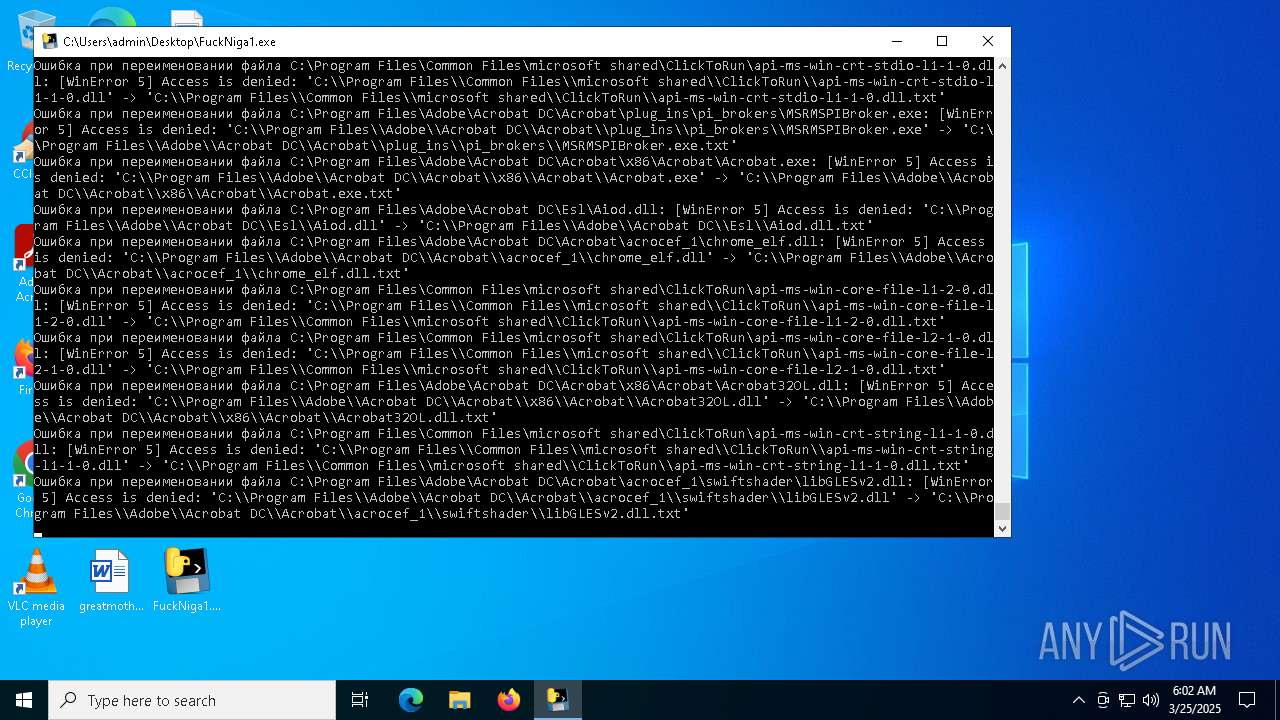
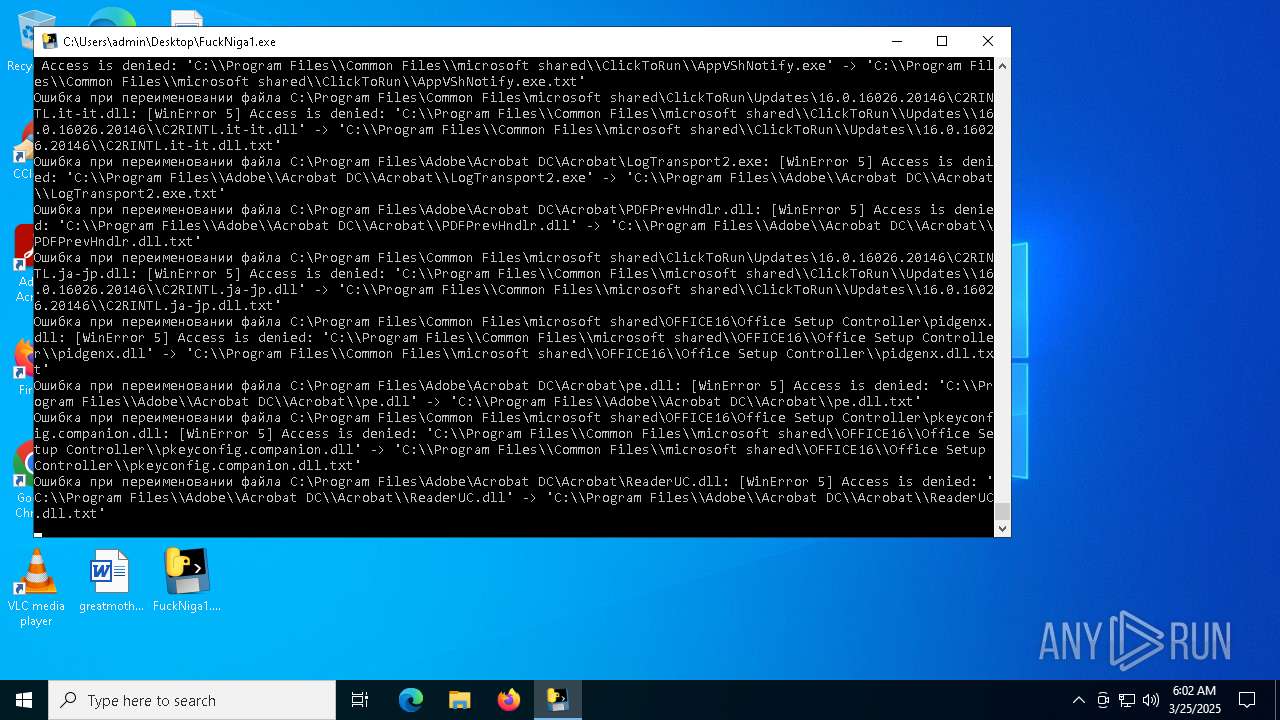
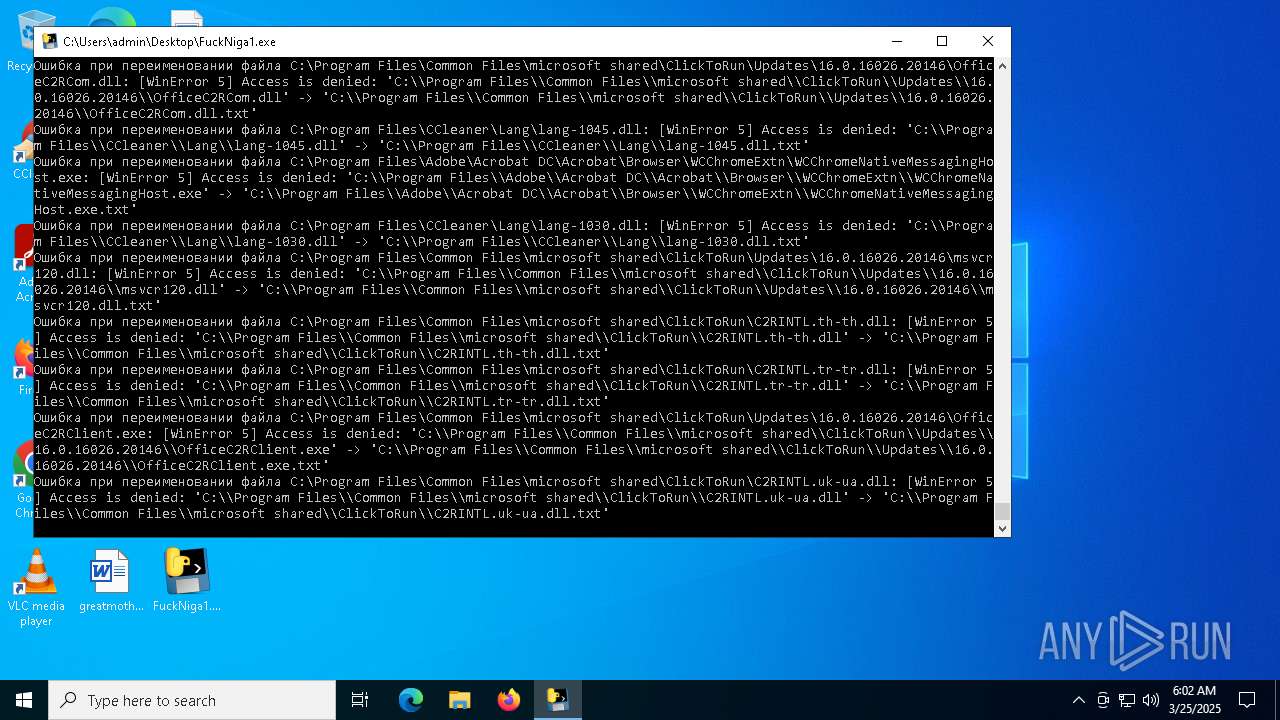
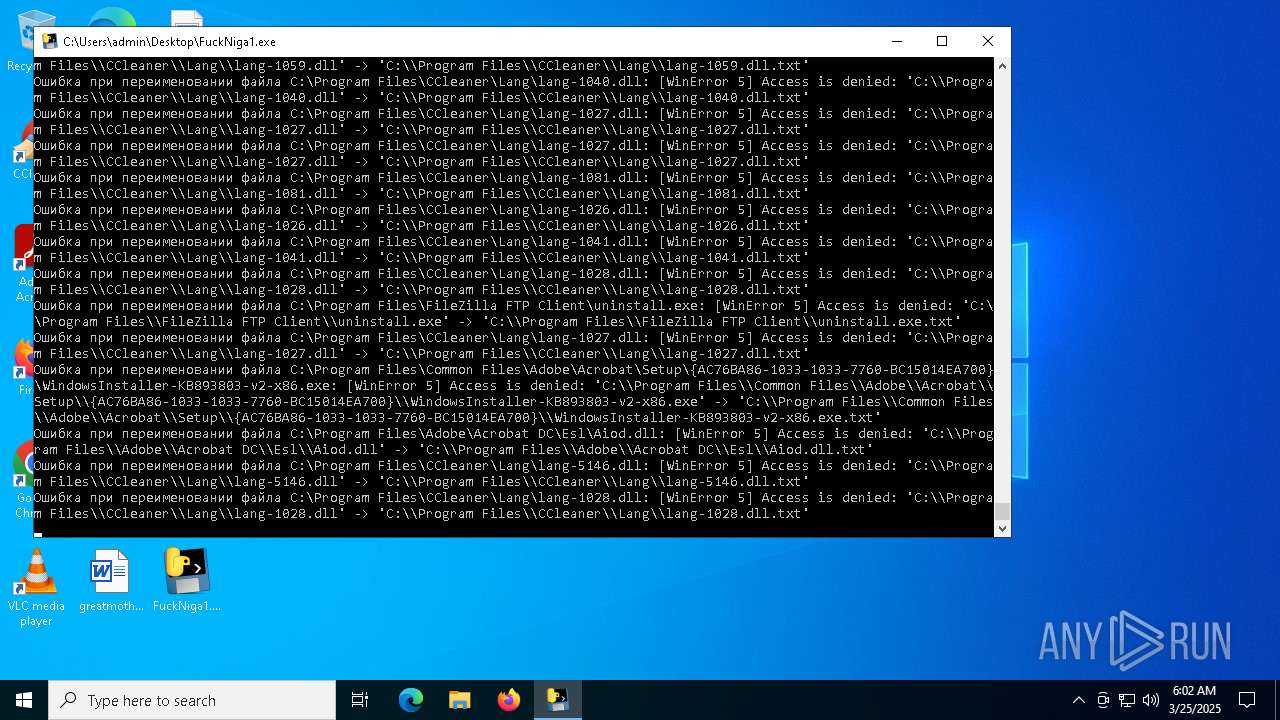
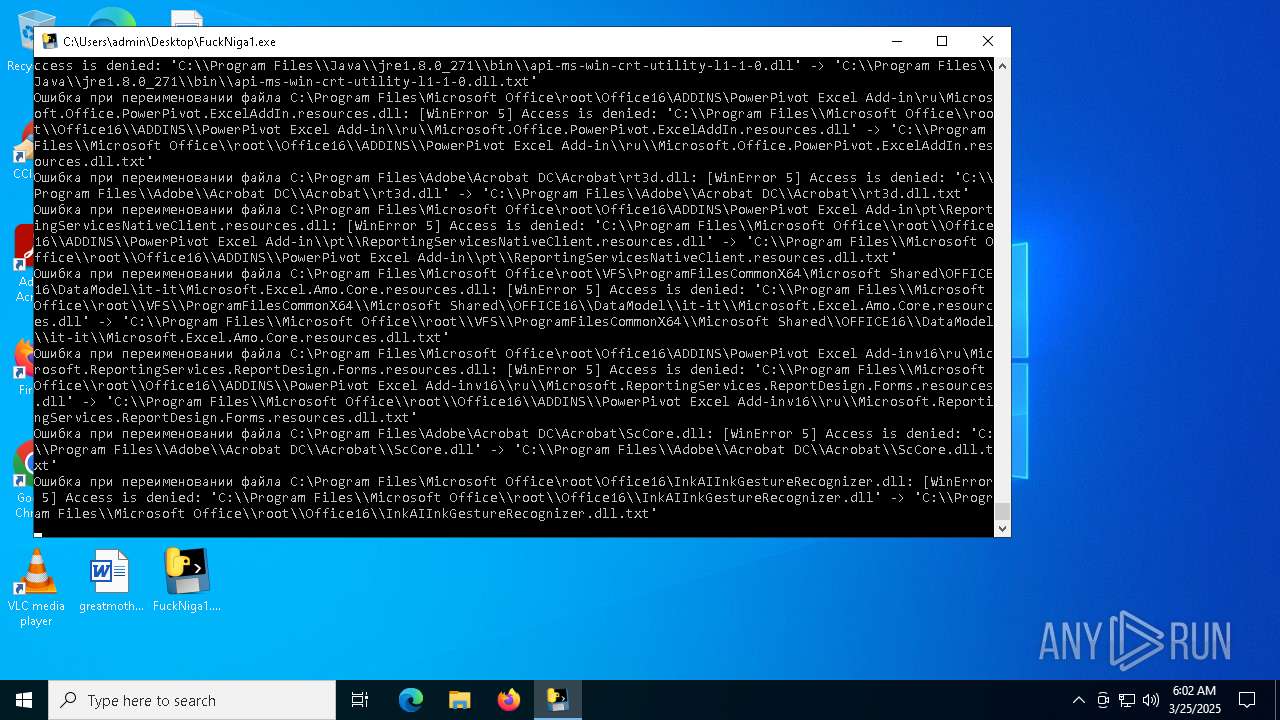
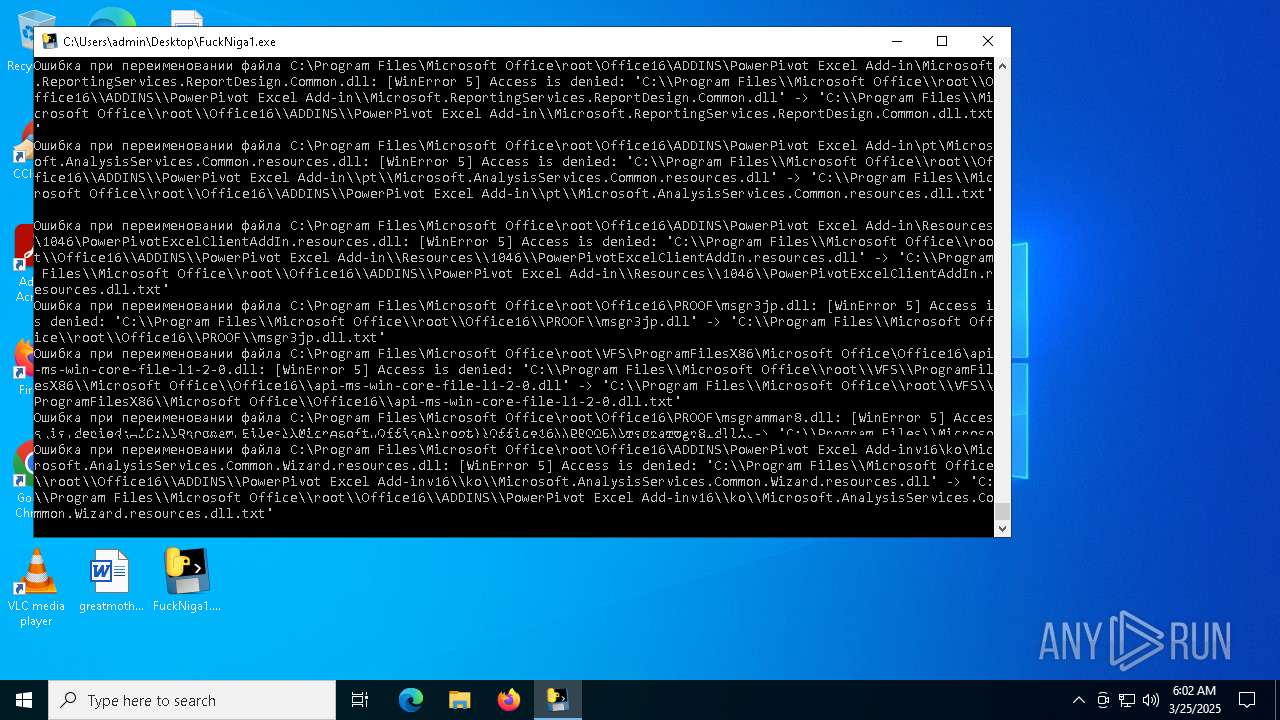
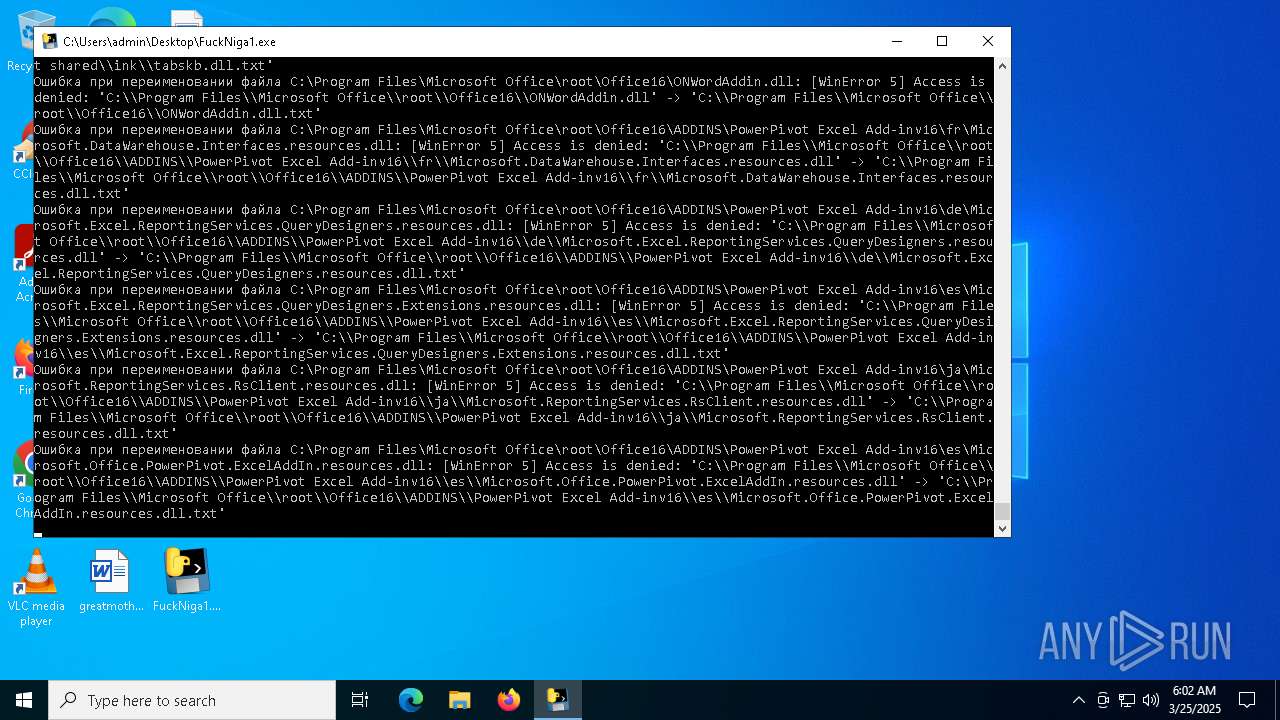
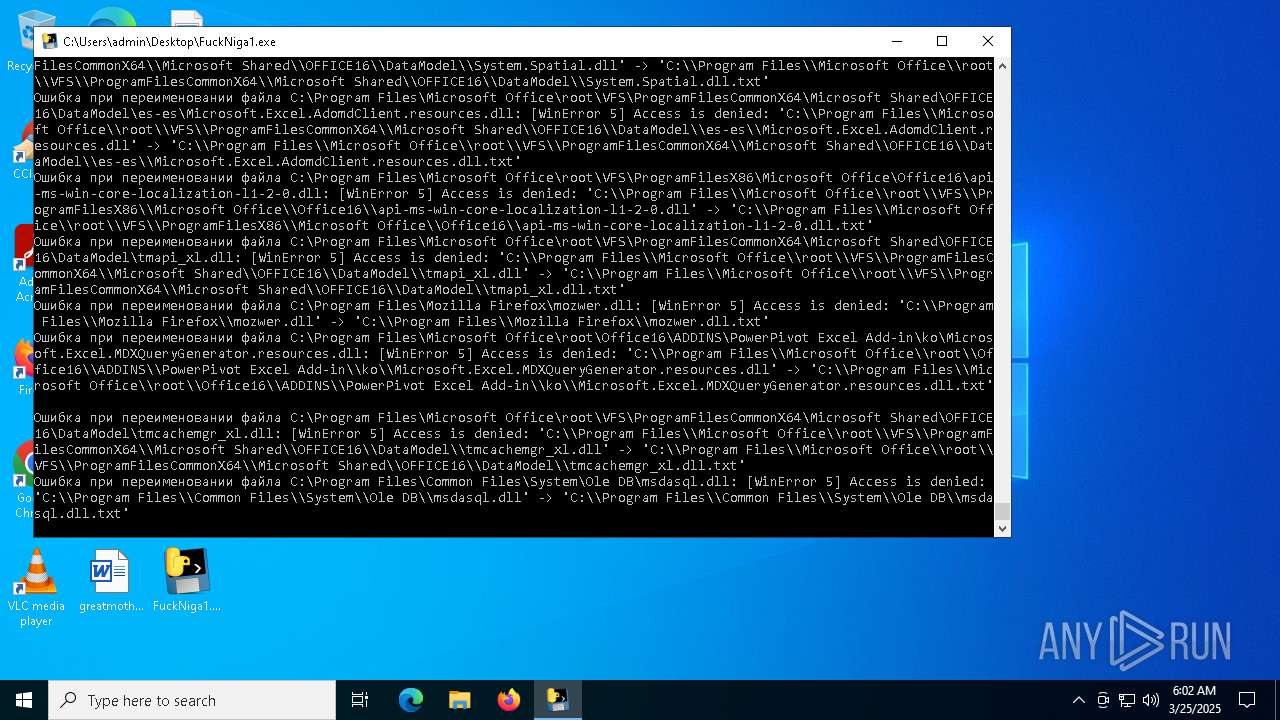
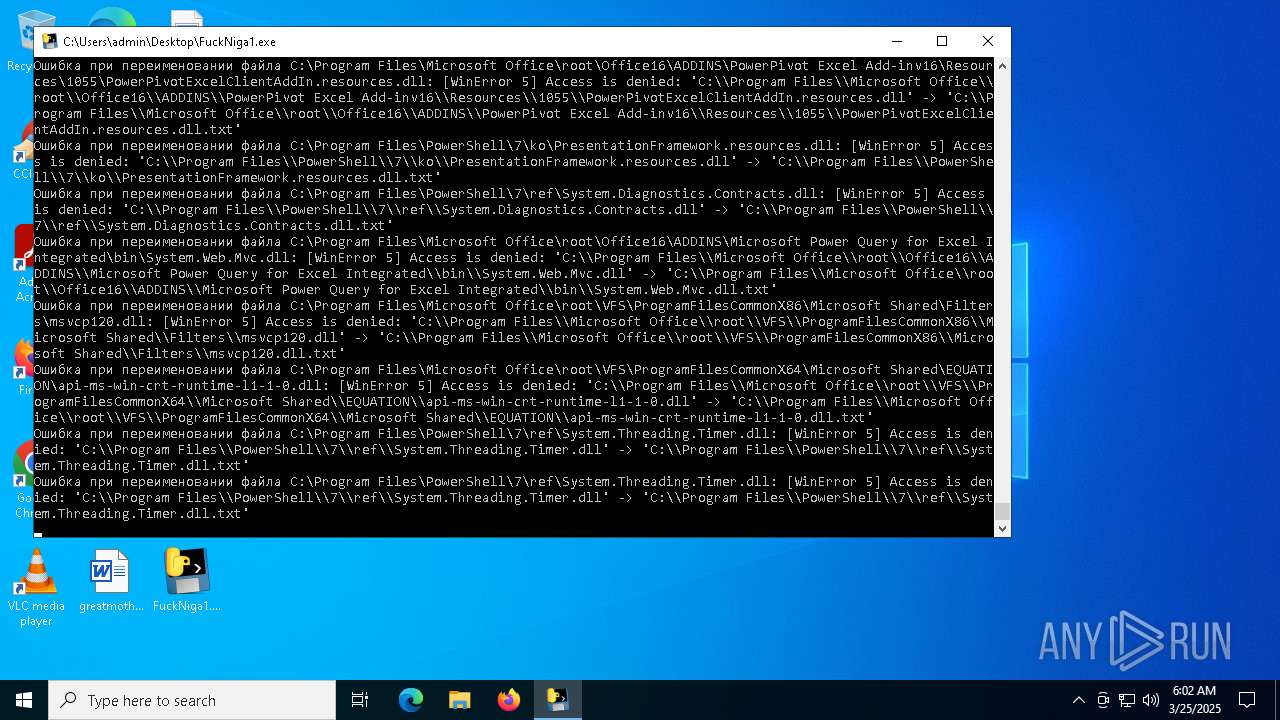
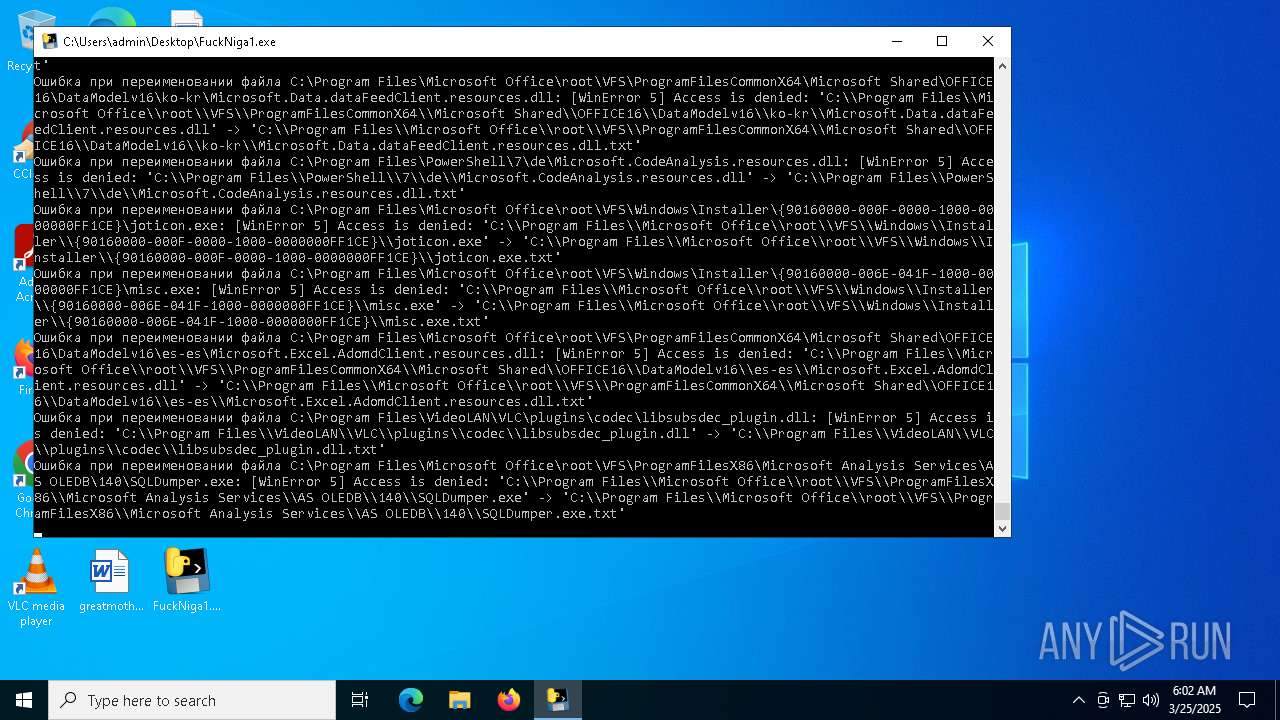
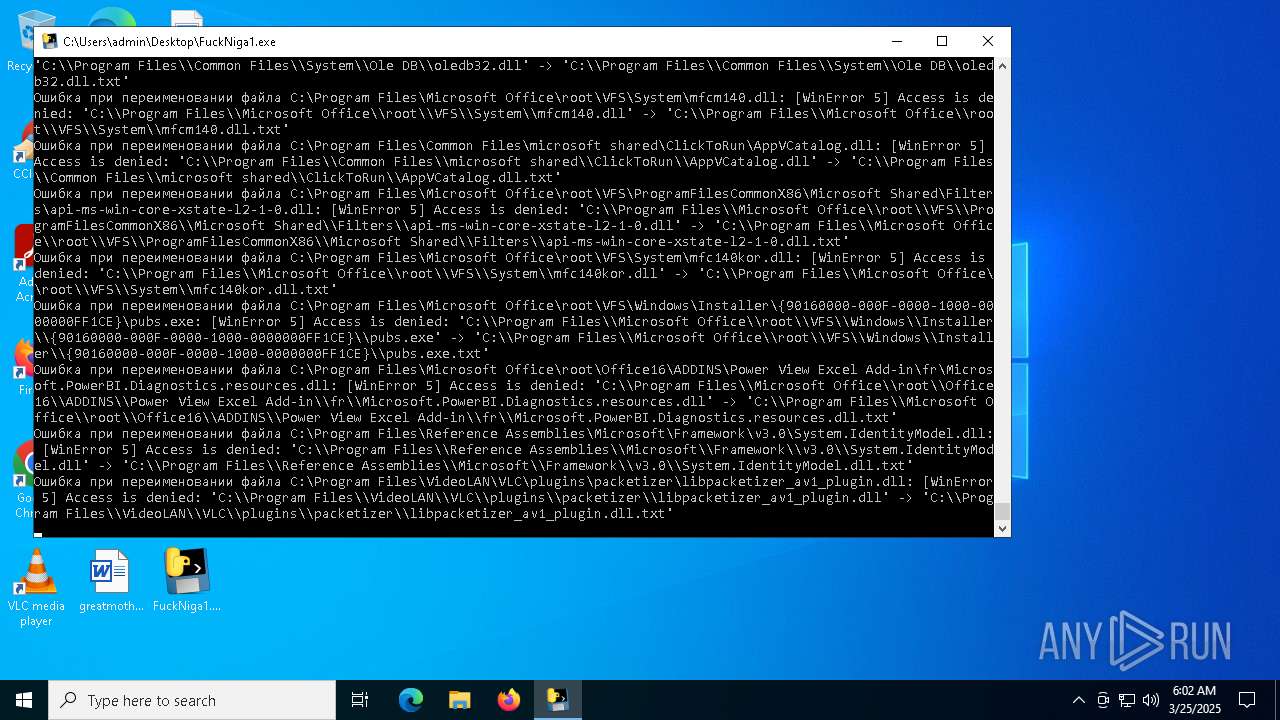
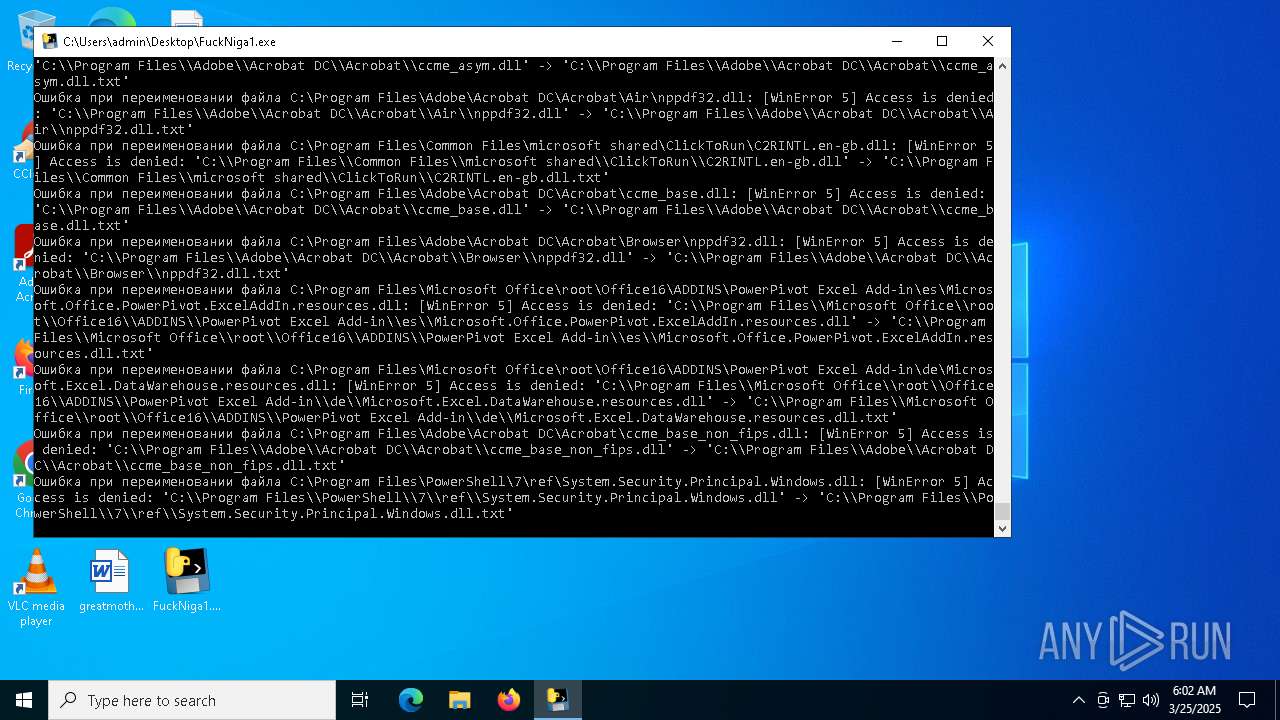
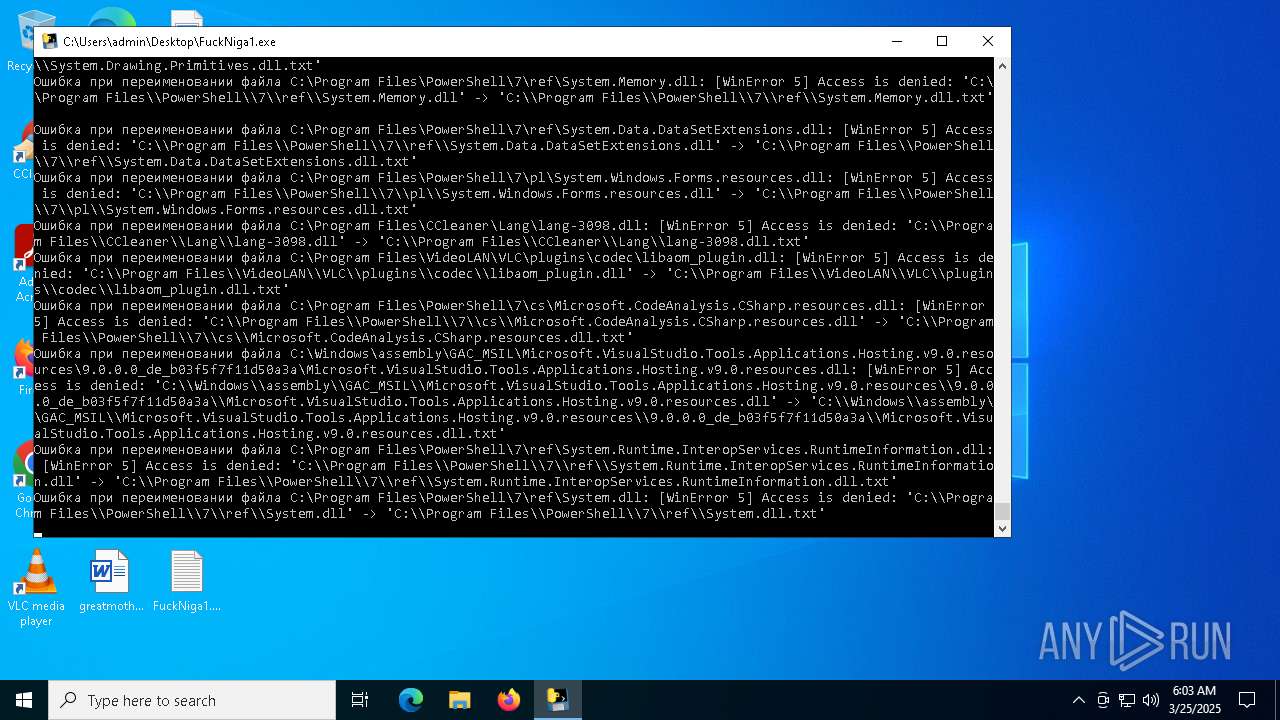
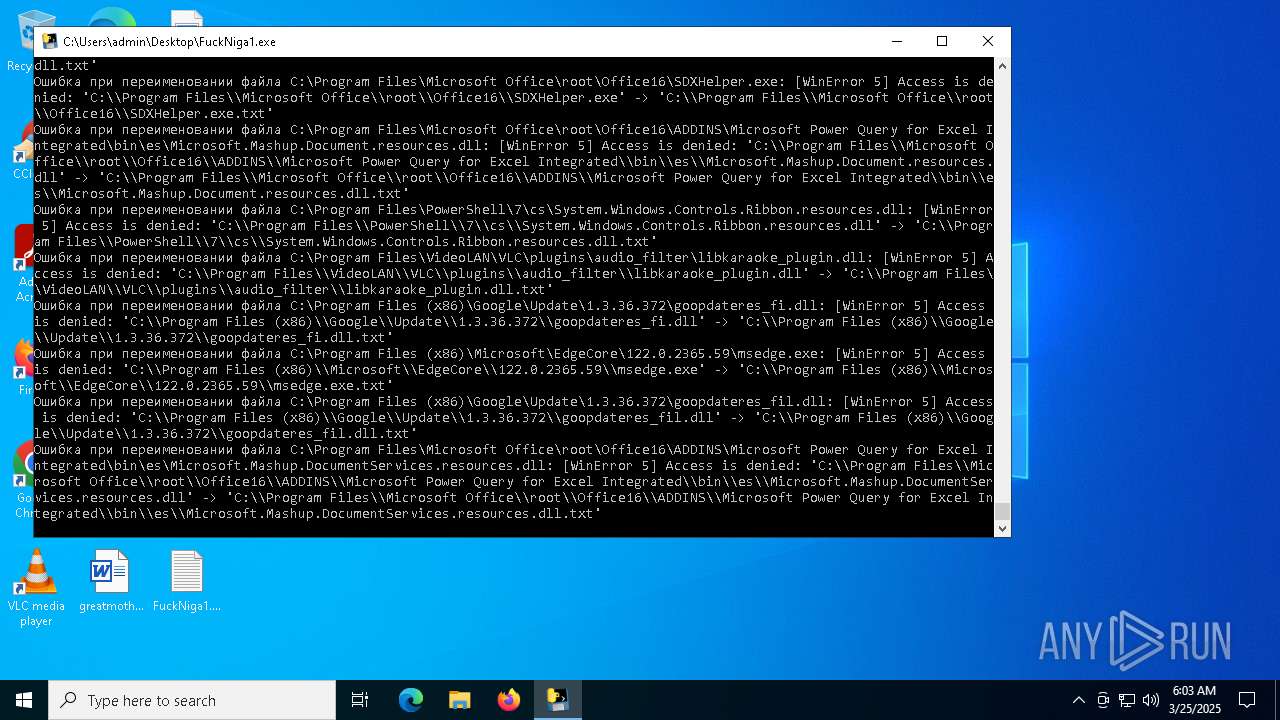
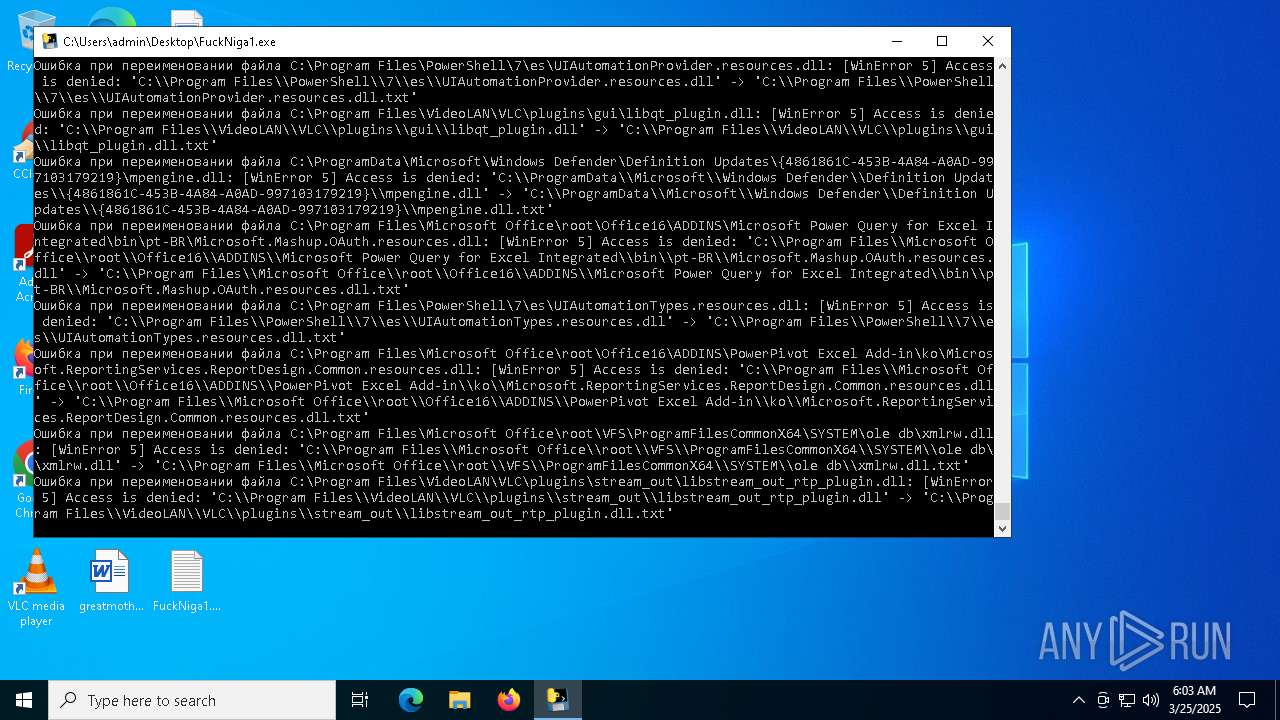
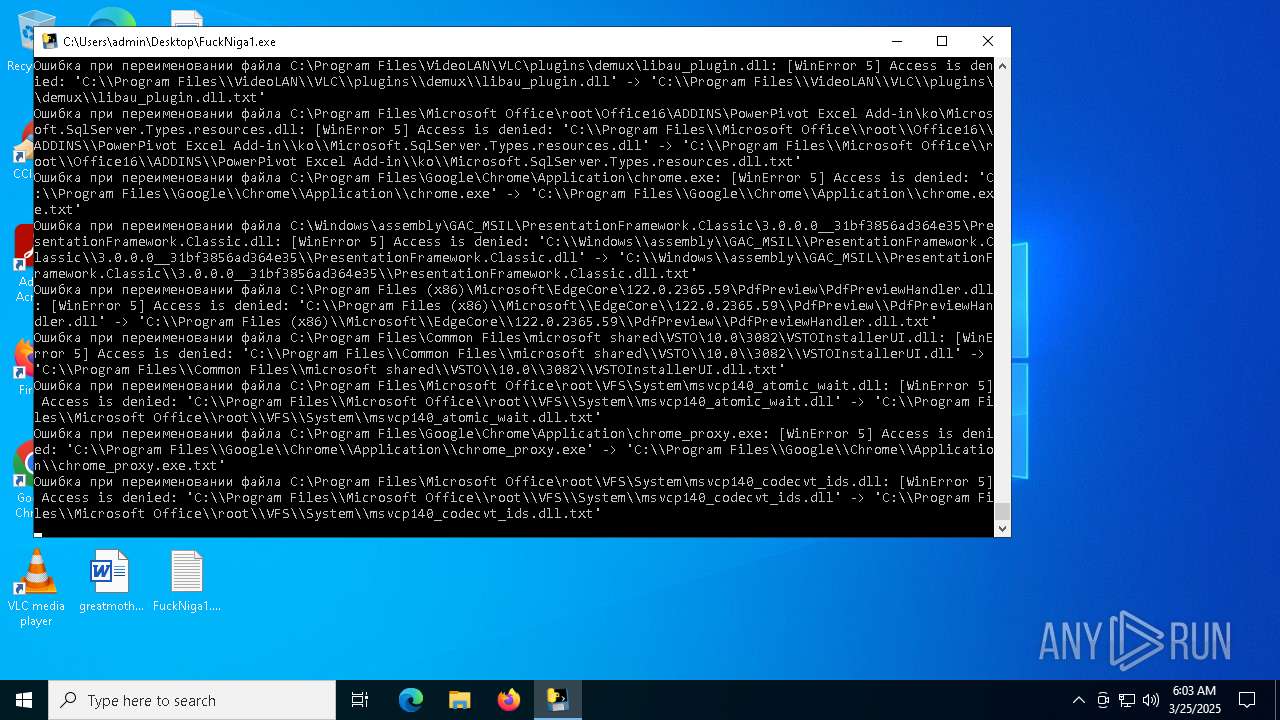
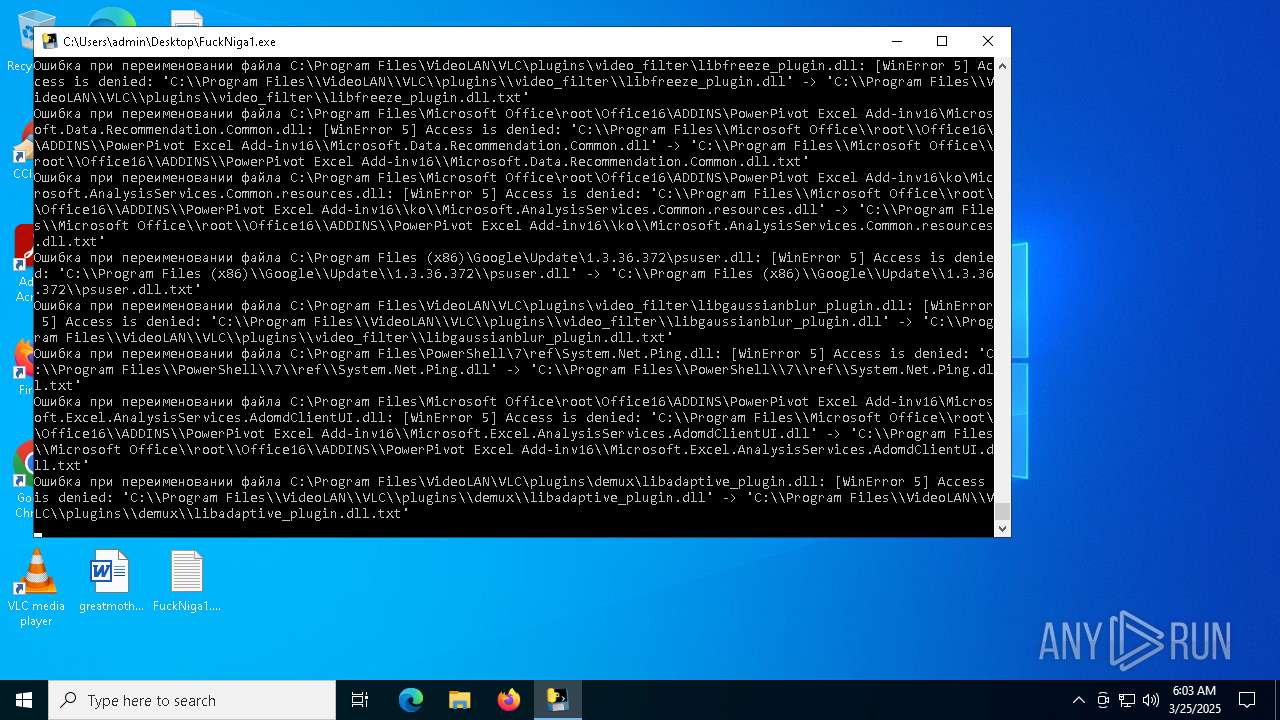
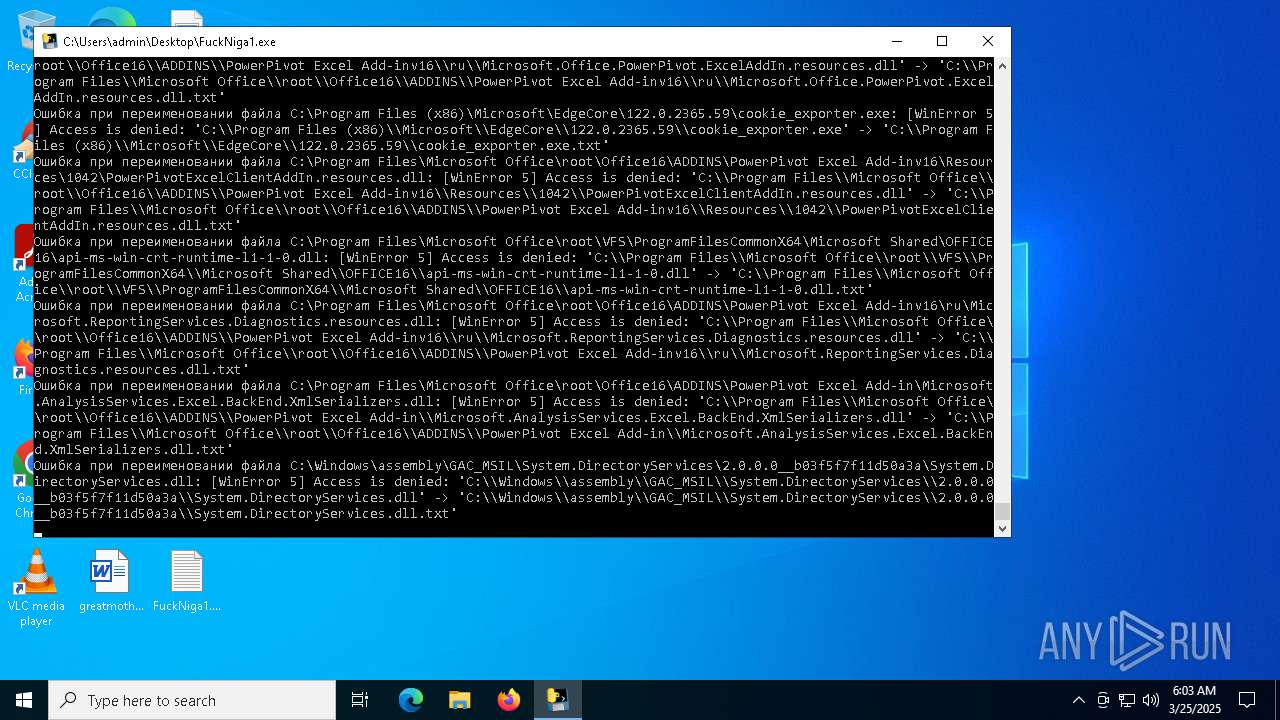
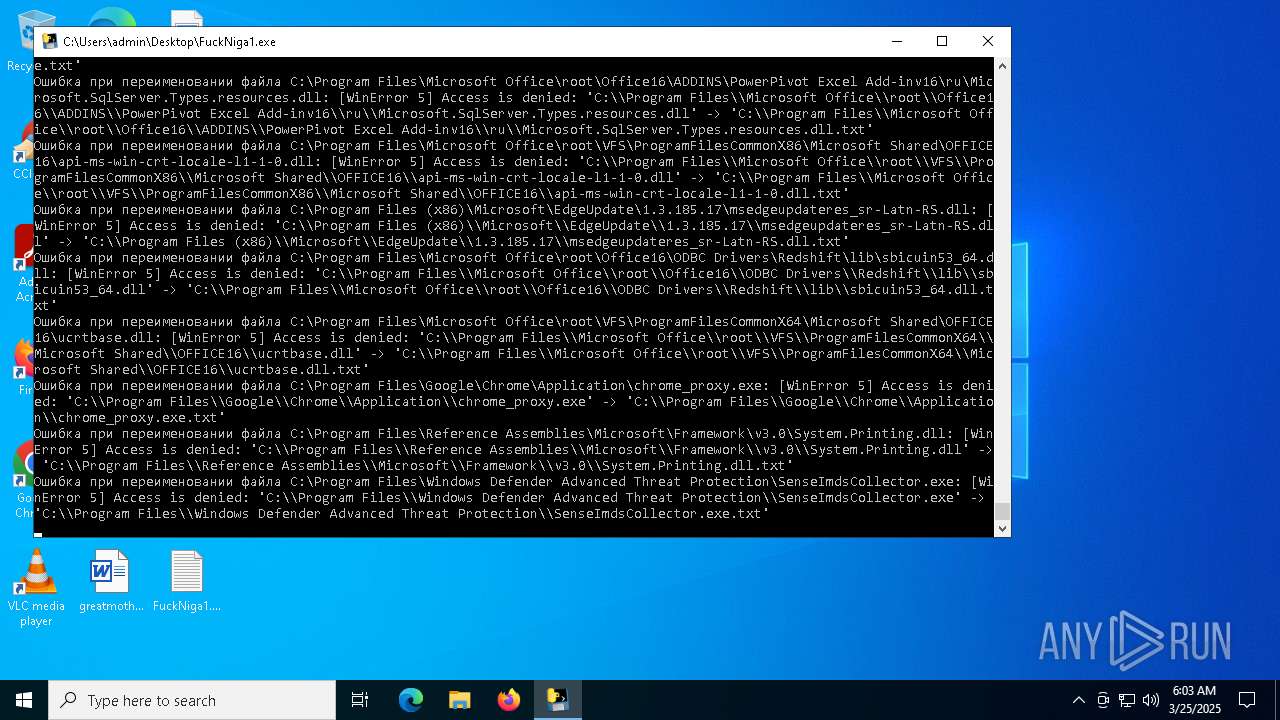
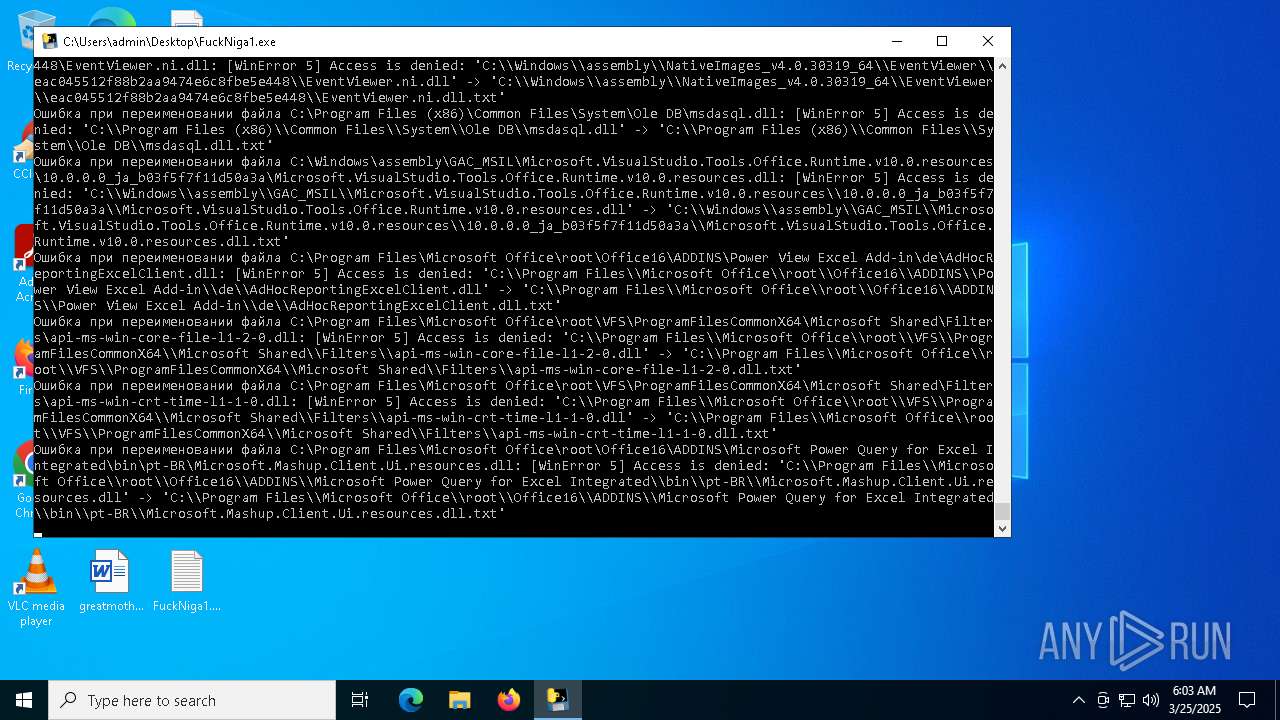
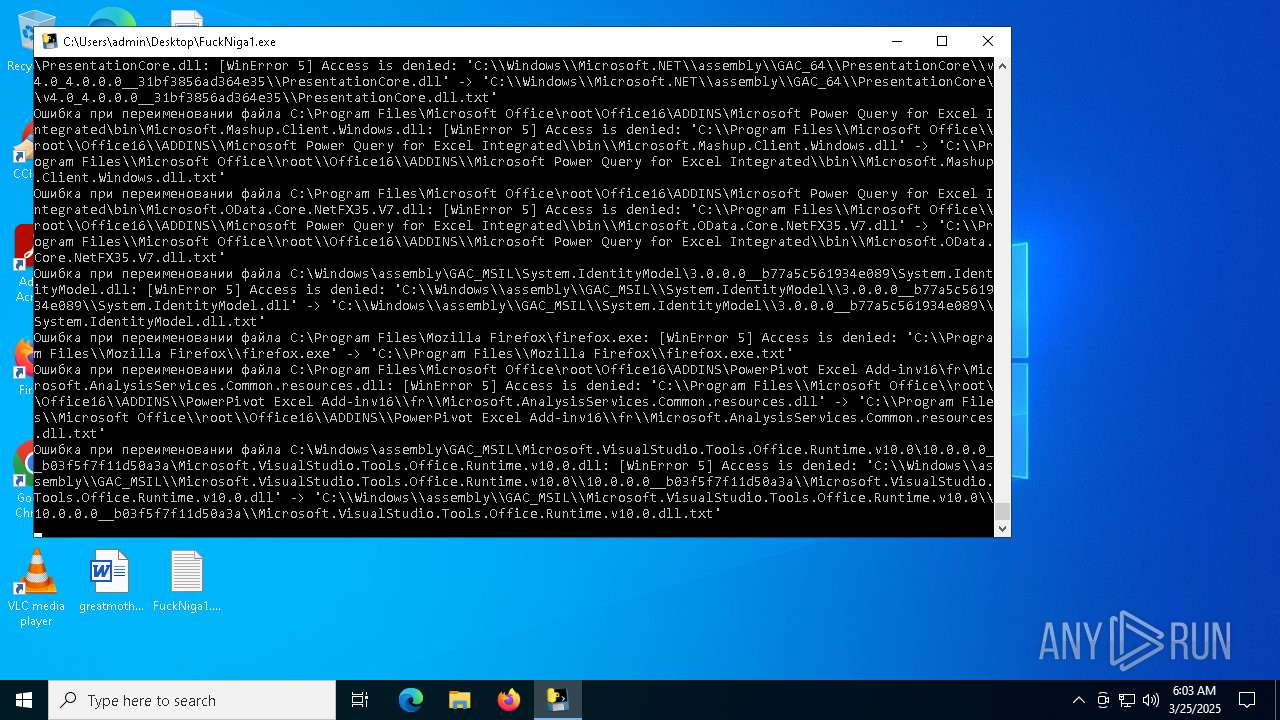
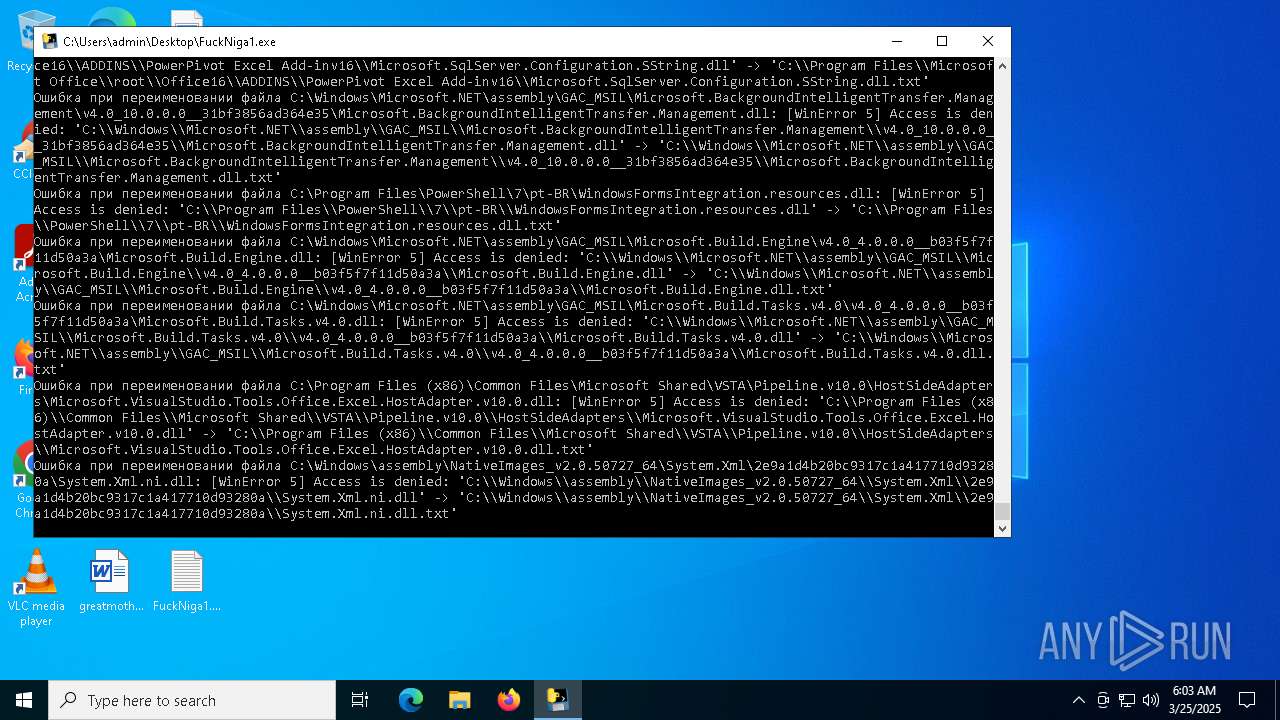
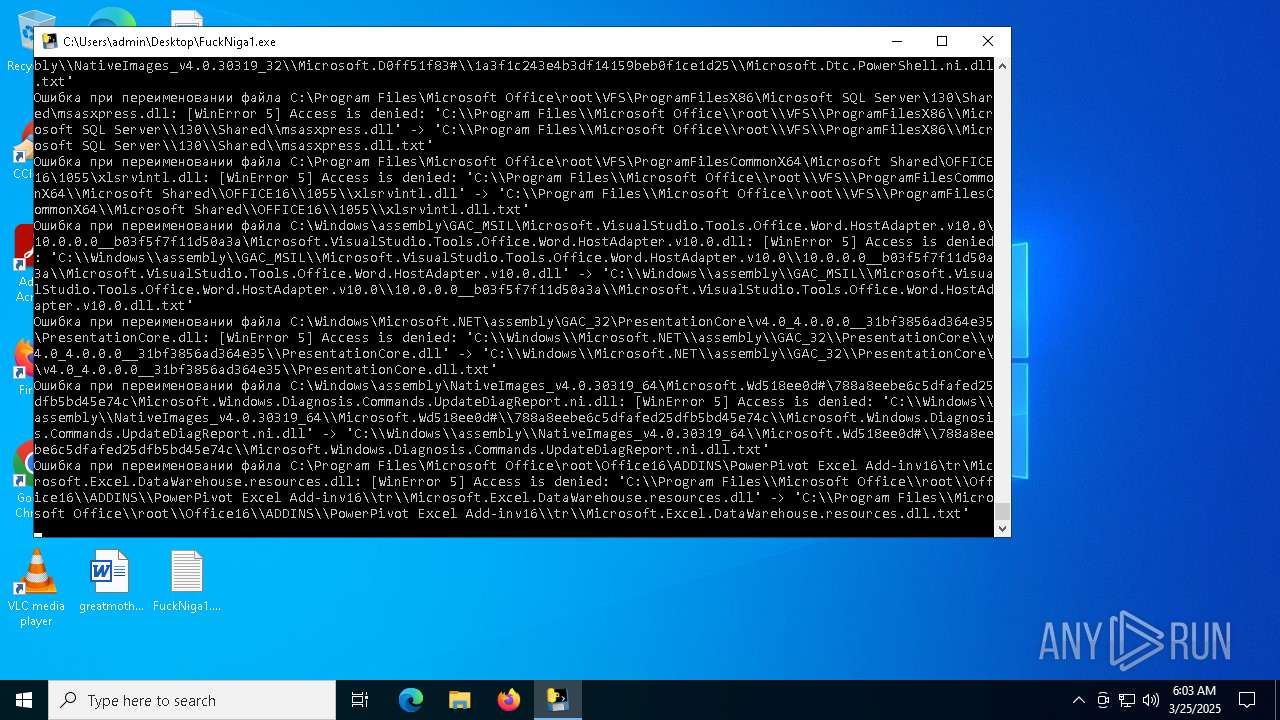
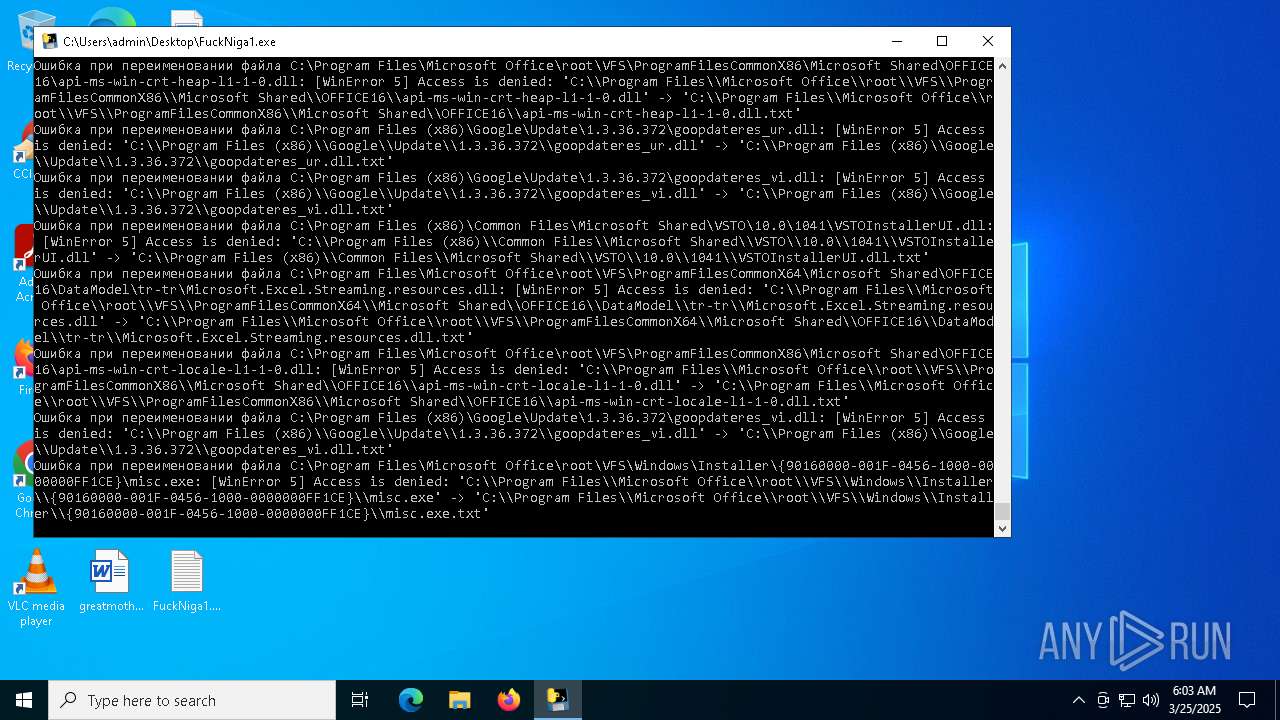
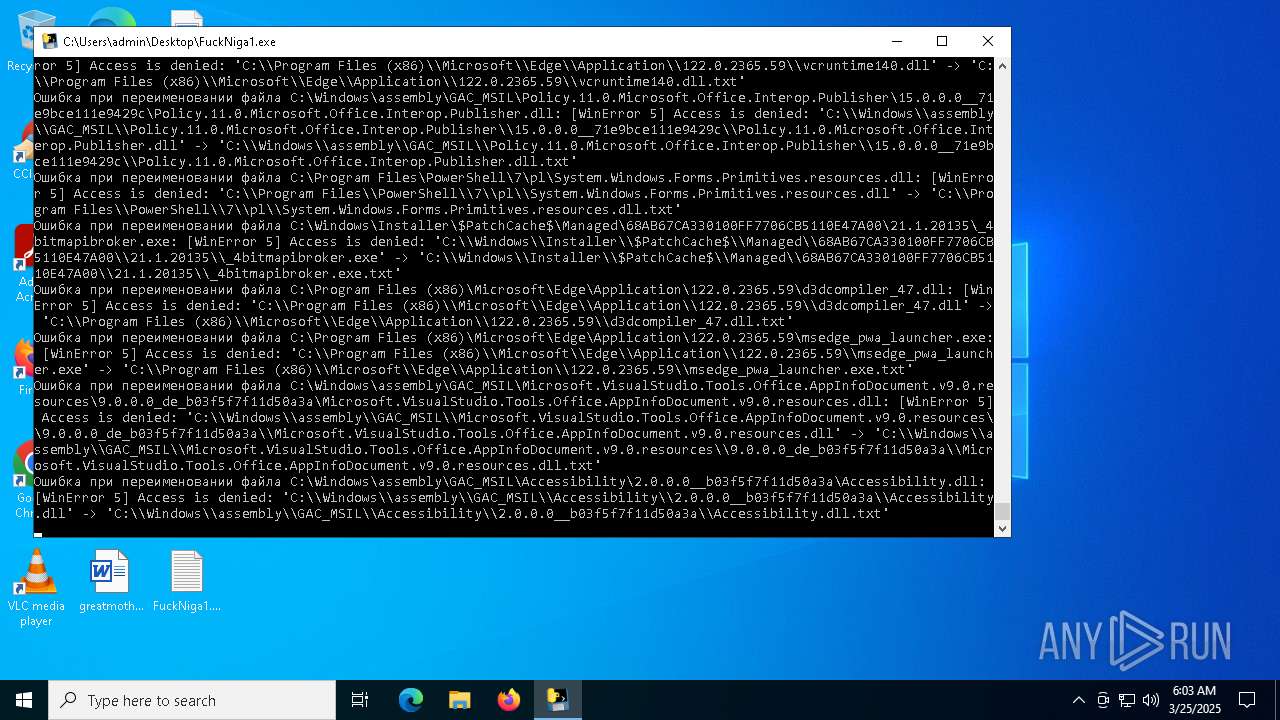
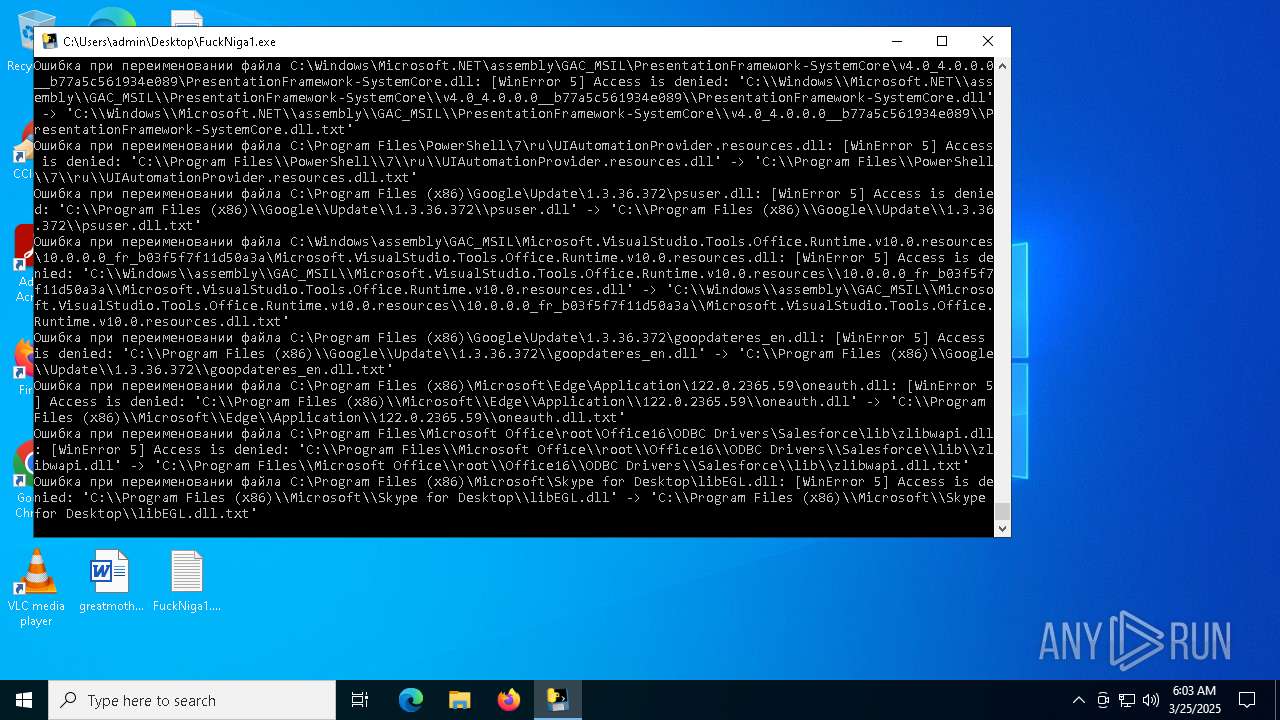
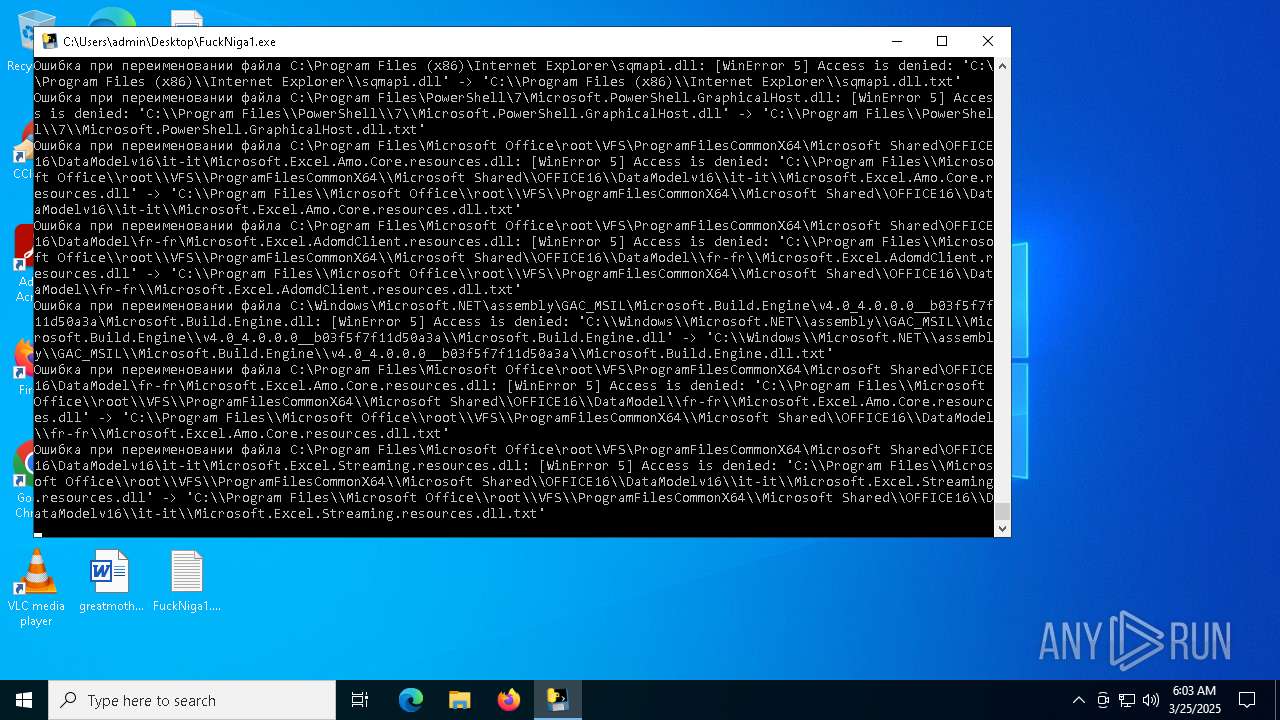
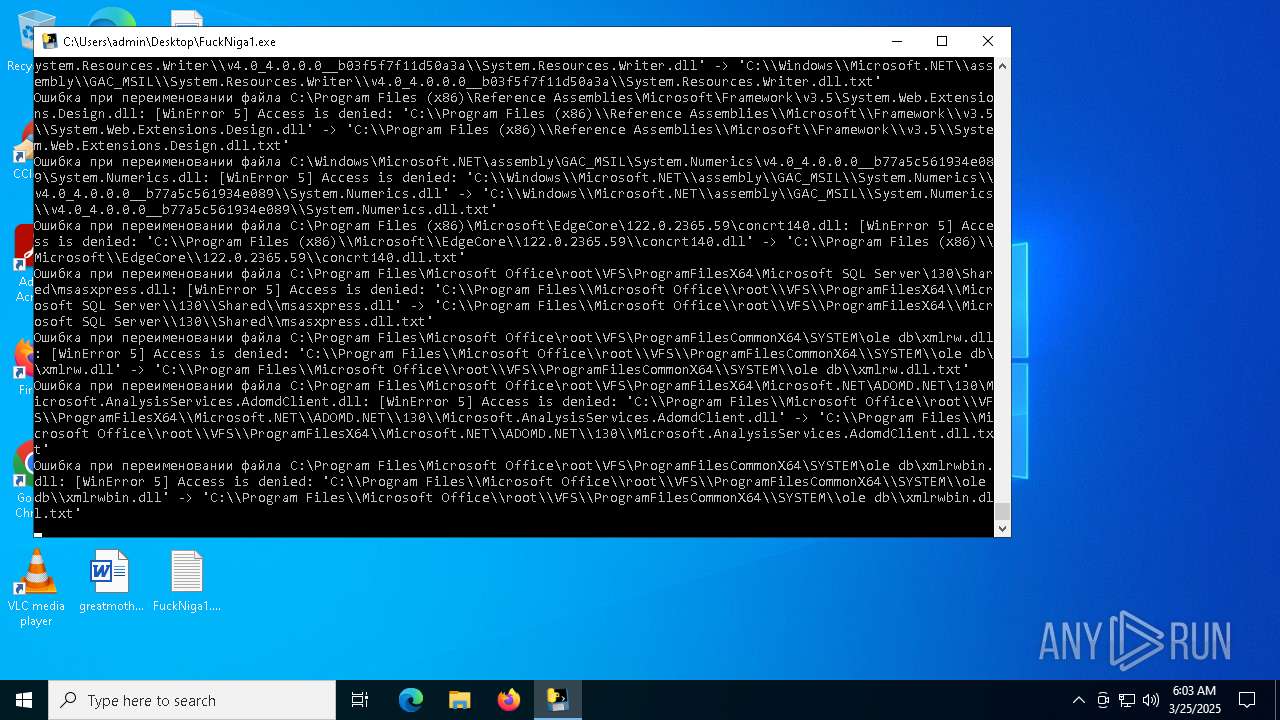
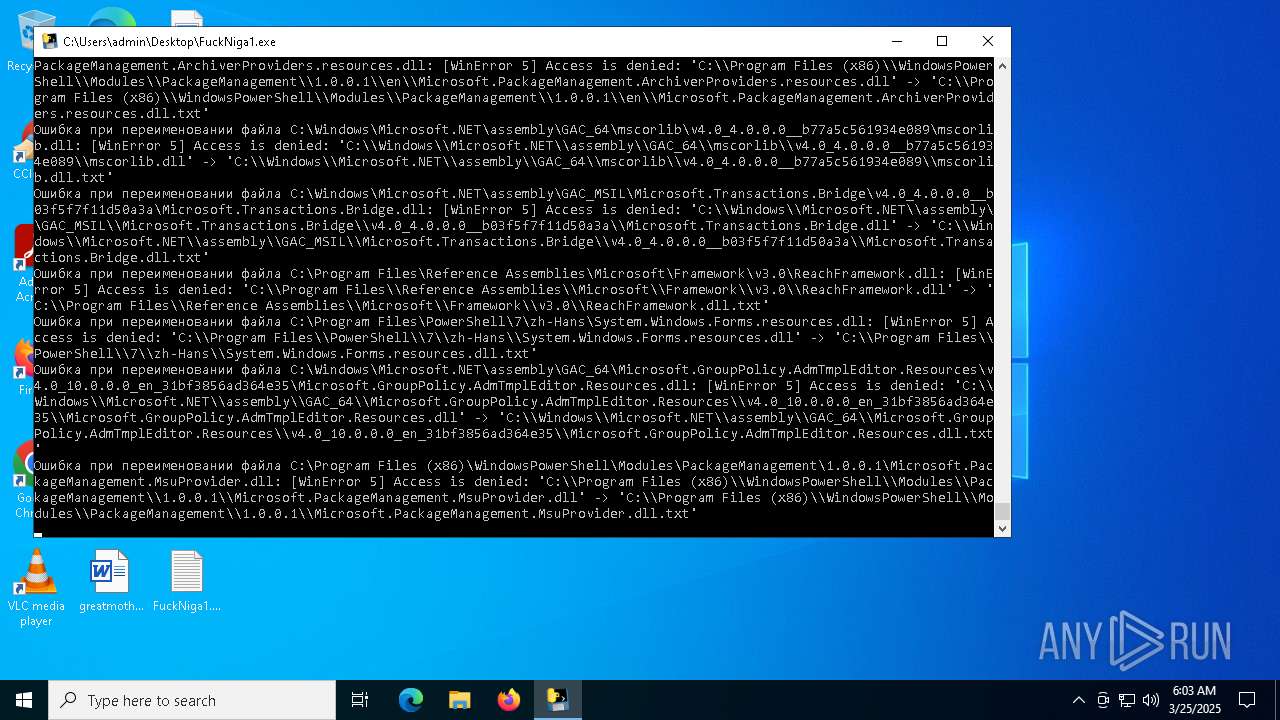
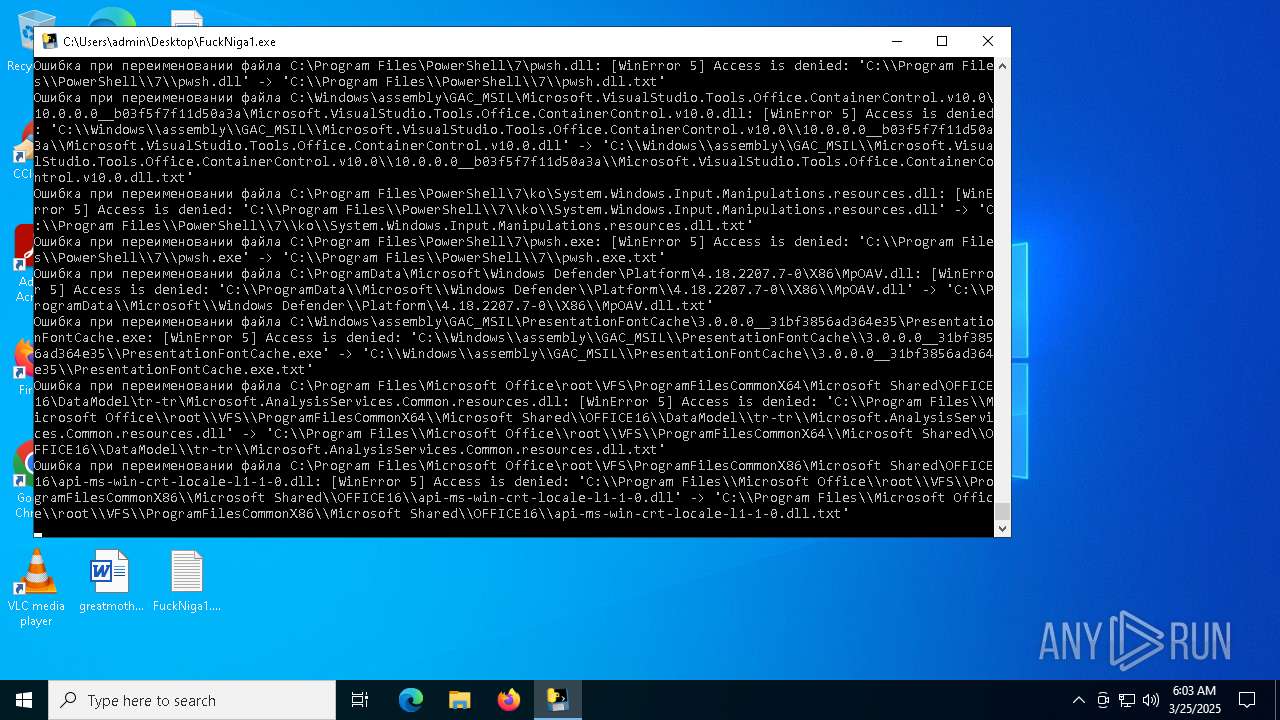
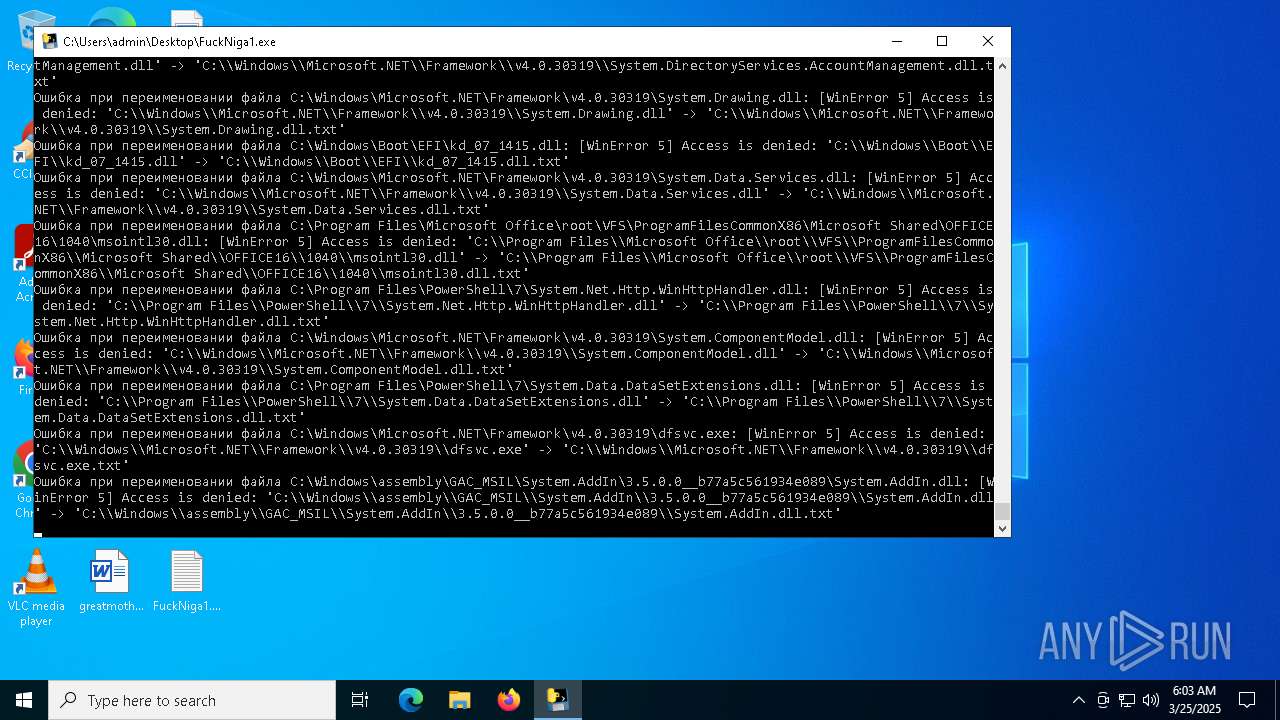
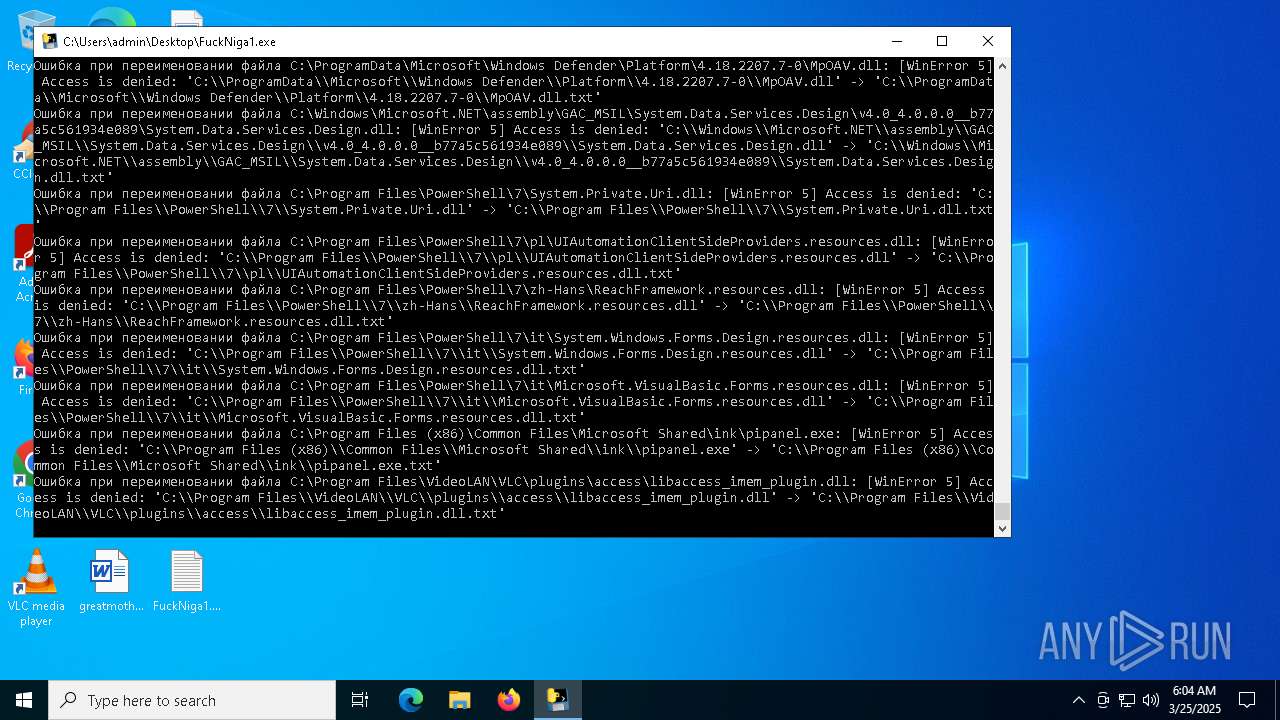
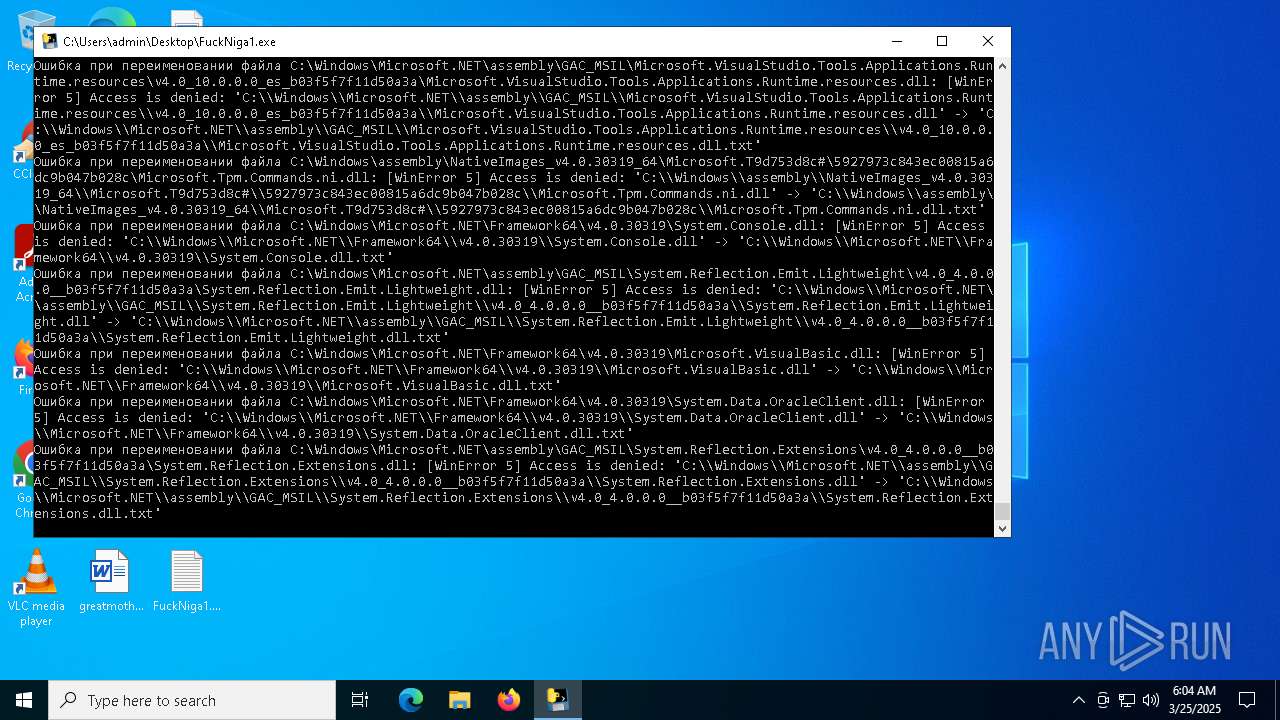
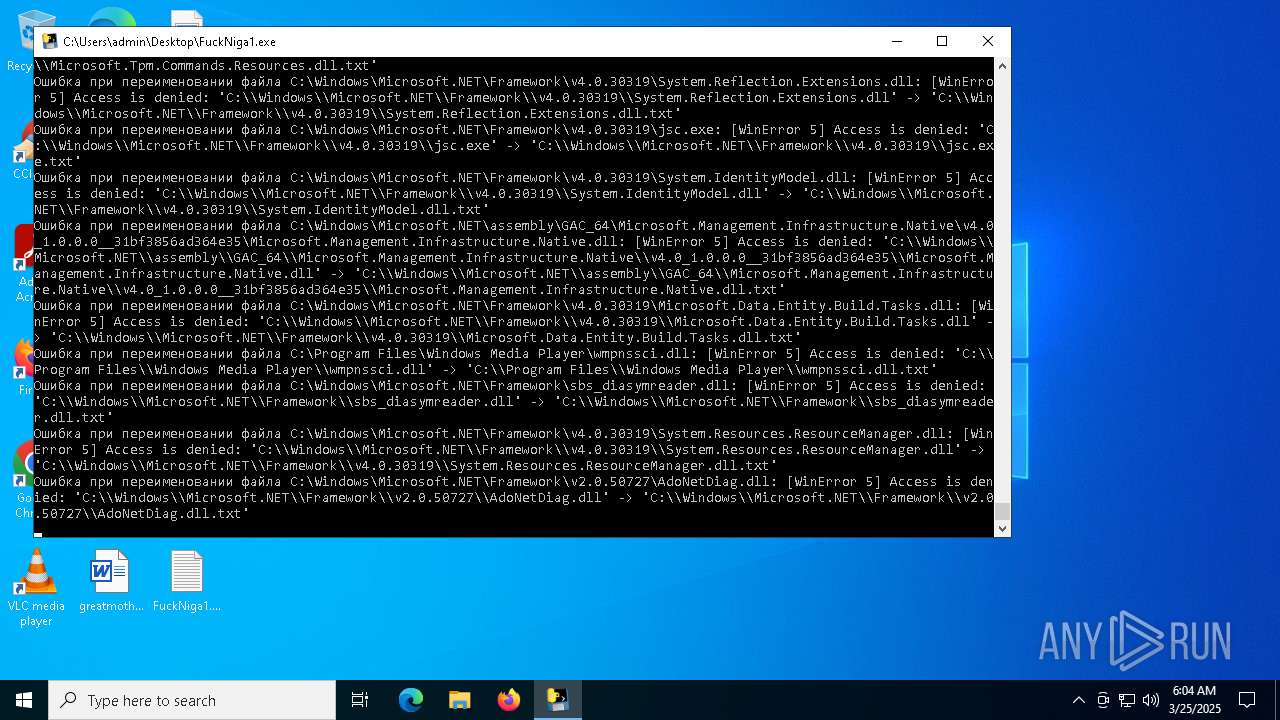
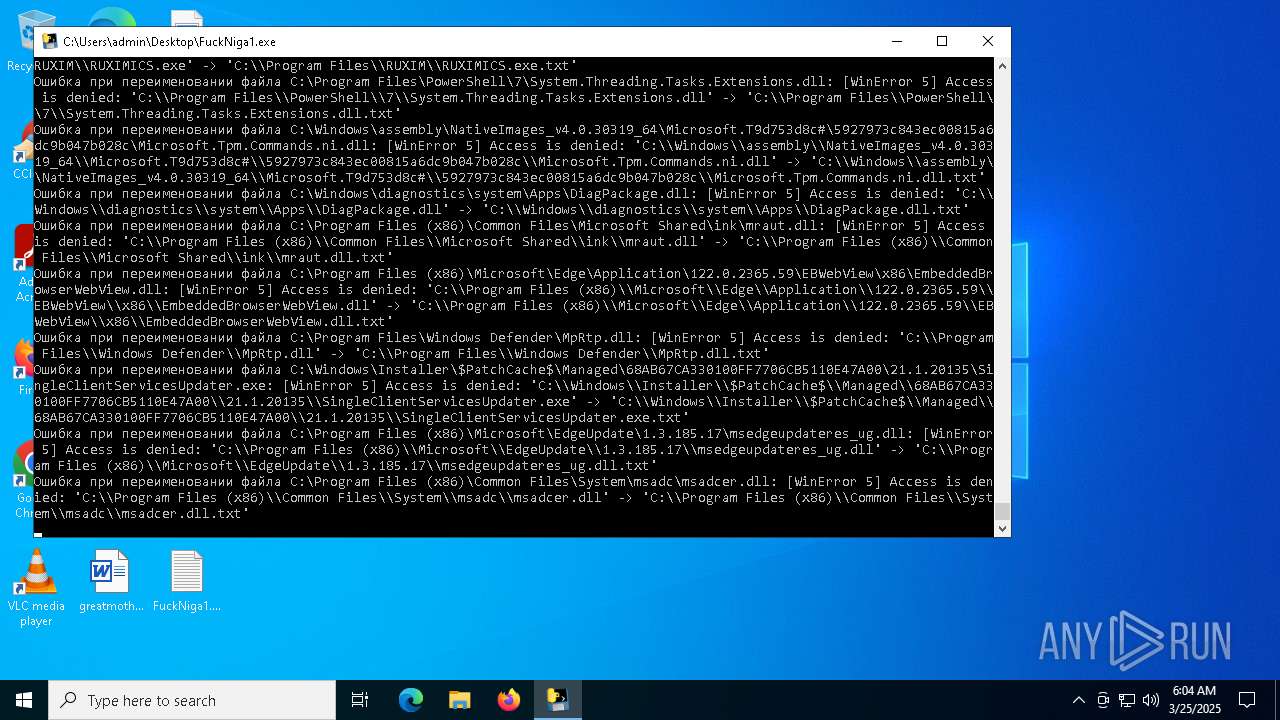
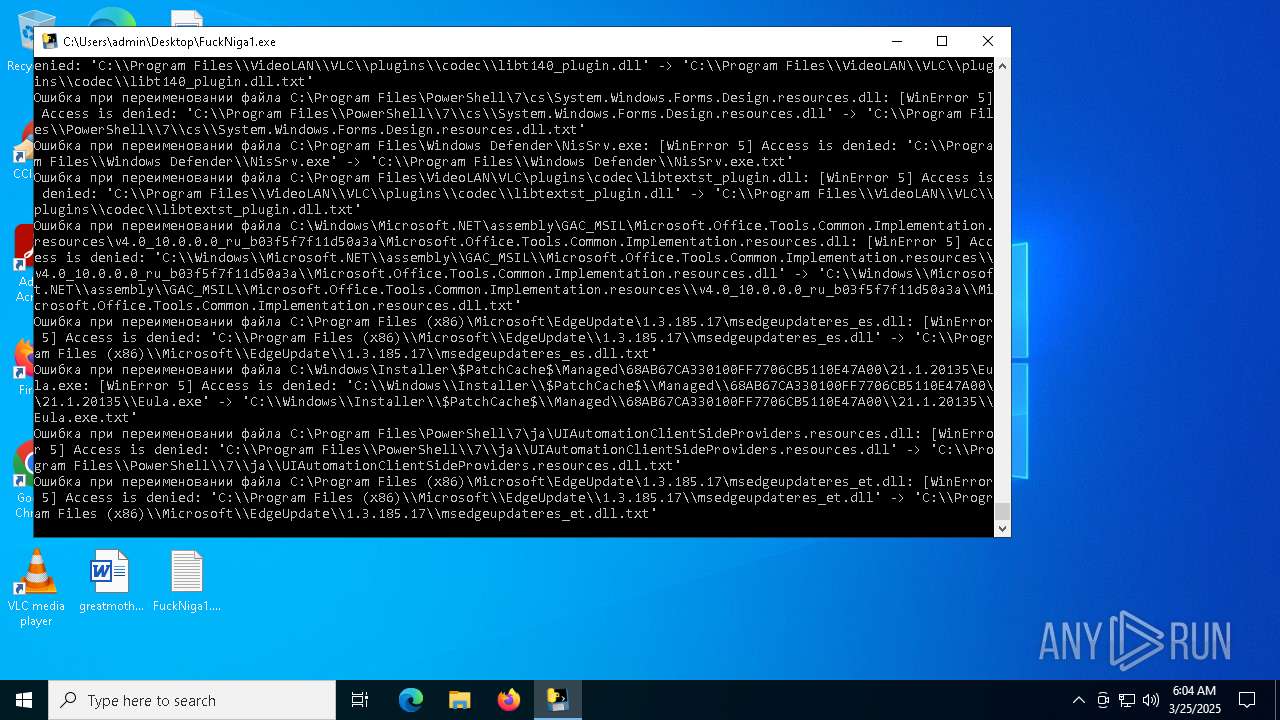
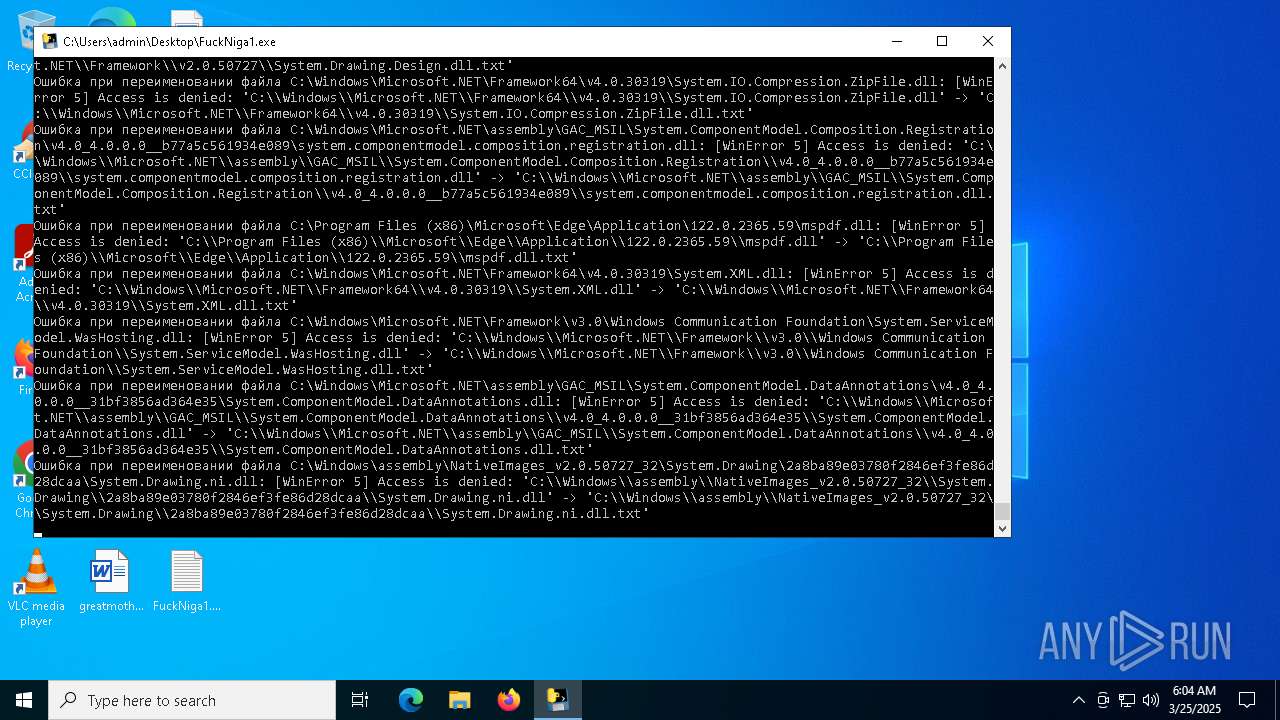
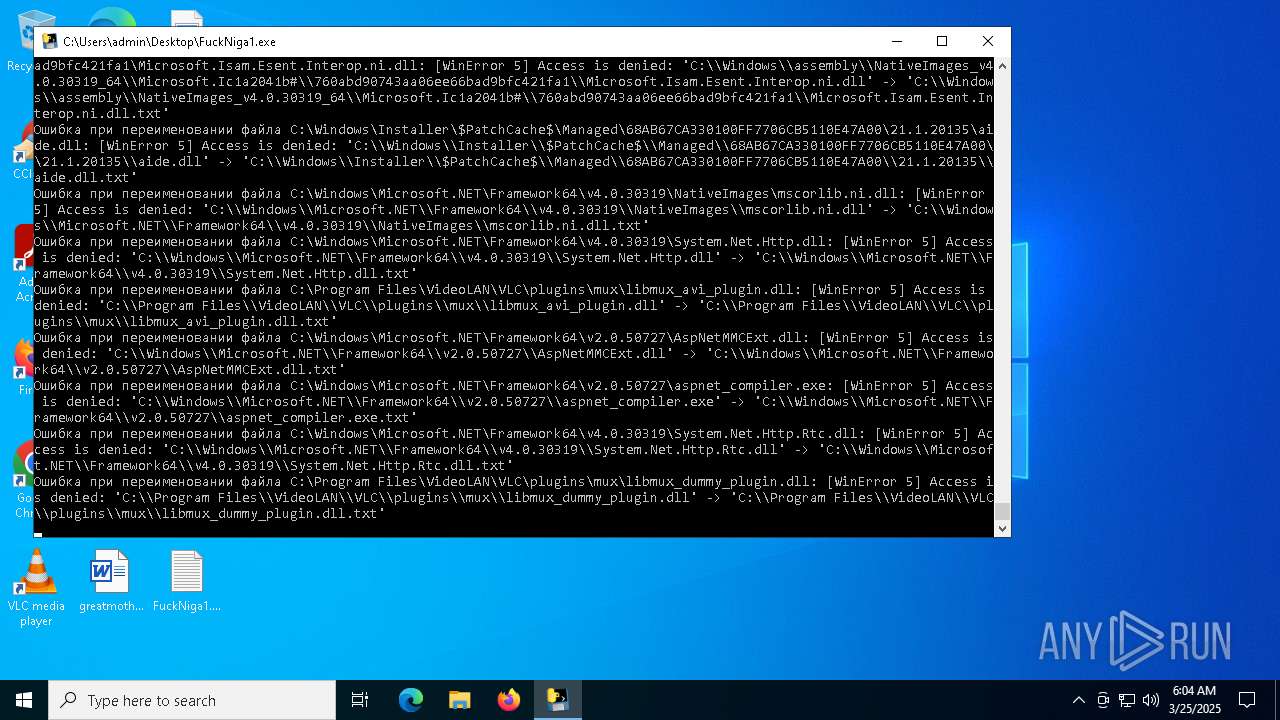
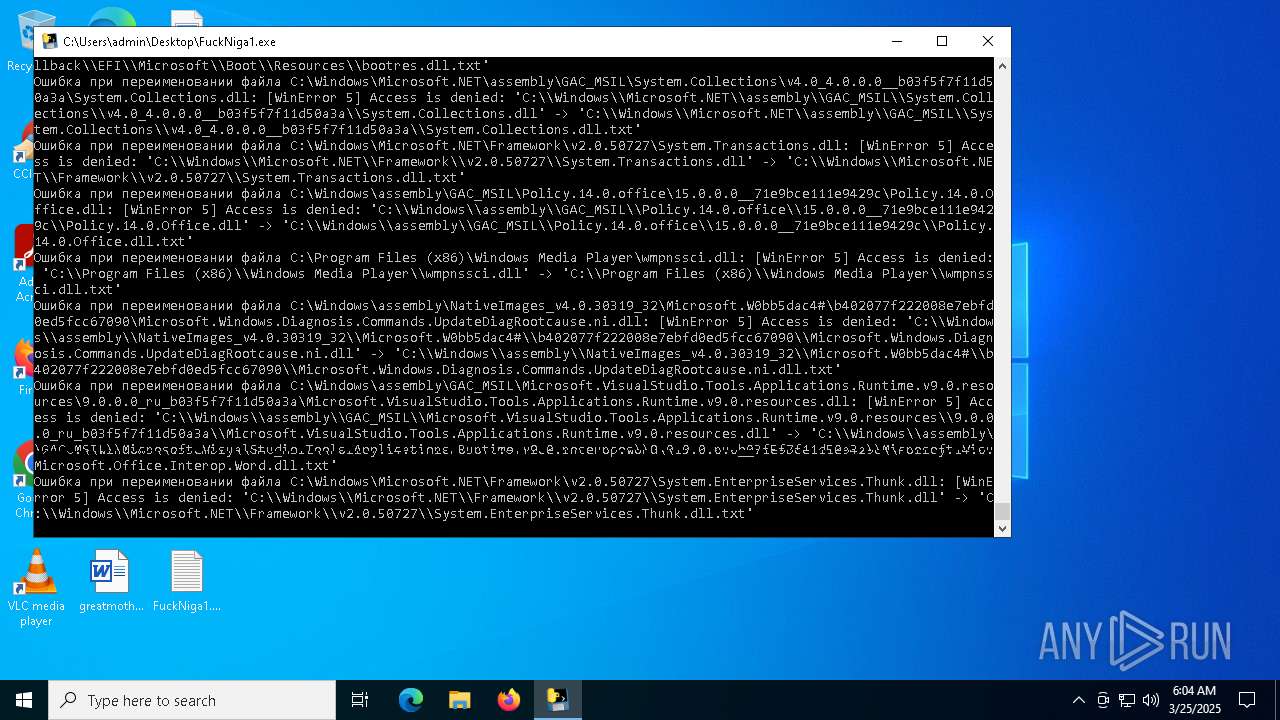
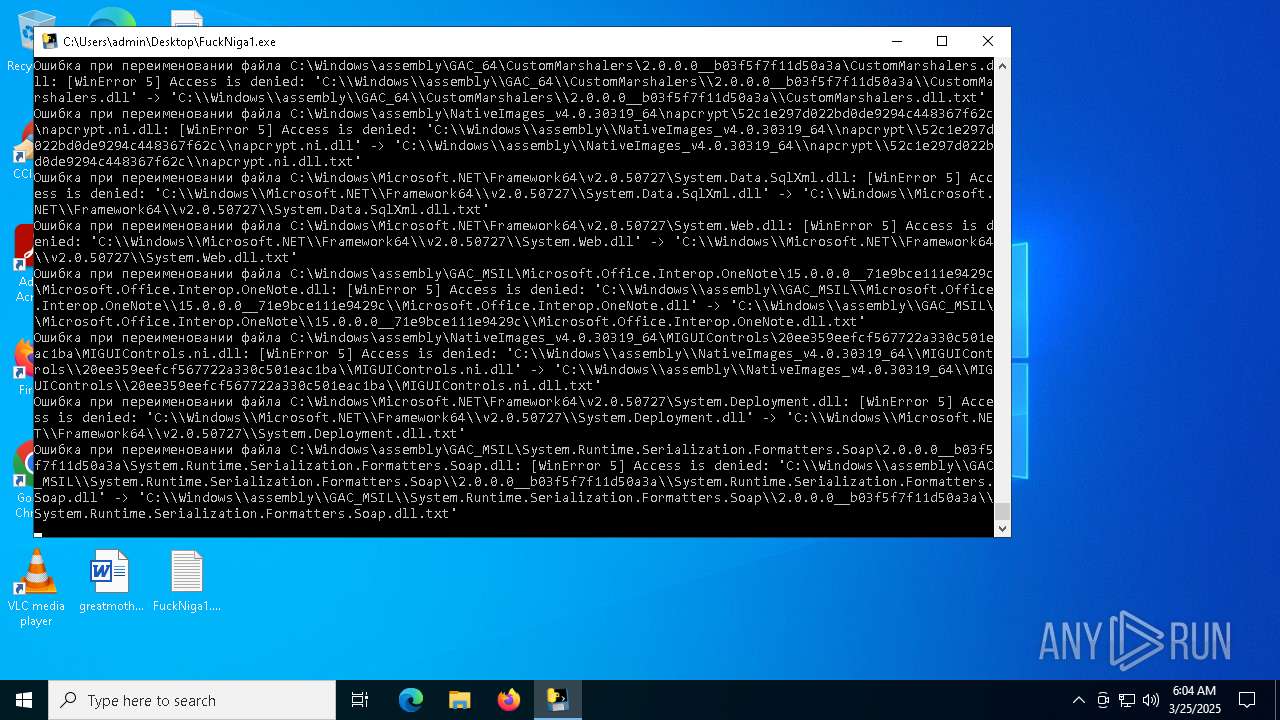
| File name: | FuckNiga1.exe |
| Full analysis: | https://app.any.run/tasks/12310a07-990a-4d6d-b913-23b741e30e75 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 06:02:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 7B8D9A0CAA9E7F30965F36CDB11C53BA |
| SHA1: | 8694DAB6B2D163C227133CE72B6D4EA67C3BE761 |
| SHA256: | 2082FB5DC6DED791901A71BCB9DA9EFABA3AF4CB16B96B53A764D1FDA49A2FA0 |
| SSDEEP: | 98304:eVIyDmgGmSyu4YJbebWn7CvlfaMh3pmV4CseEesQHc/kHqqHmRdoiLhrc0W6lpht:2OglOkmPf |
MALICIOUS
No malicious indicators.SUSPICIOUS
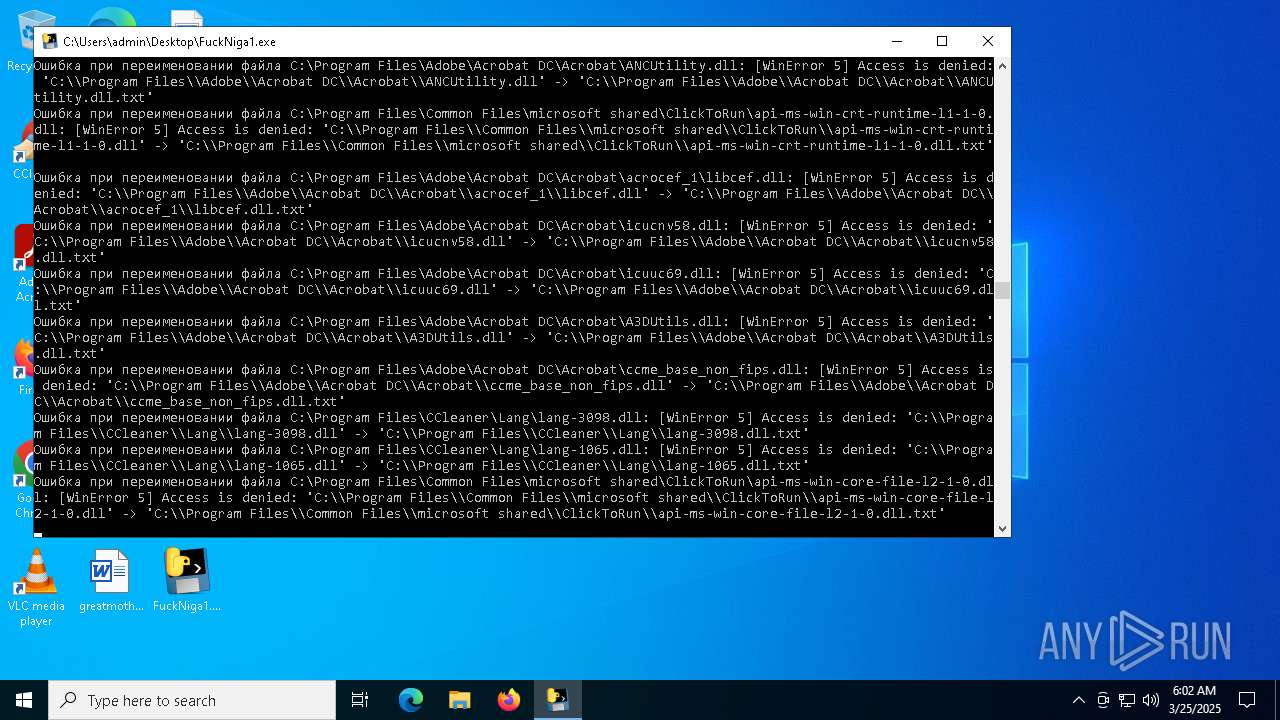
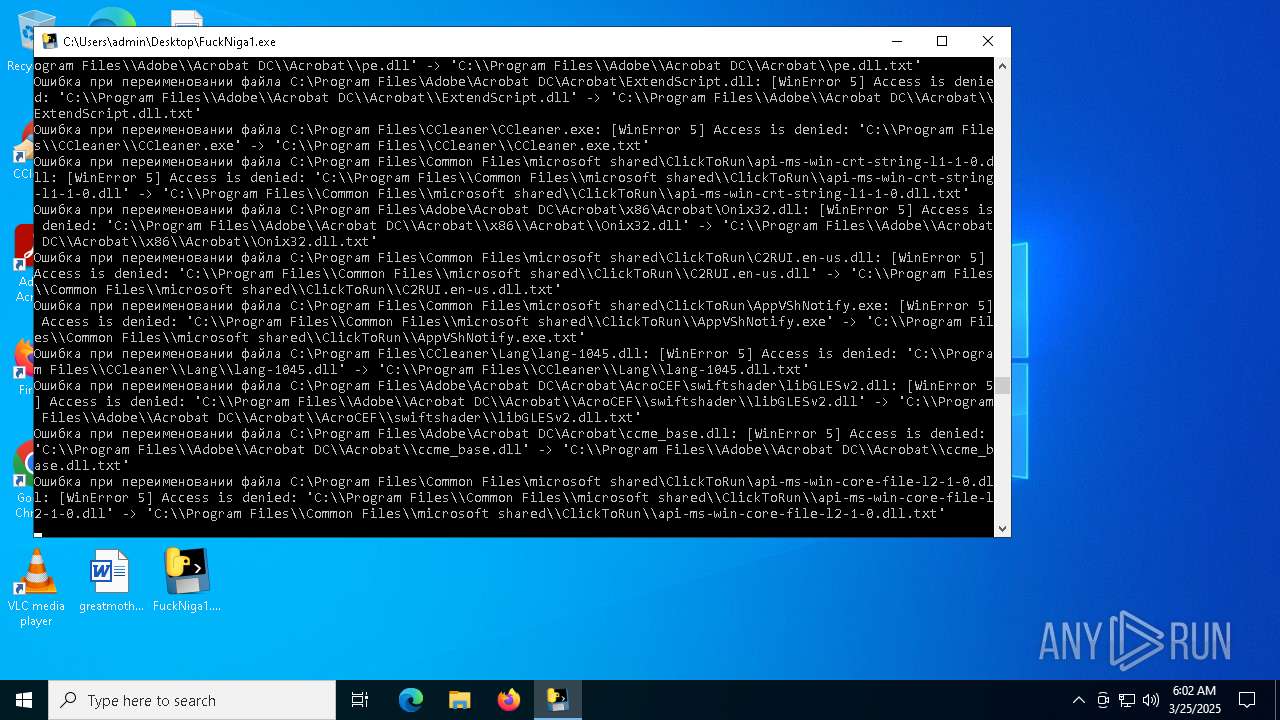
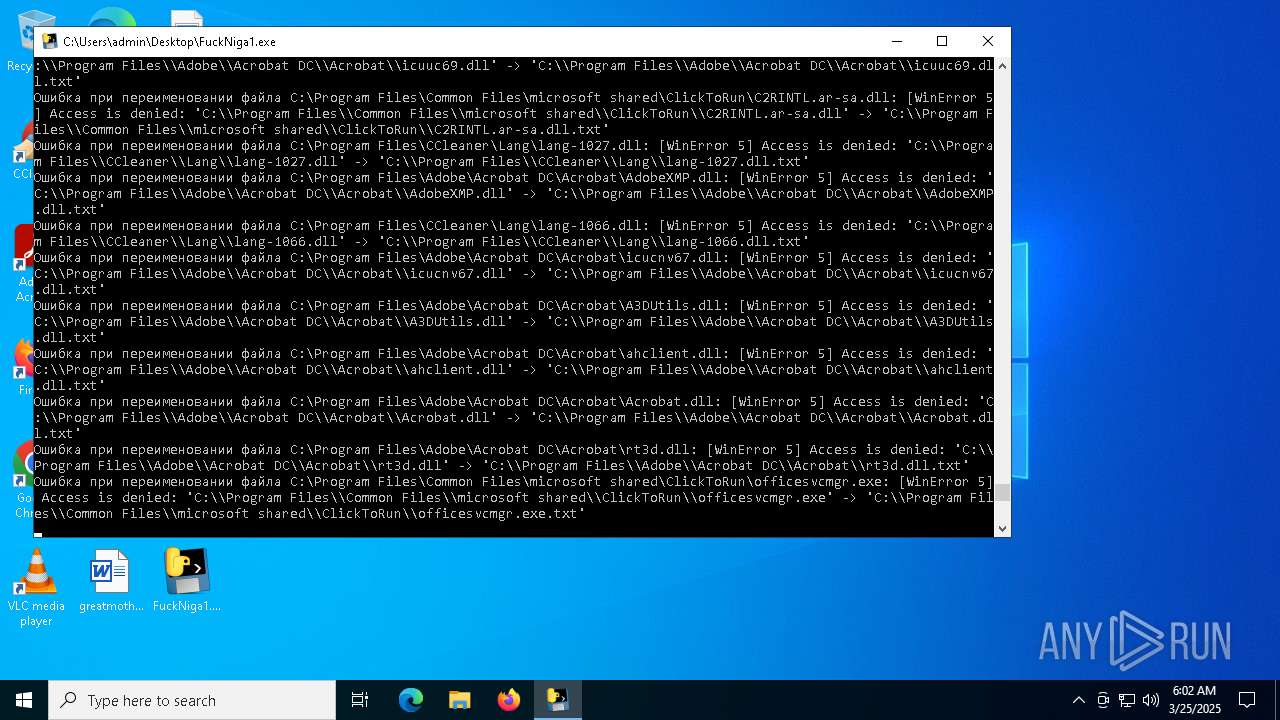
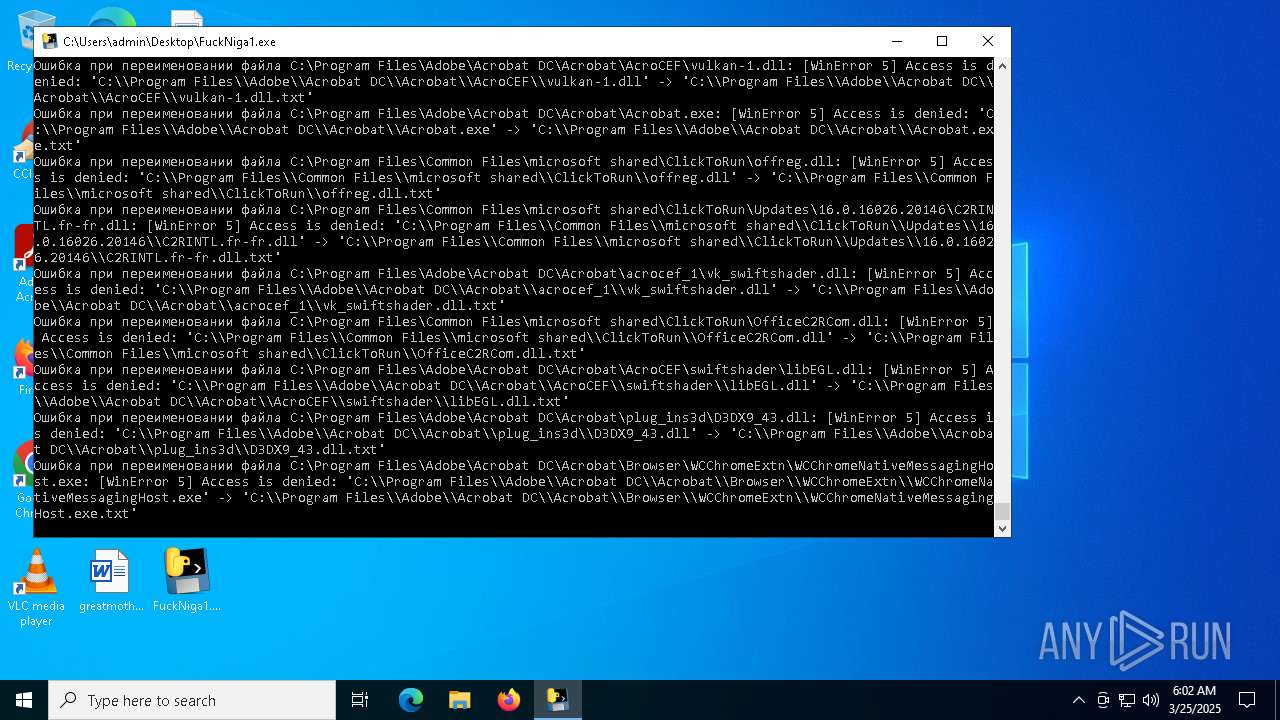
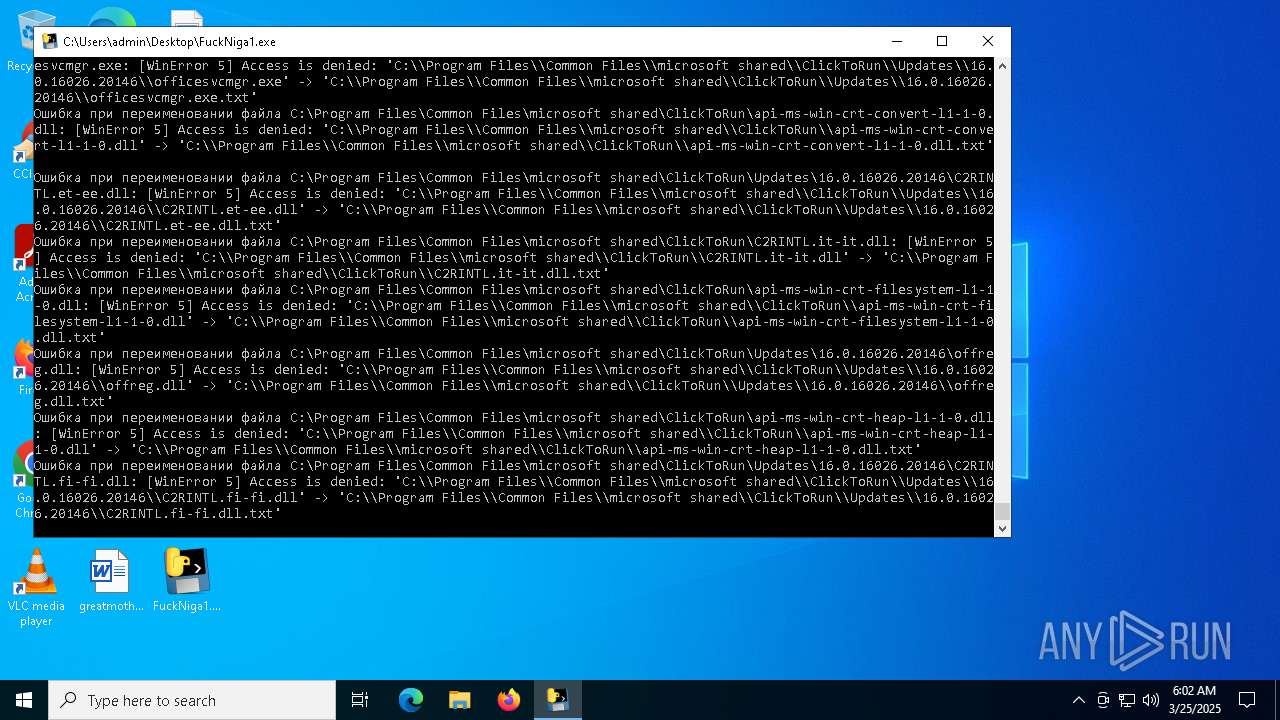
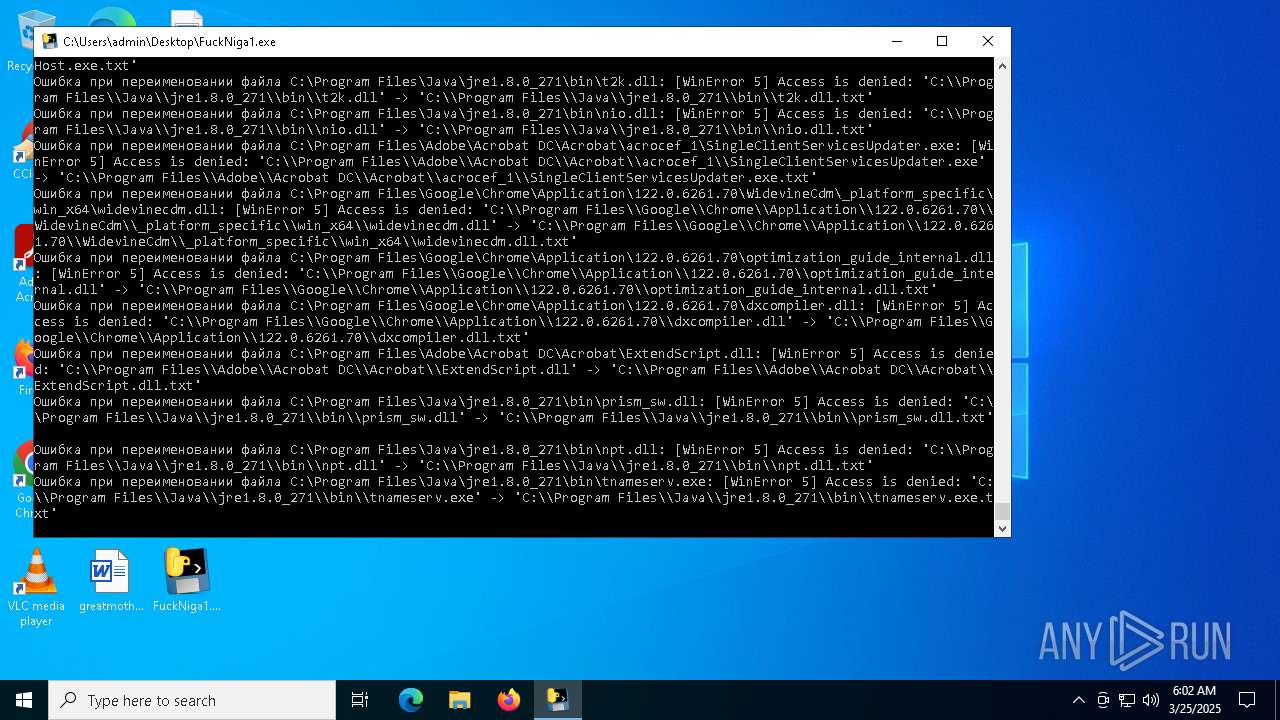
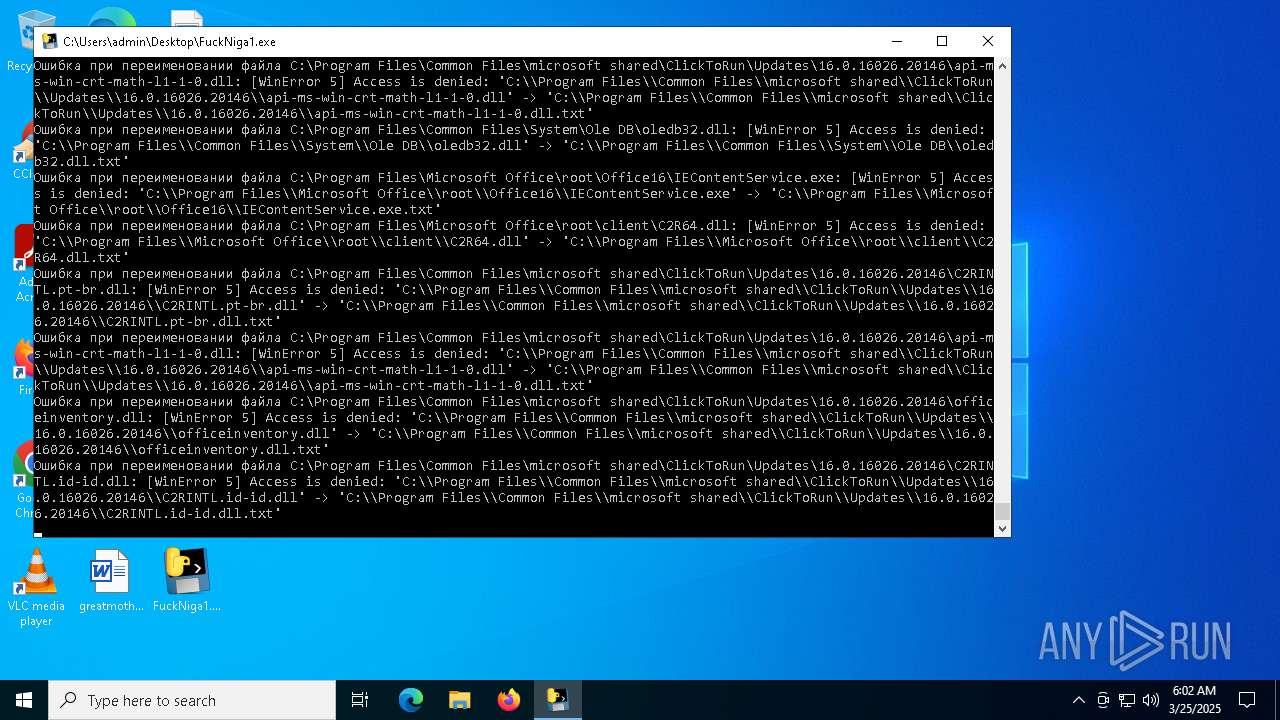
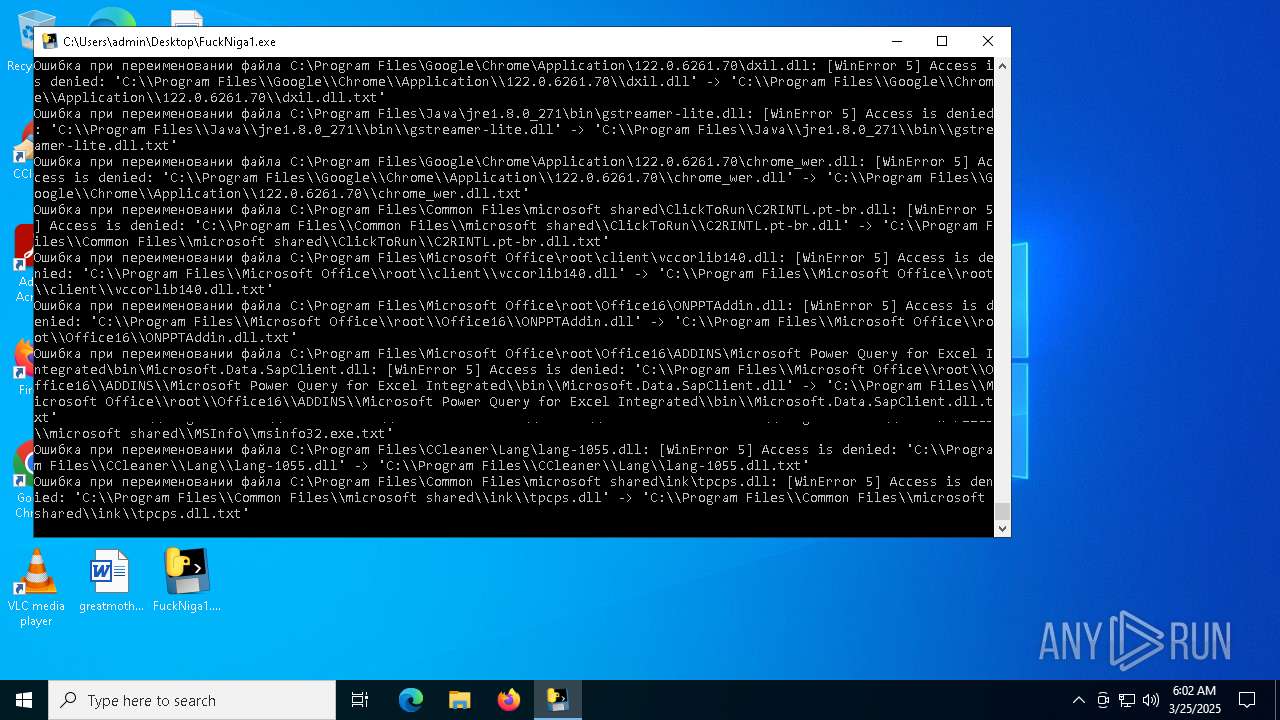
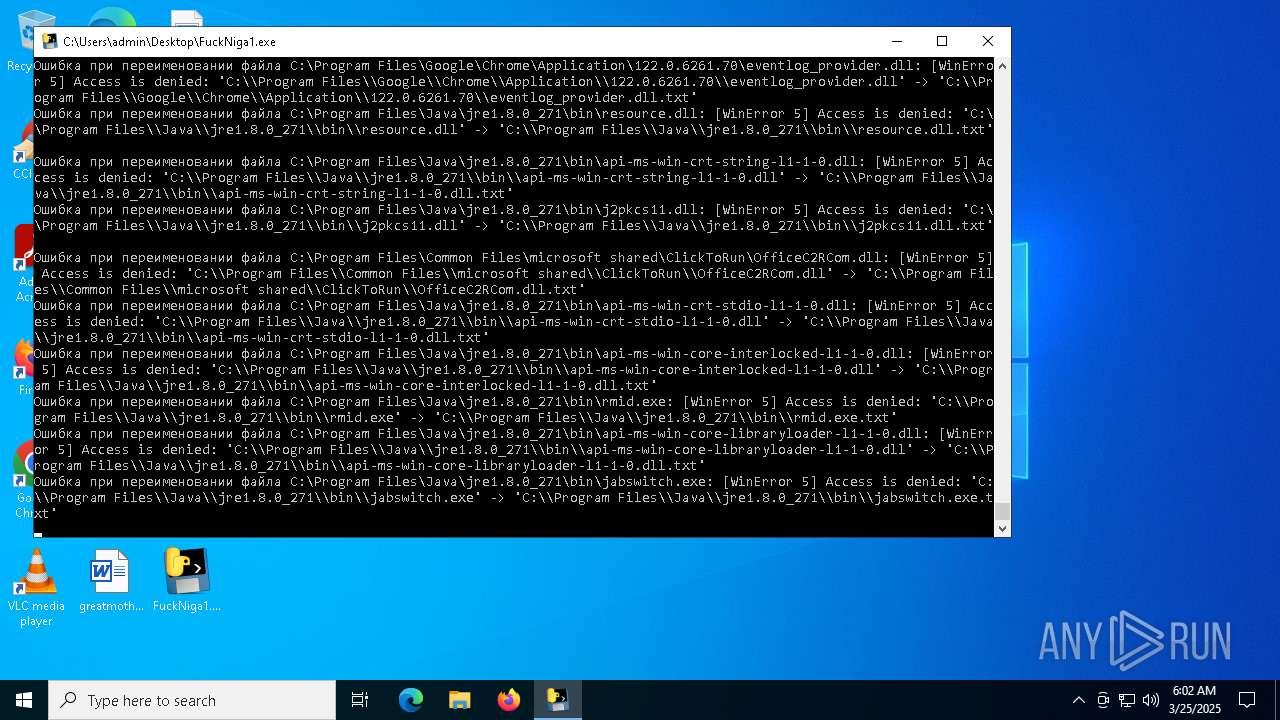
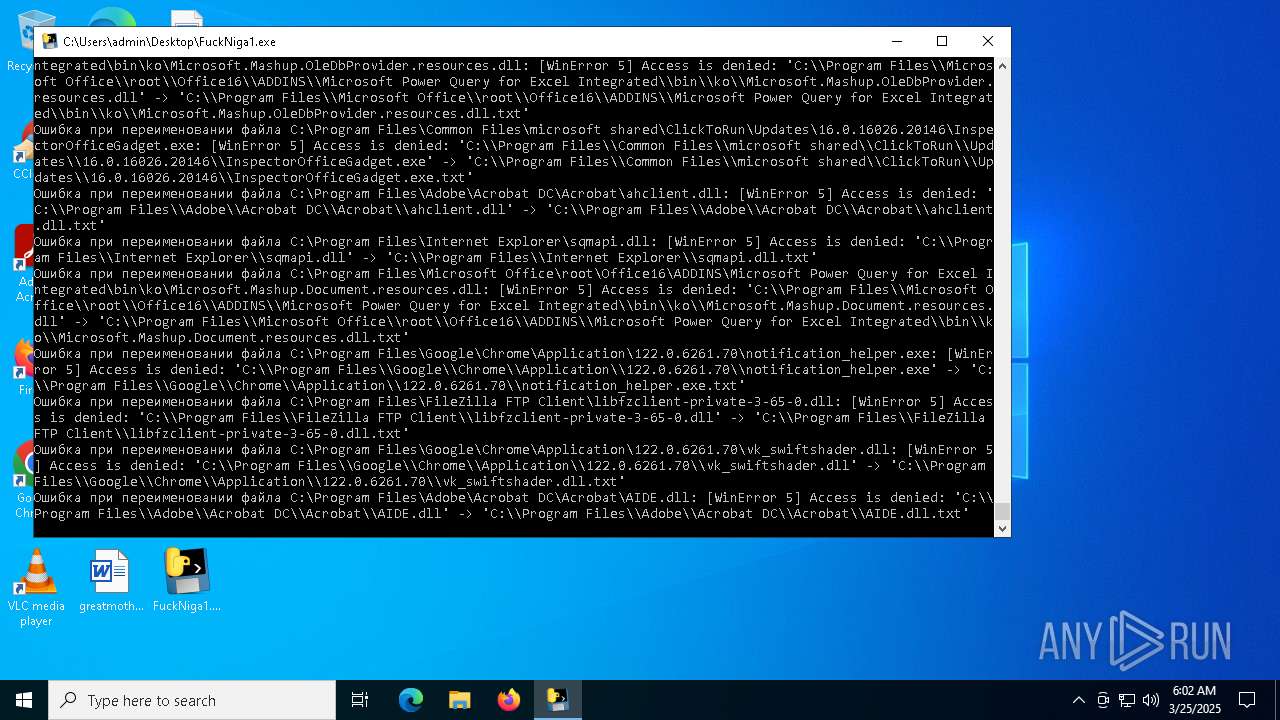
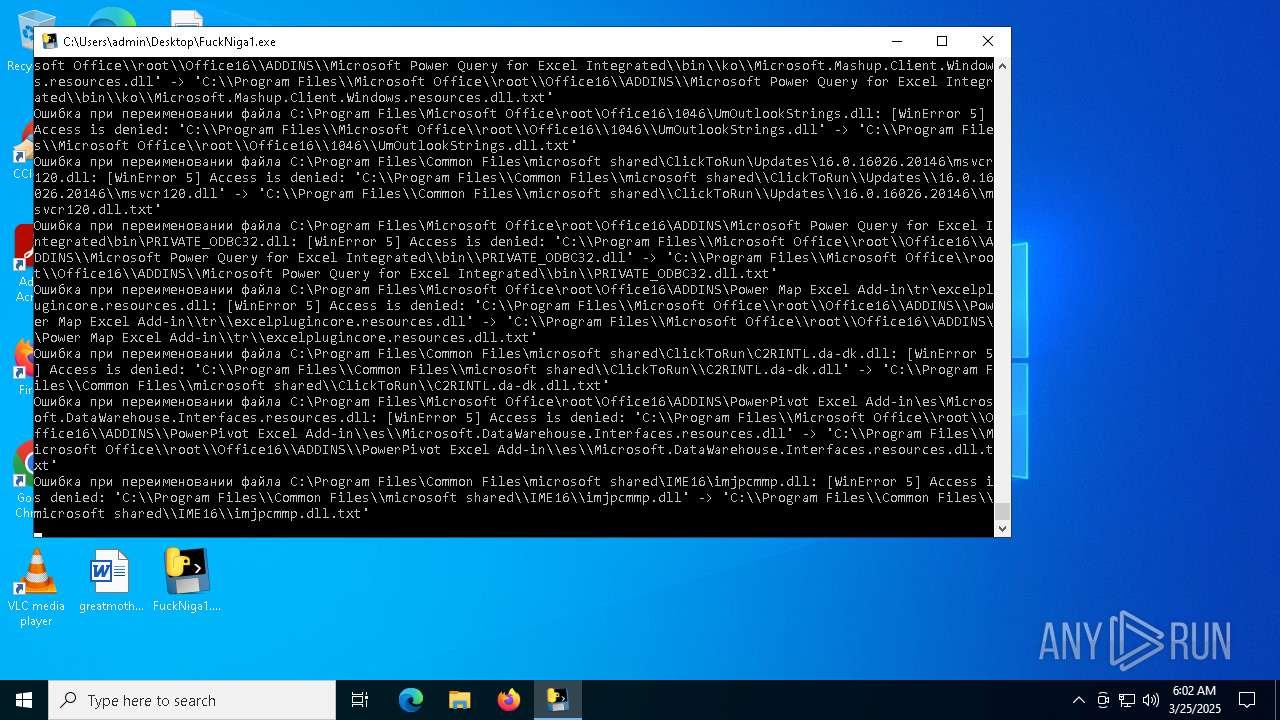
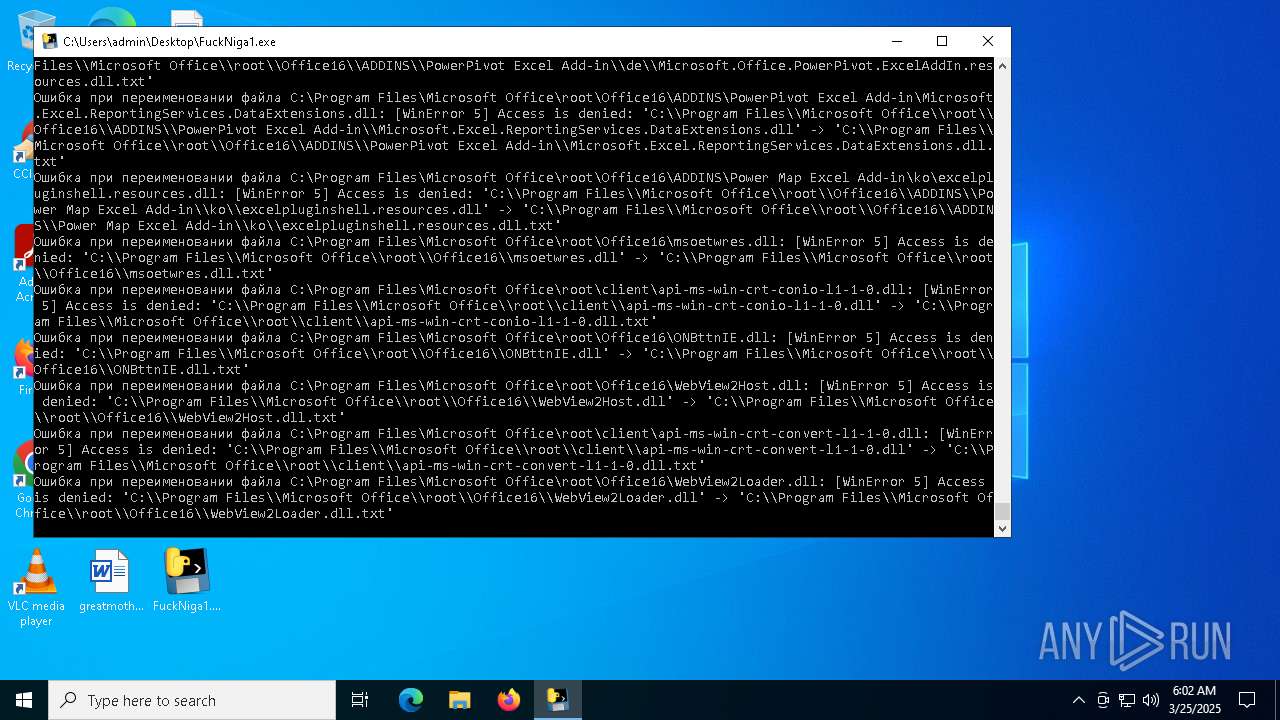
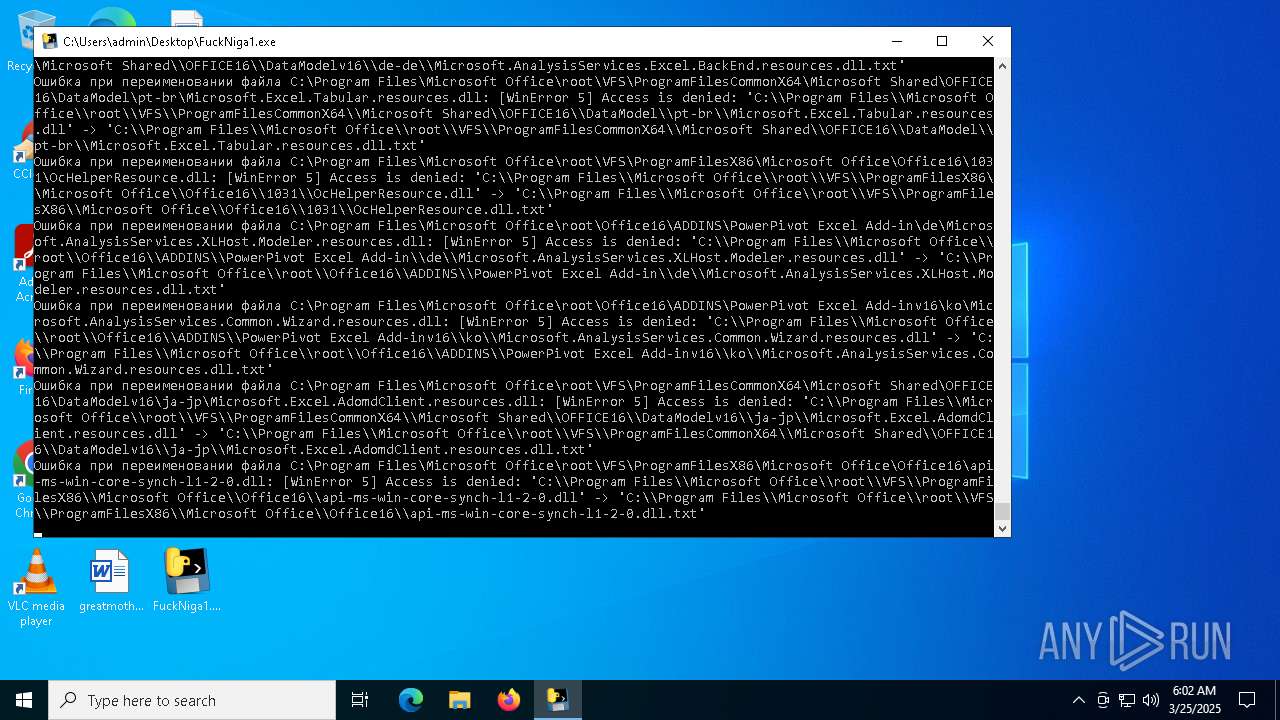
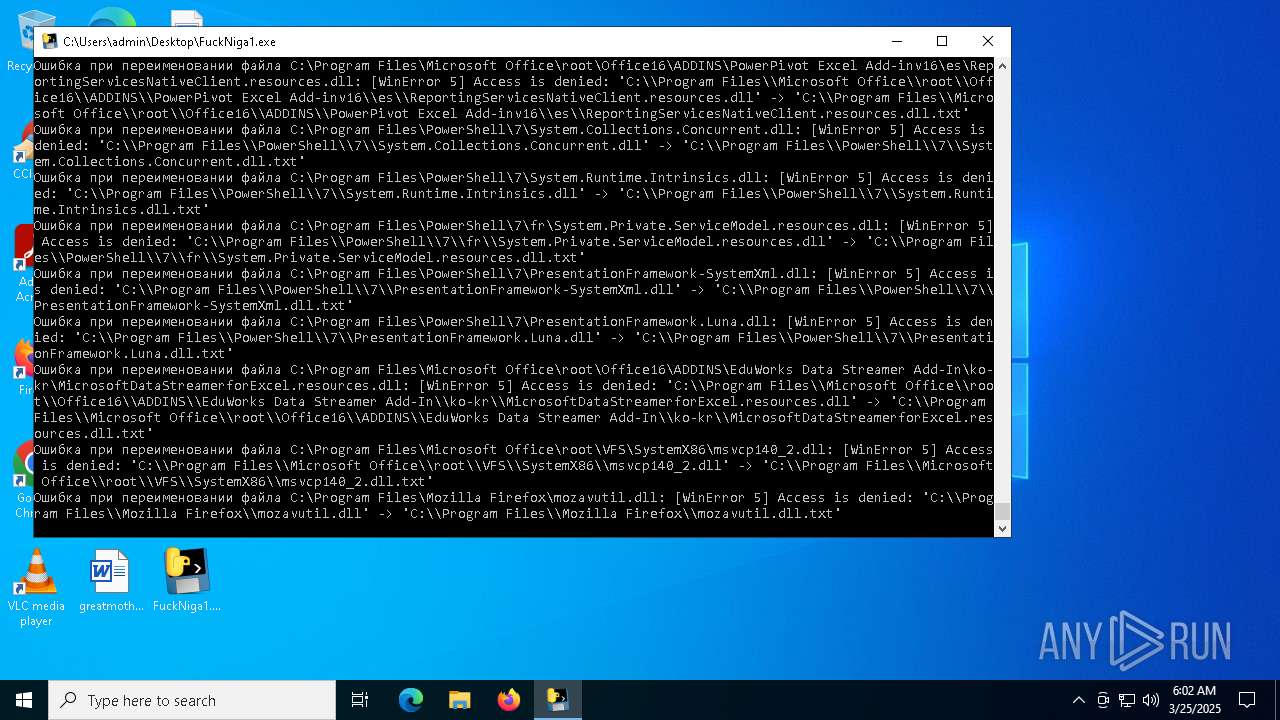
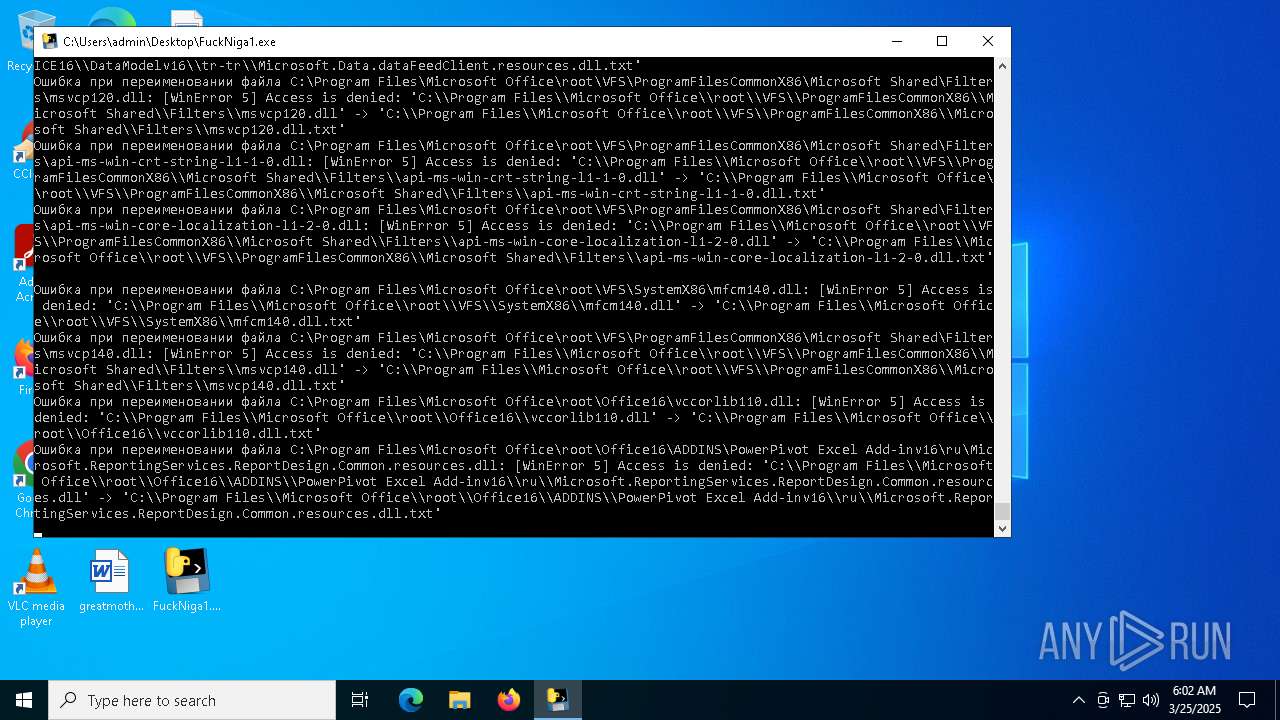
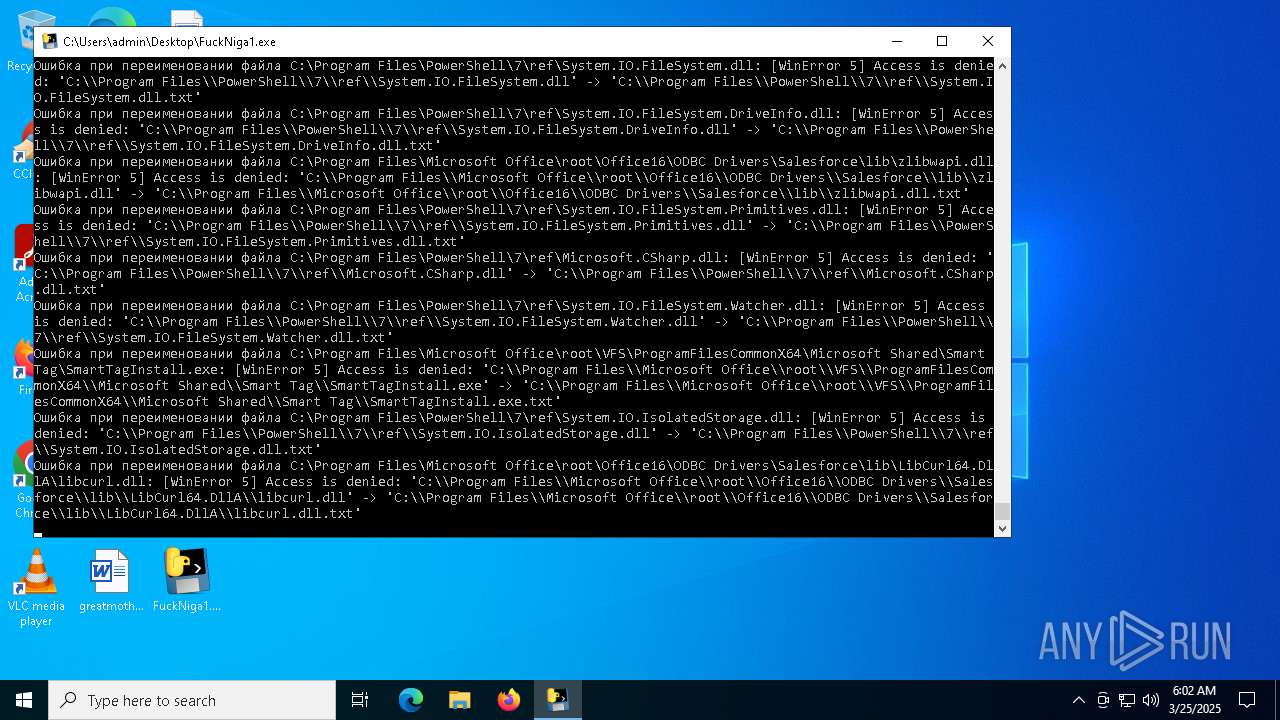
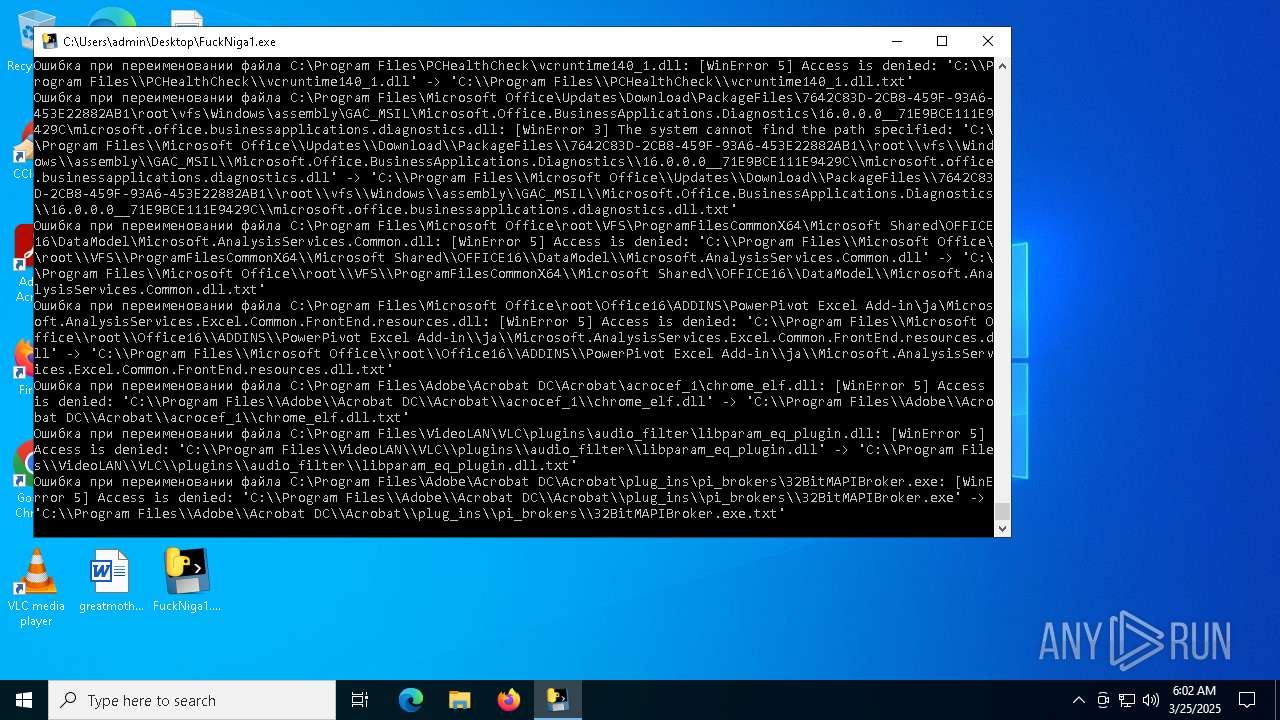
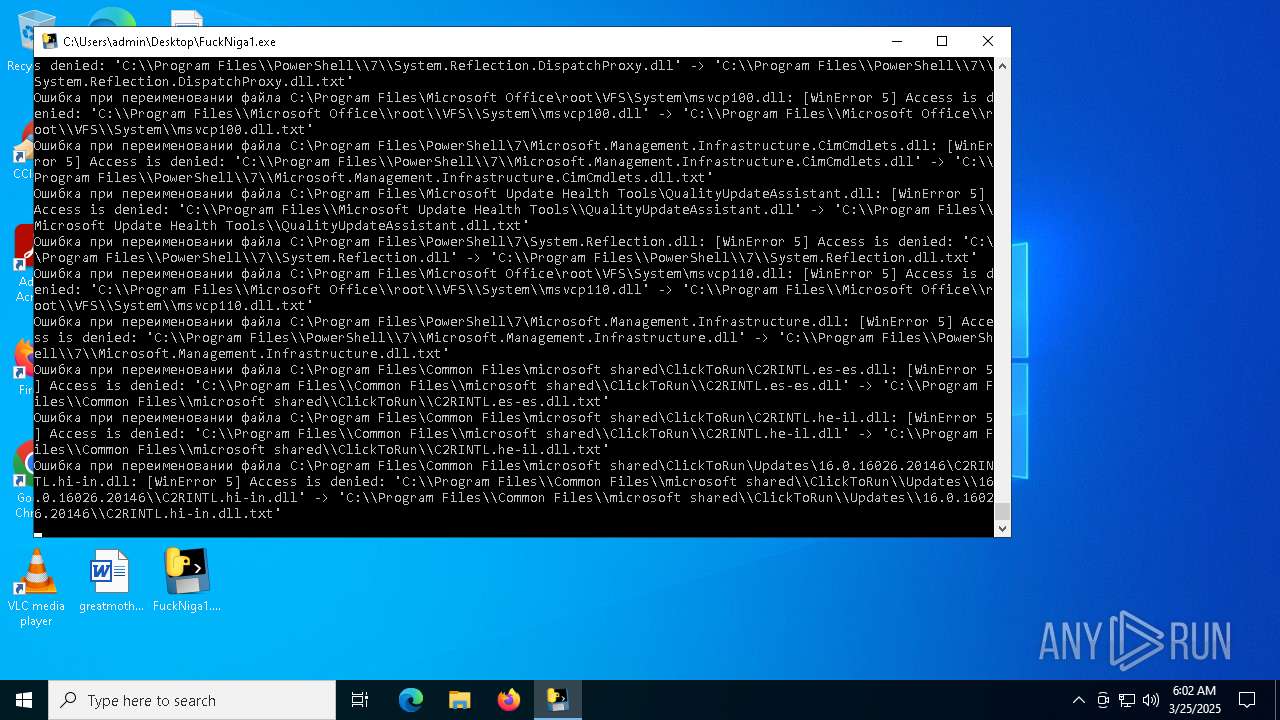
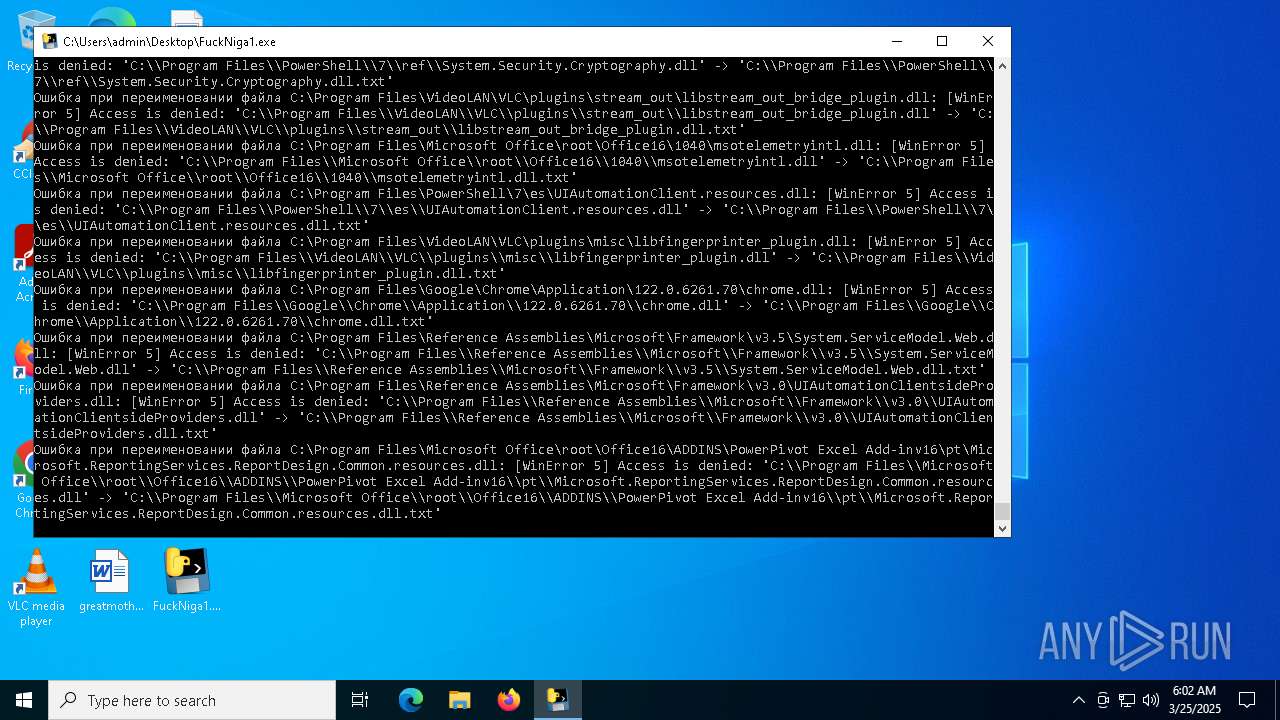
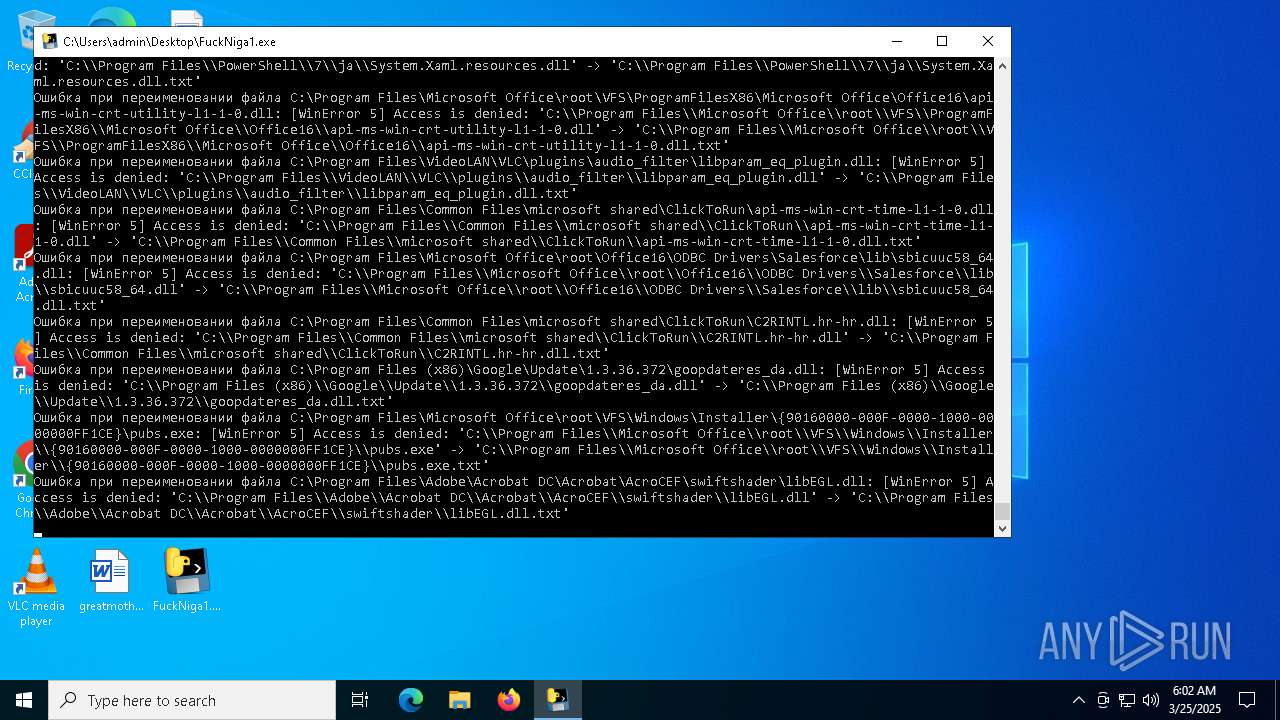
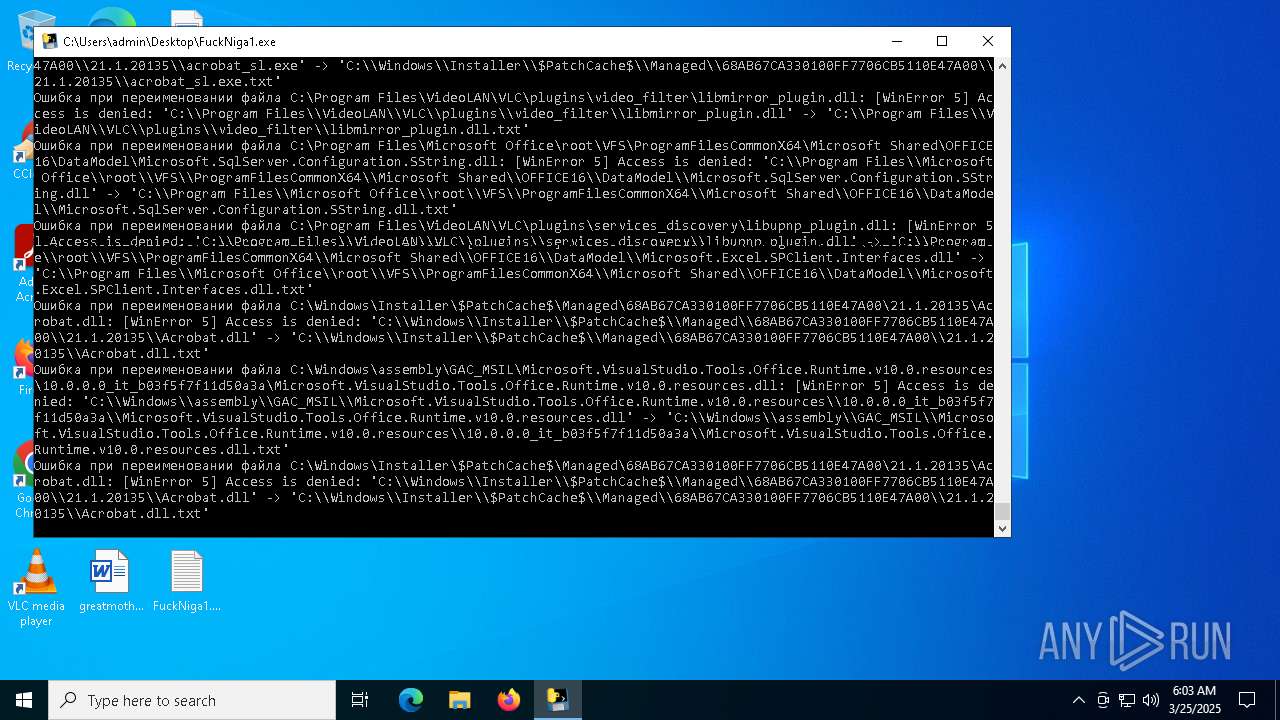
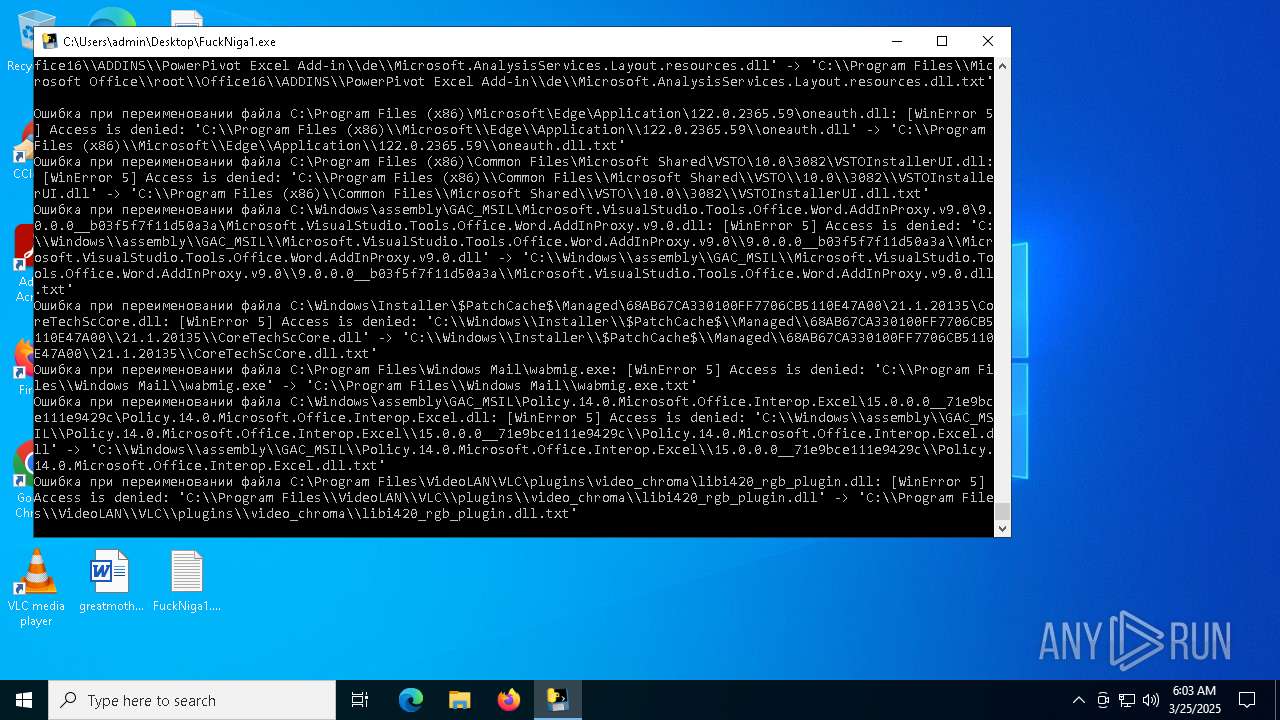
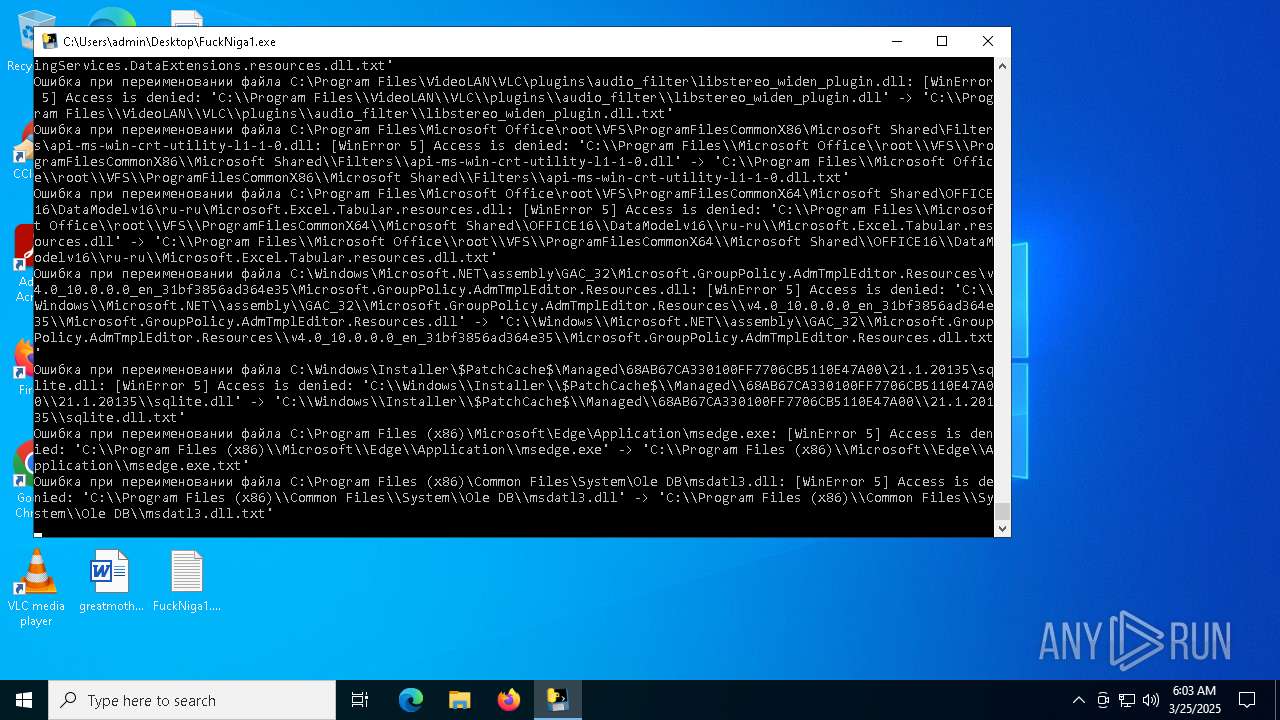
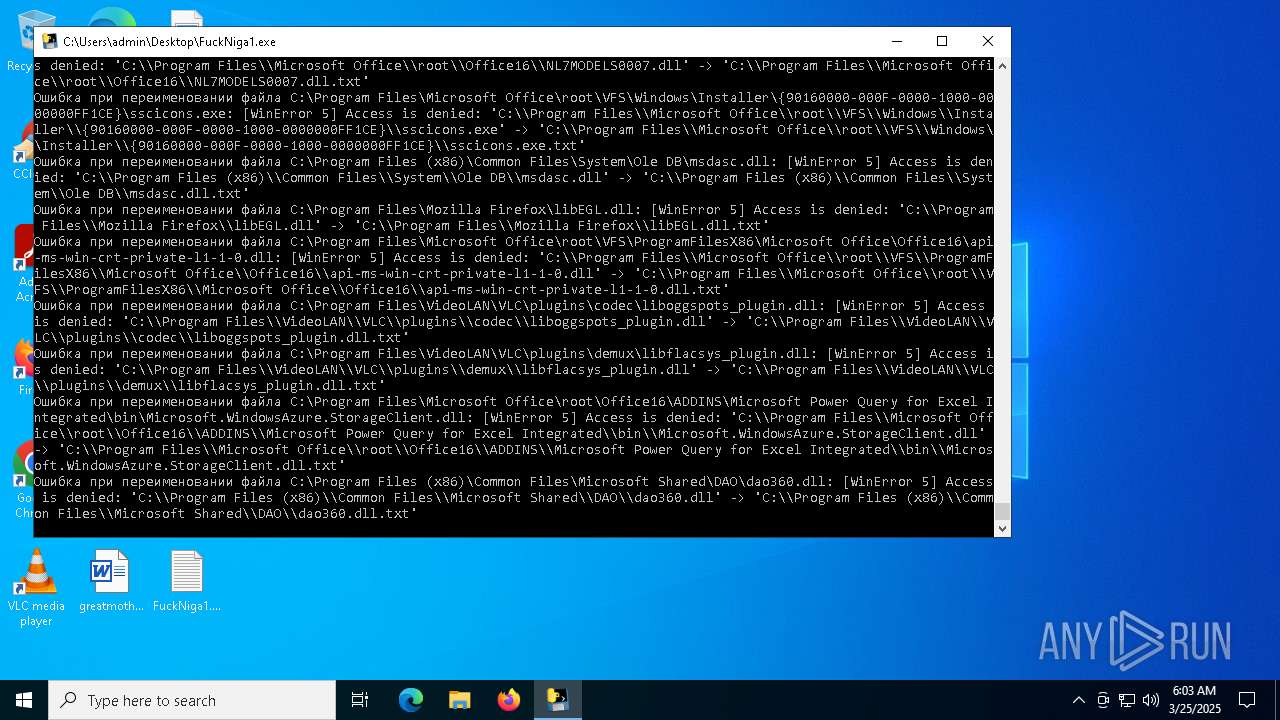
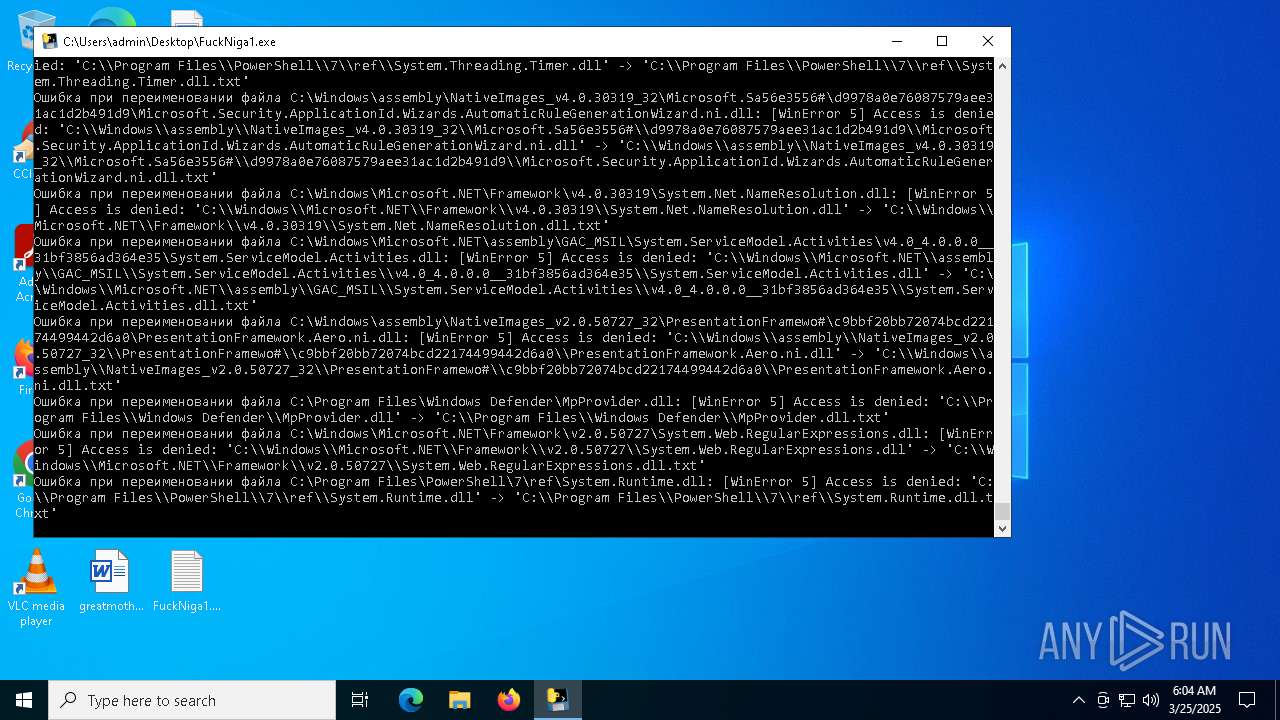
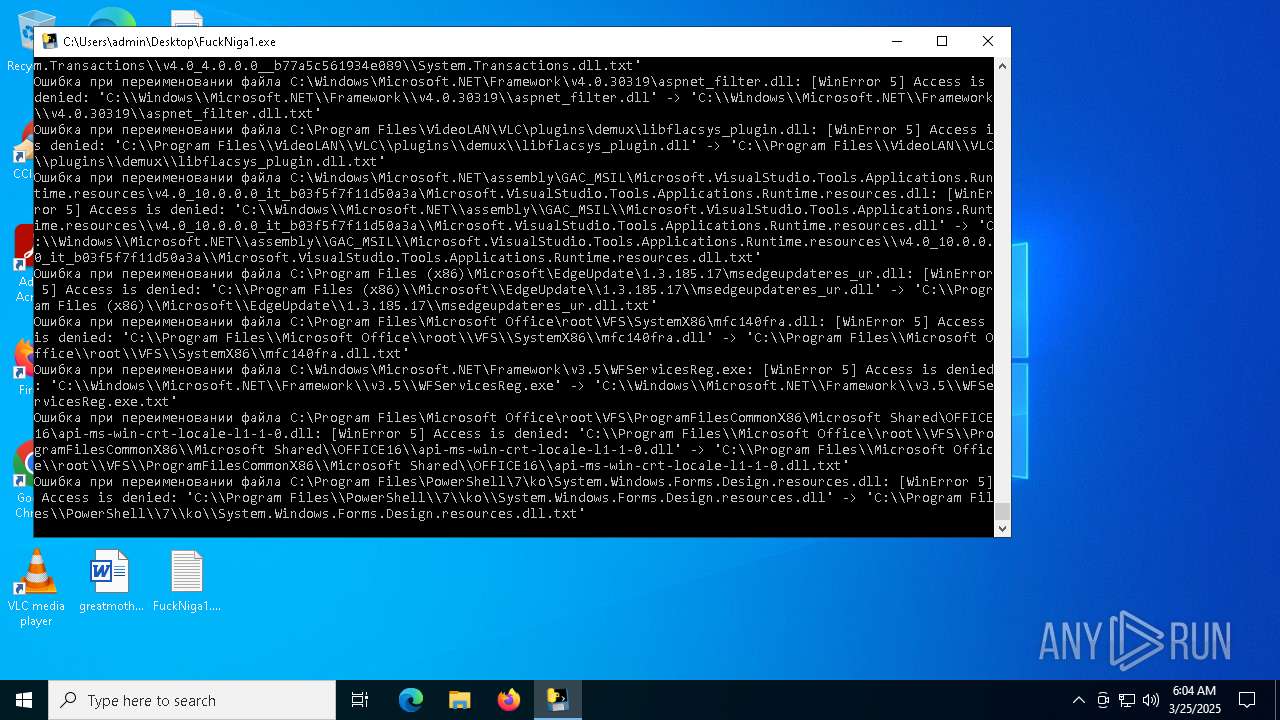
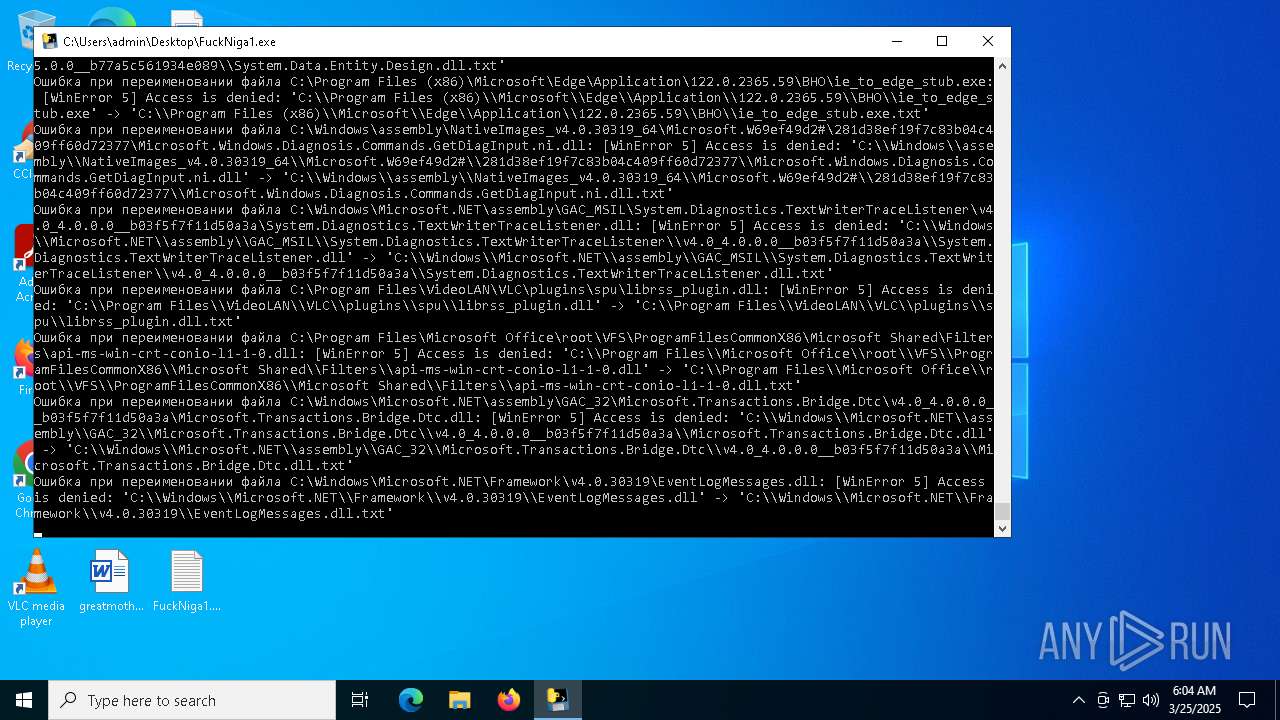
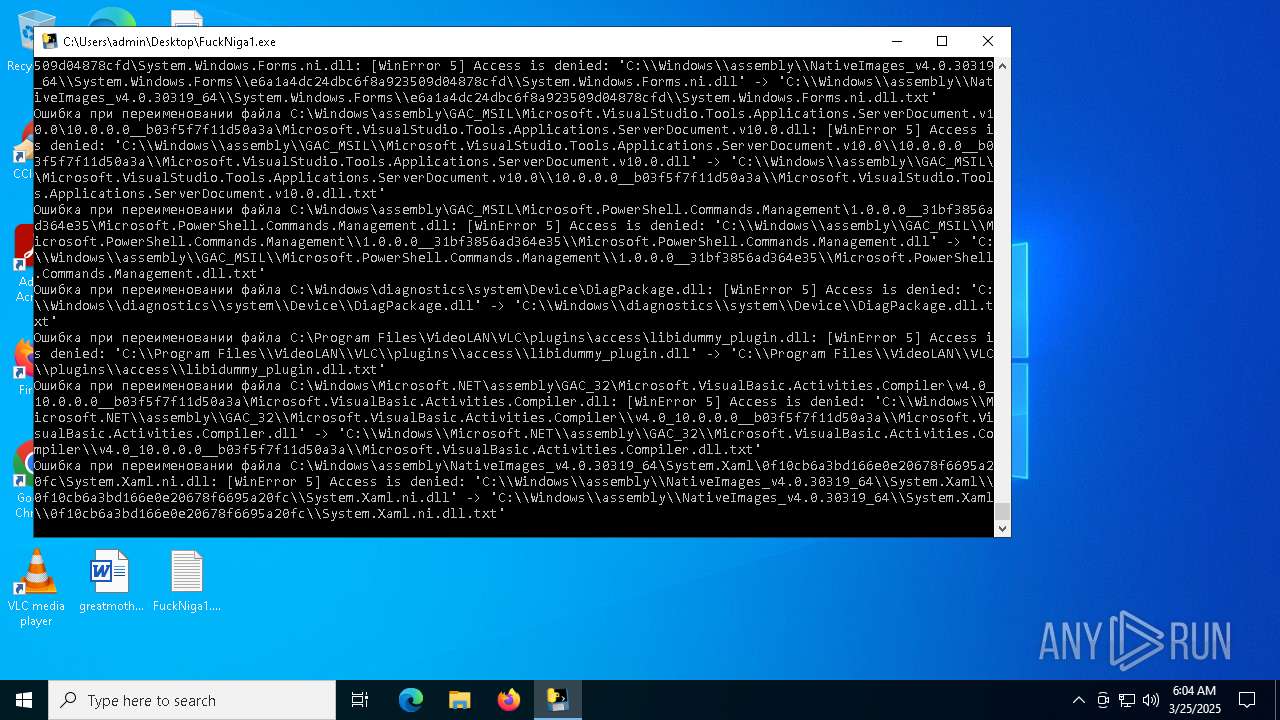
The process drops C-runtime libraries
- FuckNiga1.exe (PID: 4040)
- FuckNiga1.exe (PID: 1184)
- FuckNiga1.exe (PID: 4272)
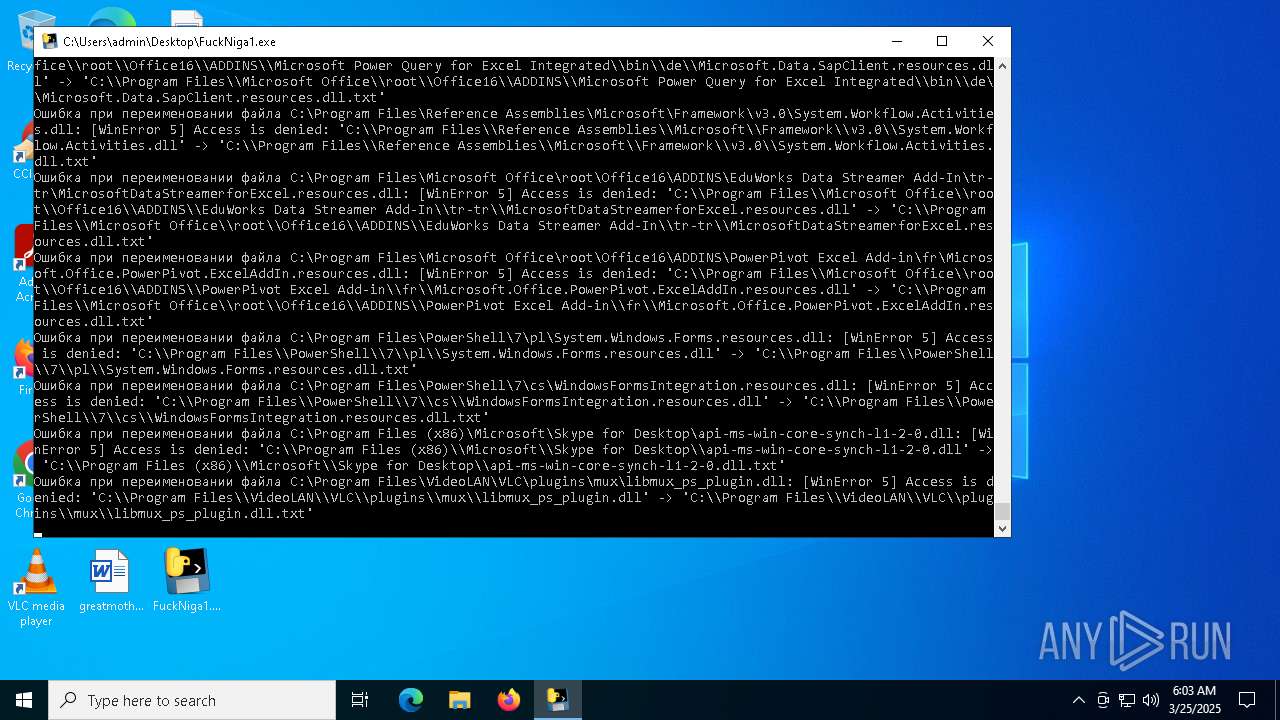
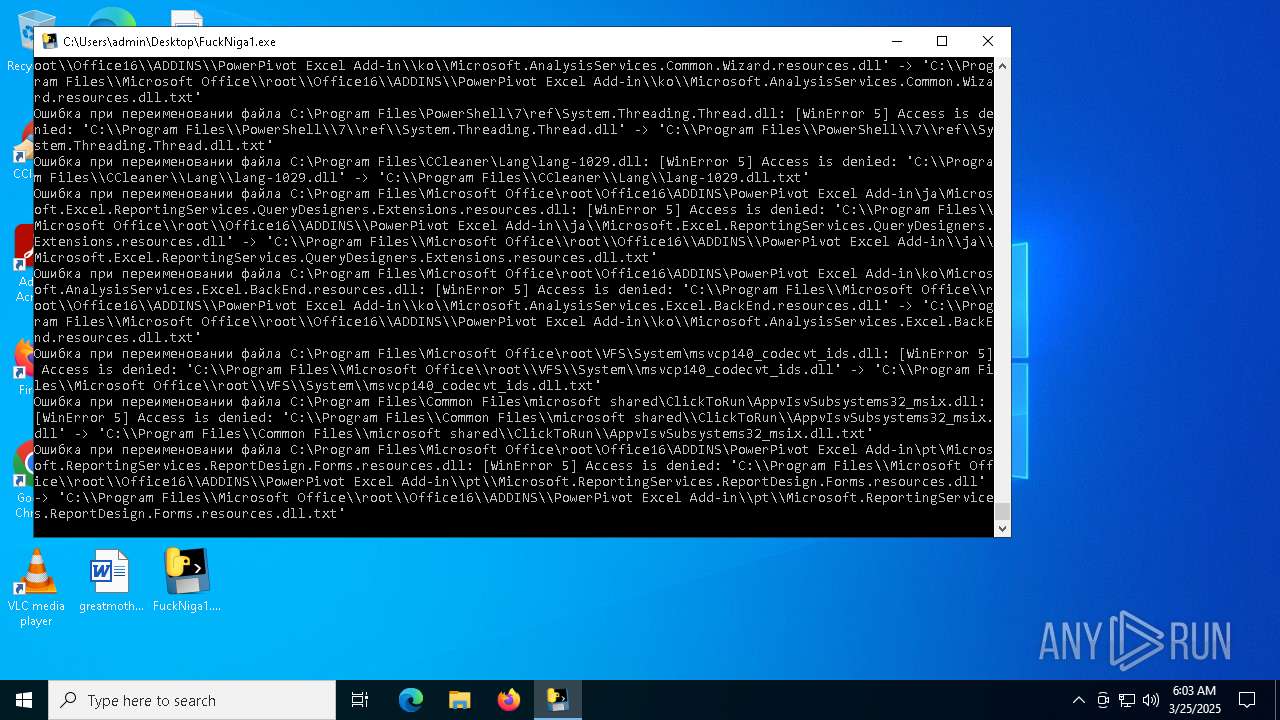
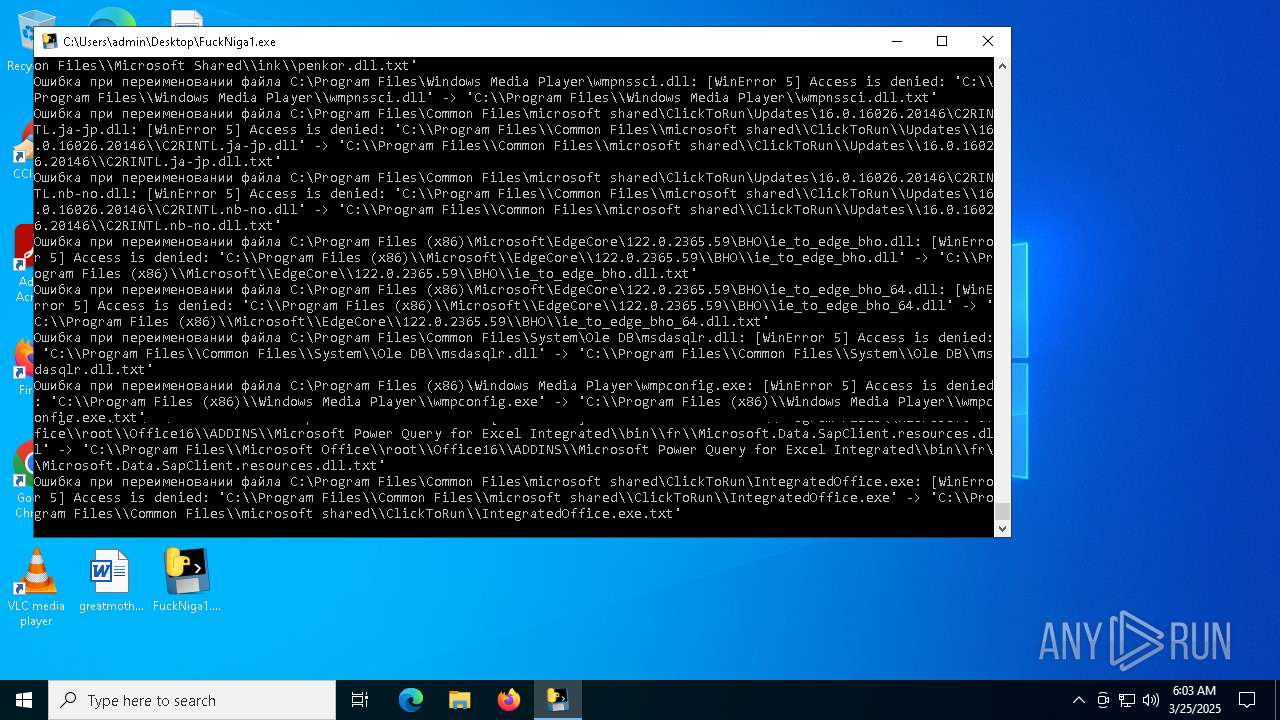
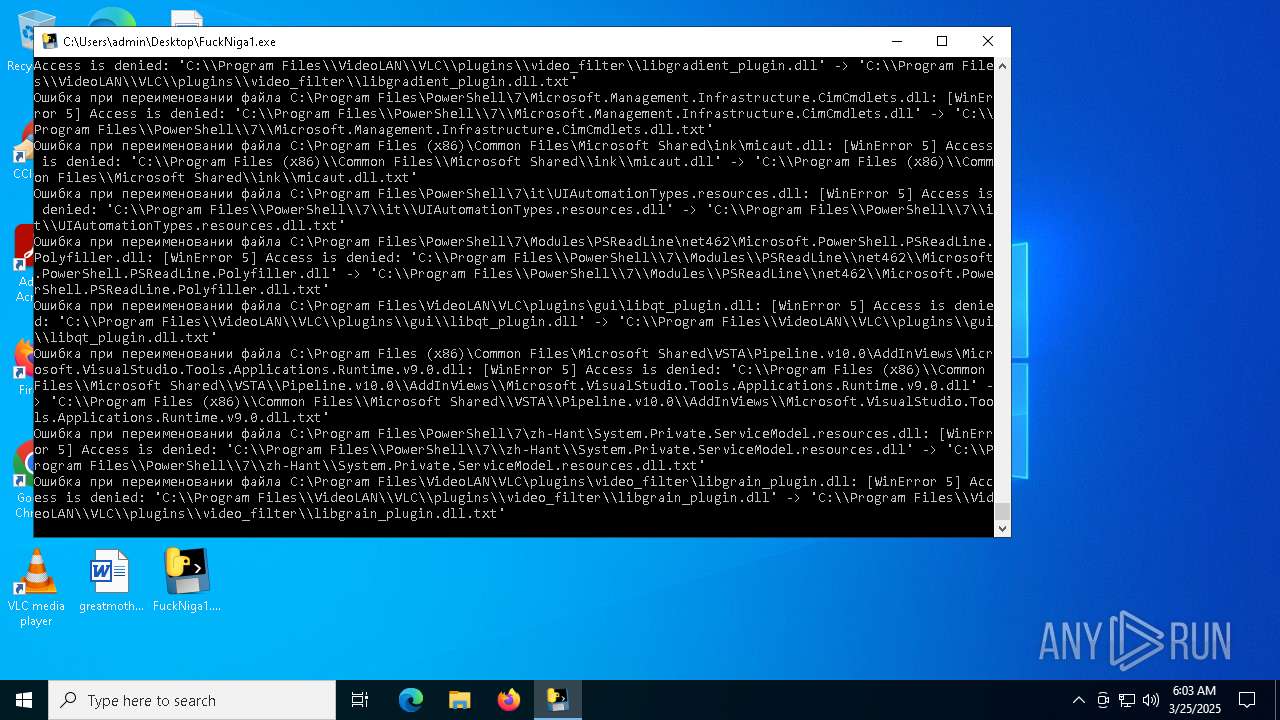
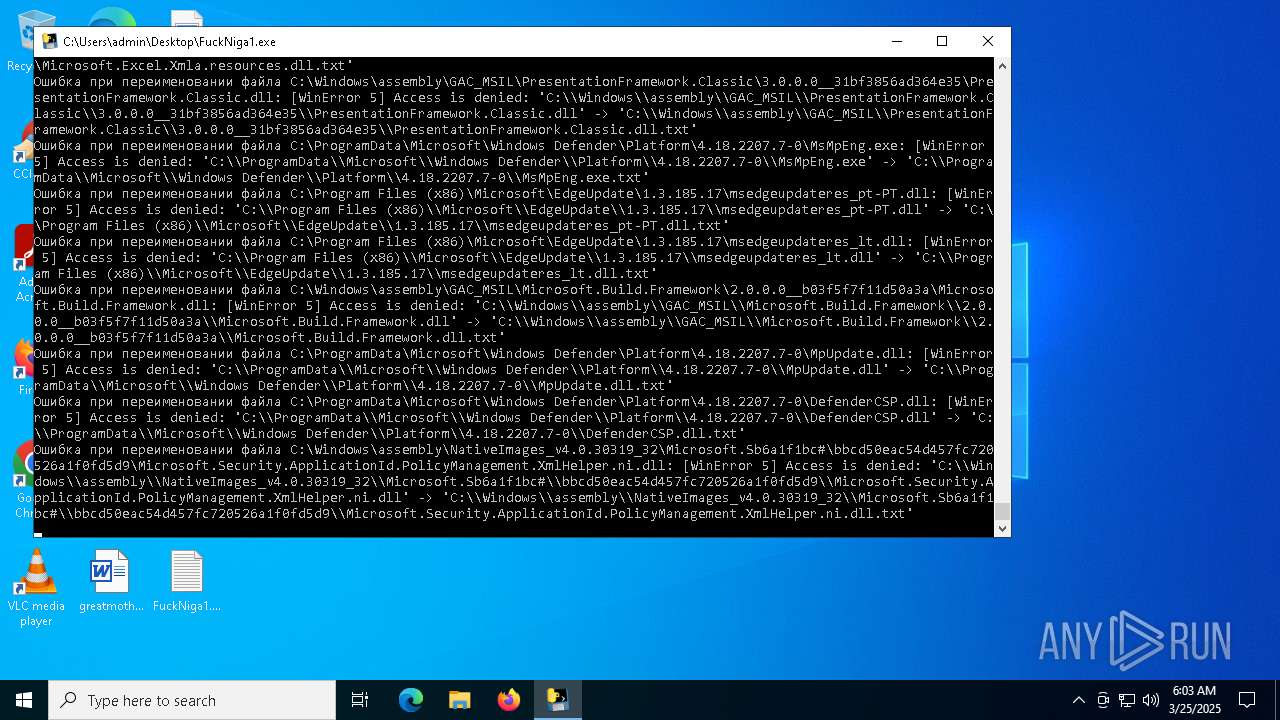
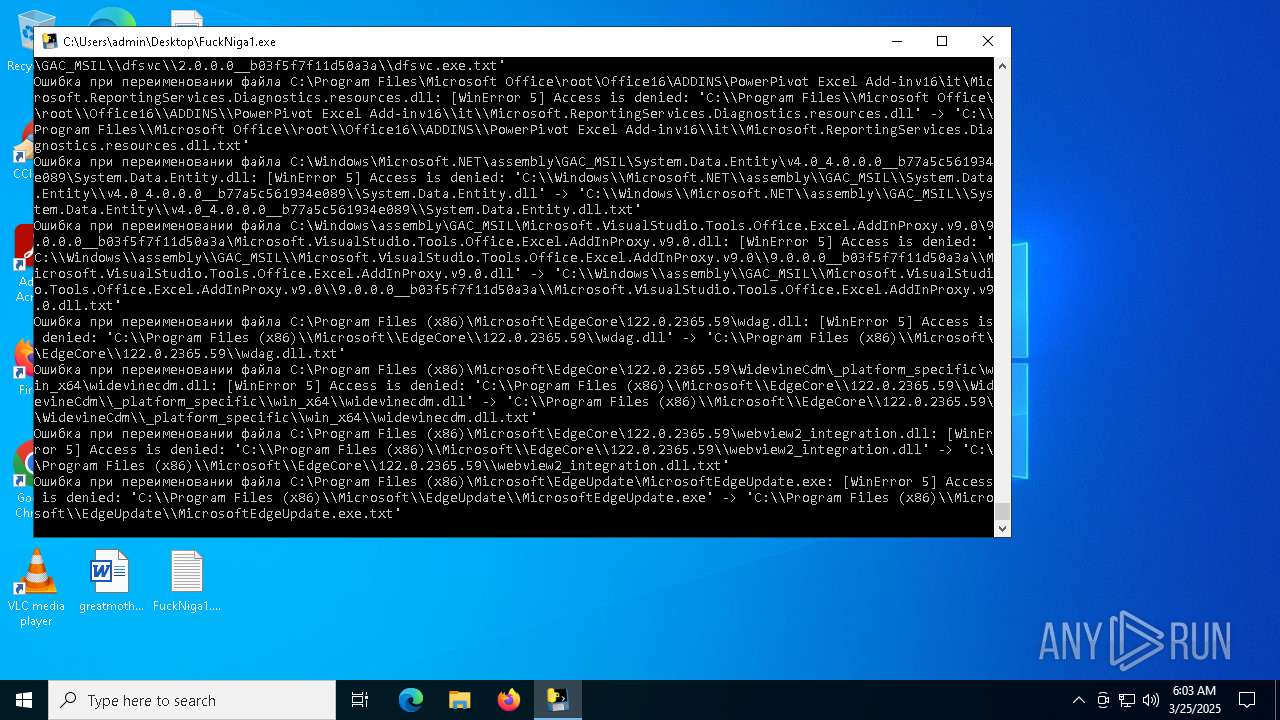
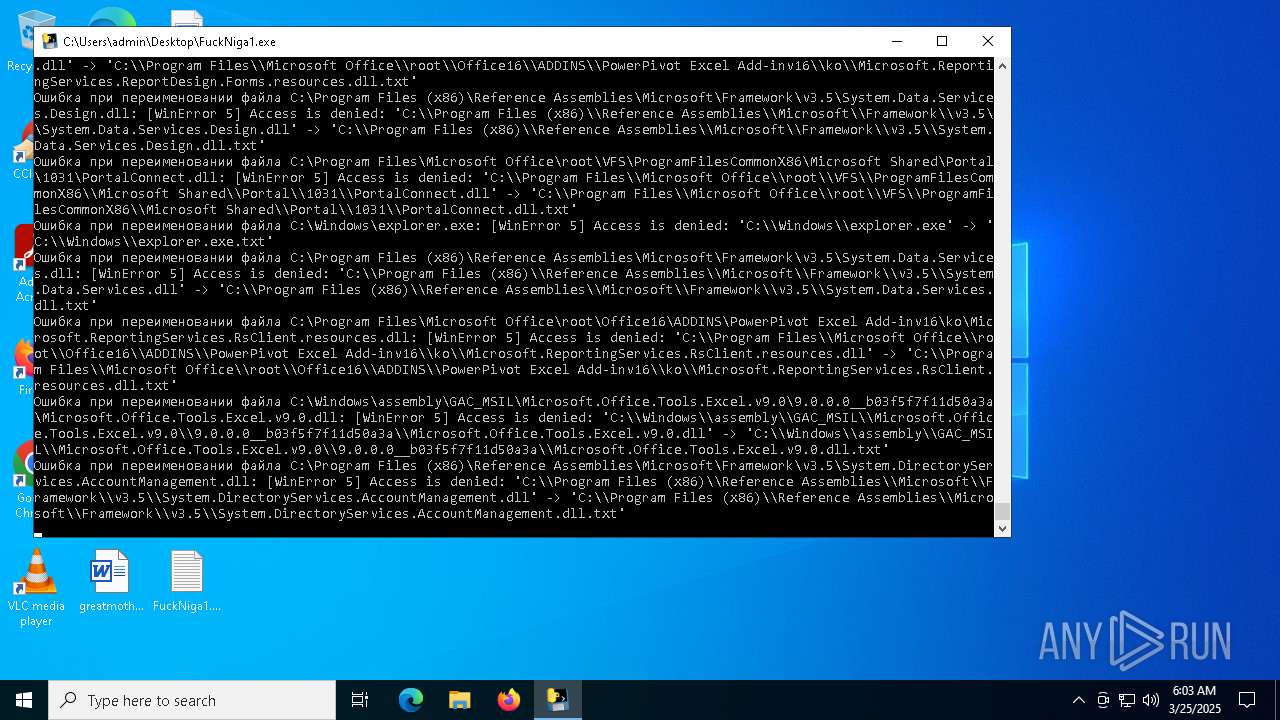
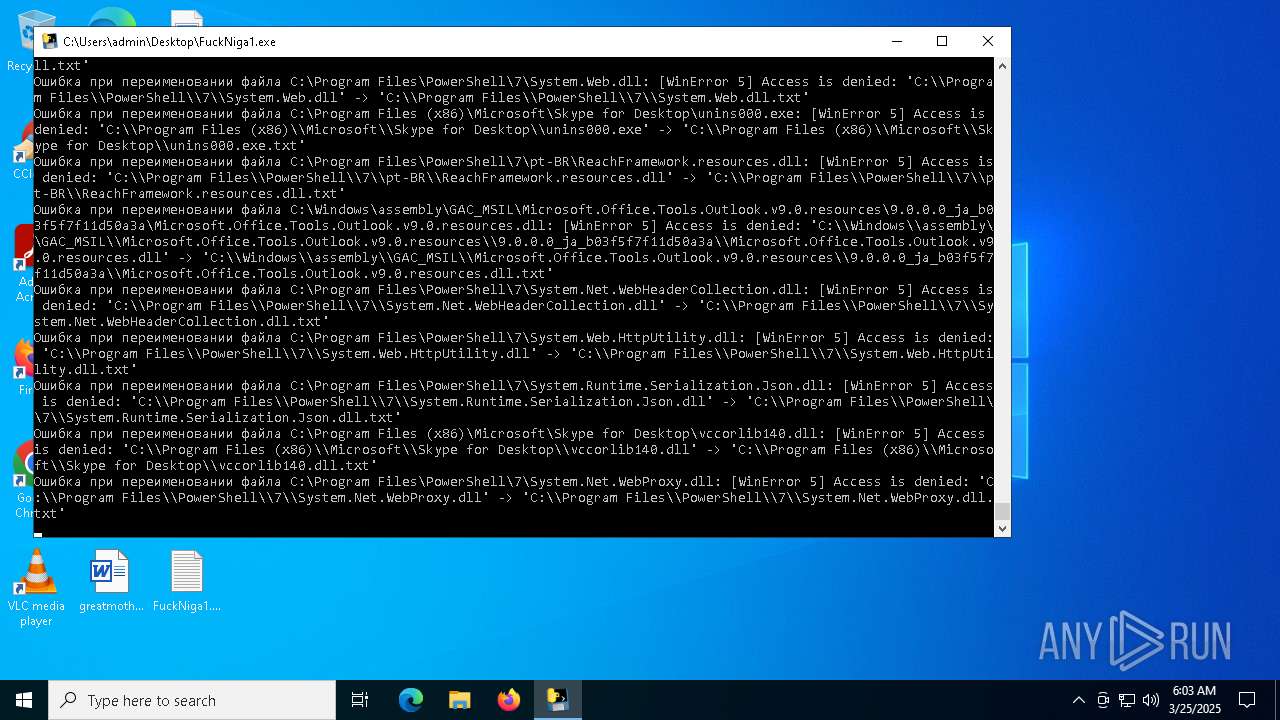
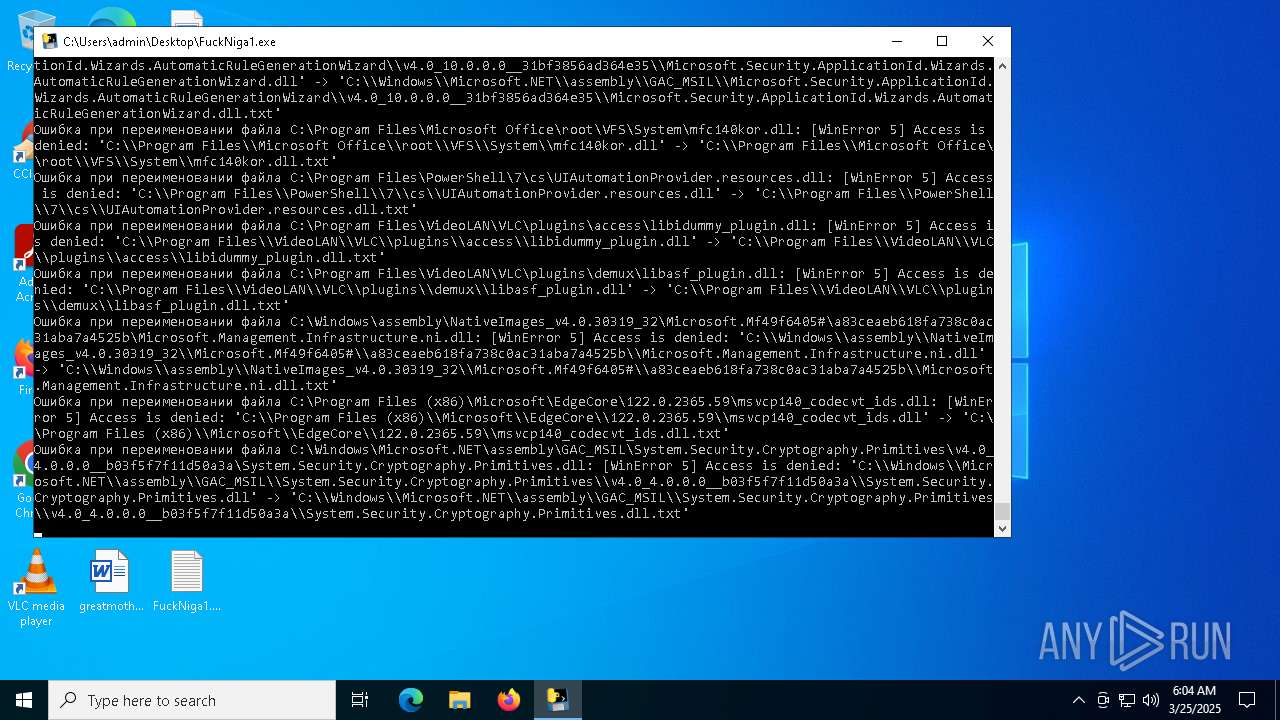
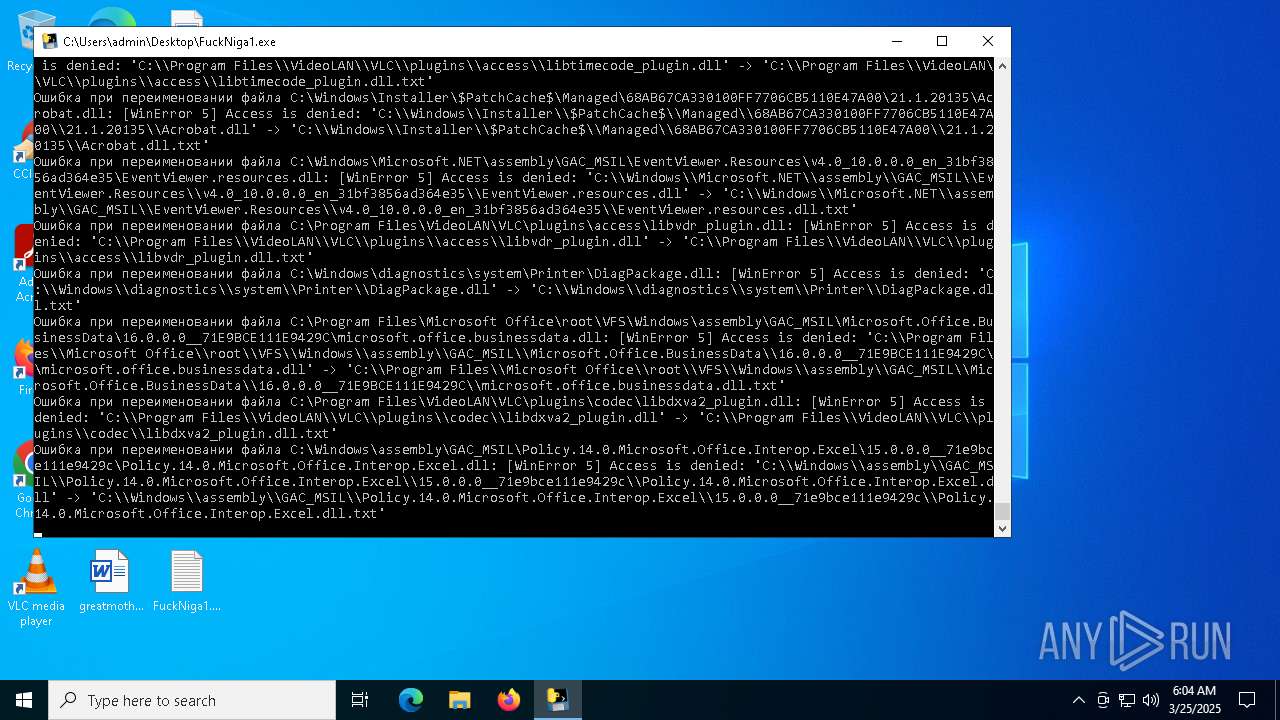
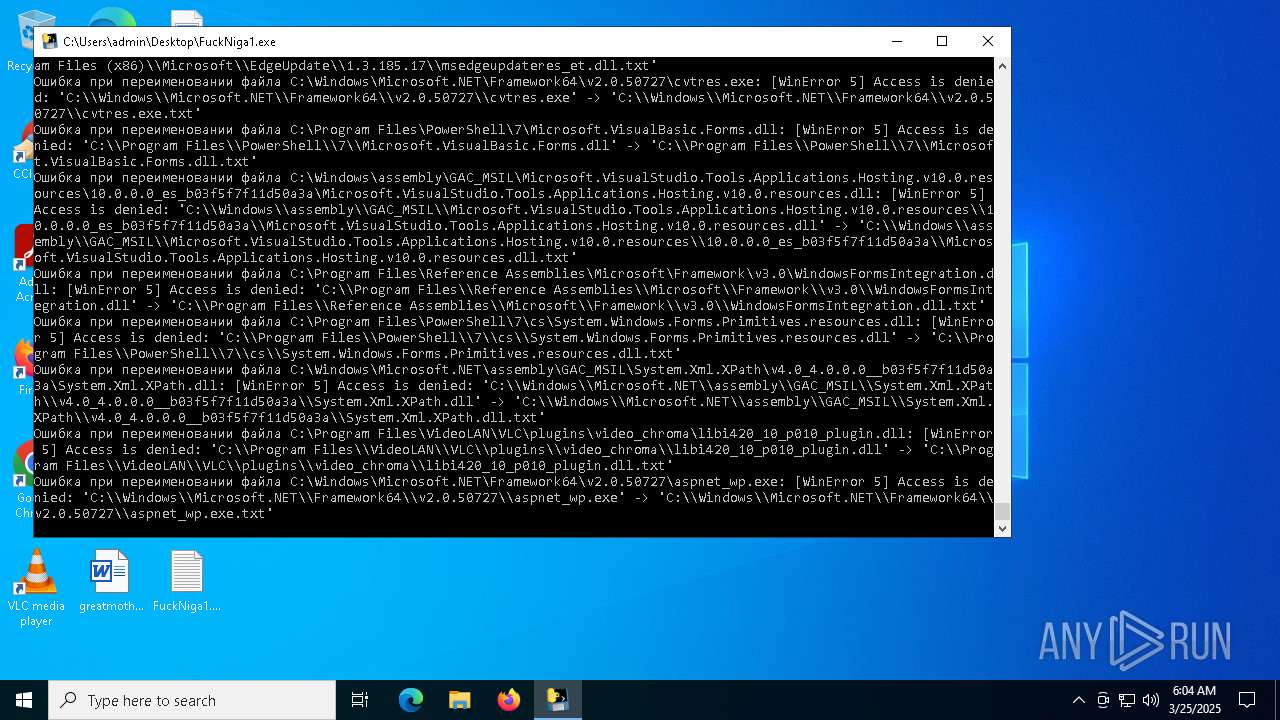
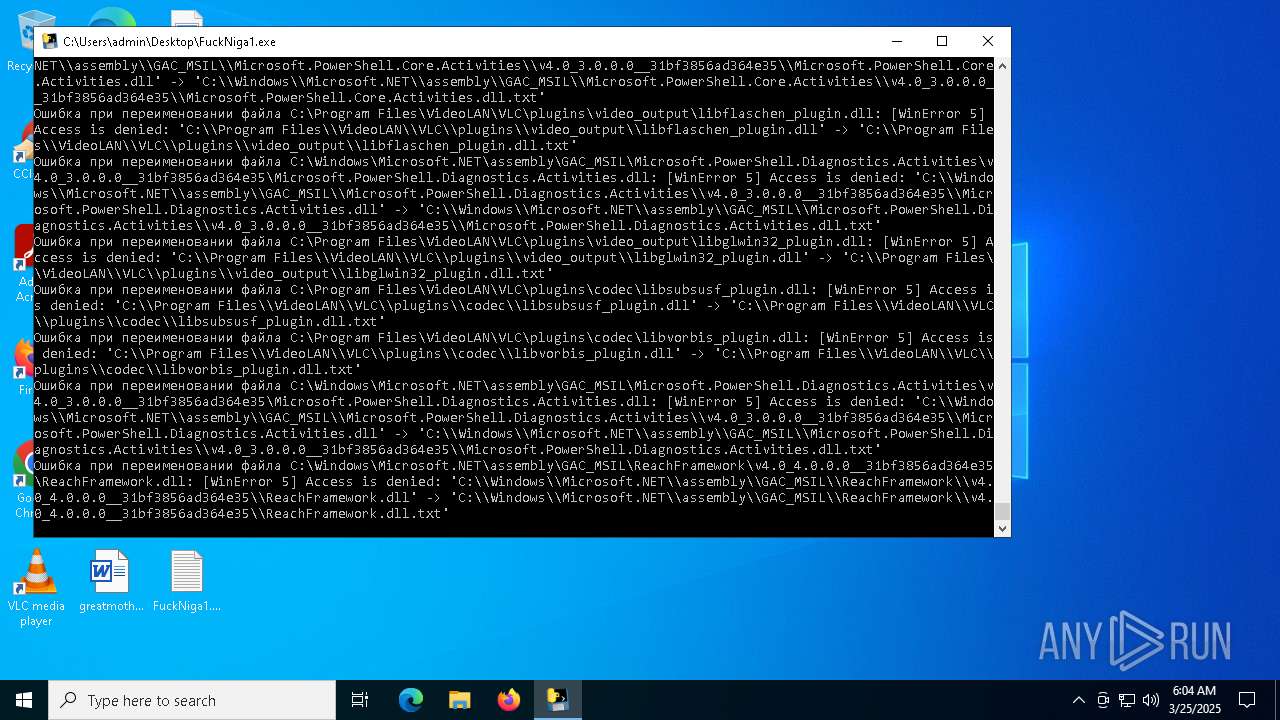
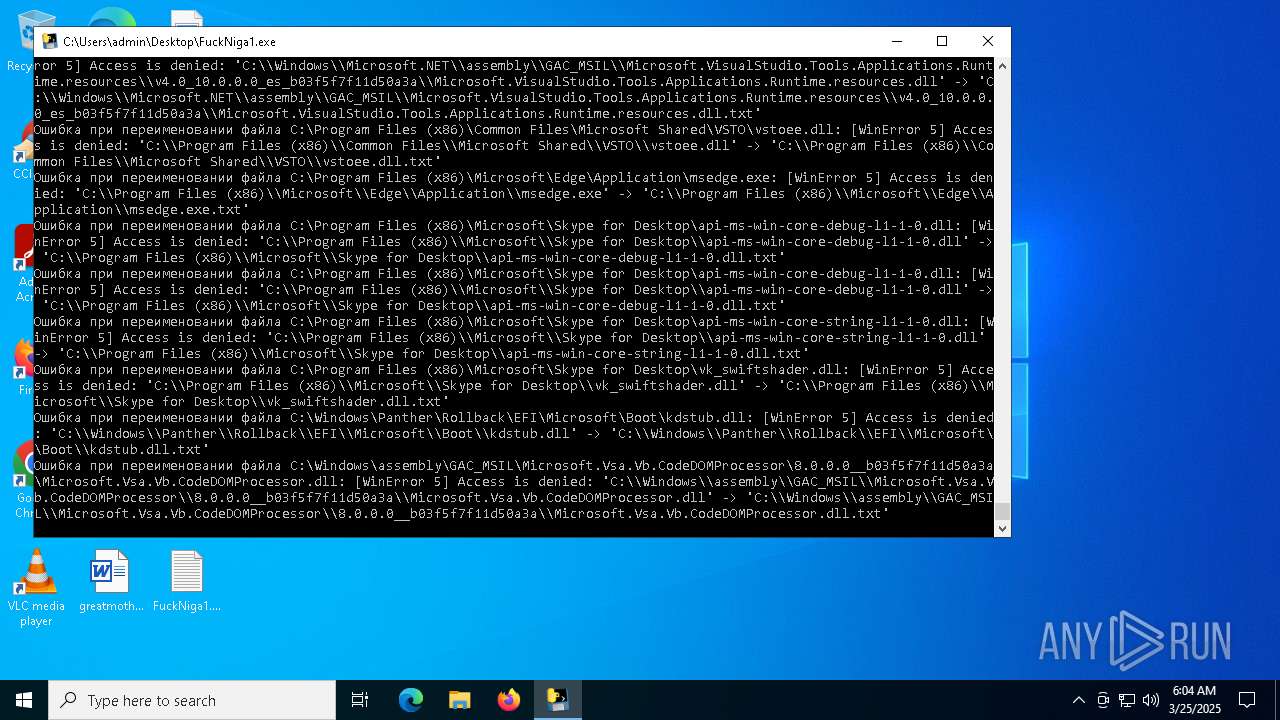
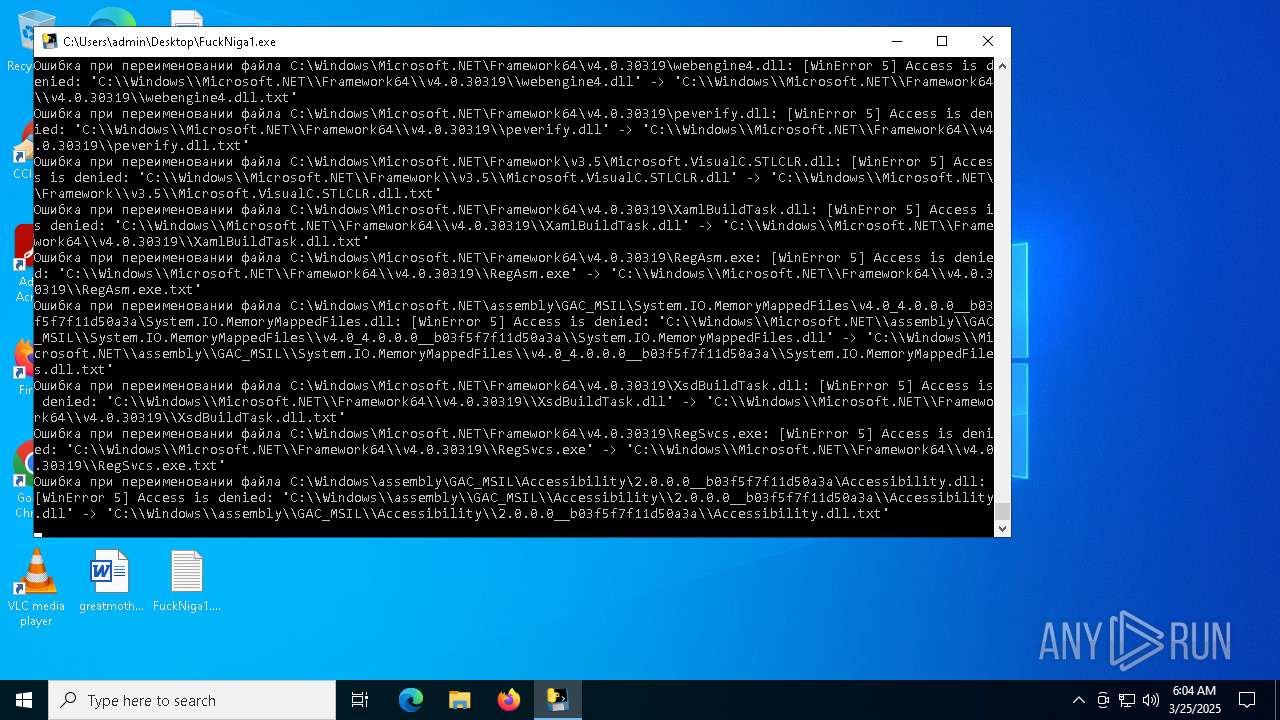
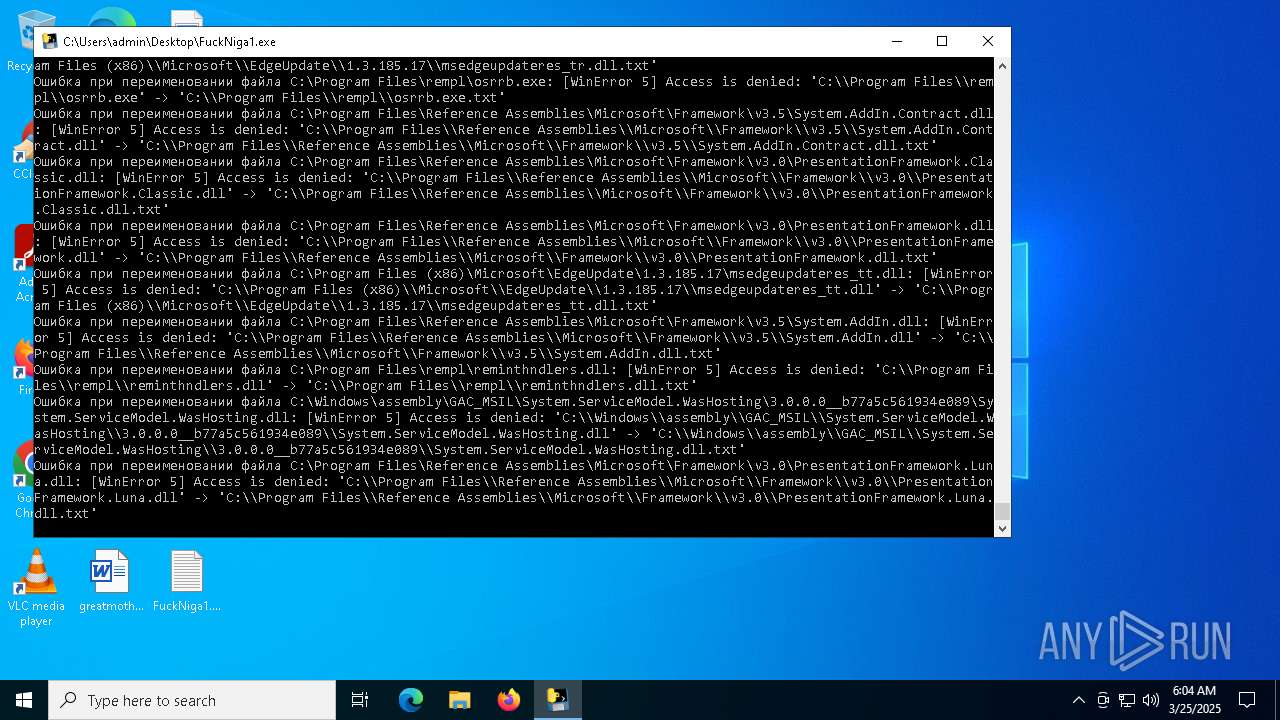
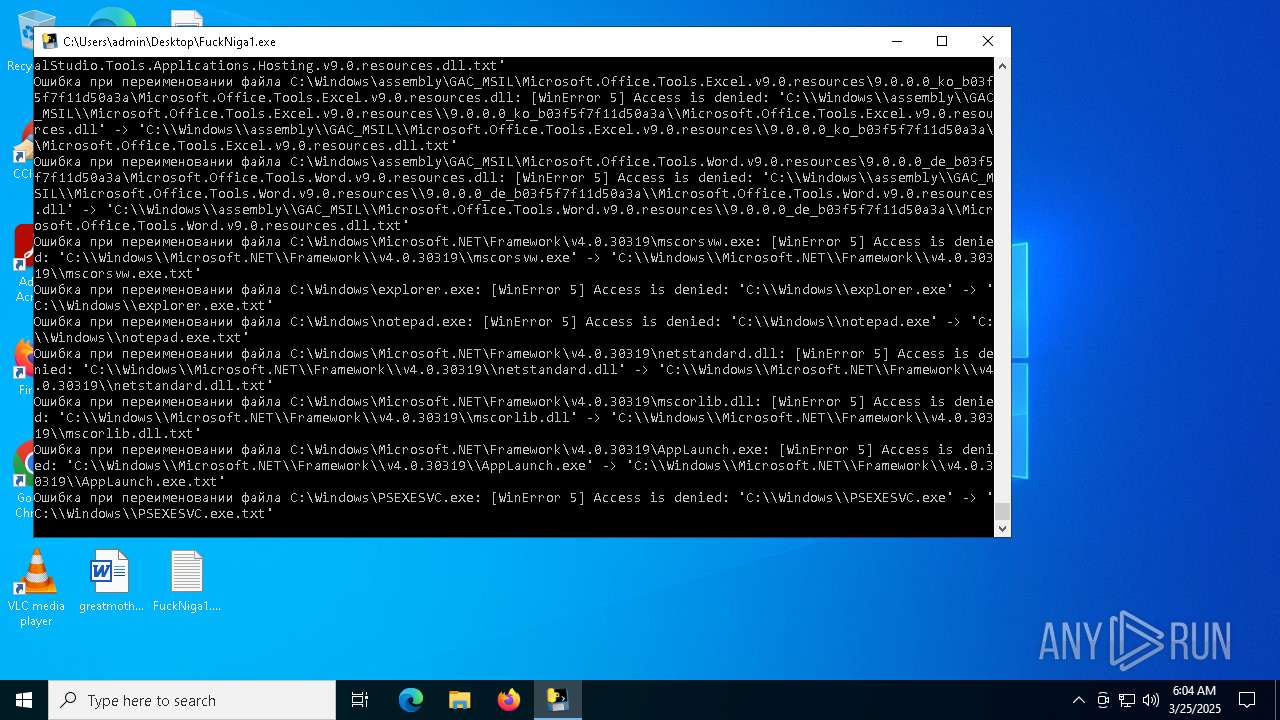
Process drops legitimate windows executable
- FuckNiga1.exe (PID: 4040)
- FuckNiga1.exe (PID: 1184)
- FuckNiga1.exe (PID: 2108)
- FuckNiga1.exe (PID: 4272)
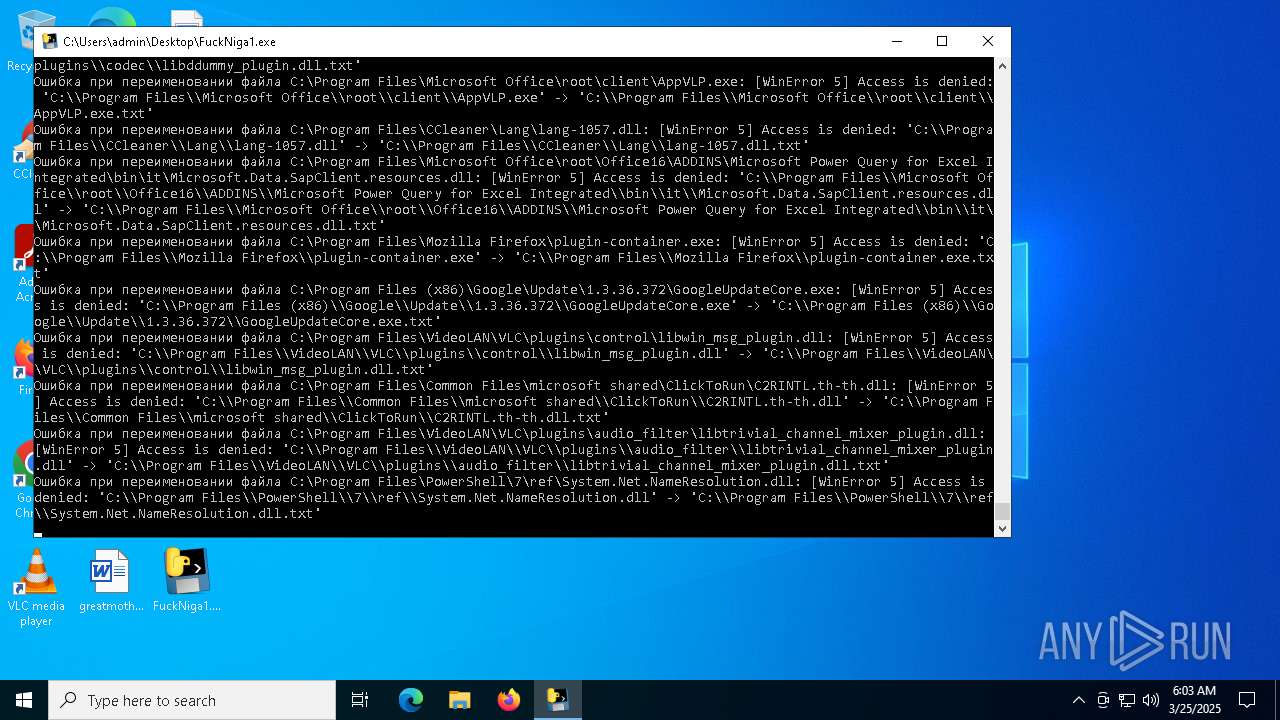
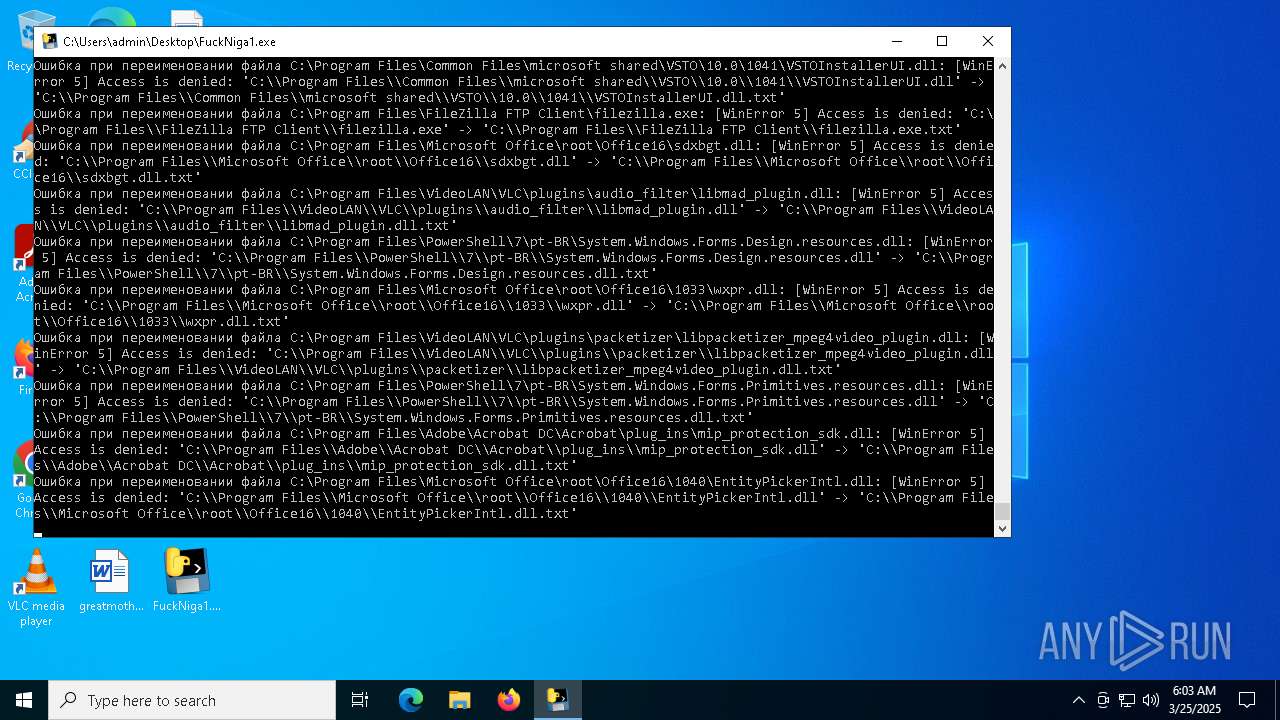
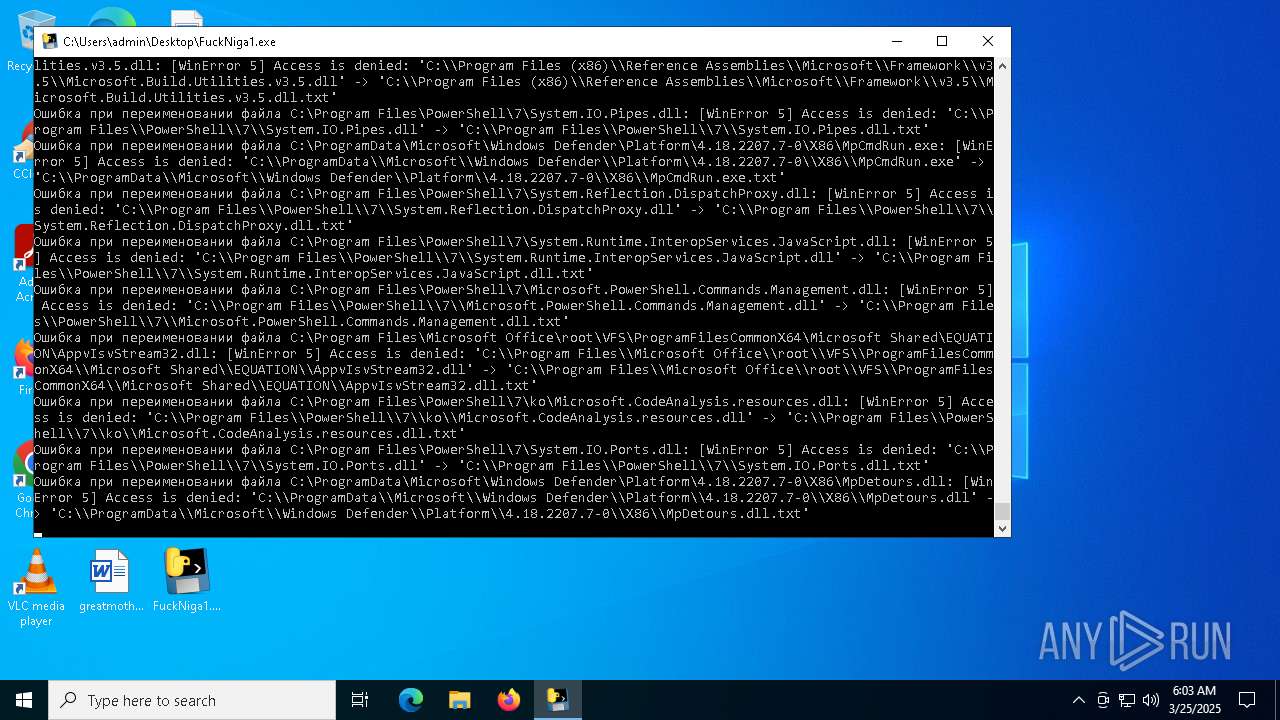
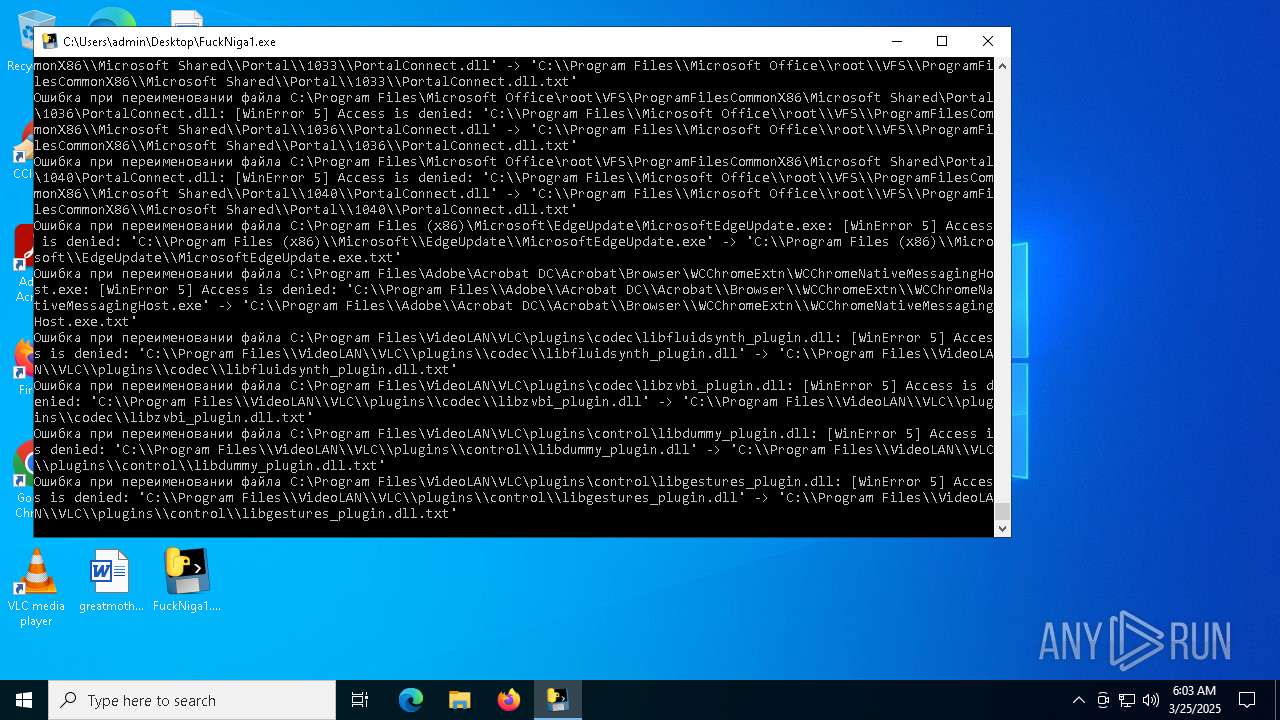
Executable content was dropped or overwritten
- FuckNiga1.exe (PID: 4040)
- FuckNiga1.exe (PID: 1184)
- FuckNiga1.exe (PID: 4272)
- FuckNiga1.exe (PID: 2108)
- FuckNiga1.exe (PID: 672)
Process drops python dynamic module
- FuckNiga1.exe (PID: 4040)
Loads Python modules
- FuckNiga1.exe (PID: 2108)
- FuckNiga1.exe (PID: 1056)
- FuckNiga1.exe (PID: 1184)
- FuckNiga1.exe (PID: 5892)
- FuckNiga1.exe (PID: 960)
- FuckNiga1.exe (PID: 4776)
- FuckNiga1.exe (PID: 4272)
- FuckNiga1.exe (PID: 6372)
- FuckNiga1.exe (PID: 672)
- FuckNiga1.exe (PID: 1276)
- FuckNiga1.exe (PID: 2148)
- FuckNiga1.exe (PID: 5588)
- FuckNiga1.exe (PID: 3884)
- FuckNiga1.exe (PID: 1324)
- FuckNiga1.exe (PID: 2384)
- FuckNiga1.exe (PID: 6048)
- FuckNiga1.exe (PID: 904)
- FuckNiga1.exe (PID: 6148)
- FuckNiga1.exe (PID: 6068)
- FuckNiga1.exe (PID: 2392)
- FuckNiga1.exe (PID: 4812)
- FuckNiga1.exe (PID: 3900)
- FuckNiga1.exe (PID: 1764)
- FuckNiga1.exe (PID: 5344)
- FuckNiga1.exe (PID: 5164)
- FuckNiga1.exe (PID: 7188)
- FuckNiga1.exe (PID: 5548)
- FuckNiga1.exe (PID: 7208)
- FuckNiga1.exe (PID: 7244)
- FuckNiga1.exe (PID: 7264)
- FuckNiga1.exe (PID: 7224)
- FuckNiga1.exe (PID: 7300)
- FuckNiga1.exe (PID: 7284)
- FuckNiga1.exe (PID: 7316)
- FuckNiga1.exe (PID: 7344)
- FuckNiga1.exe (PID: 7440)
- FuckNiga1.exe (PID: 7460)
- FuckNiga1.exe (PID: 7476)
- FuckNiga1.exe (PID: 7508)
- FuckNiga1.exe (PID: 7524)
- FuckNiga1.exe (PID: 7548)
- FuckNiga1.exe (PID: 7572)
- FuckNiga1.exe (PID: 7492)
- FuckNiga1.exe (PID: 7620)
- FuckNiga1.exe (PID: 7684)
- FuckNiga1.exe (PID: 7652)
- FuckNiga1.exe (PID: 7668)
- FuckNiga1.exe (PID: 7604)
- FuckNiga1.exe (PID: 7636)
- FuckNiga1.exe (PID: 7700)
- FuckNiga1.exe (PID: 7748)
- FuckNiga1.exe (PID: 7716)
- FuckNiga1.exe (PID: 7780)
- FuckNiga1.exe (PID: 7824)
- FuckNiga1.exe (PID: 7872)
- FuckNiga1.exe (PID: 7944)
- FuckNiga1.exe (PID: 7960)
- FuckNiga1.exe (PID: 8008)
- FuckNiga1.exe (PID: 7988)
- FuckNiga1.exe (PID: 8048)
- FuckNiga1.exe (PID: 7896)
- FuckNiga1.exe (PID: 8080)
- FuckNiga1.exe (PID: 8100)
- FuckNiga1.exe (PID: 8120)
- FuckNiga1.exe (PID: 8148)
- FuckNiga1.exe (PID: 8164)
- FuckNiga1.exe (PID: 8064)
- FuckNiga1.exe (PID: 6676)
- FuckNiga1.exe (PID: 1040)
- FuckNiga1.exe (PID: 6960)
- FuckNiga1.exe (PID: 8184)
- FuckNiga1.exe (PID: 1240)
- FuckNiga1.exe (PID: 6572)
- FuckNiga1.exe (PID: 5084)
- FuckNiga1.exe (PID: 4844)
- FuckNiga1.exe (PID: 6736)
- FuckNiga1.exe (PID: 2908)
- FuckNiga1.exe (PID: 3332)
- FuckNiga1.exe (PID: 4212)
- FuckNiga1.exe (PID: 3008)
- FuckNiga1.exe (PID: 4464)
- FuckNiga1.exe (PID: 4896)
- FuckNiga1.exe (PID: 5136)
- FuckNiga1.exe (PID: 6540)
- FuckNiga1.exe (PID: 4000)
- FuckNiga1.exe (PID: 7432)
- FuckNiga1.exe (PID: 6760)
- FuckNiga1.exe (PID: 4724)
- FuckNiga1.exe (PID: 7596)
- FuckNiga1.exe (PID: 7452)
- FuckNiga1.exe (PID: 5404)
- FuckNiga1.exe (PID: 4424)
- FuckNiga1.exe (PID: 2064)
- FuckNiga1.exe (PID: 6208)
- FuckNiga1.exe (PID: 5600)
- FuckNiga1.exe (PID: 8208)
- FuckNiga1.exe (PID: 8224)
- FuckNiga1.exe (PID: 8240)
- FuckNiga1.exe (PID: 8256)
- FuckNiga1.exe (PID: 8316)
- FuckNiga1.exe (PID: 8288)
- FuckNiga1.exe (PID: 2084)
- FuckNiga1.exe (PID: 8332)
- FuckNiga1.exe (PID: 8408)
- FuckNiga1.exe (PID: 8348)
- FuckNiga1.exe (PID: 8364)
- FuckNiga1.exe (PID: 8384)
- FuckNiga1.exe (PID: 8424)
- FuckNiga1.exe (PID: 8464)
- FuckNiga1.exe (PID: 8488)
- FuckNiga1.exe (PID: 8512)
- FuckNiga1.exe (PID: 8536)
- FuckNiga1.exe (PID: 8440)
- FuckNiga1.exe (PID: 8600)
- FuckNiga1.exe (PID: 8572)
- FuckNiga1.exe (PID: 8620)
- FuckNiga1.exe (PID: 8636)
- FuckNiga1.exe (PID: 8660)
- FuckNiga1.exe (PID: 8556)
- FuckNiga1.exe (PID: 8700)
- FuckNiga1.exe (PID: 8720)
- FuckNiga1.exe (PID: 8680)
- FuckNiga1.exe (PID: 8776)
- FuckNiga1.exe (PID: 8752)
Application launched itself
- FuckNiga1.exe (PID: 2108)
- FuckNiga1.exe (PID: 4040)
- FuckNiga1.exe (PID: 1056)
- FuckNiga1.exe (PID: 1184)
- FuckNiga1.exe (PID: 5892)
- FuckNiga1.exe (PID: 960)
- FuckNiga1.exe (PID: 4272)
- FuckNiga1.exe (PID: 6372)
- FuckNiga1.exe (PID: 672)
- FuckNiga1.exe (PID: 1276)
- FuckNiga1.exe (PID: 1324)
- FuckNiga1.exe (PID: 2148)
- FuckNiga1.exe (PID: 3884)
- FuckNiga1.exe (PID: 5588)
- FuckNiga1.exe (PID: 4776)
- FuckNiga1.exe (PID: 2384)
- FuckNiga1.exe (PID: 6048)
- FuckNiga1.exe (PID: 3900)
- FuckNiga1.exe (PID: 6068)
- FuckNiga1.exe (PID: 6148)
- FuckNiga1.exe (PID: 904)
- FuckNiga1.exe (PID: 2392)
- FuckNiga1.exe (PID: 1764)
- FuckNiga1.exe (PID: 7208)
- FuckNiga1.exe (PID: 5164)
- FuckNiga1.exe (PID: 5344)
- FuckNiga1.exe (PID: 5548)
- FuckNiga1.exe (PID: 7188)
- FuckNiga1.exe (PID: 4812)
- FuckNiga1.exe (PID: 7244)
- FuckNiga1.exe (PID: 7224)
- FuckNiga1.exe (PID: 7264)
- FuckNiga1.exe (PID: 7284)
- FuckNiga1.exe (PID: 7300)
- FuckNiga1.exe (PID: 7316)
- FuckNiga1.exe (PID: 7344)
- FuckNiga1.exe (PID: 7440)
- FuckNiga1.exe (PID: 7460)
- FuckNiga1.exe (PID: 7476)
- FuckNiga1.exe (PID: 7492)
- FuckNiga1.exe (PID: 7508)
- FuckNiga1.exe (PID: 7524)
- FuckNiga1.exe (PID: 7548)
- FuckNiga1.exe (PID: 7572)
- FuckNiga1.exe (PID: 7636)
- FuckNiga1.exe (PID: 7620)
- FuckNiga1.exe (PID: 7652)
- FuckNiga1.exe (PID: 7668)
- FuckNiga1.exe (PID: 7684)
- FuckNiga1.exe (PID: 7604)
- FuckNiga1.exe (PID: 7700)
- FuckNiga1.exe (PID: 7780)
- FuckNiga1.exe (PID: 7716)
- FuckNiga1.exe (PID: 7748)
- FuckNiga1.exe (PID: 7824)
- FuckNiga1.exe (PID: 7872)
- FuckNiga1.exe (PID: 7944)
- FuckNiga1.exe (PID: 7960)
- FuckNiga1.exe (PID: 8048)
- FuckNiga1.exe (PID: 7988)
- FuckNiga1.exe (PID: 8008)
- FuckNiga1.exe (PID: 7896)
- FuckNiga1.exe (PID: 8064)
- FuckNiga1.exe (PID: 8080)
- FuckNiga1.exe (PID: 8100)
- FuckNiga1.exe (PID: 8120)
- FuckNiga1.exe (PID: 8148)
- FuckNiga1.exe (PID: 6676)
- FuckNiga1.exe (PID: 8184)
- FuckNiga1.exe (PID: 1040)
- FuckNiga1.exe (PID: 6960)
- FuckNiga1.exe (PID: 1240)
- FuckNiga1.exe (PID: 8164)
- FuckNiga1.exe (PID: 2908)
- FuckNiga1.exe (PID: 6572)
- FuckNiga1.exe (PID: 5084)
- FuckNiga1.exe (PID: 6736)
- FuckNiga1.exe (PID: 3332)
- FuckNiga1.exe (PID: 4844)
- FuckNiga1.exe (PID: 4212)
- FuckNiga1.exe (PID: 3008)
- FuckNiga1.exe (PID: 4464)
- FuckNiga1.exe (PID: 6540)
- FuckNiga1.exe (PID: 5136)
- FuckNiga1.exe (PID: 4000)
- FuckNiga1.exe (PID: 7432)
- FuckNiga1.exe (PID: 7596)
- FuckNiga1.exe (PID: 6760)
- FuckNiga1.exe (PID: 4896)
- FuckNiga1.exe (PID: 4724)
- FuckNiga1.exe (PID: 7452)
- FuckNiga1.exe (PID: 5404)
- FuckNiga1.exe (PID: 4424)
- FuckNiga1.exe (PID: 2064)
- FuckNiga1.exe (PID: 5600)
- FuckNiga1.exe (PID: 8208)
- FuckNiga1.exe (PID: 8224)
- FuckNiga1.exe (PID: 8240)
- FuckNiga1.exe (PID: 8256)
- FuckNiga1.exe (PID: 8288)
- FuckNiga1.exe (PID: 6208)
- FuckNiga1.exe (PID: 2084)
- FuckNiga1.exe (PID: 8348)
- FuckNiga1.exe (PID: 8316)
- FuckNiga1.exe (PID: 8332)
- FuckNiga1.exe (PID: 8384)
- FuckNiga1.exe (PID: 8364)
- FuckNiga1.exe (PID: 8408)
- FuckNiga1.exe (PID: 8464)
- FuckNiga1.exe (PID: 8440)
- FuckNiga1.exe (PID: 8536)
- FuckNiga1.exe (PID: 8424)
- FuckNiga1.exe (PID: 8488)
- FuckNiga1.exe (PID: 8512)
- FuckNiga1.exe (PID: 8556)
- FuckNiga1.exe (PID: 8572)
- FuckNiga1.exe (PID: 8600)
- FuckNiga1.exe (PID: 8620)
- FuckNiga1.exe (PID: 8636)
- FuckNiga1.exe (PID: 8680)
- FuckNiga1.exe (PID: 8700)
- FuckNiga1.exe (PID: 8720)
- FuckNiga1.exe (PID: 8660)
- FuckNiga1.exe (PID: 8752)
- FuckNiga1.exe (PID: 8776)
INFO
Reads the computer name
- FuckNiga1.exe (PID: 4040)
Checks supported languages
- FuckNiga1.exe (PID: 4040)
- FuckNiga1.exe (PID: 2108)
- FuckNiga1.exe (PID: 1056)
- FuckNiga1.exe (PID: 1184)
- FuckNiga1.exe (PID: 5892)
- FuckNiga1.exe (PID: 960)
- FuckNiga1.exe (PID: 4272)
- FuckNiga1.exe (PID: 6372)
- FuckNiga1.exe (PID: 672)
- FuckNiga1.exe (PID: 4776)
- FuckNiga1.exe (PID: 2148)
- FuckNiga1.exe (PID: 5588)
- FuckNiga1.exe (PID: 3884)
- FuckNiga1.exe (PID: 1324)
- FuckNiga1.exe (PID: 2384)
- FuckNiga1.exe (PID: 1276)
- FuckNiga1.exe (PID: 6048)
- FuckNiga1.exe (PID: 3900)
- FuckNiga1.exe (PID: 6068)
- FuckNiga1.exe (PID: 6148)
- FuckNiga1.exe (PID: 904)
- FuckNiga1.exe (PID: 2392)
- FuckNiga1.exe (PID: 4812)
- FuckNiga1.exe (PID: 5164)
- FuckNiga1.exe (PID: 5344)
- FuckNiga1.exe (PID: 5548)
- FuckNiga1.exe (PID: 7188)
- FuckNiga1.exe (PID: 7208)
- FuckNiga1.exe (PID: 1764)
- FuckNiga1.exe (PID: 7244)
- FuckNiga1.exe (PID: 7264)
- FuckNiga1.exe (PID: 7224)
- FuckNiga1.exe (PID: 7300)
- FuckNiga1.exe (PID: 7284)
- FuckNiga1.exe (PID: 7316)
- FuckNiga1.exe (PID: 7344)
- FuckNiga1.exe (PID: 7440)
- FuckNiga1.exe (PID: 7460)
- FuckNiga1.exe (PID: 7476)
- FuckNiga1.exe (PID: 7492)
- FuckNiga1.exe (PID: 7548)
- FuckNiga1.exe (PID: 7508)
- FuckNiga1.exe (PID: 7524)
- FuckNiga1.exe (PID: 7572)
- FuckNiga1.exe (PID: 7652)
- FuckNiga1.exe (PID: 7668)
- FuckNiga1.exe (PID: 7684)
- FuckNiga1.exe (PID: 7604)
- FuckNiga1.exe (PID: 7620)
- FuckNiga1.exe (PID: 7636)
- FuckNiga1.exe (PID: 7716)
- FuckNiga1.exe (PID: 7748)
- FuckNiga1.exe (PID: 7780)
- FuckNiga1.exe (PID: 7824)
- FuckNiga1.exe (PID: 7872)
- FuckNiga1.exe (PID: 7896)
- FuckNiga1.exe (PID: 7700)
- FuckNiga1.exe (PID: 7960)
- FuckNiga1.exe (PID: 7988)
- FuckNiga1.exe (PID: 8008)
- FuckNiga1.exe (PID: 8048)
- FuckNiga1.exe (PID: 8064)
- FuckNiga1.exe (PID: 7944)
- FuckNiga1.exe (PID: 8080)
- FuckNiga1.exe (PID: 8164)
- FuckNiga1.exe (PID: 8120)
- FuckNiga1.exe (PID: 8148)
- FuckNiga1.exe (PID: 8100)
- FuckNiga1.exe (PID: 8184)
- FuckNiga1.exe (PID: 1040)
- FuckNiga1.exe (PID: 6676)
- FuckNiga1.exe (PID: 6960)
- FuckNiga1.exe (PID: 2908)
- FuckNiga1.exe (PID: 1240)
- FuckNiga1.exe (PID: 3332)
- FuckNiga1.exe (PID: 6572)
- FuckNiga1.exe (PID: 5084)
- FuckNiga1.exe (PID: 4844)
- FuckNiga1.exe (PID: 6736)
- FuckNiga1.exe (PID: 3008)
- FuckNiga1.exe (PID: 4896)
- FuckNiga1.exe (PID: 6540)
- FuckNiga1.exe (PID: 5136)
- FuckNiga1.exe (PID: 4212)
- FuckNiga1.exe (PID: 4464)
- FuckNiga1.exe (PID: 7432)
- FuckNiga1.exe (PID: 7596)
- FuckNiga1.exe (PID: 6760)
- FuckNiga1.exe (PID: 5600)
- FuckNiga1.exe (PID: 4724)
- FuckNiga1.exe (PID: 4000)
- FuckNiga1.exe (PID: 5404)
- FuckNiga1.exe (PID: 4424)
- FuckNiga1.exe (PID: 2064)
- FuckNiga1.exe (PID: 6208)
- FuckNiga1.exe (PID: 7452)
- FuckNiga1.exe (PID: 8208)
- FuckNiga1.exe (PID: 8224)
- FuckNiga1.exe (PID: 8240)
- FuckNiga1.exe (PID: 8256)
- FuckNiga1.exe (PID: 8288)
- FuckNiga1.exe (PID: 2084)
- FuckNiga1.exe (PID: 8316)
- FuckNiga1.exe (PID: 8332)
- FuckNiga1.exe (PID: 8348)
- FuckNiga1.exe (PID: 8364)
- FuckNiga1.exe (PID: 8384)
- FuckNiga1.exe (PID: 8408)
- FuckNiga1.exe (PID: 8464)
- FuckNiga1.exe (PID: 8488)
- FuckNiga1.exe (PID: 8512)
- FuckNiga1.exe (PID: 8556)
- FuckNiga1.exe (PID: 8424)
- FuckNiga1.exe (PID: 8440)
- FuckNiga1.exe (PID: 8536)
- FuckNiga1.exe (PID: 8572)
- FuckNiga1.exe (PID: 8636)
- FuckNiga1.exe (PID: 8600)
- FuckNiga1.exe (PID: 8620)
- FuckNiga1.exe (PID: 8660)
- FuckNiga1.exe (PID: 8700)
- FuckNiga1.exe (PID: 8752)
- FuckNiga1.exe (PID: 8680)
- FuckNiga1.exe (PID: 8720)
- FuckNiga1.exe (PID: 8776)
- FuckNiga1.exe (PID: 8836)
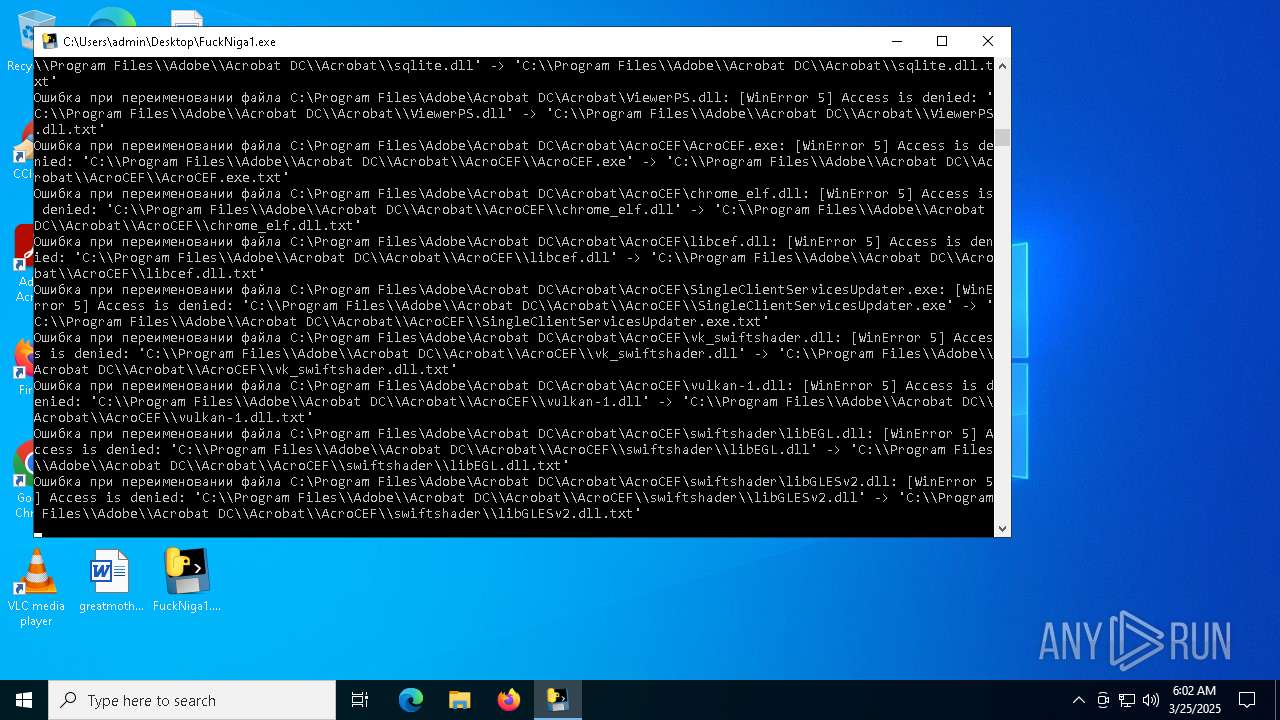
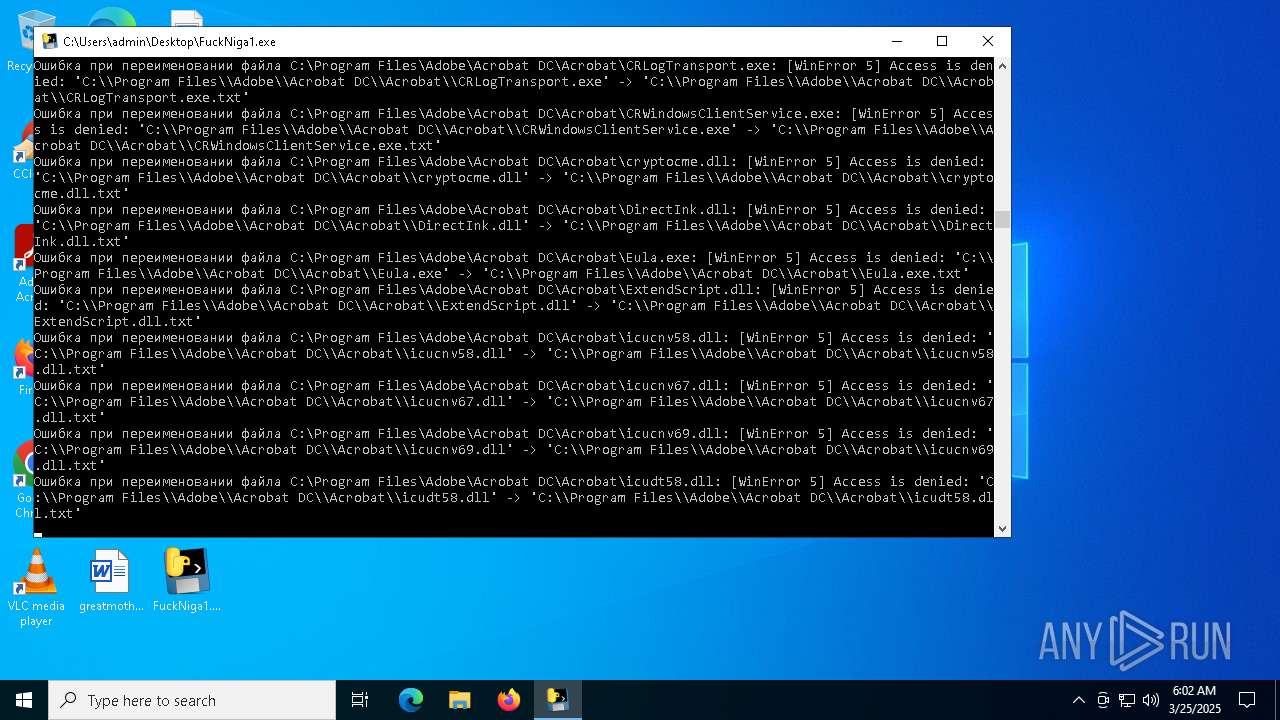
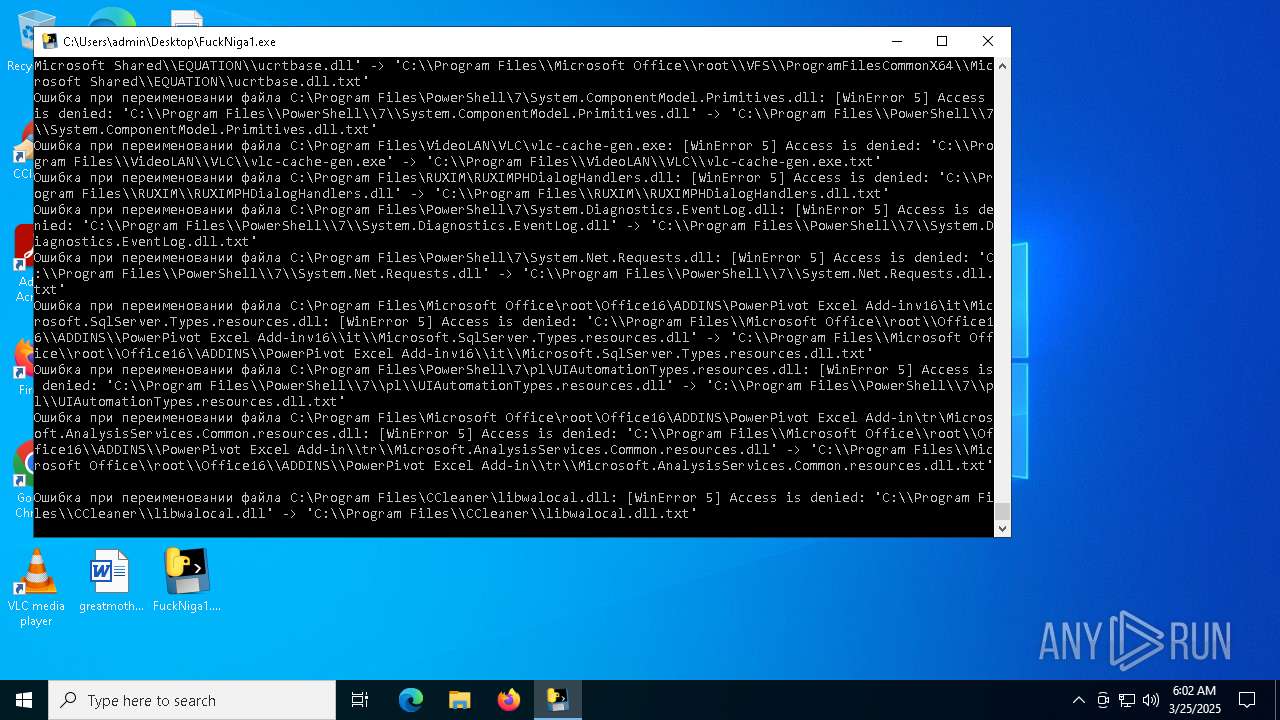
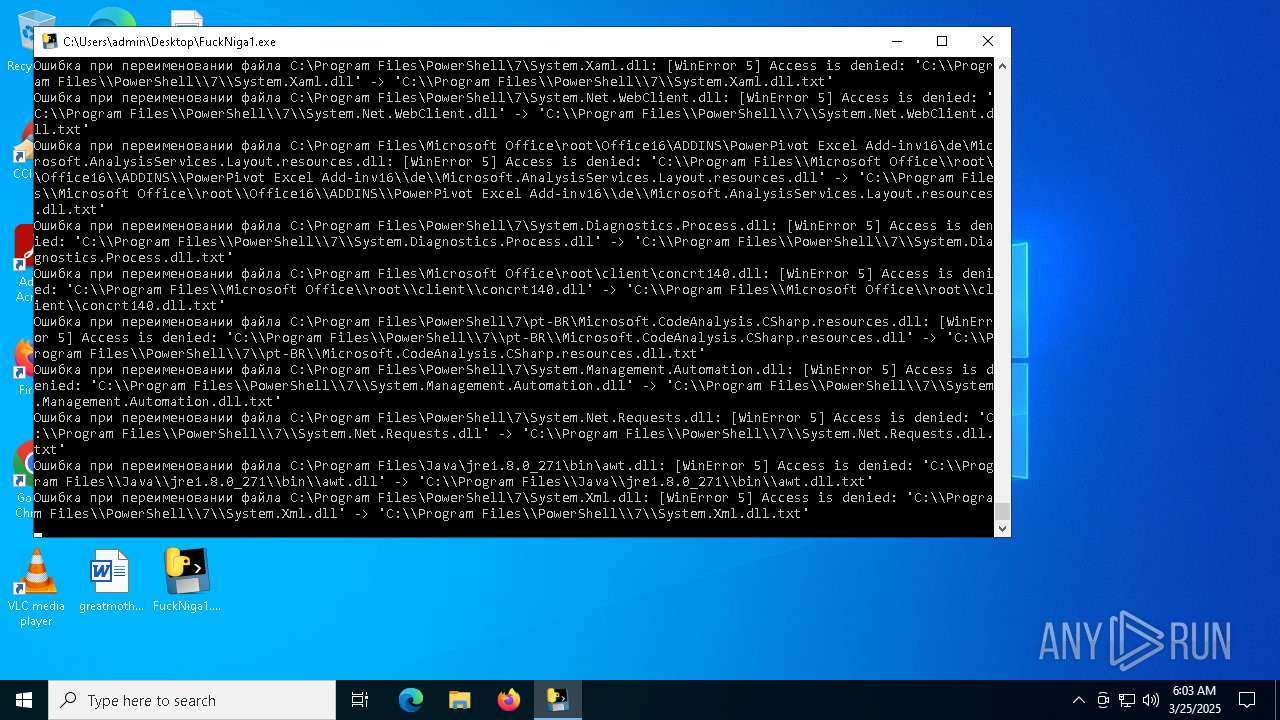
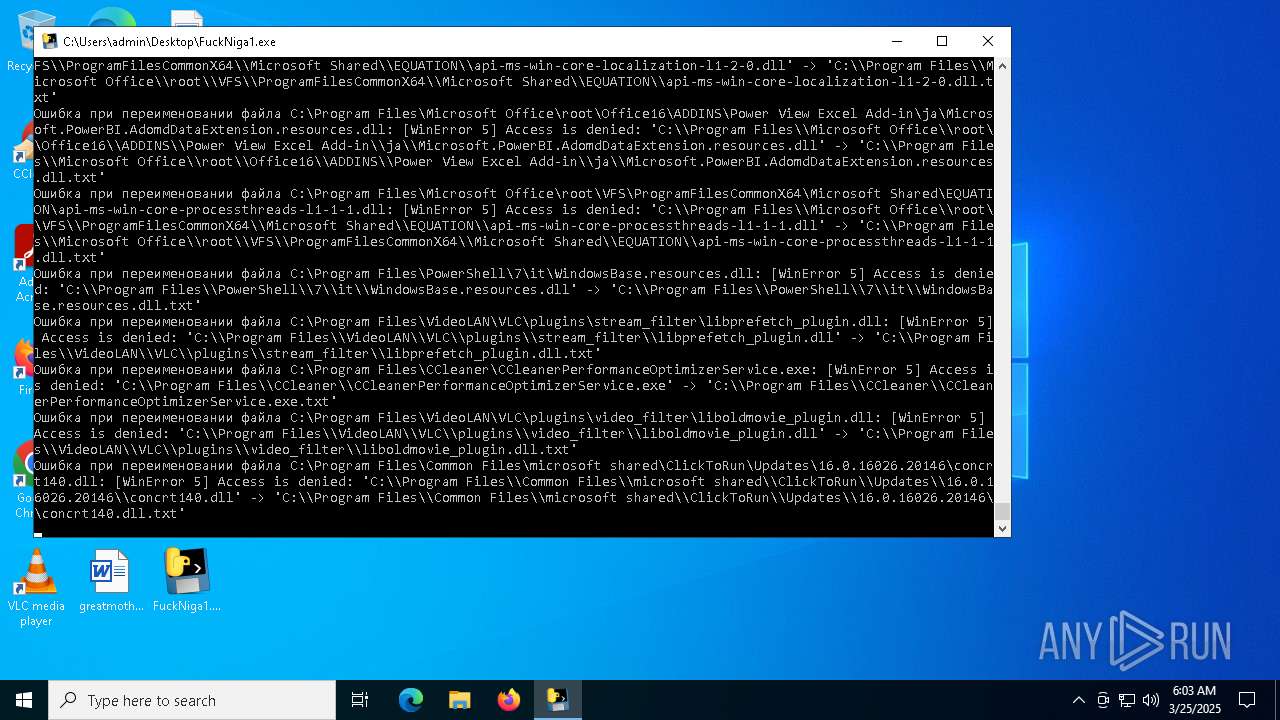
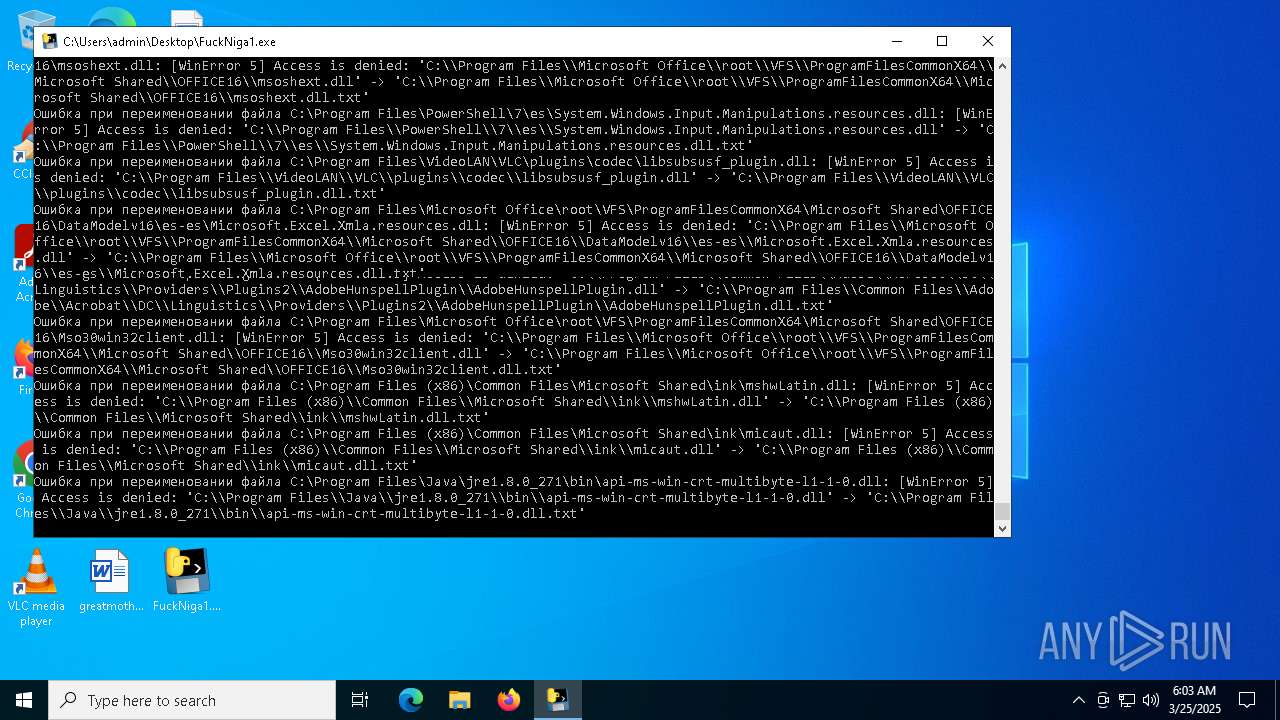
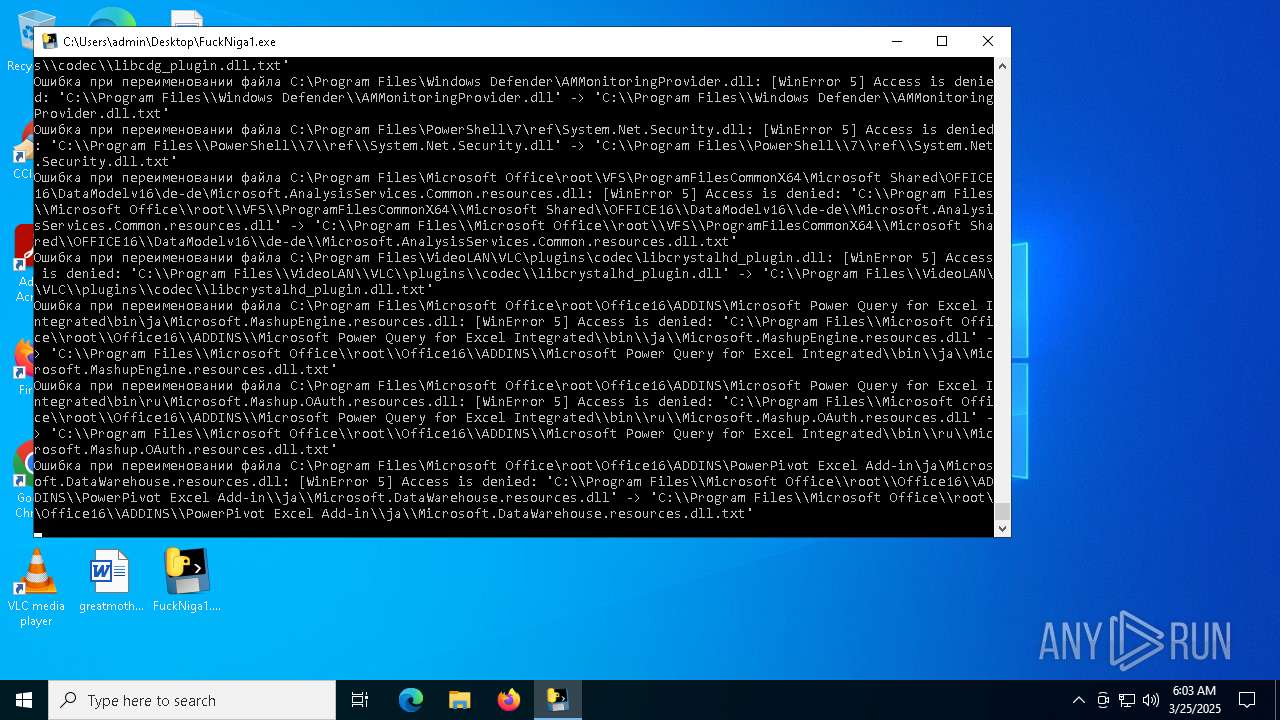
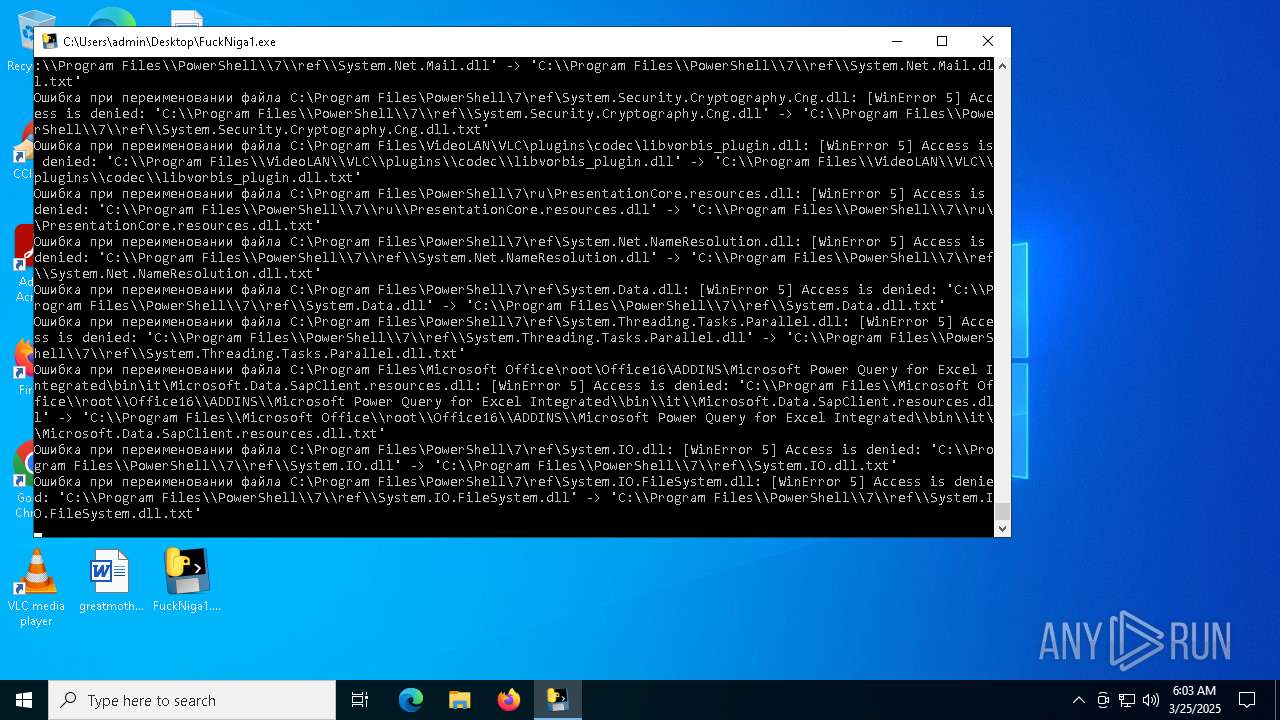
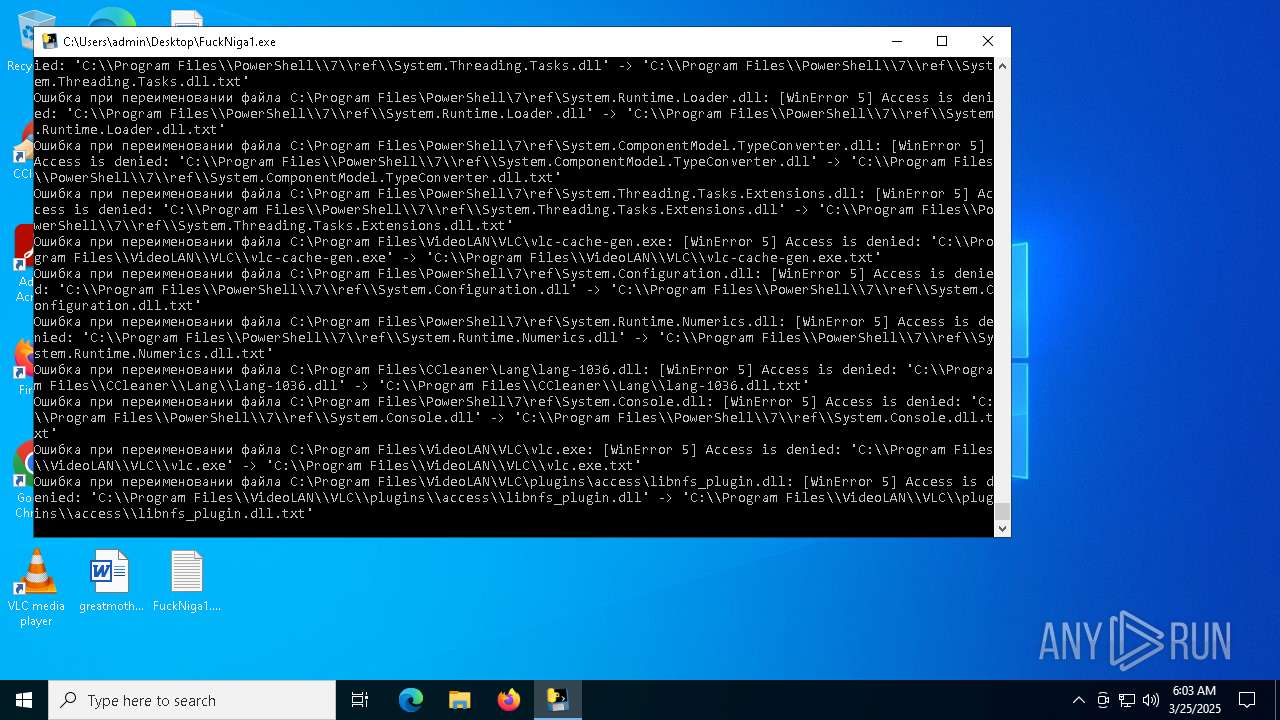
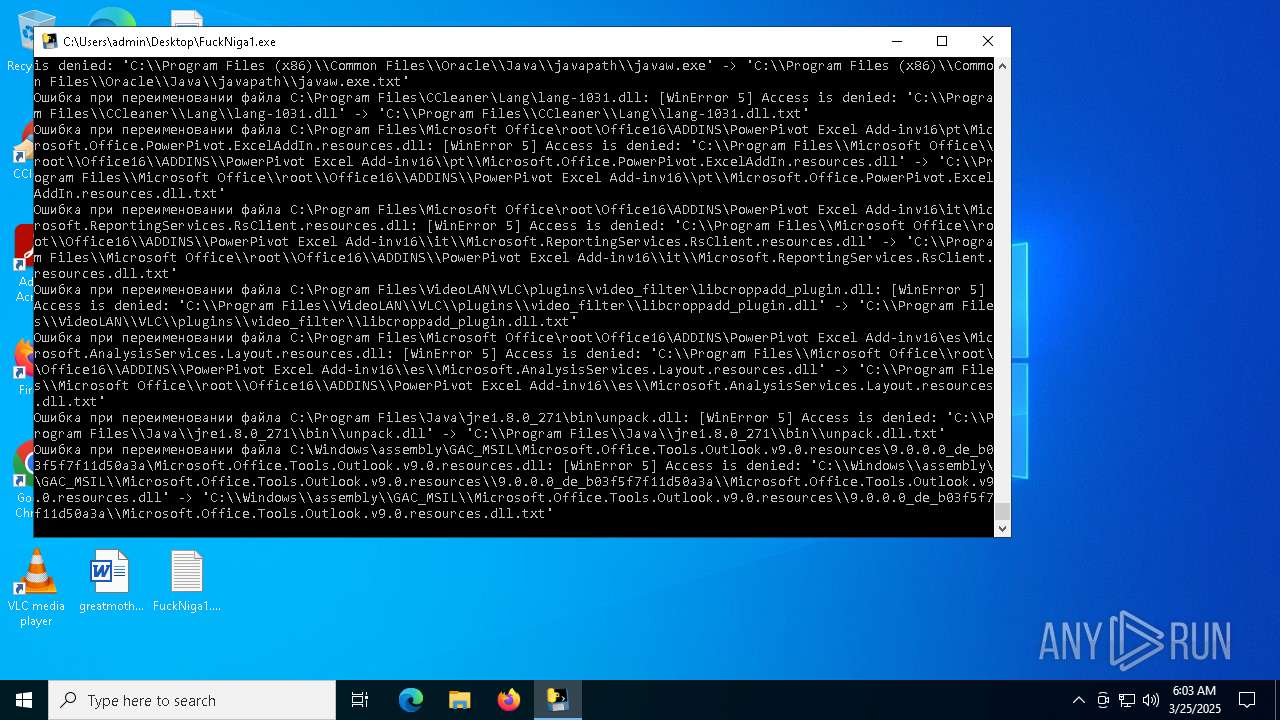
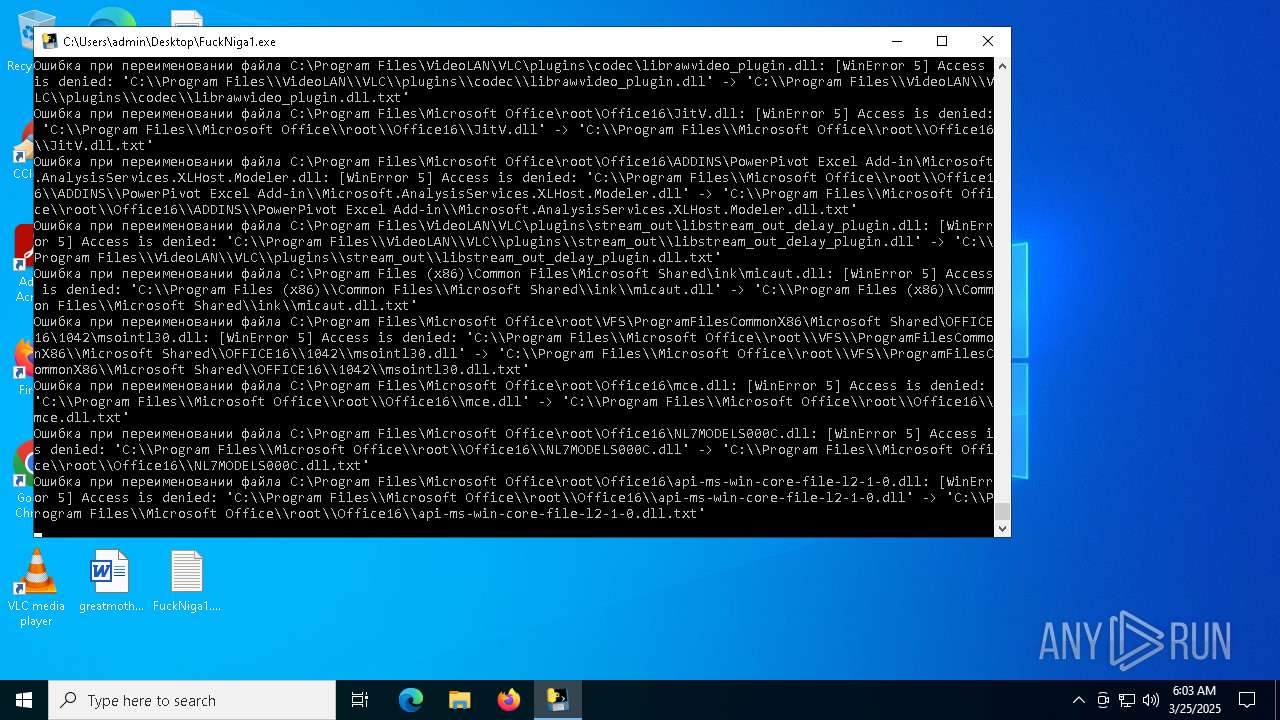
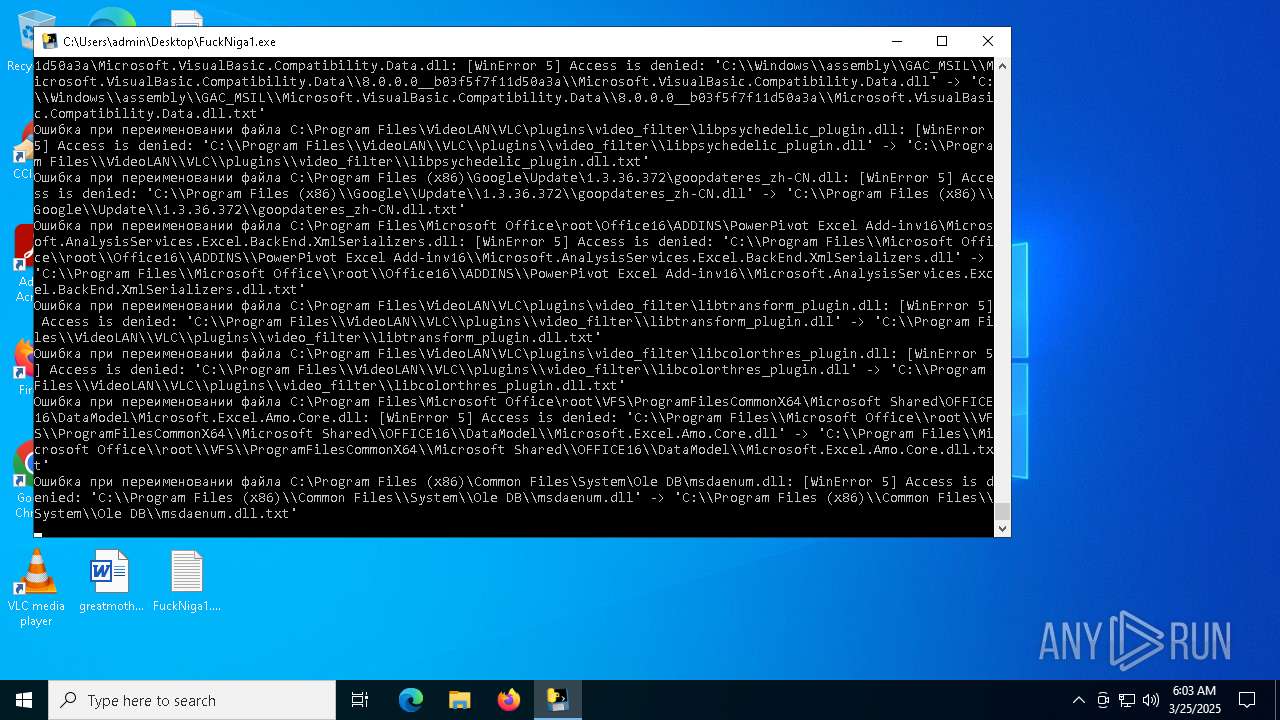
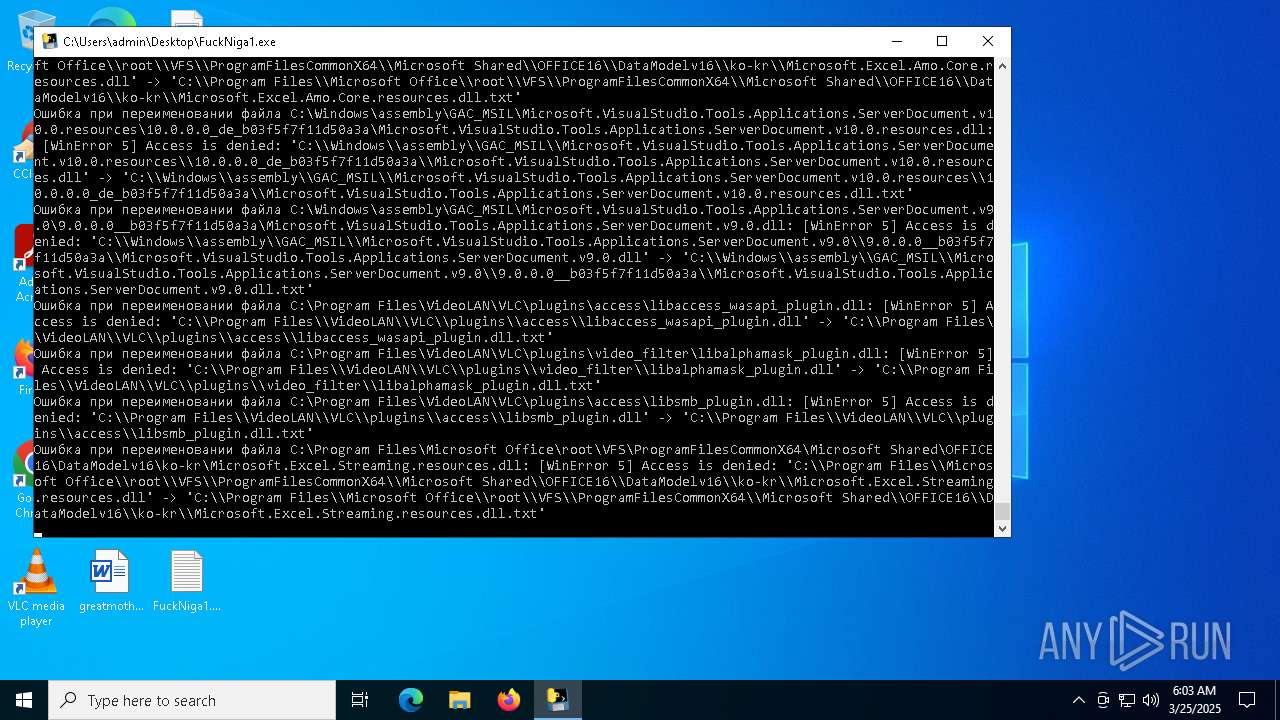
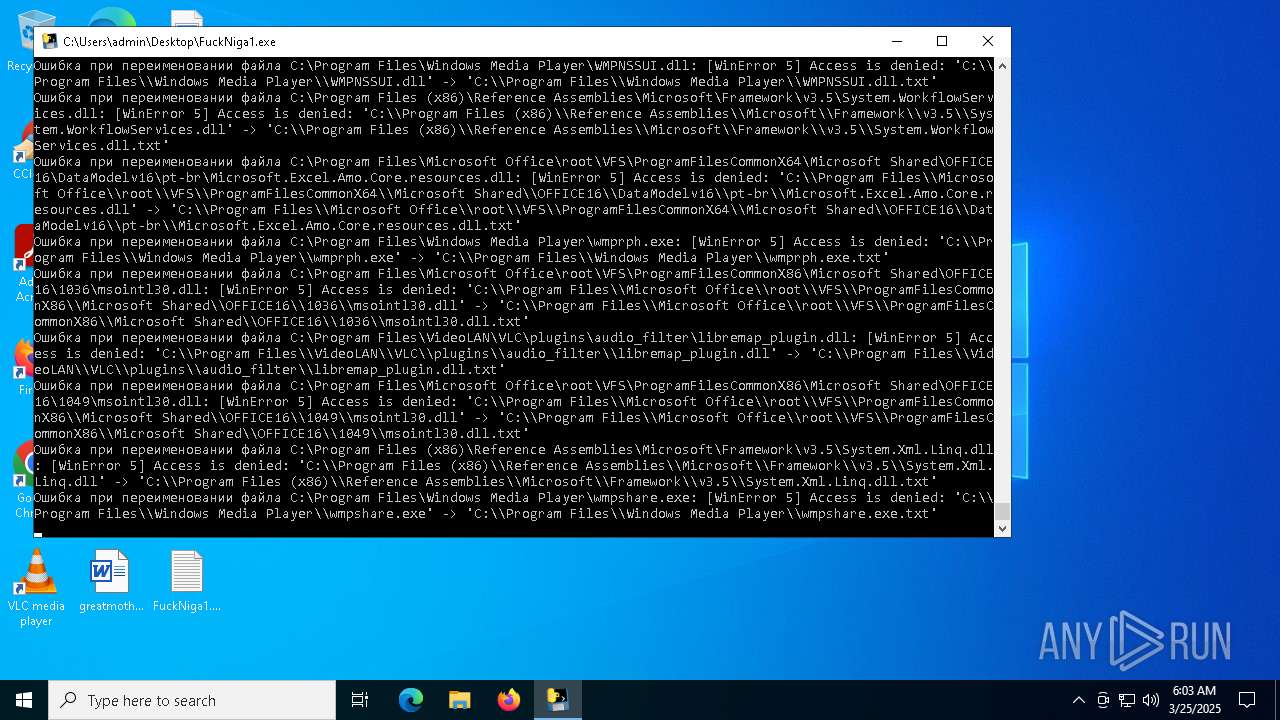
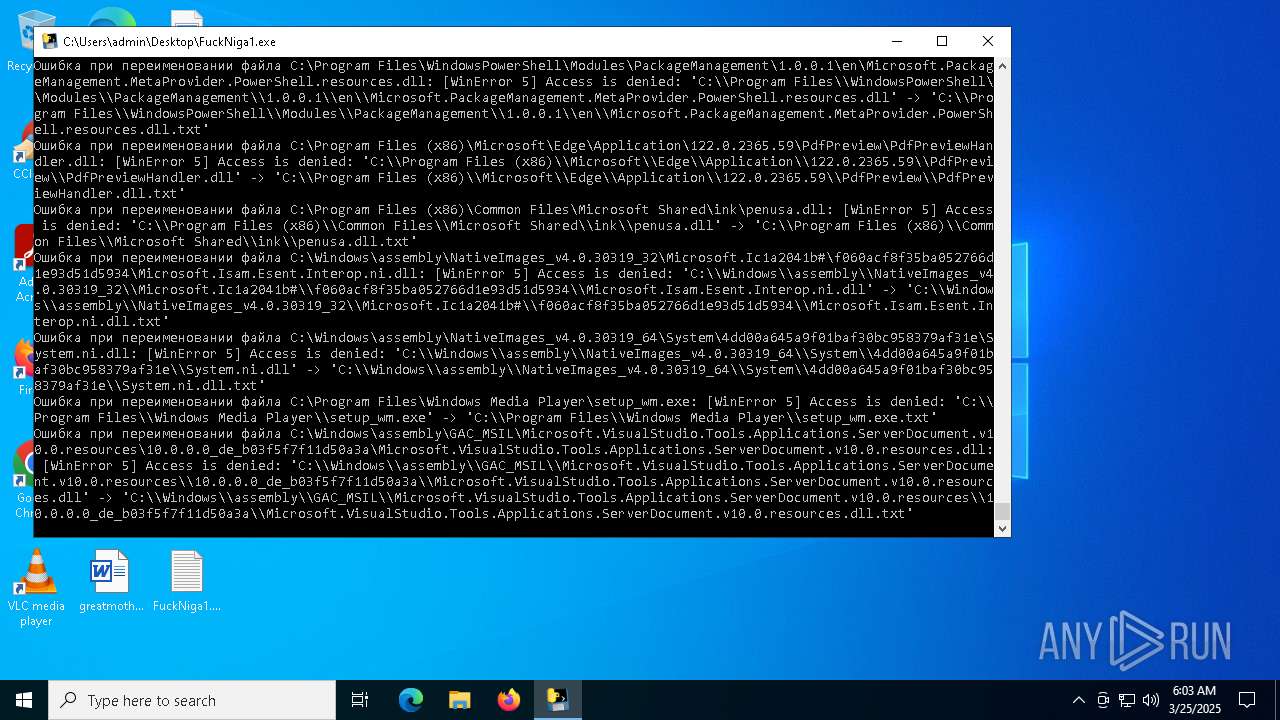
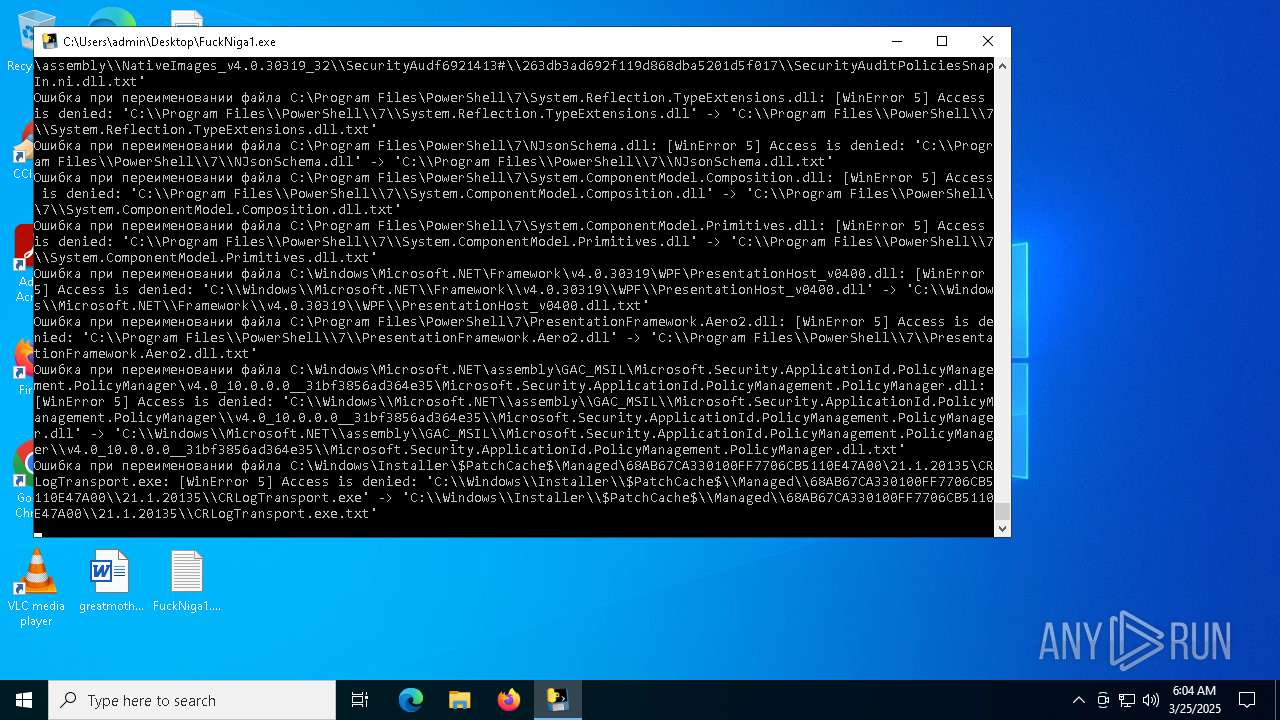
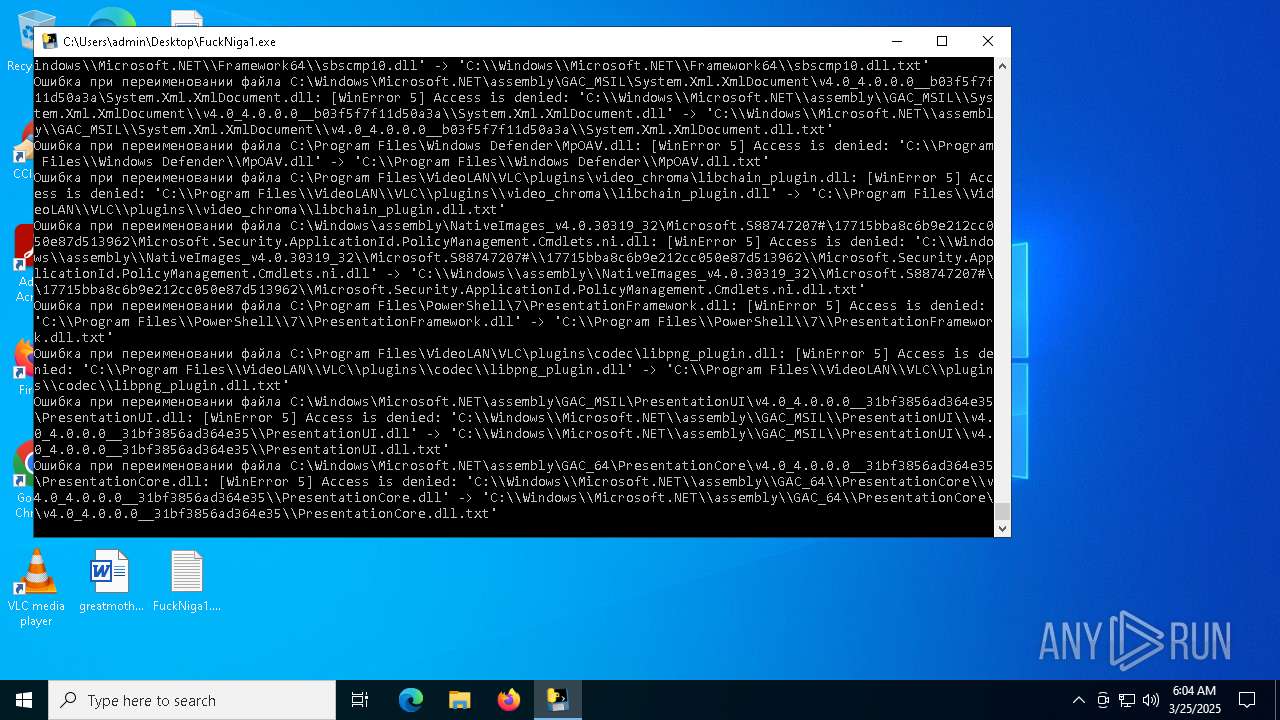
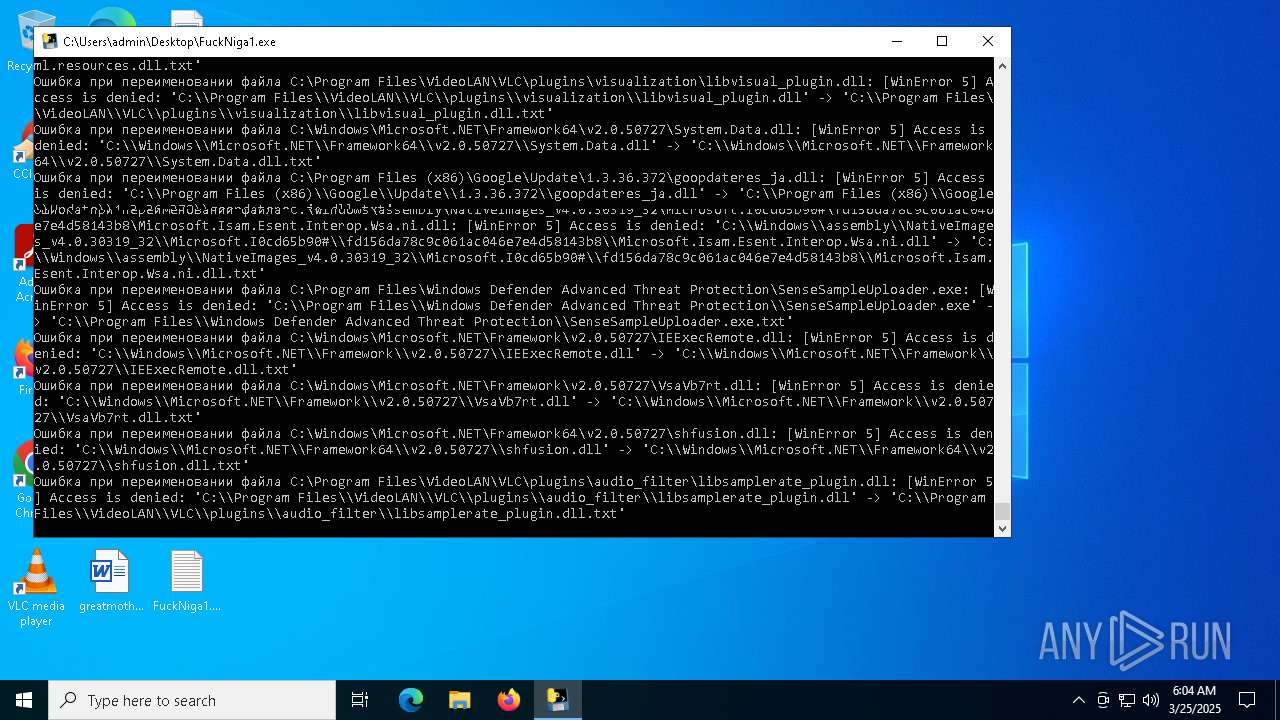
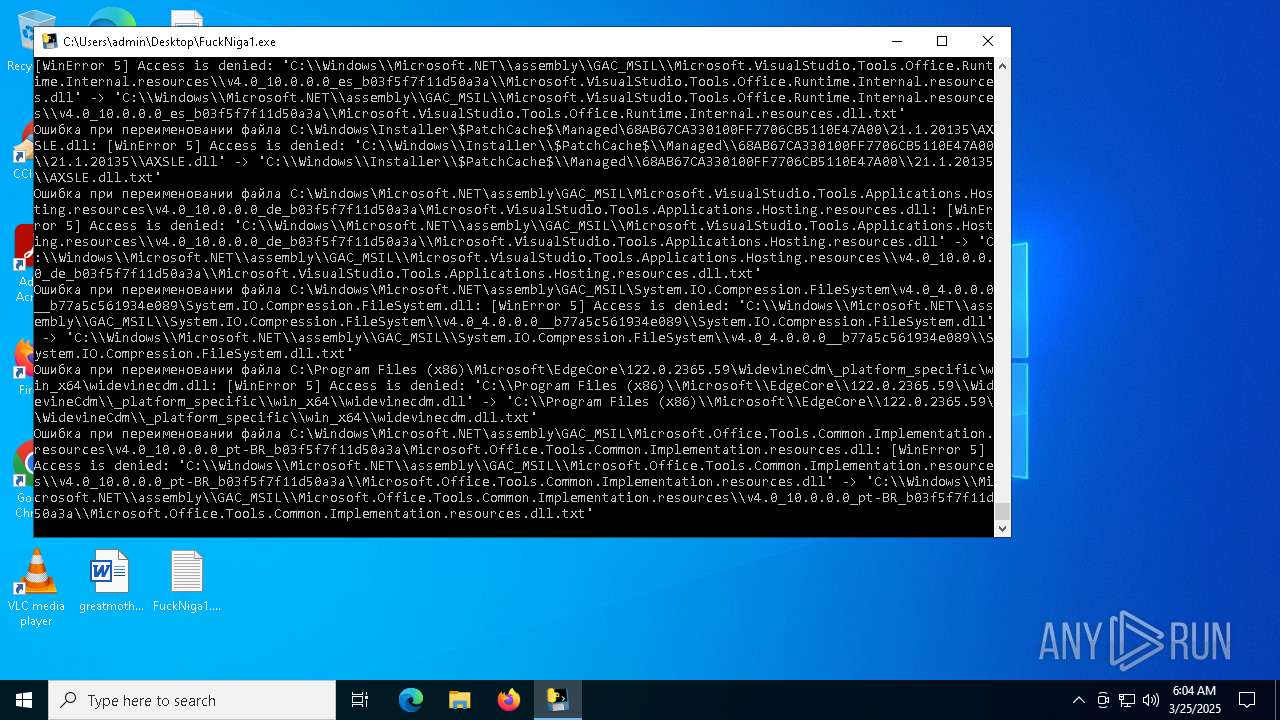
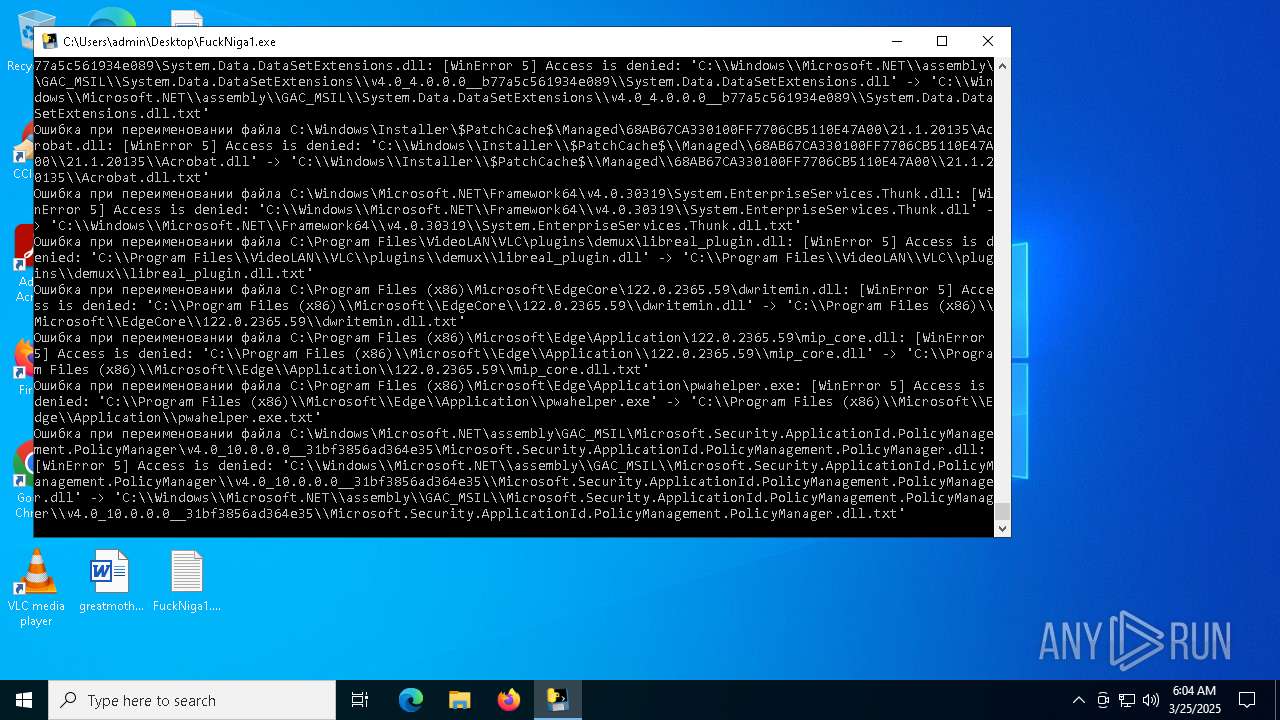
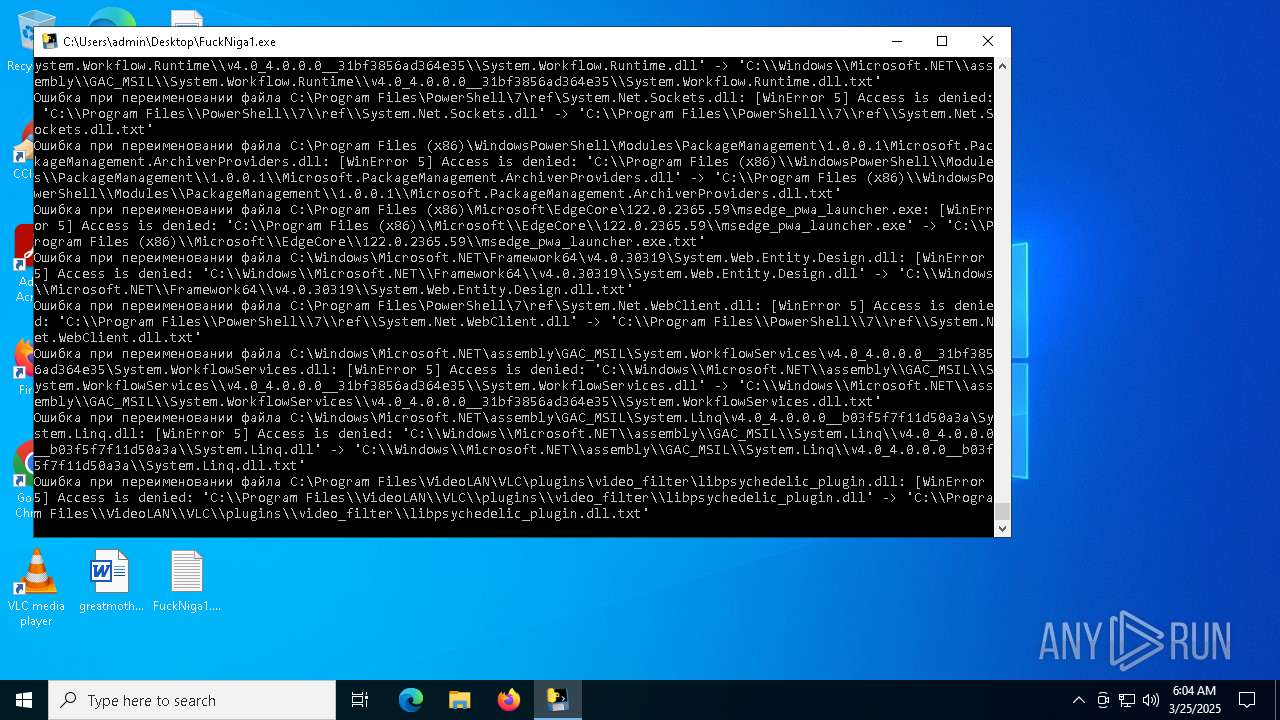
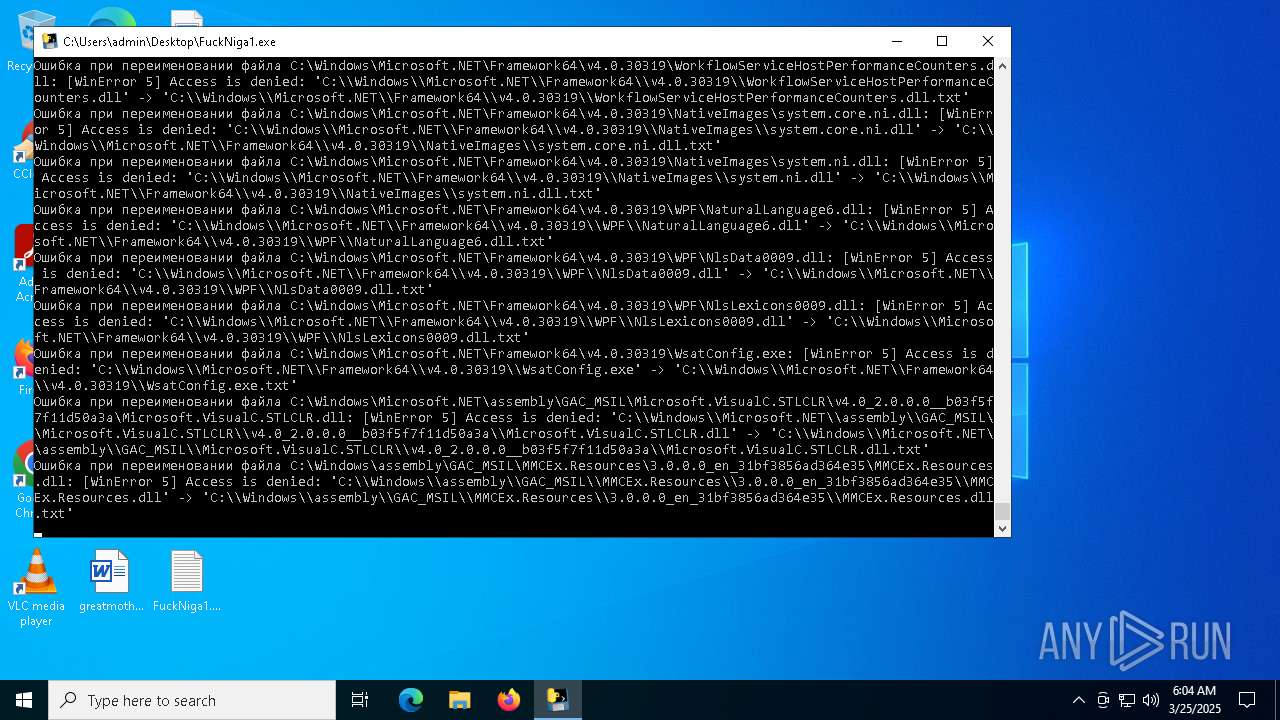
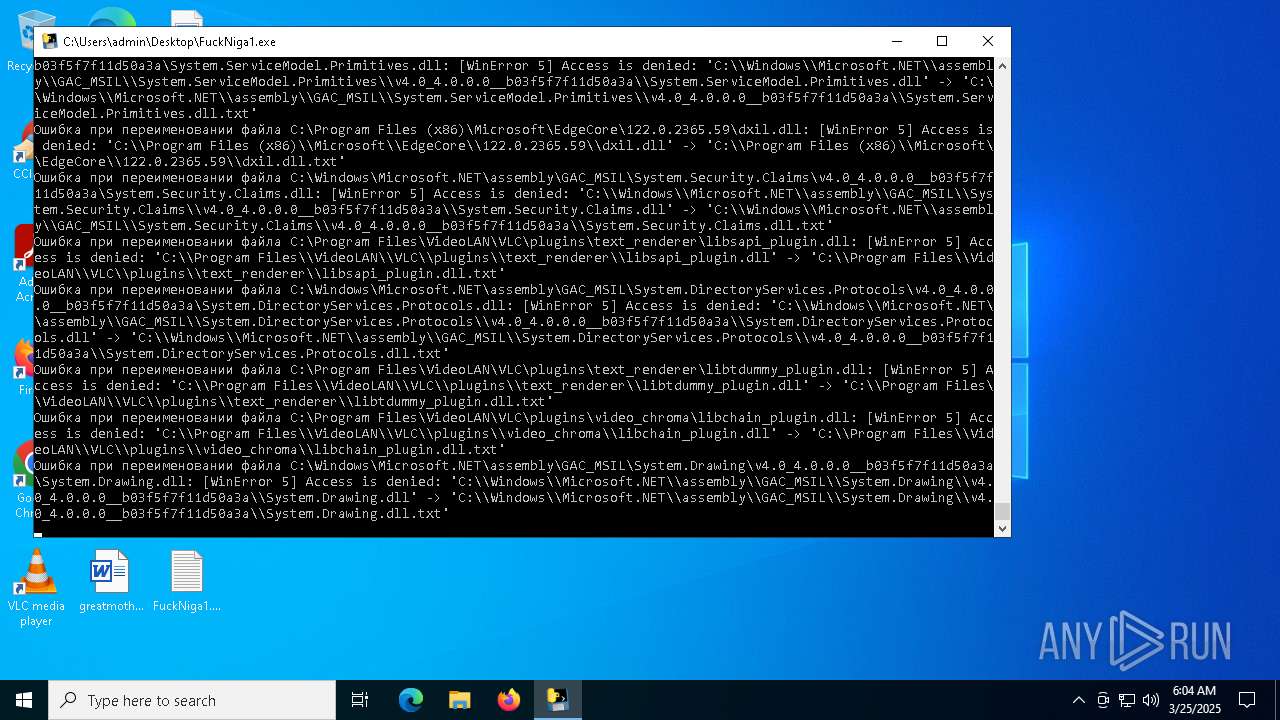
Create files in a temporary directory
- FuckNiga1.exe (PID: 4040)
The sample compiled with english language support
- FuckNiga1.exe (PID: 4040)
- FuckNiga1.exe (PID: 1184)
- FuckNiga1.exe (PID: 4272)
- FuckNiga1.exe (PID: 2108)
- FuckNiga1.exe (PID: 672)
PyInstaller has been detected (YARA)
- FuckNiga1.exe (PID: 4040)
- FuckNiga1.exe (PID: 2108)
- FuckNiga1.exe (PID: 1056)
- FuckNiga1.exe (PID: 1184)
- FuckNiga1.exe (PID: 5892)
SQLite executable
- FuckNiga1.exe (PID: 1184)
- FuckNiga1.exe (PID: 672)
Checks proxy server information
- slui.exe (PID: 8792)
Reads the software policy settings
- slui.exe (PID: 8792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:03:25 05:36:31+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 176640 |
| InitializedDataSize: | 152576 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc320 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
250
Monitored processes
128
Malicious processes
9
Suspicious processes
113
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | "C:\Users\admin\Desktop\FuckNiga1.exe" "--multiprocessing-fork" "parent_pid=6372" "pipe_handle=408" | C:\Users\admin\Desktop\FuckNiga1.exe | FuckNiga1.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 904 | "C:\Users\admin\Desktop\FuckNiga1.exe" "--multiprocessing-fork" "parent_pid=6148" "pipe_handle=372" | C:\Users\admin\Desktop\FuckNiga1.exe | — | FuckNiga1.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 960 | "C:\Users\admin\Desktop\FuckNiga1.exe" "--multiprocessing-fork" "parent_pid=5892" "pipe_handle=368" | C:\Users\admin\Desktop\FuckNiga1.exe | — | FuckNiga1.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1040 | "C:\Users\admin\Desktop\FuckNiga1.exe" "--multiprocessing-fork" "parent_pid=6676" "pipe_handle=372" | C:\Users\admin\Desktop\FuckNiga1.exe | — | FuckNiga1.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1056 | "C:\Users\admin\Desktop\FuckNiga1.exe" "--multiprocessing-fork" "parent_pid=2108" "pipe_handle=392" | C:\Users\admin\Desktop\FuckNiga1.exe | — | FuckNiga1.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1184 | "C:\Users\admin\Desktop\FuckNiga1.exe" "--multiprocessing-fork" "parent_pid=1056" "pipe_handle=504" | C:\Users\admin\Desktop\FuckNiga1.exe | FuckNiga1.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1240 | "C:\Users\admin\Desktop\FuckNiga1.exe" "--multiprocessing-fork" "parent_pid=1040" "pipe_handle=536" | C:\Users\admin\Desktop\FuckNiga1.exe | — | FuckNiga1.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1276 | "C:\Users\admin\Desktop\FuckNiga1.exe" "--multiprocessing-fork" "parent_pid=2384" "pipe_handle=276" | C:\Users\admin\Desktop\FuckNiga1.exe | — | FuckNiga1.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1324 | "C:\Users\admin\Desktop\FuckNiga1.exe" "--multiprocessing-fork" "parent_pid=3884" "pipe_handle=376" | C:\Users\admin\Desktop\FuckNiga1.exe | — | FuckNiga1.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1764 | "C:\Users\admin\Desktop\FuckNiga1.exe" "--multiprocessing-fork" "parent_pid=4812" "pipe_handle=380" | C:\Users\admin\Desktop\FuckNiga1.exe | — | FuckNiga1.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
22 754
Read events
22 754
Write events
0
Delete events
0
Modification events
Executable files
154
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4040 | FuckNiga1.exe | C:\Users\admin\AppData\Local\Temp\_MEI40402\VCRUNTIME140.dll | executable | |
MD5:BE8DBE2DC77EBE7F88F910C61AEC691A | SHA256:4D292623516F65C80482081E62D5DADB759DC16E851DE5DB24C3CBB57B87DB83 | |||
| 4040 | FuckNiga1.exe | C:\Users\admin\AppData\Local\Temp\_MEI40402\_socket.pyd | executable | |
MD5:E43AED7D6A8BCD9DDFC59C2D1A2C4B02 | SHA256:2C2A6A6BA360E38F0C2B5A53B4626F833A3111844D95615EBF35BE0E76B1EF7A | |||
| 4040 | FuckNiga1.exe | C:\Users\admin\AppData\Local\Temp\_MEI40402\_decimal.pyd | executable | |
MD5:CEA3B419C7CA87140A157629C6DBD299 | SHA256:95B9850E6FB335B235589DD1348E007507C6B28E332C9ABB111F2A0035C358E5 | |||
| 4040 | FuckNiga1.exe | C:\Users\admin\AppData\Local\Temp\_MEI40402\libcrypto-3.dll | executable | |
MD5:E547CF6D296A88F5B1C352C116DF7C0C | SHA256:05FE080EAB7FC535C51E10C1BD76A2F3E6217F9C91A25034774588881C3F99DE | |||
| 4040 | FuckNiga1.exe | C:\Users\admin\AppData\Local\Temp\_MEI40402\_hashlib.pyd | executable | |
MD5:D19CB5CA144AE1FD29B6395B0225CF40 | SHA256:F95EC2562A3C70FB1A6E44D72F4223CE3C7A0F0038159D09DCE629F59591D5AA | |||
| 4040 | FuckNiga1.exe | C:\Users\admin\AppData\Local\Temp\_MEI40402\libffi-8.dll | executable | |
MD5:0F8E4992CA92BAAF54CC0B43AACCCE21 | SHA256:EFF52743773EB550FCC6CE3EFC37C85724502233B6B002A35496D828BD7B280A | |||
| 4040 | FuckNiga1.exe | C:\Users\admin\AppData\Local\Temp\_MEI40402\_ctypes.pyd | executable | |
MD5:C8AFA1EBB28828E1115C110313D2A810 | SHA256:8978972CF341CCD0EDF8435D63909A739DF7EF29EC7DD57ED5CAB64B342891F0 | |||
| 4040 | FuckNiga1.exe | C:\Users\admin\AppData\Local\Temp\_MEI40402\base_library.zip | compressed | |
MD5:763D1A751C5D47212FBF0CAEA63F46F5 | SHA256:378A4B40F4FA4A8229C93E0AFEE819085251AF03402CCEFA3B469651E50E60B7 | |||
| 4040 | FuckNiga1.exe | C:\Users\admin\AppData\Local\Temp\_MEI40402\pyexpat.pyd | executable | |
MD5:815F1BDABB79C6A12B38D84AA343196D | SHA256:31712AE276E2CED05ECDA3E1C08FBBCC2CFF8474A972626ABA55F7797F0ED8C9 | |||
| 4040 | FuckNiga1.exe | C:\Users\admin\AppData\Local\Temp\_MEI40402\libssl-3.dll | executable | |
MD5:19A2ABA25456181D5FB572D88AC0E73E | SHA256:2E9FBCD8F7FDC13A5179533239811456554F2B3AA2FB10E1B17BE0DF81C79006 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
21
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6964 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
8792 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |