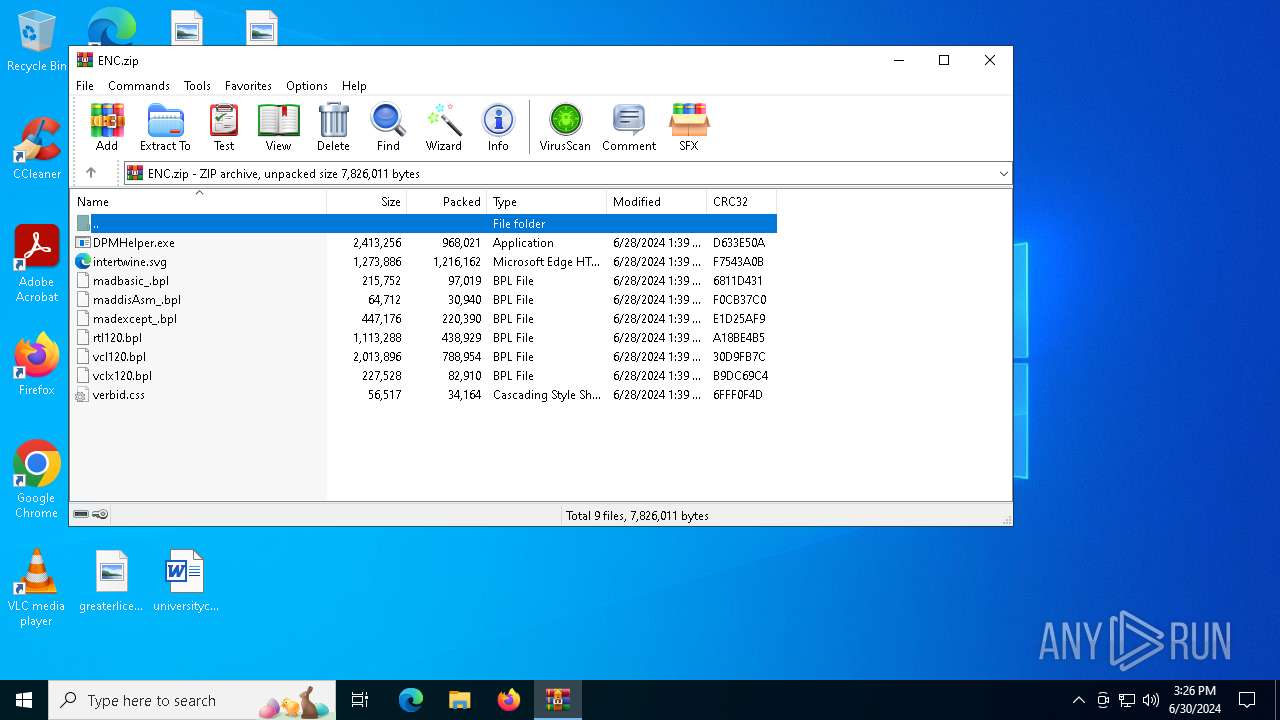
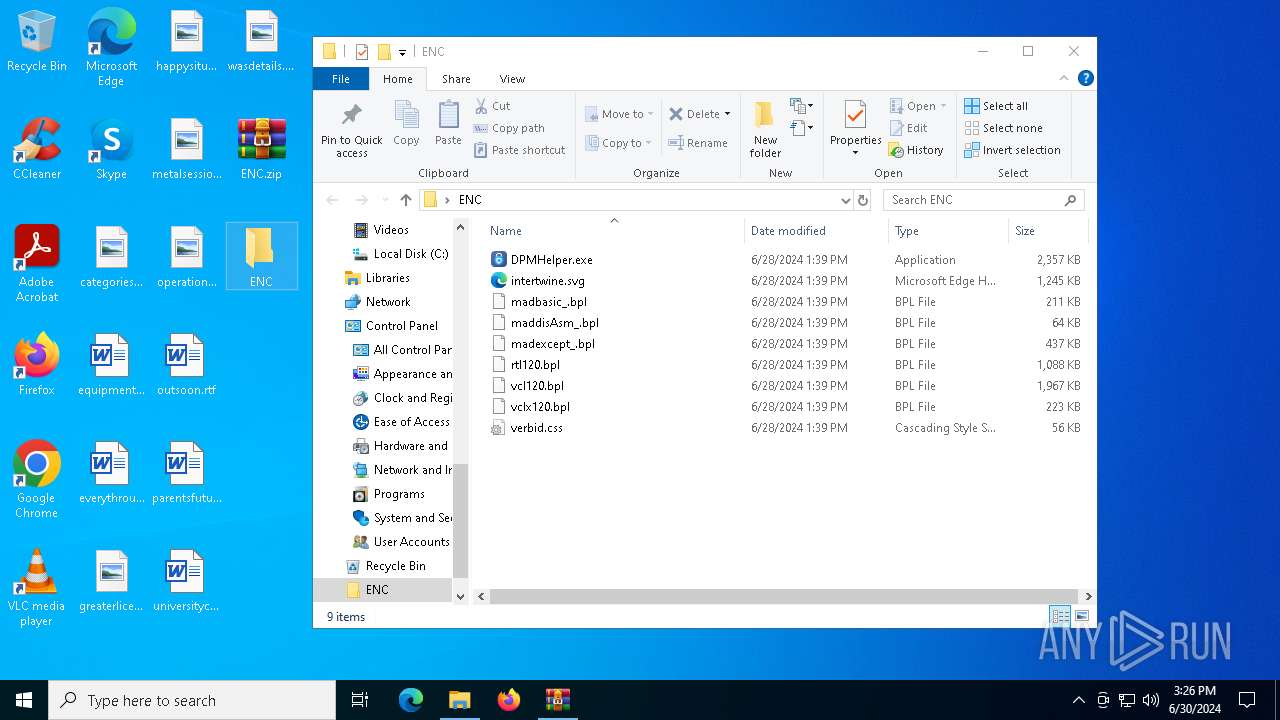
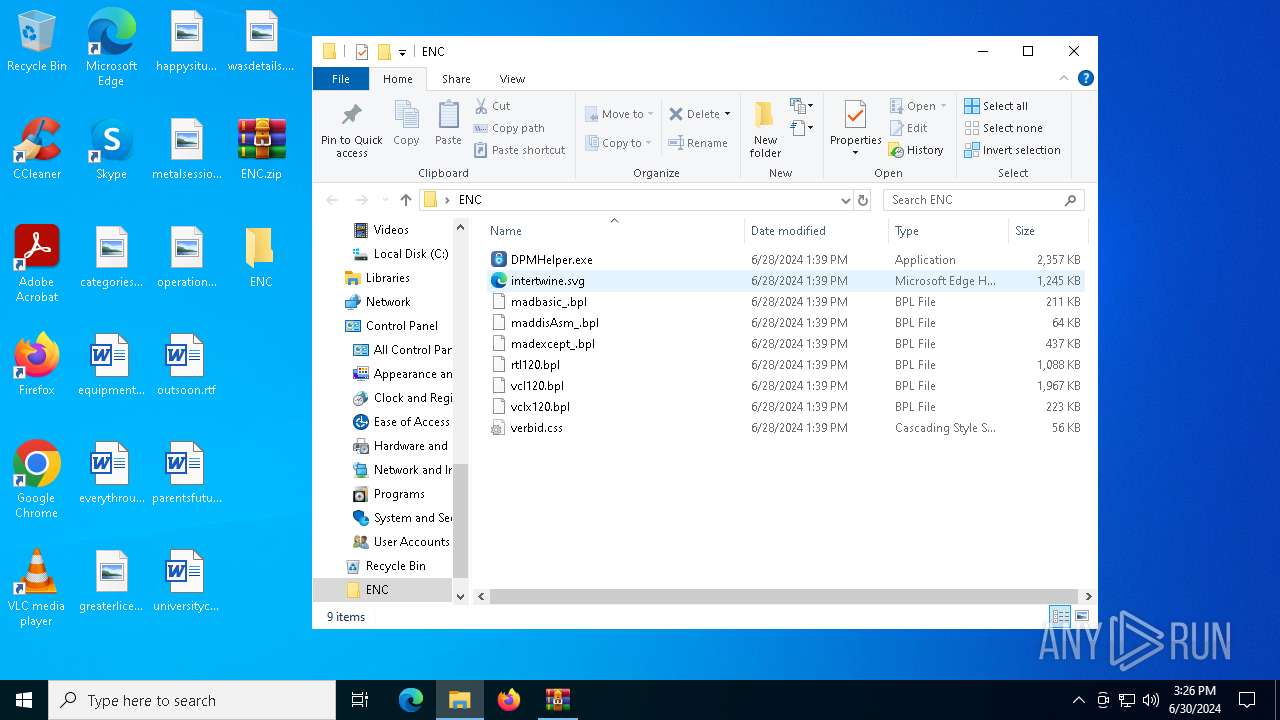
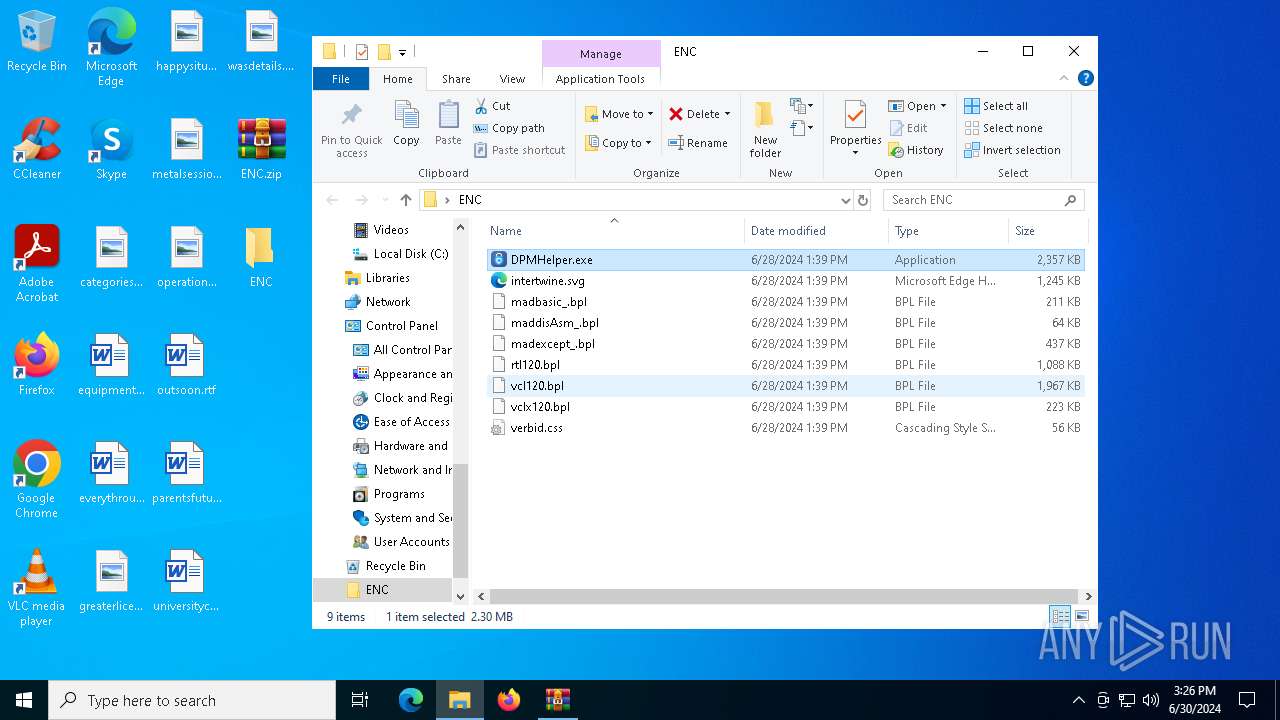
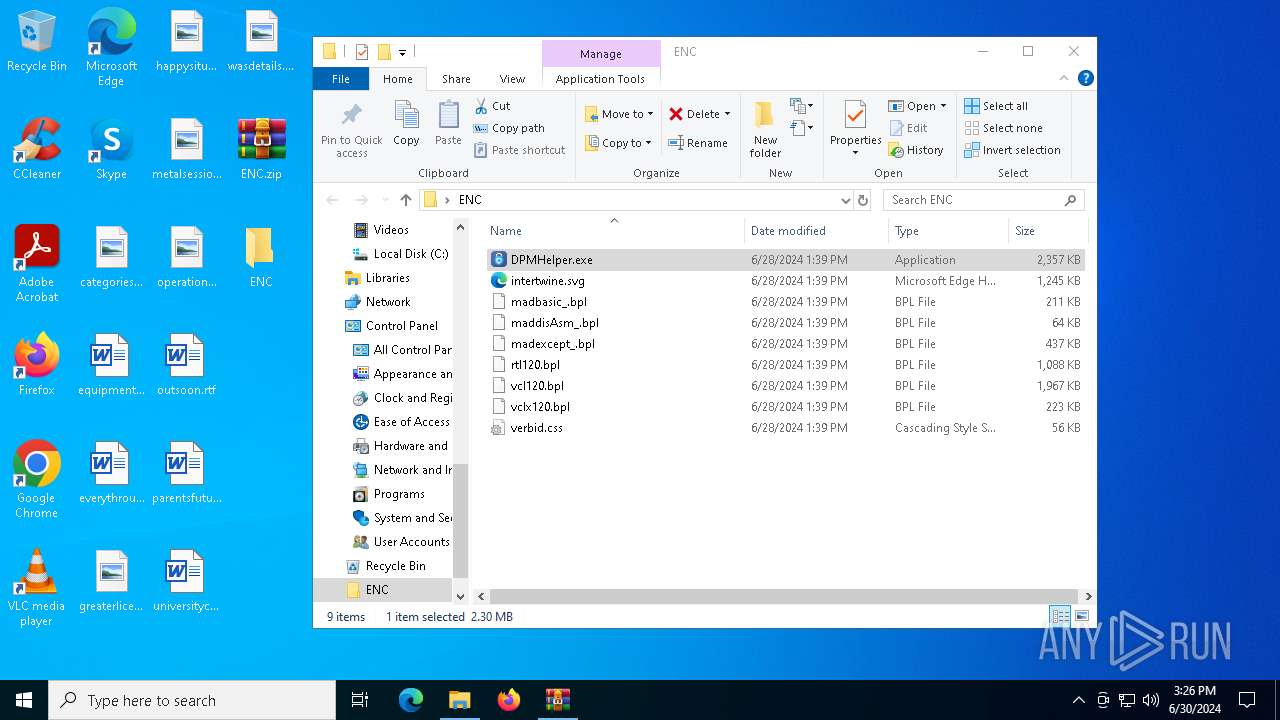
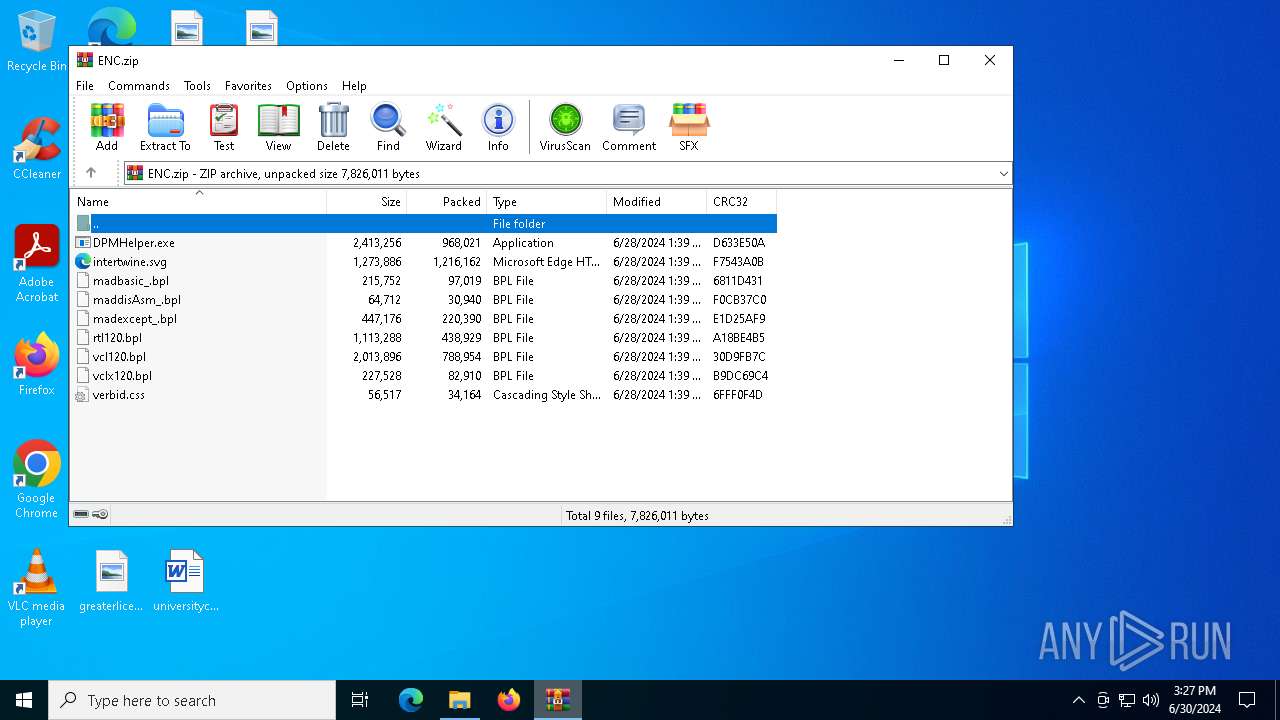
| File name: | ENC |
| Full analysis: | https://app.any.run/tasks/d124fe84-07dd-49e3-aa0d-97878153bd49 |
| Verdict: | Malicious activity |
| Analysis date: | June 30, 2024, 15:26:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 34DD73380E19295EEF9C195A9F35C9B3 |
| SHA1: | 1DBA9C380A04DB59525E3FBECA22306E4CF97992 |
| SHA256: | 208E322FE1E0E726AA69B3AC530DA9AD4432DC046202CD06CE655148A73895A8 |
| SSDEEP: | 98304:D2BtFZVErO7S8cEoJbfijeyxz4iKBDf9IQrb6F5YGdrzXRrwHcb/csU9Sy5vqz7C:KjIyfG |
MALICIOUS
Drops the executable file immediately after the start
- DPMHelper.exe (PID: 5932)
- WinRAR.exe (PID: 4052)
- Eonte.au3 (PID: 1784)
- cmd.exe (PID: 4148)
SUSPICIOUS
Executable content was dropped or overwritten
- cmd.exe (PID: 4148)
- DPMHelper.exe (PID: 5932)
- Eonte.au3 (PID: 1784)
The executable file from the user directory is run by the CMD process
- Eonte.au3 (PID: 1784)
Starts CMD.EXE for commands execution
- DPMHelper.exe (PID: 2272)
Starts application with an unusual extension
- cmd.exe (PID: 4148)
Starts itself from another location
- DPMHelper.exe (PID: 5932)
INFO
Checks supported languages
- DPMHelper.exe (PID: 5932)
- Eonte.au3 (PID: 1784)
- DPMHelper.exe (PID: 2272)
Manual execution by a user
- DPMHelper.exe (PID: 5932)
Creates files or folders in the user directory
- DPMHelper.exe (PID: 5932)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4052)
Reads the computer name
- DPMHelper.exe (PID: 5932)
- Eonte.au3 (PID: 1784)
- DPMHelper.exe (PID: 2272)
Create files in a temporary directory
- DPMHelper.exe (PID: 2272)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:28 13:39:16 |
| ZipCRC: | 0xd633e50a |
| ZipCompressedSize: | 968021 |
| ZipUncompressedSize: | 2413256 |
| ZipFileName: | DPMHelper.exe |
Total processes
142
Monitored processes
7
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1784 | C:\Users\admin\AppData\Local\Temp\Eonte.au3 | C:\Users\admin\AppData\Local\Temp\Eonte.au3 | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Version: 3, 3, 14, 5 Modules
| |||||||||||||||
| 2272 | C:\Users\admin\AppData\Roaming\OracleSuper_test\DPMHelper.exe | C:\Users\admin\AppData\Roaming\OracleSuper_test\DPMHelper.exe | — | DPMHelper.exe | |||||||||||
User: admin Company: iTop Inc. Integrity Level: MEDIUM Description: DualSafe Password Manager Version: 1.4.0.3 Modules
| |||||||||||||||
| 2404 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4052 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\ENC.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4148 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | DPMHelper.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4280 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5932 | "C:\Users\admin\Desktop\ENC\DPMHelper.exe" | C:\Users\admin\Desktop\ENC\DPMHelper.exe | explorer.exe | ||||||||||||
User: admin Company: iTop Inc. Integrity Level: MEDIUM Description: DualSafe Password Manager Exit code: 0 Version: 1.4.0.3 Modules
| |||||||||||||||
Total events
4 161
Read events
4 140
Write events
21
Delete events
0
Modification events
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\ENC.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\ieframe.dll,-24585 |
Value: Cascading Style Sheet Document | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\ENC | |||
Executable files
14
Suspicious files
18
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4148 | cmd.exe | C:\Users\admin\AppData\Local\Temp\sbklifwxkfj | — | |
MD5:— | SHA256:— | |||
| 4052 | WinRAR.exe | C:\Users\admin\Desktop\ENC\madexcept_.bpl | executable | |
MD5:98E59596EDD9B888D906C5409E515803 | SHA256:A6CA13AF74A64E4AB5EBB2D12B757CECF1A683CB9CD0AE7906DB1B4B2C8A90C0 | |||
| 4052 | WinRAR.exe | C:\Users\admin\Desktop\ENC\DPMHelper.exe | executable | |
MD5:5D52EF45B6E5BF144307A84C2AF1581B | SHA256:26A24D3B0206C6808615C7049859C2FE62C4DCD87E7858BE40AE8112B0482616 | |||
| 5932 | DPMHelper.exe | C:\Users\admin\AppData\Roaming\OracleSuper_test\madbasic_.bpl | executable | |
MD5:E03A0056E75D3A5707BA199BC2EA701F | SHA256:7826395127E791A883359EA81308174700DA0AF8052CC9853B19FD29C2E4BADB | |||
| 4052 | WinRAR.exe | C:\Users\admin\Desktop\ENC\maddisAsm_.bpl | executable | |
MD5:EF3B47B2EA3884914C13C778FF29EB5B | SHA256:475F7CDFFD8ED4D6F52BD98AE2BB684F1C923A1BE2A692757A9AF788A39B1D87 | |||
| 4052 | WinRAR.exe | C:\Users\admin\Desktop\ENC\vclx120.bpl | executable | |
MD5:3CB8F7606940C9B51C45EBAEB84AF728 | SHA256:2FEEC33D1E3F3D69C717F4528B8F7F5C030CAAE6FB37C2100CB0B5341367D053 | |||
| 4052 | WinRAR.exe | C:\Users\admin\Desktop\ENC\madbasic_.bpl | executable | |
MD5:E03A0056E75D3A5707BA199BC2EA701F | SHA256:7826395127E791A883359EA81308174700DA0AF8052CC9853B19FD29C2E4BADB | |||
| 5932 | DPMHelper.exe | C:\Users\admin\AppData\Roaming\OracleSuper_test\vclx120.bpl | executable | |
MD5:3CB8F7606940C9B51C45EBAEB84AF728 | SHA256:2FEEC33D1E3F3D69C717F4528B8F7F5C030CAAE6FB37C2100CB0B5341367D053 | |||
| 5932 | DPMHelper.exe | C:\Users\admin\AppData\Roaming\OracleSuper_test\rtl120.bpl | executable | |
MD5:1681F93E11A7ED23612A55BCEF7F1023 | SHA256:7ED5369FCF0283EA18974C43DBFF80E6006B155B76DA7C72FA9619EB03F54CEF | |||
| 4052 | WinRAR.exe | C:\Users\admin\Desktop\ENC\vcl120.bpl | binary | |
MD5:CD778689B7768456C271FCAD811846D0 | SHA256:6BA0CEB1BE8E979CB480A67F9C2AA80D6E5CE7E3A94057167E0ECDC843B17804 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
68
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 142.250.184.195:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | unknown |
— | — | GET | 200 | 142.250.184.195:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | unknown |
1436 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1436 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1972 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
1888 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
1888 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
4172 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2912 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3172 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1436 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1544 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1544 | svchost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
4656 | SearchApp.exe | 92.123.104.56:443 | — | Akamai International B.V. | DE | unknown |
1060 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |