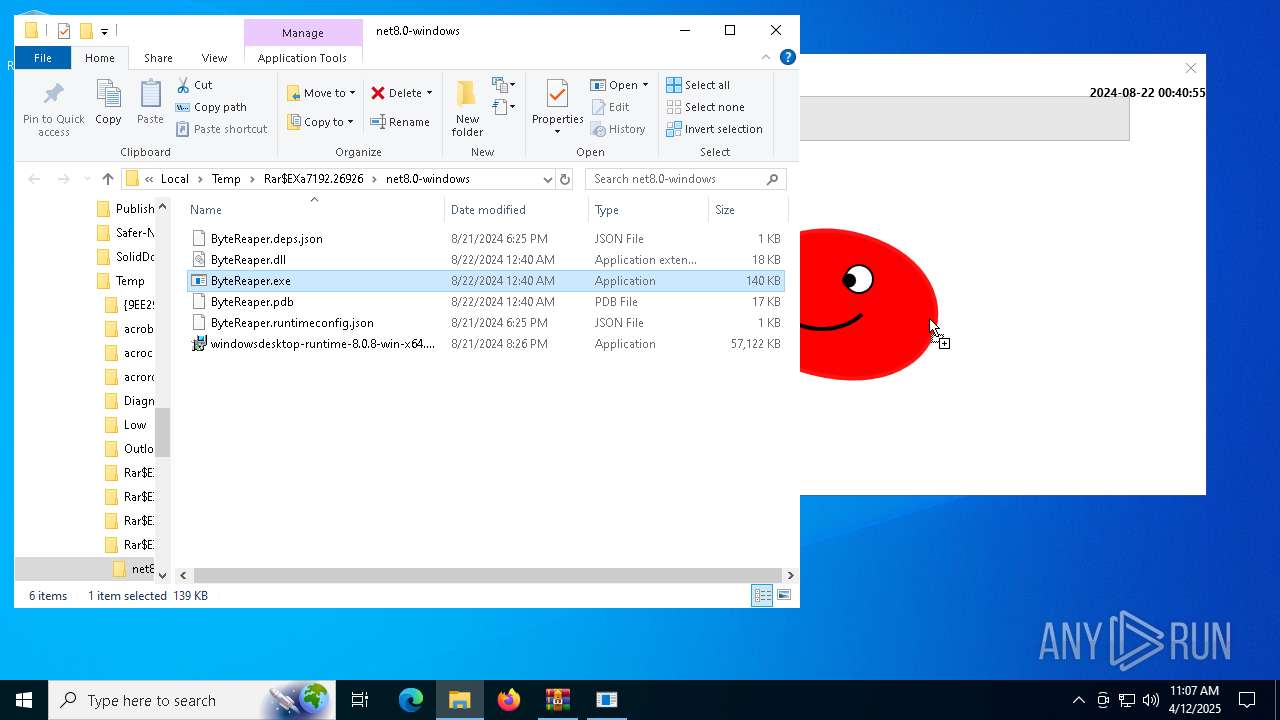
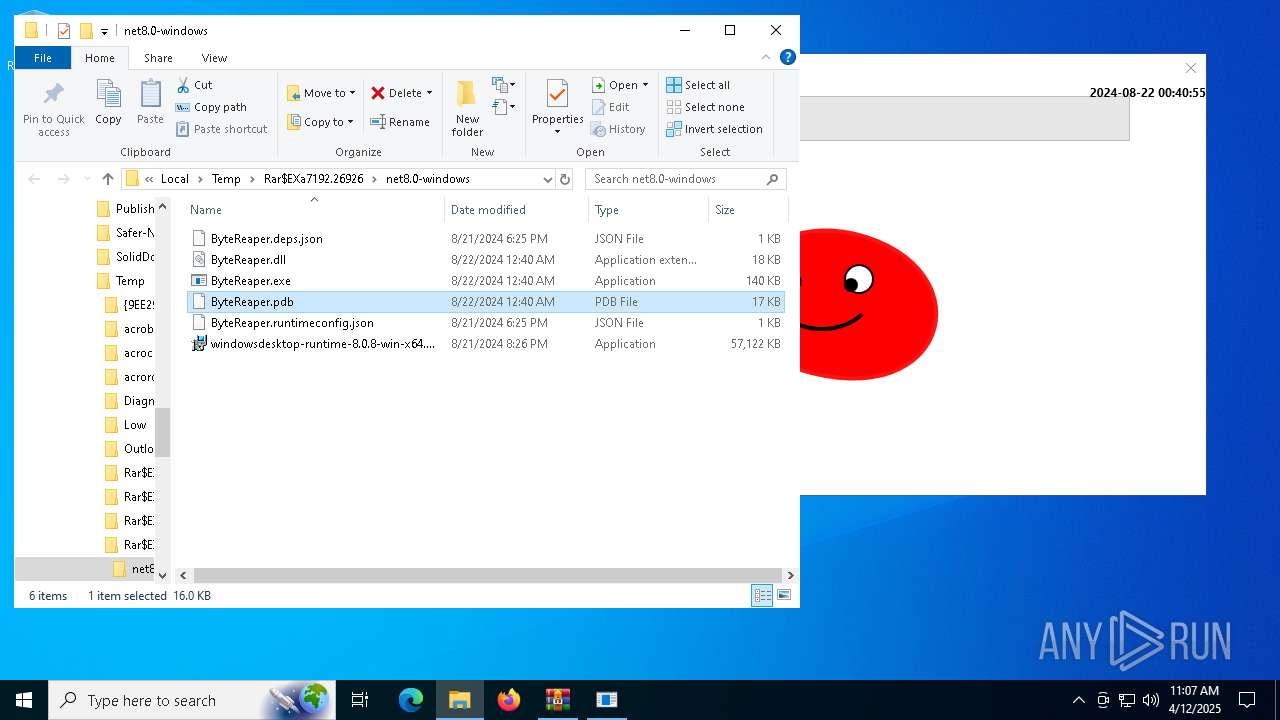
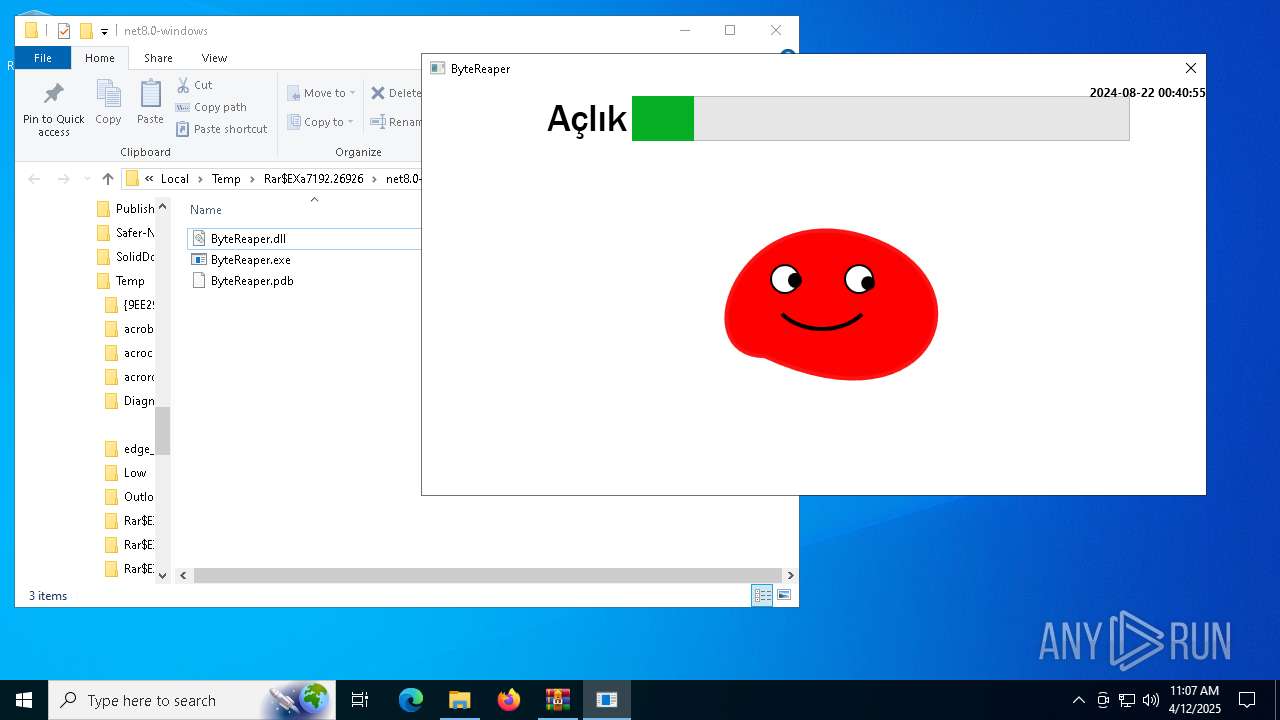
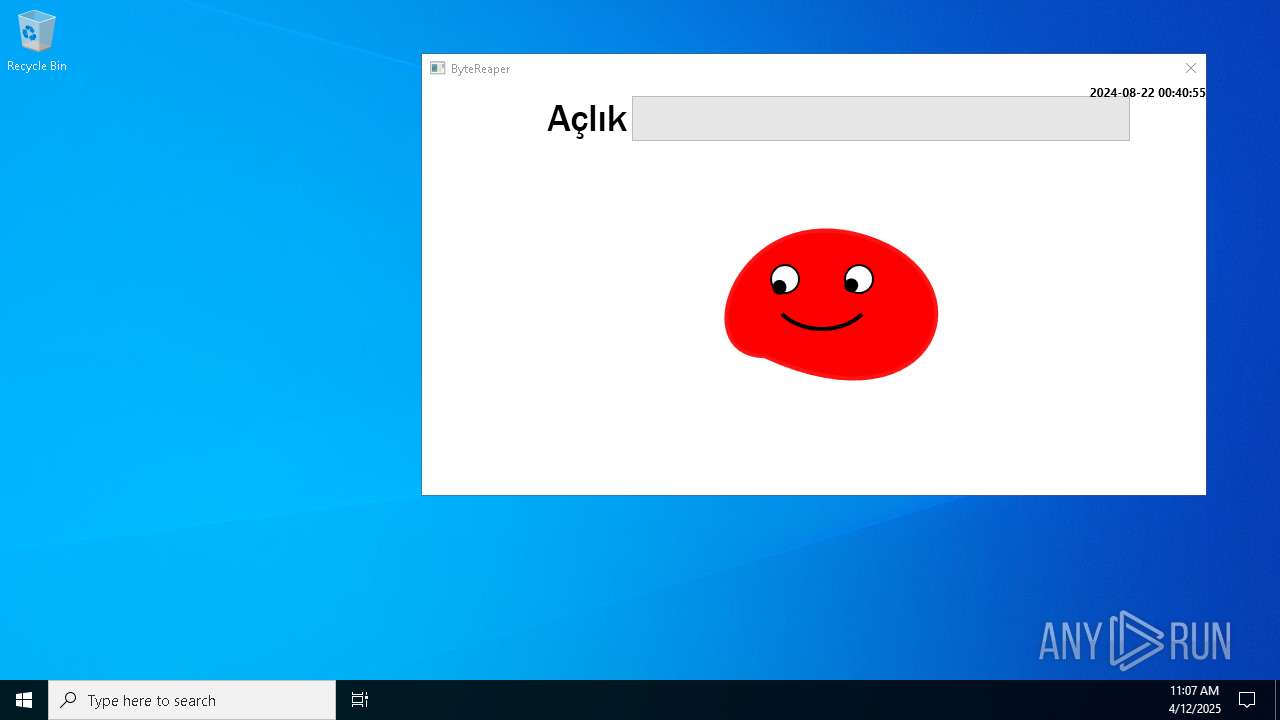
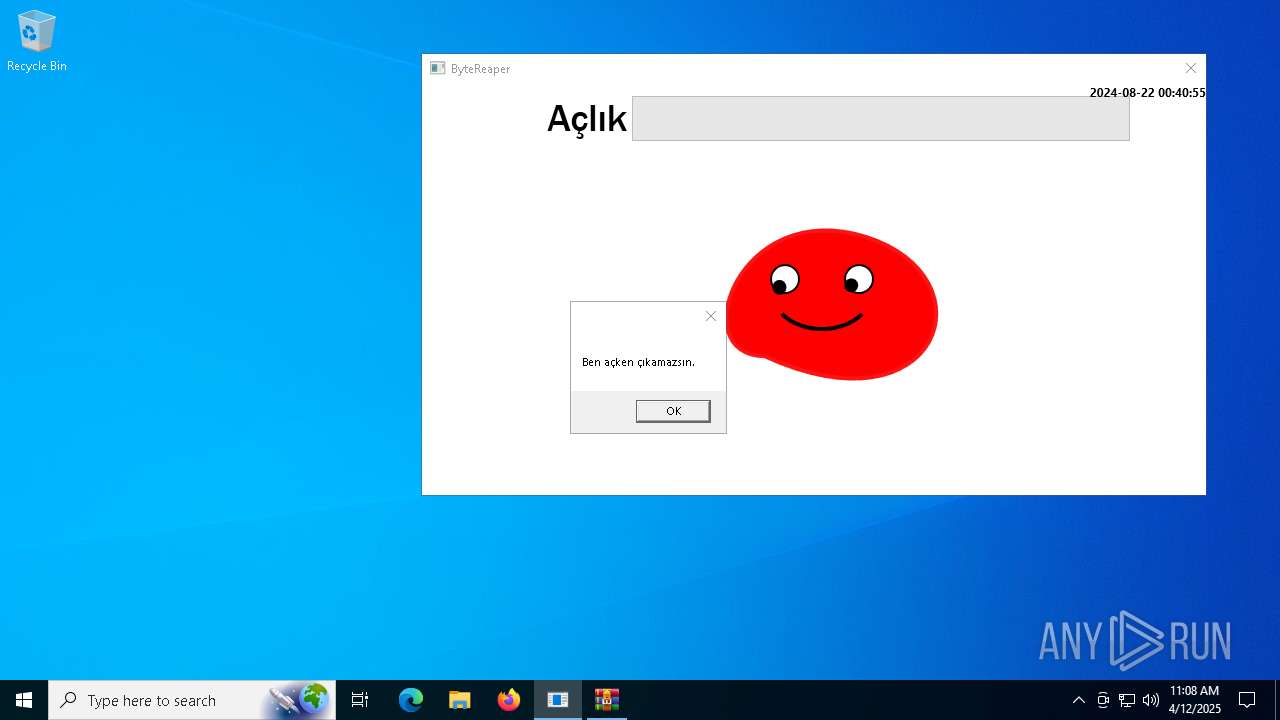
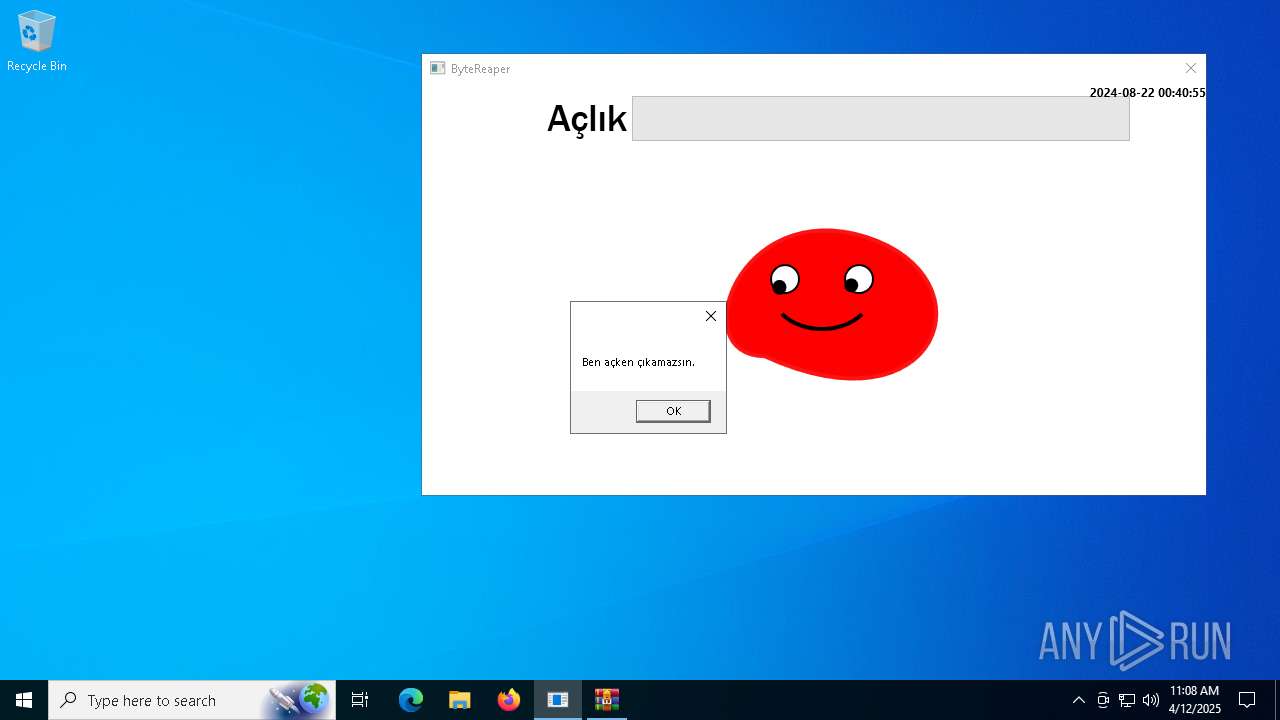
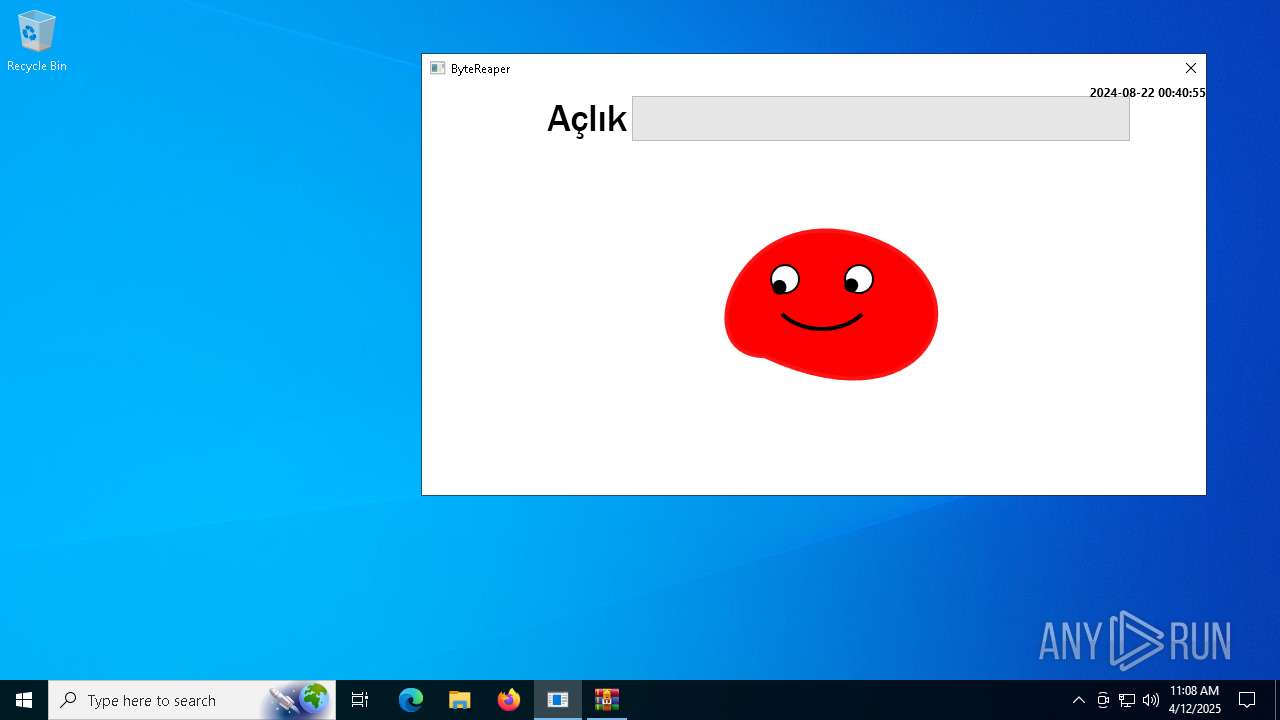
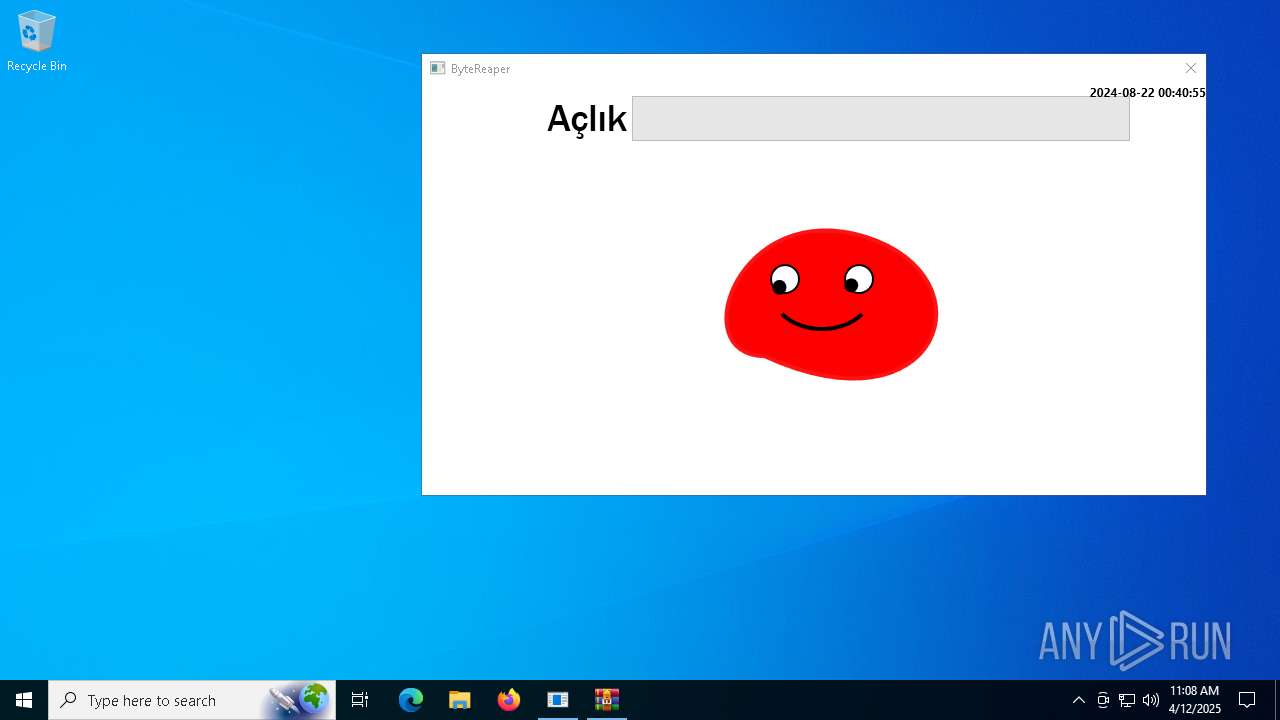
| URL: | sparrow99.com.tr/projeler |
| Full analysis: | https://app.any.run/tasks/39eca038-e068-4985-9721-075460bcfb9f |
| Verdict: | Malicious activity |
| Analysis date: | April 12, 2025, 11:04:27 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MD5: | CB8103876F4C523985CC6B001630FD87 |
| SHA1: | E9B8123C709B4E05B12A33E47D378F4EC7AC042A |
| SHA256: | 20B0B2201B8F4875D92398149AF5776F3CD6CEB9BA947CB98F49A9BD82E1AD8A |
| SSDEEP: | 3:iX3PhXn:iX/hXn |
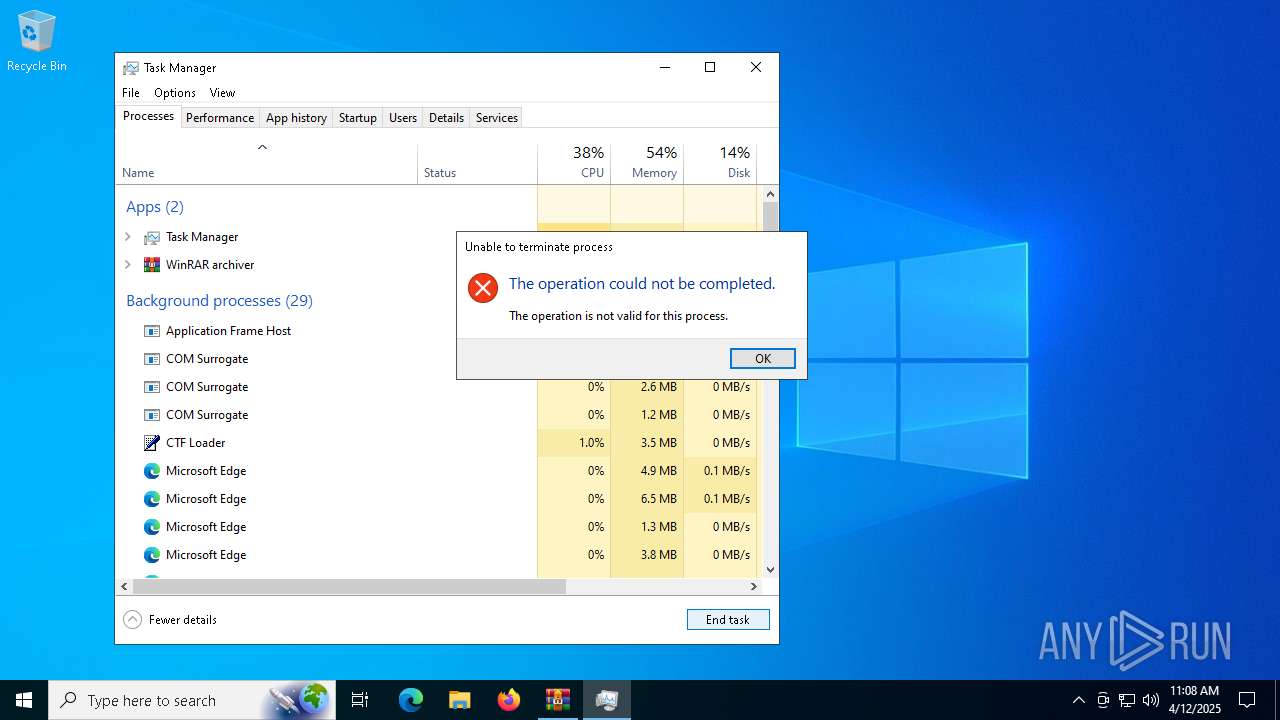
MALICIOUS
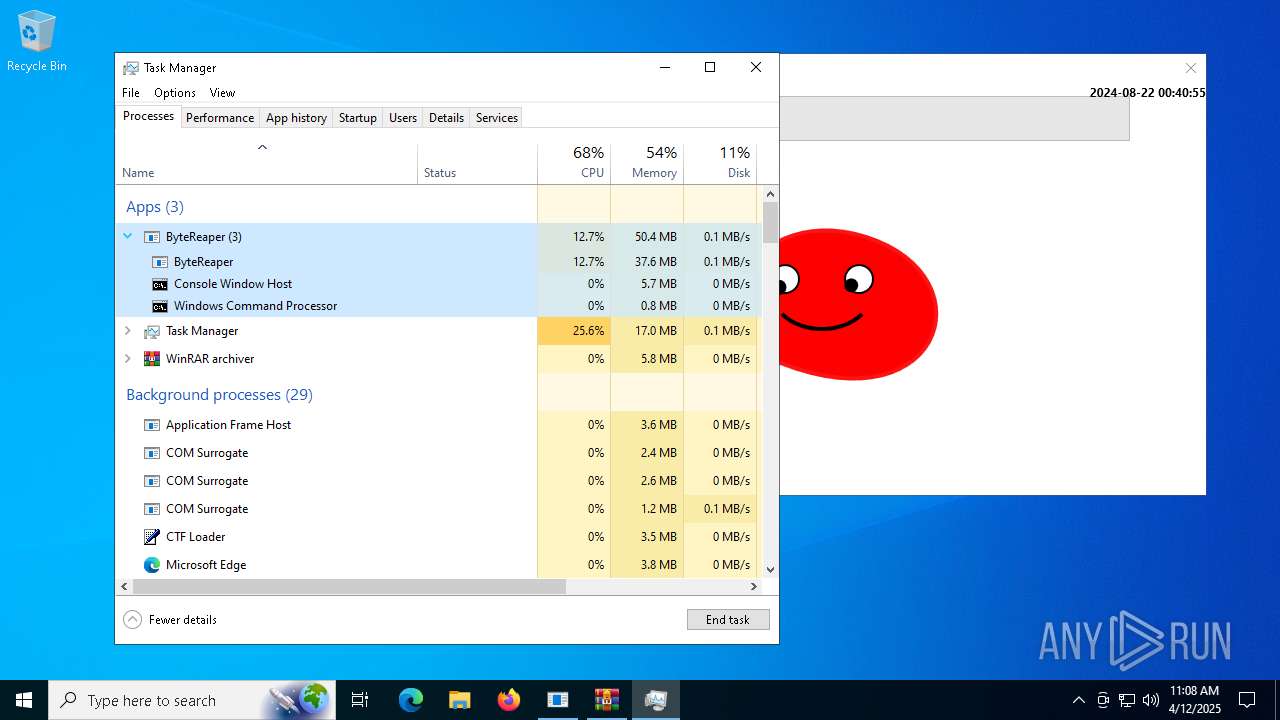
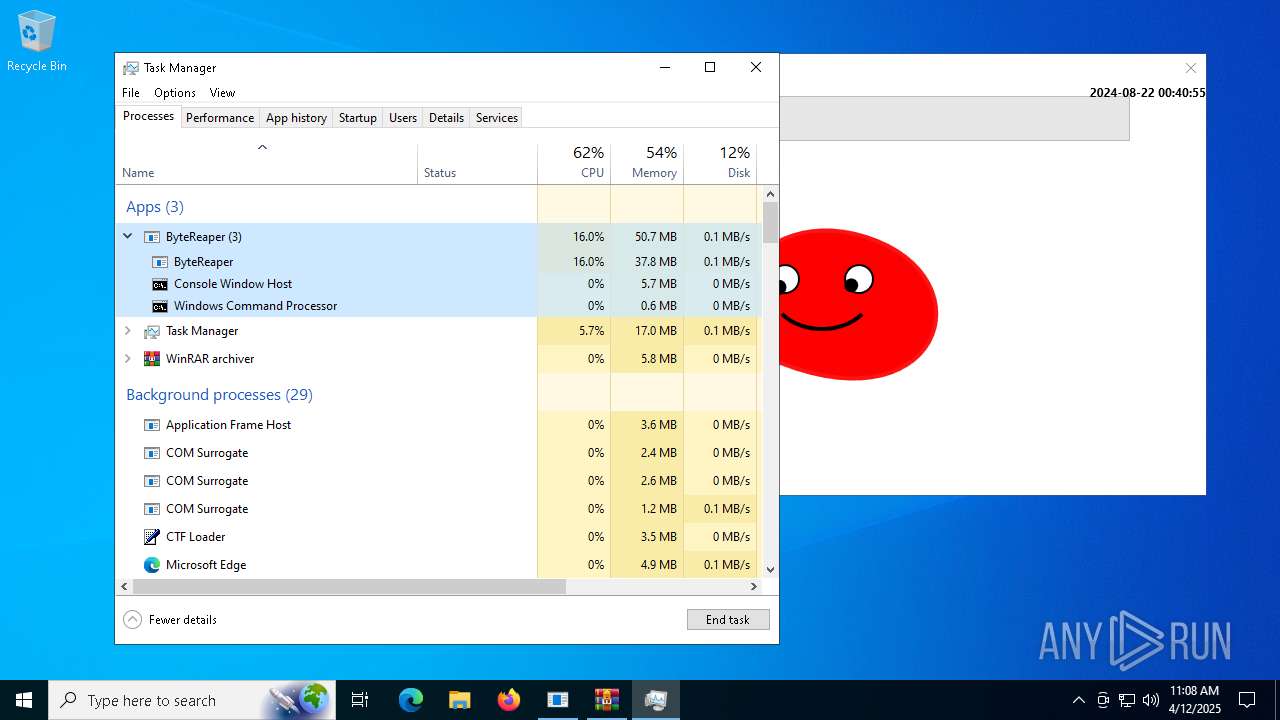
Changes the autorun value in the registry
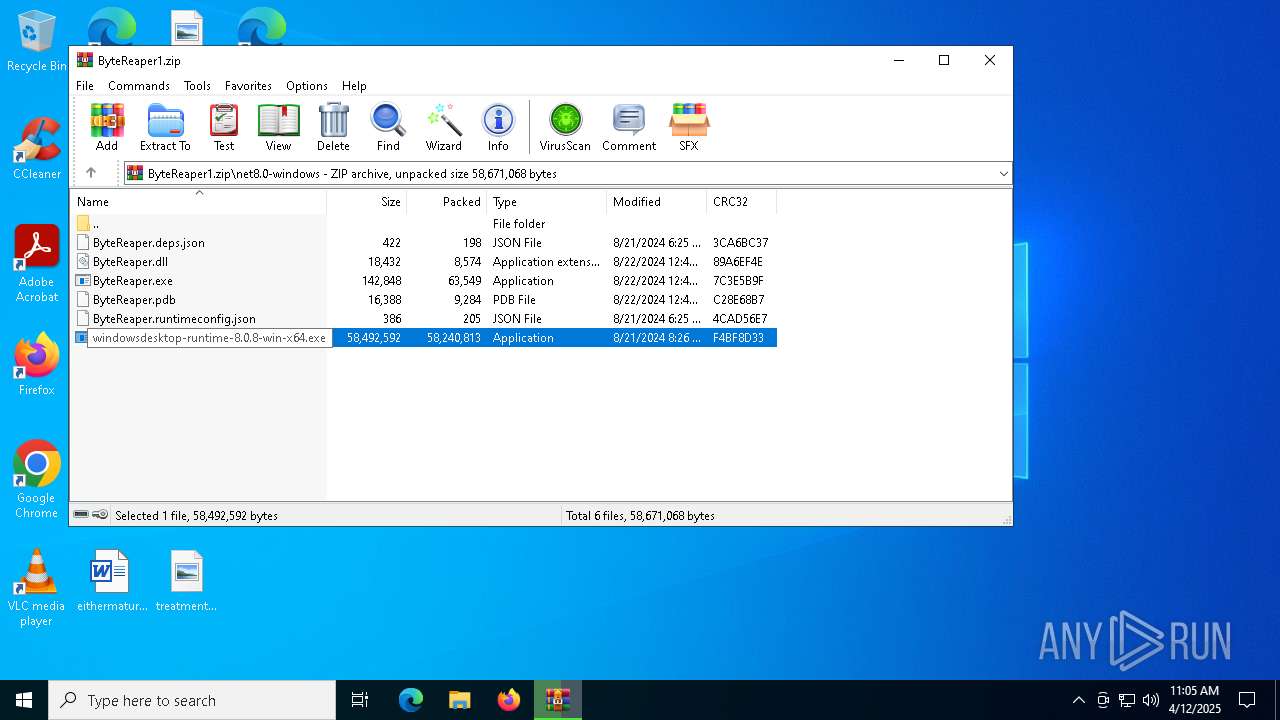
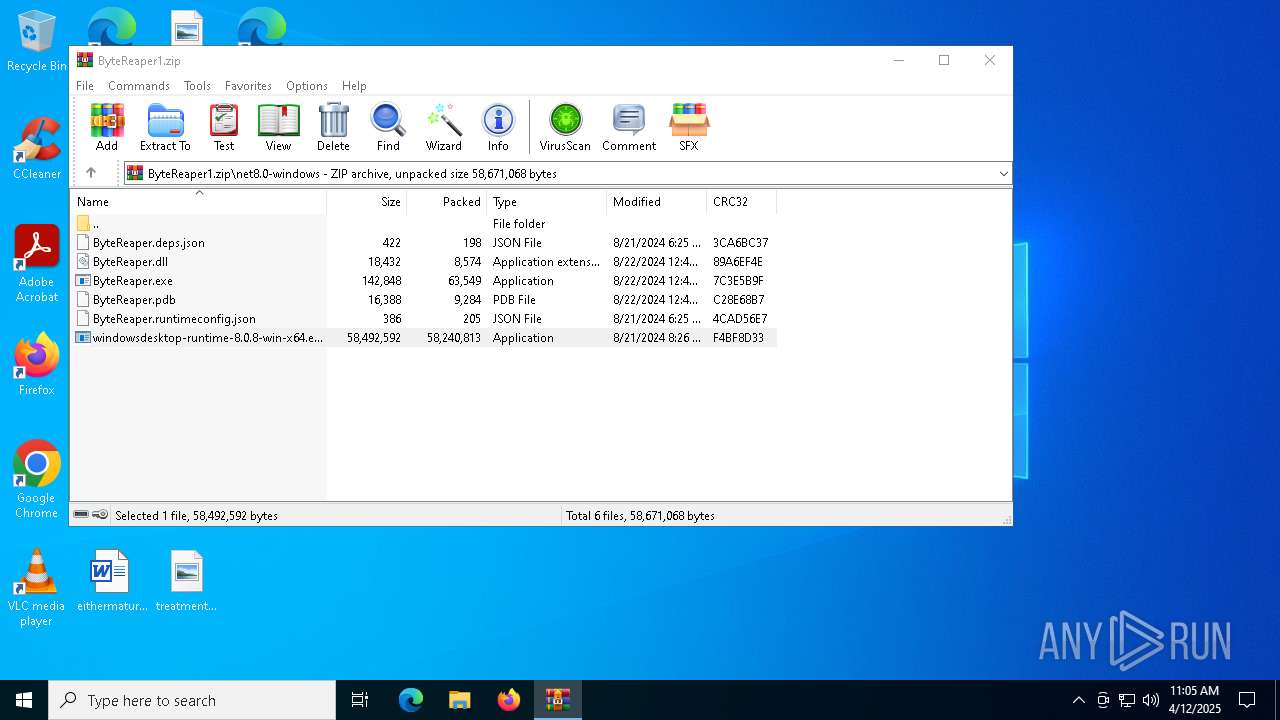
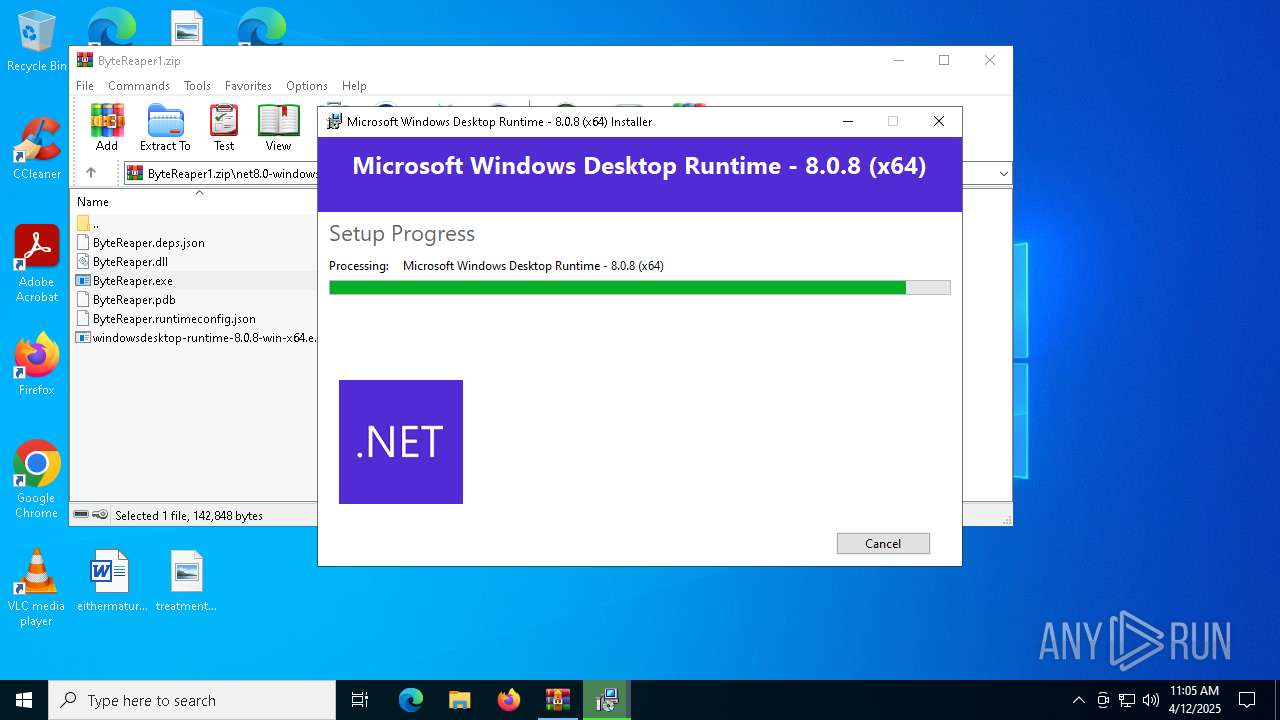
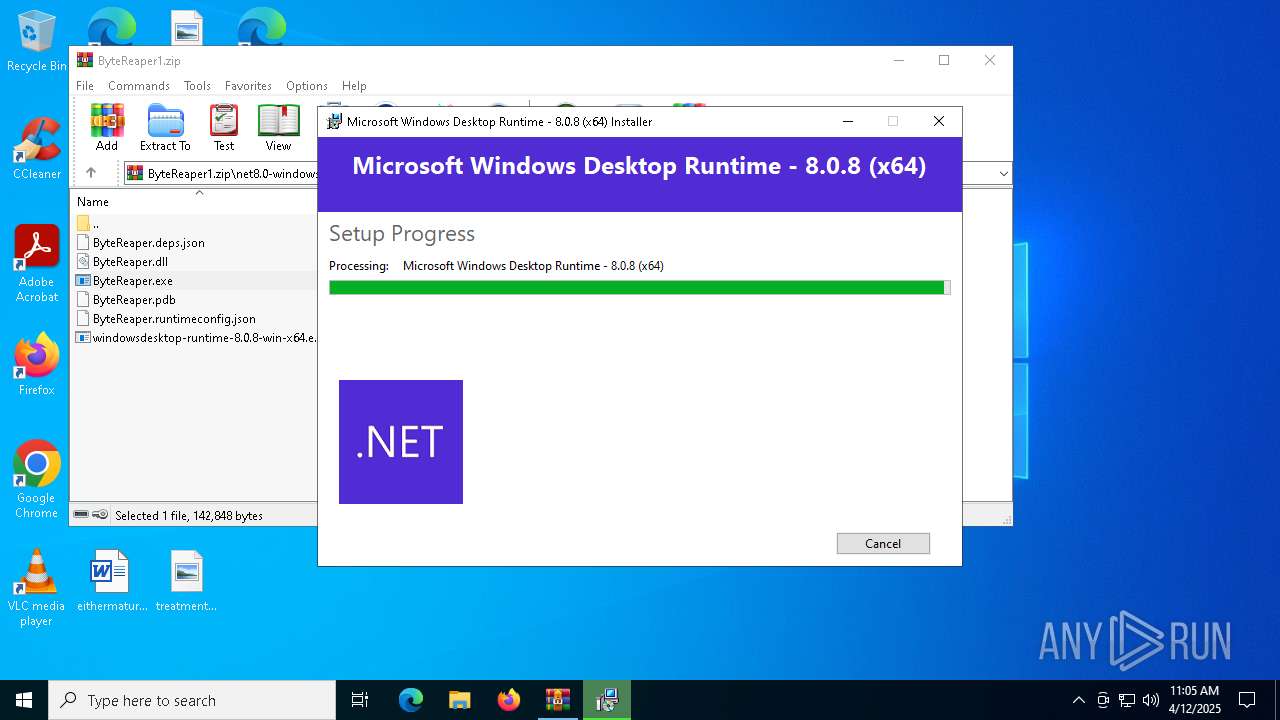
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 976)
SUSPICIOUS
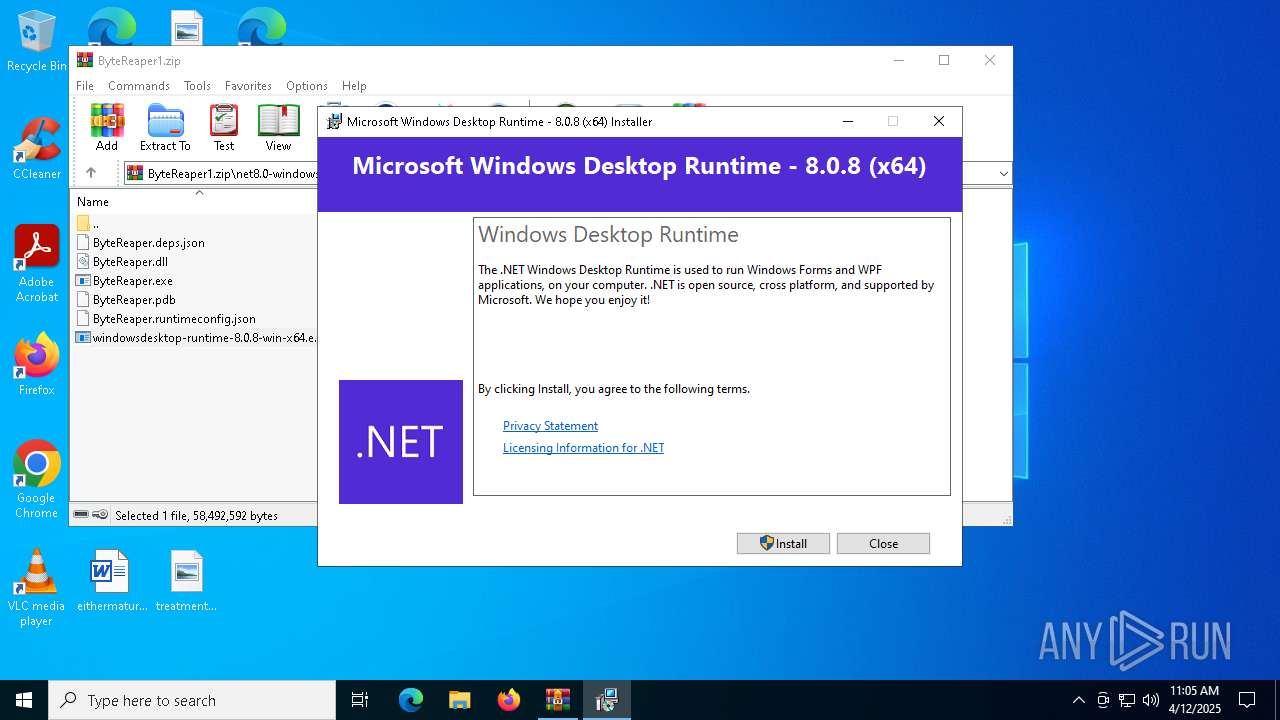
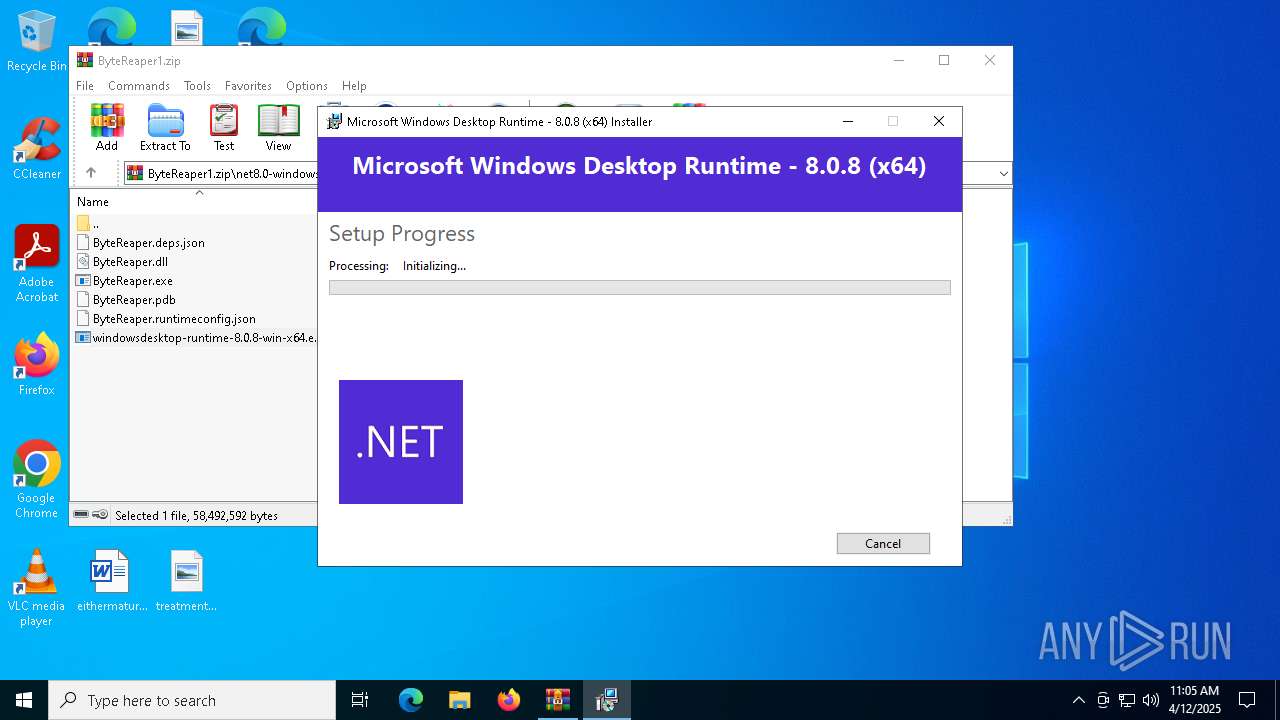
Starts a Microsoft application from unusual location
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 3020)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 8184)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 976)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7192)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 8184)
- ShellExperienceHost.exe (PID: 7100)
- StartMenuExperienceHost.exe (PID: 7552)
- ShellExperienceHost.exe (PID: 8196)
Executable content was dropped or overwritten
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 3020)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 976)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 8184)
Process drops legitimate windows executable
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 3020)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 976)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 8184)
- msiexec.exe (PID: 7804)
Searches for installed software
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 8184)
Starts itself from another location
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 8184)
Creates a software uninstall entry
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 976)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7804)
The process creates files with name similar to system file names
- msiexec.exe (PID: 7804)
The process drops C-runtime libraries
- msiexec.exe (PID: 7804)
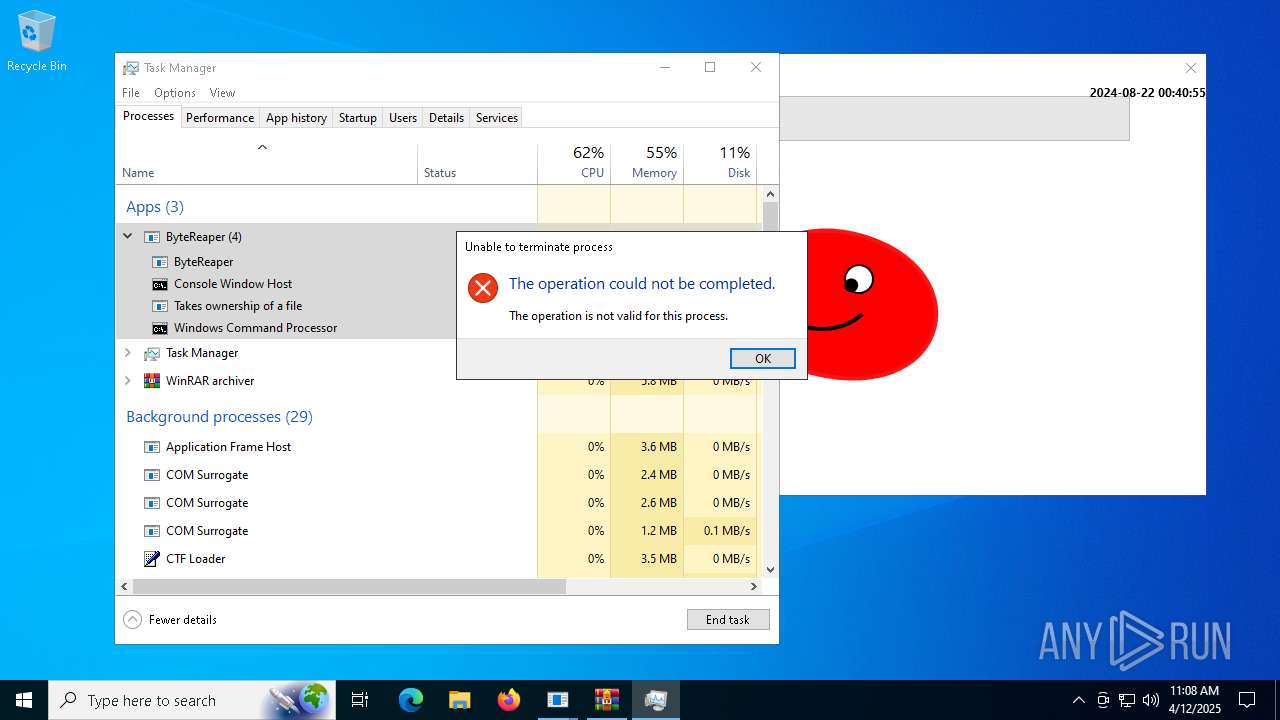
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 7992)
- cmd.exe (PID: 7512)
- cmd.exe (PID: 7836)
- cmd.exe (PID: 5024)
- cmd.exe (PID: 3804)
- cmd.exe (PID: 6640)
- cmd.exe (PID: 2140)
- cmd.exe (PID: 3580)
- cmd.exe (PID: 4012)
- cmd.exe (PID: 516)
- cmd.exe (PID: 7712)
- cmd.exe (PID: 8112)
- cmd.exe (PID: 8000)
- cmd.exe (PID: 3976)
- cmd.exe (PID: 2236)
- cmd.exe (PID: 2020)
- cmd.exe (PID: 3900)
- cmd.exe (PID: 6100)
- cmd.exe (PID: 7568)
- cmd.exe (PID: 5624)
- cmd.exe (PID: 7468)
- cmd.exe (PID: 7672)
- cmd.exe (PID: 5272)
- cmd.exe (PID: 7432)
- cmd.exe (PID: 5600)
- cmd.exe (PID: 5800)
- cmd.exe (PID: 4624)
- cmd.exe (PID: 976)
- cmd.exe (PID: 7628)
- cmd.exe (PID: 5072)
- cmd.exe (PID: 6296)
- cmd.exe (PID: 7500)
- cmd.exe (PID: 7828)
- cmd.exe (PID: 6720)
- cmd.exe (PID: 4376)
- cmd.exe (PID: 5896)
- cmd.exe (PID: 4444)
- cmd.exe (PID: 8136)
- cmd.exe (PID: 7488)
- cmd.exe (PID: 5112)
- cmd.exe (PID: 4868)
- cmd.exe (PID: 5232)
- cmd.exe (PID: 2516)
- cmd.exe (PID: 7776)
- cmd.exe (PID: 5676)
- cmd.exe (PID: 5752)
- cmd.exe (PID: 4120)
- cmd.exe (PID: 7932)
- cmd.exe (PID: 6832)
- cmd.exe (PID: 6076)
- cmd.exe (PID: 8180)
- cmd.exe (PID: 3144)
- cmd.exe (PID: 5156)
- cmd.exe (PID: 8084)
- cmd.exe (PID: 7392)
- cmd.exe (PID: 4688)
- cmd.exe (PID: 7688)
- cmd.exe (PID: 5952)
- cmd.exe (PID: 4452)
- cmd.exe (PID: 7080)
- cmd.exe (PID: 3344)
- cmd.exe (PID: 1660)
- cmd.exe (PID: 7668)
- cmd.exe (PID: 4108)
- cmd.exe (PID: 8076)
- cmd.exe (PID: 5124)
- cmd.exe (PID: 5188)
- cmd.exe (PID: 7944)
- cmd.exe (PID: 6684)
- cmd.exe (PID: 7940)
- cmd.exe (PID: 7524)
- cmd.exe (PID: 7276)
- cmd.exe (PID: 2620)
- cmd.exe (PID: 5508)
- cmd.exe (PID: 2740)
- cmd.exe (PID: 1764)
- cmd.exe (PID: 7584)
- cmd.exe (PID: 2896)
- cmd.exe (PID: 6744)
- cmd.exe (PID: 672)
- cmd.exe (PID: 3952)
- cmd.exe (PID: 7848)
- cmd.exe (PID: 5132)
- cmd.exe (PID: 6300)
- cmd.exe (PID: 3020)
- cmd.exe (PID: 6332)
- cmd.exe (PID: 5728)
- cmd.exe (PID: 1008)
- cmd.exe (PID: 8172)
- cmd.exe (PID: 7020)
- cmd.exe (PID: 1852)
- cmd.exe (PID: 6696)
- cmd.exe (PID: 7448)
- cmd.exe (PID: 3268)
- cmd.exe (PID: 5980)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 6116)
- cmd.exe (PID: 8184)
- cmd.exe (PID: 7184)
- cmd.exe (PID: 5364)
- cmd.exe (PID: 7172)
- cmd.exe (PID: 5812)
- cmd.exe (PID: 7980)
- cmd.exe (PID: 5416)
- cmd.exe (PID: 824)
- cmd.exe (PID: 5344)
- cmd.exe (PID: 5936)
- cmd.exe (PID: 6344)
- cmd.exe (PID: 4140)
- cmd.exe (PID: 1164)
- cmd.exe (PID: 1240)
- cmd.exe (PID: 7380)
- cmd.exe (PID: 7480)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 544)
- cmd.exe (PID: 6756)
- cmd.exe (PID: 7484)
- cmd.exe (PID: 2604)
- cmd.exe (PID: 628)
- cmd.exe (PID: 1600)
- cmd.exe (PID: 2776)
- cmd.exe (PID: 2344)
- cmd.exe (PID: 6960)
- cmd.exe (PID: 6612)
- cmd.exe (PID: 5756)
- cmd.exe (PID: 3016)
- cmd.exe (PID: 7744)
- cmd.exe (PID: 4900)
- cmd.exe (PID: 8072)
- cmd.exe (PID: 6516)
- cmd.exe (PID: 7300)
- cmd.exe (PID: 7292)
- cmd.exe (PID: 6964)
- cmd.exe (PID: 7756)
- cmd.exe (PID: 6804)
- cmd.exe (PID: 4640)
- cmd.exe (PID: 6096)
- cmd.exe (PID: 7452)
- cmd.exe (PID: 5744)
- cmd.exe (PID: 7504)
- cmd.exe (PID: 6700)
- cmd.exe (PID: 4144)
- cmd.exe (PID: 7232)
- cmd.exe (PID: 5632)
- cmd.exe (PID: 5572)
- cmd.exe (PID: 2900)
- cmd.exe (PID: 536)
- cmd.exe (PID: 1280)
- cmd.exe (PID: 7564)
- cmd.exe (PID: 6928)
- cmd.exe (PID: 6956)
- cmd.exe (PID: 6492)
- cmd.exe (PID: 512)
- cmd.exe (PID: 6548)
- cmd.exe (PID: 4212)
- cmd.exe (PID: 5772)
- cmd.exe (PID: 6212)
- cmd.exe (PID: 4516)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 2904)
- cmd.exe (PID: 1676)
- cmd.exe (PID: 7012)
- cmd.exe (PID: 3768)
- cmd.exe (PID: 7652)
- cmd.exe (PID: 1748)
- cmd.exe (PID: 6432)
- cmd.exe (PID: 1176)
- cmd.exe (PID: 4692)
- cmd.exe (PID: 4480)
- cmd.exe (PID: 5436)
- cmd.exe (PID: 3244)
- cmd.exe (PID: 2284)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 7604)
- cmd.exe (PID: 7388)
- cmd.exe (PID: 6968)
- cmd.exe (PID: 4936)
- cmd.exe (PID: 5700)
- cmd.exe (PID: 4660)
- cmd.exe (PID: 6856)
- cmd.exe (PID: 2468)
- cmd.exe (PID: 236)
- cmd.exe (PID: 7692)
- cmd.exe (PID: 5032)
- cmd.exe (PID: 3364)
- cmd.exe (PID: 6036)
- cmd.exe (PID: 6480)
- cmd.exe (PID: 904)
- cmd.exe (PID: 4388)
- cmd.exe (PID: 5244)
- cmd.exe (PID: 2656)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 5384)
- cmd.exe (PID: 5044)
- cmd.exe (PID: 7768)
- cmd.exe (PID: 6172)
- cmd.exe (PID: 2136)
- cmd.exe (PID: 7716)
- cmd.exe (PID: 7100)
- cmd.exe (PID: 2924)
- cmd.exe (PID: 300)
- cmd.exe (PID: 7096)
- cmd.exe (PID: 7540)
- cmd.exe (PID: 7556)
- cmd.exe (PID: 5316)
- cmd.exe (PID: 6524)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 8108)
- cmd.exe (PID: 6108)
- cmd.exe (PID: 1168)
- cmd.exe (PID: 7920)
- cmd.exe (PID: 4348)
- cmd.exe (PID: 3124)
- cmd.exe (PID: 7812)
- cmd.exe (PID: 5036)
- cmd.exe (PID: 8068)
- cmd.exe (PID: 8120)
- cmd.exe (PID: 7408)
- cmd.exe (PID: 4256)
- cmd.exe (PID: 7724)
- cmd.exe (PID: 6796)
- cmd.exe (PID: 6120)
- cmd.exe (PID: 4888)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 1388)
- cmd.exe (PID: 8060)
- cmd.exe (PID: 4028)
- cmd.exe (PID: 6972)
- cmd.exe (PID: 7620)
- cmd.exe (PID: 8176)
- cmd.exe (PID: 4236)
- cmd.exe (PID: 1916)
- cmd.exe (PID: 456)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 5004)
- cmd.exe (PID: 7924)
- cmd.exe (PID: 7188)
- cmd.exe (PID: 6632)
- cmd.exe (PID: 1912)
- cmd.exe (PID: 6384)
- cmd.exe (PID: 4464)
- cmd.exe (PID: 7384)
- cmd.exe (PID: 7420)
- cmd.exe (PID: 7792)
- cmd.exe (PID: 856)
- cmd.exe (PID: 5048)
- cmd.exe (PID: 4288)
- cmd.exe (PID: 8164)
- cmd.exe (PID: 7400)
- cmd.exe (PID: 7144)
- cmd.exe (PID: 2248)
- cmd.exe (PID: 4180)
- cmd.exe (PID: 7560)
- cmd.exe (PID: 8140)
- cmd.exe (PID: 7060)
- cmd.exe (PID: 5208)
- cmd.exe (PID: 5892)
- cmd.exe (PID: 6872)
- cmd.exe (PID: 6316)
- cmd.exe (PID: 8208)
- cmd.exe (PID: 8292)
- cmd.exe (PID: 4908)
- cmd.exe (PID: 8372)
- cmd.exe (PID: 8540)
- cmd.exe (PID: 8624)
- cmd.exe (PID: 8712)
- cmd.exe (PID: 8800)
- cmd.exe (PID: 8884)
- cmd.exe (PID: 8968)
- cmd.exe (PID: 9136)
- cmd.exe (PID: 9052)
- cmd.exe (PID: 5264)
- cmd.exe (PID: 8288)
- cmd.exe (PID: 6836)
- cmd.exe (PID: 8396)
- cmd.exe (PID: 8476)
- cmd.exe (PID: 8564)
- cmd.exe (PID: 8696)
- cmd.exe (PID: 8856)
- cmd.exe (PID: 8776)
- cmd.exe (PID: 8456)
- cmd.exe (PID: 9040)
- cmd.exe (PID: 8256)
- cmd.exe (PID: 9180)
- cmd.exe (PID: 8204)
- cmd.exe (PID: 8216)
- cmd.exe (PID: 8380)
- cmd.exe (PID: 8560)
- cmd.exe (PID: 8548)
- cmd.exe (PID: 8304)
- cmd.exe (PID: 8868)
- cmd.exe (PID: 8880)
- cmd.exe (PID: 9208)
- cmd.exe (PID: 9016)
- cmd.exe (PID: 9144)
- cmd.exe (PID: 7476)
- cmd.exe (PID: 8392)
- cmd.exe (PID: 8940)
- cmd.exe (PID: 9100)
- cmd.exe (PID: 8632)
- cmd.exe (PID: 8992)
- cmd.exe (PID: 8660)
- cmd.exe (PID: 8556)
- cmd.exe (PID: 8616)
- cmd.exe (PID: 8820)
- cmd.exe (PID: 8752)
- cmd.exe (PID: 8944)
- cmd.exe (PID: 8932)
- cmd.exe (PID: 4124)
- cmd.exe (PID: 8264)
- cmd.exe (PID: 7396)
- cmd.exe (PID: 8336)
- cmd.exe (PID: 8472)
- cmd.exe (PID: 8736)
- cmd.exe (PID: 8628)
- cmd.exe (PID: 8784)
- cmd.exe (PID: 8928)
- cmd.exe (PID: 8972)
- cmd.exe (PID: 9096)
- cmd.exe (PID: 8700)
- cmd.exe (PID: 3888)
- cmd.exe (PID: 8536)
- cmd.exe (PID: 6276)
- cmd.exe (PID: 8552)
- cmd.exe (PID: 8952)
- cmd.exe (PID: 8976)
- cmd.exe (PID: 9000)
- cmd.exe (PID: 8364)
- cmd.exe (PID: 8236)
- cmd.exe (PID: 8416)
- cmd.exe (PID: 8544)
- cmd.exe (PID: 9196)
- cmd.exe (PID: 9060)
- cmd.exe (PID: 8424)
- cmd.exe (PID: 8592)
- cmd.exe (PID: 9068)
- cmd.exe (PID: 8772)
- cmd.exe (PID: 8640)
- cmd.exe (PID: 7680)
- cmd.exe (PID: 8808)
- cmd.exe (PID: 8276)
- cmd.exe (PID: 9148)
- cmd.exe (PID: 2980)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 6500)
- cmd.exe (PID: 1704)
- cmd.exe (PID: 8816)
- cmd.exe (PID: 9076)
- cmd.exe (PID: 9104)
- cmd.exe (PID: 8240)
- cmd.exe (PID: 8300)
- cmd.exe (PID: 8612)
- cmd.exe (PID: 9072)
- cmd.exe (PID: 8232)
- cmd.exe (PID: 8484)
- cmd.exe (PID: 4420)
- cmd.exe (PID: 8340)
- cmd.exe (PID: 8760)
- cmd.exe (PID: 8876)
- cmd.exe (PID: 8656)
- cmd.exe (PID: 8828)
- cmd.exe (PID: 9092)
- cmd.exe (PID: 8964)
- cmd.exe (PID: 4268)
- cmd.exe (PID: 8316)
- cmd.exe (PID: 9020)
- cmd.exe (PID: 8832)
- cmd.exe (PID: 8524)
- cmd.exe (PID: 8744)
- cmd.exe (PID: 5180)
- cmd.exe (PID: 8900)
- cmd.exe (PID: 9032)
- cmd.exe (PID: 7220)
- cmd.exe (PID: 9168)
- cmd.exe (PID: 8520)
- cmd.exe (PID: 6152)
- cmd.exe (PID: 8764)
- cmd.exe (PID: 8580)
- cmd.exe (PID: 8848)
- cmd.exe (PID: 9044)
- cmd.exe (PID: 6704)
- cmd.exe (PID: 7424)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 8492)
- cmd.exe (PID: 8680)
- cmd.exe (PID: 3396)
- cmd.exe (PID: 8708)
- cmd.exe (PID: 8692)
- cmd.exe (PID: 8228)
- cmd.exe (PID: 8452)
- cmd.exe (PID: 8912)
- cmd.exe (PID: 8648)
- cmd.exe (PID: 8864)
- cmd.exe (PID: 4796)
- cmd.exe (PID: 8572)
- cmd.exe (PID: 8844)
- cmd.exe (PID: 8916)
- cmd.exe (PID: 6600)
- cmd.exe (PID: 8352)
- cmd.exe (PID: 8604)
- cmd.exe (PID: 8892)
- cmd.exe (PID: 9152)
- cmd.exe (PID: 7140)
- cmd.exe (PID: 7608)
- cmd.exe (PID: 1368)
- cmd.exe (PID: 8948)
- cmd.exe (PID: 9160)
- cmd.exe (PID: 6924)
- cmd.exe (PID: 8704)
- cmd.exe (PID: 9004)
- cmd.exe (PID: 8732)
- cmd.exe (PID: 8920)
- cmd.exe (PID: 3096)
- cmd.exe (PID: 8644)
- cmd.exe (PID: 8488)
- cmd.exe (PID: 9008)
- cmd.exe (PID: 3304)
- cmd.exe (PID: 8468)
- cmd.exe (PID: 8728)
- cmd.exe (PID: 8664)
- cmd.exe (PID: 9024)
- cmd.exe (PID: 8436)
- cmd.exe (PID: 9156)
- cmd.exe (PID: 8404)
- cmd.exe (PID: 8260)
- cmd.exe (PID: 232)
- cmd.exe (PID: 8596)
- cmd.exe (PID: 8924)
- cmd.exe (PID: 8720)
- cmd.exe (PID: 8636)
- cmd.exe (PID: 8804)
- cmd.exe (PID: 8716)
- cmd.exe (PID: 9088)
- cmd.exe (PID: 8824)
- cmd.exe (PID: 7256)
- cmd.exe (PID: 9012)
- cmd.exe (PID: 8768)
- cmd.exe (PID: 7892)
- cmd.exe (PID: 8872)
- cmd.exe (PID: 9048)
- cmd.exe (PID: 8936)
- cmd.exe (PID: 8960)
- cmd.exe (PID: 8908)
- cmd.exe (PID: 5172)
- cmd.exe (PID: 8568)
- cmd.exe (PID: 9204)
- cmd.exe (PID: 8584)
- cmd.exe (PID: 8504)
- cmd.exe (PID: 8408)
- cmd.exe (PID: 8676)
- cmd.exe (PID: 1136)
- cmd.exe (PID: 8428)
- cmd.exe (PID: 8852)
- cmd.exe (PID: 8608)
- cmd.exe (PID: 8588)
- cmd.exe (PID: 4616)
- cmd.exe (PID: 9064)
- cmd.exe (PID: 6348)
- cmd.exe (PID: 8756)
- cmd.exe (PID: 8792)
- cmd.exe (PID: 7696)
- cmd.exe (PID: 8328)
- cmd.exe (PID: 8904)
- cmd.exe (PID: 8252)
- cmd.exe (PID: 9028)
- cmd.exe (PID: 8116)
- cmd.exe (PID: 8996)
- cmd.exe (PID: 8780)
- cmd.exe (PID: 8444)
- cmd.exe (PID: 9108)
- cmd.exe (PID: 9140)
- cmd.exe (PID: 2408)
- cmd.exe (PID: 9200)
- cmd.exe (PID: 8724)
- cmd.exe (PID: 8248)
- cmd.exe (PID: 2596)
- cmd.exe (PID: 8448)
- cmd.exe (PID: 5360)
- cmd.exe (PID: 9212)
- cmd.exe (PID: 8412)
- cmd.exe (PID: 8988)
- cmd.exe (PID: 8600)
- cmd.exe (PID: 8840)
- cmd.exe (PID: 6168)
- cmd.exe (PID: 9120)
- cmd.exe (PID: 4008)
- cmd.exe (PID: 9036)
- cmd.exe (PID: 8984)
- cmd.exe (PID: 8860)
- cmd.exe (PID: 8688)
- cmd.exe (PID: 8496)
- cmd.exe (PID: 5500)
- cmd.exe (PID: 9116)
- cmd.exe (PID: 8360)
- cmd.exe (PID: 8980)
- cmd.exe (PID: 9084)
- cmd.exe (PID: 9128)
- cmd.exe (PID: 8324)
- cmd.exe (PID: 8576)
- cmd.exe (PID: 8308)
- cmd.exe (PID: 9124)
- cmd.exe (PID: 8652)
- cmd.exe (PID: 8320)
- cmd.exe (PID: 8388)
- cmd.exe (PID: 8668)
- cmd.exe (PID: 8464)
- cmd.exe (PID: 8532)
- cmd.exe (PID: 8280)
- cmd.exe (PID: 8896)
- cmd.exe (PID: 8296)
- cmd.exe (PID: 5200)
- cmd.exe (PID: 2840)
- cmd.exe (PID: 9232)
- cmd.exe (PID: 7120)
- cmd.exe (PID: 8224)
- cmd.exe (PID: 8672)
- cmd.exe (PID: 7636)
- cmd.exe (PID: 9652)
- cmd.exe (PID: 9400)
- cmd.exe (PID: 9568)
- cmd.exe (PID: 9736)
- cmd.exe (PID: 9816)
- cmd.exe (PID: 8384)
- cmd.exe (PID: 9316)
- cmd.exe (PID: 9484)
- cmd.exe (PID: 9904)
- cmd.exe (PID: 4976)
- cmd.exe (PID: 9988)
- cmd.exe (PID: 9556)
- cmd.exe (PID: 10160)
- cmd.exe (PID: 9292)
- cmd.exe (PID: 9472)
- cmd.exe (PID: 9376)
- cmd.exe (PID: 9848)
- cmd.exe (PID: 9616)
- cmd.exe (PID: 9696)
- cmd.exe (PID: 9740)
- cmd.exe (PID: 10108)
- cmd.exe (PID: 10200)
- cmd.exe (PID: 8376)
- cmd.exe (PID: 10072)
- cmd.exe (PID: 9908)
- cmd.exe (PID: 10064)
- cmd.exe (PID: 9604)
- cmd.exe (PID: 9656)
- cmd.exe (PID: 9788)
- cmd.exe (PID: 9952)
- cmd.exe (PID: 10060)
- cmd.exe (PID: 10208)
- cmd.exe (PID: 9416)
- cmd.exe (PID: 9300)
- cmd.exe (PID: 9312)
- cmd.exe (PID: 9500)
- cmd.exe (PID: 9688)
- cmd.exe (PID: 9628)
- cmd.exe (PID: 9748)
- cmd.exe (PID: 9372)
- cmd.exe (PID: 9364)
- cmd.exe (PID: 9560)
- cmd.exe (PID: 10124)
- cmd.exe (PID: 10100)
- cmd.exe (PID: 9660)
- cmd.exe (PID: 9264)
- cmd.exe (PID: 9432)
- cmd.exe (PID: 9576)
- cmd.exe (PID: 9868)
- cmd.exe (PID: 10204)
- cmd.exe (PID: 9936)
- cmd.exe (PID: 9980)
- cmd.exe (PID: 6340)
- cmd.exe (PID: 9764)
- cmd.exe (PID: 10120)
- cmd.exe (PID: 9968)
- cmd.exe (PID: 9224)
- cmd.exe (PID: 9516)
- cmd.exe (PID: 9592)
- cmd.exe (PID: 9332)
- cmd.exe (PID: 9932)
- cmd.exe (PID: 9260)
- cmd.exe (PID: 10132)
- cmd.exe (PID: 9548)
- cmd.exe (PID: 9744)
- cmd.exe (PID: 9524)
- cmd.exe (PID: 10024)
- cmd.exe (PID: 9940)
- cmd.exe (PID: 10144)
- cmd.exe (PID: 9356)
- cmd.exe (PID: 9552)
- cmd.exe (PID: 9596)
- cmd.exe (PID: 9976)
- cmd.exe (PID: 9732)
- cmd.exe (PID: 9320)
- cmd.exe (PID: 9680)
- cmd.exe (PID: 9404)
- cmd.exe (PID: 9896)
- cmd.exe (PID: 10088)
- cmd.exe (PID: 9384)
- cmd.exe (PID: 10056)
- cmd.exe (PID: 10040)
- cmd.exe (PID: 9800)
- cmd.exe (PID: 9496)
- cmd.exe (PID: 9304)
- cmd.exe (PID: 9648)
- cmd.exe (PID: 10052)
- cmd.exe (PID: 9992)
- cmd.exe (PID: 8356)
- cmd.exe (PID: 9644)
- cmd.exe (PID: 9464)
- cmd.exe (PID: 9308)
- cmd.exe (PID: 10136)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 10232)
- cmd.exe (PID: 9812)
- cmd.exe (PID: 9348)
- cmd.exe (PID: 9900)
- cmd.exe (PID: 9492)
- cmd.exe (PID: 9852)
- cmd.exe (PID: 10116)
- cmd.exe (PID: 9892)
- cmd.exe (PID: 10164)
- cmd.exe (PID: 9716)
- cmd.exe (PID: 9612)
- cmd.exe (PID: 9488)
- cmd.exe (PID: 9640)
- cmd.exe (PID: 9840)
- cmd.exe (PID: 9832)
- cmd.exe (PID: 8836)
- cmd.exe (PID: 10016)
- cmd.exe (PID: 9672)
- cmd.exe (PID: 9768)
- cmd.exe (PID: 10184)
- cmd.exe (PID: 10172)
- cmd.exe (PID: 9220)
- cmd.exe (PID: 9528)
- cmd.exe (PID: 9536)
- cmd.exe (PID: 9872)
- cmd.exe (PID: 9804)
- cmd.exe (PID: 8272)
- cmd.exe (PID: 9624)
- cmd.exe (PID: 9584)
- cmd.exe (PID: 9676)
- cmd.exe (PID: 9824)
- cmd.exe (PID: 9944)
- cmd.exe (PID: 9256)
- cmd.exe (PID: 10188)
- cmd.exe (PID: 9268)
- cmd.exe (PID: 10156)
- cmd.exe (PID: 10220)
- cmd.exe (PID: 9780)
- cmd.exe (PID: 9928)
- cmd.exe (PID: 9912)
- cmd.exe (PID: 9572)
- cmd.exe (PID: 9972)
- cmd.exe (PID: 9884)
- cmd.exe (PID: 9380)
- cmd.exe (PID: 10044)
- cmd.exe (PID: 9920)
- cmd.exe (PID: 10228)
- cmd.exe (PID: 9636)
- cmd.exe (PID: 9664)
- cmd.exe (PID: 10028)
- cmd.exe (PID: 10224)
- cmd.exe (PID: 9620)
- cmd.exe (PID: 9808)
- cmd.exe (PID: 9608)
- cmd.exe (PID: 8480)
- cmd.exe (PID: 9340)
- cmd.exe (PID: 9712)
- cmd.exe (PID: 10096)
- cmd.exe (PID: 9728)
- cmd.exe (PID: 9704)
- cmd.exe (PID: 9392)
- cmd.exe (PID: 9476)
- cmd.exe (PID: 9512)
- cmd.exe (PID: 10020)
- cmd.exe (PID: 8332)
- cmd.exe (PID: 9964)
- cmd.exe (PID: 10176)
- cmd.exe (PID: 9684)
- cmd.exe (PID: 9692)
- cmd.exe (PID: 9324)
- cmd.exe (PID: 496)
- cmd.exe (PID: 9860)
- cmd.exe (PID: 9668)
- cmd.exe (PID: 9864)
- cmd.exe (PID: 9368)
- cmd.exe (PID: 10032)
- cmd.exe (PID: 10236)
- cmd.exe (PID: 9880)
- cmd.exe (PID: 9508)
- cmd.exe (PID: 9844)
- cmd.exe (PID: 2064)
- cmd.exe (PID: 9388)
- cmd.exe (PID: 7076)
- cmd.exe (PID: 9960)
- cmd.exe (PID: 10196)
- cmd.exe (PID: 9176)
- cmd.exe (PID: 7832)
- cmd.exe (PID: 10140)
- cmd.exe (PID: 9280)
- cmd.exe (PID: 9828)
- cmd.exe (PID: 9996)
- cmd.exe (PID: 10000)
- cmd.exe (PID: 8788)
- cmd.exe (PID: 6400)
- cmd.exe (PID: 10068)
- cmd.exe (PID: 9188)
- cmd.exe (PID: 9480)
- cmd.exe (PID: 9284)
- cmd.exe (PID: 9820)
- cmd.exe (PID: 9288)
- cmd.exe (PID: 9924)
- cmd.exe (PID: 9132)
- cmd.exe (PID: 8440)
- cmd.exe (PID: 10048)
- cmd.exe (PID: 8512)
- cmd.exe (PID: 552)
- cmd.exe (PID: 9700)
Explorer used for Indirect Command Execution
- cmd.exe (PID: 4012)
Starts CMD.EXE for commands execution
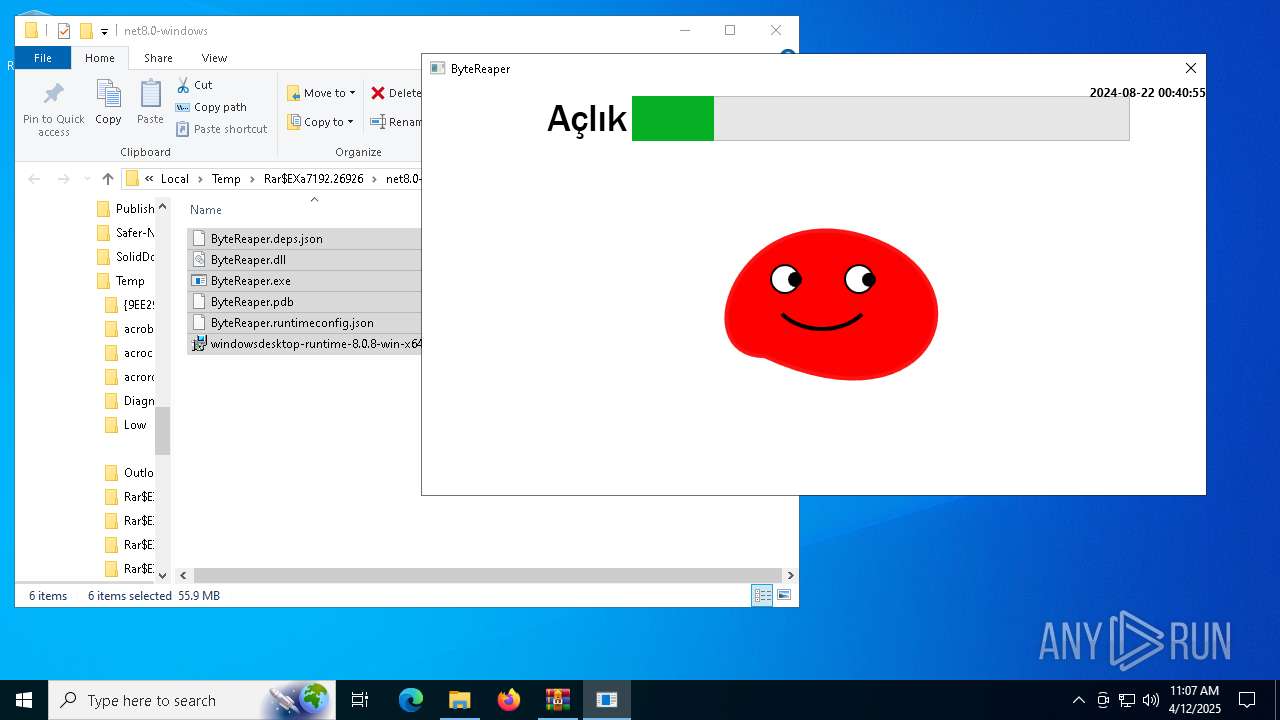
- ByteReaper.exe (PID: 8028)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 7552)
- SearchApp.exe (PID: 1568)
INFO
Application launched itself
- msedge.exe (PID: 7300)
- msedge.exe (PID: 5972)
Autorun file from Downloads
- msedge.exe (PID: 900)
Reads Microsoft Office registry keys
- msedge.exe (PID: 7300)
Reads Environment values
- identity_helper.exe (PID: 1324)
- identity_helper.exe (PID: 8140)
- SearchApp.exe (PID: 1568)
Checks supported languages
- identity_helper.exe (PID: 1324)
- identity_helper.exe (PID: 8140)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 3020)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 8184)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 976)
- msiexec.exe (PID: 7804)
- msiexec.exe (PID: 7736)
- ByteReaper.exe (PID: 7424)
- msiexec.exe (PID: 7764)
- msiexec.exe (PID: 7408)
- ByteReaper.exe (PID: 7900)
- ByteReaper.exe (PID: 8028)
- ShellExperienceHost.exe (PID: 7100)
- msiexec.exe (PID: 7552)
- TextInputHost.exe (PID: 4944)
- StartMenuExperienceHost.exe (PID: 7552)
- SearchApp.exe (PID: 1568)
- ShellExperienceHost.exe (PID: 8196)
Reads the computer name
- identity_helper.exe (PID: 1324)
- identity_helper.exe (PID: 8140)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 8184)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 976)
- msiexec.exe (PID: 7804)
- ByteReaper.exe (PID: 7424)
- msiexec.exe (PID: 7736)
- msiexec.exe (PID: 7764)
- msiexec.exe (PID: 7408)
- msiexec.exe (PID: 7552)
- ByteReaper.exe (PID: 7900)
- ByteReaper.exe (PID: 8028)
- ShellExperienceHost.exe (PID: 7100)
- StartMenuExperienceHost.exe (PID: 7552)
- TextInputHost.exe (PID: 4944)
- SearchApp.exe (PID: 1568)
- ShellExperienceHost.exe (PID: 8196)
Create files in a temporary directory
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 3020)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 8184)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 976)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7192)
- msiexec.exe (PID: 7804)
- msedge.exe (PID: 7488)
The sample compiled with english language support
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 3020)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 8184)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 976)
- msiexec.exe (PID: 7804)
- msedge.exe (PID: 7488)
Process checks computer location settings
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 8184)
- ByteReaper.exe (PID: 8028)
- StartMenuExperienceHost.exe (PID: 7552)
- SearchApp.exe (PID: 1568)
Reads the machine GUID from the registry
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 976)
- msiexec.exe (PID: 7804)
- SearchApp.exe (PID: 1568)
Creates files in the program directory
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 976)
- ByteReaper.exe (PID: 8028)
Reads the software policy settings
- msiexec.exe (PID: 7804)
- slui.exe (PID: 2148)
- slui.exe (PID: 5408)
- SearchApp.exe (PID: 1568)
Creates files or folders in the user directory
- msiexec.exe (PID: 7804)
Creates a software uninstall entry
- msiexec.exe (PID: 7804)
Checks proxy server information
- slui.exe (PID: 5408)
- SearchApp.exe (PID: 1568)
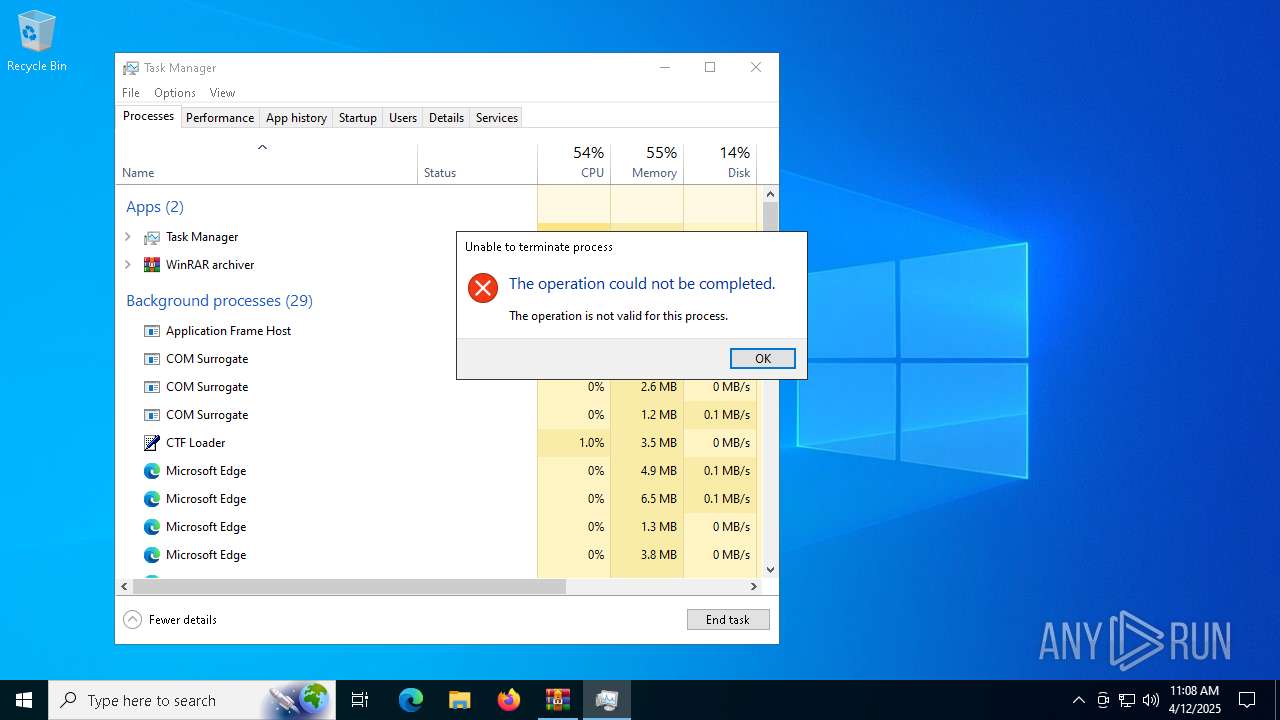
Manual execution by a user
- Taskmgr.exe (PID: 9808)
- Taskmgr.exe (PID: 9296)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 9296)
- explorer.exe (PID: 6900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
2 411
Monitored processes
2 259
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 132 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | "cmd.exe" /c takeown /f "C:\Windows\System32\certutil.exe" /a && icacls "C:\Windows\System32\certutil.exe" /grant administrators:F | C:\Windows\System32\cmd.exe | — | ByteReaper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | "cmd.exe" /c takeown /f "C:\Windows\System32\AppVStreamingUX.dll" /a && icacls "C:\Windows\System32\AppVStreamingUX.dll" /grant administrators:F | C:\Windows\System32\cmd.exe | — | ByteReaper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | takeown /f "C:\Windows\System32\apds.dll" /a | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Takes ownership of a file Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | "cmd.exe" /c takeown /f "C:\Windows\System32\aspnet_counters.dll" /a && icacls "C:\Windows\System32\aspnet_counters.dll" /grant administrators:F | C:\Windows\System32\cmd.exe | — | ByteReaper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
68 950
Read events
67 828
Write events
1 067
Delete events
55
Modification events
| (PID) Process: | (7300) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7300) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7300) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7300) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7300) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: E0A71D1129912F00 | |||
| (PID) Process: | (7300) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 9A78261129912F00 | |||
| (PID) Process: | (7300) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262988 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {F047D92B-DA26-42B4-A199-144D9104BD90} | |||
| (PID) Process: | (7300) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262988 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {F0C20954-2368-43A9-907E-DDFFFFBECA35} | |||
| (PID) Process: | (7300) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262988 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {CA61B3AC-A9B6-413A-BE1E-488D5A370415} | |||
| (PID) Process: | (7300) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262988 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {DE50BFC3-78FA-4957-B5A8-8297F9FFDBAD} | |||
Executable files
514
Suspicious files
684
Text files
182
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10b4bb.TMP | — | |
MD5:— | SHA256:— | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10b4cb.TMP | — | |
MD5:— | SHA256:— | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10b4cb.TMP | — | |
MD5:— | SHA256:— | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10b4cb.TMP | — | |
MD5:— | SHA256:— | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10b4cb.TMP | — | |
MD5:— | SHA256:— | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
92
DNS requests
86
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5352 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5352 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7804 | msiexec.exe | GET | 200 | 23.216.77.27:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5400 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d0729495-2185-4a92-a46f-fde358fd775c?P1=1744953267&P2=404&P3=2&P4=fzUhyO3AYYgiWFksgkjdvJgyJWtRUksUaZhVeLhuX1blrXIk16hsG%2fuGUy0n1RB9iOTJn7NV2mpUAkuFeW%2fkOQ%3d%3d | unknown | — | — | whitelisted |
7804 | msiexec.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
5400 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d0729495-2185-4a92-a46f-fde358fd775c?P1=1744953267&P2=404&P3=2&P4=fzUhyO3AYYgiWFksgkjdvJgyJWtRUksUaZhVeLhuX1blrXIk16hsG%2fuGUy0n1RB9iOTJn7NV2mpUAkuFeW%2fkOQ%3d%3d | unknown | — | — | whitelisted |
5400 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d0729495-2185-4a92-a46f-fde358fd775c?P1=1744953267&P2=404&P3=2&P4=fzUhyO3AYYgiWFksgkjdvJgyJWtRUksUaZhVeLhuX1blrXIk16hsG%2fuGUy0n1RB9iOTJn7NV2mpUAkuFeW%2fkOQ%3d%3d | unknown | — | — | whitelisted |
5400 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d0729495-2185-4a92-a46f-fde358fd775c?P1=1744953267&P2=404&P3=2&P4=fzUhyO3AYYgiWFksgkjdvJgyJWtRUksUaZhVeLhuX1blrXIk16hsG%2fuGUy0n1RB9iOTJn7NV2mpUAkuFeW%2fkOQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7300 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7596 | msedge.exe | 188.114.97.3:443 | sparrow99.com.tr | — | — | unknown |
7596 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7596 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7596 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
sparrow99.com.tr |
| unknown |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.bing.com |
| whitelisted |